Access control device and verification method thereof, verification device and verification method thereof, verification system and verification method thereof
The technology of a verification device and verification method is applied in transmission systems, digital transmission systems, safety communication devices, etc., and can solve problems such as illegal pass verification of access control cards
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
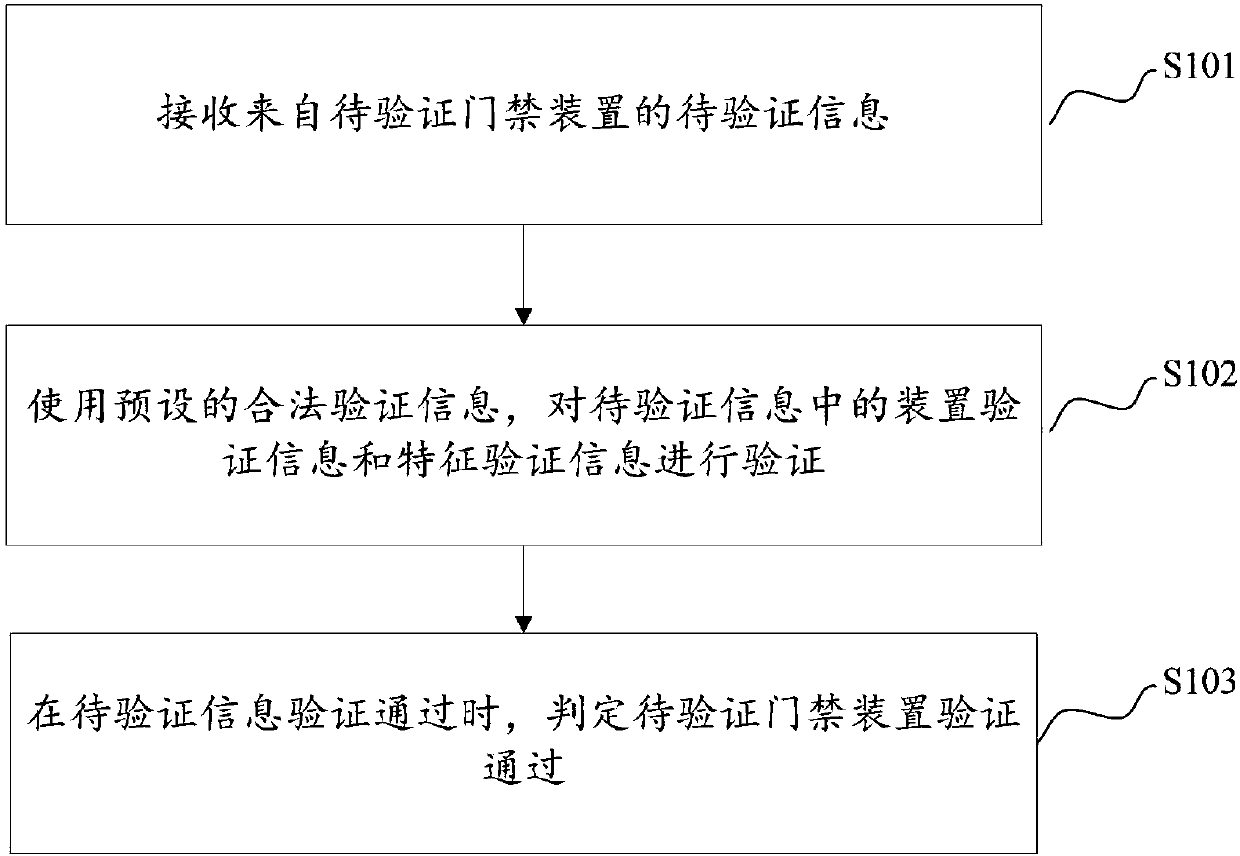
[0058] figure 1 The basic flow chart of the access control verification device verification method provided in this embodiment, the method includes:
[0059] S101. Receive information to be verified from an access control device to be verified.
[0060] In this embodiment, the information to be verified here includes the device verification information of the access control device to be verified and the feature verification information of the user of the access control device to be verified. In the actual application process, the device verification information can be a unique sequence in the device SN, and the feature verification information can be biometric features such as fingerprint features, vein features, and palmprint features, which can uniquely determine the user of the access control device.
