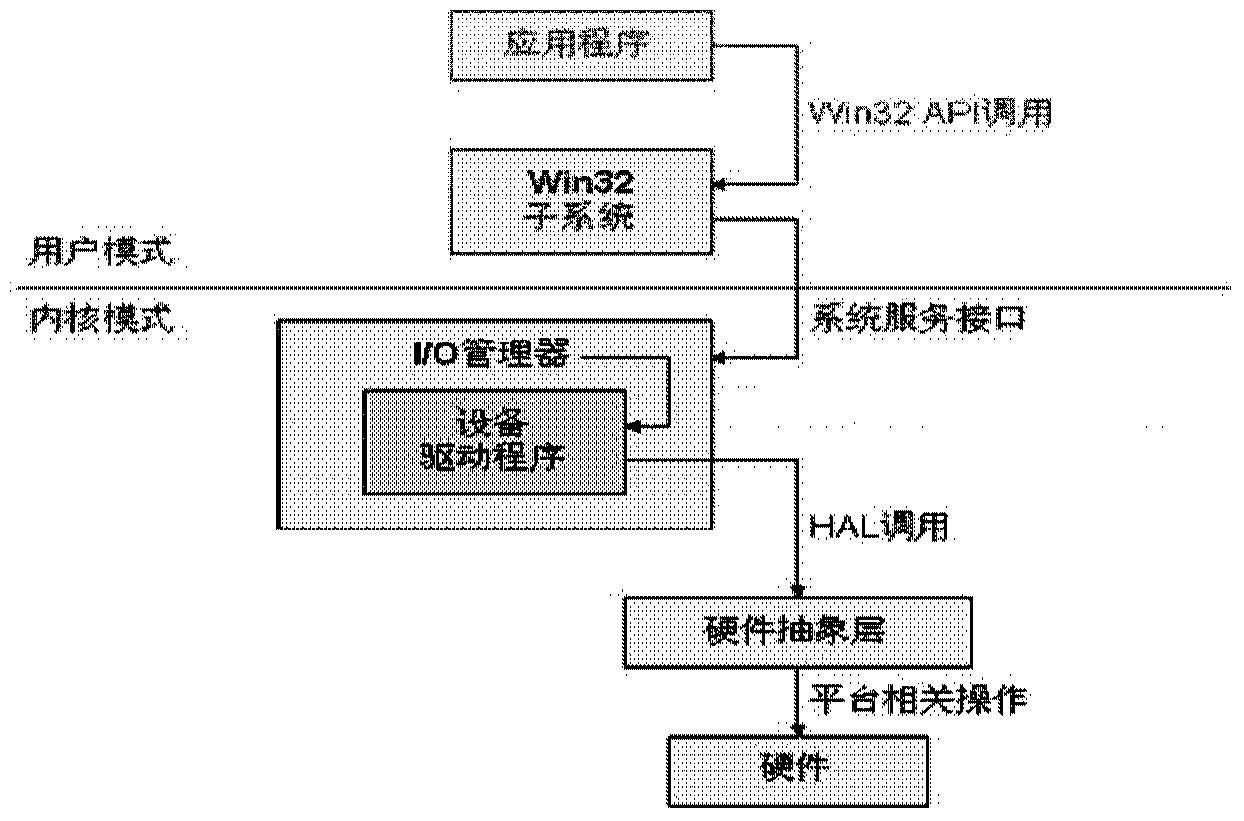
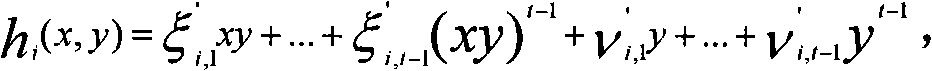Patents
Literature
59results about How to "Achieve legitimacy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
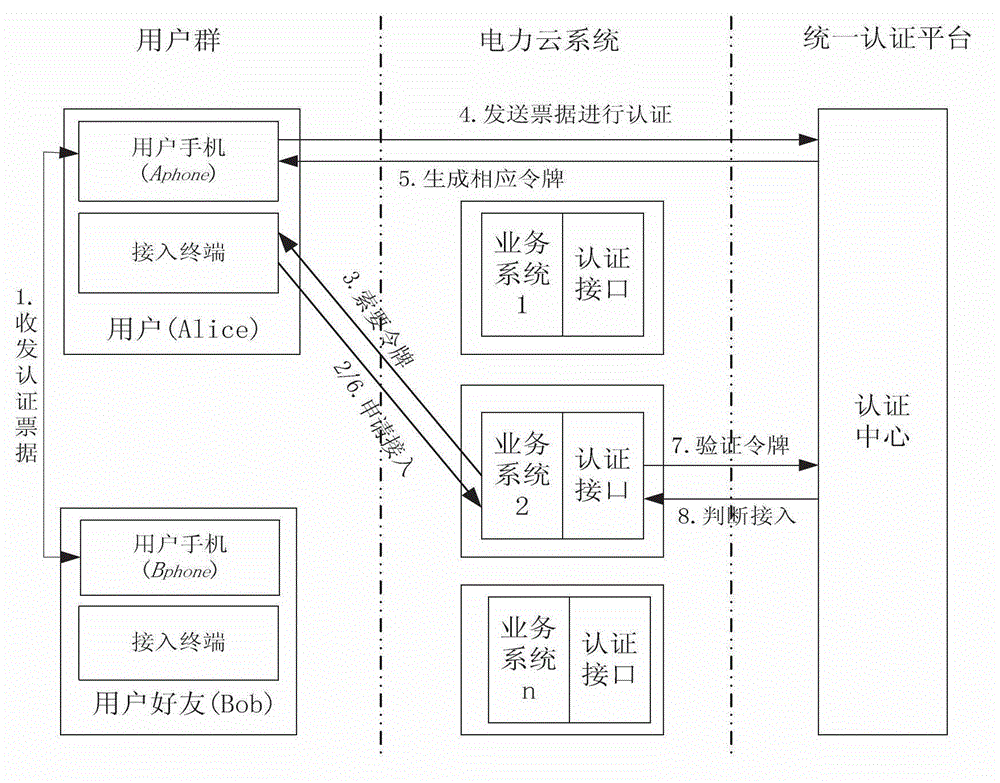
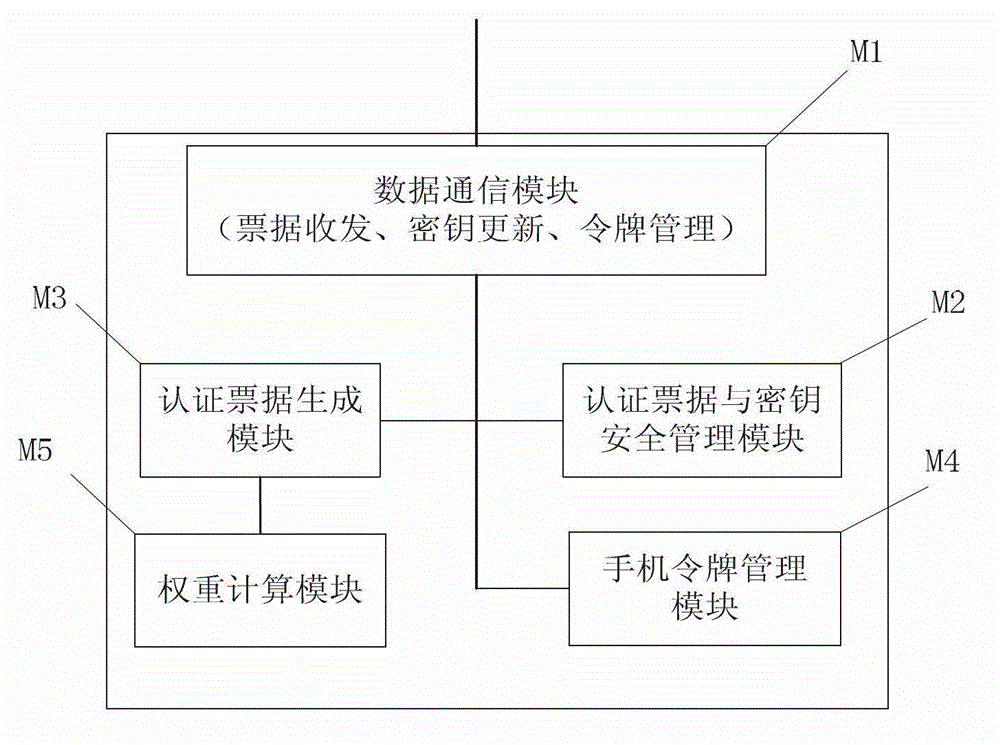
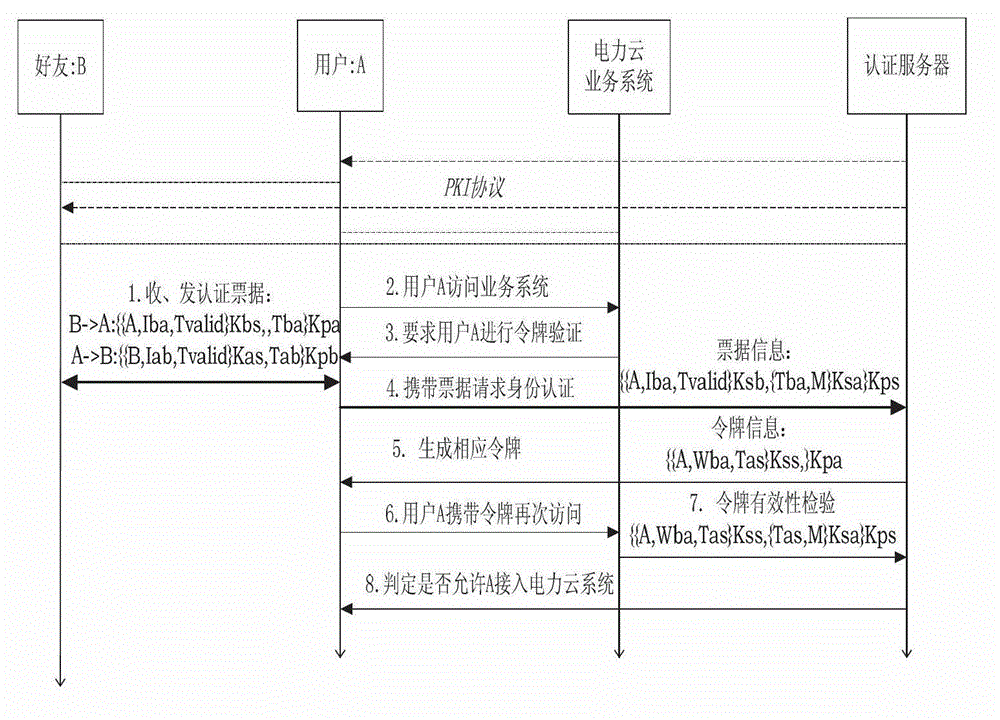
Uniform identity authentication method based on social characteristics in power cloud system
InactiveCN102946603AAchieve legitimacyEasy to operateSecurity arrangementHigh level techniquesElectric power systemInternet privacy
The invention discloses a uniform identity authentication mechanism in a power cloud, and relates to a user identity authentication mode of a network terminal. The purpose of authenticating user identity is achieved by transmitting trust between a user and a friend by utilizing the social characteristics of a mobile phone of the user. The mapping relation between a user name and the mobile phone of the user is created, so that when the user uses other terminals to access a business system, the legality of the user identity is authenticated by utilizing the bills of the mobile phone, and the user performs related operations on different business systems of the power cloud in the permission scope by utilizing a grade token issued by an authentication center. The running efficiency of the power cloud is effectively enhanced, the user experience of the user is improved, the stability and the reliability of the business system are enhanced, and the complexity of maintenance is reduced at the same time. Therefore, the uniform identity authentication mechanism can be widely applied to power systems and related fields.
Owner:STATE GRID CHONGQING ELECTRIC POWER
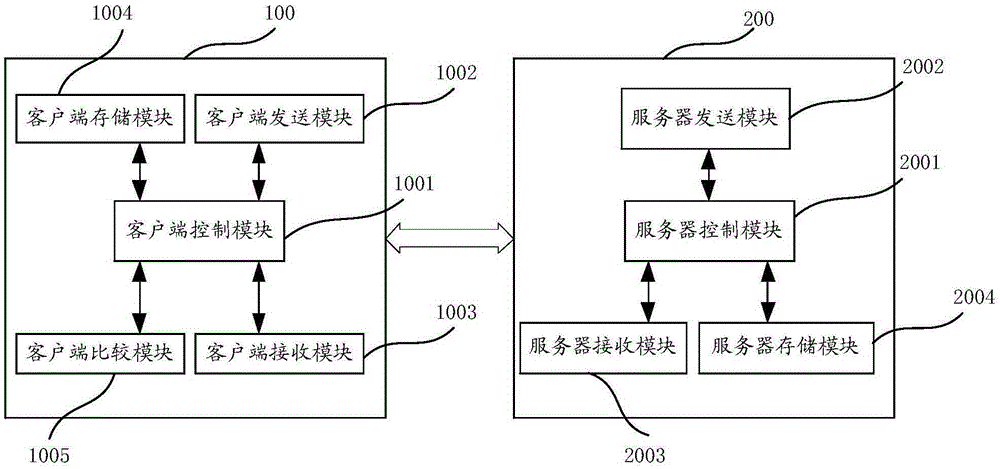
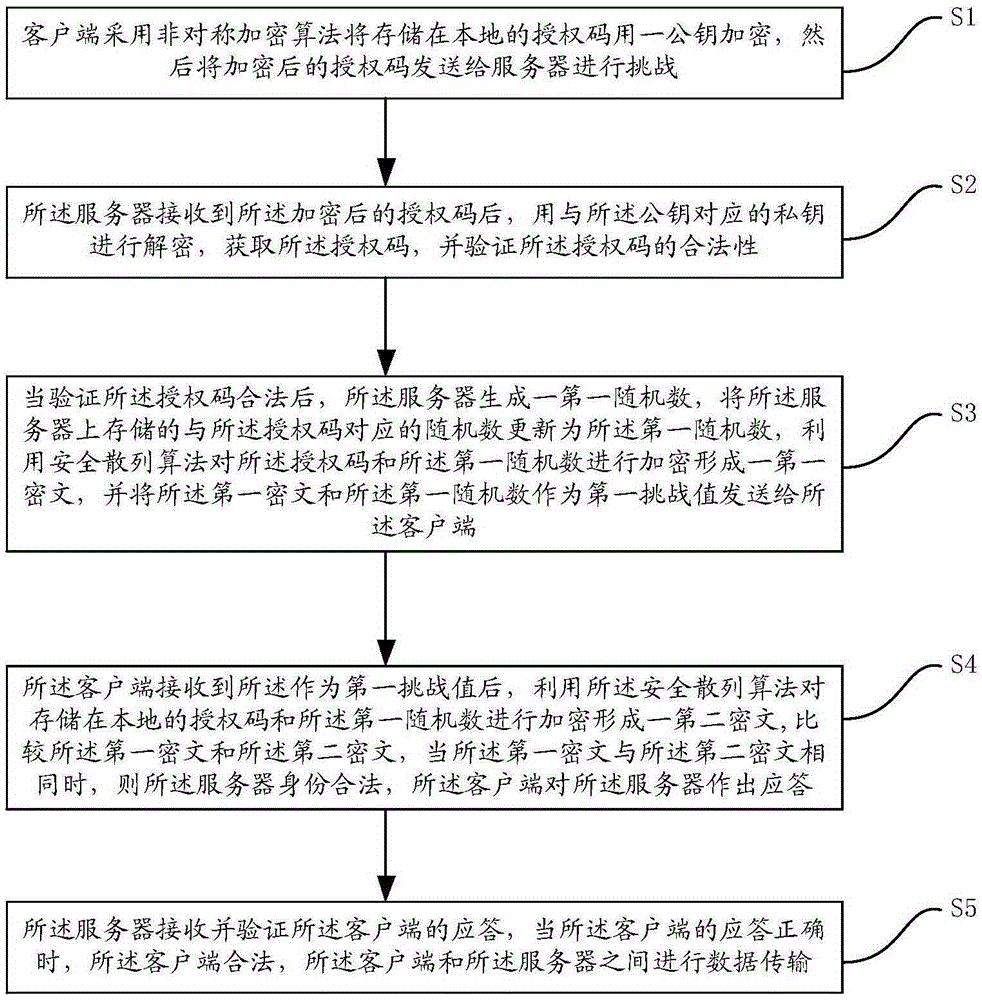
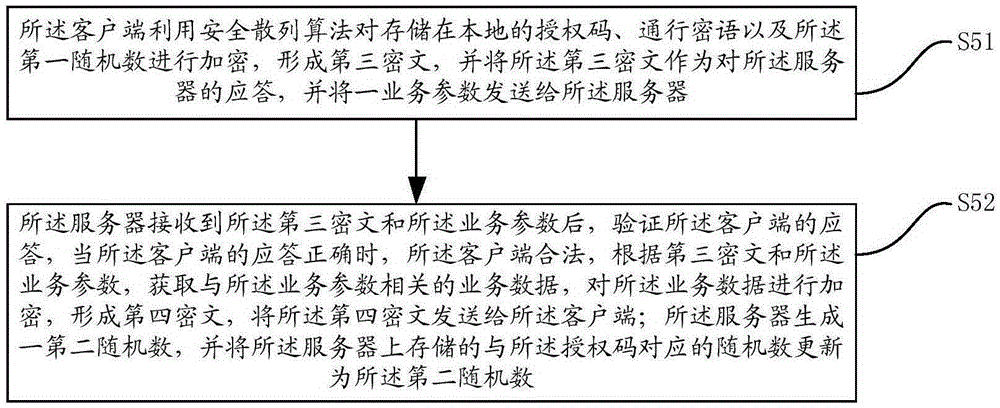
Data interaction method and data interaction device based on CHAP protocol
ActiveCN105282168AAchieve legitimacyImplement authenticationUser identity/authority verificationInteraction deviceClient-side
The invention provides a data interaction method and a data interaction device based on the CHAP protocol. The data interaction device based on the CHAP protocol comprises a client and a server. The client and the server carry out data interaction after identity authentication succeeds. The legitimacy of the client and the server is verified using a first random number, an asymmetric encryption algorithm and a secure hash algorithm, and therefore, identity authentication between the client and the server is realized, and attack from the middleman is avoided. Data transmission is carried out between the client and the server after identity authentication succeeds, so that the safety and reliability of data transmission between the client and the server are ensured, and replay attack is avoided.
