Embedded web server anti-replay attack method
A WEB server, embedded technology, applied in the field of information, can solve the problems of users' personal privacy, property security threats, security risks, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
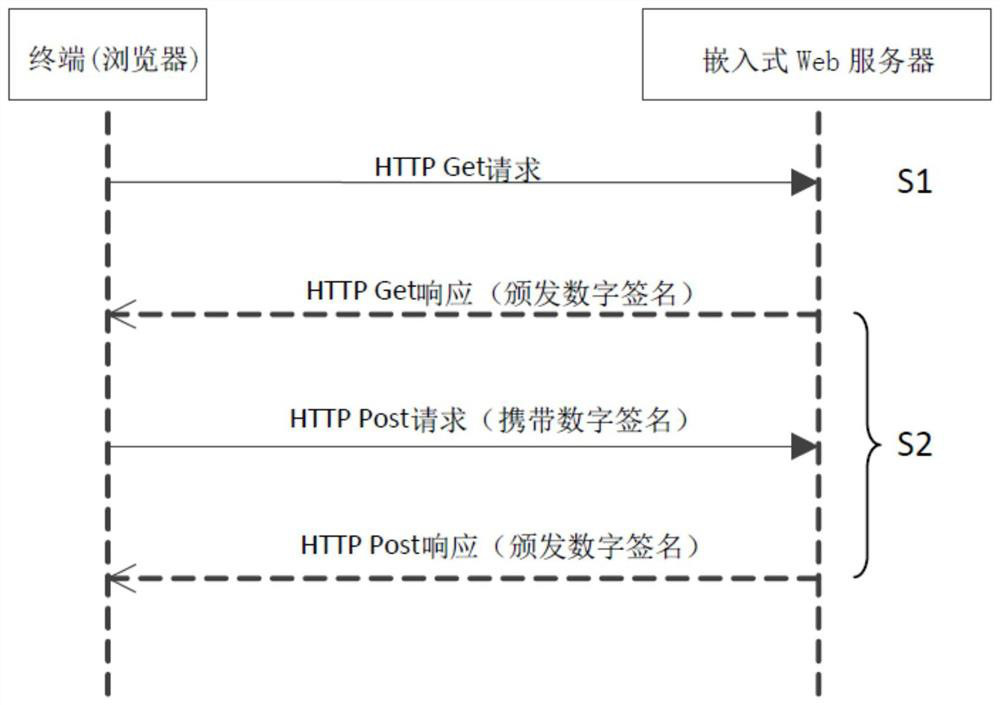
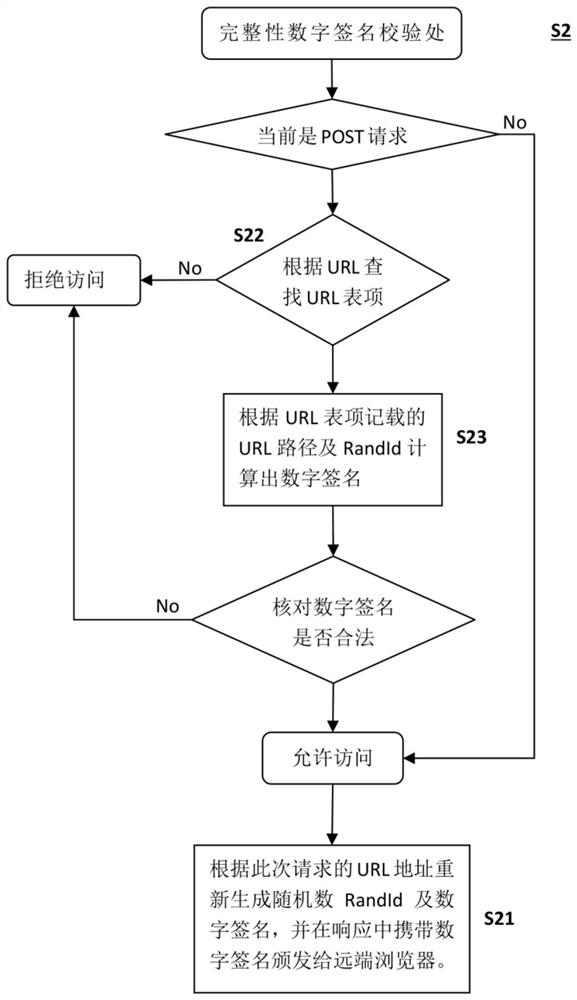
[0025] refer to Figure 1 to Figure 3 As shown, the present invention provides a kind of embedded WEB server anti-replay attack method, comprises the following steps:
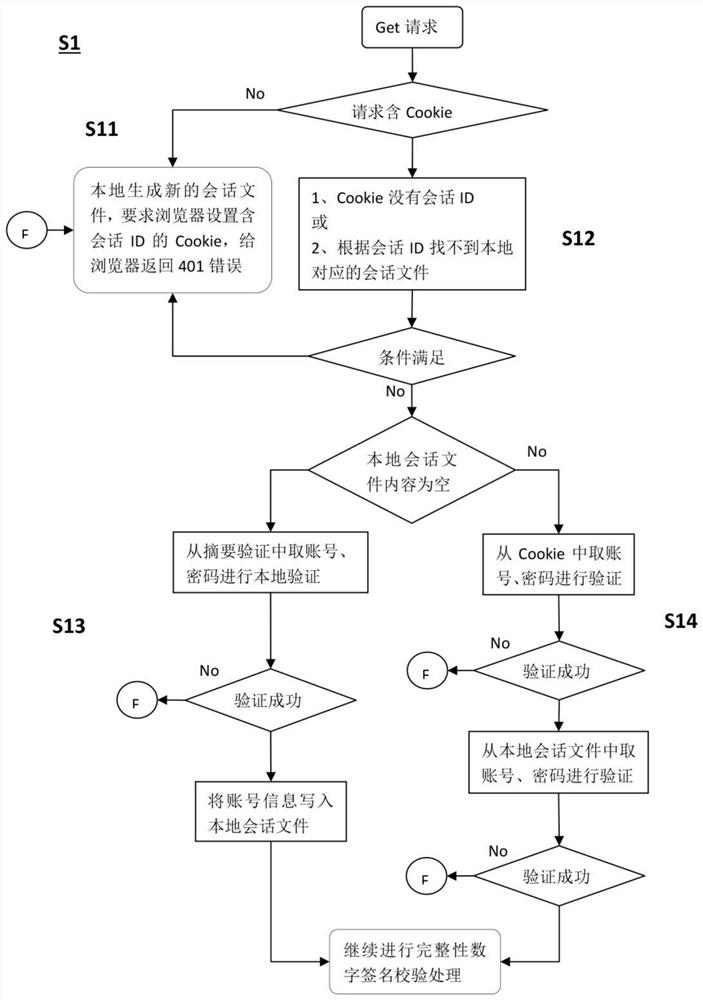
[0026] S1. The terminal sends a Get request to the embedded Web server; the Get request is verified for identity validity, and after the verification is successful, the next step is entered.
[0027] Wherein, the Get request to perform identity verification includes the following steps:
[0028] S11. Detect whether the Get request contains Cookie information, if yes, enter the next step; if no, generate a session ID with a random value, generate a session file with the session ID as the name locally, and return it to the user's browser 401 error, and include the cookie information of the session ID in the 401 error response, requiring the terminal to carry the cookie informati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com