Security protection method and system for light-weight database
A security protection and database technology, applied in the field of database protection, can solve problems such as system security risks, not verifying the security status of the database operating platform, ignoring the security constraints of the operating platform, etc., so as to avoid security risks and increase security strength.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
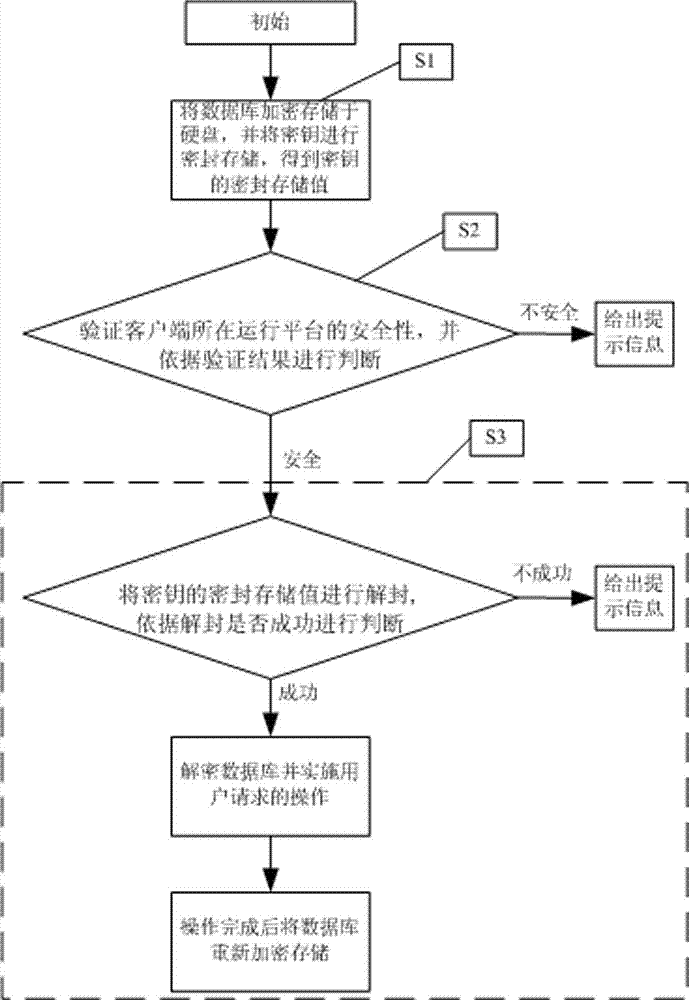
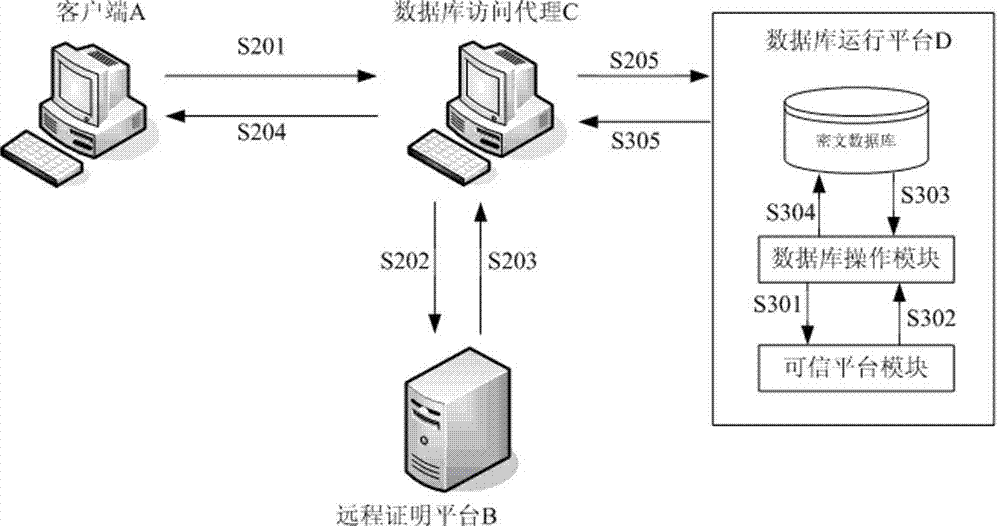
[0032] A database protection function is accomplished jointly by using trusted platform modules. Trusted Platform Module (TPM) is a chip that is planted inside a computer to provide a root of trust for the computer. Chip specifications are developed by the Trusted Computing Group. According to the "TPM Main Specification Level 2 Version 1.2, Revision 116" (referred to as TPM 1.2) specification description issued by TCG, the chip can provide the sealed storage (TPM_Seal), unsealed operation (TPM_Unseal), complete Functions such as performance measurement (TPM_SHA1Complete), key generation (TPM_GetRandom), etc.
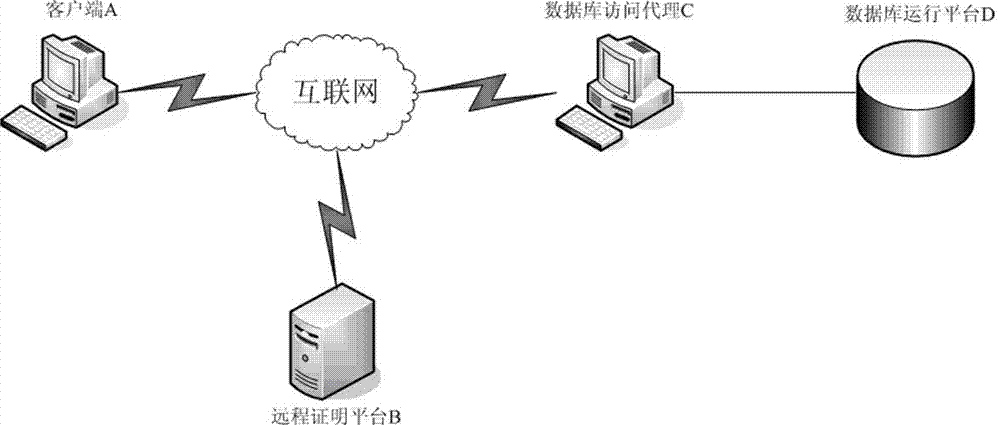
[0033]The database protection method of the present invention includes: (1) the user accesses the database through the database access agent instead of directly operating the database; (2) before responding to the user's operation request on the database, the database access agent first authenticates the client through the remote certification platform If the verifica...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com