Software encrypting registration piracy-preventing method
A software encryption, anti-piracy technology, applied in the direction of instruments, program/content distribution protection, electronic digital data processing, etc., can solve the problem of difficult to prevent pirates from obtaining registration codes.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
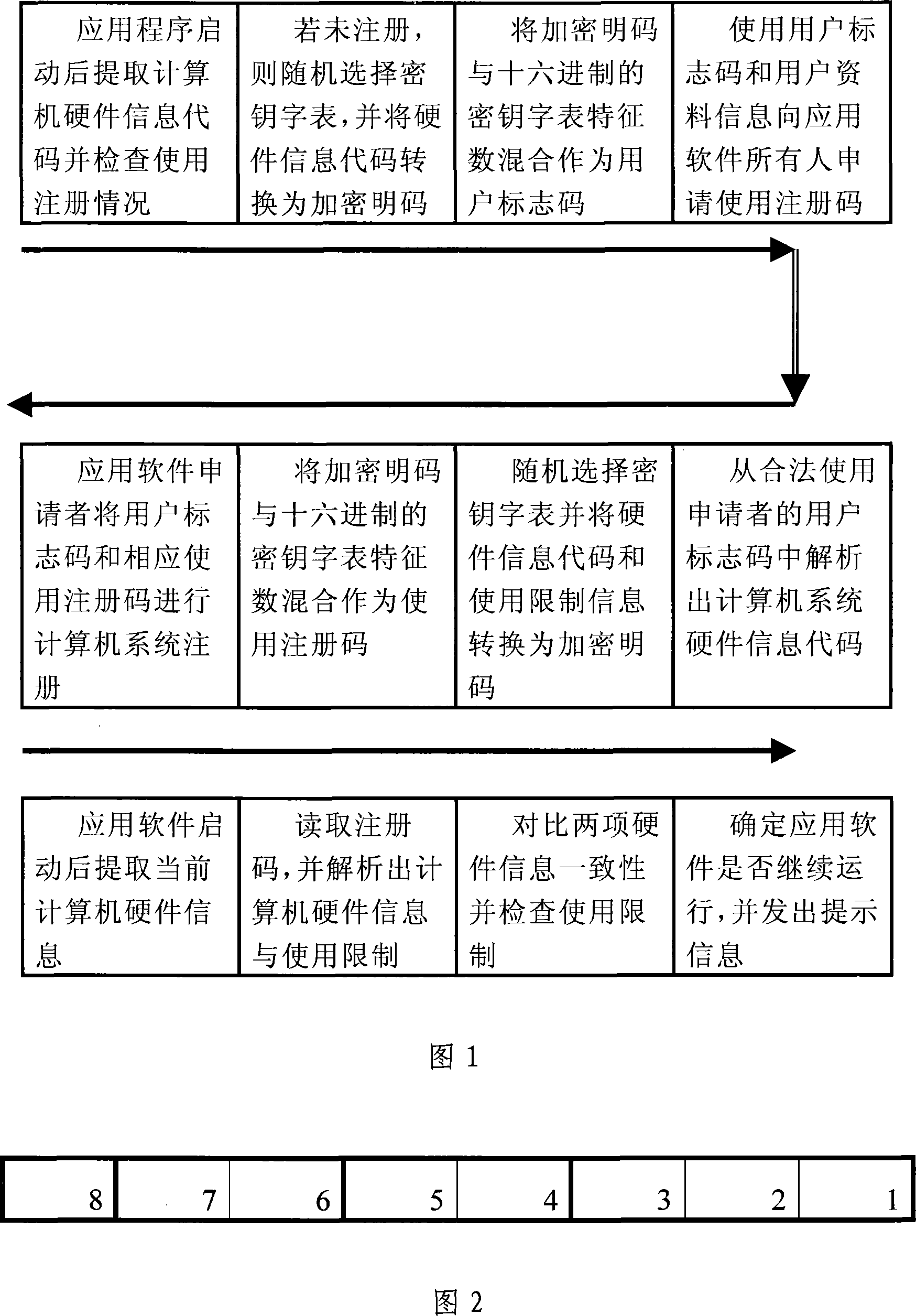
[0051] Taking the implementation process of the anti-piracy method of encrypted registration based on the volume number of the disk partition as an example, as shown in FIG. 1 , this encrypted registration anti-piracy method can also be used for other hardware feature codes. The disk partition volume number of the computer system is a 4-byte random integer, which is generated when the disk partition is formatted, has a very low recurrence rate, and is usually used as a sign of the disk partition. Encrypting the software system through the volume number of the computer system disk partition has become a method to protect software copyright.
[0052] After the application software is started, the registration information of the application software is first read from the registry of the computer system and checked. If the user's computer has not registered the application software or the registration information is wrong, the application software encrypts the user's computer har...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com