File Access and Modification Authority Control Method Based on Data Sharing
A file access and permission modification technology, applied in the field of information security, can solve the problems of stealing users' private data alone, large computational complexity, and untrustworthy storage servers, reducing transmission bandwidth and storage space, and reducing computational complexity. the effect of improving access efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The present invention will be described in further detail below in conjunction with the accompanying drawings.
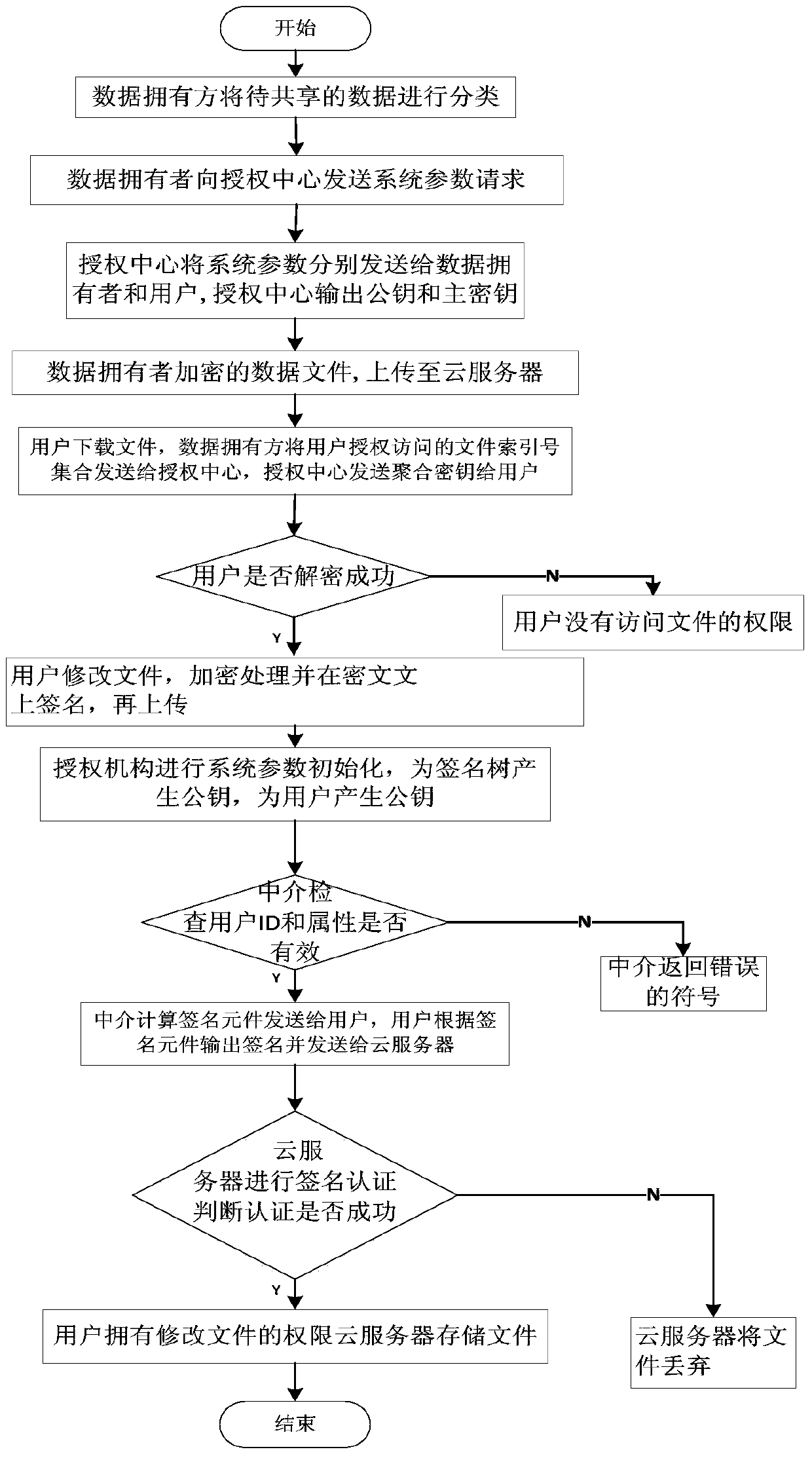
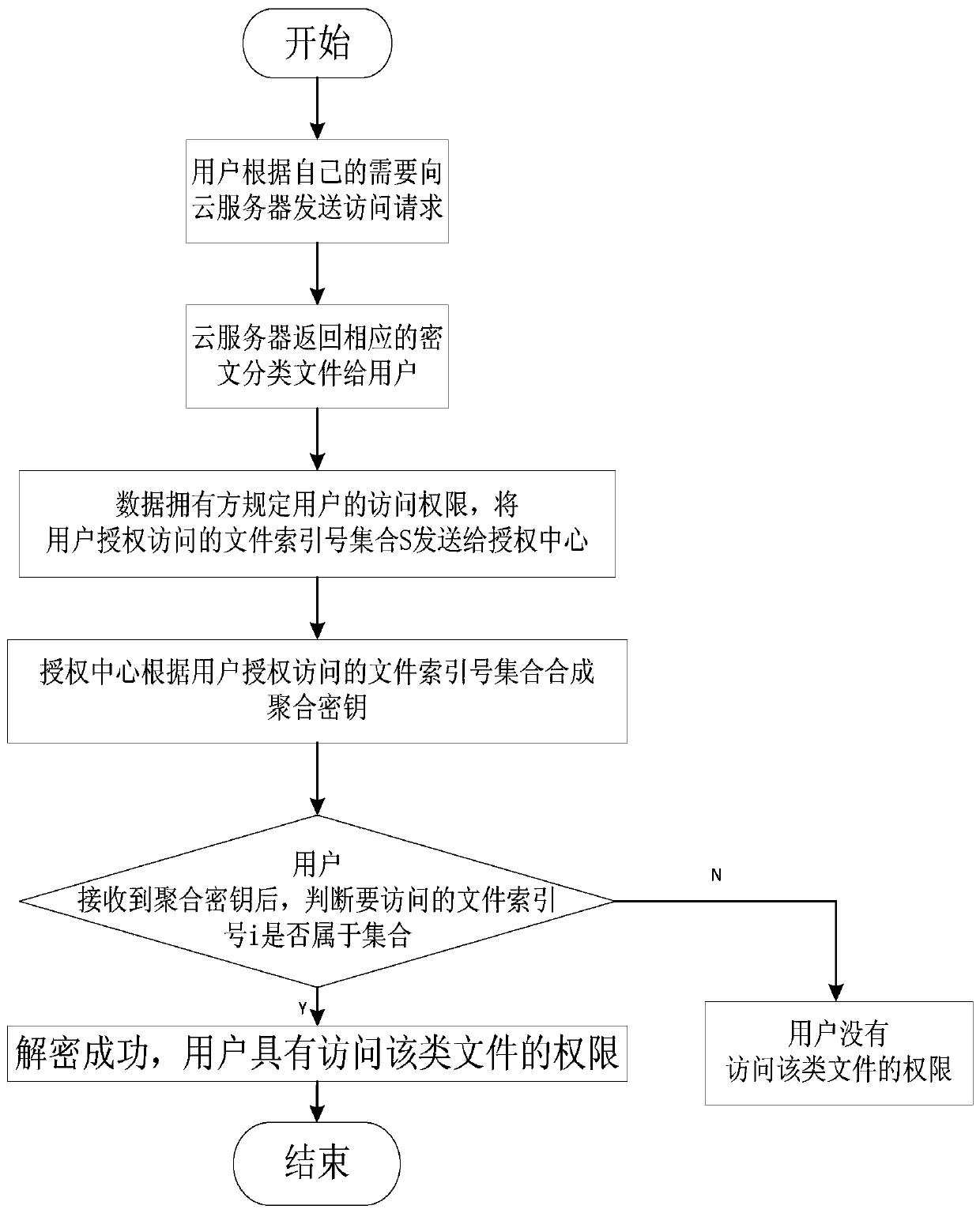
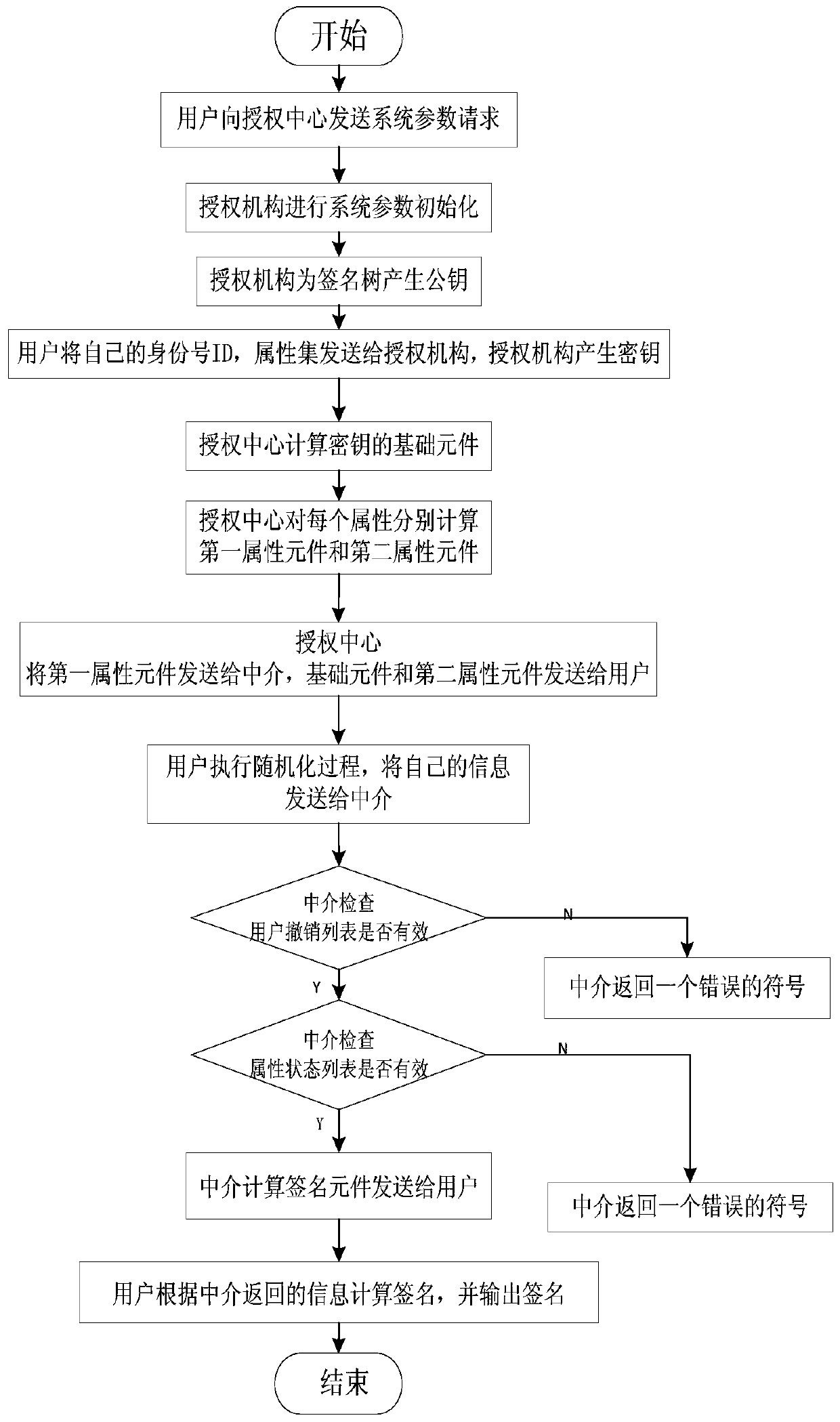
[0027] refer to figure 1 , the implementation steps of the present invention are as follows:
[0028] Step 1: The data owner classifies the data to be shared.
[0029] 1.1) The data owner classifies data files according to attributes, that is, classifies files with the same data attributes into one category, and affixes an attribute label to each classified file;
[0030] 1.2) Mark an index number for each classification file, denoted as i, i∈{1,2,...n}, n is the largest classification file number.
[0031] Step 2: The data owner encrypts the classified files respectively.
[0032] 2.1) The data owner sends a system parameter Q request to the authorization center;
[0033] 2.2) The authorization center randomly selects the p-order bilinear group G, the generator g∈G, and selects the first random number α∈Z p , where Z p Represents the set {1,2,...p}, an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com