Owner:SHENGQU INFORMATION TECH SHANGHAI
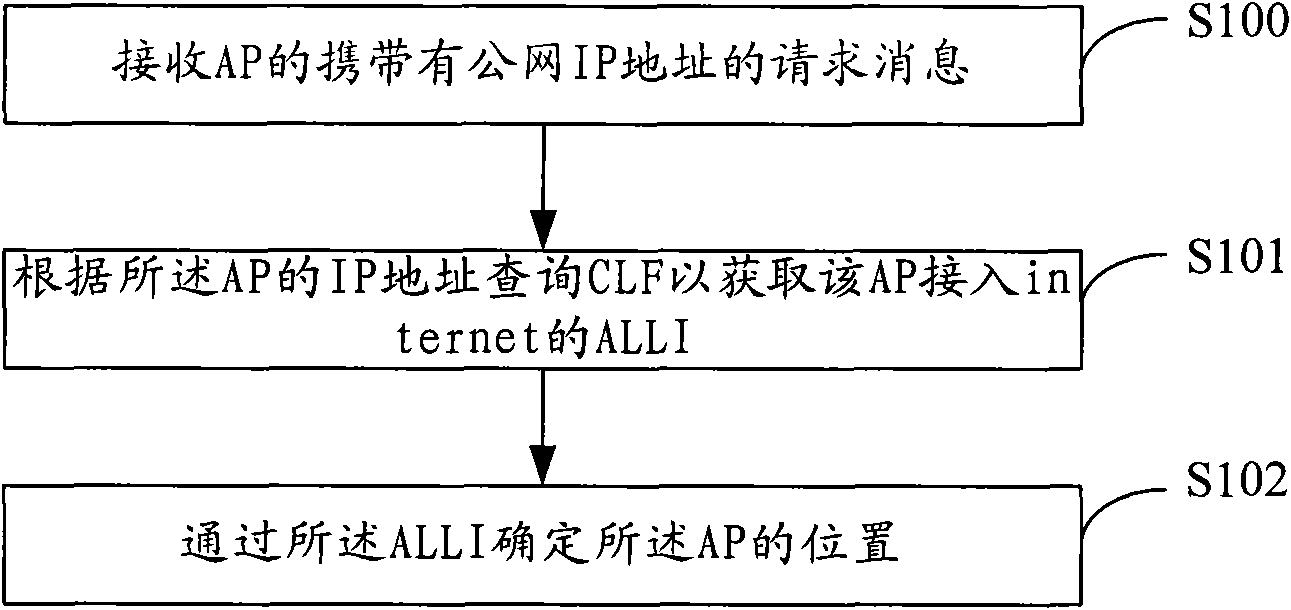
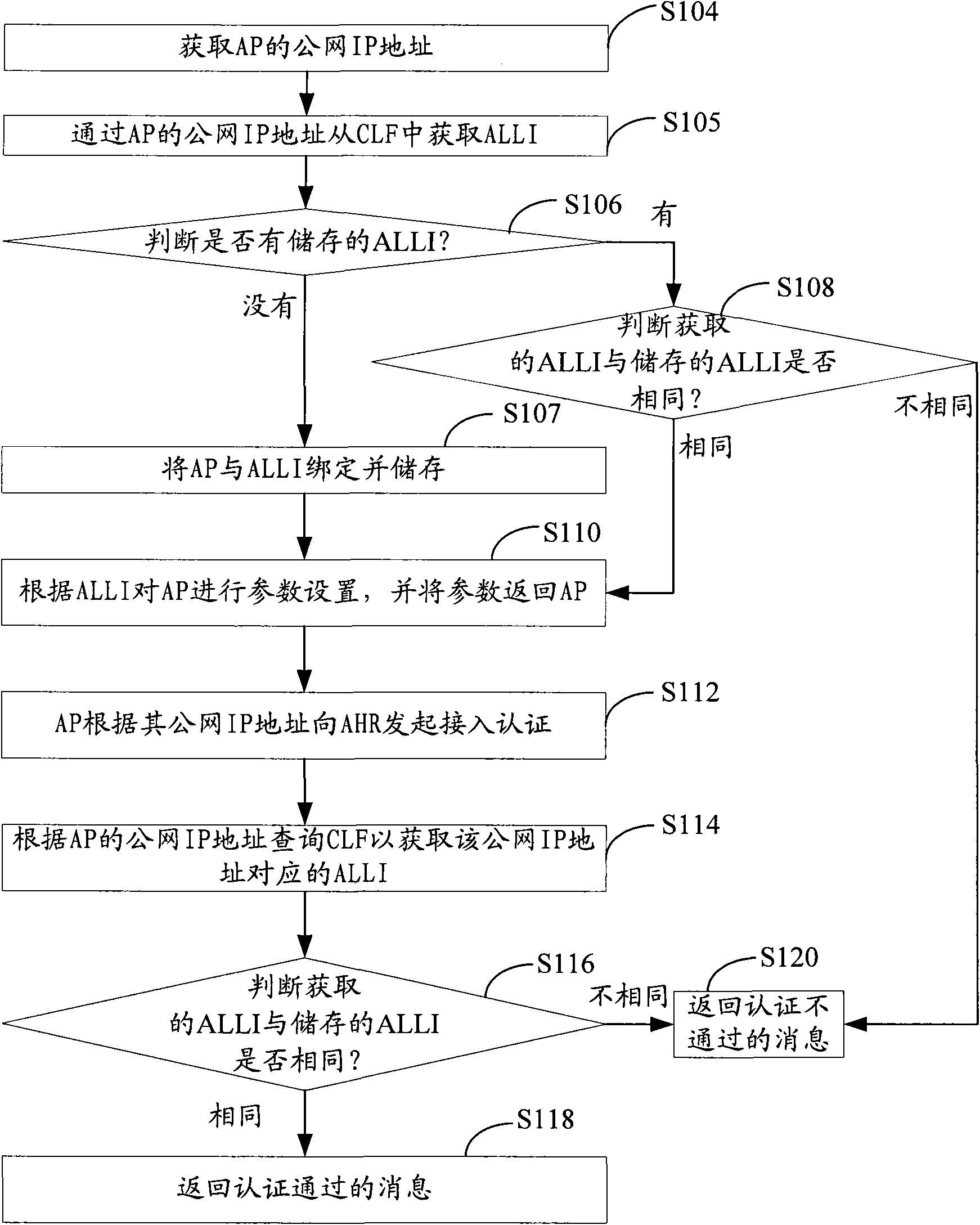
Position locating and verifying methods and system of wireless access device and attribution server
ActiveCN101674566AAchieve legitimacyAchieving detection legitimacyNetwork topologiesSecurity arrangementIp addressReal-time computing
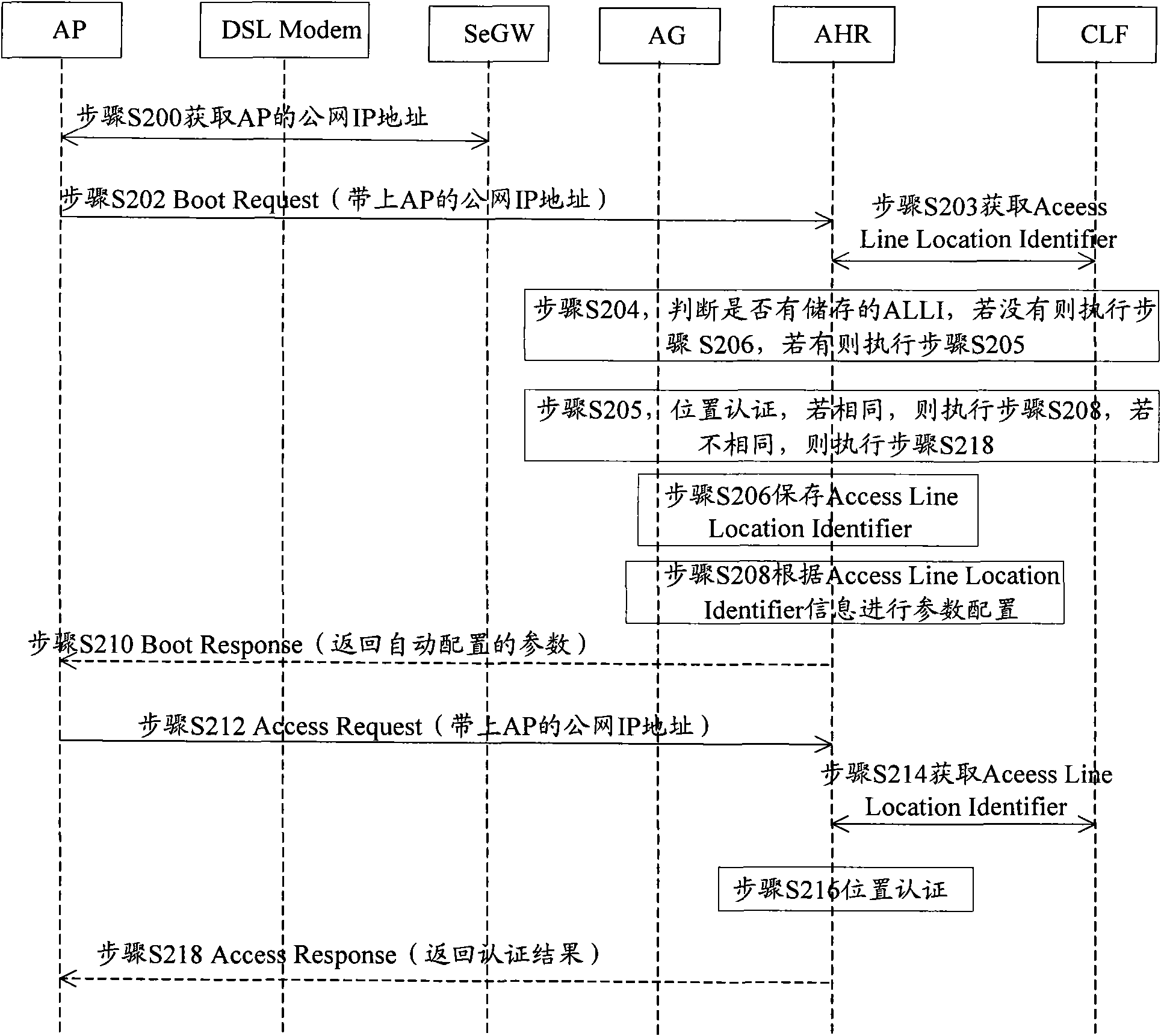
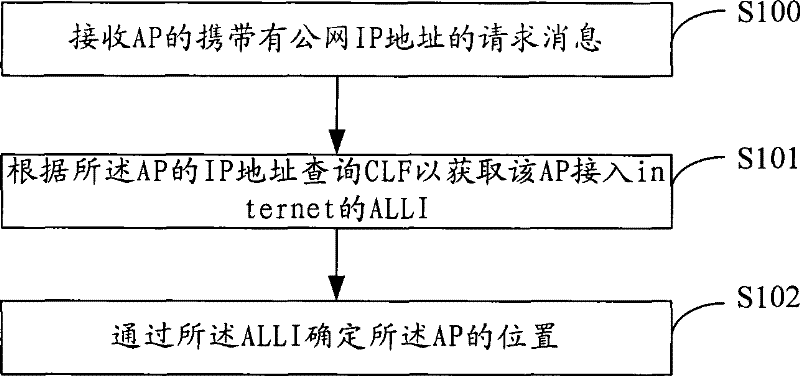
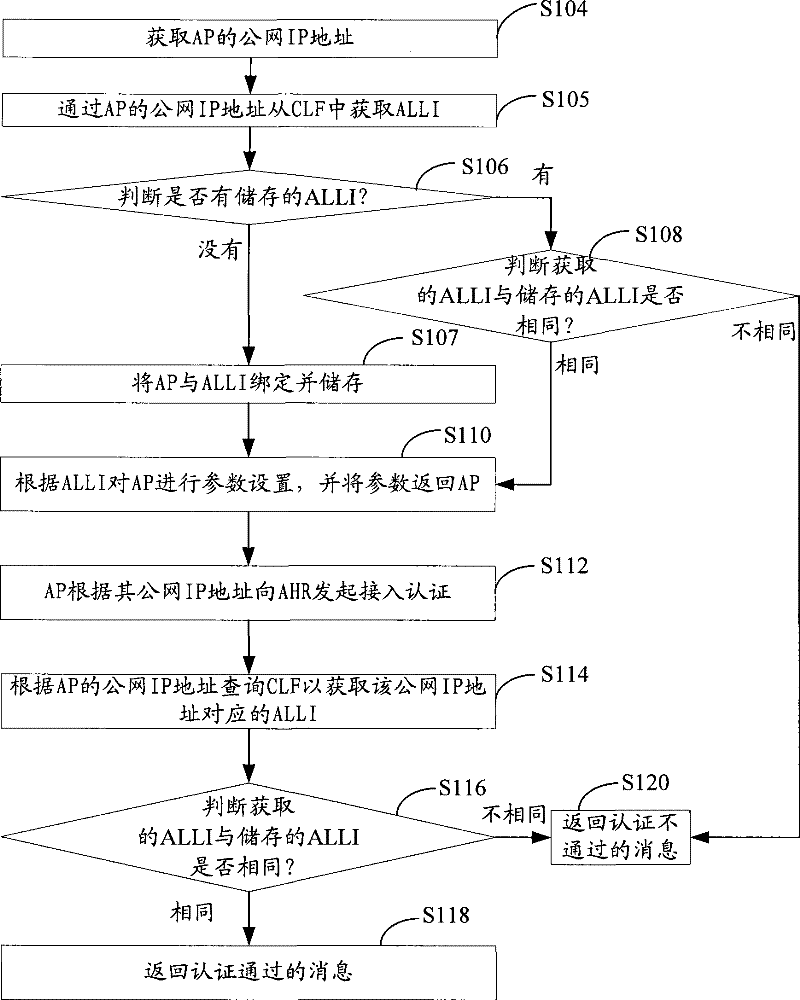
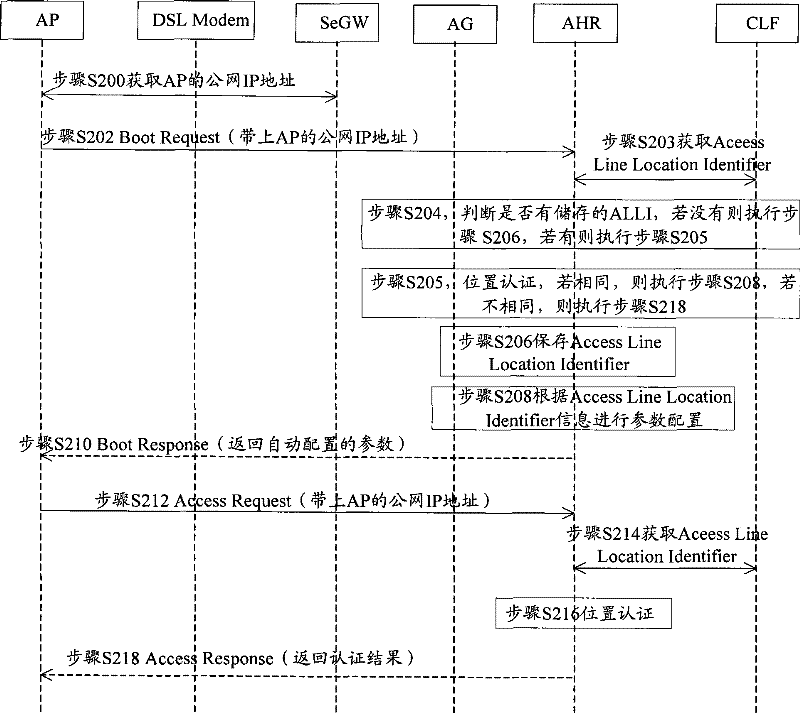
The embodiment of the invention discloses a position locating method of a wireless access device, comprises the following steps: inquiring a CLF according to an IP address of an AP so as to acquire anALLI of an AP access network, wherein the ALLI is used for identifying a line position of the AP access network; and confirming the position of the AP by an ALLI identifier. Meanwhile, the inventionalso provides a position verifying method of the wireless access device, comprising the following steps: inquiring the CLF according to the IP address of the AP so as to acquire the ALLI of the AP access network; and when the acquired ALLI of the AP access network is same as a stored ALLI of the AP access network, the position of the AP does not change. The embodiment of the invention also provides an attribution server and a system which can accurately locate and verify the position of the AP, thereby realizing the validity for the position detection of the AP.
