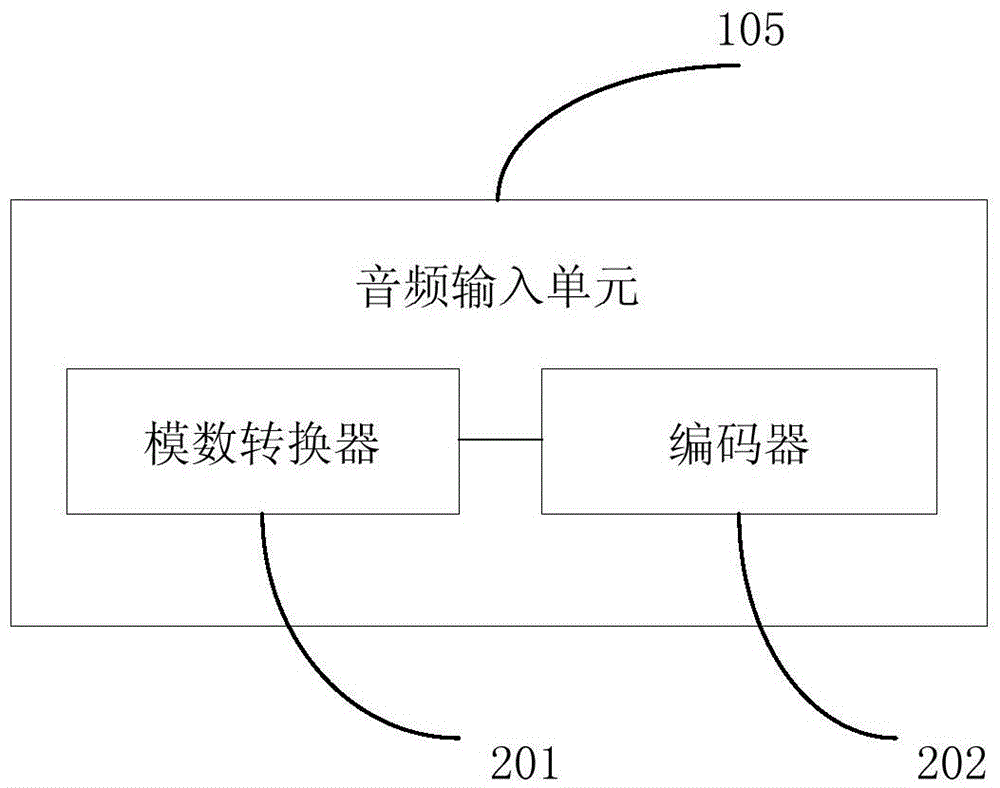
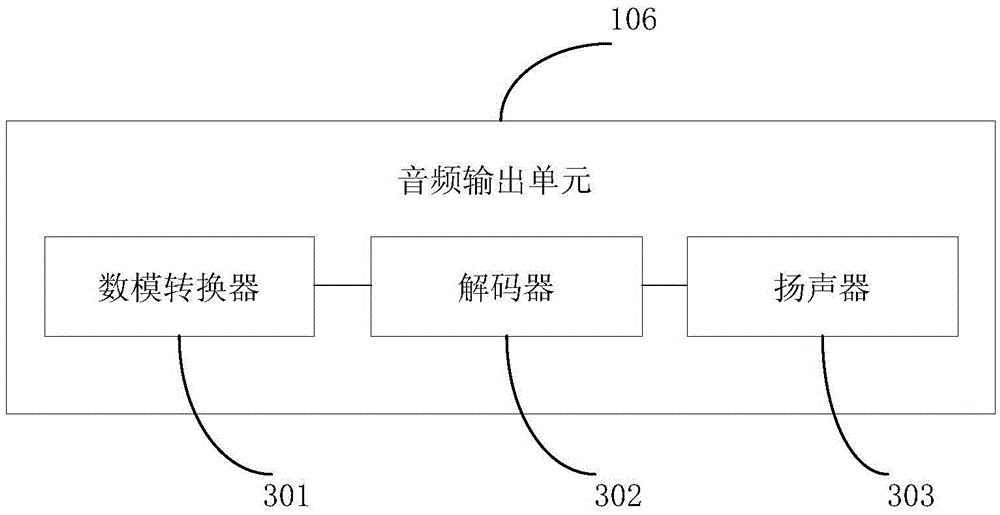
Patents
Literature
79results about How to "Implement authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
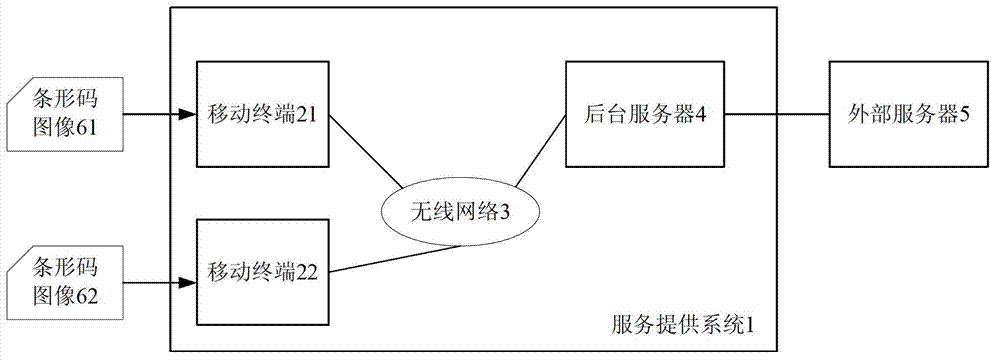
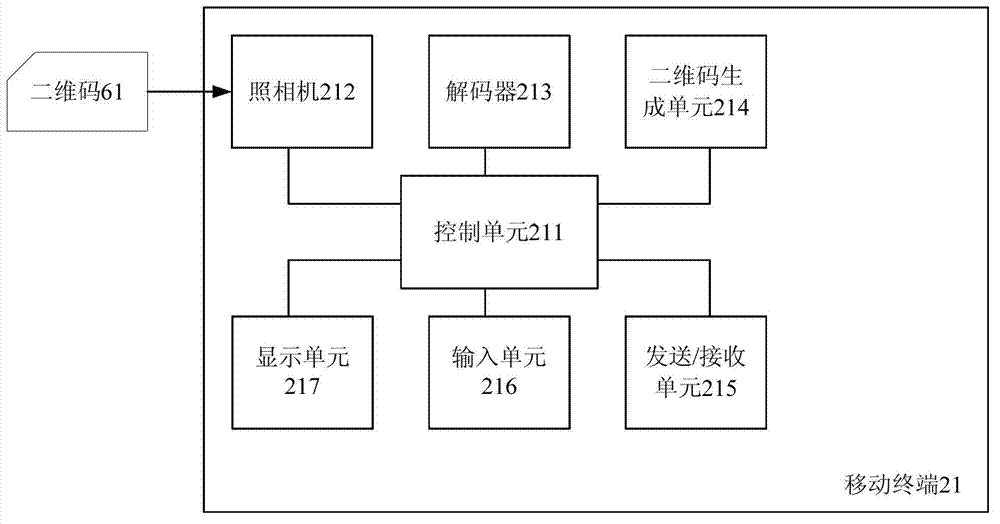
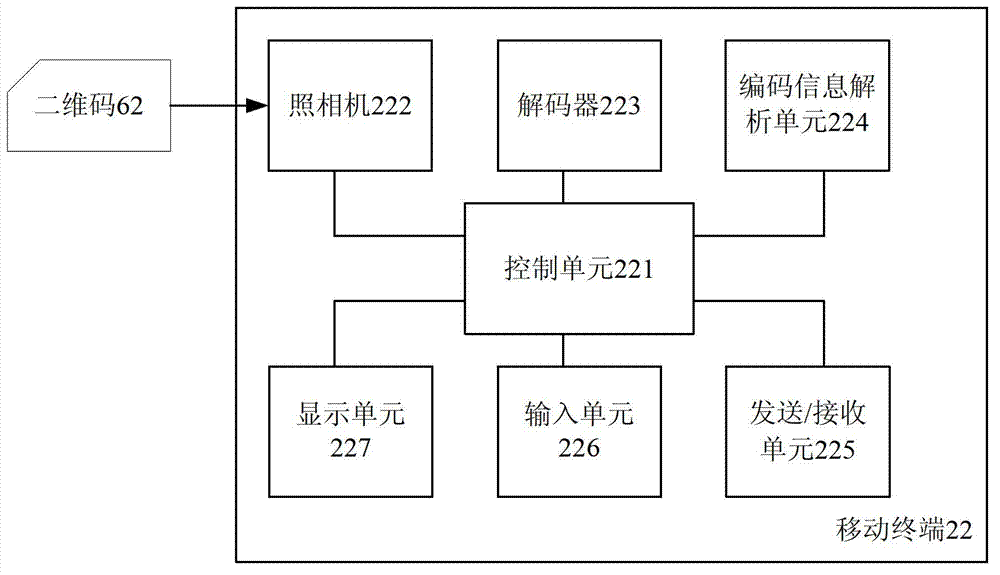
Method and device for adopting bar code images for communication
ActiveCN102821157AEasy to buyImprove recommendationsAcutation objectsDigital data authenticationBarcodeComputer terminal
The invention discloses a method and a device for communication between a mobile terminal and a background server. The method provided by the invention comprises the following steps that a first bar code image is generated and is issued onto at least one region capable of being touched by a user of a mobile terminal, the first bar code image at least comprises service information, and the unique relevance relationship between the first bar code image and the mobile terminal is built; the first bar code image is subjected to photo taking through a camera arranged in the mobile terminal, and the mobile terminal decodes the first bar code image; and the background server generates a second bar code image and sends the second bar code image to the mobile terminal, and the second bar code image at least comprises the service information. The method and the device disclosed by the invention can realize the identity verification of the user, so the safety of user information is ensured.
Owner:成都元码链科技有限公司
Data interaction method and data interaction device based on CHAP protocol
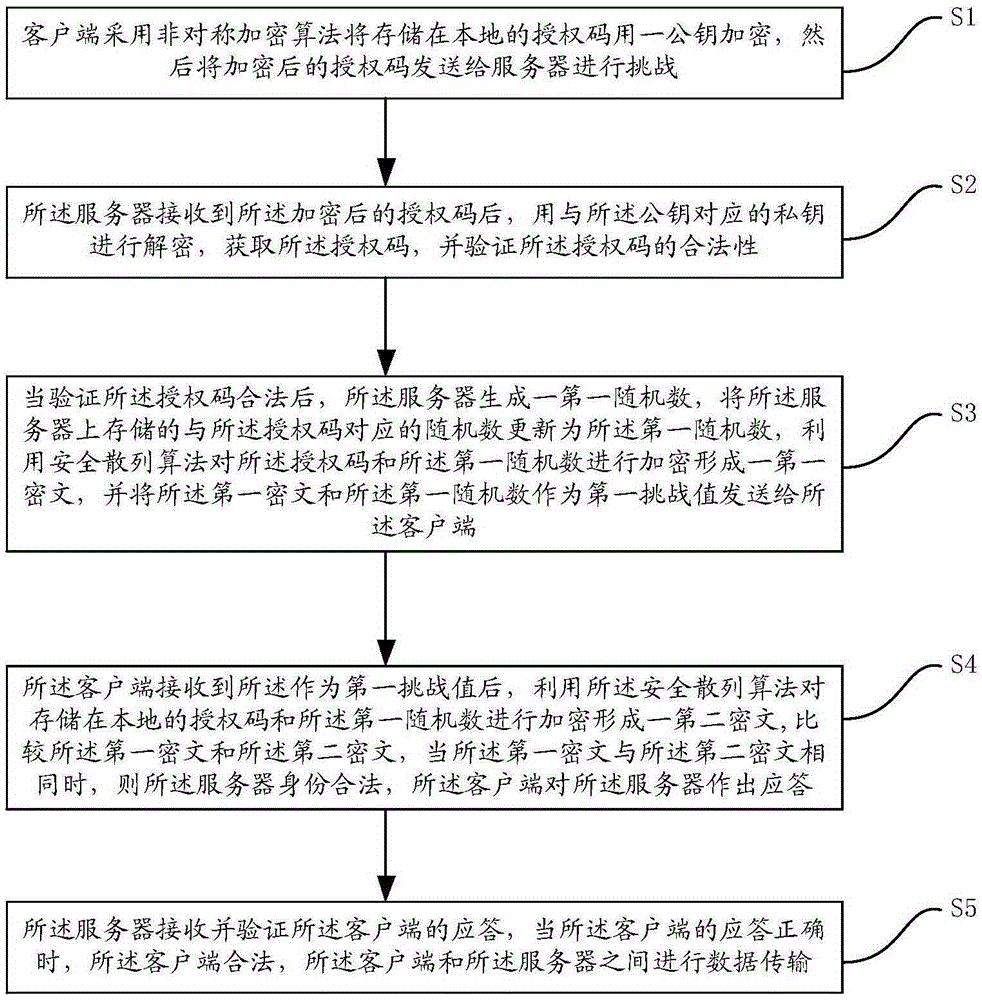
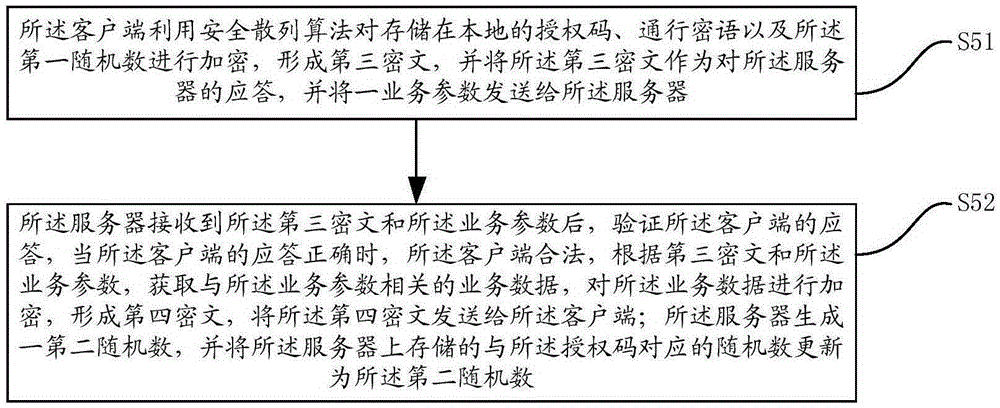
ActiveCN105282168AAchieve legitimacyImplement authenticationUser identity/authority verificationInteraction deviceClient-side
The invention provides a data interaction method and a data interaction device based on the CHAP protocol. The data interaction device based on the CHAP protocol comprises a client and a server. The client and the server carry out data interaction after identity authentication succeeds. The legitimacy of the client and the server is verified using a first random number, an asymmetric encryption algorithm and a secure hash algorithm, and therefore, identity authentication between the client and the server is realized, and attack from the middleman is avoided. Data transmission is carried out between the client and the server after identity authentication succeeds, so that the safety and reliability of data transmission between the client and the server are ensured, and replay attack is avoided.
Owner:SHENGQU INFORMATION TECH SHANGHAI
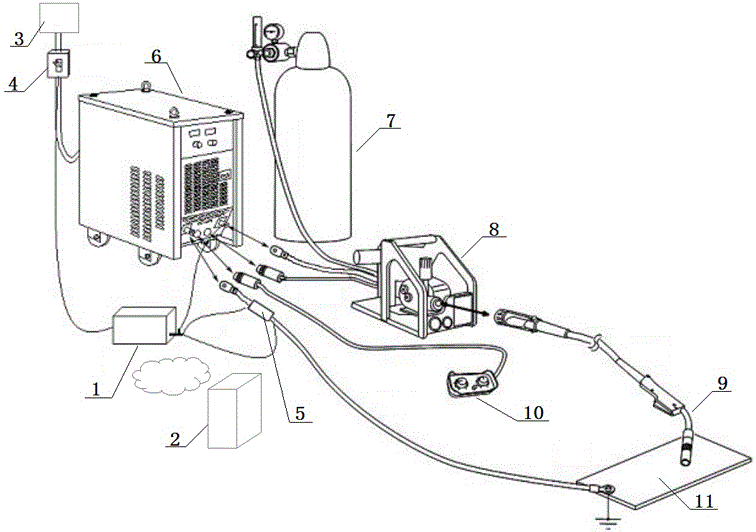
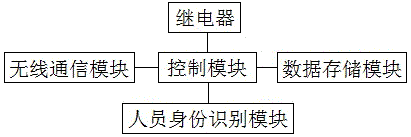
Industrial welder intelligent monitoring system and monitoring method
InactiveCN106141516AImplement authenticationEasy to trackWelding/cutting auxillary devicesDigital data authenticationAutomatic controlMonitoring system
The invention relates to an industrial welder intelligent monitoring system; a traditional welder monitoring structure is improved; a staff identity identifying structure is introduced; and on the basis, the invention further relates to a monitoring method of the industrial welder intelligent monitoring system. An internal structure design of a measuring control box (1) introduces a staff identity identifying module to obtain identity information of staff; the identity information of the staff is sent to an upper server (2) for comparing with prestored staff identity information to realize the staff identity verification; according to the verification result, the power supply for a welder is automatically controlled, so that persons without specific welding qualification can be effectively prevented from performing specific welder operations; and based on the staff identity verification, the association between the obtained welder work monitoring data and the staff can be realized, so that the quality event tracking is convenient, and more effective technical support is provided for the welding quality guarantee.
Owner:JIANGSU MODERN SHIPBUILDING TECH
Method for carrying out cloud protection certification, server and client
ActiveCN107579991AImplement authenticationKey distribution for secure communicationInternet privacyClient-side
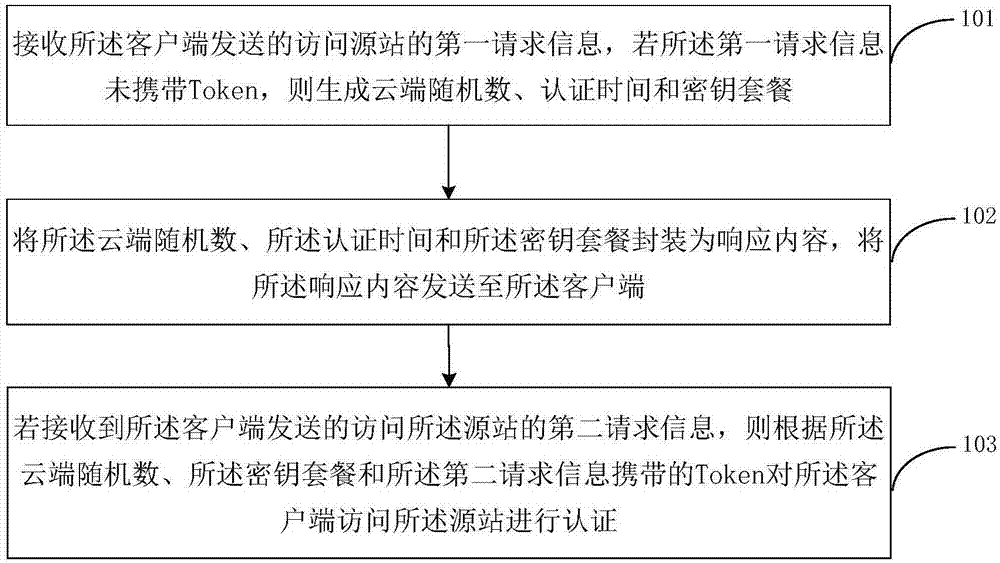
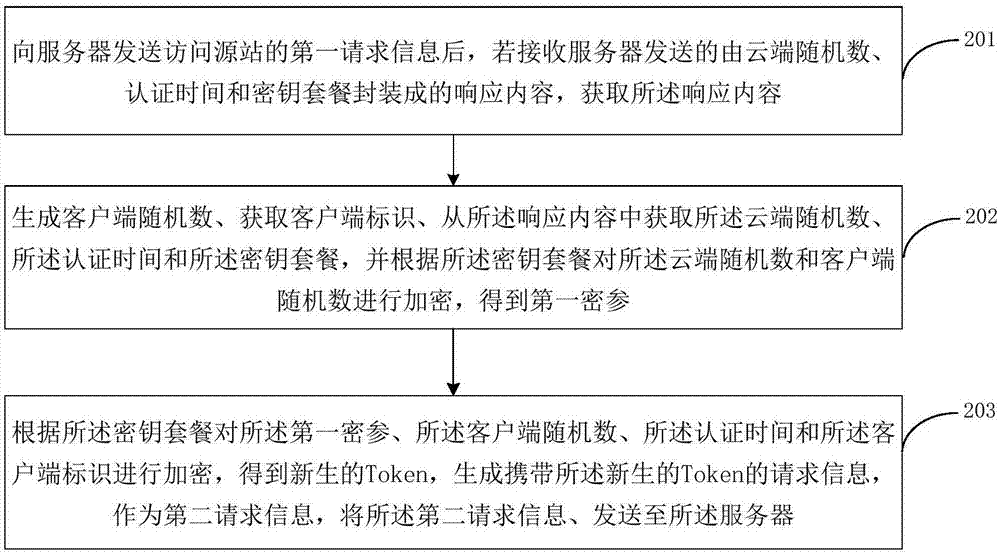
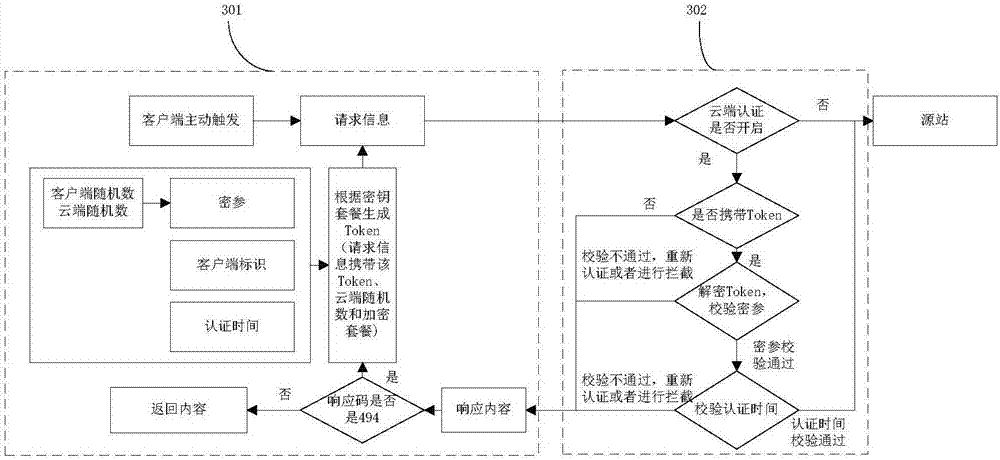
Embodiments of the invention disclose a method for carrying out cloud protection certification, a server and a client. According to the method, after received request information is judged to not carry a Token, a response content which is encapsulated by a cloud random number, certification time and a key package is generated and is sent to the client; the client obtains a newborn Token accordingto the response content, a client identifier and a client random number generated by the client, generates second request information carrying the newborn Token and sends the second request information to the server; and the server realizes certification about whether to allow the client to visit a source station through the Token. According to the method, through interaction with the client, theclient which sends the first request information without the Token regenerates the second request information carrying the Token, so that the legality of the Token carried by the second request information about the request information and the authenticity about the client are checked, and the authentication of the Token is carried out on the request information without the Token.
