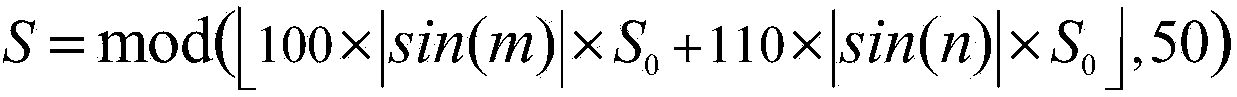Encryption and decryption method for numeric type data
An encryption method and numerical technology, applied in the field of information security, can solve problems such as hidden safety hazards in backup information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment 1
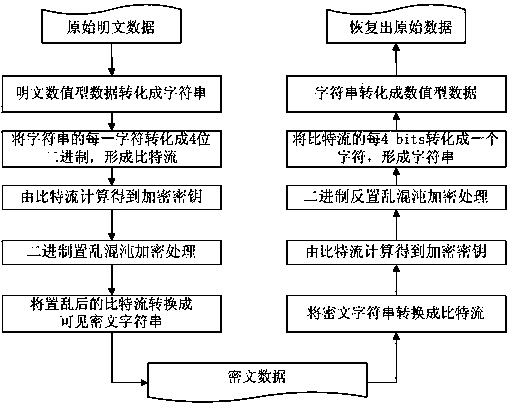
[0062] According to the encryption and decryption steps of the above numerical data, when the initial value Z in the encryption key 10 ,Z 20 , S 0 and the initial value in the decryption key When consistent, take Z 10 = Z ~ 10 = 0.123 , Z 20 = Z ~ 20 = 0.234 , S 0 = S ~ 0 = 80 , Combined with specific numerical data (such as: -3.1415926, 65536, 1.61803399 and 5.1847e+21) for encryption and decryption, the results are shown in Table 4. It can be seen from the following table: the ciphertext string is disorderly, without any trace of the ...
specific Embodiment 2
[0065] According to the above-mentioned encryption steps of numerical data, the encryption key is similar to the specific embodiment 1. When a certain encryption key changes slightly: Z 10 = 0.123000000000001; or Z 20 = 0.234000000000001; or S 0 =81; or slight changes occur in the numerical data to be encrypted, the encryption result of the numerical data is shown in Table 5. It can be seen from the table below: Once the encryption key changes even slightly, that is, "missing by a tiny bit", the ciphertext string will be "by a thousand miles", so it can be seen that a numerical data encryption method proposed in this patent is key-sensitive. The encryption key is not only related to the initial value of the key, but also associated with the original data to be encrypted, which can better resist known / chosen plaintext attacks.
[0066] Table 5 Encryption and decryption results of numerical data when the encryption and decryption keys are inconsistent
[0067]
specific Embodiment 3
[0068] According to the encryption and decryption steps of the above numerical data, the initial values in the encryption and decryption keys and the numerical data to be encrypted are similar to the specific embodiment 1, except that the decryption key changes slightly: or or Or the ciphertext string to be decrypted changes slightly, and the decryption result of the numerical data is shown in Table 6. It can be seen from the following table: once the encryption key and the decryption key are inconsistent, even if there is a slight difference, the recovered numerical data is useless information. It can be seen that a numerical data encryption and decryption method proposed in this patent is safe and doable.
[0069] Table 6 Encryption and decryption results of numerical data when the encryption and decryption keys are inconsistent
[0070]
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com