Method and system for preventing set top box software from malicious upgrade
A set-top box and anti-malicious technology, applied in the field of communication, can solve the problems of increasing the possibility of data transmission being intercepted, upgrading and destroying the software of the set-top box, and failing to complete the upgrade, so as to reduce the possibility of data leakage, protect interests, and improve data security. sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
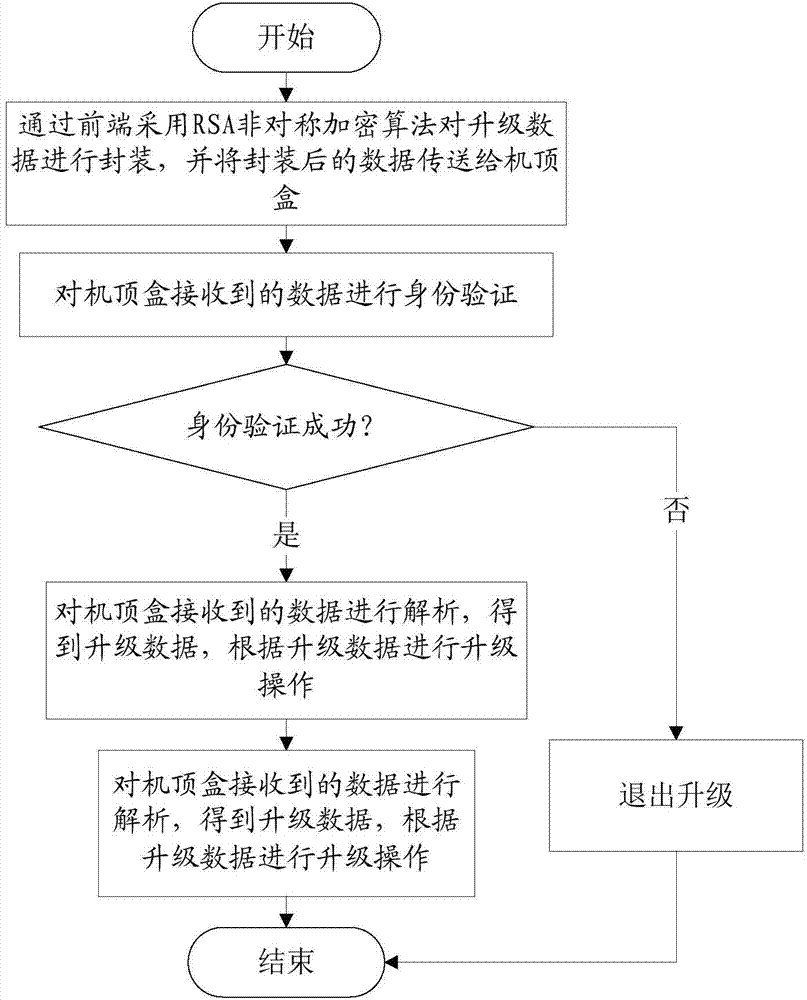
[0028] see figure 1 , a method for anti-malicious upgrade of set-top box software, comprising the steps of:
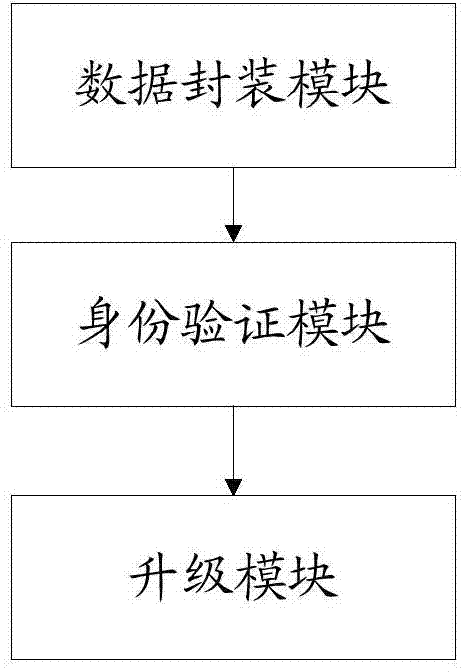
[0029] Step 10, adopting the RSA asymmetric encryption algorithm to encapsulate the upgrade data through the front end, and transmit the encapsulated data to the set-top box; this step 10 further includes:
[0030] Step 11, generate a pair of RSA secret keys through the RSA secret key generation tool, including the RSA public key and the RSA private key, and solidify the RSA public key in the upgrade module inside the set-top box or store it in the flash memory of the set-top box;
[0031] Step 12, perform a hash operation on the upgrade data by the RSA private key, generate a fixed-length first hash data, and insert the first hash data into the head of the upgrade data to obtain encapsulated data, and send it to the set-top box;
[0032] Step 20, perform a hash operation on the upgrade data in the received data through the RSA public key in the set-top box to generat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com