Owner:BEIJING QIANXIN TECH
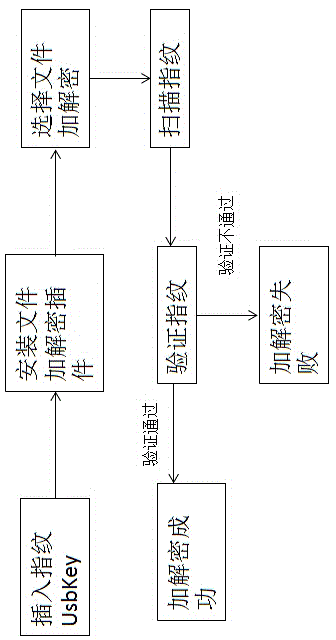
Method for performing identity authentication and file encryption and decryption based on fingerprint UsbKey
InactiveCN104021332AImplement encryption protectionNot easy to loseDigital data authenticationOperational systemEngineering
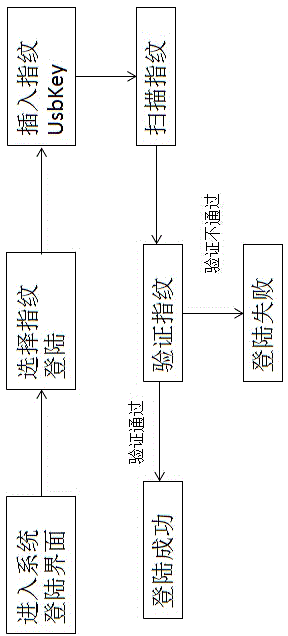
The invention discloses a method for performing identity authentication and file encryption and decryption based on a fingerprint UsbKey, relating to the field of computer information security. A memory unit, a fingerprint identifier and an indication light are integrated on U disc-like equipment with USB interfaces, configuration management is performed by special PC (personal computer for running Windows, Linux and other normal operation systems) terminal management software, and the U disc-like equipment has a memory function of an ordinary U disc, enables a user to perform identity authentication and file encryption and decryption through fingerprints and also can be taken as the ordinary U disc. Password and key management are performed by the safe and convenient method, and loss caused by the fact that a password or a key is lost is avoided.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
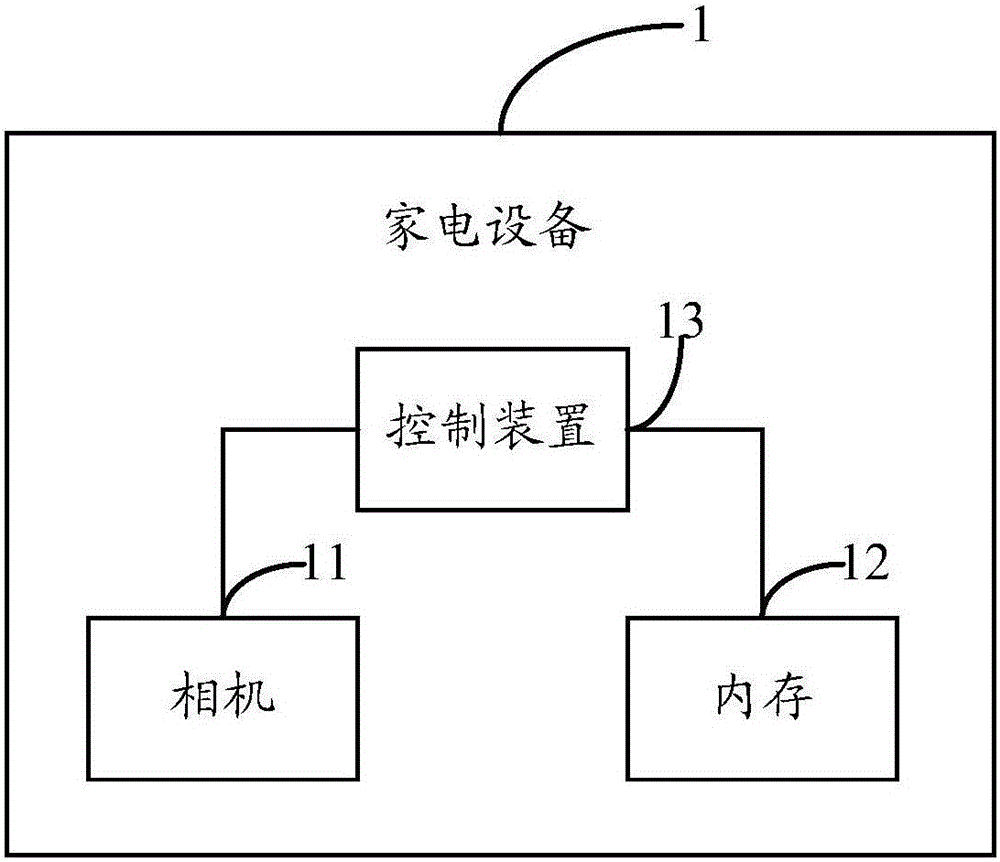
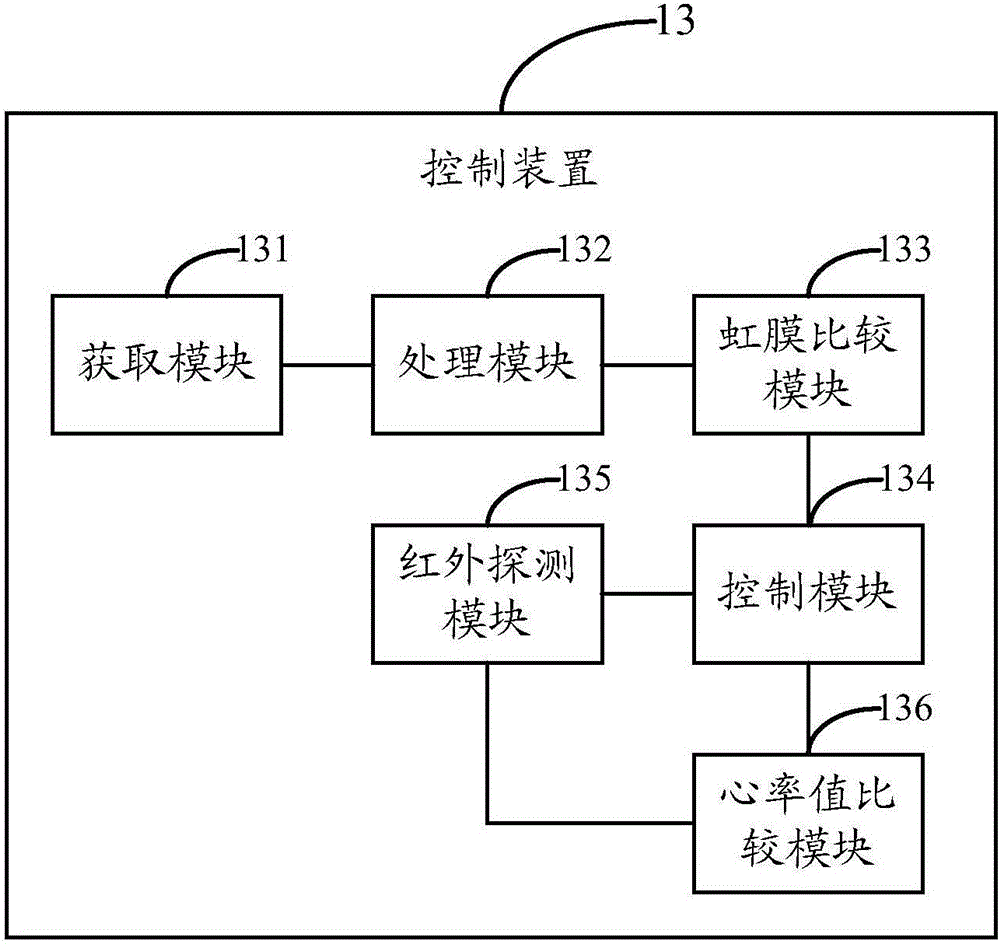
Control apparatus and method for household appliances, and household appliances
InactiveCN105574385AImplement authenticationTo achieve the purpose of environmental protection and energy savingDigital data authenticationComputer moduleIris image
The invention discloses a control apparatus for household appliances. The control apparatus comprises an obtaining module, a processing module, an iris comparison module, a control module, an infrared detection module and a heart rate comparison module, wherein the obtaining module is used for controlling a camera to shoot an iris of a user and obtaining a corresponding authenticated iris image; the processing module is used for extracting the feature information of the authenticated iris image; the iris comparison module is used for comparing the feature information extracted by the processing module with the feature information of an original iris; the control module is used for opening the household appliances when the user passes the identity authentication; the infrared detection module is used for obtaining a heart rate value of the user in a detection region according to a preset period; the heart rate comparison module is used for comparing the obtained heart rate value with a preset heart rate threshold value; and the control module is also used for closing the household appliances when the obtained heart rate value is lower than the preset heart rate threshold value. Correspondingly, the invention also discloses the control apparatus for the household appliances, and the household appliances. By adoption of the invention, identity authentication for the user can be realized, and electric energy can be saved.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Method and system for obtaining battery information
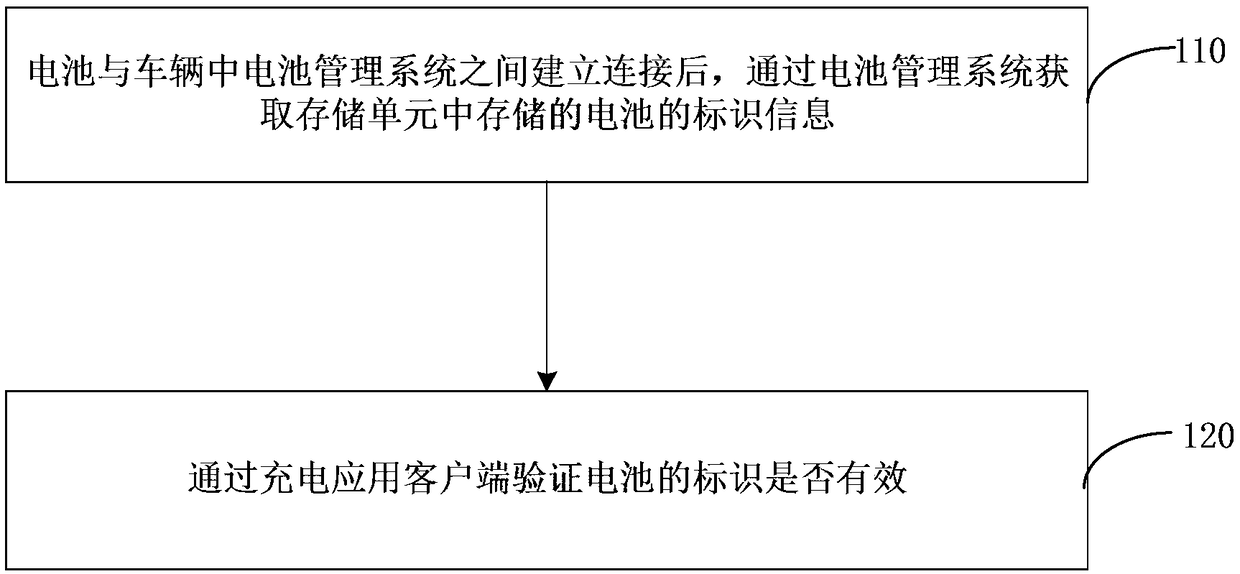
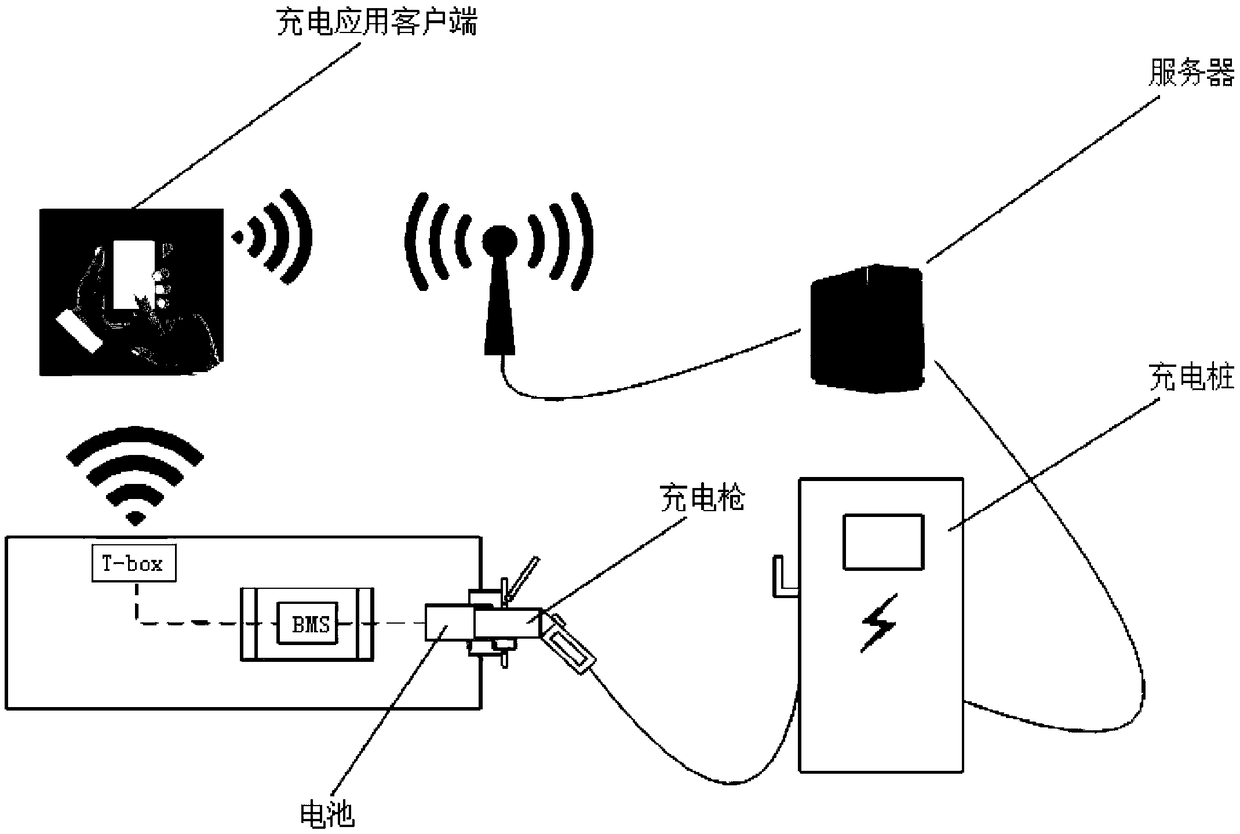
InactiveCN108649635AImplement authenticationCircuit authenticationCharging stationsBattery chargeElectrical battery
The embodiment of the invention discloses a method and system for obtaining battery information. The method comprises the following steps: after a connection is established between a battery and a battery management system in a vehicle, obtaining identification information of the battery stored in a storage unit through the battery management system; and verifying whether the identification information of the battery is valid through a charging application client, so that when the identification information of the battery is valid, a charging device connected to the battery charges the batterybased on charging parameters configured in the charging application client. By adoption of the method and system provided by the embodiment of the invention, the identity verification between the battery and the battery management system in the vehicle is achieved, and by adoption of the charging application client, the battery is charged by the charging application client bound based on the battery.
Owner:ZHICHEAUTO TECH BEIJING +1
Method and system for preventing set top box software from malicious upgrade
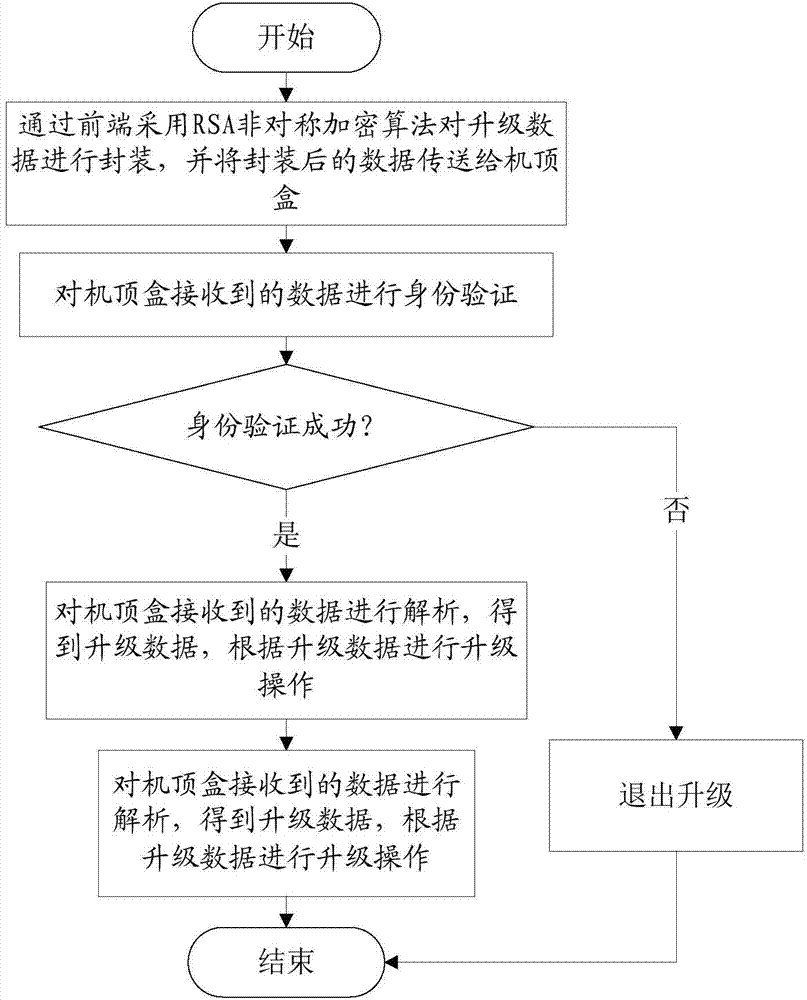
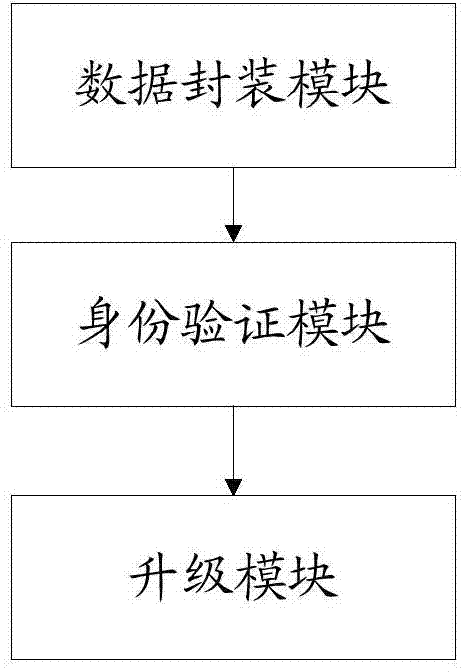
InactiveCN104780445APrevent malicious modificationProtect interestsSelective content distributionEncapsulated dataData shipping
The invention provides a method for preventing set top box software from malicious upgrade, comprising the steps as follows: step 10, encapsulating upgrade data by adopting RSA asymmetric cryptographic algorithm via a front end and transmitting the encapsulated data to a set top box; step 20, authenticating data received by the set top box, and entering a step 30 if the authentication is successful; otherwise, quitting the upgrade; step 30, analyzing the data received by the set top box to obtain upgrade data and performing upgrade according to the upgrade data. The invention further provides a system for preventing set top box software from malicious upgrade, comprising a data encapsulation module, an authentication module and an upgrade module. The method and the system of the invention improve safety of data and effectively prevent illegal operation.