Owner:HUAWEI TECH CO LTD
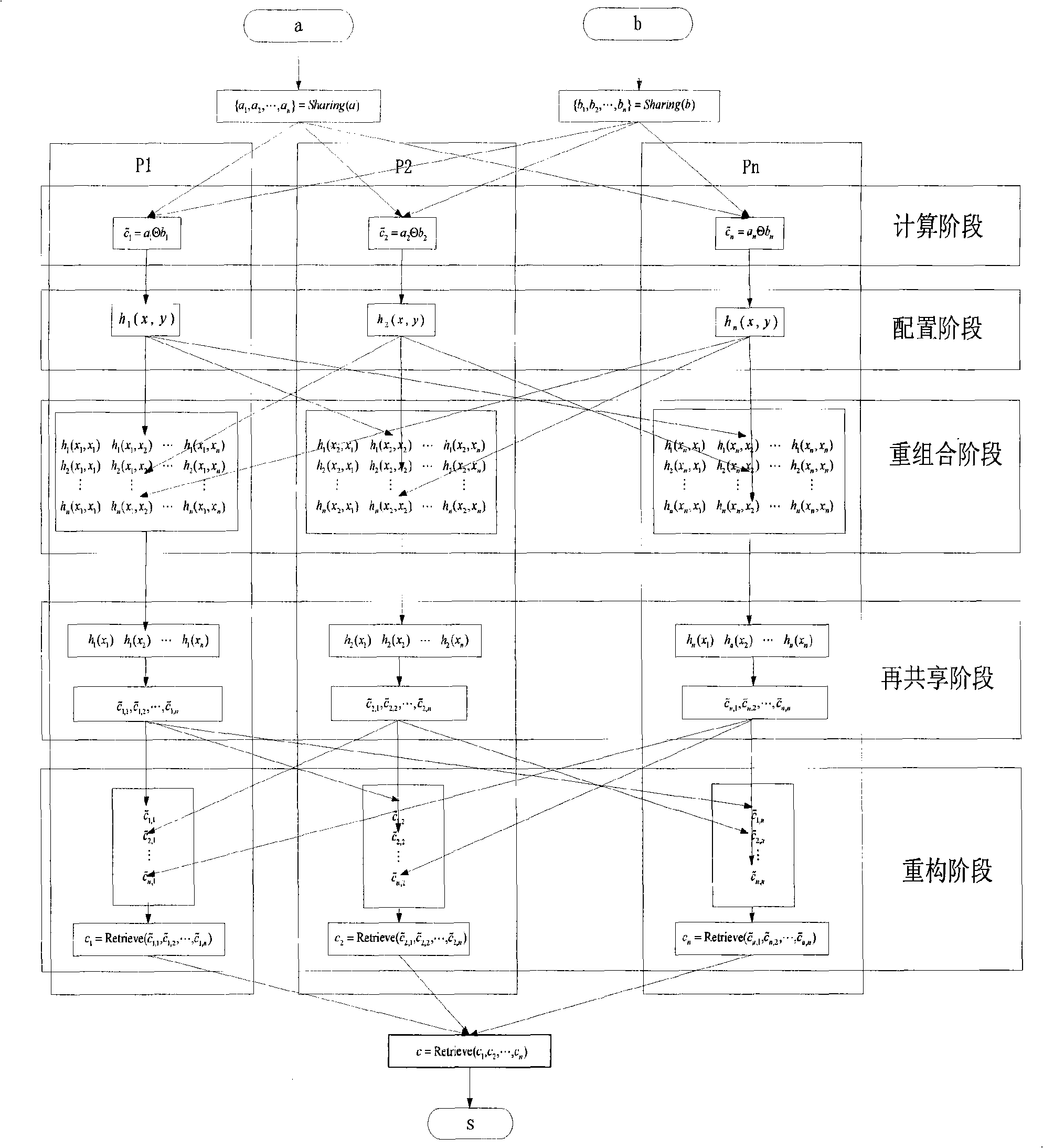
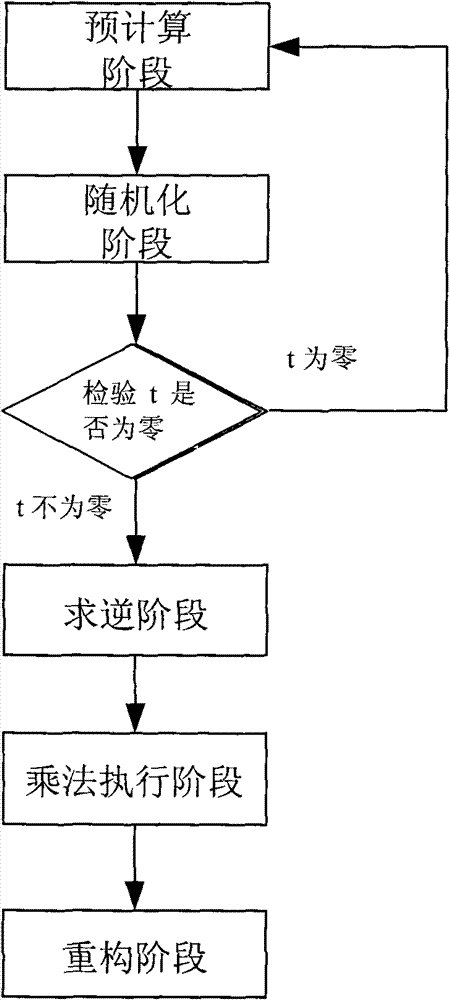
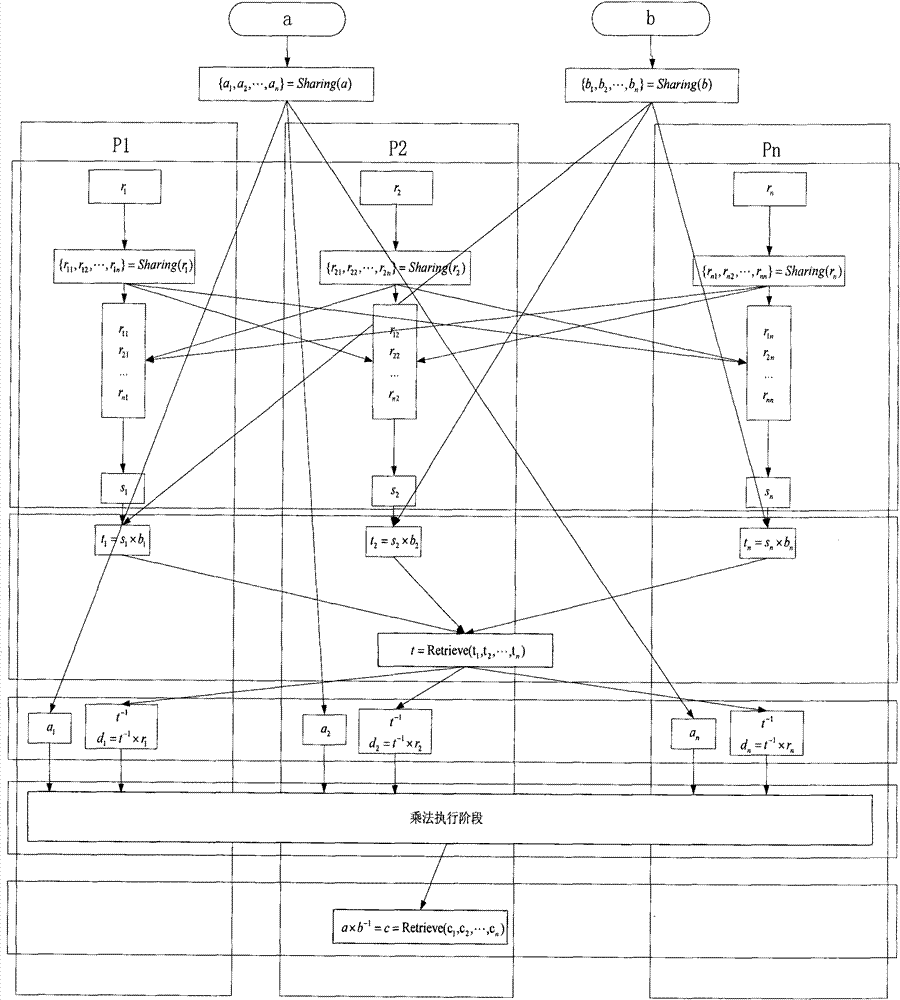
Construction method of division protocol based on cryptology in distributed computation
InactiveCN101729554AEasy to implementReduce computational complexityKey distribution for secure communicationFault toleranceCipher
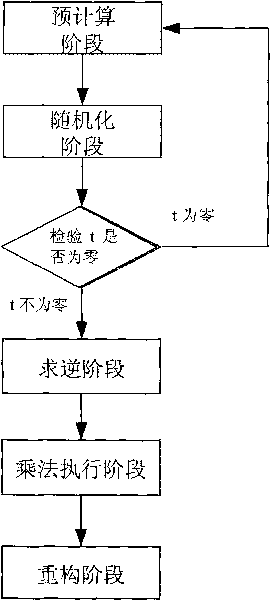
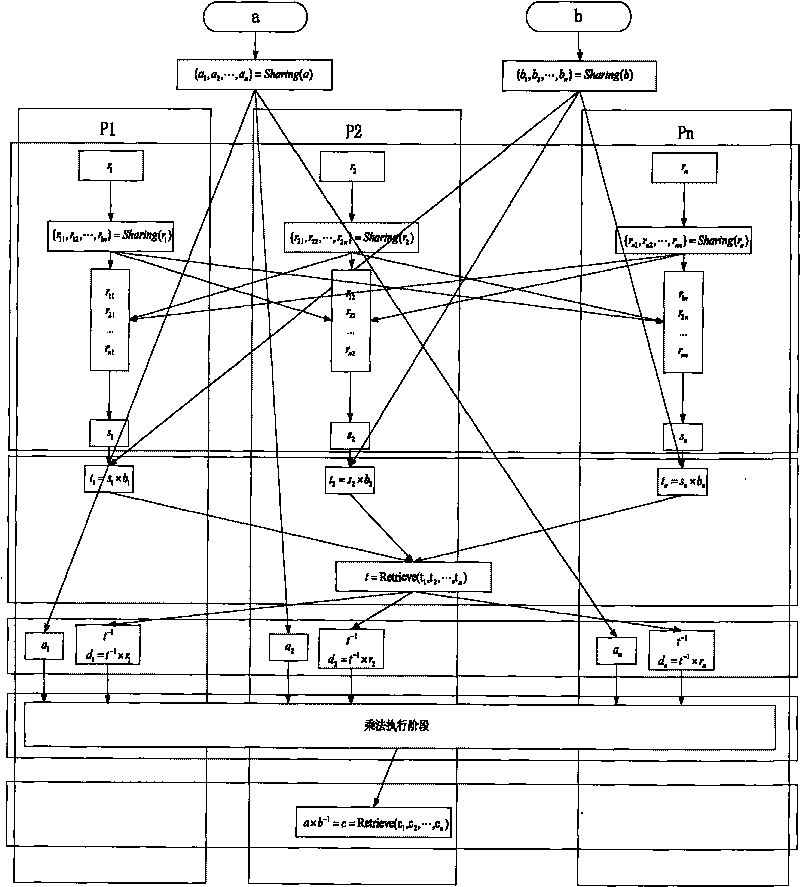
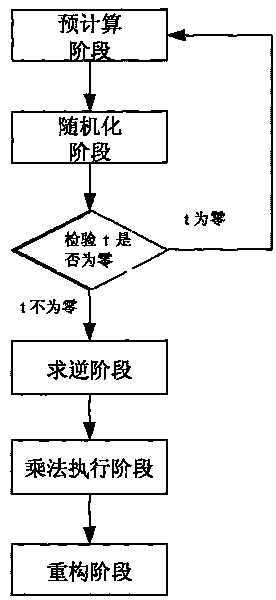
The invention discloses a construction method of a division protocol based on cryptology in distributed computation, belonging to the field of information safety. The formation method is characterized in that (1) each member who participates in the computation dependently selects a random number and sends the shared value of the random number to all parties for local hybrid operation so as to obtain a public random shared value; (2) each member randomizes the sharing of an input secret value b by using the public random shared value and reconstructs the randomizing value of the secret value btogether; (3) each member inspects whether a randomizing result of the secret value b is inverse or not, if so, the member solves an inverse element of the randomizing value of the secret value b andthen de-randomizes the inverse element to obtain the inverse sharing of the secret value b by utilizing the public random shared value; (4) each member utilizes the obtained inverse sharing of the secret value b and a sharing executive multiplication protocol of a secret value a to obtain the sharing of the a / b; and (5) each member reconstructs a real computing result by mutually exchanging the obtained sharing of the a / b. The invention has the characteristics of high efficiency, fault tolerance and safety.
Owner:PEKING UNIV
Message authentication method
InactiveCN1802018AImprove securityAchieve authenticationUser identity/authority verificationRadio/inductive link selection arrangementsMessage authentication codeBase station
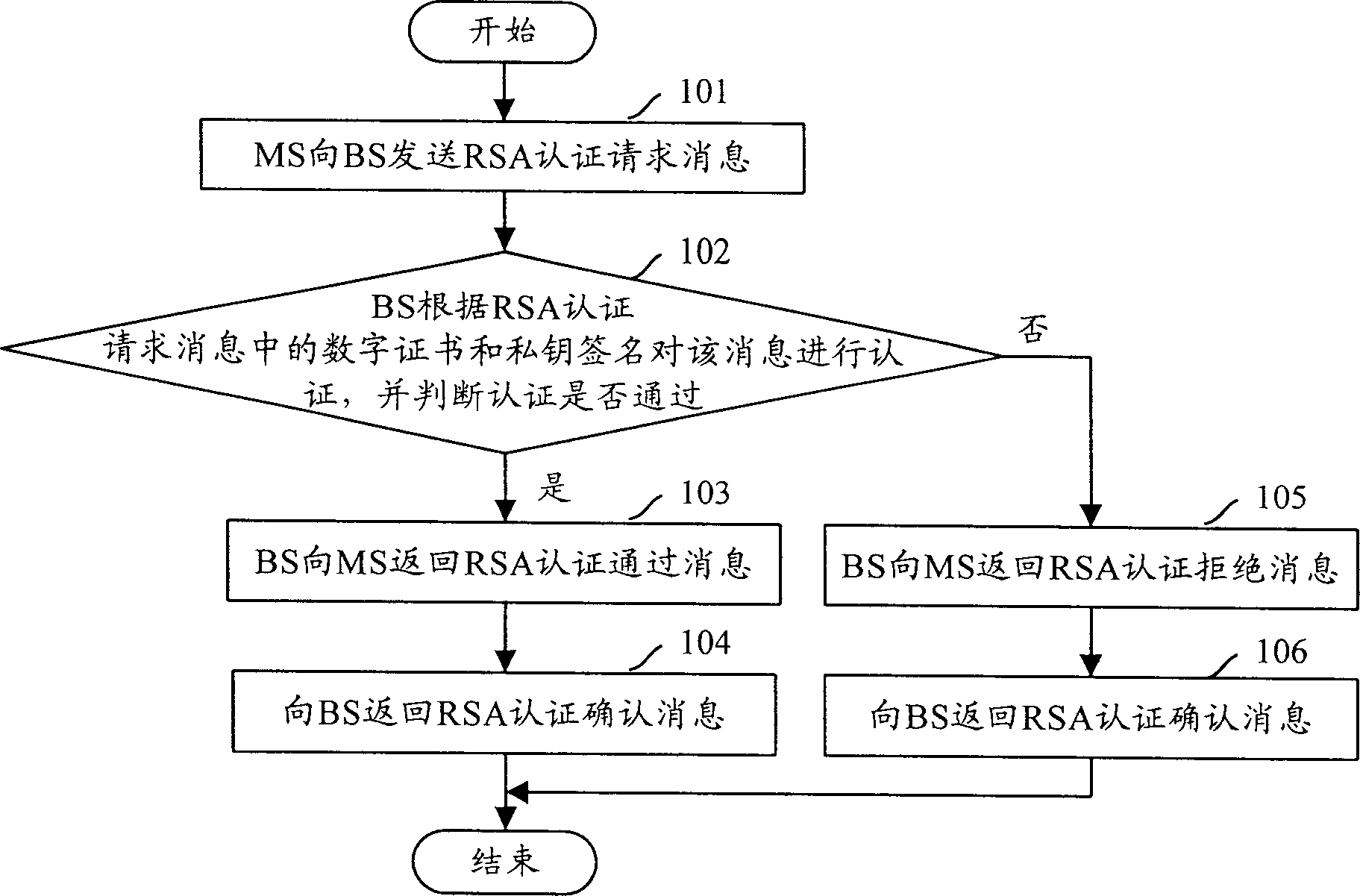
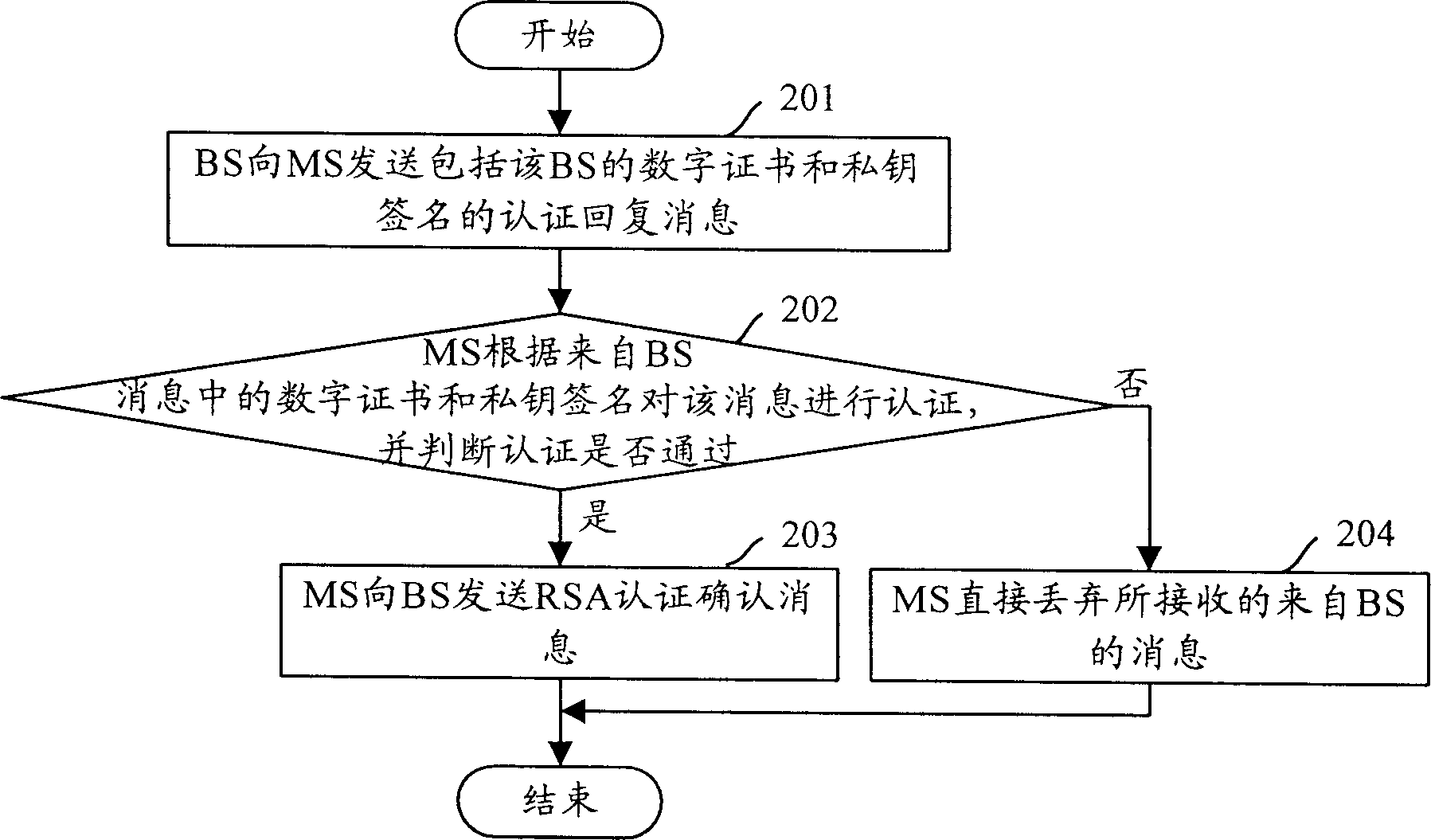
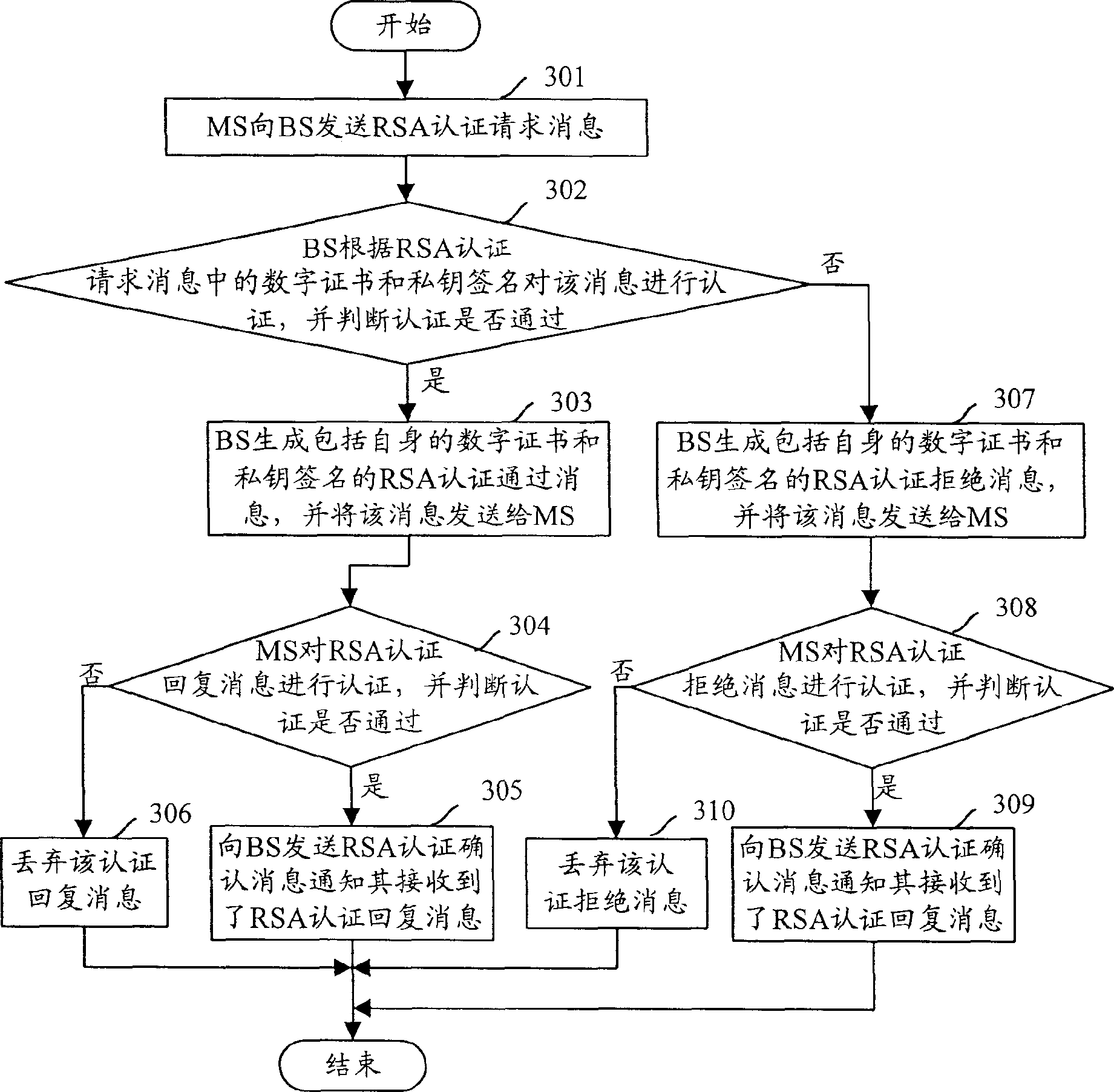
Present invention discloses a message authenticating method used in termination MS and base station BS. It contains MS transmitting authenticating request message to BS, BS transmitting authenticating reversion message including BS digit certificate and private key sign to MS after received said authenticating request message and authenticating, MS authenticating said message according to digit certificate and private key signature after receiving said authenticating reversion message, judging whether passing authenticating, and dropping said message from BS judging out it not passing authenticating. Said invention raises RSA authenticating security.
