Management system and method for user safety authority limit
A technology for security management and user permissions, applied in the direction of preventing unauthorized use of memory, etc., can solve the problems of single access control, poor scalability, and insufficient flexibility, and achieve a security and scalability guarantee. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
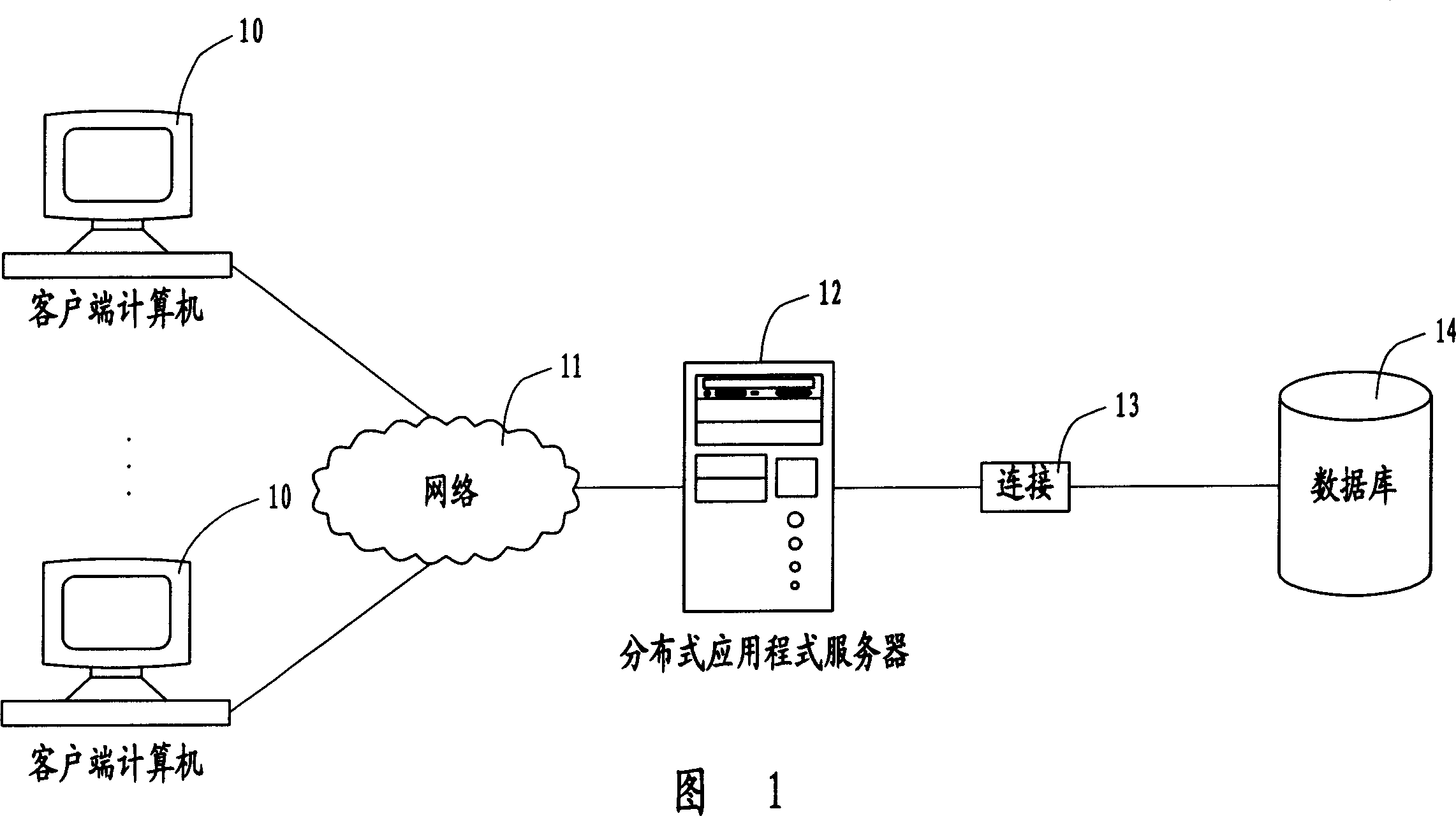
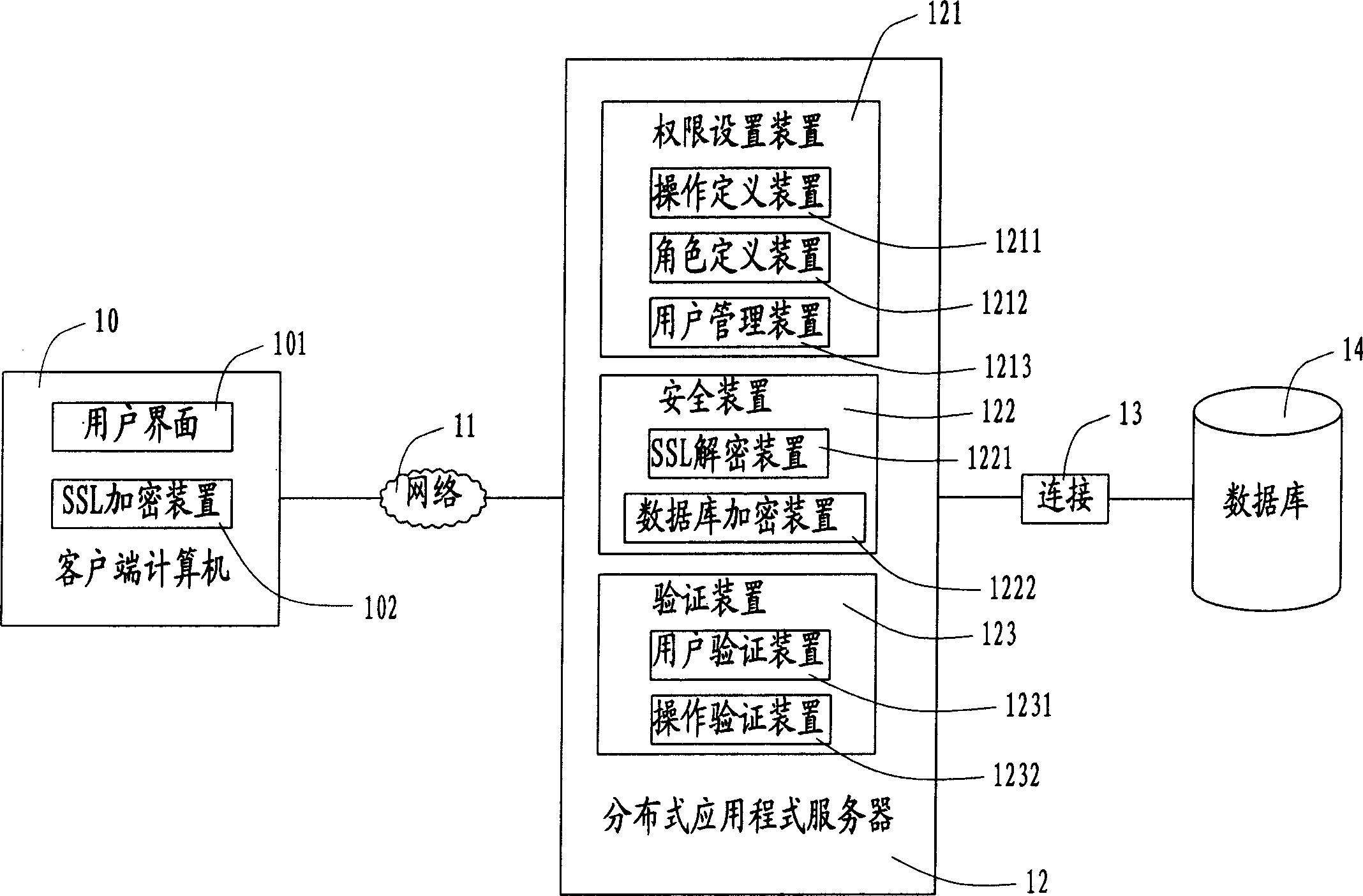
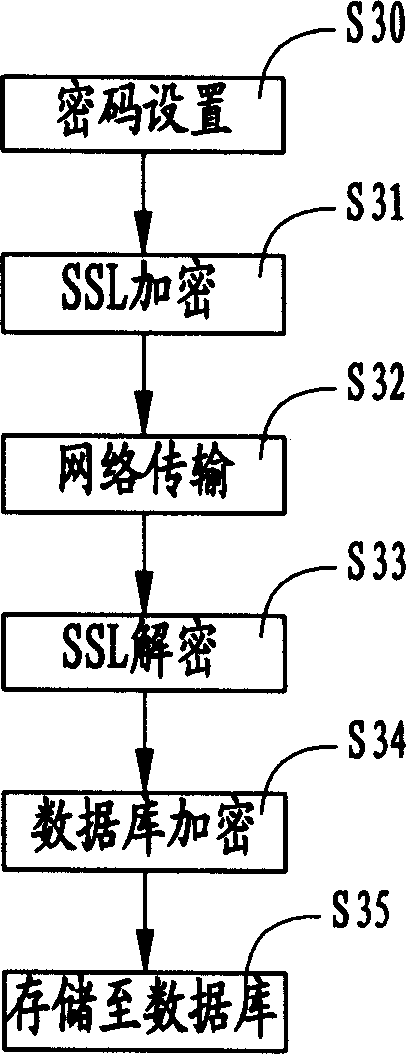
[0017] As shown in FIG. 1 , it is a hardware architecture diagram of the user rights security management system of the present invention. A plurality of client computers 10 are connected via a network 11 to a distributed application server 12 ; the distributed application server 12 is connected to a database 14 via a connection 13 . Wherein, the network 11 is an electronic network, which may be Intranet, Internet or other types of networks. The connection 13 is a database connection, such as an open database connection (Open Database Connectivity, ODBC), or a Java database connection (Java Database Connectivity, JDBC). The client computer 10 provides the user with an interactive user interface, through which the user sets the user ID and password, user authority settings and sends various operation requests. The distributed application program server 12 stores a series of software program devices (as shown in the second figure), which are used for encrypting and decrypting us...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com