Owner:FUJIAN NEWLAND COMM SCI TECH
Unmanned aerial vehicle safety certifiable information communication processing method based on cloud platform
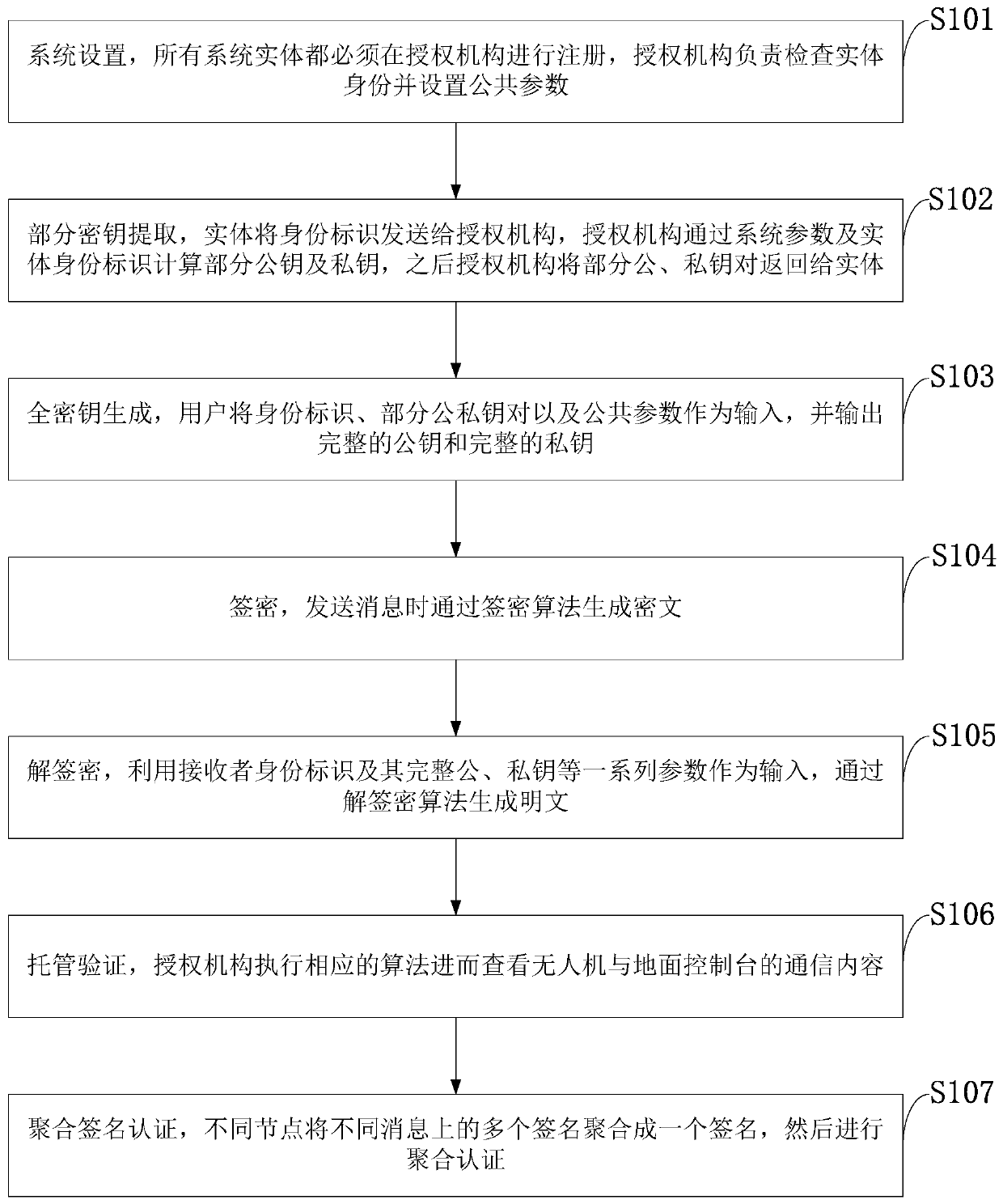
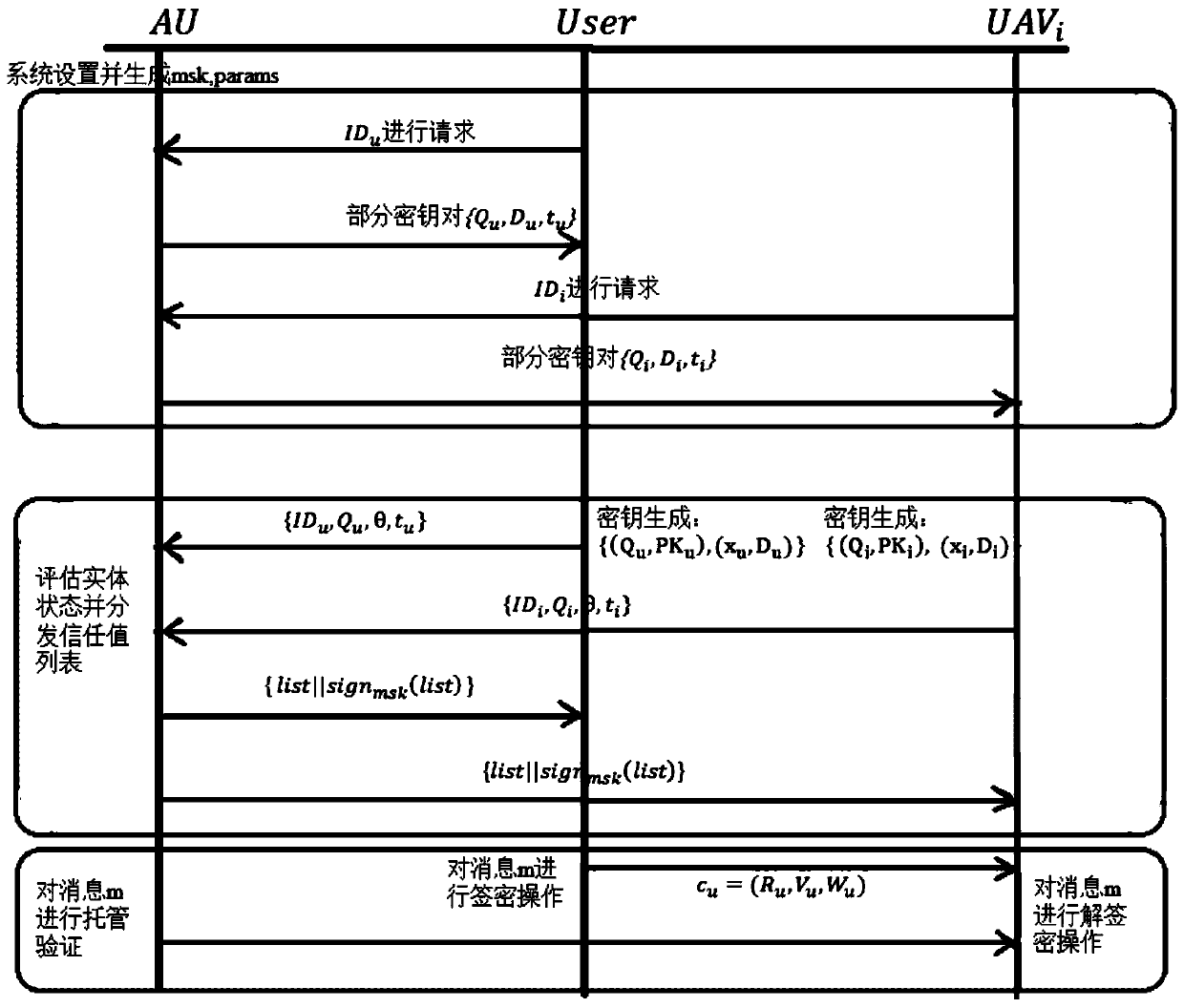
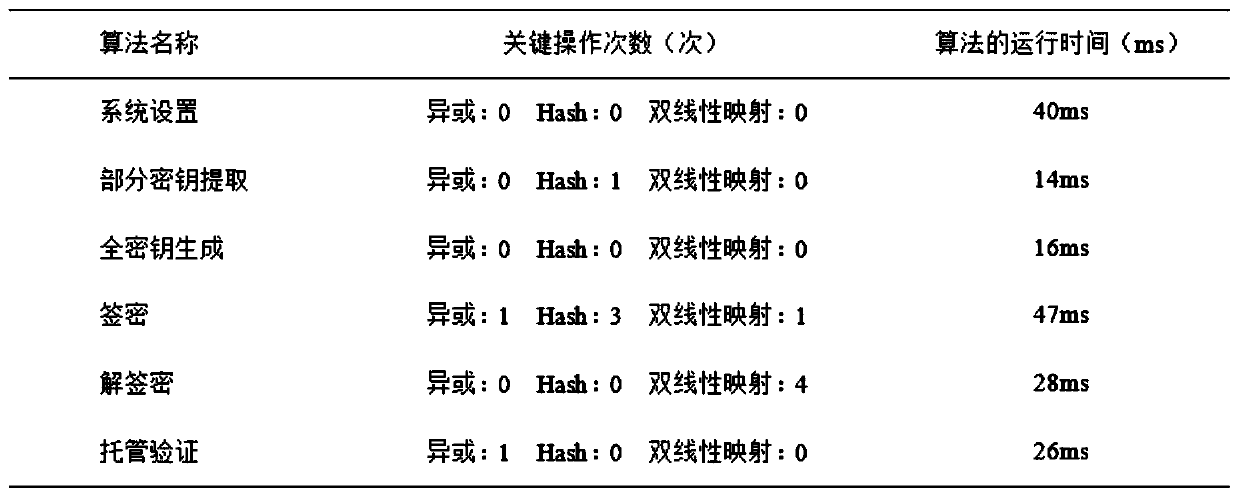
ActiveCN110690959AReduce overheadSolve redundancyKey distribution for secure communicationTransmission systemsPlaintextAlgorithm
The invention belongs to the technical field of unmanned aerial vehicle communication, and discloses an unmanned aerial vehicle safety certifiable information communication processing method and system setting based on a cloud platform. The method includes: setting a system; extracting a part of secret keys; generating a full key; generating a ciphertext through a signcryption algorithm when a message is sent; generating a plaintext through an unsigncryption algorithm by taking the receiver identity label and the parameters thereof as input; enabling the authorization mechanism to execute a corresponding algorithm so as to check and supervise the communication content of the unmanned aerial vehicle and the ground console; and enabling different nodes to aggregate a plurality of signatureson different messages into one signature for aggregation authentication, so as to reduce the authentication overhead. According to the invention, confidentiality, authentication, non-repudiation and unforgeability are realized; public key encryption and digital signature are combined, and confidentiality and identity authentication can be achieved at the same time. The authorization mechanism provides part of the key through the secure channel, and can check the access command and the location information. The control command and the position information cannot be forged under the condition ofno other part of private keys.
Owner:XIDIAN UNIV
Authentication method, system, and computer-readable storage medium
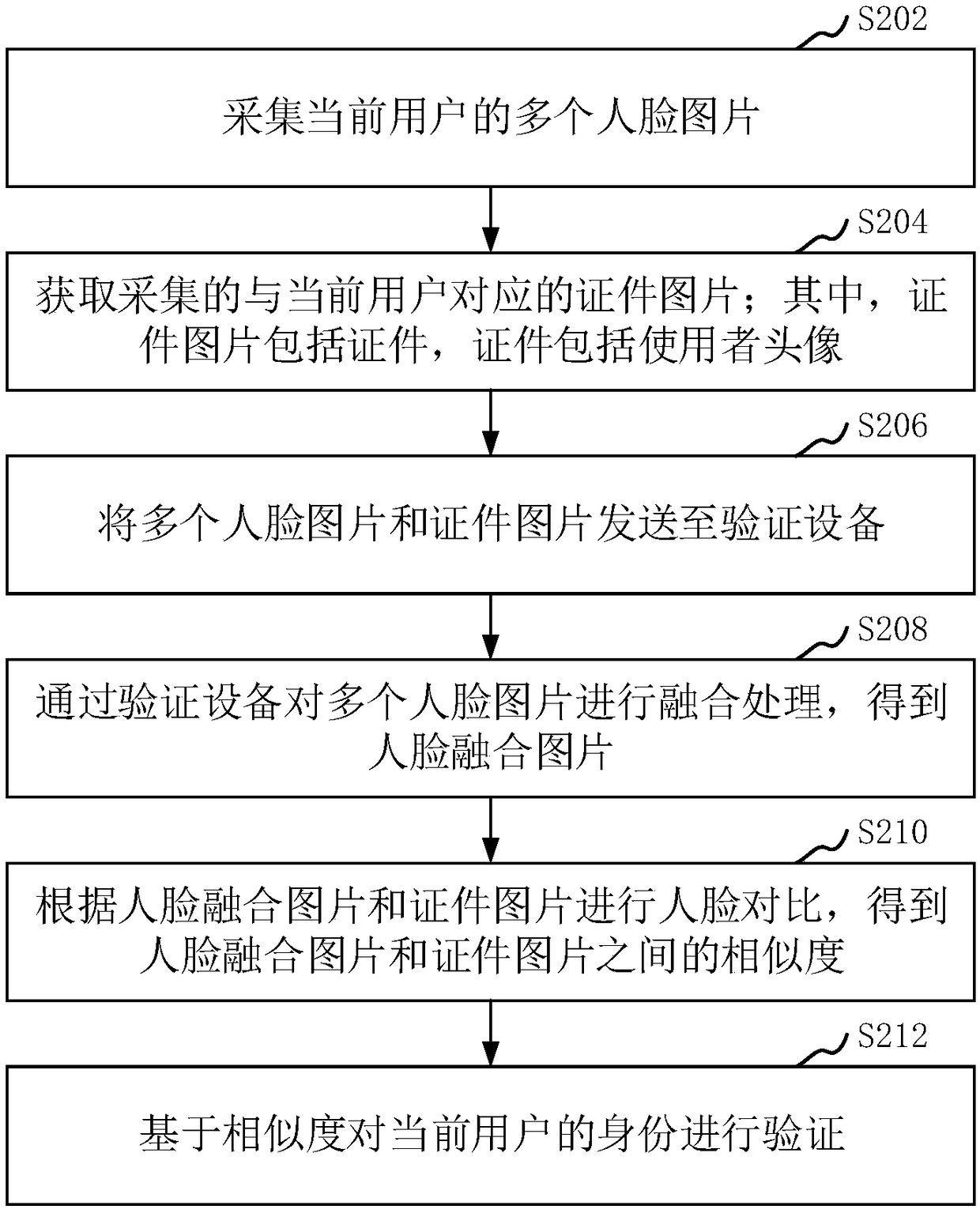
PendingCN109409060AImplement authenticationQuality improvementImage enhancementImage analysisPattern recognitionAuthentication
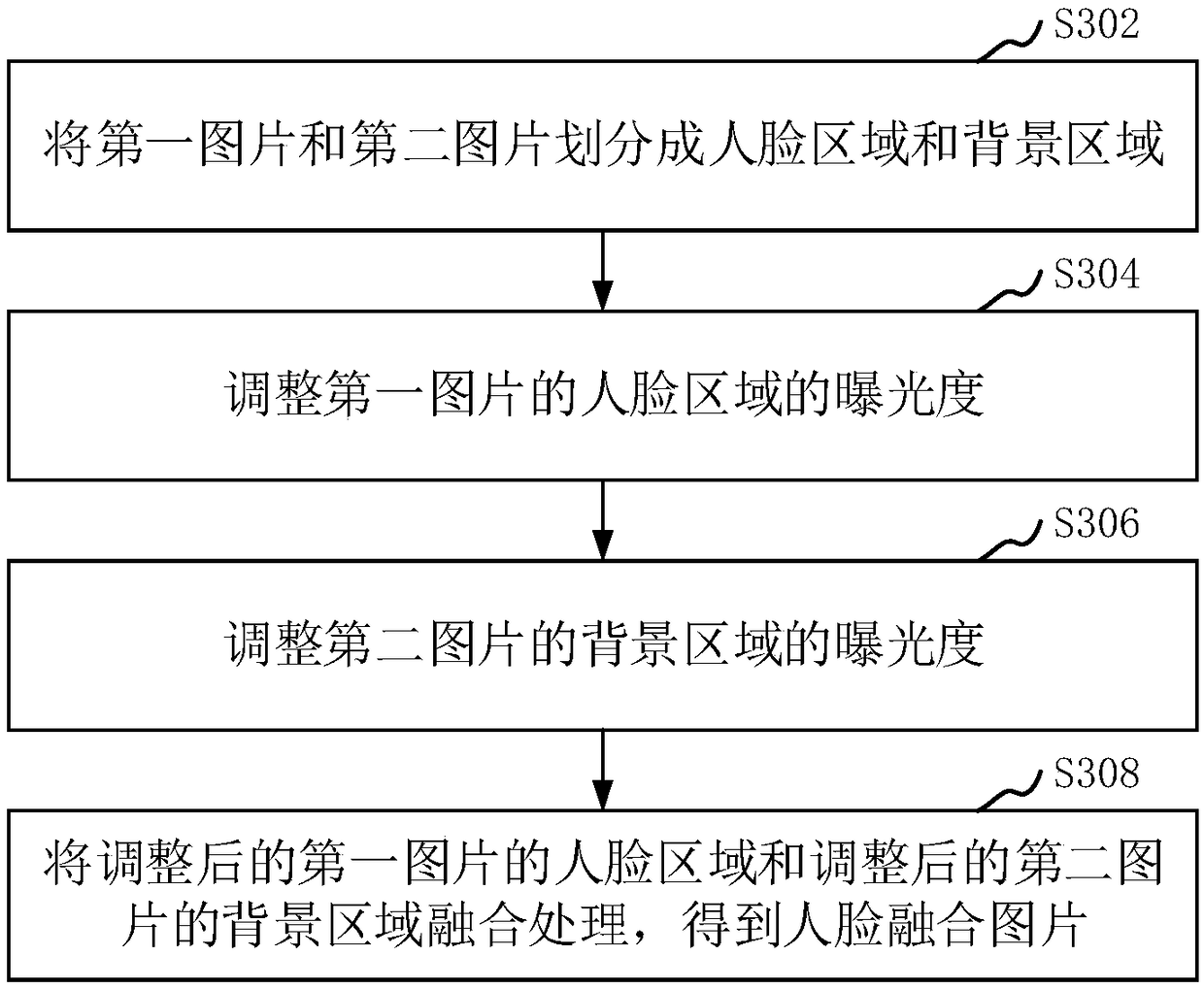
The present application relates to an authentication method, a system, and a computer readable storage medium. The authentication method is based on face recognition. The method comprises the following steps: collecting a plurality of personal face pictures of a current user; obtaining a certificate picture of a certificate corresponding to the current user; among them, the picture of the certificate includes the certificate, and the certificate includes the head portrait of the user; sending a plurality of personal face pictures and a certificate picture to an authentication device; Face fusion images are obtained by fusion processing of multiple face images by a verification device, and the face fusion images are processed by a verification device. According to the face fusion picture and the certificate picture, the similarity between the face fusion picture and the certificate picture is obtained. Authenticates the identity of the current user based on similarity. The method can directly verify the identity of a user by using a low-configuration high-speed camera.
Owner:CHINA PING AN LIFE INSURANCE CO LTD
Head-mounted online examination machine
ActiveCN105654803ARealize online closed-book examImplement authenticationCharacter and pattern recognitionElectrical appliancesLine sensorEngineering
The invention provides a head-mounted online examination machine and belongs to the technical field of computer education and network. The examination machine comprises a shell, a head-mounted frame, observation mirrors, an observation mirror bracket, a light inductor, a distance inductor, a control board, an iris recognition and eye monitoring camera set, an earphone cover, a playing trumpet and a microphone, wherein the examination machine is provided with a connector connected with a PC (Personal Computer) side; the observation mirror bracket is fixedly connected with the shell; the two observation mirrors are mounted on the observation mirror bracket; the light inductor is arranged at the lower part of the observation mirror bracket; the distance inductor is mounted on the observation mirror bracket; the control board is fixedly connected with the shell; the iris recognition and eye monitoring camera set is used for photographing irises of examiners; and the earphone cover is internally provided with the playing trumpet and the microphone. With the adoption of the device provided by the invention, online closed-book exams can be realized, and identity verification of the examiners can be realized; and a condition that the examiners pick off the device to cheat in an examination process can be prevented and a condition that the examiners cheat by hearing sounds can be prevented.
Owner:SHENZHEN HUAYI MEDICAL TECH CO LTD
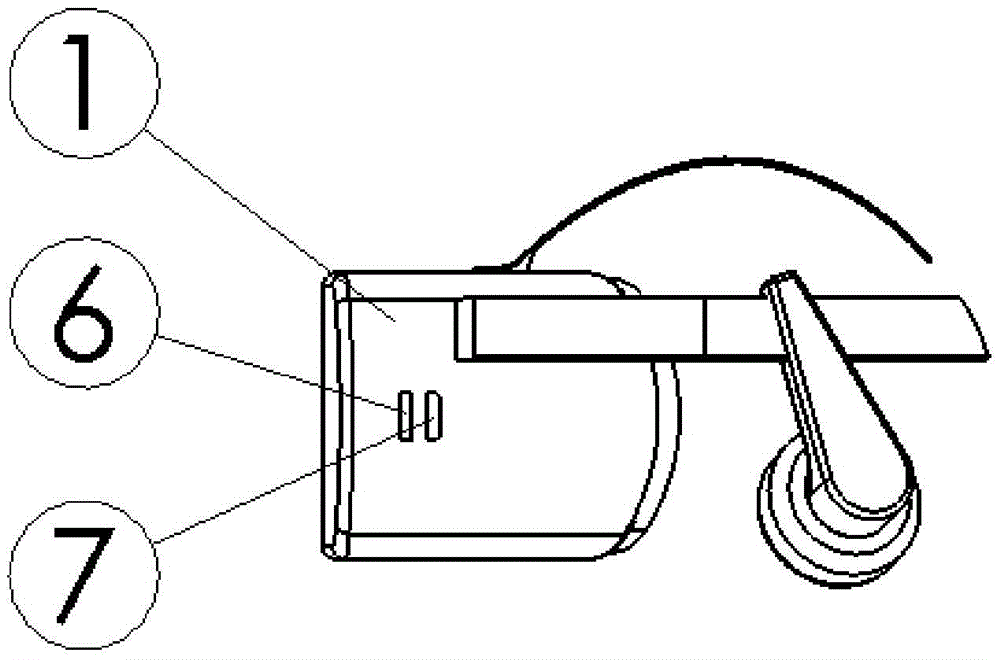
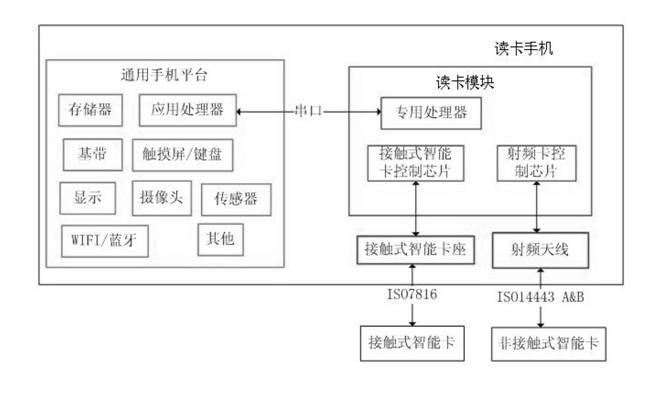
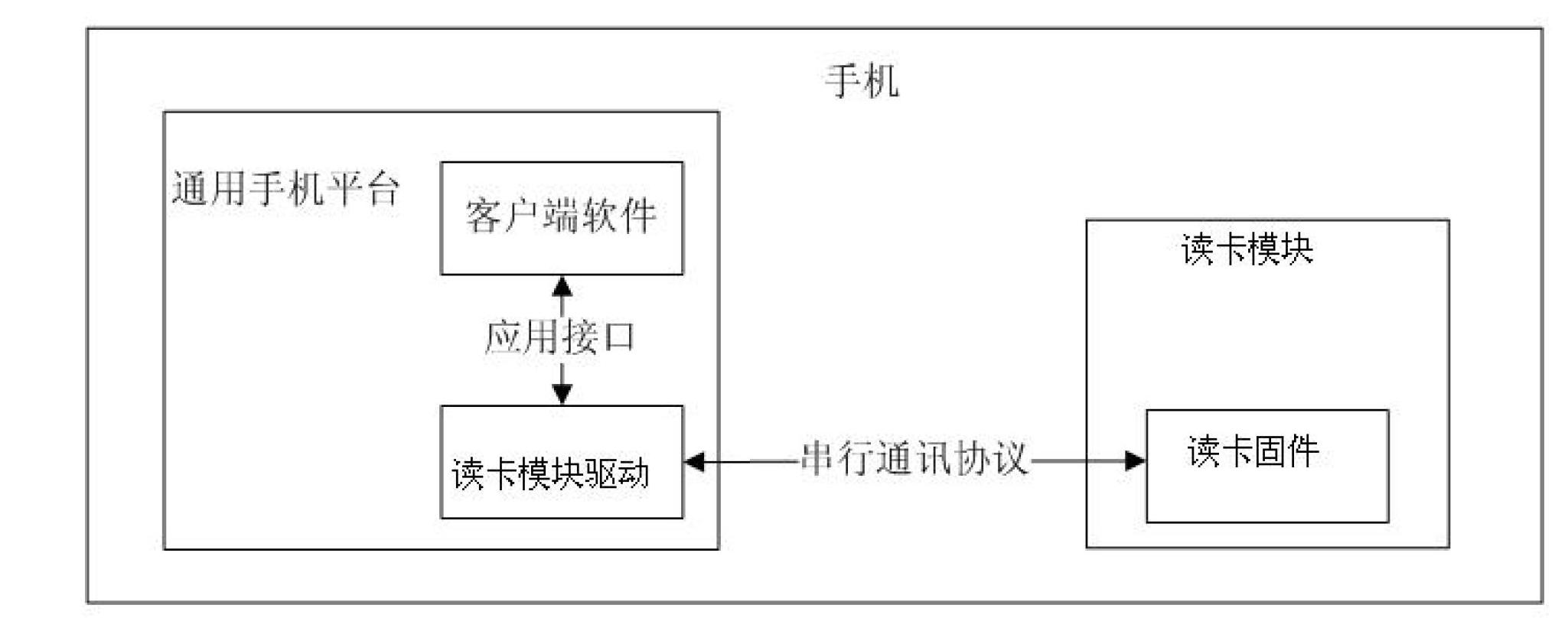
Mobile terminal with read card function and mobile terminal payment method
ActiveCN102693480AImplement authenticationImprove conveniencePayment architecturePaymentComputer terminal
The invention discloses a mobile terminal with a read card function for reading intelligent card information. The mobile terminal is characterized in that: an intelligent card read module is disposed in the terminal, connected with a processor on a general mobile terminal platform by a COM and processes read-write operation to intelligent cards. Users can read the intelligent card held by themselves via the mobile terminal with the read card function with increasing of intelligent card circulation, thereby the problem of USB key use inconvenience is solved.