Owner:HUAWEI TECH CO LTD
Mobile terminal E-voting method based on facial feature recognition and system thereof
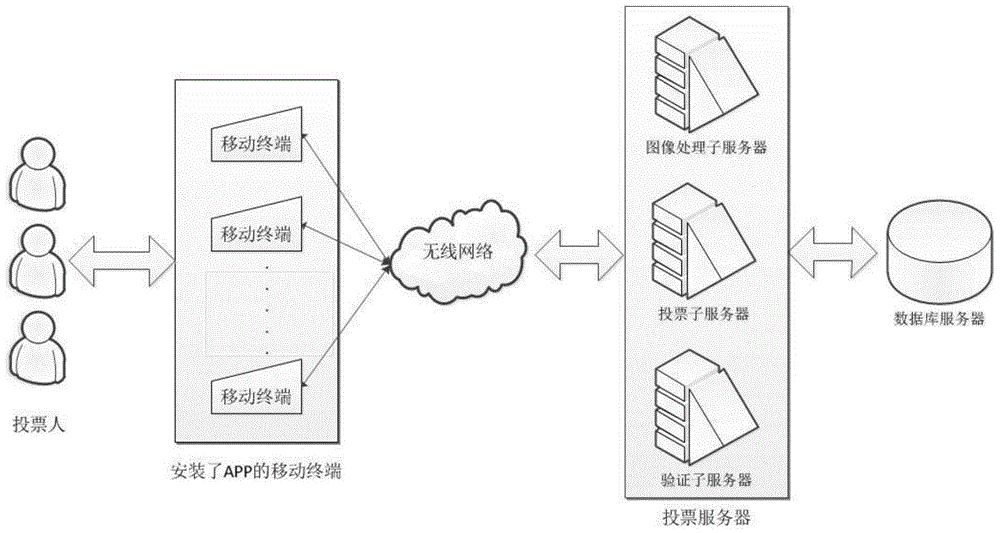
ActiveCN105225328AOvercome deficienciesImprove securityVoting apparatusUser identity/authority verificationConfidentialityComputer terminal
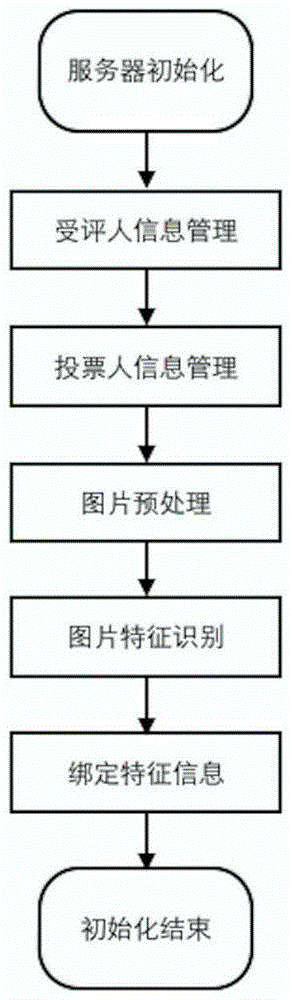
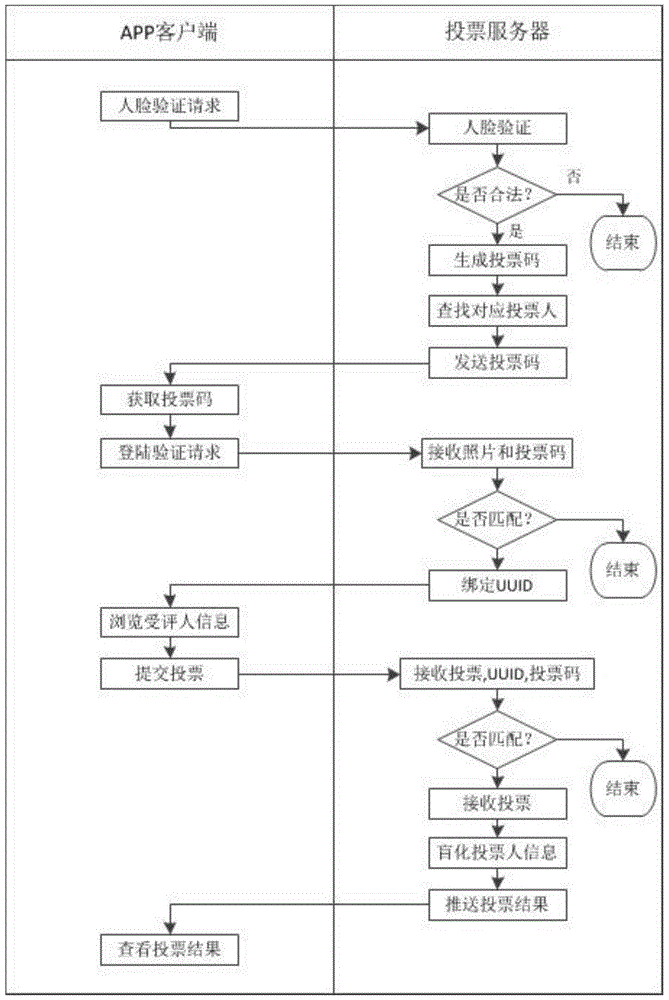
A mobile terminal E-voting method based on facial feature recognition comprises the following steps: (1) data of a voting server SS is initialized; and (2) a mobile terminal starts to vote. A voter needs to pass cross validation of a system during the voting process, and the process is as follows: (2.1) first validation: after first validation, jumping to a login interface and starting login certification which needs a voting code T_codei, equipment T_UUIDi and a face photo T_pici, wherein the voting code T_codei is obtained by a user from a mail-box T_maili and obtaining a voting code from the mail-box is second validation; and the equipment T_UUIDi is automatically obtained by an APP from equipment and the face photo T_pici is shot by an APP camera; (2.2) second validation: entering the voting code T_codei obtained from the mail-box T_maili; (2.3) third validation; and (2.4) voting. The invention also provides a mobile terminal E-voting system based on facial feature recognition. The method and the system consider both high security and high confidentiality and are convenient to use.
Owner:ZHEJIANG UNIV OF TECH
Door lock communication verifying method and device, a terminal and a computer readable storage medium
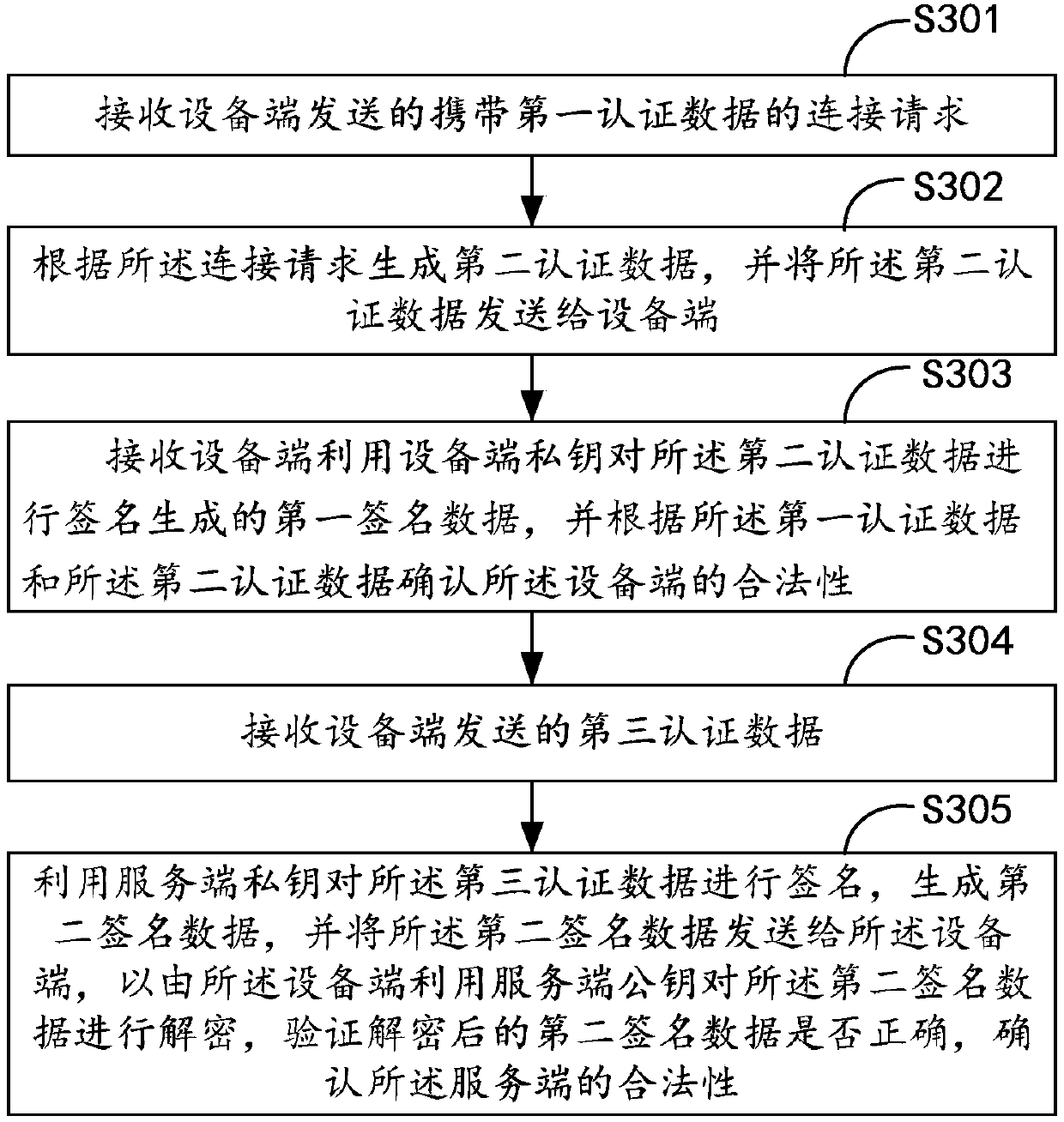
InactiveCN108683674AAchieve legitimacyEnsure safetyIndividual entry/exit registersTransmissionValidation methodsComputer terminal
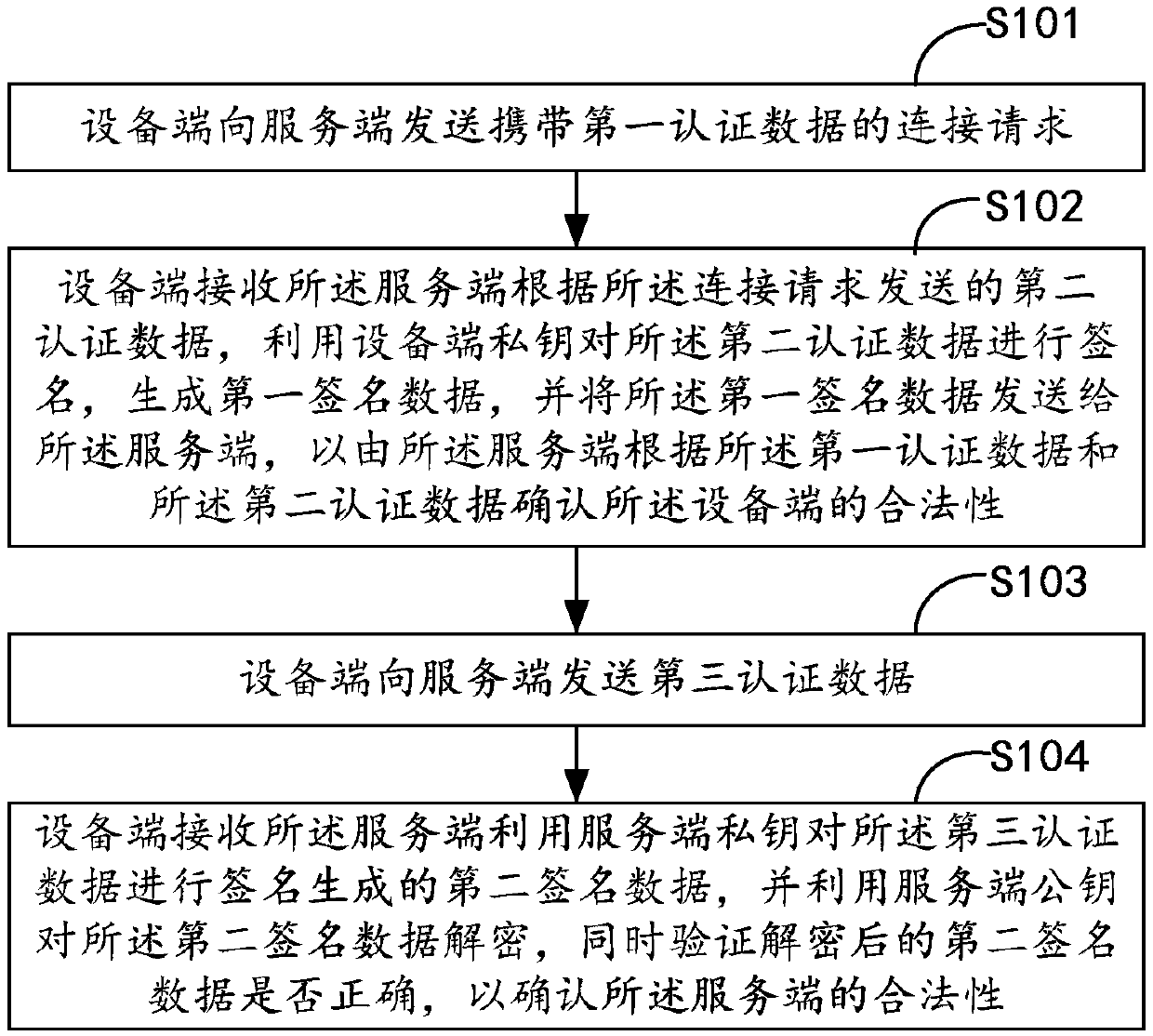
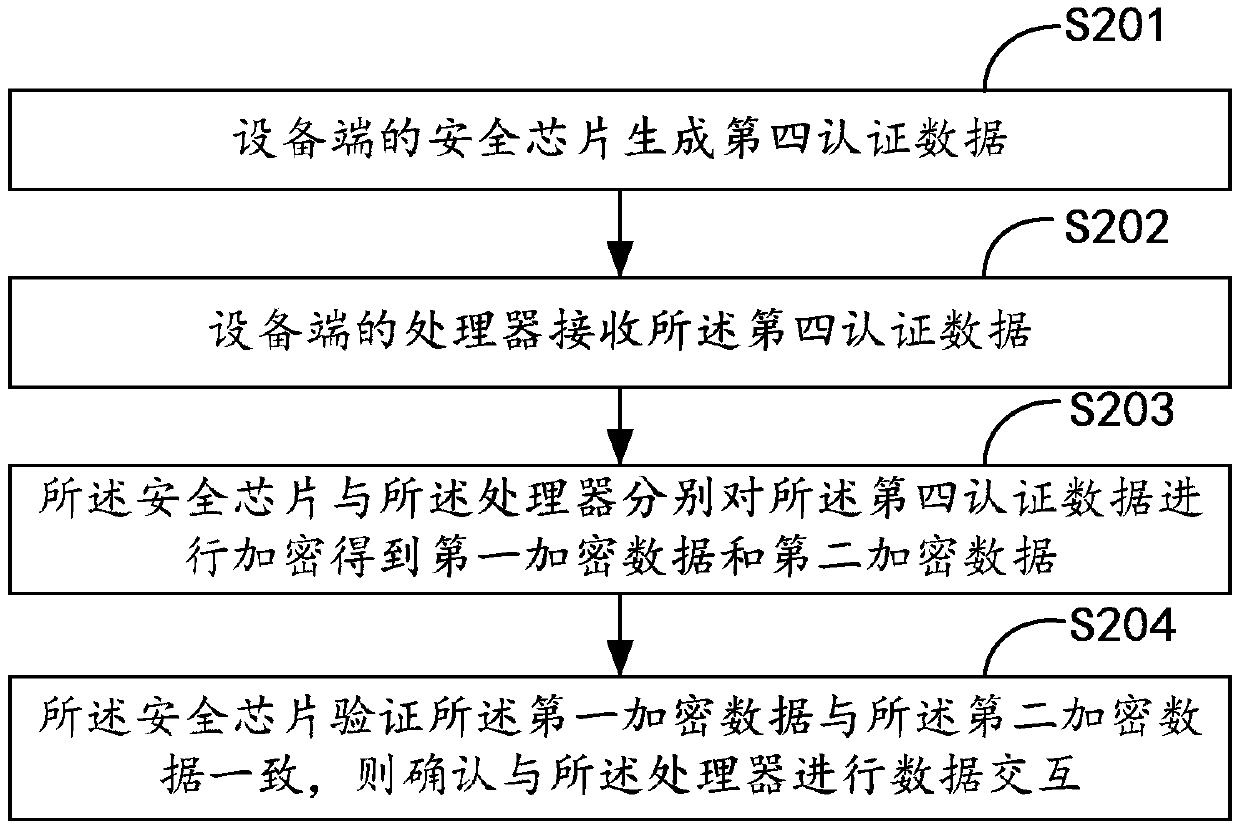
The invention belongs to the technical field of door lock information security and particularly relates to a door lock communication verifying method and device, a terminal and a computer readable storage medium. The verifying method includes the following steps: a device end sends a connection request carrying first authentication data to a server end, the device end receives second authentication data sent by the server end according to the connection request, first signature data is generated and sent to the server end, the server end confirms the legality of the device end according to thefirst authentication data and the second authentication data, the device end sends third authentication data to the server end, the device end receives the second signature data which is generated bythe server end after the third authentication data is signed by the server end to confirm the legality of the server, two-way security encryption authentication is established between the device endand the server end of a door lock, only when the two-way security encryption authentication between the device end and the server end is successful can communication between the device end and the server end be established, and network data security of the door lock can be effectively guaranteed.