[0061] In some other examples of this embodiment, before the step S101, it further includes sending the random factor to the access control device, and pre-storing the sent ...
no. 2 example
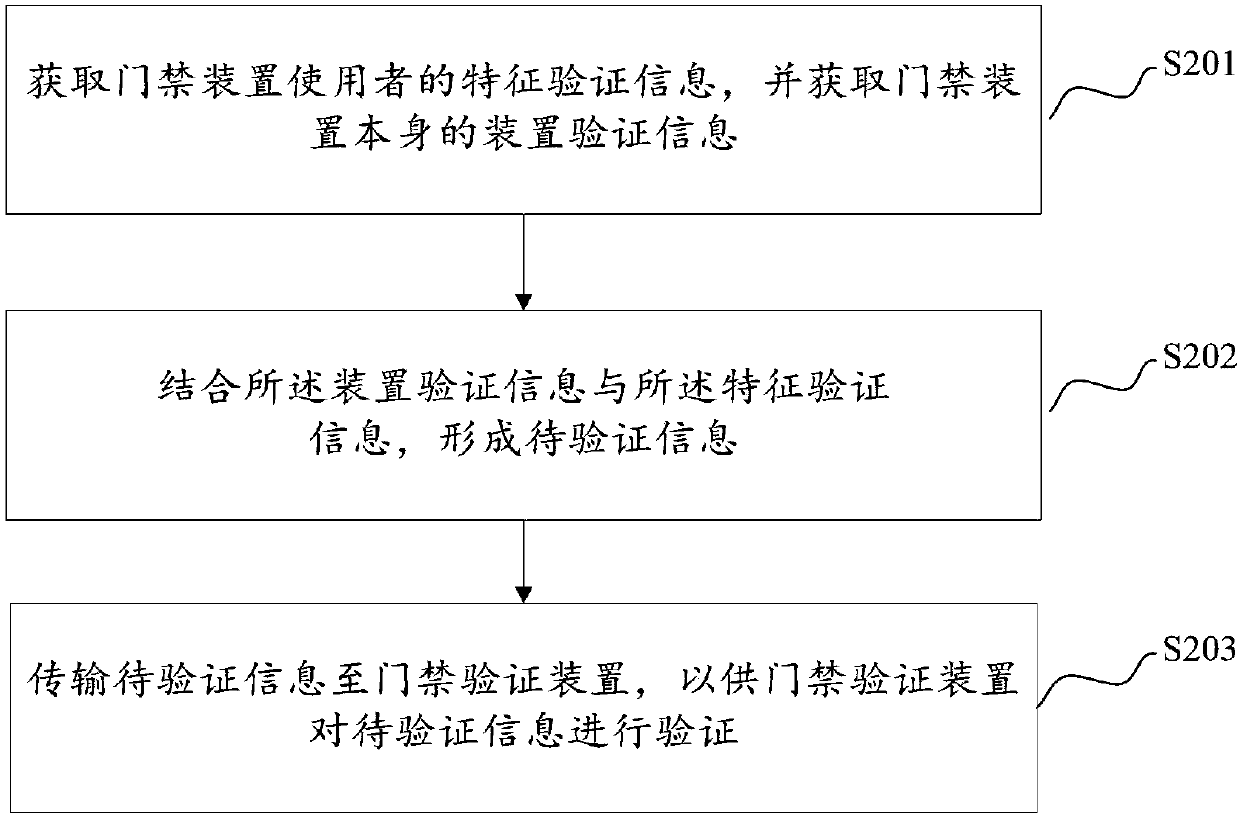
[0070] figure 2 The basic flow chart of the access control device verification method provided in this embodiment, the method includes:
[0071] S201. Obtain feature verification information of a user of the access control device, and obtain device verification information of the access control device itself.