Owner:FUJIAN LANDI COMML EQUIP CO LTD
Method and system for guiding airplane docking and identifying airplane type based on machine vision
ActiveCN105373135AImprove intelligenceImprove the level of operation managementImage enhancementHydraulic/pneumatic visible signallingInformation processingMachine vision
The invention discloses a method and a system for guiding airplane docking and identifying an airplane type based on machine vision. The method comprises the steps of S1, setting an airplane docking scene, dividing a monitored scene into different information processing functional areas; S2, image pre-processing for performing preprocessing on a photographed image; S3, capturing the airplane, confirming a fact that the airplane appears in the image through identifying the engine and the front wheel of the airplane in the image; S4, tracking the airplane, performing continuous tracking real-time updating on the captured images of the engine and the front wheel of the airplane; S5, positioning the airplane, realizing real-time positioning on the airplane and accurately determining the deviation degree of the airplane relative to a guiding line and a distance between the airplane and a stopping line; and S6, displaying information, outputting and displaying the deviation degree of the airplane relative to the guiding line and the distance between the airplane and the stopping line in the step S5. The method and the system have advantages of realizing airplane docking guiding in a visual manner and effectively accuracy in an airplane docking process.
Owner:SHENZHEN CIMC TIANDA AIRPORT SUPPORT
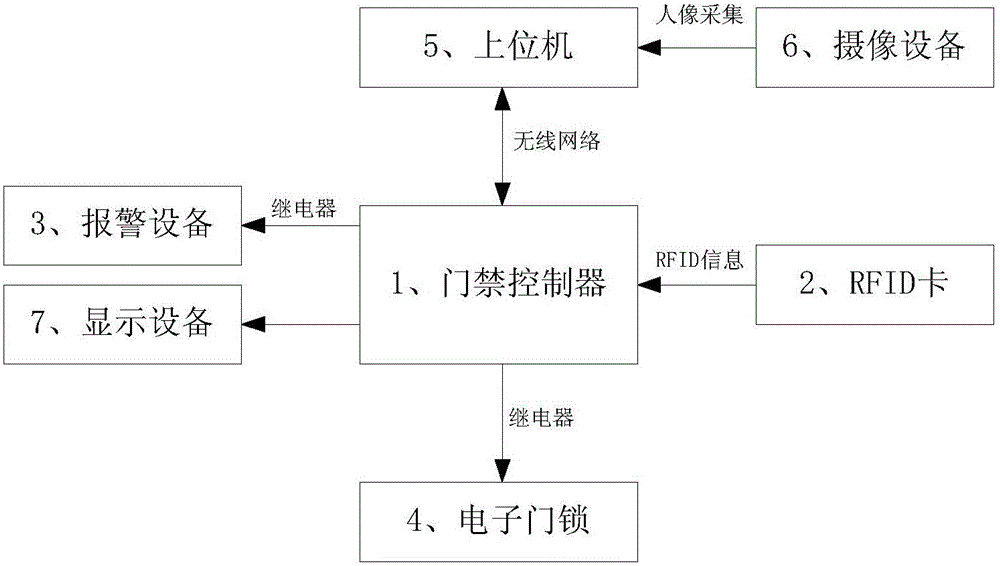
Access control device
InactiveCN105931342ASolve identity verification difficultiesAddressing Vulnerability to Identity TheftIndividual entry/exit registersElectronic accessCommunication interface
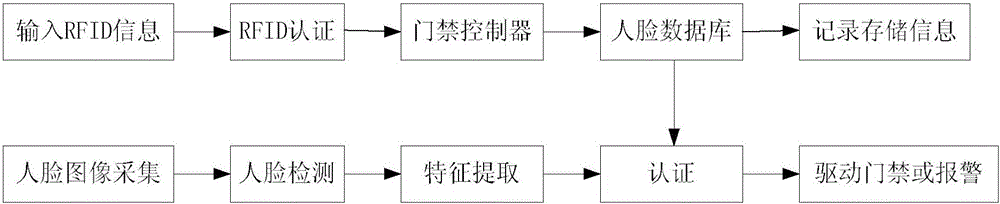
The invention discloses an access control device, comprising an access control unit, an RFID (radio frequency identification) card, an alarm device, an electronic door lock, an upper computer and a photographic device. The access control unit uses a low-frequency communication interface to receive RFID information transmitted by the RFID card; the access control unit wirelessly communicates with the upper computer through a wireless network, and the photographic device acquires a human image and transmits the acquired data to the upper computer; the access control unit dries the electronic door lock through a relay; the access control unit connects with the alarm device through a relay. The access control device provides identification by combining RFID with facial recognition, the problem of the traditional mode that personnel is difficult to identify and their identities are vulnerable to stealing may be effectively solved, and safety of use of electronic access control may be effectively improved.
Owner:胡昔兵
Building door access control method, cloud server and computer-readable storage medium
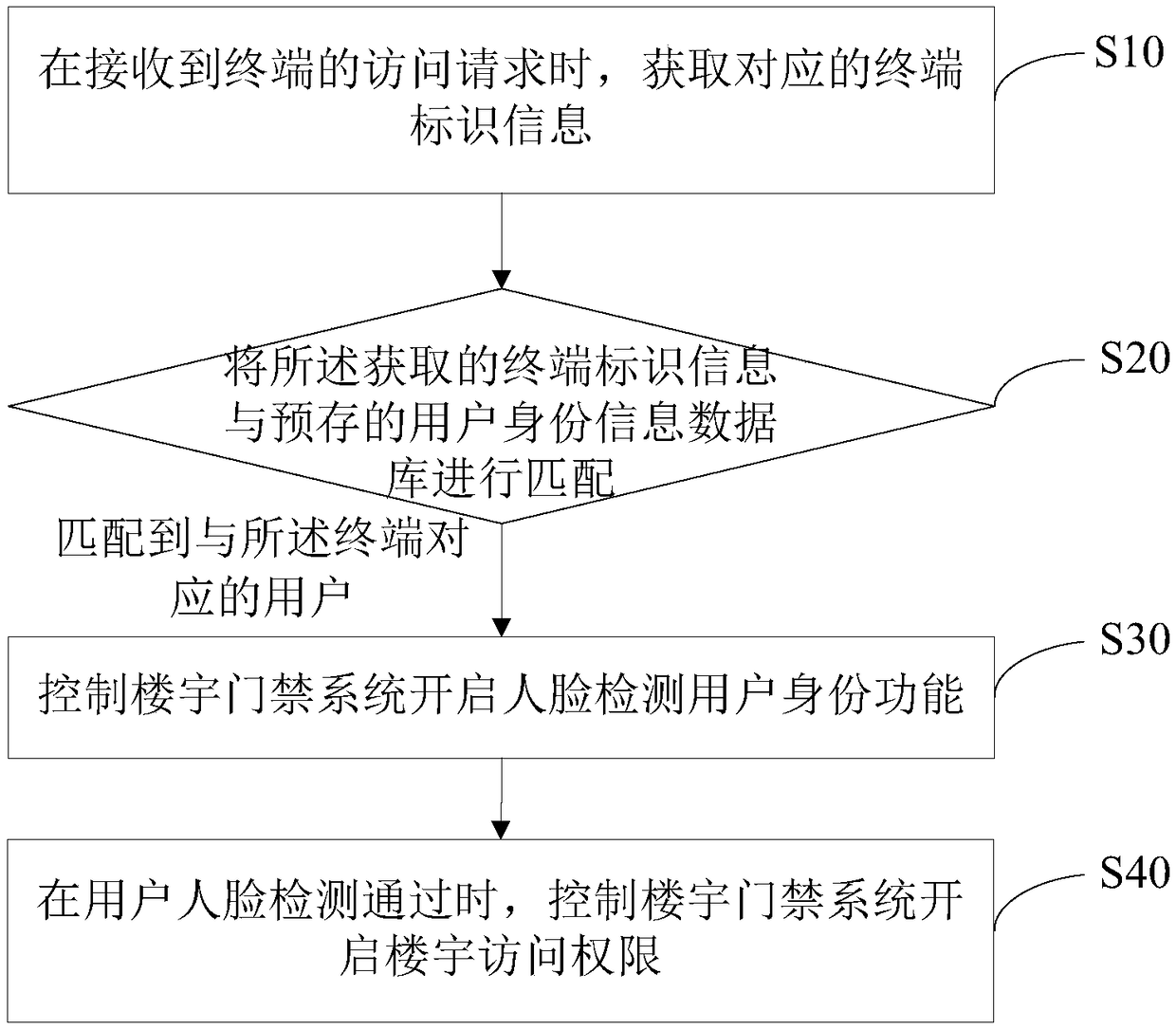
InactiveCN108806041AEasy accessImprove experienceIndividual entry/exit registersFace detectionComputer terminal
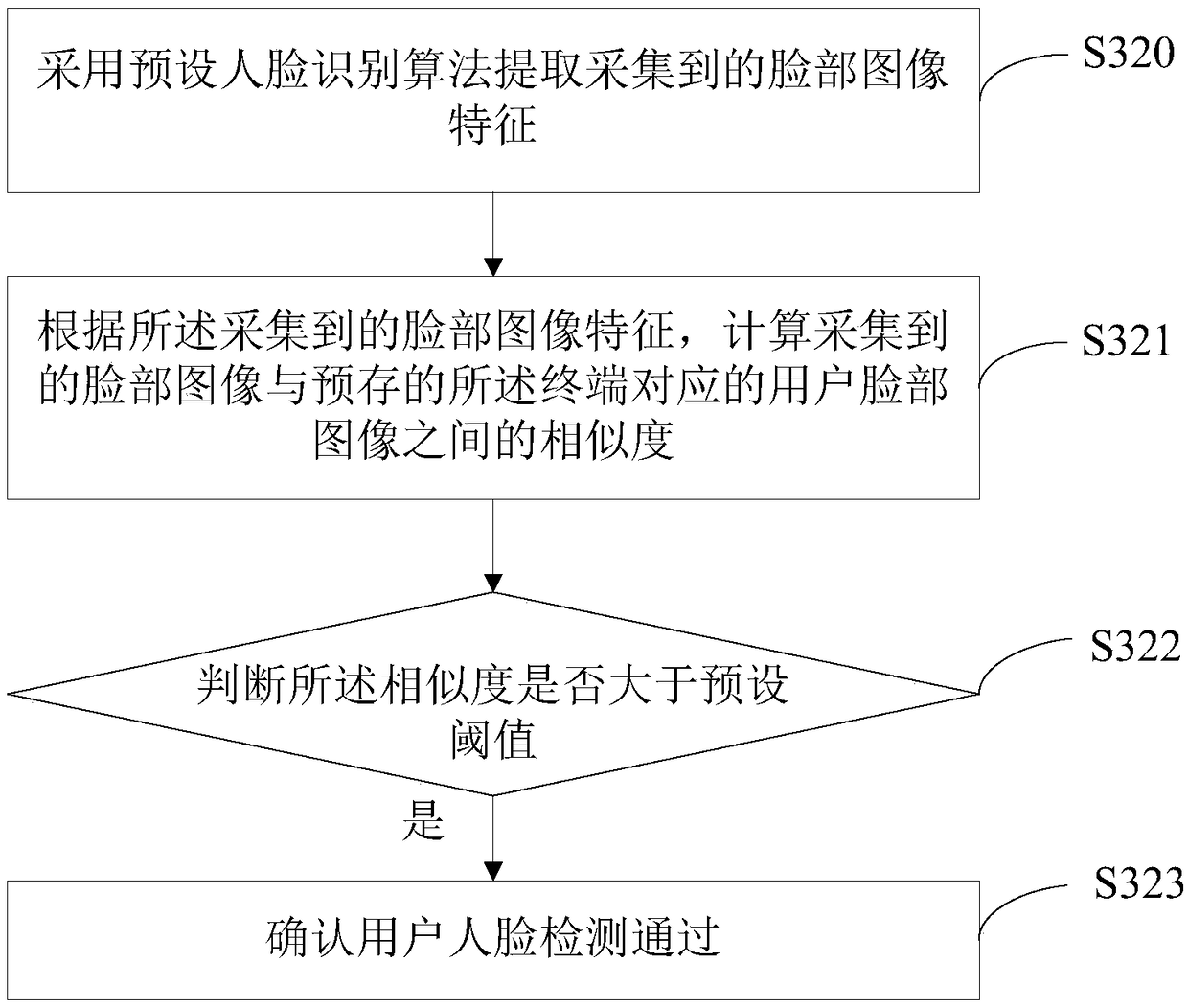
The invention discloses a building door access control method. The method is applied to a cloud server. The method comprises the following steps: acquiring corresponding terminal identification information when an access request of the terminal is received; matching the acquired terminal identification information with pre-stored user identity information database; controlling a building door access system to open a face detection user identity function if the user corresponding to the terminal is matched; controlling the building door access system to open building access permission when facedetection of the user is passed. The invention further discloses a cloud server and a computer-readable storage medium. According to the method disclosed by the invention, the building access convenience is improved, and the user experience is improved.
Owner:SHENZHEN LINGDU INTELLIGENT CONTROL TECH CO LTD
Data collection method and device, intelligent wearable equipment and storage medium
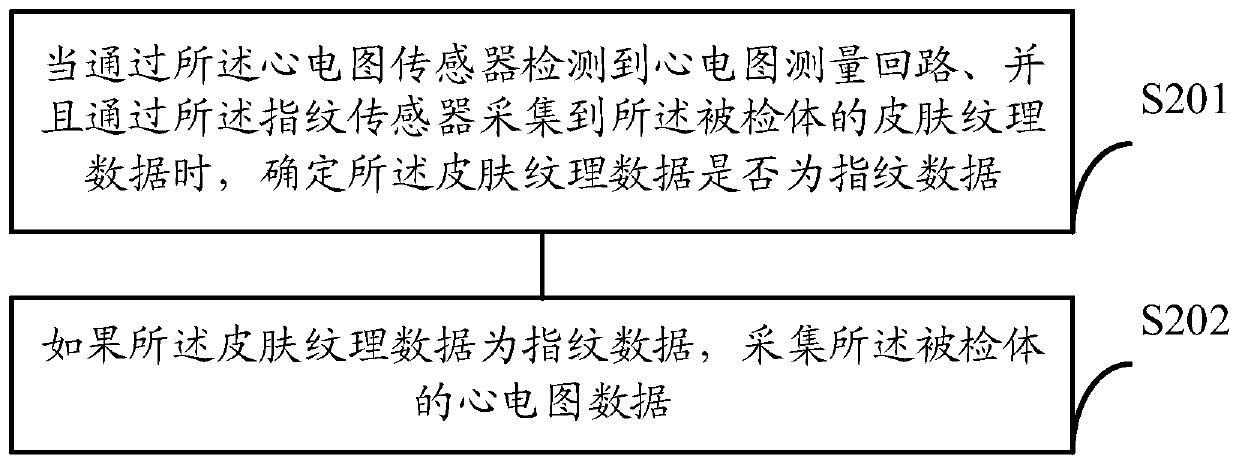
ActiveCN109938722AImprove accuracyAvoid misacquisitionDiagnostic recording/measuringSensorsPattern recognitionData acquisition
The invention discloses a data collection method and device, intelligent wearable equipment and a computer readable storage medium. The method comprises the steps that when an electrocardiogram measurement loop is detected through an electrocardiogram sensor, and skin texture data of an objected is collected through a fingerprint sensor, it is determined whether or not the skin texture data is fingerprint data; if yes, electrocardiogram data of the object is collected. The data collection method and device, the intelligent wearable equipment and the computer readable storage medium have the advantages that when it is determined that the fingerprint data is collected, the electrocardiogram data is collected, thereby avoiding the incorrect collection of the electrocardiogram data caused by the improper contact of other body parts, and improving the accuracy of electrocardiogram collection.
Owner:ANHUI HUAMI INFORMATION TECH CO LTD
Service handling method based on electronic certificate, government affair self-service terminal and storage medium
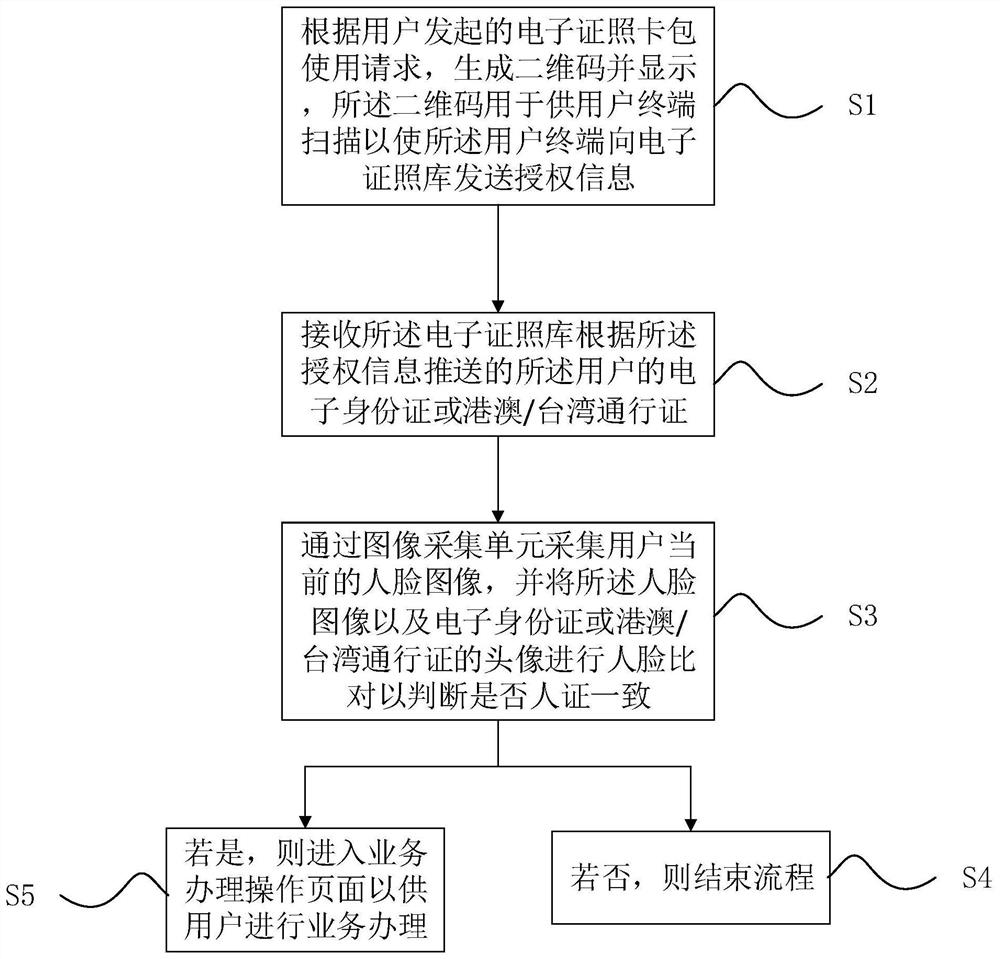
The invention discloses a service handling method based on an electronic certificate, a government affair self-service terminal and a storage medium. The method comprises the following steps: generating and displaying a two-dimensional code according to an electronic certificate card package use request initiated by a user, the two-dimensional code being used for being scanned by a user terminal to enable the user terminal to send authorization information to an electronic certificate library; receiving an electronic identity card or a Hong Kong Australian / Taiwan pass of the user pushed by theelectronic certificate library according to the authorization information; acquiring a current face image of the user through an image collection unit, and performing face comparison on the face image and the head portrait of the electronic identity card or the Hong Kong Australian / Taiwan pass to judge whether people and certificates are consistent or not; and if so, entering a service handling operation page. According to the method, the corresponding electronic certificate is acquired through the authorization information of the user, so that the electronic certificate is compared with theacquired current face image to realize identity authentication of the user, the user does not need to carry an identity card or input an identity card number, and the method is more convenient and quicker.