Owner:深圳中泰智丰物联网科技有限公司
Processing method for platform identity recognition and authority authentication
InactiveCN110688643AResolve authenticationSolve the problem of rights managementDigital data authenticationIdentity recognitionPassword
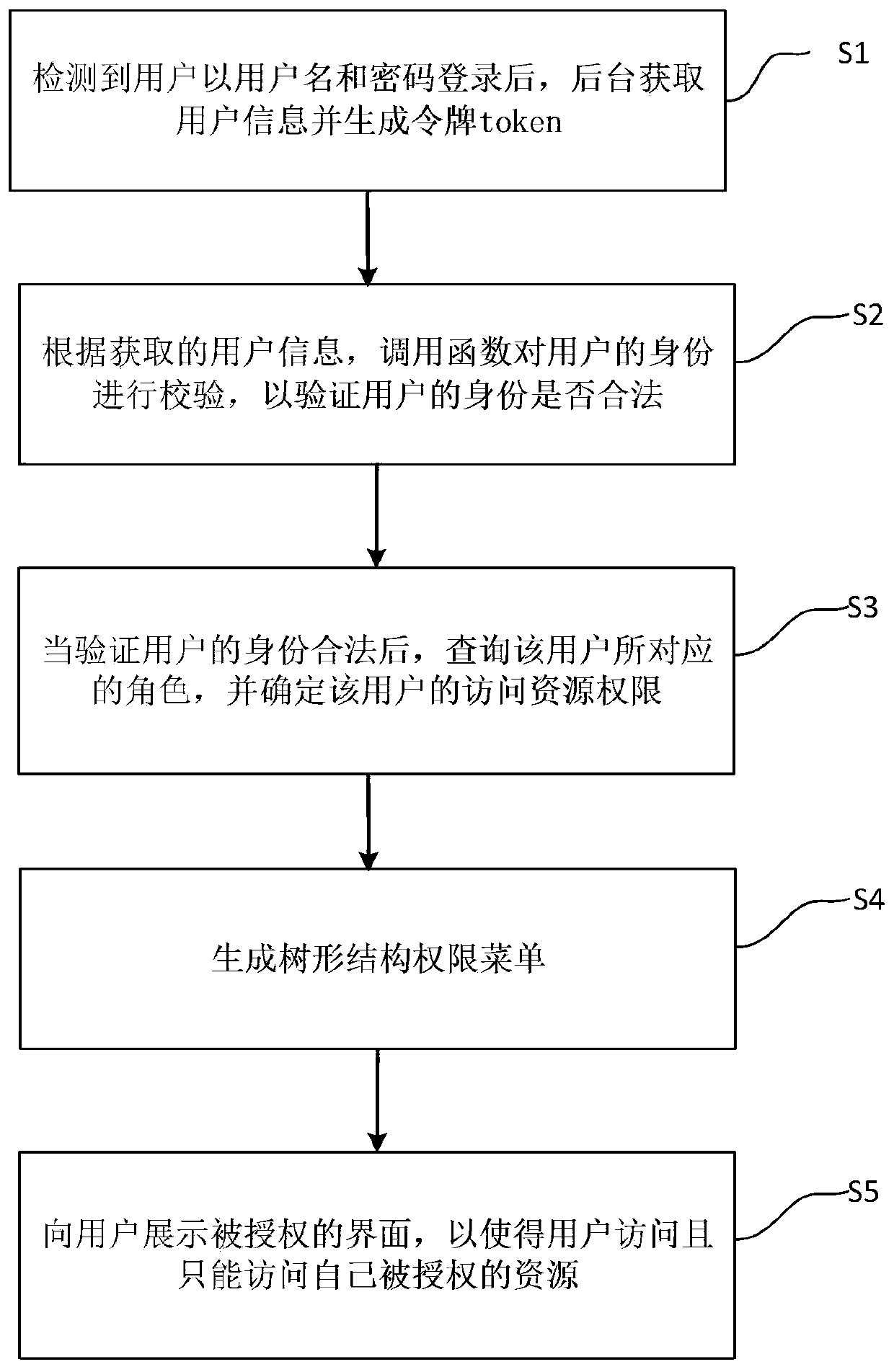
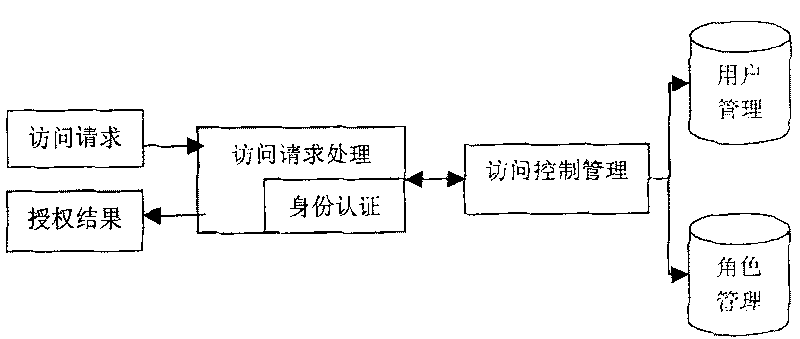
The invention provides a platform identity recognition and authority authentication processing method, which comprises the following steps: after detecting that a user logs in with a user name and a password, a background acquiring user information and generating a token; according to the obtained user information, calling a function to verify the identity of the user so as to verify whether the identity of the user is legal or not; when the identity of the user is verified to be legal, inquiring the role corresponding to the user, and determining the access resource permission of the user; generating a tree structure permission menu; and displaying the authorized interface to the user, so that the user can access and only can access own authorized resources. According to the invention, the problems of platform user identity authentication and authority management are solved, multi-terminal login is avoided, identity counterfeiting and illegal resource access are prevented, user information is protected, and the practicability is high.
Owner:BEIJING GEO POLYMERIZATION TECH
Cryptography distributed calculation and step-by-step verification method with fault-tolerant function
InactiveCN101325596AAchieve efficiencyTo achieve fault toleranceError preventionAccess structureTheoretical computer science
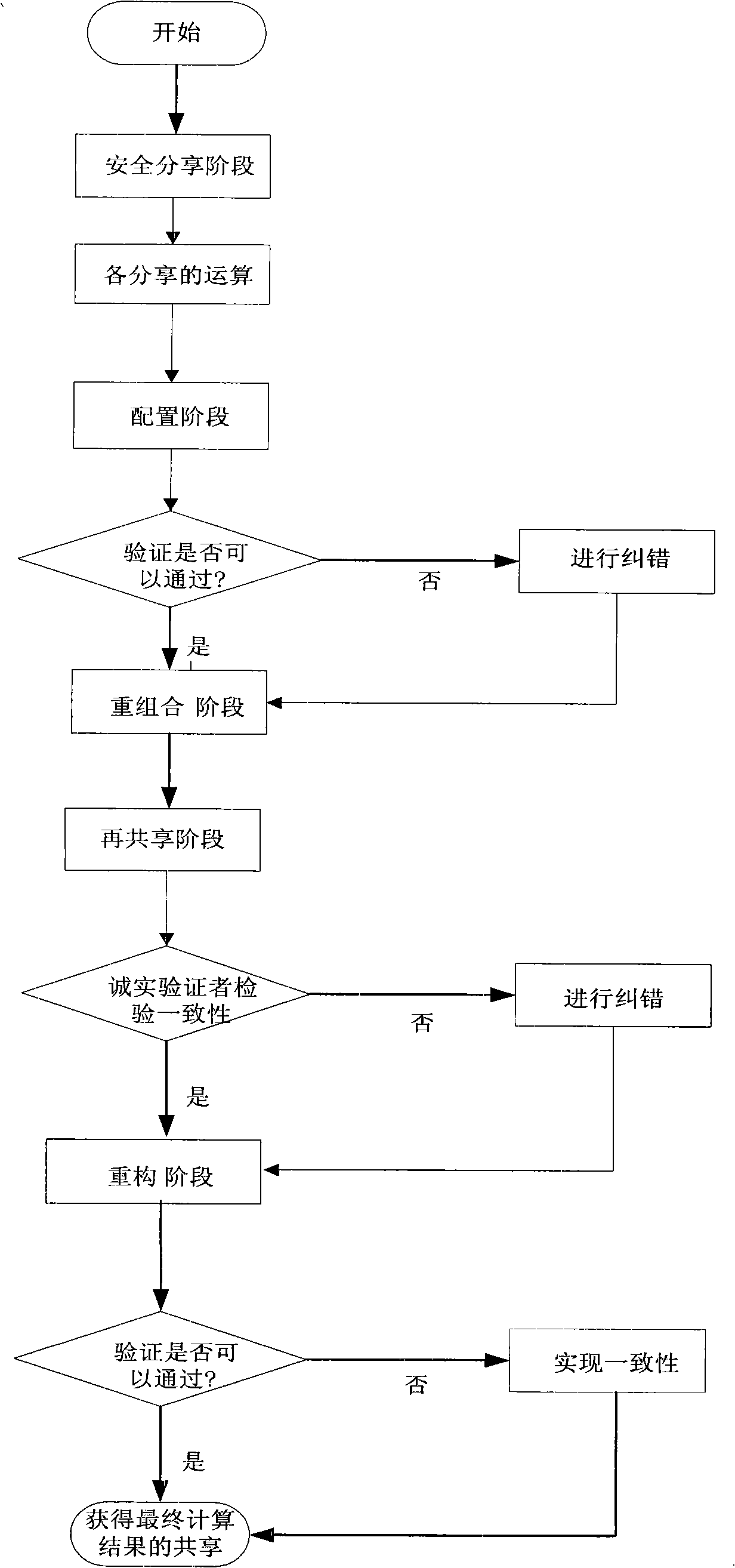
The invention discloses a fault tolerant cryptography distributed computing and multiple step testing method which belongs to the distributed computing field. The method comprises: 1) each member carries out the shared operation separately; 2) every member generates stochastic polynomial according to the required access structure and exchanges the datum induced from the stochastic polynomial; 3) every member generates combined stochastic polynomial by the received stochastic polynomial data together; 4) the result of step1) is re-shared by the combined stochastic polynomial and the re-shared result is distributed to every member; 5) each member further combines and reconstructs the receives re-shared data to gains the final result and a new re-share; 6) every member reconstructs the true result by exchanging the new re-share. The invention is a fault-tolerant and high efficient method with protocol safety, solves the problems of mass traffic and low efficiency in traditional algorithm and assures the continuity in secure computation.
Owner:PEKING UNIV
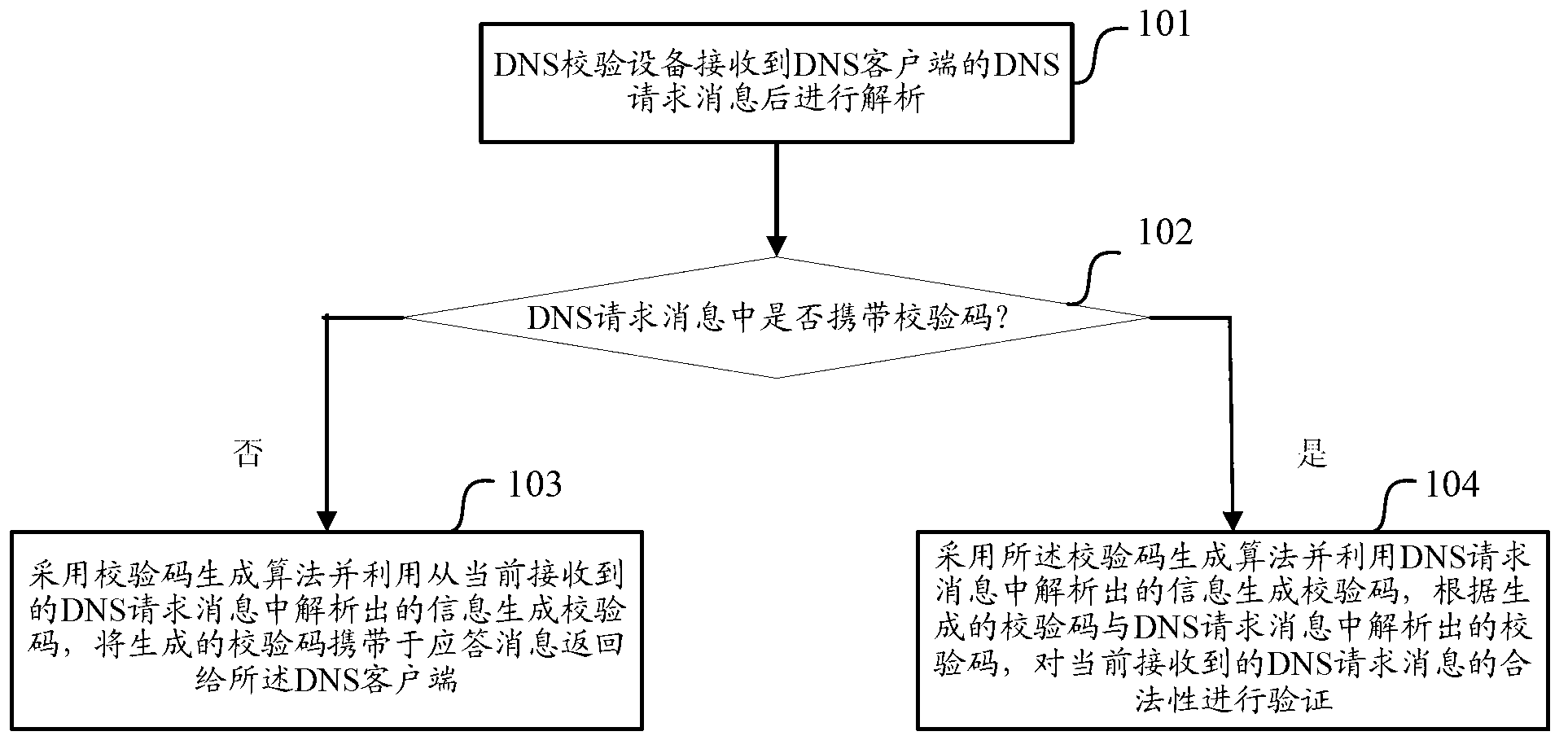
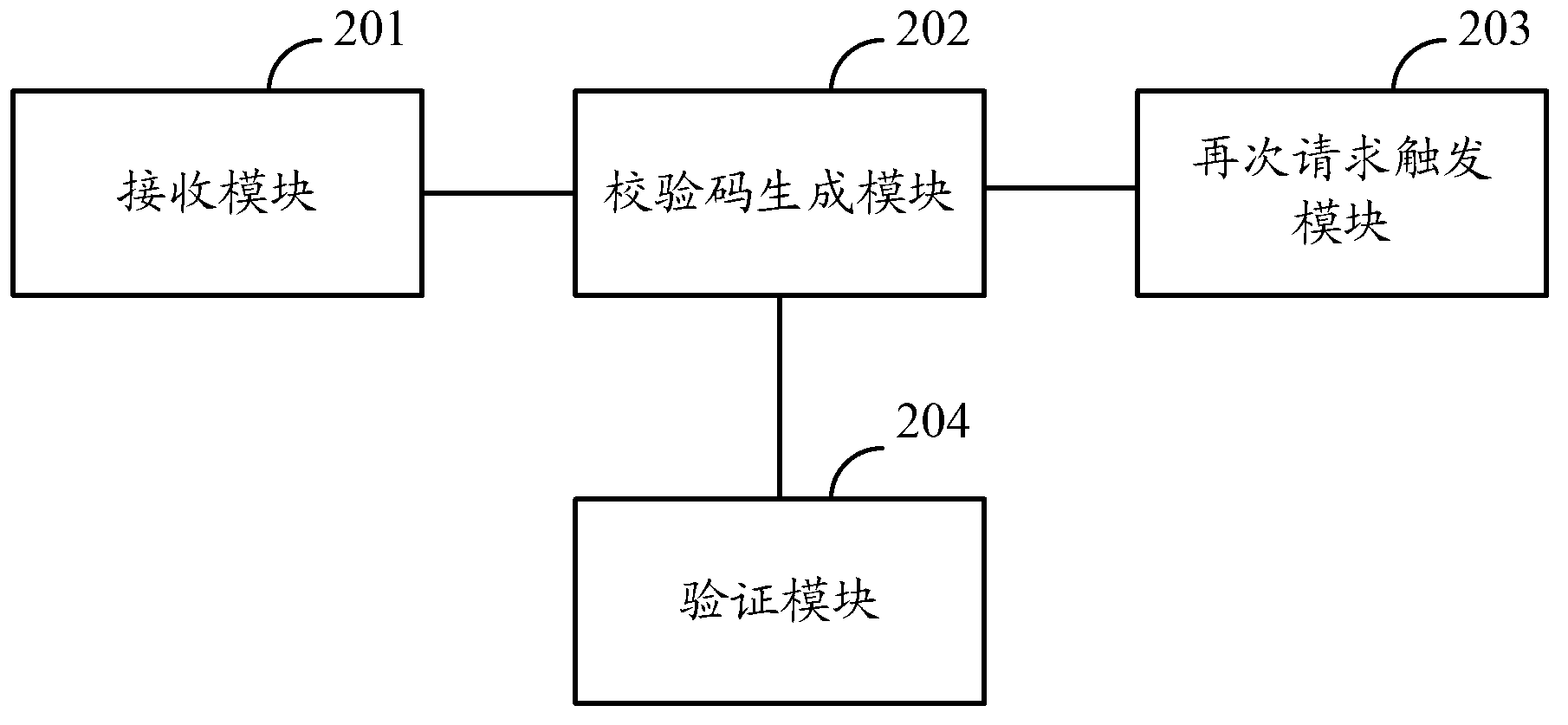
Domain name system (DNS) request authentication method and device
ActiveCN103312724ATo achieve the purpose of legality verificationAchieve legitimacyTransmissionClient-sideA domain
An embodiment of the invention discloses a domain name system (DNS) request authentication method and a device. The authentication method comprises the steps of enabling a DNS verification device to analyze DNS request messages after receiving the DNS request messages; if verification codes are not carried in the DNS request messages, adopting a verification code generating algorithm and utilizing information analyzed from the currently received DNS request messages to generate the verification codes, and returning the generated verification codes carried by answer messages to a DNS client-side; if the verification codes are carried in the DNS request messages, adopting the verification code generating algorithm and utilizing the information analyzed from the currently received DNS request messages to generate the verification codes, verifying validity of the currently received DNS request messages according to the generated verification codes and the verification codes analyzed from the currently received DNS request messages. DNS request authentication safety can be improved through the DNS request authentication method and the device.
