Identifying code generating method, safety identification method, safety identification device and safety identification system
A security verification and verification code technology, applied in transmission systems, electrical components, etc., can solve the problems of low cheating cost, long time required, cumbersome operation, etc., and achieve the effect of blocking cheating behavior, improving user experience, and increasing the difficulty of cracking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
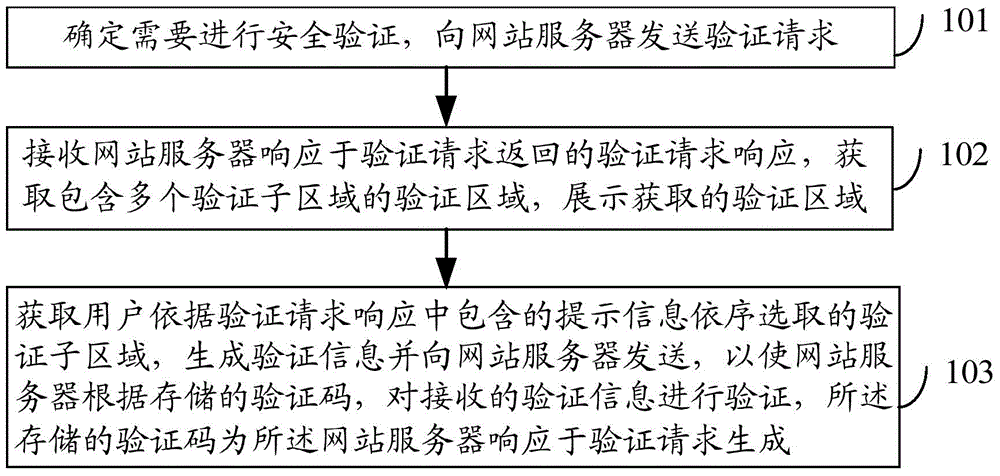
[0032] Embodiment 1. A security verification method.
[0033] figure 1 It is a schematic flowchart of a security verification method provided by an embodiment of the present invention. see figure 1 , the process includes:
[0034] Step 101, determine that security verification is required, and send a verification request to the website server;
[0035]In this step, when the user logs in to the forum, the questioning website, the user click volume statistics website, the user rating website and other website servers through the client browser, or when the user needs to post content or give a rating or submit a question after logging in to the website server, Trigger security verification. For example, when a user logs in to a BBS forum through a client browser, when starting the BBS server login interface, in order to prevent the machine program from automatically logging in, the client can determine that the user needs to perform security verification, thereby automaticall...
Embodiment 2
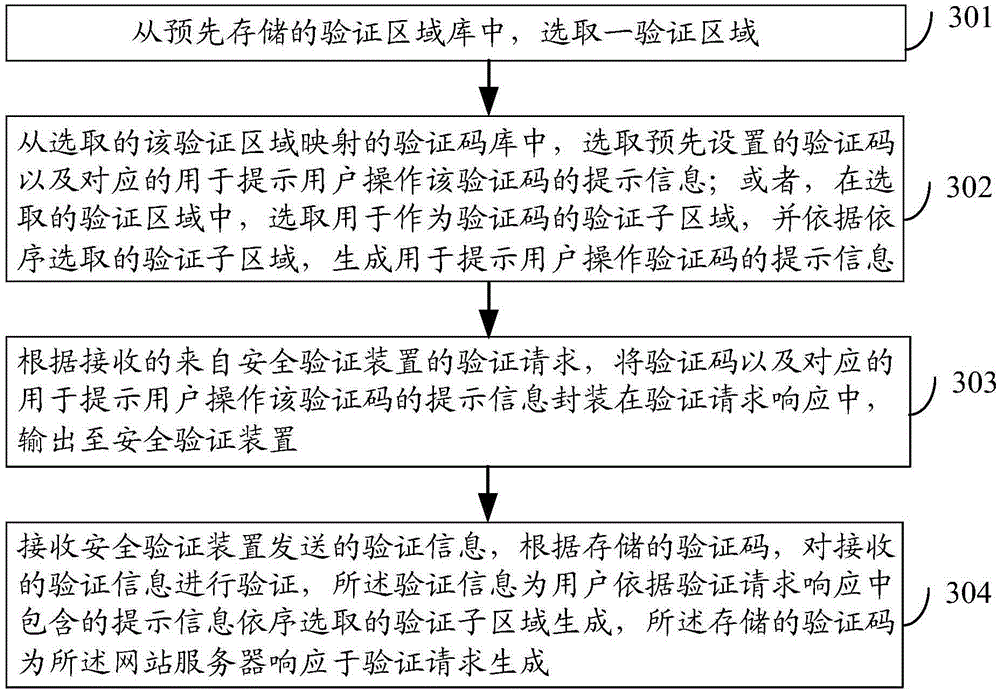
[0141] Embodiment 2, a method for generating a verification code.
