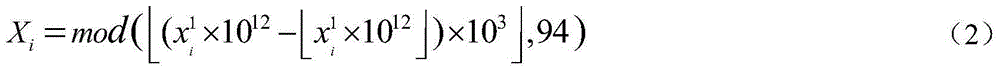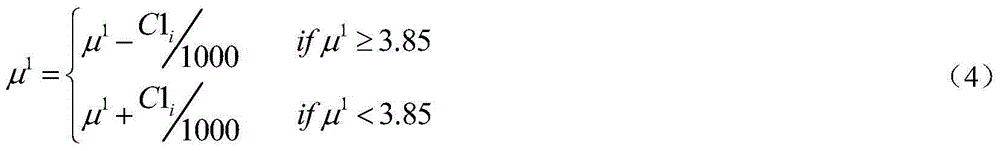Encryption and decryption method of character data
An encryption method and character-based technology, which is applied in the field of information security and can solve the problems of algorithm complexity, security, and easy to be deciphered.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment 1
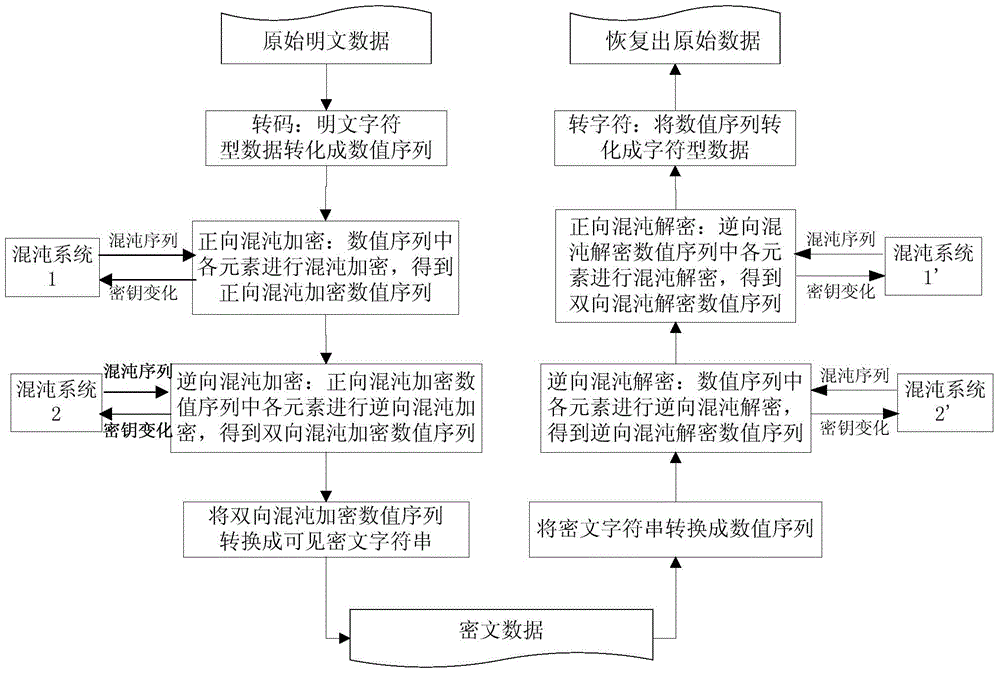
[0099] According to the encryption and decryption steps of the above character data, when x in the encryption key 0 、y 0 , μ 1 , μ 2 with the decryption key When the correspondence is consistent, take x 0 = x ~ 0 = 0.2345 , y 0 = y ~ 0 = 0.54321 , μ 1 = μ ~ 1 = 3.85 , At the same time, let the encryption key in C1 0 ,C2 0 with the decryption key in R1 0 ,R2 0 Equal, if the value is C1 0 =C2 0 =R1 0 =R2 0 =85, in conjunction with specific character data (such as: "0123," "abcd; ", and "impedance.") to encrypt and decrypt, the operation results of ea...
specific Embodiment 2
[0103] According to the encryption steps of the above-mentioned character data, the encryption key is similar to the specific embodiment 1, and only a certain encryption key changes slightly: x 0 = 0.234500000000001; or y 0 = 0.543210000000001; or μ 1 = 3.850000000000001; or μ 2 =3.860000000000001, the encryption result of character data is shown in Table 2. It can be seen from the following table: once the encryption key changes even slightly, that is, "missing by a tiny bit", the ciphertext string will be "distanced by a thousand miles", so it can be seen that a character data encryption method proposed in this patent is key-sensitive. sex.
[0104] Table 2 Encryption results of character data when the encryption key changes slightly
[0105]
specific Embodiment 3
[0106] According to the encryption steps of the above-mentioned character data, the encryption key is similar to the specific embodiment 1, for the character data to be encrypted (such as "aaaaaaaaaaa", "baaaaaaaaaa", "aaaaaaaaaab", "aaaaabaaaaa" and "aaaaaaaaaa" slightly changed ) are encrypted separately, and the encryption results are shown in Table 3. It can be seen from the table below that slight changes in the data to be encrypted (plaintext) will cause the encrypted ciphertext string to be "unrecognizable", so it can be seen that the character data encryption method proposed in this patent is sensitive to encrypted character data. As can be seen from the analysis of the above-mentioned specific embodiment 2 and example 3, the ciphertext produced by a character data encryption method proposed in this patent is not only closely related to the encryption key, but also depends on the character data (plaintext) to be encrypted. A character data encryption method is proposed...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com