Owner:CHINACACHE INT HLDG
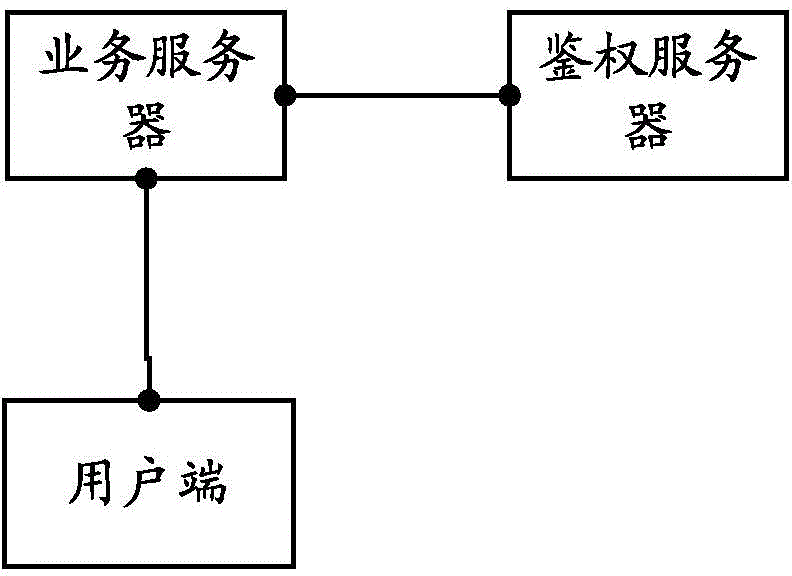
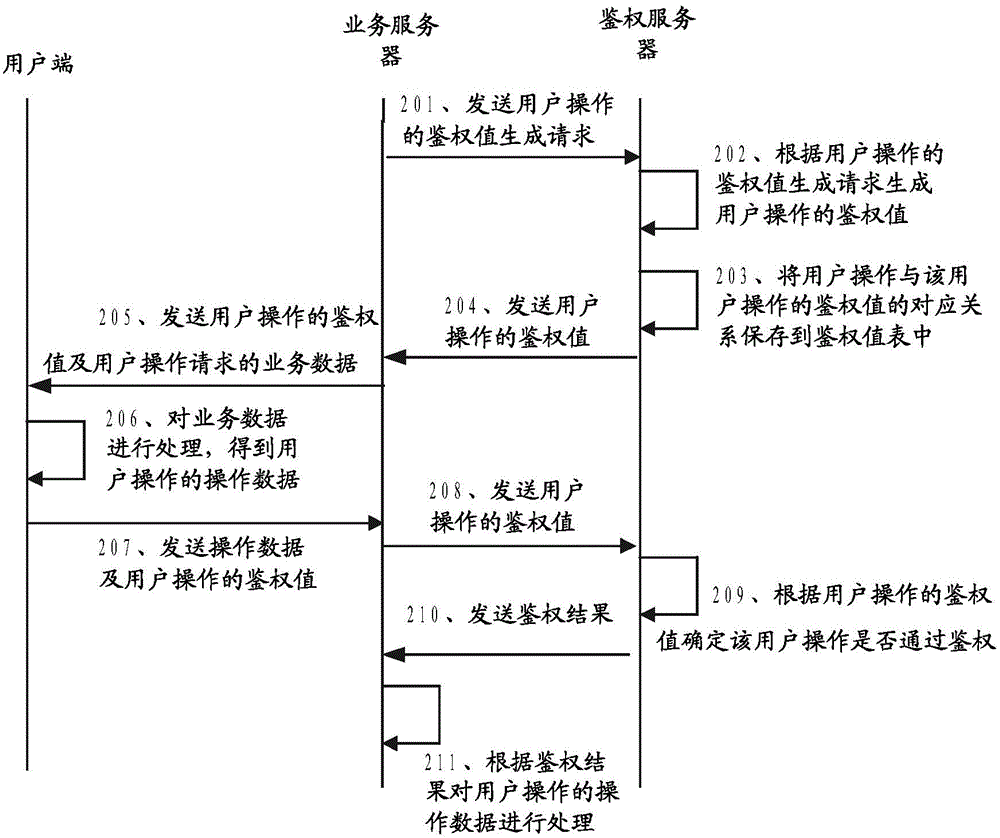
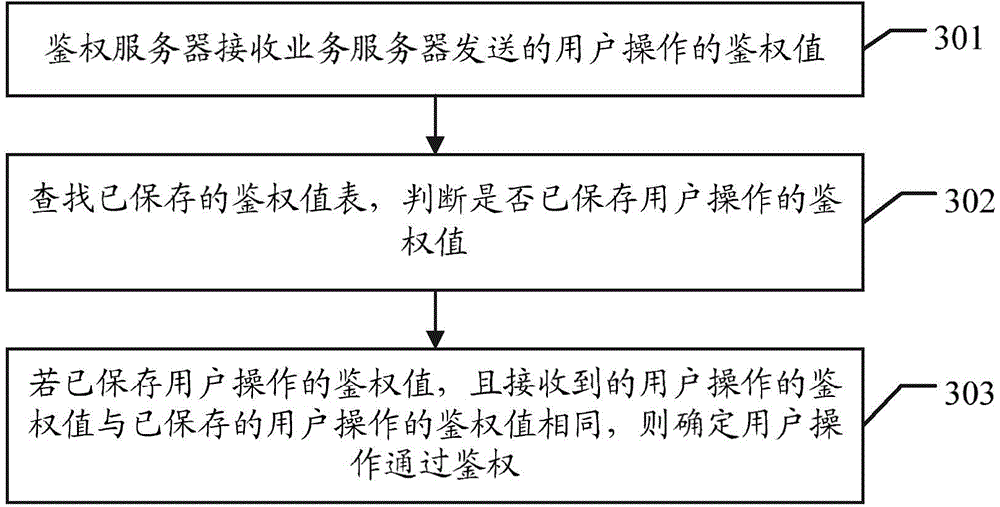
Authentication method, system and authentication server
The invention discloses an authentication method, an authentication system and an authentication server. The authentication system includes an authentication server, a service server and a user end; the service server is used for receiving the operation data of user operation and the authentication value of the user operation which are transmitted by the user end, and transmitting the authentication value of the user operation to the authentication server, the authentication server is used for determining whether the user operation passes through authentication according to the authentication value of the user operation, and transmitting an authentication result to the service server, and the service server is further used for processing the operation data of the user operation according to the authentication result. Based on the authentication server, the validity of the user operation is judged through utilizing the authentication value, and therefore, problems of long processing time and resource waste caused by repeated input of accounts and passwords can be effectively avoided, and judgment on the validity of the user operation can be realized simply and effectively.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
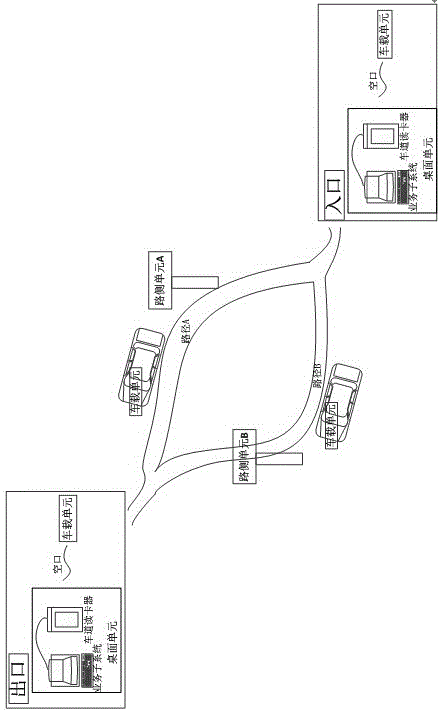
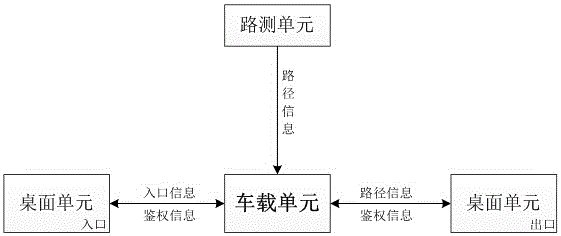
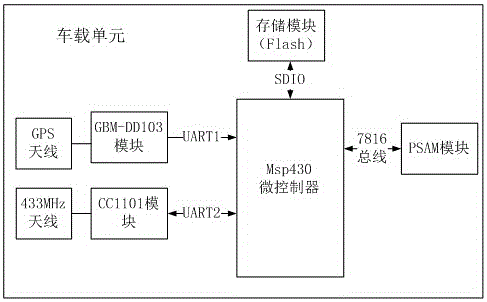
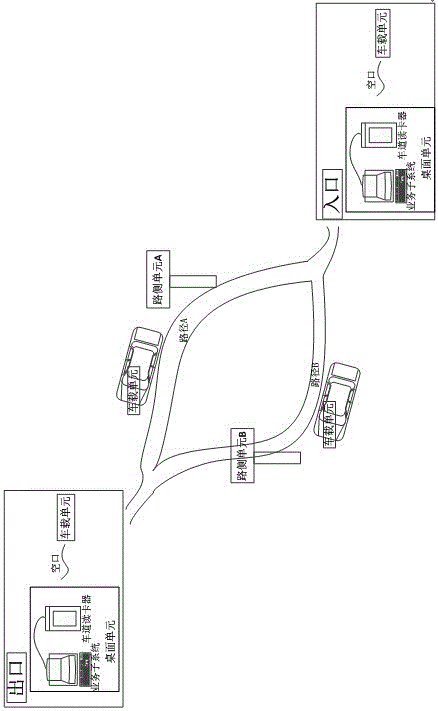
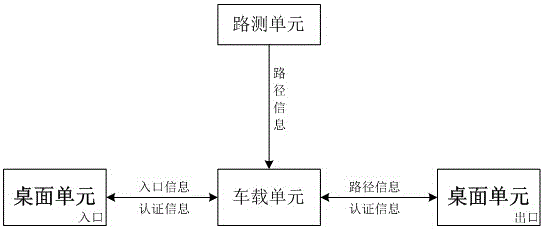
Vehicle-mounted unit applied to path identification system and safe method of vehicle-mounted unit
InactiveCN106408673ARealize the authentication functionAchieve legitimacyTicket-issuing apparatusRF moduleElectronic tagging
The invention discloses a vehicle-mounted unit applied to a path identification system and a safe method of the vehicle-mounted unit. The path identification system comprises the vehicle-mounted unit composed of an electronic label, a roadside unit composed of a roadside identification station and a desktop unit composed of a lane card reader and a service subsystem; the vehicle-mounted unit comprises an Msp430 microcontroller module, a PSAM safety certificate module, a GBM-DD103 positioning time service module, a CC1101 RF module, antennas and a FLASH storage module; and the GBM-DD103 positioning time service module and the PSAM safety certificate module configured in the vehicle-mounted unit provide positioning time-service and encryption functions respectively. A visitor can authorized via the encryption function, invalid access is prevented, and the legality and validity of a path identification can be determined via the positioning time-service function; and thus, the safety of the whole system is improved.
Owner:TIANJIN 712 COMM & BROADCASTING CO LTD
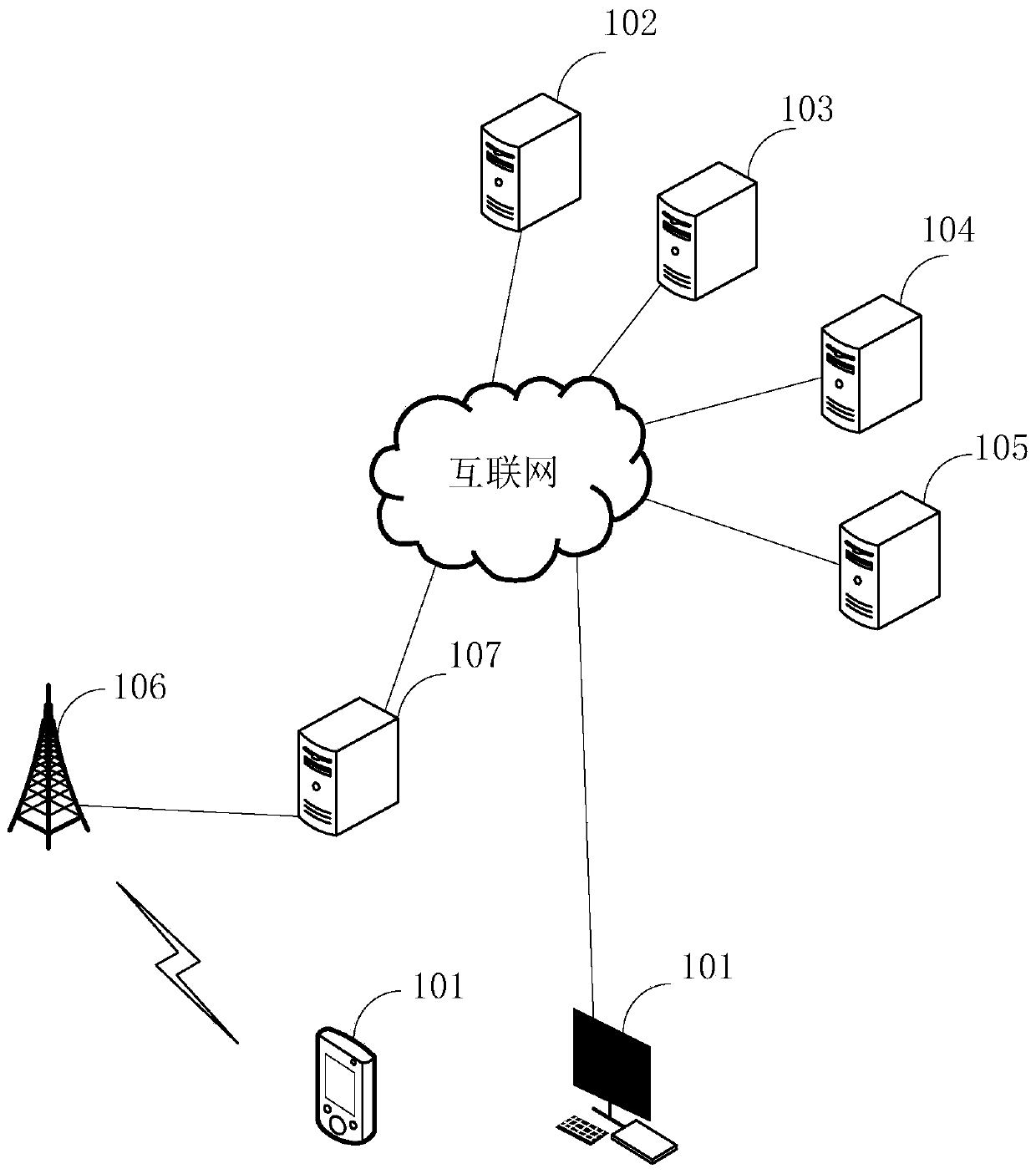
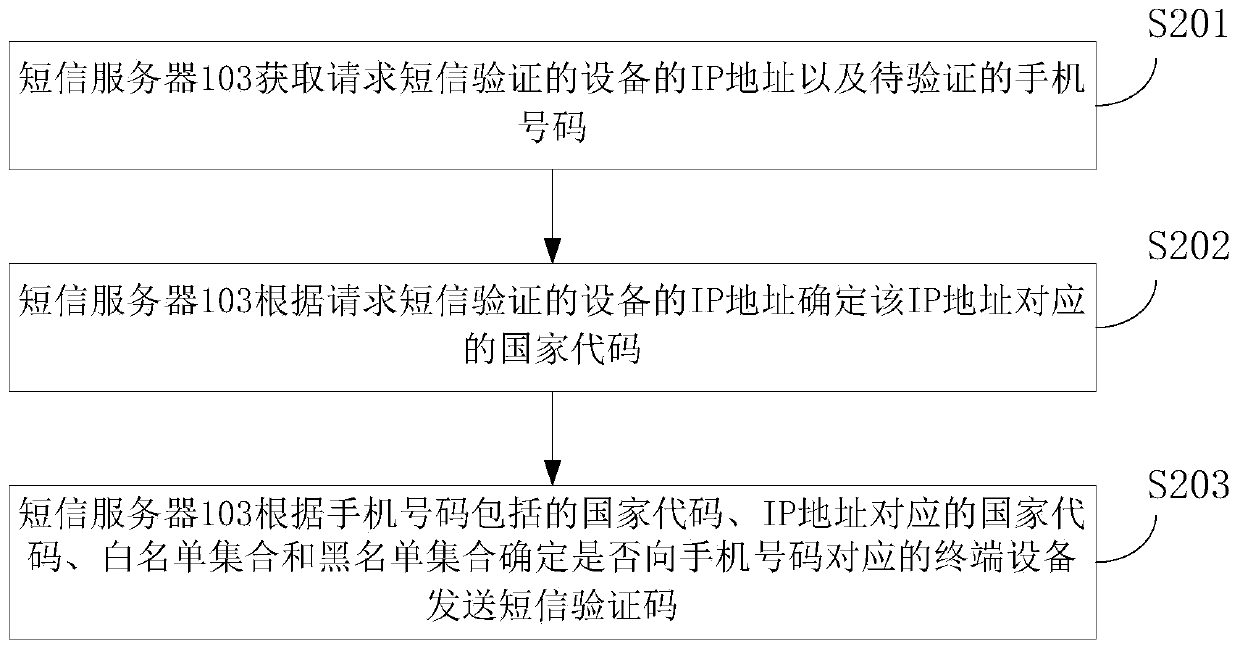
Short message verification code sending method and device, short message server and storage medium
ActiveCN111049822AAchieve legitimacyMessaging/mailboxes/announcementsTransmissionIp addressWhitelist
The invention relates to a short message verification code sending method and device, a short message server and a storage medium, relates to the field of short message verification, and is used for discriminating the legality of mobile phone numbers of various countries. The short message verification code sending method comprises the steps that an internet protocol IP address of equipment requesting short message verification and a to-be-verified mobile phone number are acquired, and the mobile phone number comprises a country code; determining a country code corresponding to the IP addressaccording to the IP address; determining whether to send a short message verification code to terminal equipment corresponding to the mobile phone number or not according to the country code includedin the mobile phone number, the country code corresponding to the IP address, the white list set and the black list set; wherein the white list set comprises at least one white list, the black list set comprises at least one black list, the white list comprises country codes allowing short message verification codes to be sent, and the black list comprises country codes not allowing short messageverification codes to be sent.
