Video-encryption camera and encryption method thereof
An encryption method and camera technology, applied in the field of video information security, can solve problems such as hidden safety hazards, low system integration, and inapplicability to portable occasions, and achieve the effect of improving encryption efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
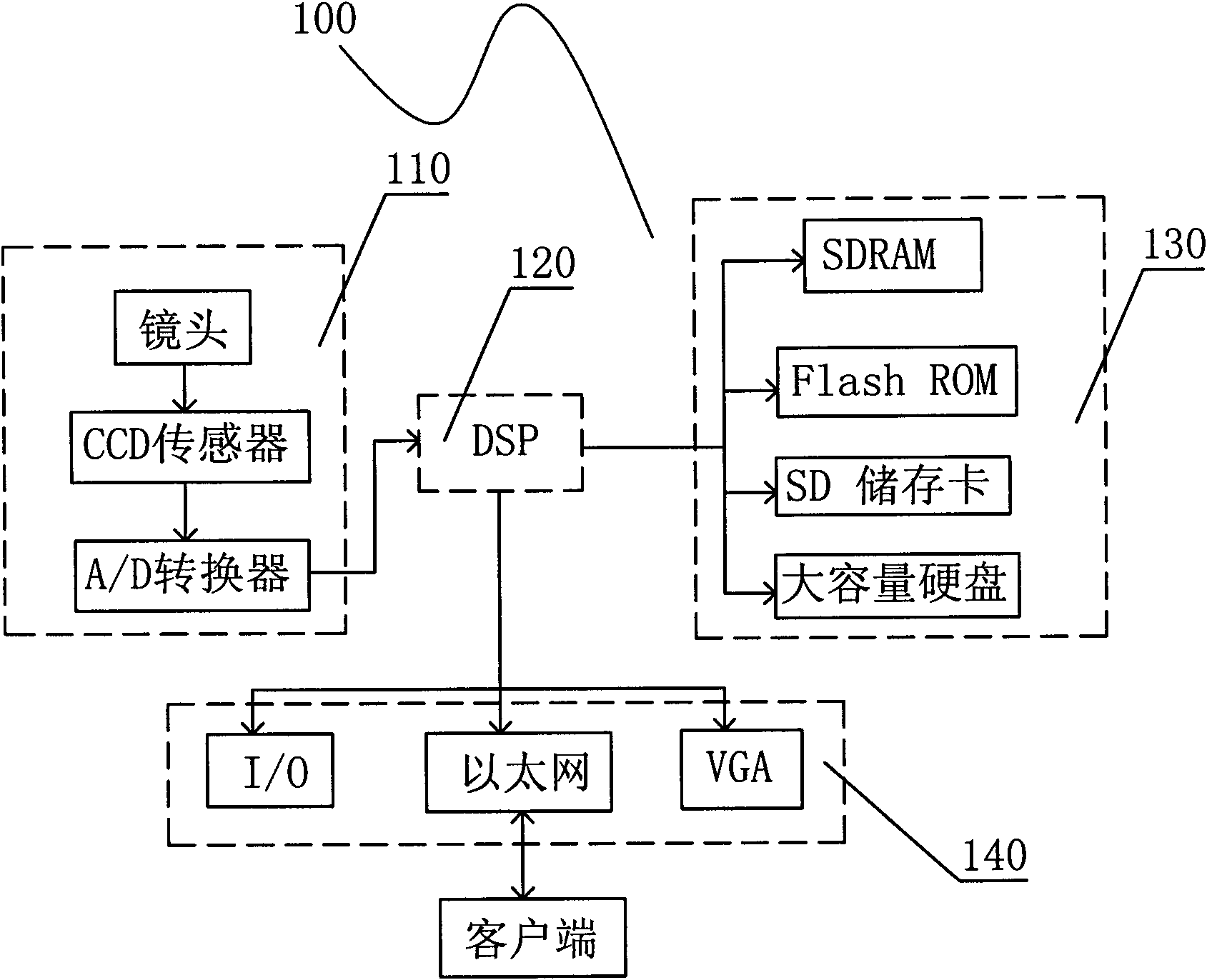
[0019] see figure 1 , which is a structural block diagram of the video encryption camera of the present invention. The video encryption camera 100 includes a video acquisition module 110 , a video preprocessing and encryption module 120 , a video storage module 130 and a video transmission module 140 . The video capture module 110 completes the video capture, and sends the video data to the video preprocessing and encryption module 120 . Because the captured video will be restricted and disturbed by various conditions, such as uneven light, noise pollution generated by line transmission, etc., which will affect the clarity and video quality of the video, so the video preprocessing and encryption module 120 first performs video data processing. preprocess to improve its video quality; then encrypt the video data. The video data encrypted by the video preprocessing and encryption module 120 will be stored in the video storage module 130 in real time. The video transmission mo...
