Identity recognition keyboard and method of performing identity authentication according to identity recognition keyboard
A technology of identity recognition and identity verification, applied in the field of identity verification, which can solve problems such as low security, fuzzy memory of passwords, data acquisition and theft, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
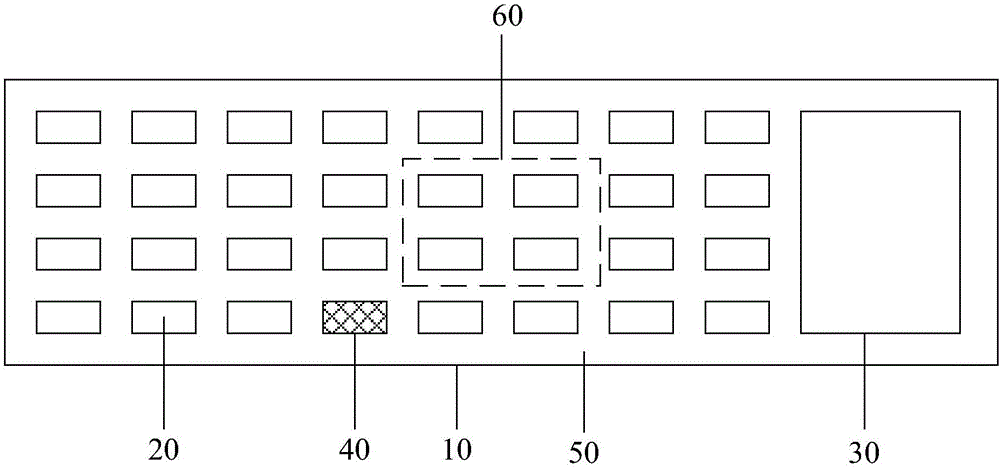
[0041] Embodiment 1: as Figure 1-2 As shown, the invention provides an identification keyboard, including a keyboard body 10 and a plurality of keys 20 arranged on the keyboard body 10 (its structure is a commonly used keyboard structure), and also includes a fingerprint identification area 30 arranged on the keyboard body 10 , the blue light sensing board 50 and the learning unit 60 arranged in the keyboard main body 10;
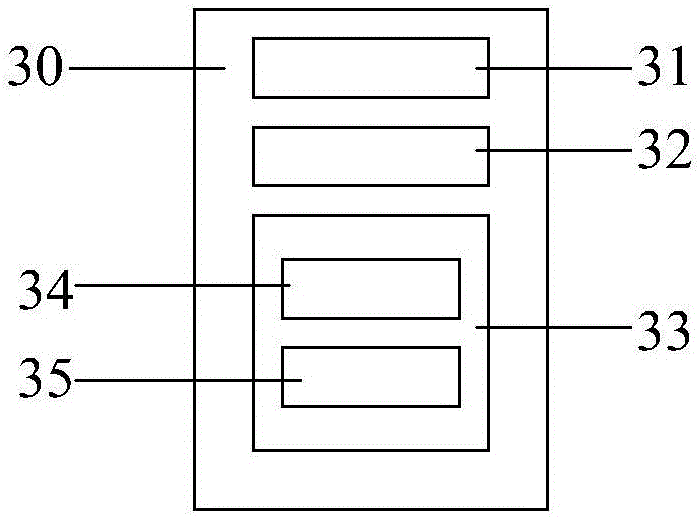
[0042] Fingerprint identification area 30 is used for entering user's fingerprint, generates the complete fingerprint image of each finger; Wherein: fingerprint identification area 30 comprises LED light source 31, fingerprint collection lens 32 and image processor 33; Each finger of the user is photographed and collected at least three times to generate at least three fingerprint images, and the generated at least three fingerprint images are transmitted to the image processor 33; the image processor 33 includes a preprocessing unit 34 and a synthesis uni...
Embodiment 2
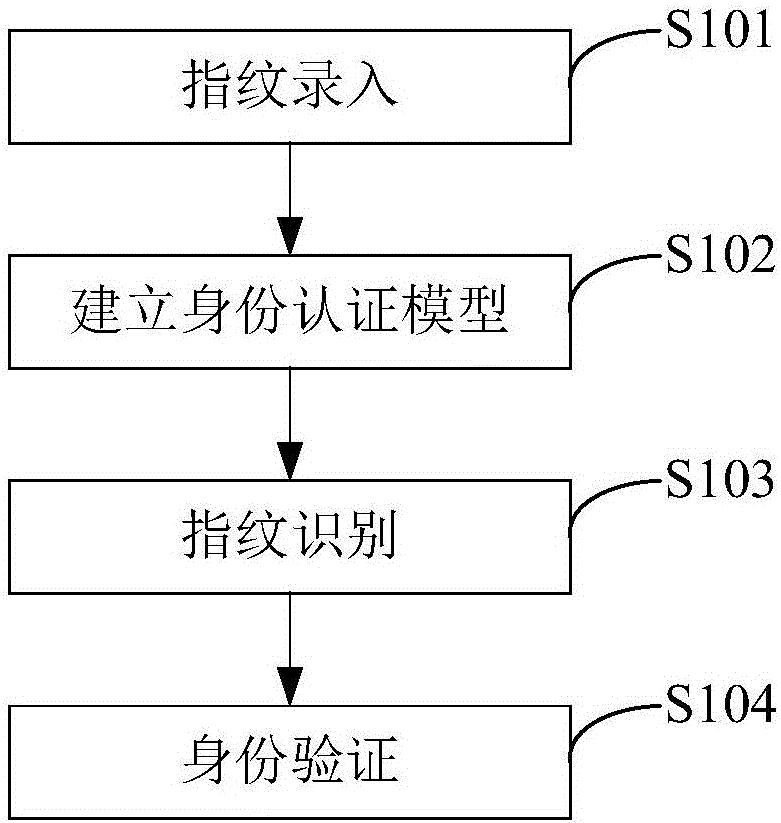
[0048] Embodiment 2: The present invention provides a method for identity verification based on an identity recognition keyboard, including:
[0049] S101. Fingerprint entry: enter the user's fingerprint in the fingerprint identification area, generate and store a complete fingerprint image of each finger; where:
[0050] Step 11, taking pictures of each finger of the user at least three times to generate at least three fingerprint images;
[0051] Step 12, preprocessing the generated fingerprint images respectively, the preprocessing includes removing water marks and sweat stains from the fingerprint image;
[0052] Step 13, vertically project the preprocessed fingerprint image according to the same direction as the pixel points of the core and the pixels around the core, and slightly shift the fingerprint image so that the pixels of the core of the preprocessed fingerprint image are accurate coincide to generate a complete fingerprint image for that finger.
[0053] S102. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com