Owner:BEIJING DAJIA INTERNET INFORMATION TECH CO LTD
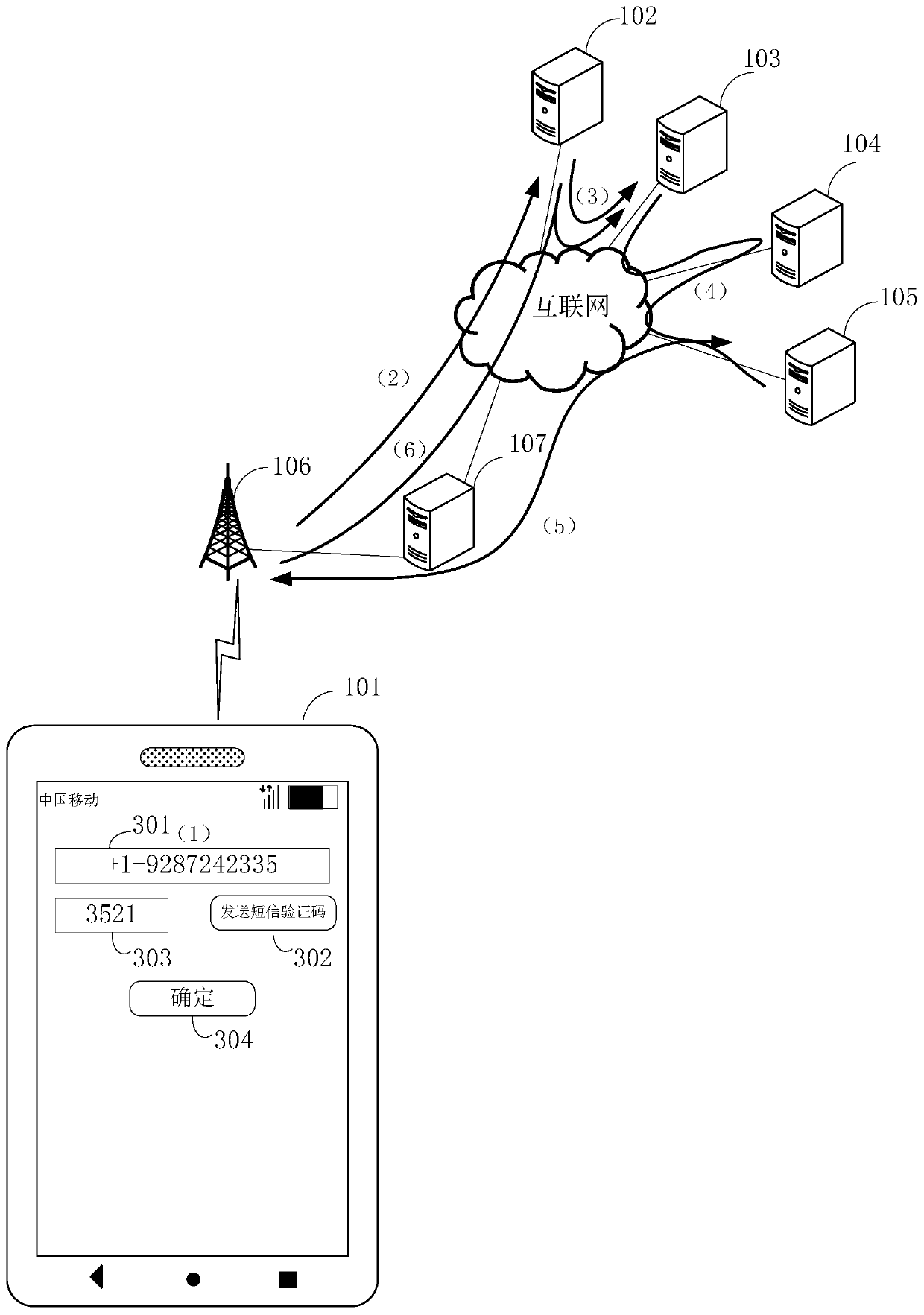
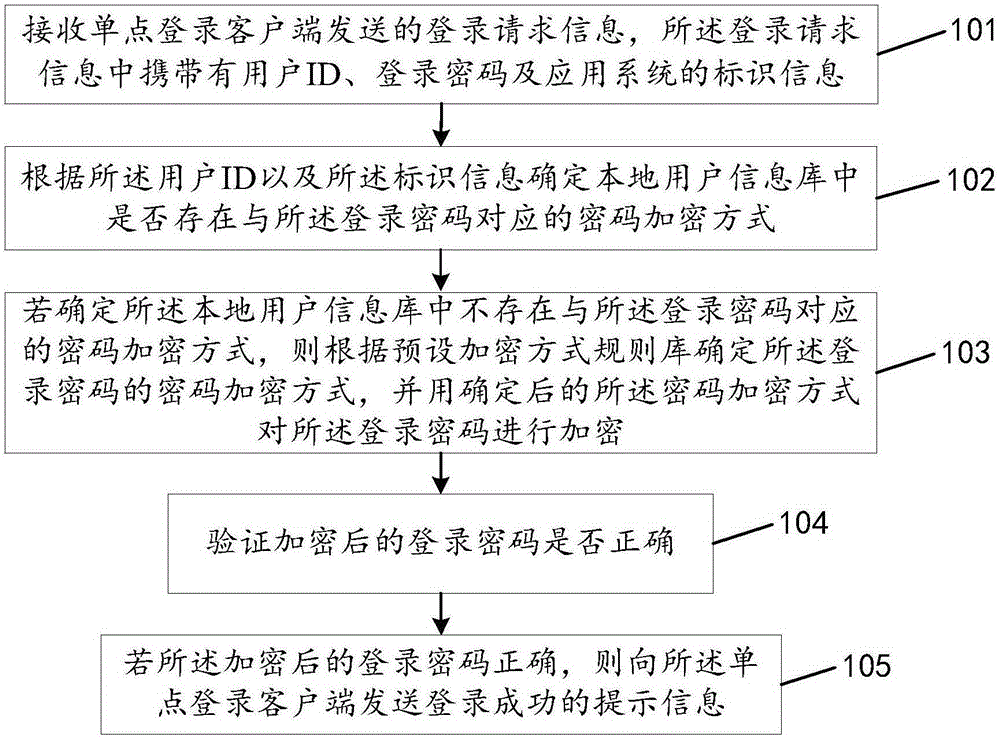
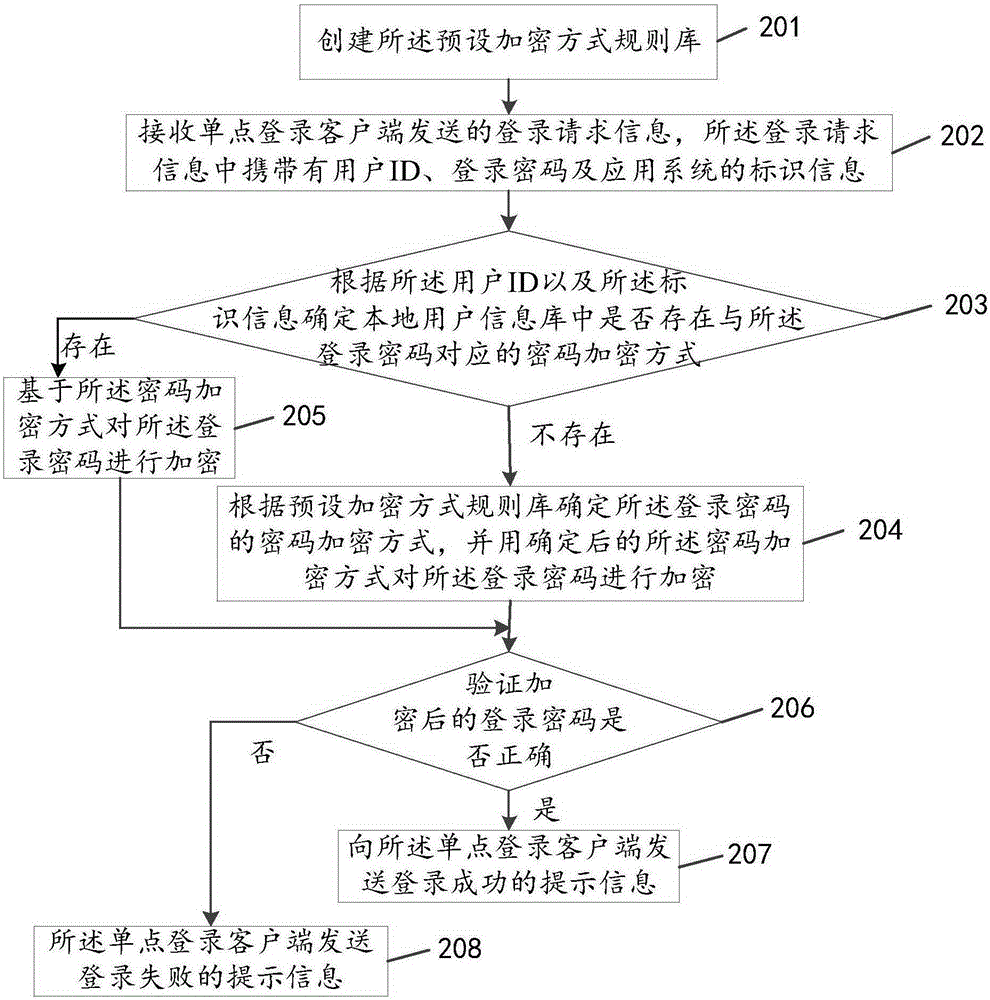
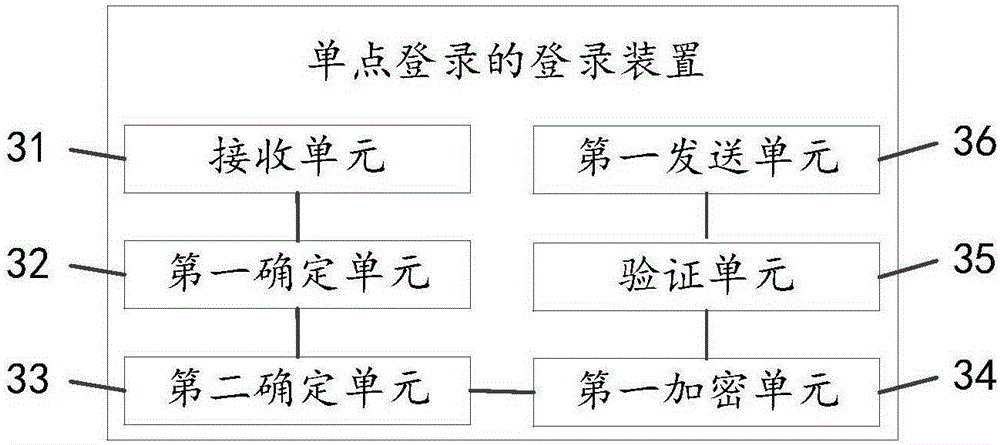
Single sign-on registration method and device
The invention discloses a single sign-on registration method and device, and relates to the communication technical field; the method mainly comprises the following steps; receiving sign-on request information sent by a single sign-on client end, wherein the sign-on request information comprises a user ID, a sign-on password, and application system identification information; determining whether a local user information database has a password encoding mode corresponding to the sign-on password or not according to the user ID and the identification information; if not, determining a password encoding mode of the sign-on password according to a preset encoding mode rule database, and using the determined password encoding mode to encode the sign-on password; verifying the encoded sign-on password is correct or not; if the encoded sign-on password is correct, sending prompt information of successful registration to the single sign-on client end. The single sign-on registration method and device are mainly applied to a process having various password encoding modes in the single sign-on system.
Owner:BEIJING GRIDSUM TECH CO LTD
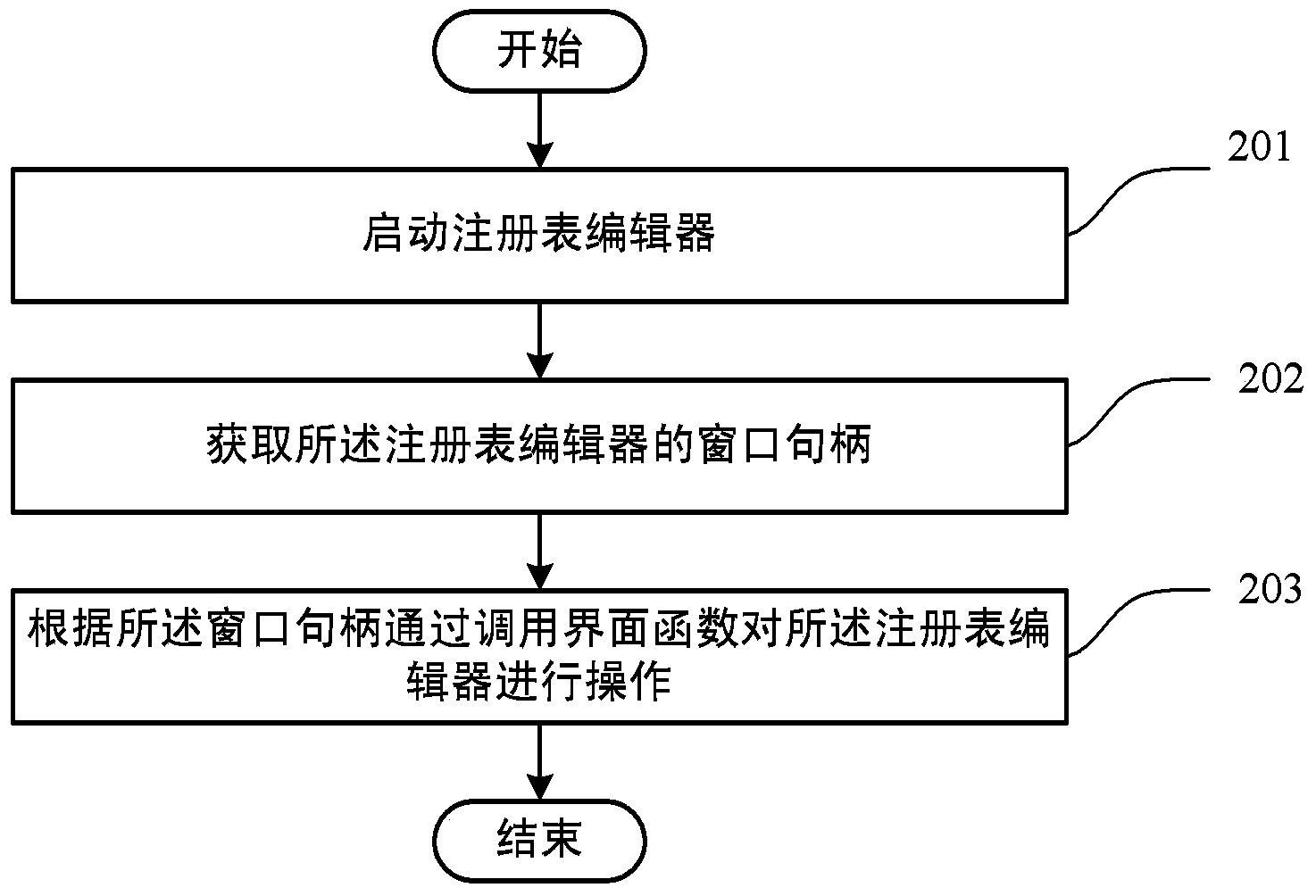
Method and device for operating registry
ActiveCN103593186AOperational securityAchieve legitimacyPlatform integrity maintainanceSpecific program execution arrangementsSoftware engineeringStart up
The invention discloses a method and device for operating a registry. The method comprises the steps of starting up a registry editor, obtaining a window handle of the registry editor and operating the registry editor by calling interface functions according to the window handle. Due to the facts that the registry editor is started up by calling the interface functions, and the registry is operated by calling the interface functions, the functional legitimacy of operating the registry can be achieved, security operation performed on the registry can be guaranteed, and meanwhile system security is ensured.
