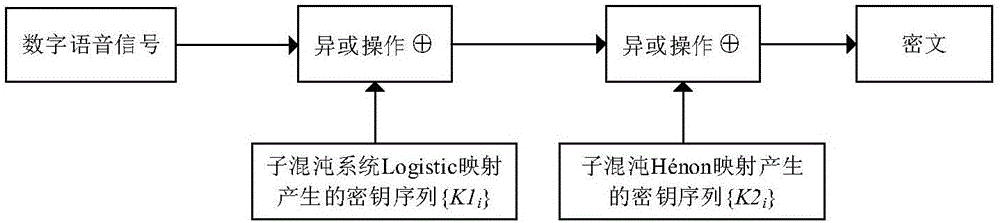
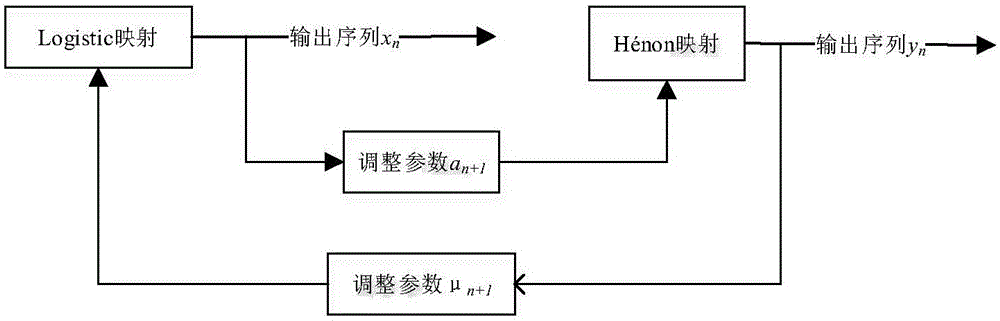
Chaotic encryption method for voice information
A technology of chaotic encryption and voice information, which is used in secure communication through chaotic signals, secure communication devices, digital transmission systems, etc., can solve the problems of short period of chaotic sequences, the impact of chaotic system performance, and limited calculation accuracy, so as to reduce the effective accuracy. effect, enhanced encryption security, less resource required effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] The present invention will be further described below through specific embodiments.
[0028] A chaotic encryption method for voice information, comprising the steps of:
[0029] 1) Construct a dynamic variable parameter compound chaotic system, which is formed by cascading Logistic mapping and Hénon mapping, and use this system to generate a real-valued chaotic sequence with the same length as the plaintext speech sequence. The Logistic map is a classic one-dimensional chaotic map. When the bifurcation parameter 3.57<μ≤4, the system enters a chaotic state. The Hénon map is a two-dimensional discrete chaotic map. When 0.7≤ɑ≤1.4, the system enters a chaotic state. The Logisitc map and the Hénon map of the chaotic system with dynamic variable parameters can be adjusted in cascading order without affecting the performance of generating chaotic sequences.
[0030] Among them, the dynamic changes of μ and ɑ in the present invention are bifurcation parameters of Logistic map...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com