Owner:GUANGDONG KAMFU TECH CO LTD
Electronic equipment, device and method for controlling state switching of target equipment
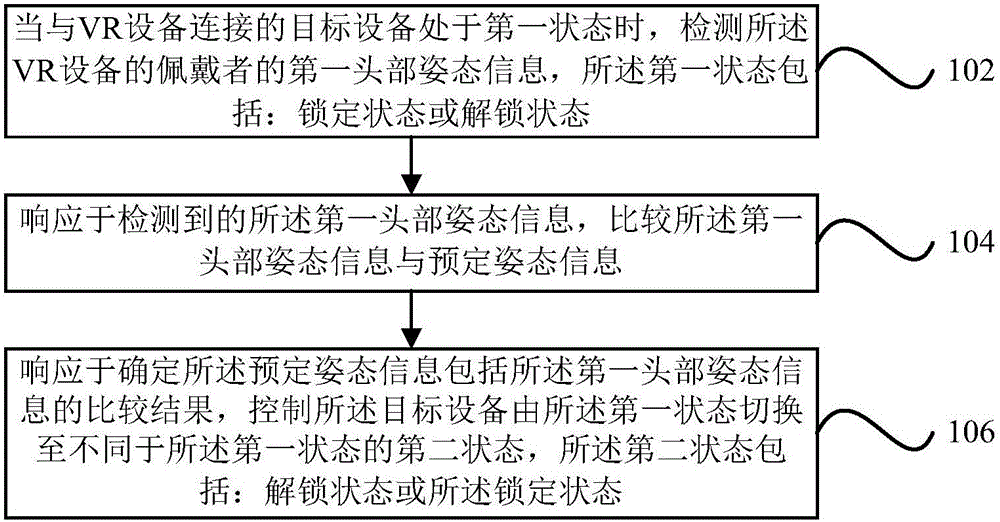
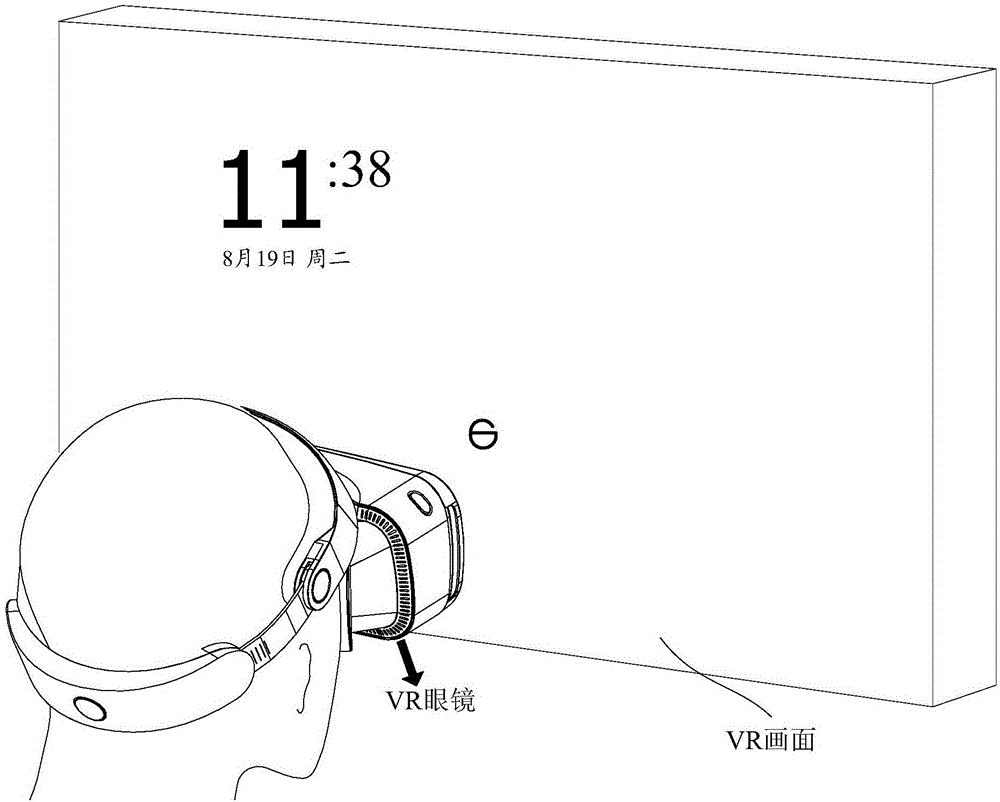
InactiveCN106843479AImplement authenticationImplement state switching operationsInput/output for user-computer interactionGraph readingState switchingComputer science
The invention relates to electronic equipment, a device and a method for controlling state switching of target equipment. The method includes: when the target equipment connected with VR (virtual reality) equipment is in a first state, detecting first head posture information of a wearer of the VR equipment, wherein the first state includes a locked state or an unlocked state; responding to the detected first head posture information, and comparing the first head posture information with preset posture information; responding to a comparison result which determines that the preset posture information includes the first head posture information, and controlling the target equipment to switch from the first state to a second state different from the first state, wherein the second state includes the unlocked state or the locked state. By the technical scheme, state switching of the target equipment in a virtual reality scene can be realized conveniently and quickly.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
Rural consumer goods circulation application platform
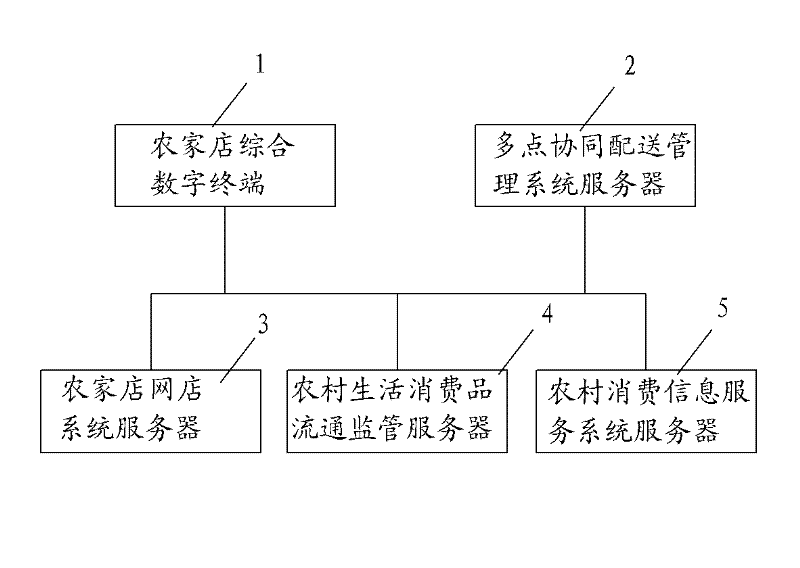
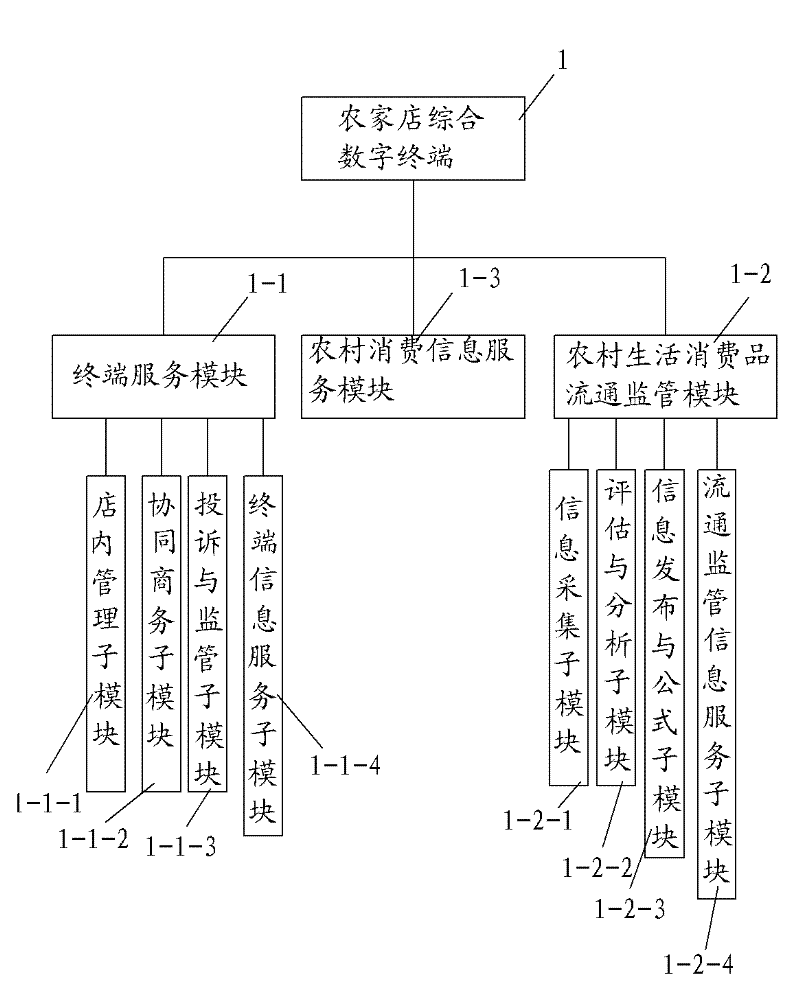
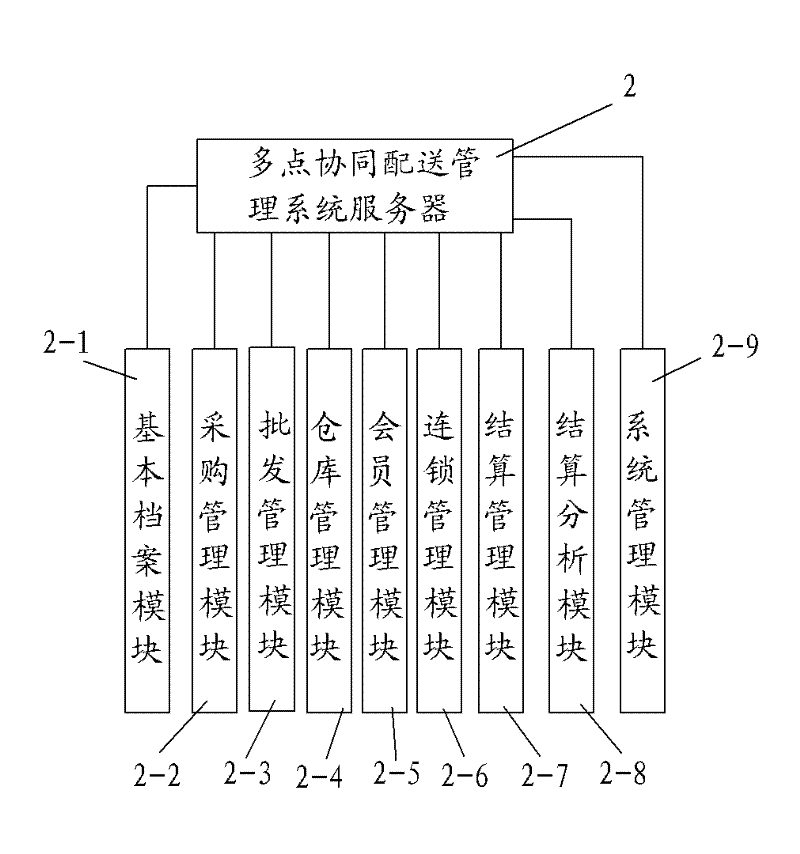
InactiveCN102346875ASimple operation modeRich informationData processing applicationsData acquisitionComputer science
The invention belongs to the goods circulation field, especially relating to a rural consumer goods circulation application platform. The platform comprises a rural store integration digital terminal, a multi-point cooperation dispatching management system server, a rural store network store system server, a rural consumer goods circulation supervision system server, and a rural consumption information service system server which are mutually connected through a network. The platform has the following advantages that: with regards to a rural consumer goods circulation mode, a channel organization with rural stores and consumer goods circulation enterprises as main propulsion power is established, a network has multiple functions, and on the basis of finishing rural store data acquisition, information interaction among a government department, a circulation enterprise, a rural store, and a consumer is realized. Opening a rural store on a network is realized, a rural store operation state is expanded, a capability of rural living article market supervision is reinforced and raised, security and health of rural living articles are ensured, and trust degree of public to quality of domestic rural circulated goods is raised.
Owner:BEIJING ZHONGHE MINBEN TECH
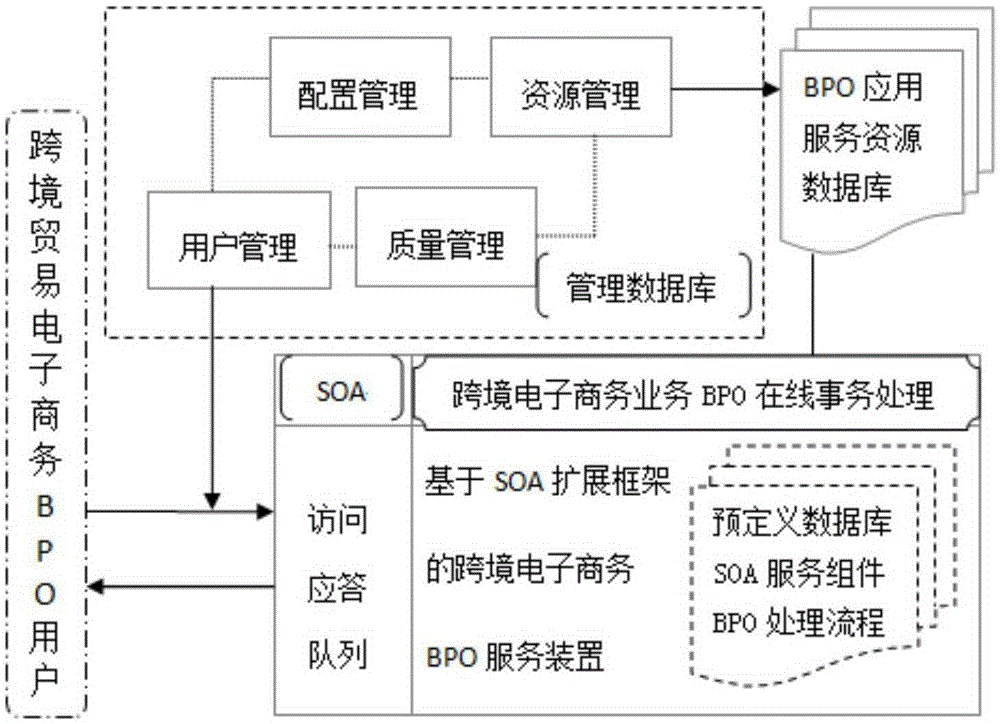
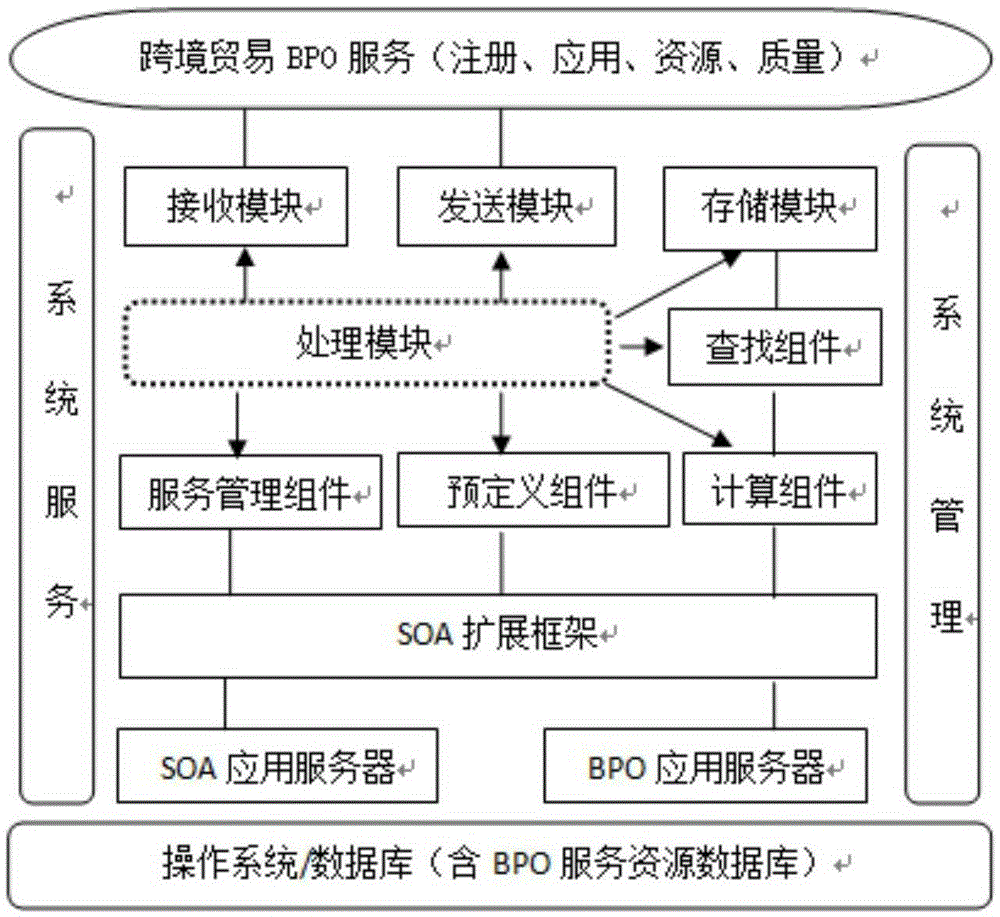
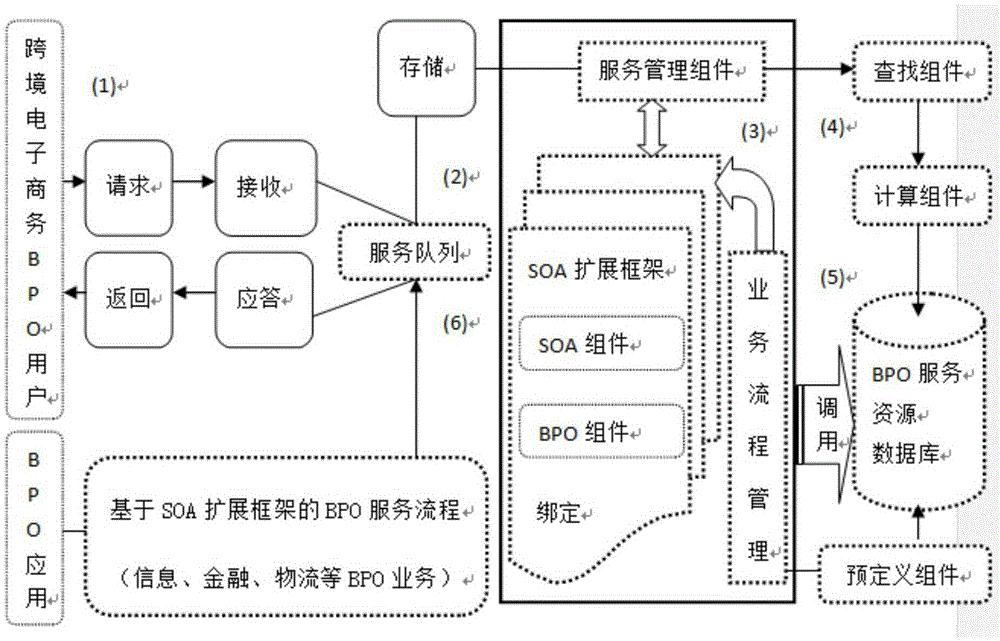
Cross-border e-commerce BPO service method and device based on SOA expansion framework
InactiveCN105427149AImplement authenticationImplement the authorization mechanismBuying/selling/leasing transactionsLogistics managementOnline business
The invention relates to a cross-border e-commerce BPO service method and device based on the SOA expansion framework. Core business operations, including information, finance and logistics, of common reusable cross-border e-commerce based on the SOA are expanded and decomposed into multiple pre-defined BPO online processing flows, when a business service request sent by a user is obtained, preset functions application resource and service quality, to be selected, of the cross-border e-commerce BPO business are reasonably selected and combined according to the preset SOA serve assembly and the BPO business processing flows, the BPO business is placed into a preset BPO business queue of the SOA, a service response is parsed into a service request response returned to the user, and the needed cross-border e-commerce BPO application service is provided for the user. According to the service method and device, multiple cross-border e-commerce BPO service access flows can be defined, configured and managed flexibly efficiently, online business processing is also flexible and efficient, and the BPO service application can be expanded by utilizing the SOA configuration expansion framework rapidly.
Owner:SHANGHAI TOPEASE INFORMATION TECH
Multifunctional mobile POS machine and application method thereof
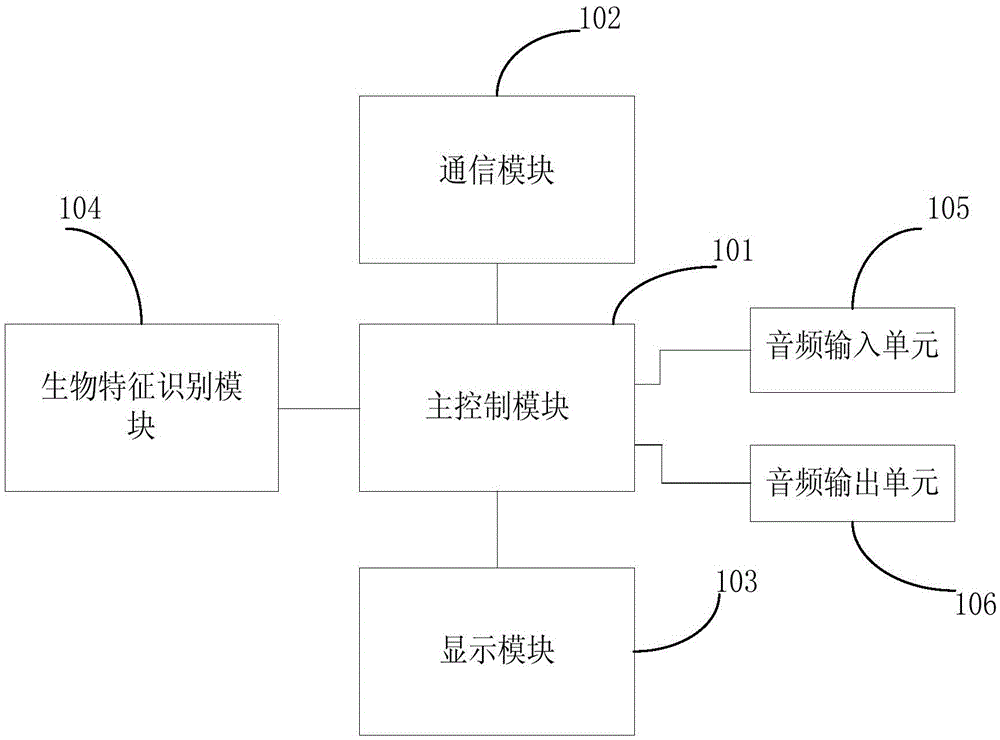
InactiveCN105488925AImplement voice controlImplement authenticationCash registersVoice dataAudio frequency
The embodiment of the invention provides a multifunctional mobile POS machine and an application method thereof and belongs to the network communication technical field. The multifunctional mobile POS machine comprises a main control module, a communication module, an audio module, a display module and a biometric characteristic identification module; the communication module, the audio module, the display module and the biometric characteristic identification module are connected with the main control module; the audio module includes an audio input unit and an audio output unit; the audio input unit is used for acquiring the voice data of a user and transmitting the voice data to the main control module; the audio output unit is used for playing voice response data issued by the main control module; and the biometric characteristic identification module is used for acquiring the biometric characteristic information of the user and transmitting the biometric characteristic information to the main control module. With the multifunctional mobile POS machine and the application method thereof of the invention adopted, the complexity of the operation of the user and the security of electronic payment can be improved.
