Video encryption system
An encryption system and video technology, applied in transmission systems, digital transmission systems, key distribution, and can solve problems such as lack of security guarantees
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0152] Included in this embodiment:
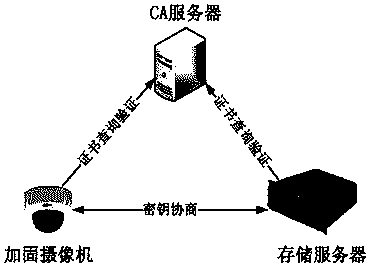
[0153] (1) Key negotiation
[0154] When the storage server and the hardened camera establish a video connection, key negotiation is performed every 24 hours, and the video key encryption key is replaced after the negotiation is successful. The key agreement is based on the public key cryptographic algorithm and is carried out under the support of the CA server.
[0155] (2) Encrypted transmission
[0156] After the key negotiation is successful, the hardened camera uses the locally generated video encryption key to encrypt the video data. The video encryption key VEK is encrypted by the interactive video key encryption key VKEK and then transmitted along with the code stream. The video encryption key VEK is updated every 1 hour. When transmitted in a video surveillance network, video data appears in encrypted form.
[0157] (3) Ciphertext storage
[0158] After the encrypted video data arrives at the storage server, the storage serve...
Embodiment 2
[0165] In this embodiment, an encryption method using the asymmetric cryptographic algorithm, symmetric cryptographic algorithm and hash cryptographic algorithm in the military public common cryptographic algorithm is provided, and the algorithm is implemented by secure cryptographic components or cryptographic products that meet the military public common cryptographic standards. The algorithm includes:
[0166] (1) Asymmetric cryptographic algorithms are used for identity authentication, digital signature, key agreement, etc.;
[0167] (2) Symmetric cryptographic algorithm is used for encryption protection of video data;
[0168] (3) The hash cryptographic algorithm is used to verify the integrity of the signature information.
[0169] In this video encryption method, its key management includes:
[0170] (1) Video key encryption key VKEK: The key length is 16 bytes, which is generated in real time by the platform's public encryption equipment, replaced every 24 hours, and...
Embodiment 3
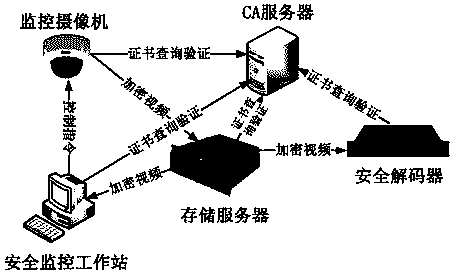
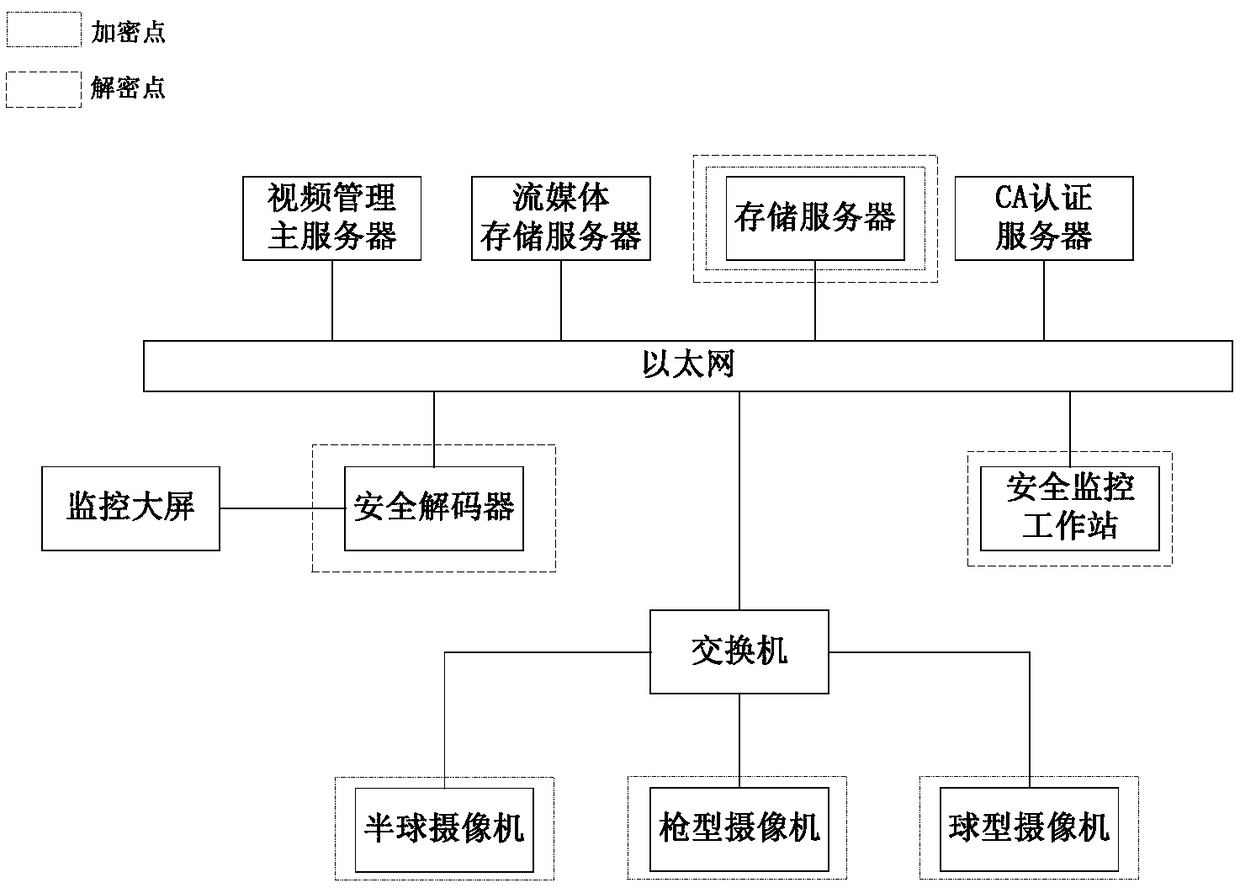
[0176] This embodiment mainly includes two parts: the secure video acquisition and access of the front-end module and the service center management of the back-end module.
[0177] First, use the video acquisition equipment of the front-end module, including high-definition security network cameras, to collect and encrypt the video data, and then transmit it to the back-end module management center through the video private network. Then through the back-end module management equipment such as the main video management server, streaming media server, storage server, security decoder, CA authentication server, and security workstation in the management center, the video data can be safely browsed by the client module, centralized storage, and watched on the TV wall. and other specific applications.
[0178] The key nodes of secure transmission of video data are reflected in:
[0179] (1) Realize the video encryption of the front-end module to protect the important and sensitiv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com