Embodiment 2
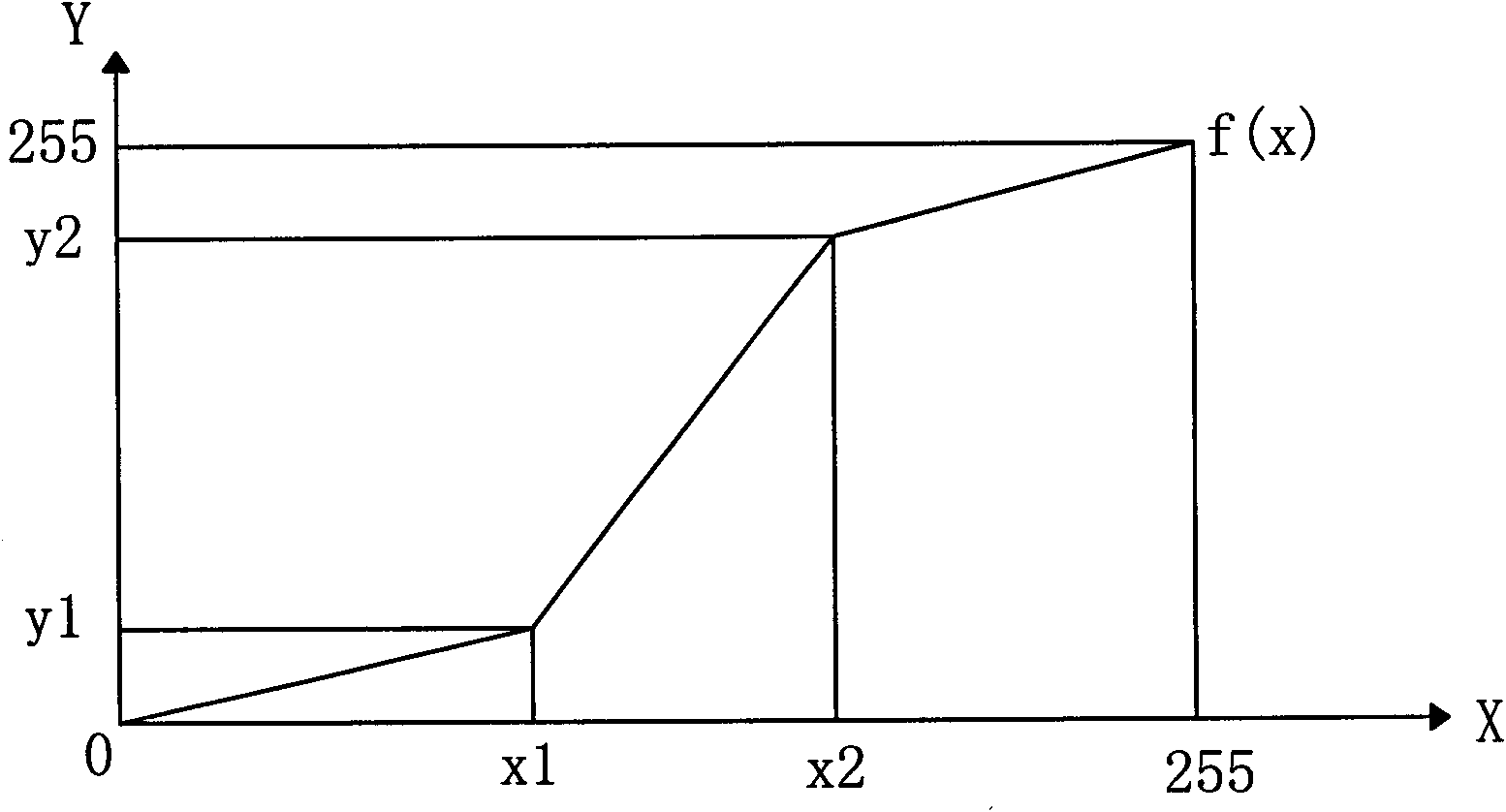
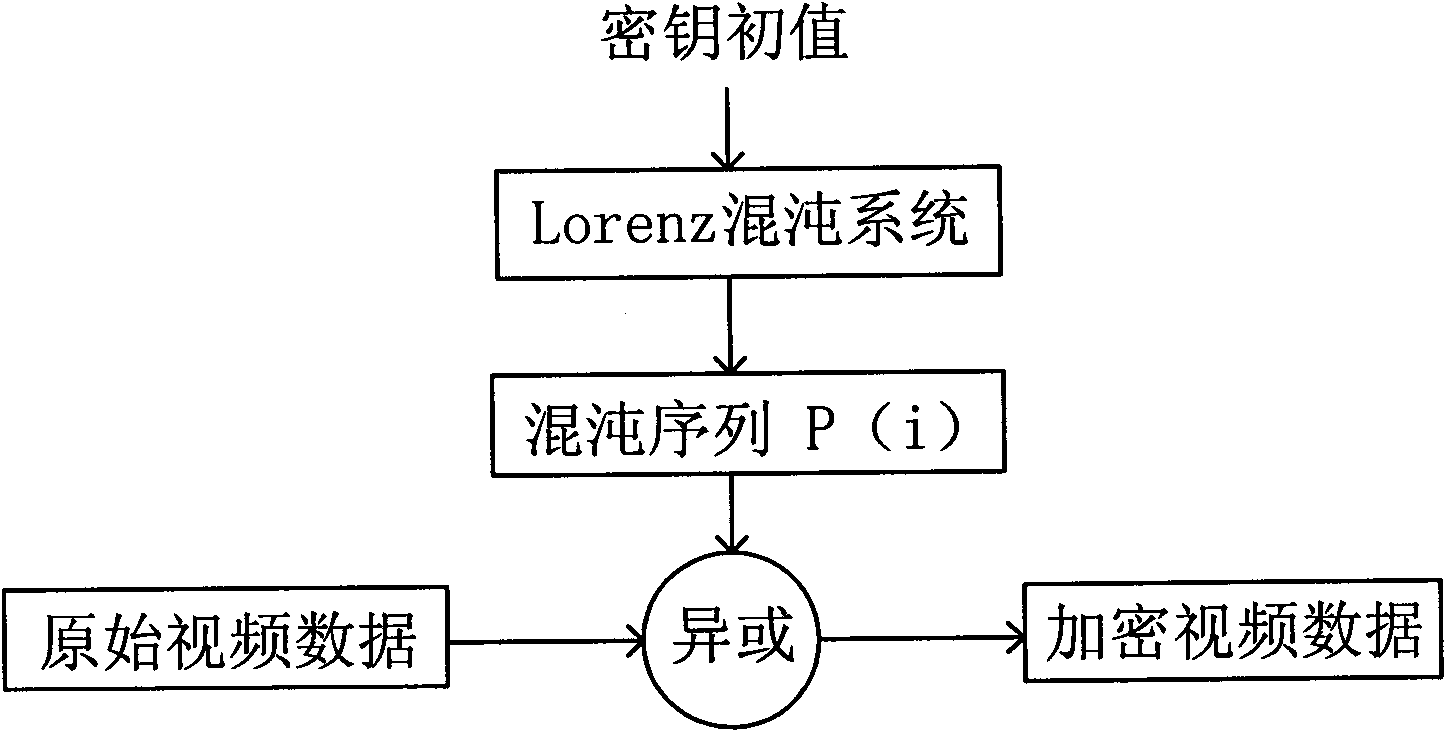
[0045] This embodiment has the same video encryption camera 100 structure as Embodiment 1, the only difference is that after the video preprocessing and encryption module 120 in this embodiment preprocesses the image, it is called and stored in the FLASH ROM according to the operator's instruction Any one of the chaotic encryption systems encrypts the video data with a dynamic key chaotic system. The principle of dynamic key chaotic system encryption is: the video data of each frame is encrypted with a different key, and the key is also scrambled by the chaotic system.
[0046] This embodiment adopts the Lorenz chaotic system dynamic key encryption method. As described in Example 1, the dynamic equation of the Lorenz system is:
[0047] dx / dt = - u ( x - y ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com