Owner:靳玉清
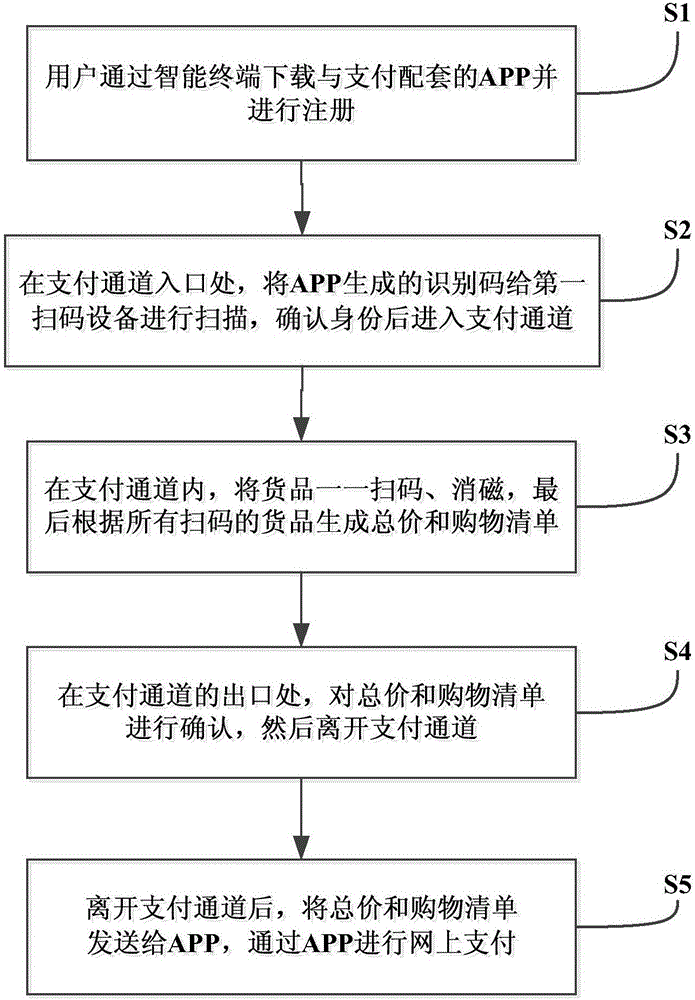
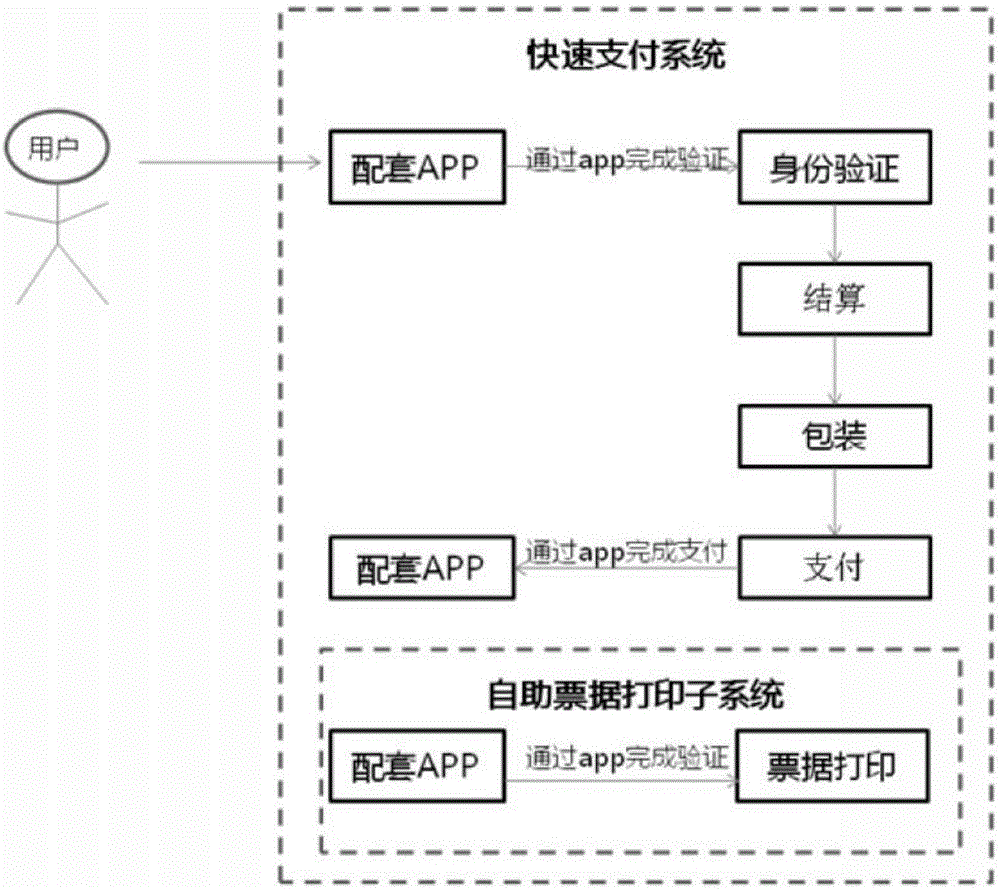
Rapid payment method and system
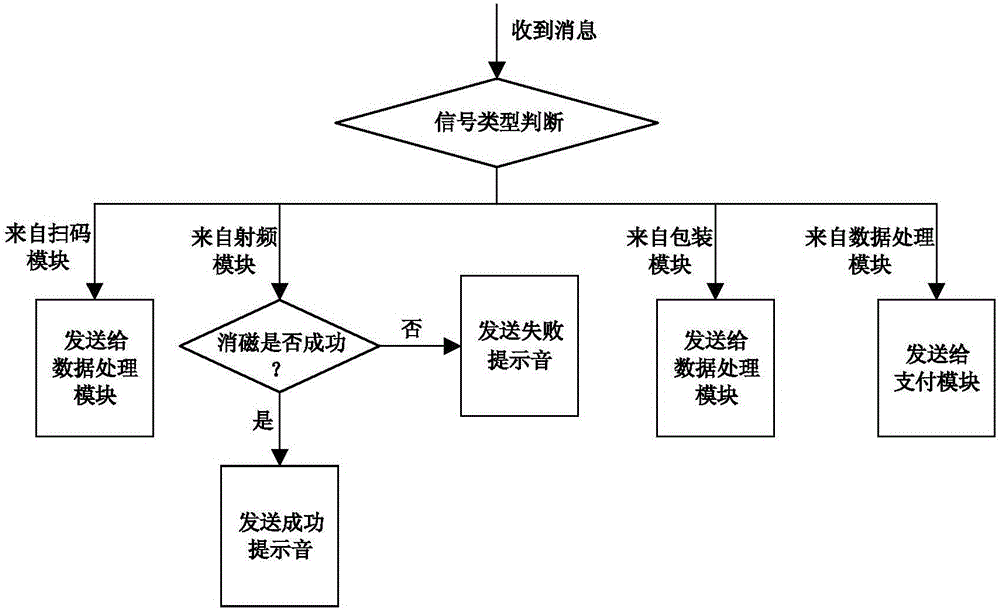
InactiveCN106340144AGood for improvingImplement authenticationCash registersBehavioral analyticsTotal price
The invention discloses a rapid payment method, which comprises the following steps: S1) a user downloads an APP matched with payment and registers through an intelligent terminal; S2) at the entrance of a payment channel, the user provides identification codes generated by the APP to a first scanning device for scanning, and enters the payment channel after identity confirmation; S3) in the payment channel, the user enables articles to be subjected to code scanning and demagnetizing, and finally, generates total price and a shopping list according to the scanned articles; S4) at the exit of the payment channel, the user confirms the total price and the shopping list, and then, leaves the payment channel; and S5) after leaving the payment channel, the user sends the total price and the shopping list to the APP, and carries out on-line payment through the APP. The invention also discloses a rapid payment system. The rapid payment method and system realize identity verification, reduce stolen rate and responsibility investigation difficulty, and facilitate to establish user's credit rating and carry out user behavior analysis; and payment is no longer done at a cashier desk, thereby effectively improving payment efficiency, and greatly reducing shopping waiting time.
Owner:李玮 +1
Access control device and verification method thereof, verification device and verification method thereof, verification system and verification method thereof
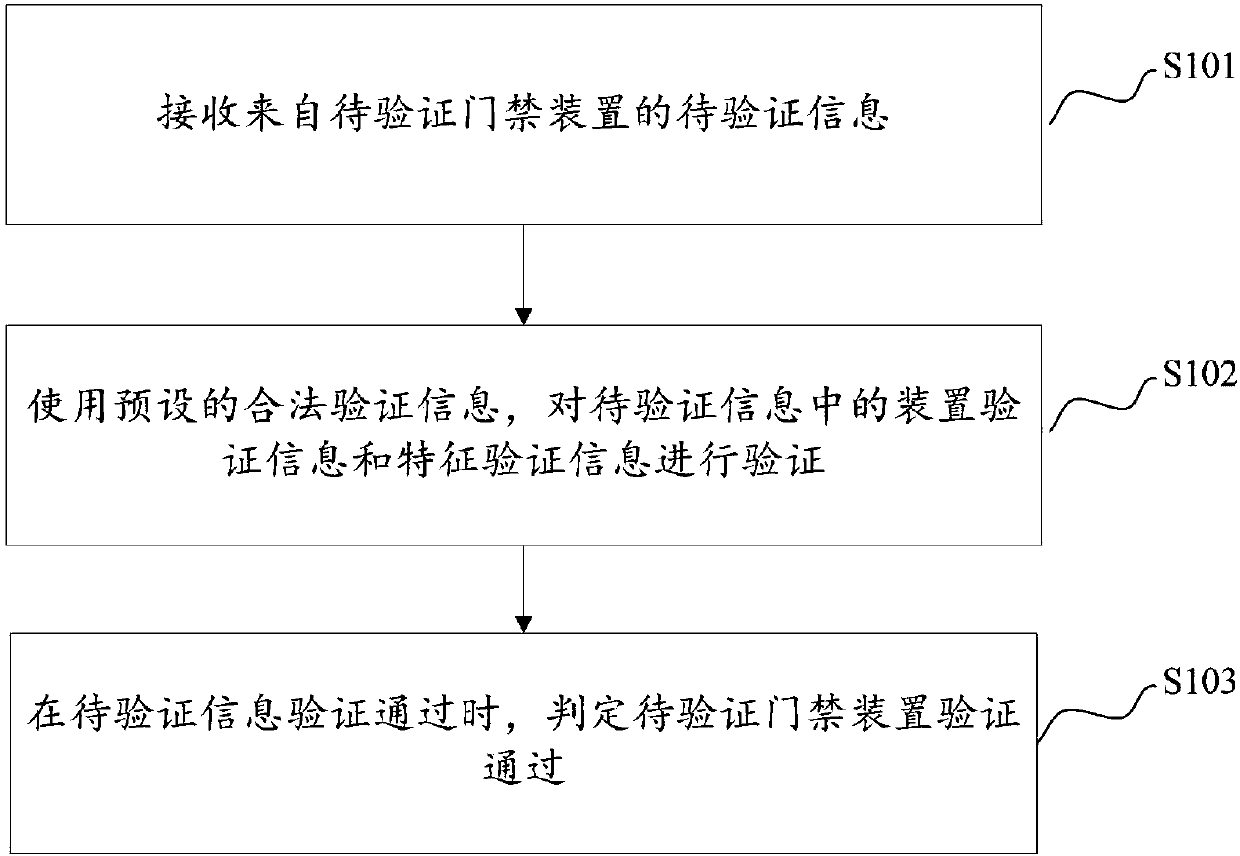
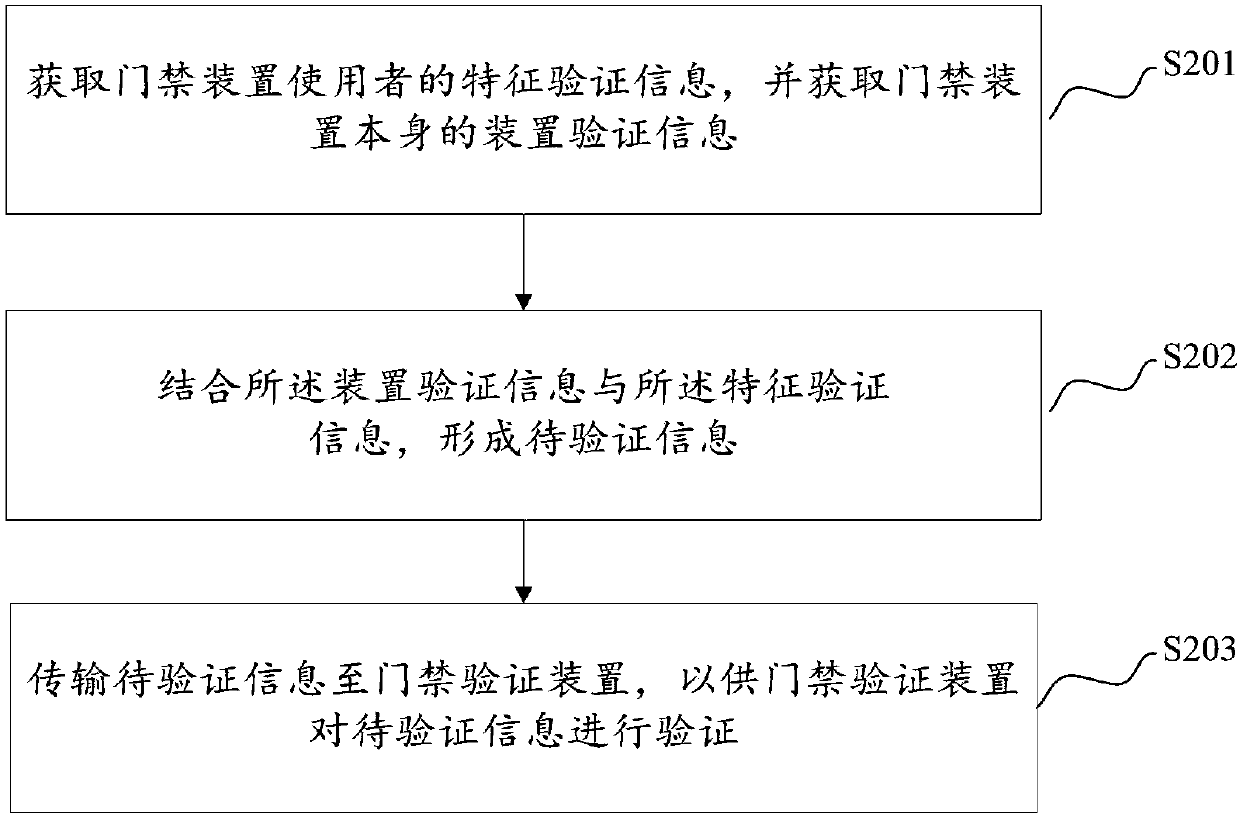
InactiveCN109961542ARealize verificationImplement authenticationKey distribution for secure communicationUser identity/authority verificationValidation methodsCard reader
The invention discloses an access control device and verification method thereof, a verification device and verification method thereof, a verification system and verification method thereof. The verification method of the access control verification device comprises the following steps that: to-be-verified information of a to-be-verified access control device is received; device verification information and feature verification information in the to-be-verified information are verified by using preset legal verification information; and when the device verification information and feature verification information in the to-be-verified information are verified successfully, the to-be-verified access control device is determined to be verified successfully. Therefore, the access control device is verified and the identity verification of the access control user is realized; and thus a problem that the identity verification of the card reader is done successfully illegally by counterfeiting the access control card easily because the existing access card reader only verifies the access control card instead of the identity of the card user in the existing access control verification process is solved.
Owner:NATIONZ TECH INC
System and method of group real name verification based on handset binding and WEB mode
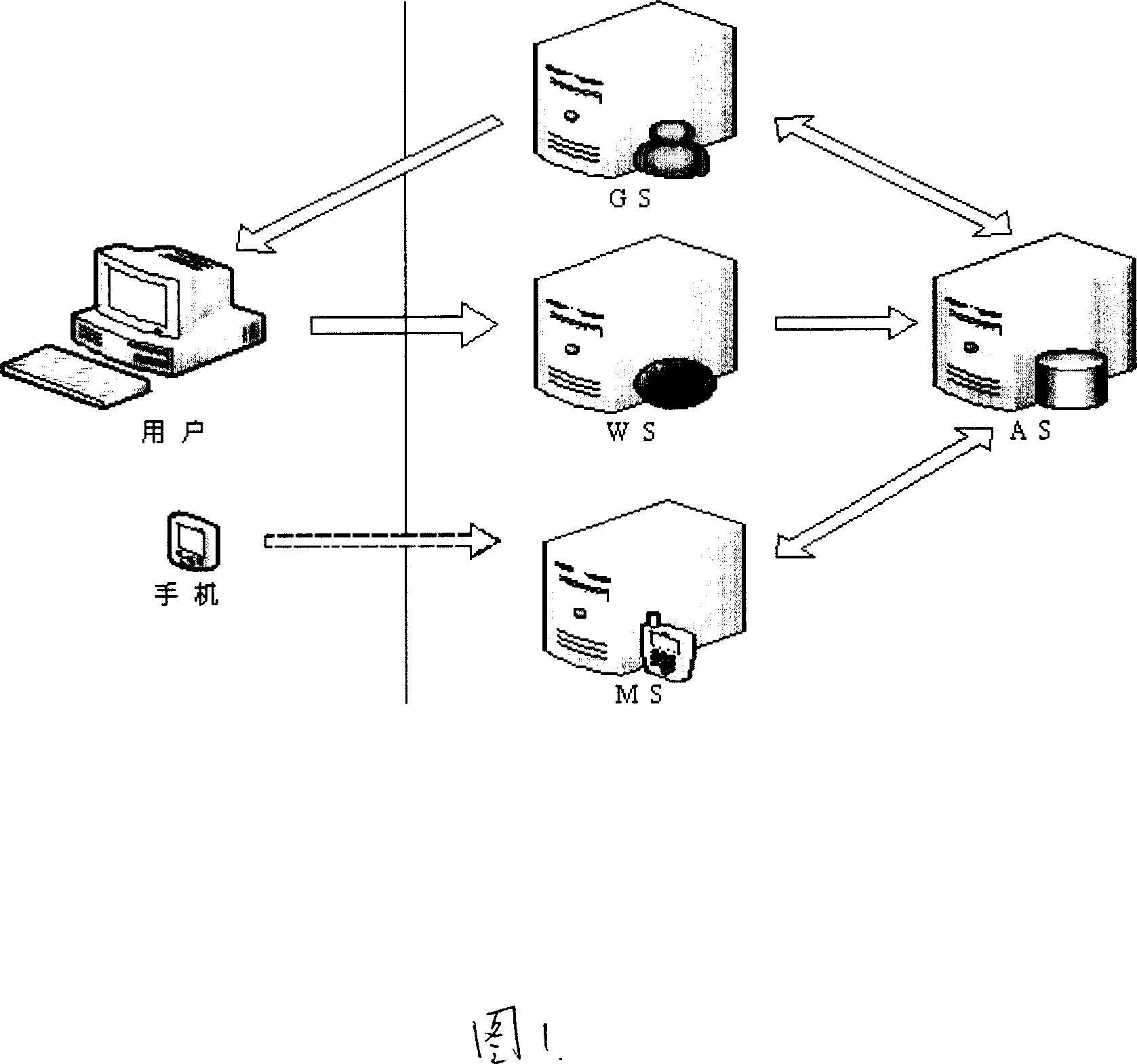
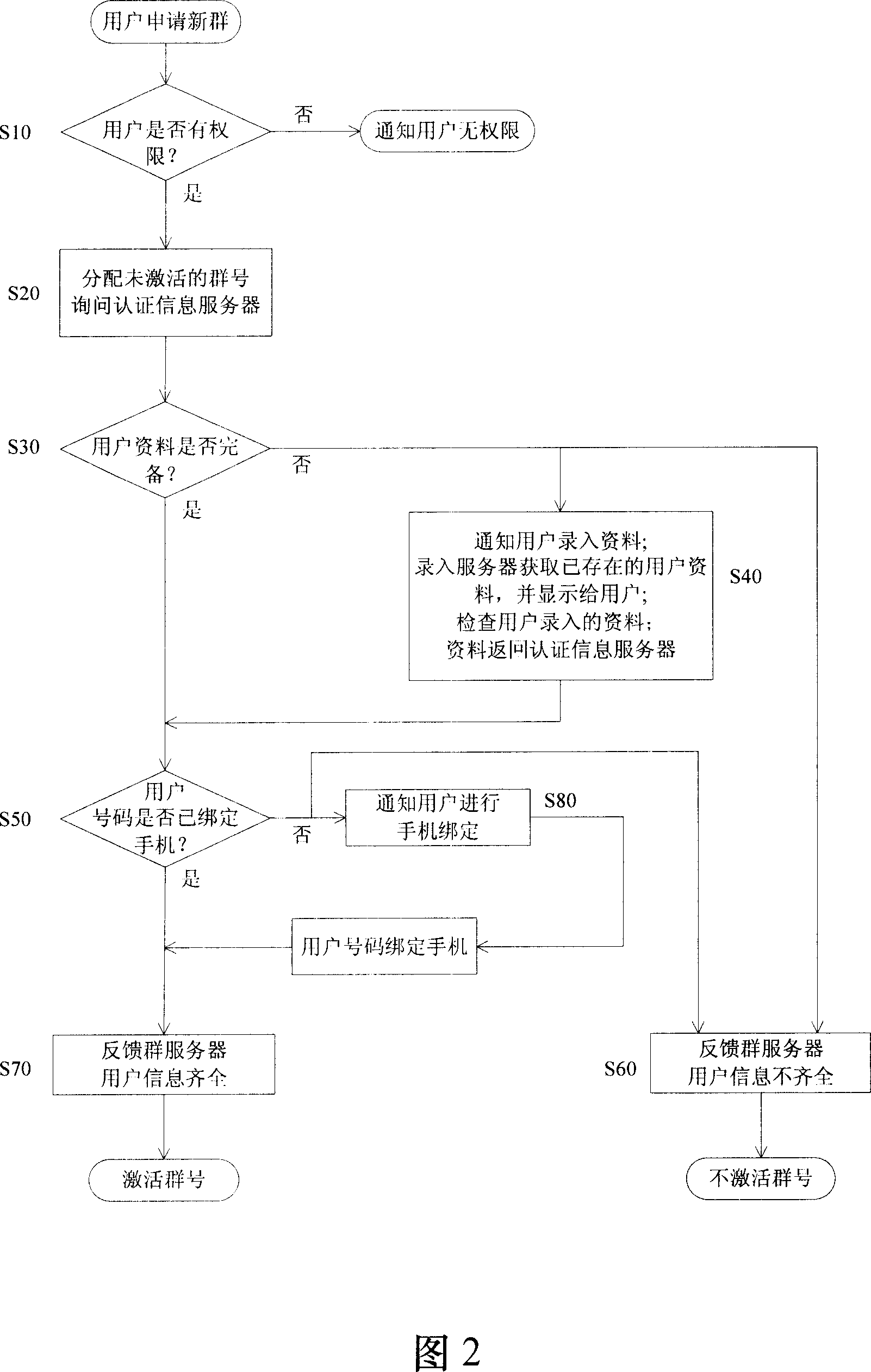
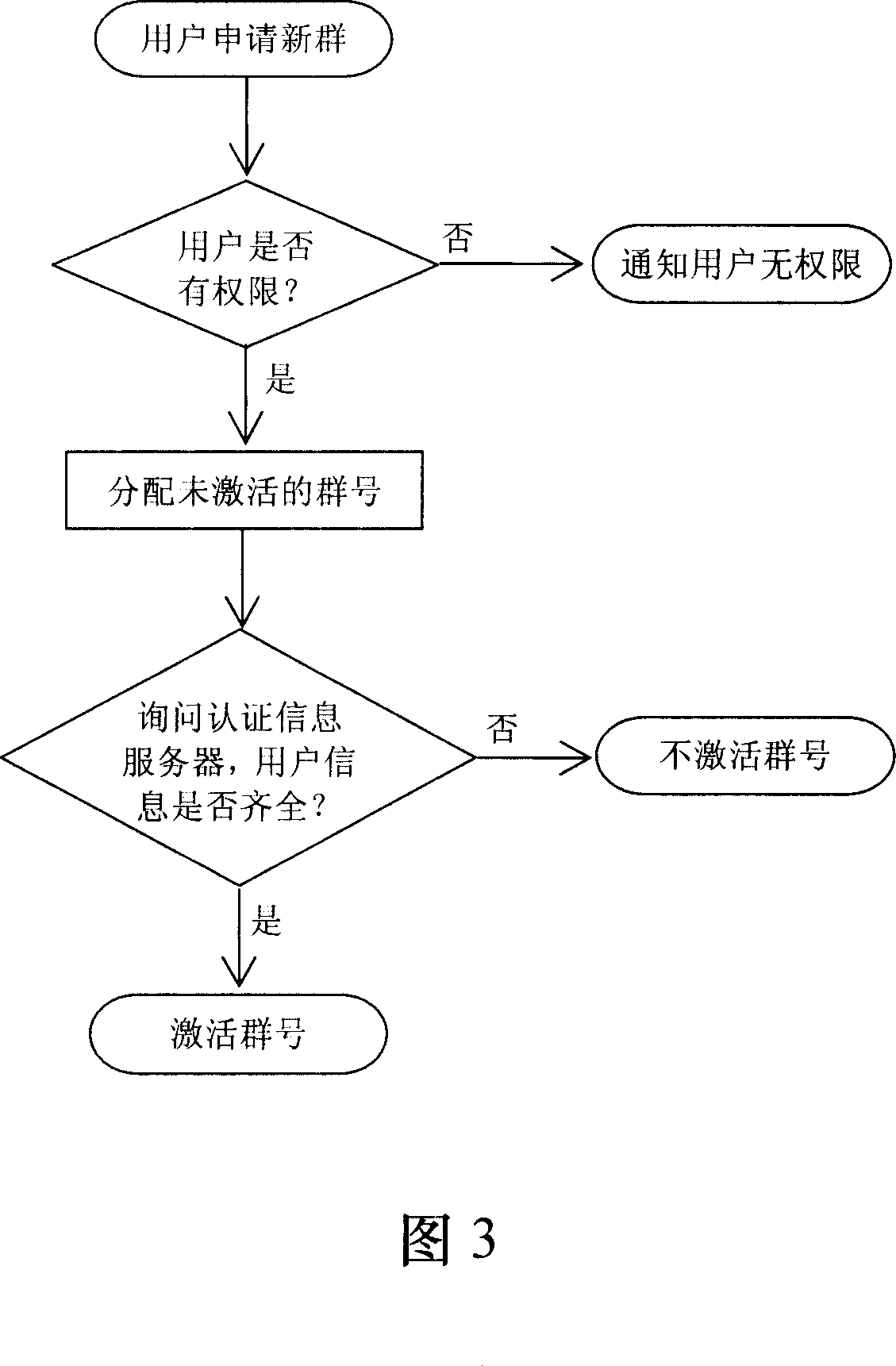
ActiveCN1992591AImplement authenticationEasy to findUser identity/authority verificationRadio/inductive link selection arrangementsVerification systemInstant messaging
A group real-name verification system and method based on the cell-phone bonding and WEB, it can achieve the verification to the IM software group administrator identification. The system includes: the group server, the authentication information server, the logging server, and the cell-phone bonding server. Firstly, the group server verifies the user authority, and allocates an un-activated group number to the competent user, and then, sends the request whether user information is complete to the authentication information server, and the authentication information server verifies the user's information or prompts the user to input information, and verifies whether the group application number of the user bonding the cell-phone or prompts the user to bond the cell-phone. The authentication information server feeds back to the group server the information whether the user information is incomplete, and if fully, the group server activates the group number, otherwise, not activates the group number. Using the system and method in the invention, it can effectively achieve the identification verification of the group's administrator, in favor of finding and restraining the group administrator, to achieve effectively managing the group and network environment.
