Method and system for protecting radio frequency identification tag and reader data safety
A technology of data security and radio frequency identification, which is applied in the field of RFID, can solve the problem of stopping label reuse, and achieve the effect of avoiding illegal theft and protecting data security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
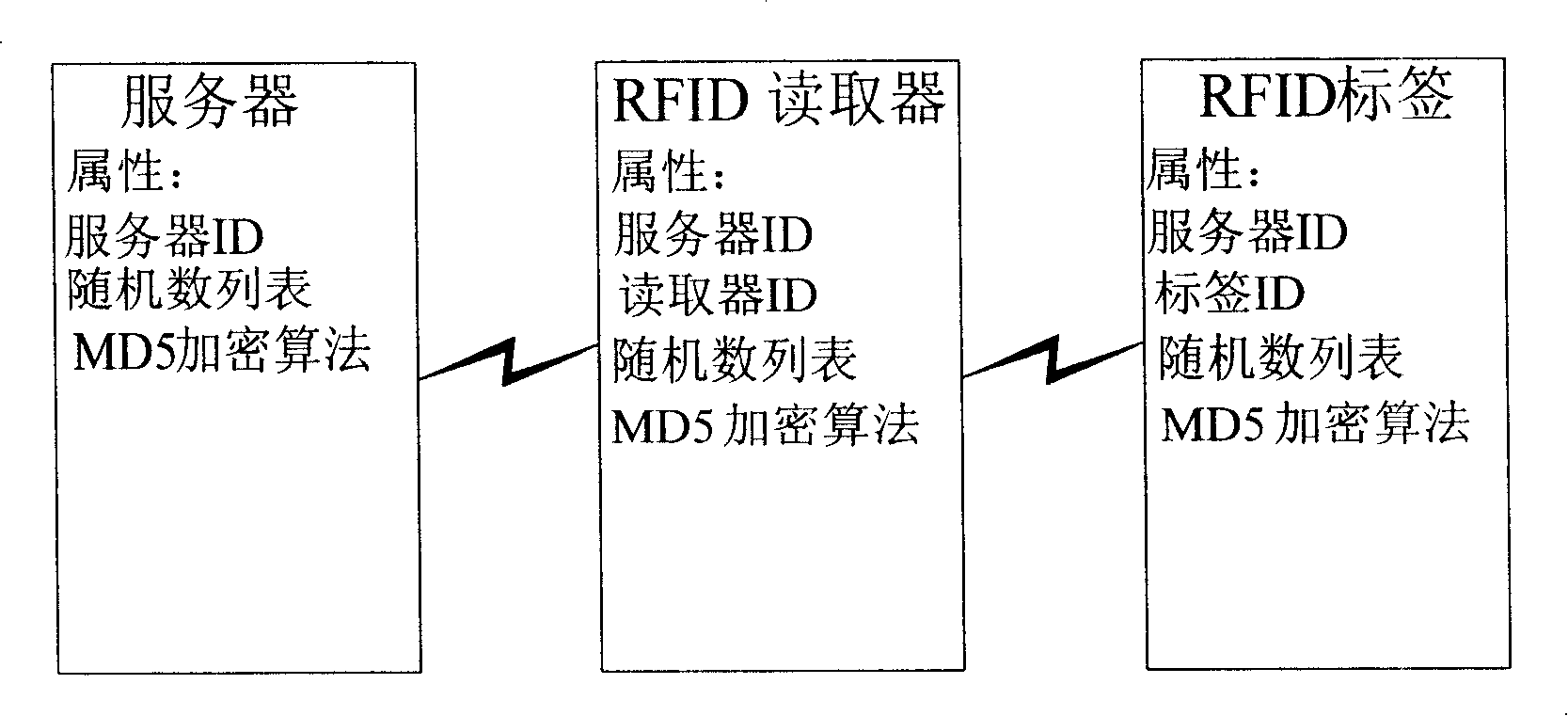
[0019] figure 1 The network entities and their attributes involved in the overall structure of an RFID application system according to an embodiment of the present invention are shown. Specifically, the RFID application system includes three network entities: server, RFID reader and RFID tag.
[0020] The server is a system service management server, and its role is to respond to requests from the RFID tags and their readers or issue commands to the RFID tags and their readers. The server can exchange data with RFID readers via wired or wireless means. The server stores its own network identification "server ID" and a list of random numbers shared with the RFID tag and its reader, and has a logic circuit capable of implementing a secure encryption algorithm (eg, MD5 encryption algorithm).
[0021] The function of the RFID reader is to respond to the command of the server or to read the information of the RFID tag. The RFID reader can exchange data with the server by wire or...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com