[0072] In the actual application process, the access control device is in the use state, that is, when the verification is performed, the device verification information and feature verification information in the access control device itself is obtained. Swipe a card, or use an access control module such as a car key to trigger verification. In this embodiment, the obtained device verification information is such as the unique serial number SN in the device, and the obtained feature verification information is to collect the feature verification information of the user of the access control device. The feature information can be fingerprint features, vein features, p...
no. 3 example
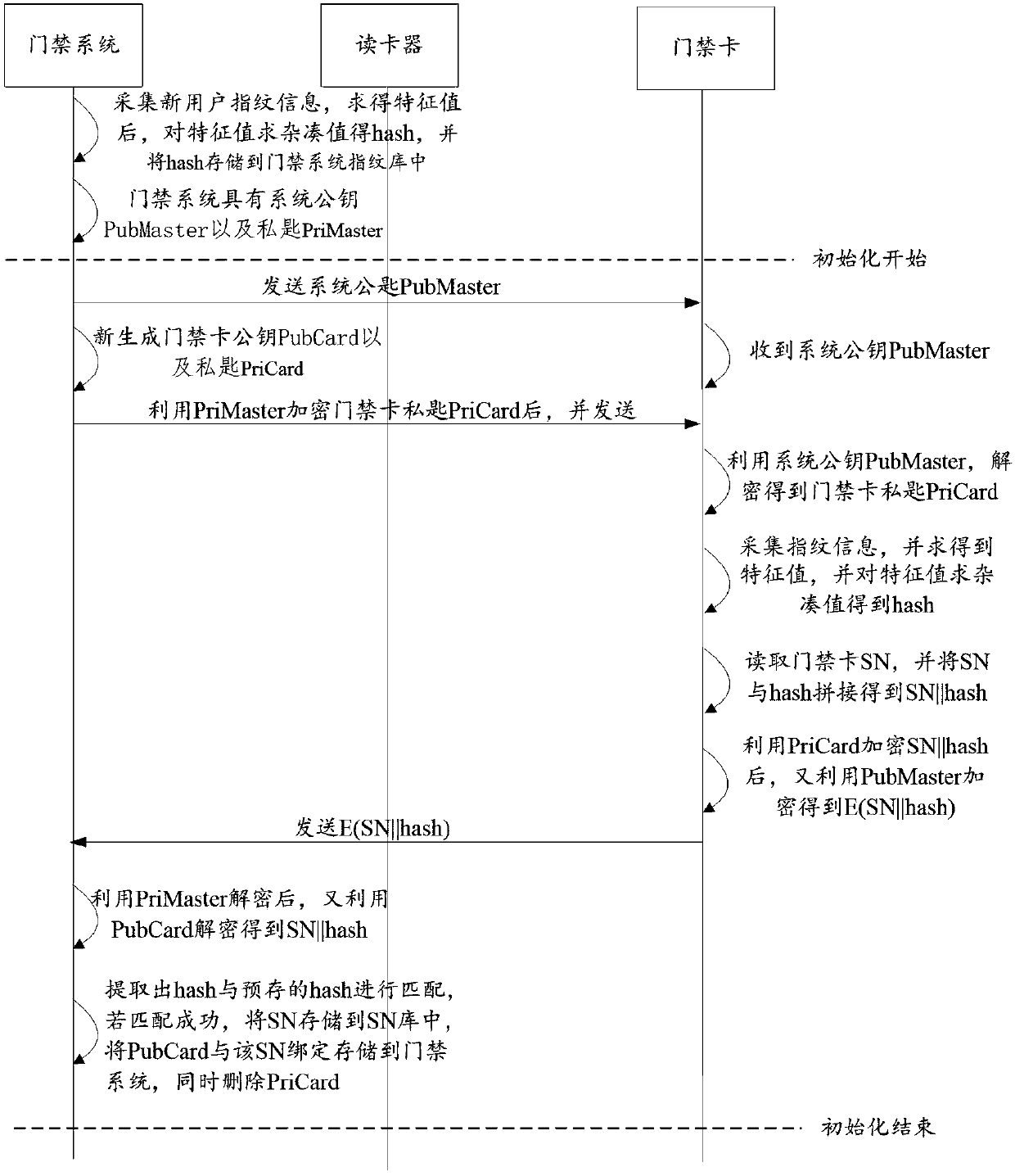
[0080] This embodiment will introduce the access control verification device verification method and the access control device verification method in the present invention according to specific community access control application scenarios, and the application scenarios should not be construed as limitations on the present invention. Specifically in the present embodiment, the access control verification device specifically refers to the access control card reader, and the access control device refers to the access control card. fingerprints are collected. At the same time, this embodiment also includes an access control system, which communicates with the access control card through a card reader. The access control system pre-stores an SN database, a public key database corresponding to the SN, and a fingerprint feature information database.
[0081] It is understandable that in the actual application process, before the access control card is used, the access control card ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com