Owner:TENCENT TECH (SHENZHEN) CO LTD
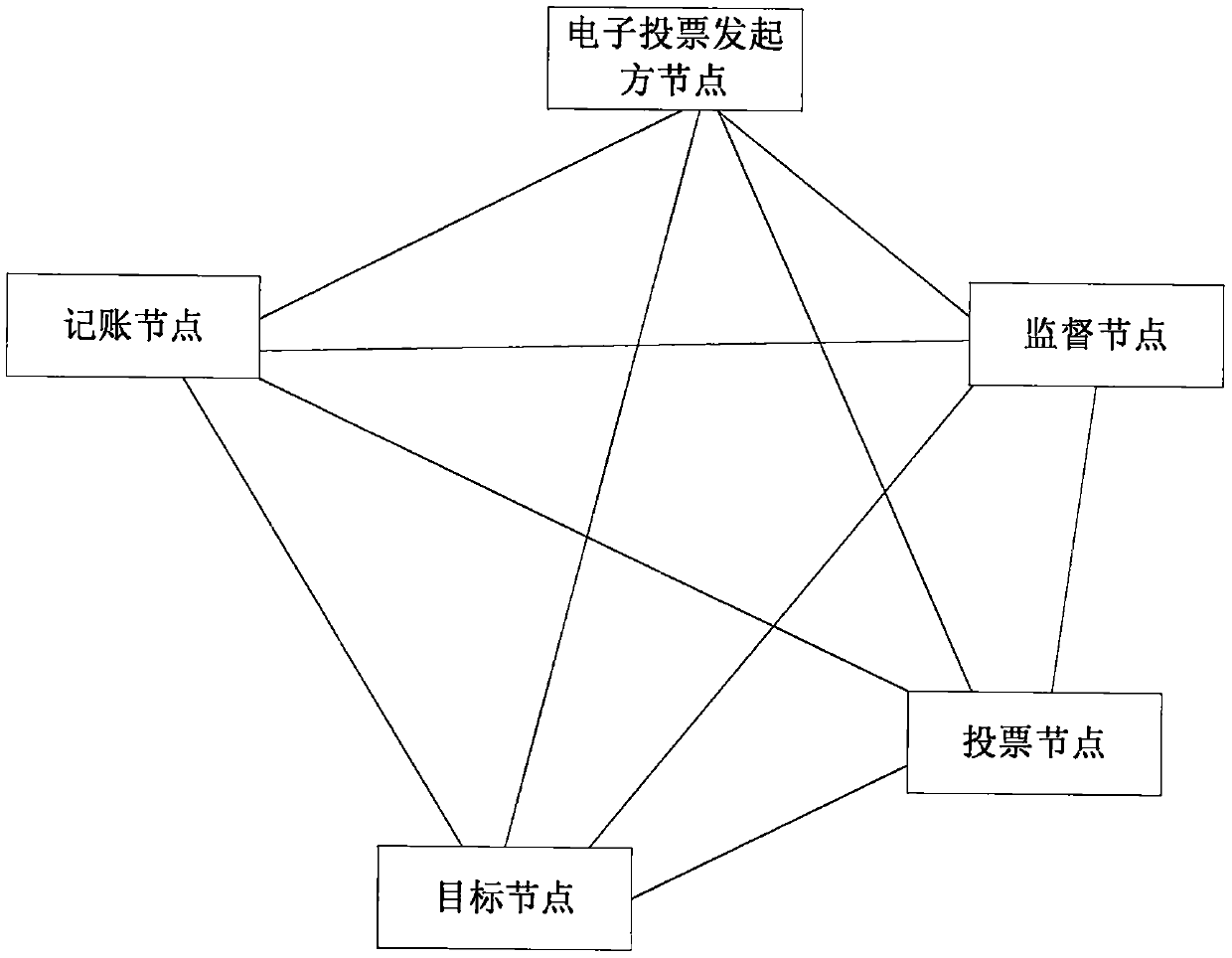
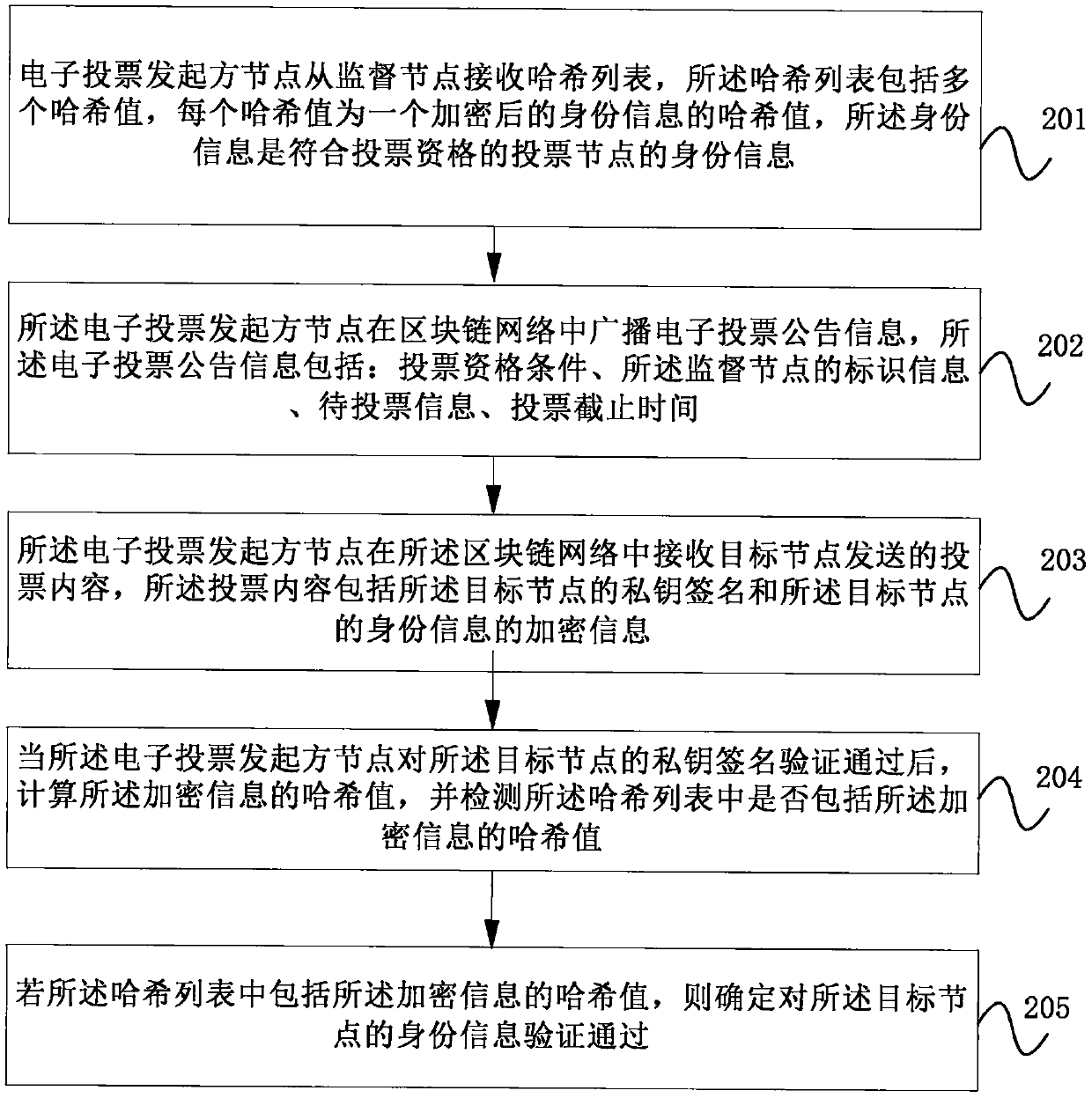
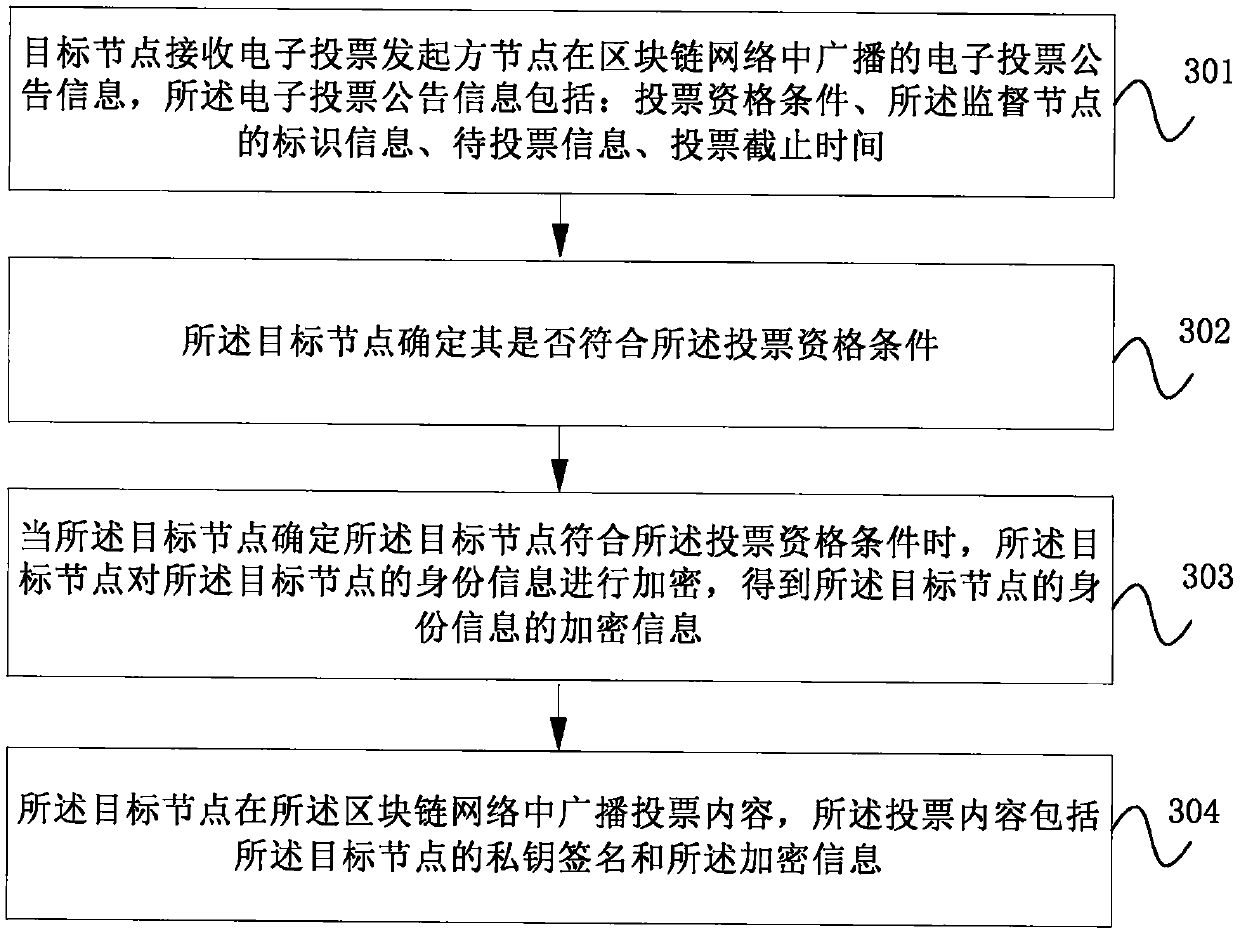
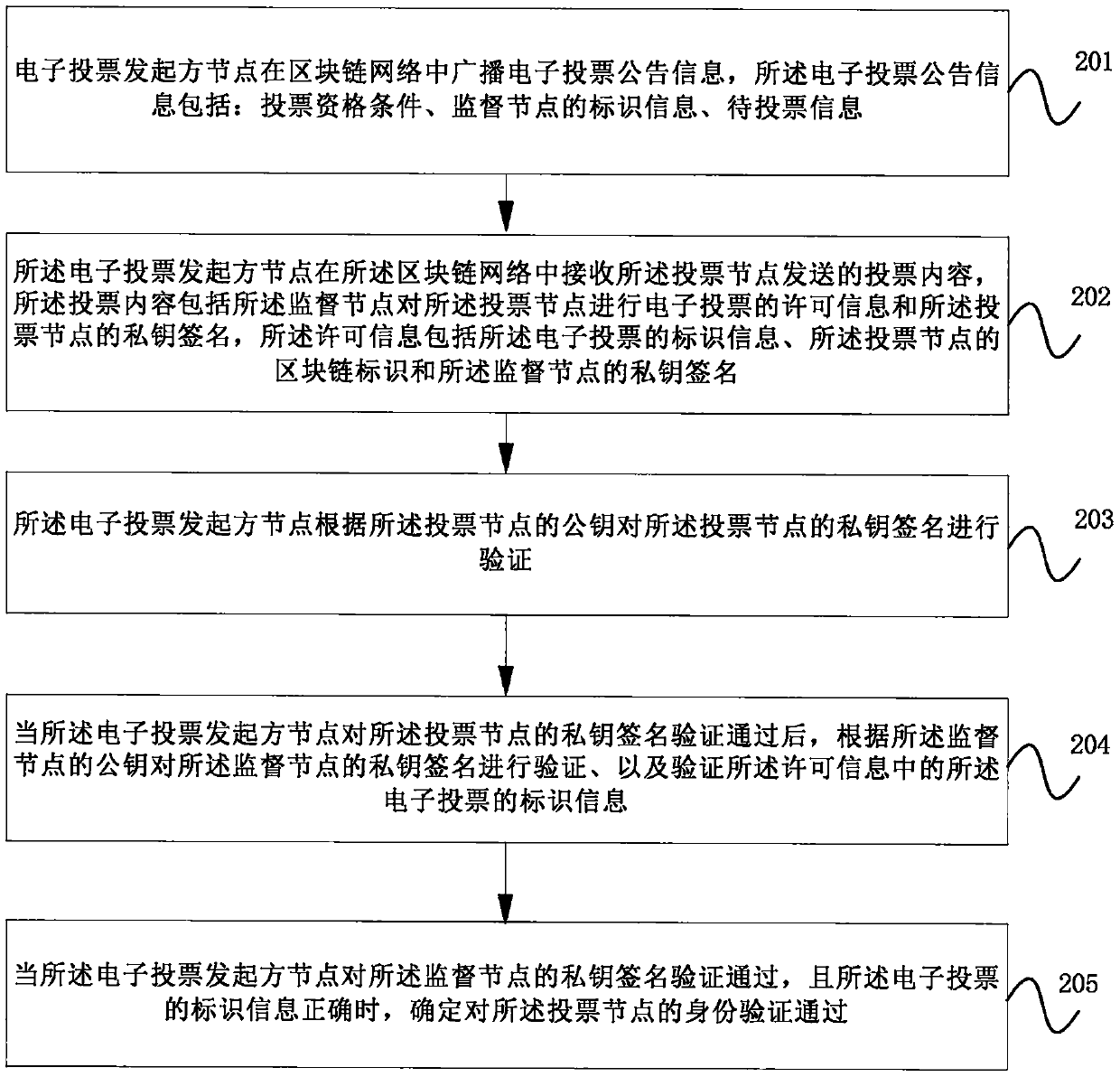
Electronic voting method and device based on block chain and storage medium
InactiveCN111047763AImprove securityImplement authenticationVoting apparatusDigital data protectionBlockchainEngineering
The embodiment of the invention provides an electronic voting method and device based on a block chain and a storage medium. The embodiment of the invention discloses a hash list formed by hash valuesof encrypted identity information in a blockchain network. The identity information is not the encrypted identity information; a voting node needs to disclose encrypted information of own identity information in the blockchain network; the hash value is irreversible; a participation node in the blockchain network can only detect whether a hash value corresponding to encrypted information of identity information is in a hash list or not; the encrypted identity information cannot be determined according to the hash value. According to the invention, the voting content of the voting node is ensured not to be tampered offline, and the voting node is also ensured not to be misrepresented, so that the voting node can vote anonymously, identity verification of the voting node by an electronicvoting initiator node is also realized, and the safety of the voting node and the safety of electronic voting are improved.