[0142] image 3 It is a schematic flowchart of a method for generating a verification code provided by an embodiment of the present invention. see image 3 , the method includes:
[0143] Step 301, selecting a verification area from a pre-stored verification area library;
[0144] In this step, the website server pre-stores a verification area database containing various verification areas, wherein, as an optional embodiment, the website server may select a verification area from the verification area library in a random manner, or may select a verification area according to a preset The selection rule for selecting a verification area from the verification area library.
[0145] Step 302: From the verification code library mapped to the selected verification area, select a pre-set verification code and corresponding prompt information for prompting the user to operate the verification code; or, in the sel...
Embodiment 3
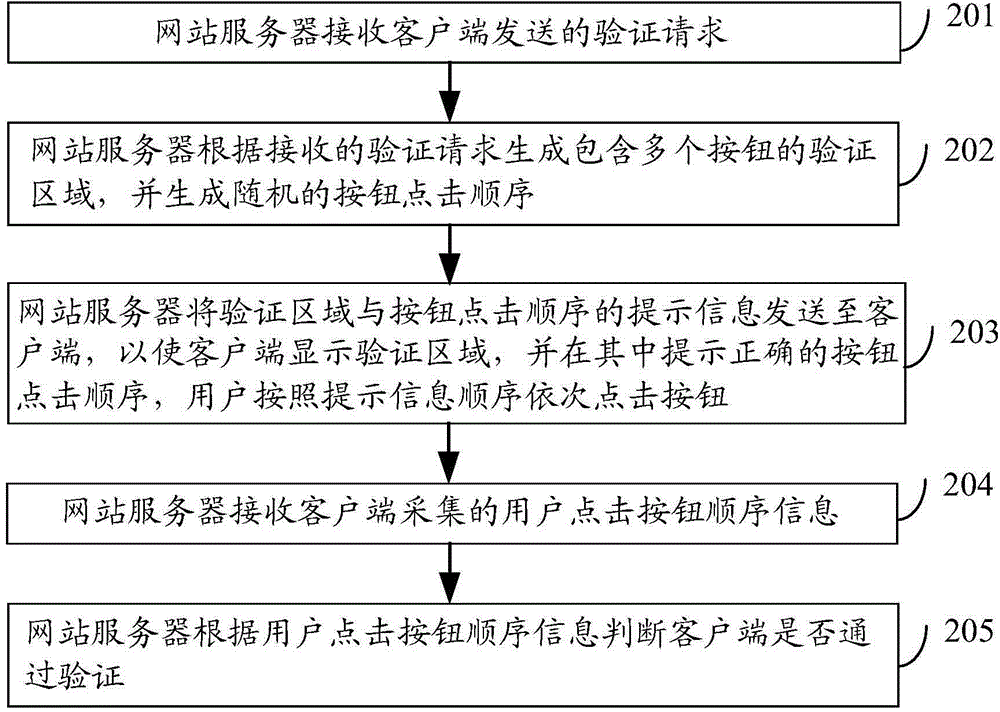
[0175] Embodiment 3, safety verification device.
[0176] Figure 4 It is a structural schematic diagram of the safety verification device provided by the embodiment of the present invention. see Figure 4 , the device includes: a verification request processing module, a verification area display module and a verification information generation module, wherein,
[0177] A verification request processing module, configured to determine that security verification is required, and send a verification request to the website server;
[0178] In the embodiment of the present invention, the verification request response includes: the verification area and the prompt information corresponding to the verification sub-area used for selecting the verification code in the verification area; The prompt information of the verification sub-area as the verification code.
[0179] In the embodiment of the present invention, the verification request response is encrypted using one or more ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com