Ciphertext indexing method for database encryption and in-base encryption system
An encryption system and database technology, applied in the fields of digital data protection, electrical digital data processing, special data processing applications, etc. sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
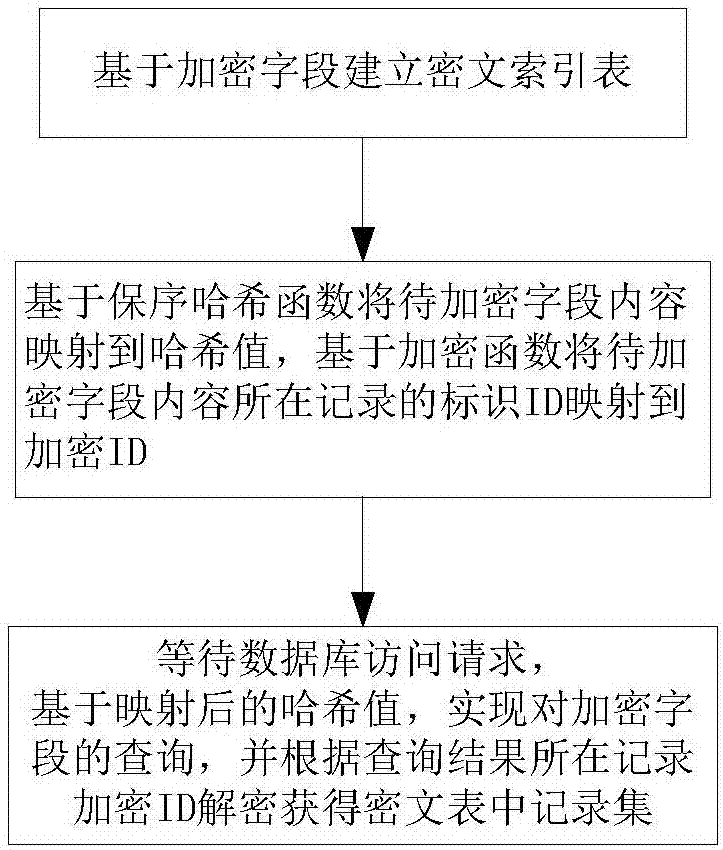
[0048] Such as figure 1 As shown, this embodiment elaborates the implementation of a database encryption-oriented ciphertext indexing method in the ORACLE database of the present invention.
[0049] Table 1 shows the original data table T1 before encryption in this embodiment. It includes two fields C1 and C2. The field ROWID is a pseudo-column provided by the ORACLE system, and its value indicates the physical location of each record, and is also the unique identifier of the encrypted record. C1 is a character field, which is a non-sensitive field and does not need to be encrypted. C2 is a numeric field and is a field to be encrypted.
[0050] Table 1: T1
[0051] ROWID C1 C2 1 Apple 1 2 Bee 2 3 Cat 3 4 dog 4
[0052] First, a ciphertext index table IND_T1 is established based on the encrypted field C2. The IND_T1 table includes the ciphertext index field INDEX_C2 and the field EROWID that has a one-to-one correspondence with e...
Embodiment 2
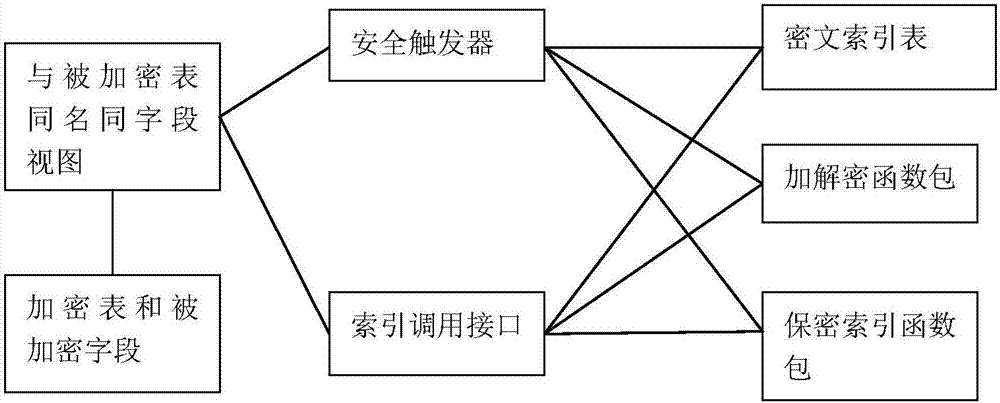
[0059] This embodiment elaborates in detail a specific example of the implementation of a transparent encryption system in a database of the present invention under an ORACLE database.
[0060] Such as figure 2 As shown, for Table 1 in Embodiment 1, a transparent encryption system in a database generates an encrypted table ET1 based on the encrypted original table, including a ciphertext index table IND_T1, a view T1 with the same name as the encrypted original table, and a security trigger , index call interface, confidential index function package, and encryption and decryption function package; among them, T1 is connected with ET1, index call interface and security trigger respectively; security trigger is respectively connected with ciphertext index table IND_T1, confidential index function package, encryption and decryption function The package is connected; the index call interface is connected with the confidential index function package, the ciphertext index table, an...
Embodiment 3
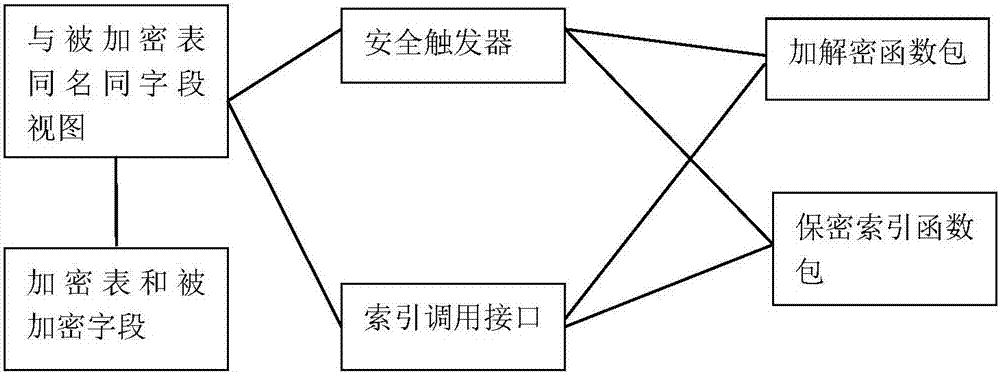
[0093] This embodiment explains in detail another specific example of the implementation of the database encryption field-oriented transparent encryption system in the database under the ORACLE database. Different from Embodiment 2, this embodiment does not use a separate ciphertext index table, which can achieve higher efficiency than Embodiment 2, but partially leaks the partial order relationship between records.
[0094] The specific method is: if image 3 As shown, for the table T1 in the above-mentioned embodiment 1, there is no need to establish the ciphertext index table IND_T1, directly rename T1 to the encrypted table ET1, and rename the field C2 to EC2, and EC2 saves the encrypted plaintext of the original C2 For ciphertext, add the ciphertext index field INDEX_C2 in ET1, and store the ciphertext index value of the original C2 plaintext in INDEX_C2, as shown in the following table:
[0095] Encrypted table ET1:
[0096] ROWID C1 EC2 INDEX_C2 1 ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com