Owner:全链通有限公司
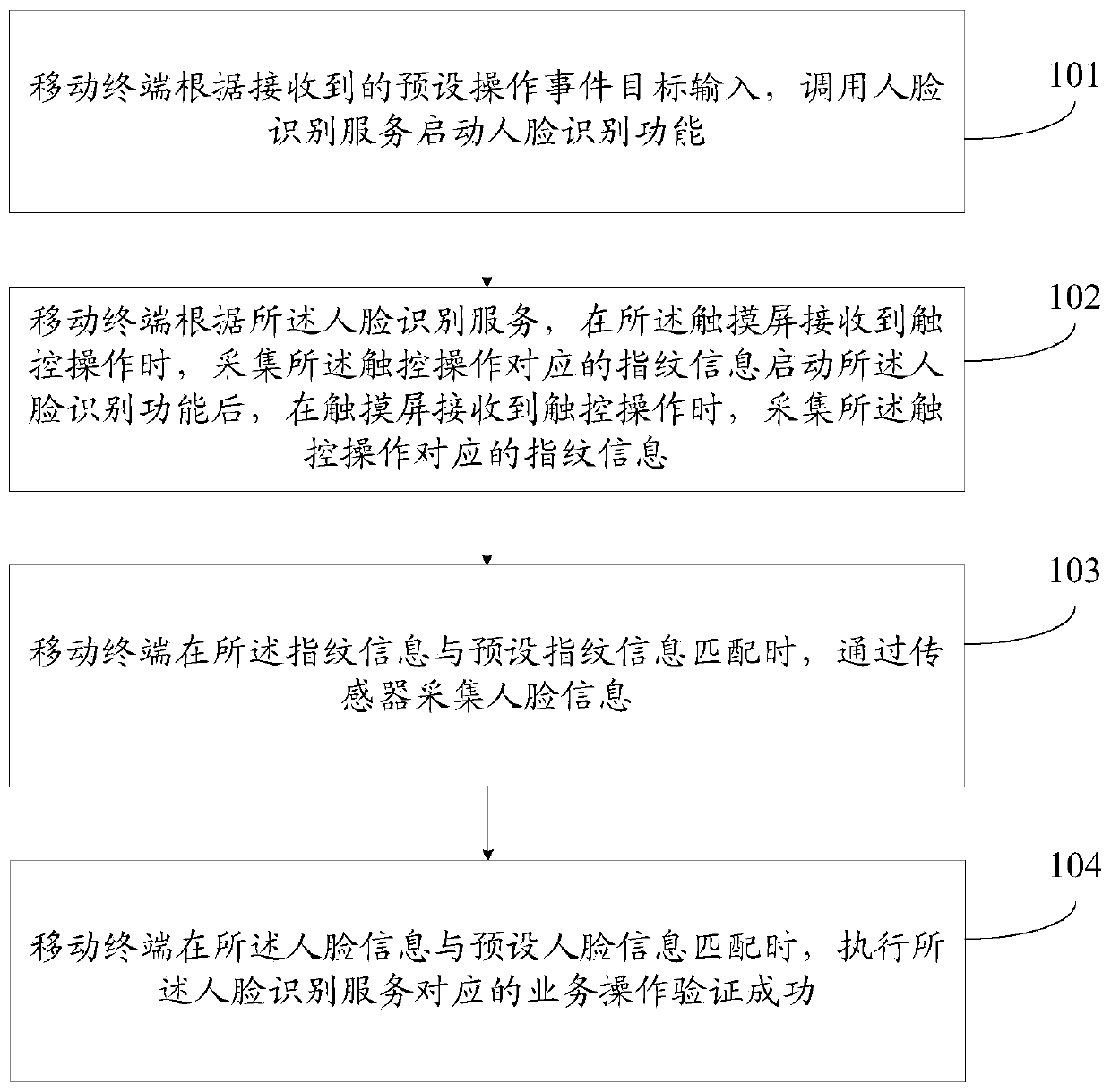
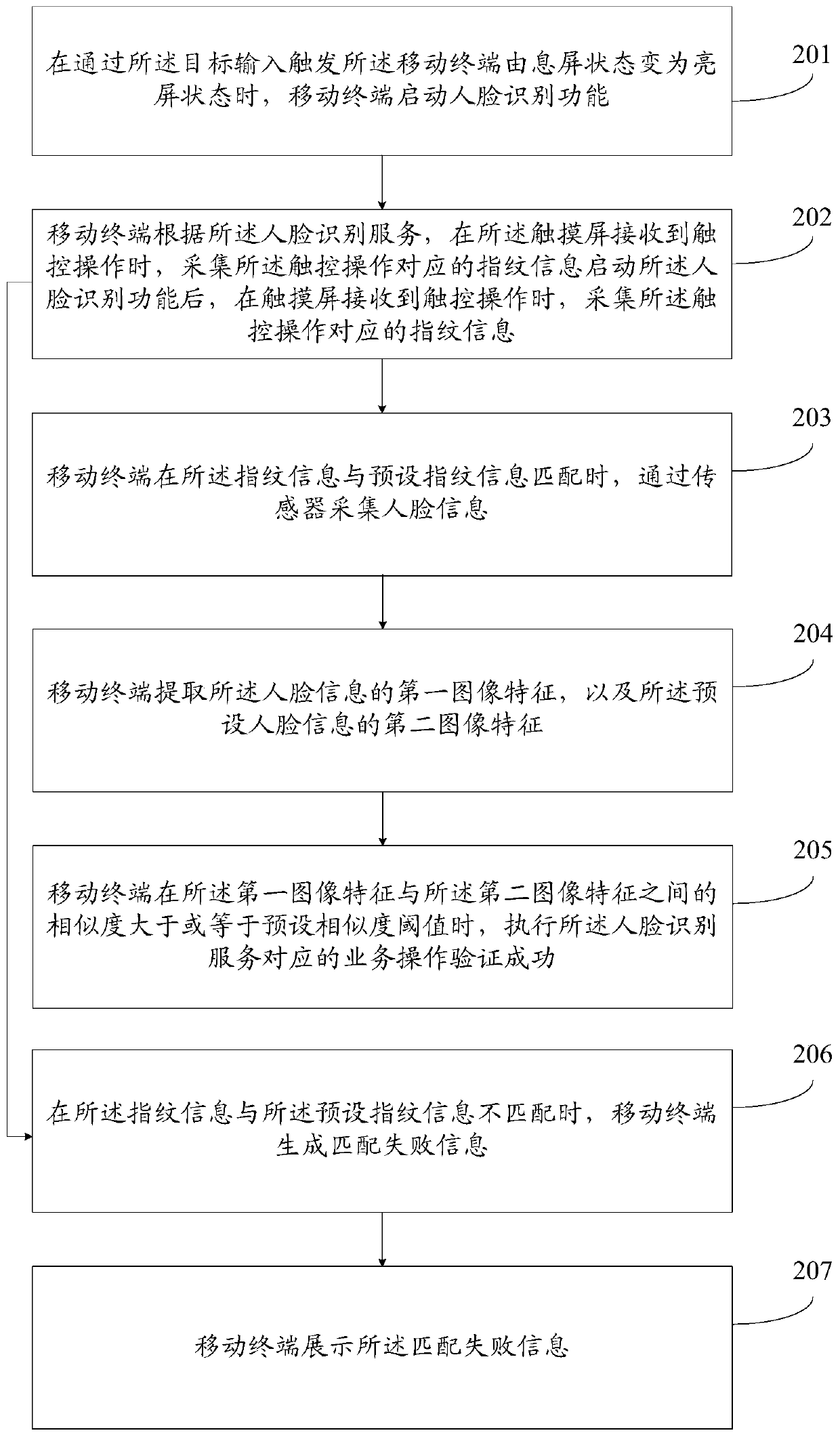
Verification method and mobile terminal
InactiveCN110188523AImplement authenticationImprove securityDigital data authenticationValidation methodsUser privacy
The invention provides a verification method and a mobile terminal, and the method comprises the steps of starting a face recognition function according to a received target input; after the face recognition function is started, when a touch screen receives the touch operation, collecting the fingerprint information corresponding to the touch operation; when the fingerprint information is matchedwith preset fingerprint information, collecting the human face information through a sensor; and when the face information is matched with the preset face information, determining that the verification is successful. According to the invention, before the face recognition operation, whether the finger of an owner is touching on the touch screen or not can be judged through a full-screen fingerprint identification technology, if yes, it is indicated that the mobile terminal is held by the owner instead of other people, so that the face recognition can be started to quickly realize user identityverification, the problem that the mobile terminal of the owner is aligned with the face of the owner to perform face recognition by others is solved, the safety of face recognition operation is improved, and the probability of the leakage of user privacy data is reduced.
Owner:VIVO MOBILE COMM CO LTD
Identity verification method and system
ActiveCN105336020AEasy to losePrevent identity impersonationIndividual entry/exit registersTime limitIdentity theft
The invention provides an identity verification method and system. The method comprises the following steps: acquiring entry and exit information; examining and verifying the entry and exit information; generating a time-limited two-dimension code after the entry and exit information passes examination and verification; determining a verification message; sending the verification message to a receiving terminal; receiving the time-limited two-dimension code send by a person coming in or going out; verifying whether the identity of the person coming in or going out is valid according to identity identification included in the time-limited two-dimension code so as to obtain a first verification result; verifying whether the received two-dimension code is valid according to entry time and departure time included in the time-limited two-dimension code so as to obtain a second verification result; and determining the identity verification results of the person coming in or going out according to the first verification result and the second verification result. The identity verification method and system provided by the invention prevent identity theft caused by loss or theft of verification information of clients; and the valid time of the time-limited two-dimension code is so precise that the code can only be used once, so fine-grained identity verification based on frequency and time is realized.
Owner:CHINA MOBILE GRP HEILONGJIANG CO LTD
Electronic voting method and device based on block chain and storage medium
ActiveCN110933098AImprove securityImplement authenticationSpecial service provision for substationUser identity/authority verificationInternet privacyEngineering
Owner:全链通有限公司
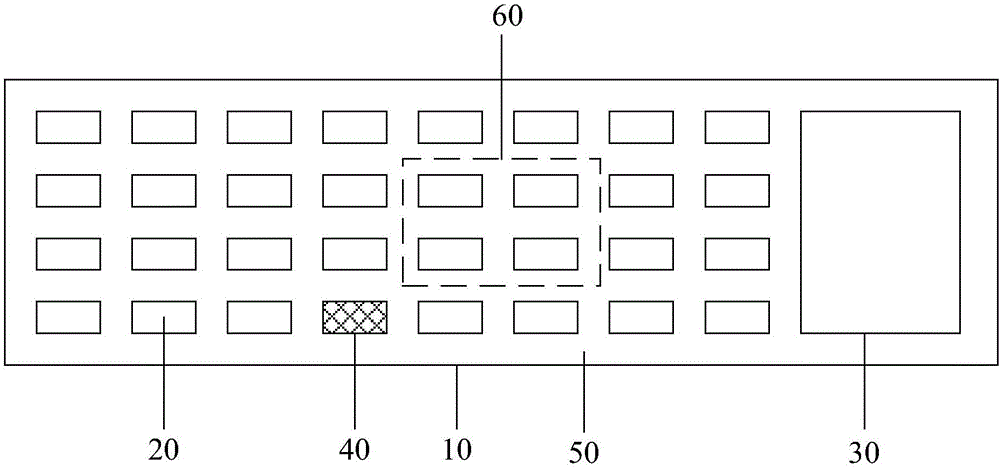
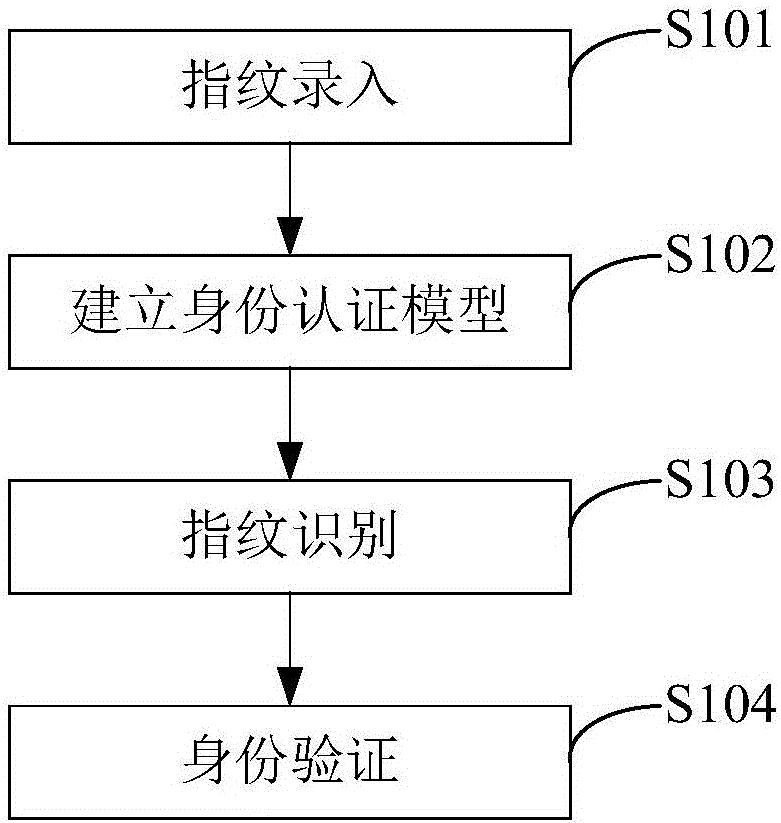
Identity recognition keyboard and method of performing identity authentication according to identity recognition keyboard
ActiveCN106529354AImplement authenticationEasy to useInternal/peripheral component protectionDigital data authenticationRadianData acquisition unit
The invention discloses an identity recognition keyboard and a method of performing identity authentication according to the identity recognition keyboard. A fingerprint recognition area is used for inputting fingerprints of a user to generate an intact fingerprint image of all fingers; a blue light induction plate is used for collecting palm information, wherein the palm information comprises basic radians and fingering of both hands working on keys; a data acquisition unit for collecting key information is arranged on each key, wherein the key information comprises the fingerprints of the fingers tapping the keys, keying strength and stay time; a learning unit performs training and learning on the palm information and the key information, and an identity authentication model for the user tapping the keyboard is established in combination with the intact fingerprint image. By arranging the fingerprint recognition area, the blue light induction plate and the data acquisition units on the keyboard, input and matching of the fingerprints of the user are realized; according to the input fingerprints of the user, encryption of a computer can be realized through the keyboard, and only when the fingerprints of the user tap the keyboard can opening of a computer coded lock, normal use of the keyboard and identity authentication of the user be realized.
Owner:BEIJING UNIV OF TECH
Fingerprint processing method and device and storage medium
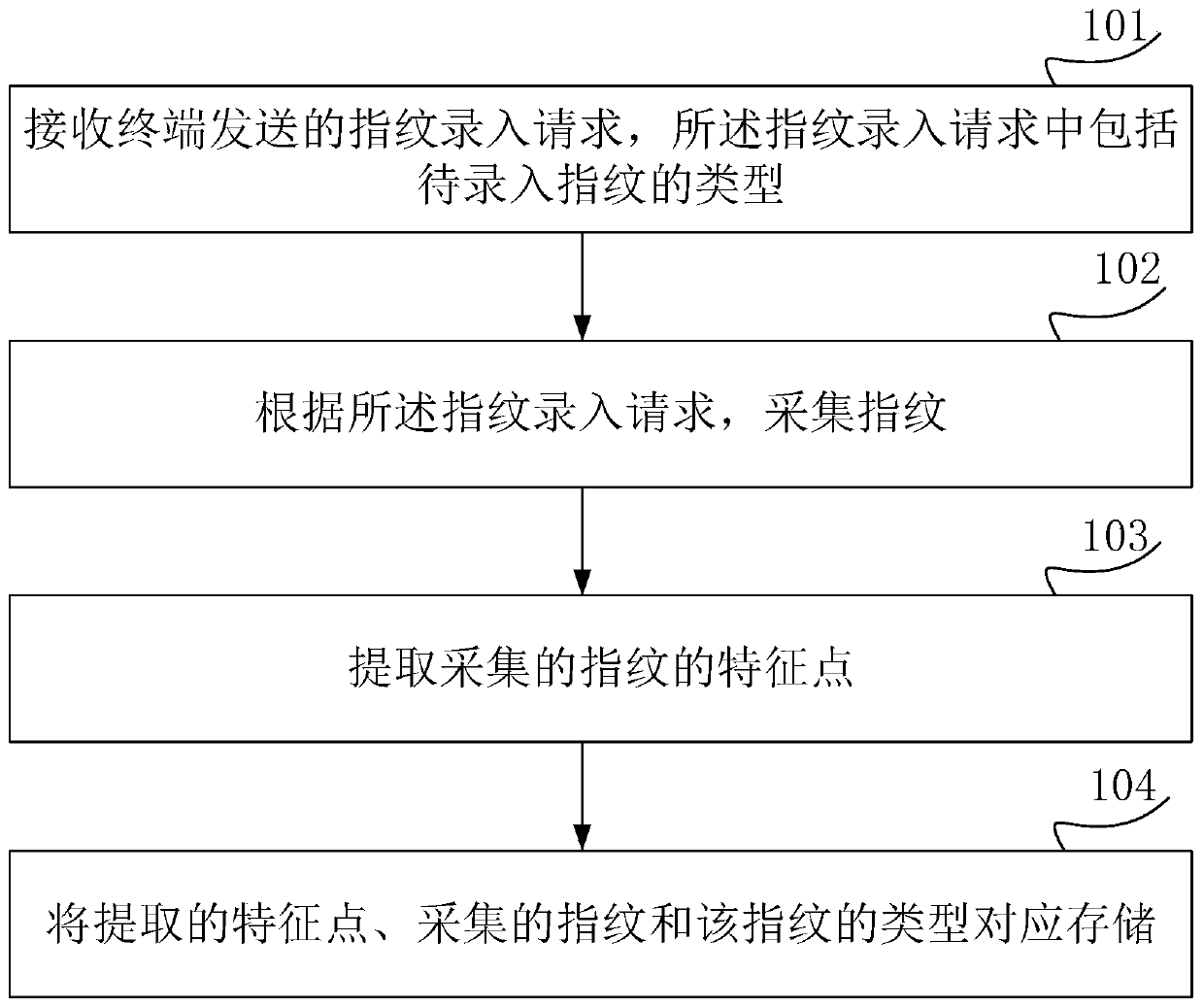
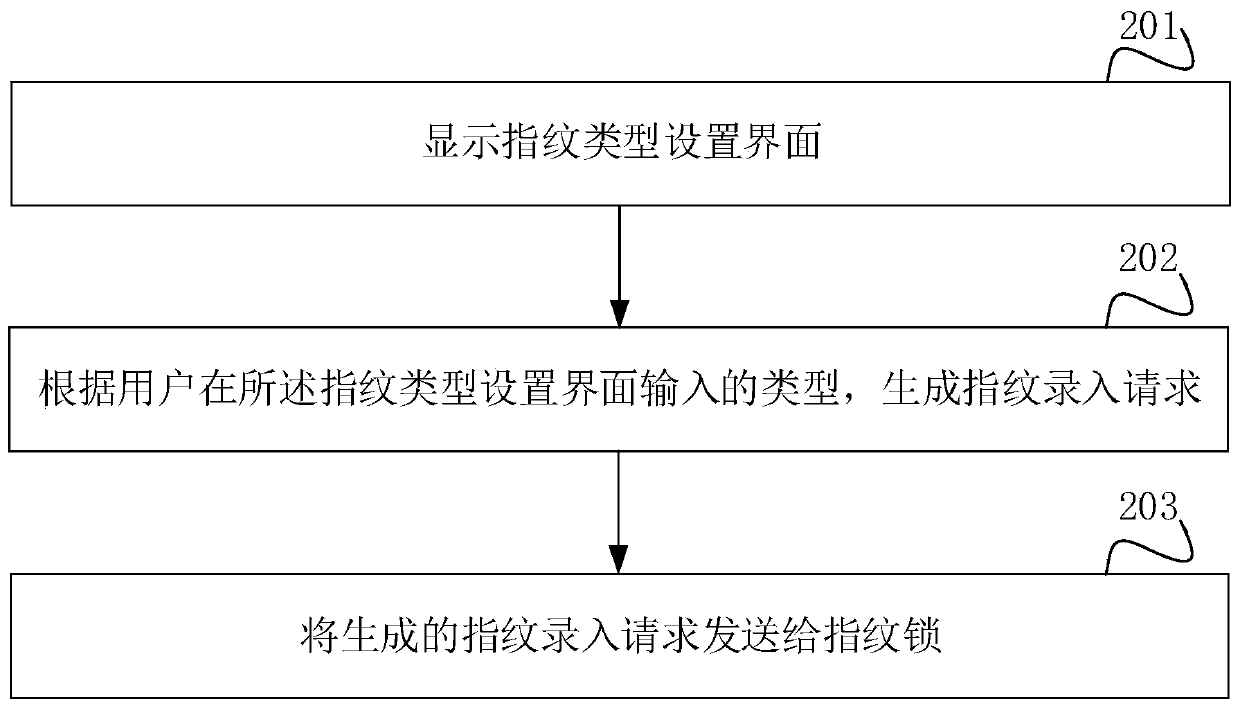
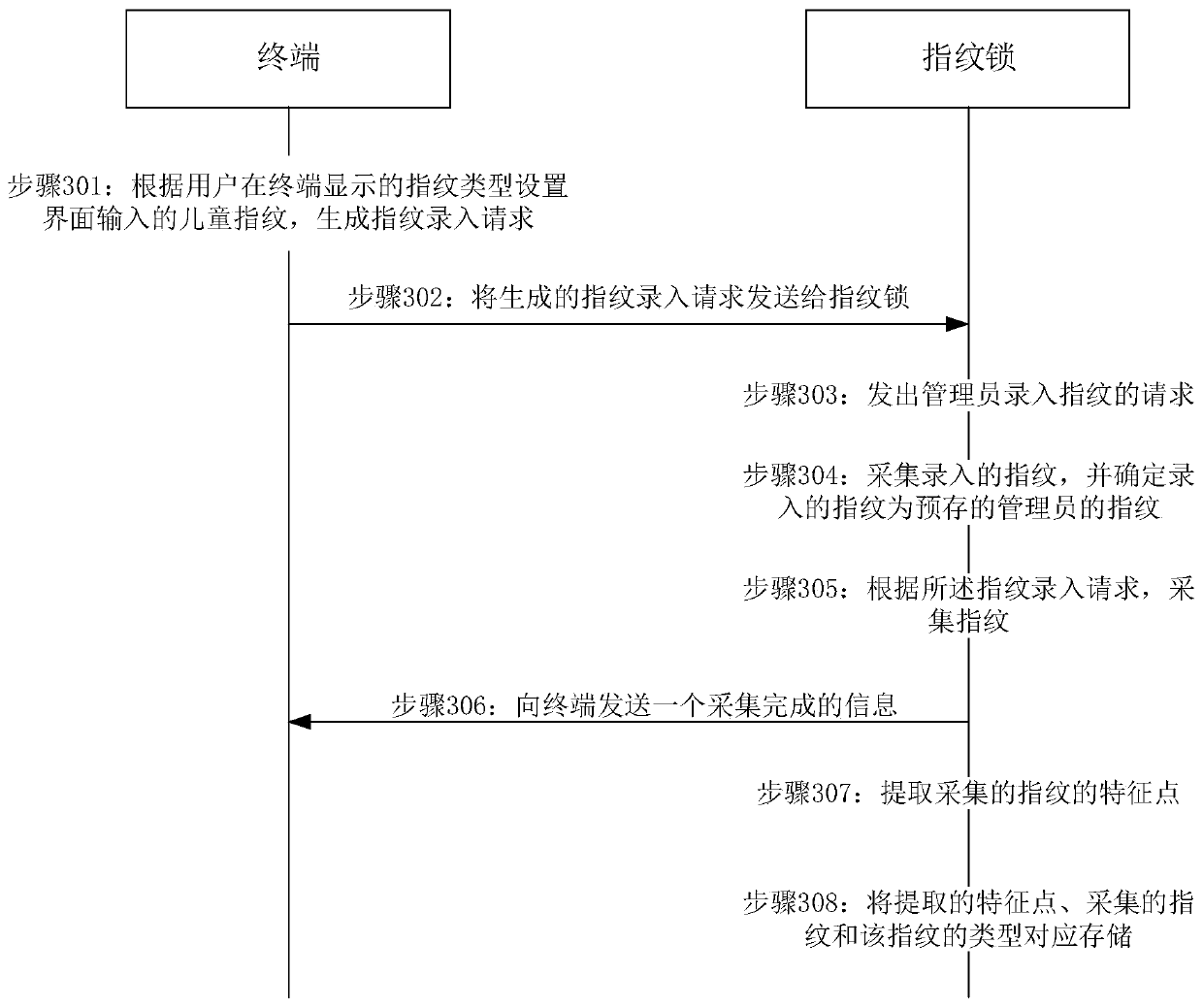
InactiveCN109948316AImplement authenticationImplement classificationCharacter and pattern recognitionDigital data authenticationFingerprintPattern recognition
The invention discloses a fingerprint processing method and device and a storage medium, relates to the field of fingerprint processing, and is used for solving the problem that fingerprints of children (such as children aged five years or less) with unshaped fingerprints are difficult to identify by a fingerprint lock on the market at present. The method comprises the following steps: acquiring auser fingerprint, and extracting respective widths of a ridge and a valley in the user fingerprint; Determining the type of the fingerprint of the user according to the respective widths of the ridgeand the valley; If it is determined that the type of the user fingerprint is an adult fingerprint, performing identity verification by adopting a fingerprint verification method corresponding to theadult fingerprint; And if it is determined that the type of the user fingerprint is the child fingerprint, performing identity verification by adopting a fingerprint verification method correspondingto the child fingerprint. Thus, classification of adult fingerprints and child fingerprints is achieved through the width of the ridge and the width of the valley in the fingerprints of the user, andidentity verification of the child fingerprints is achieved.
Owner:GREE ELECTRIC APPLIANCES INC OF ZHUHAI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com