Owner:BEIJING QIHOO TECH CO LTD
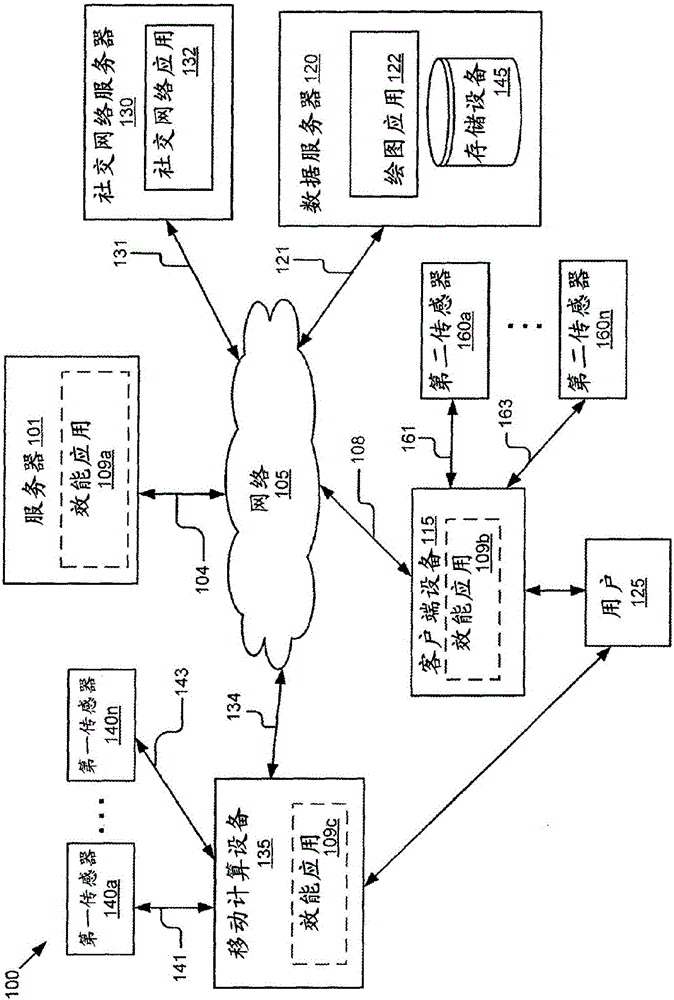
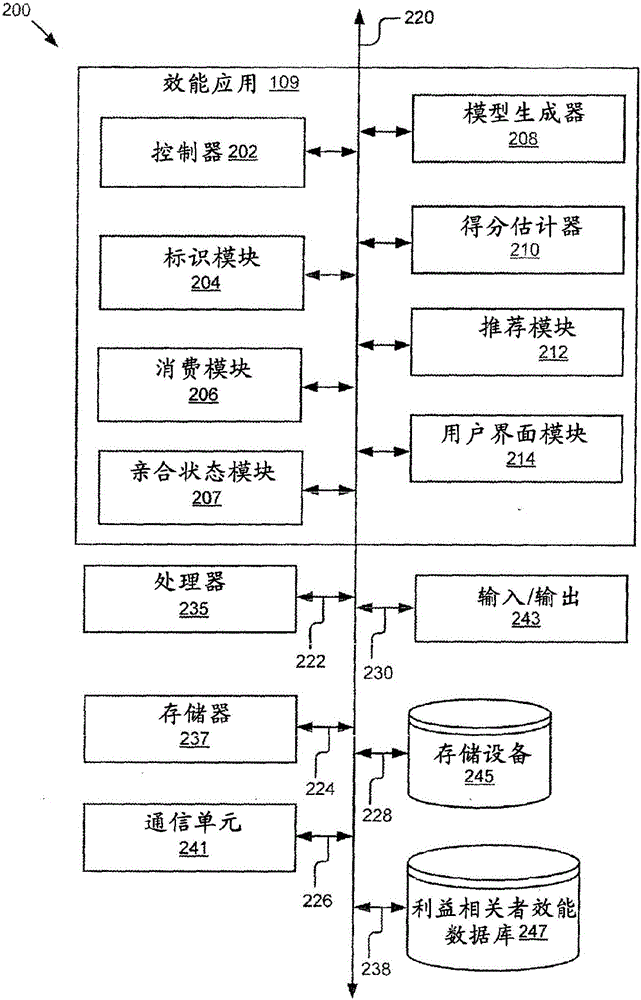
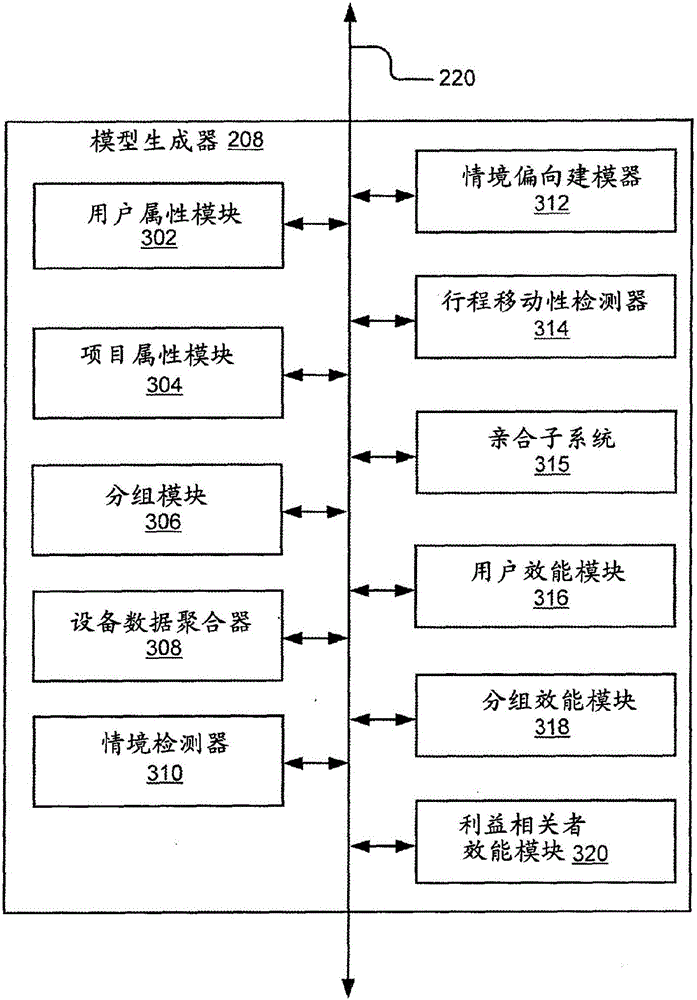
Content recommendation based on efficacy models
InactiveCN105723397AAchieve legitimacyAchieve securityGeographical information databasesMarketingEfficacyComputer science
The disclosure includes a system and method for providing recommendation items to users. The system includes a processor and a memory storing instructions that when executed cause the system to: receive identification input data associated with a user; identify the user using the identification input data; receive sensor data; determine a current situation associated with the user from one or more predefined situations described by predefined situation data and associated parameters; receive data describing a set of candidate items; generate a set of efficacy scores for the set of candidate items; eliminate one or more candidate items from the set of candidate items to obtain one or more remaining candidate items; rank the one or more remaining candidate items based on one or more associated efficacy scores; and provide one or more recommendation items to the user from the one or more ranked remaining candidate items.
Owner:TOYOTA JIDOSHA KK
An intelligent trademark auditing system and an application method thereof
InactiveCN109740009AImprove accuracyAchieve legitimacyStill image data queryingOffice automationTrademarkPattern recognition
The invention discloses an intelligent trademark auditing system and an application method thereof, and relates to the field of artificial intelligence application. The system comprises a terminal, acloud server, the terminal collects an image of a to-be-audited trademark; image preprocessing is carried out, extraction of feature values of images is carried out, the characteristic value of the image is uploaded to a cloud server; the cloud server carries out image recognition on the characteristic value of the image; analyzing and judging of the image according to the trademark judgment ruleare carried out; the cloud server judges the image which does not conform to the rule for the first time, and if not, the cloud server compares the image with the existing trademark library by usingthe image recognition model, analyzes the similarity between the image and the existing trademark library, judges whether the image conforms to the trademark judgment rule, and performs a subsequent corresponding process.
Owner:JINAN INSPUR HIGH TECH TECH DEV CO LTD
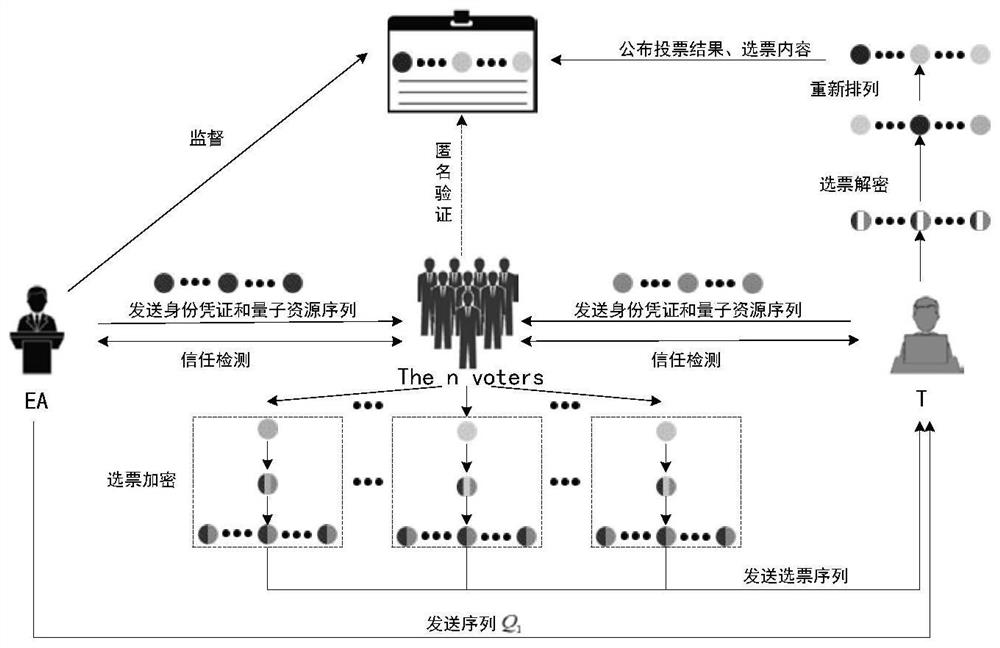
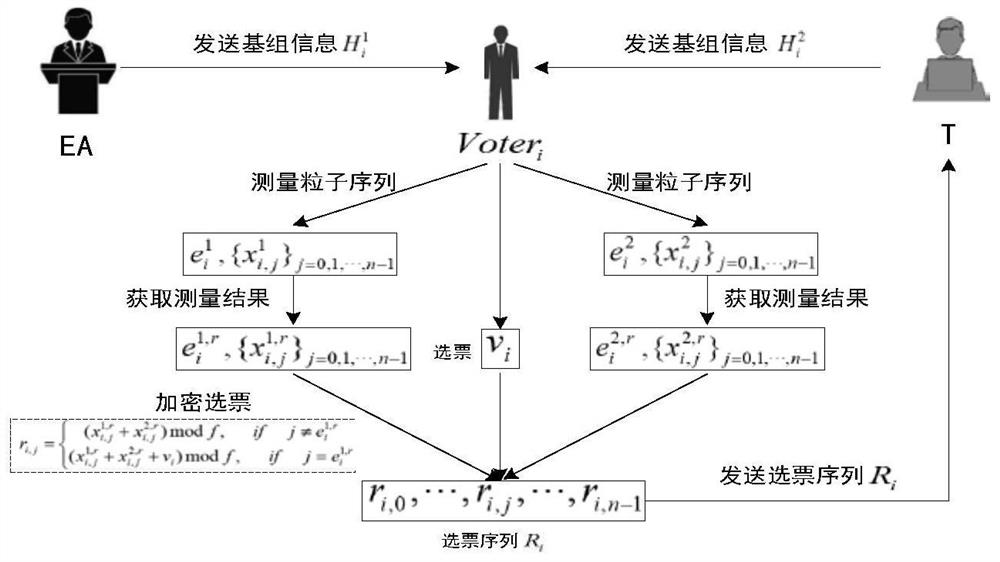
Quantum secret voting method based on single particle
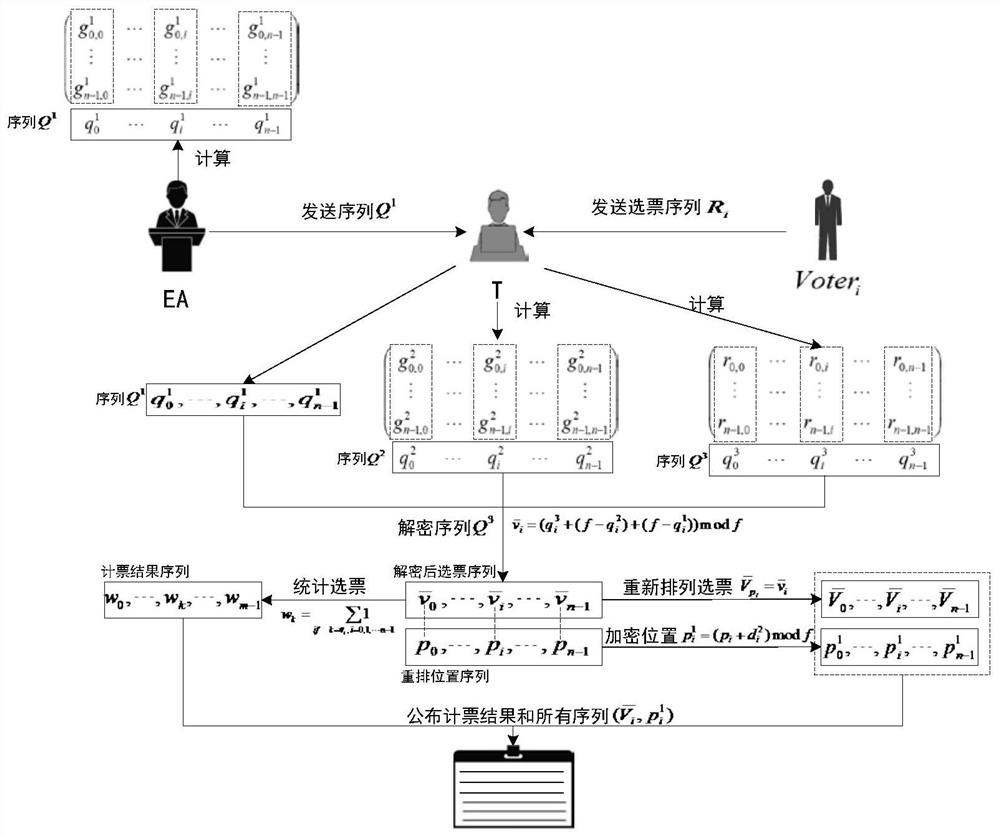
ActiveCN112511307ABreach of confidentialityAchieve fairnessVoting apparatusKey distribution for secure communicationQuantum informationInformation transmission
The invention relates to a quantum secret voting method based on a single particle. The quantum secret voting method is applied to a voting environment composed of a voting mechanism, a voter, a voterand an OADM. The OADMs are connected through optical fibers to form an annular classical quantum information fusion channel; wherein the voting mechanism, the voter and the voter are connected with an OADM and are connected to a classic quantum information fusion channel through the OADM to form a node so as to carry out information transmission between any nodes; the voting mechanism and the voter are assumed to be semi-honest, the voter is not limited to be semi-honest, in the voting process, the voting mechanism and the voter can check the identity of the voter, and identity certificates and quantum resources are distributed to the qualified voter; the voting institution and the voter respectively carry out trust detection with the voter, and the voter and the voter verify the identities of each other; the voter votes and sends the vote sequence to the vote counter; and after the voter completes voting, the voter counts votes and publishes a voting result.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
Method for ensuring data exchange safety
InactiveCN1905436BGuaranteed legalityIntegrity guaranteedUser identity/authority verificationData integritySecure transmission
The invention discloses a method for assuring data exchange and safe transmission, establishing connection between nodes through triple- handshaking mechanism between data exchange nodes, implementingID confirm of two exchange parties and negotiation of transmission secret key and establishing reliable connection for their data exchange; using global united transmission ID and random number to prevent malicious playback attack and confirming their IDs by exchanging random number and transmission secret key; using RBAC policy to make access control and implementing legality of application system access of a user; by comparing data abstract values carried in data exchange course, assuring data integrity; adopting global unique transmission secret key to make data exchange, avoiding overmanysecret key negotiation courses, implementing data exchange confidentiality and besides assuring data transmission efficiency.
Owner:BEIHANG UNIV
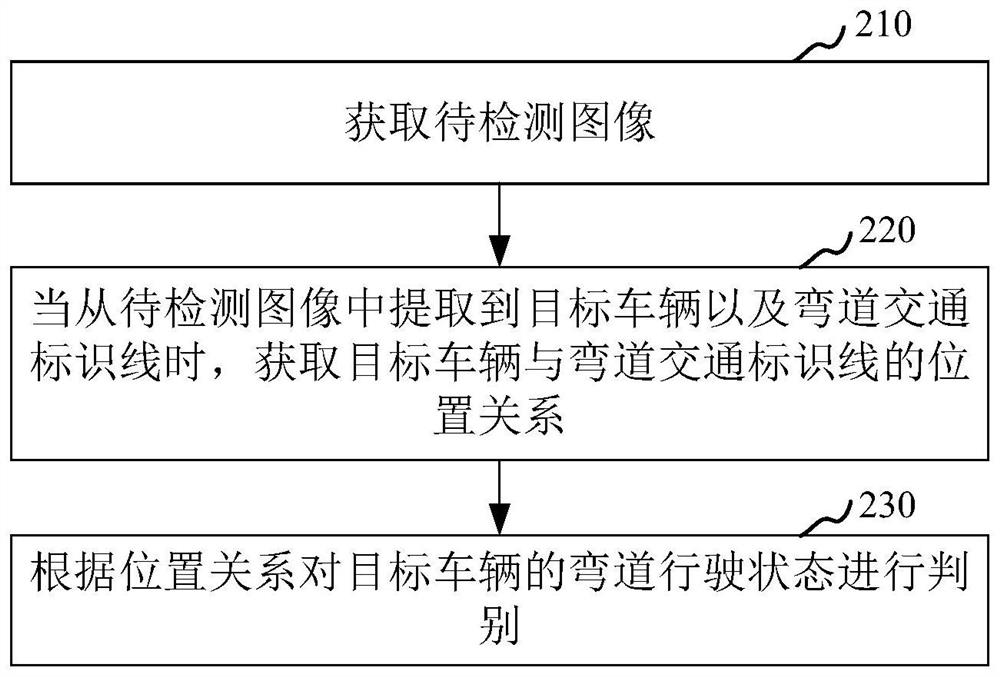
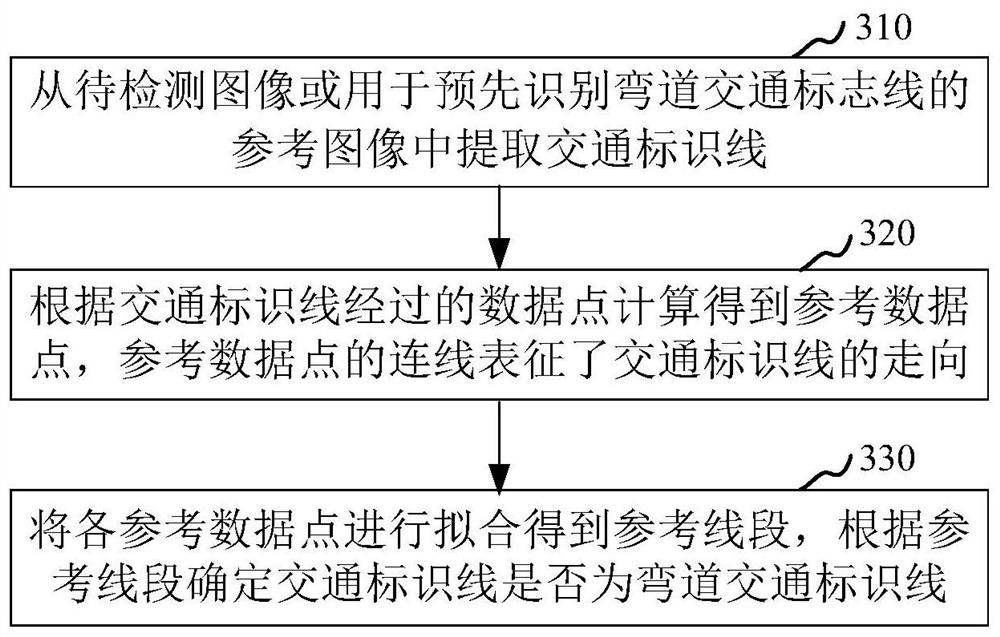
Vehicle curve driving state judgment method and device, computer equipment and medium
PendingCN112183214AImprove recognition accuracyImprove recognition efficiencyCharacter and pattern recognitionNeural architecturesTraffic signReal-time computing
The invention relates to the technical field of computers, in particular to a vehicle curve driving state judgment method and device, computer equipment and a storage medium. The method comprises thesteps of obtaining a to-be-detected image; when the target vehicle and the curve traffic sign line are extracted from the to-be-detected image, obtaining a position relationship between the target vehicle and the curve traffic sign line; and judging the curve driving state of the target vehicle according to the position relationship. By adopting the method, the judgment accuracy of the running state of the vehicle running on the curve can be improved.
Owner:上海眼控科技股份有限公司
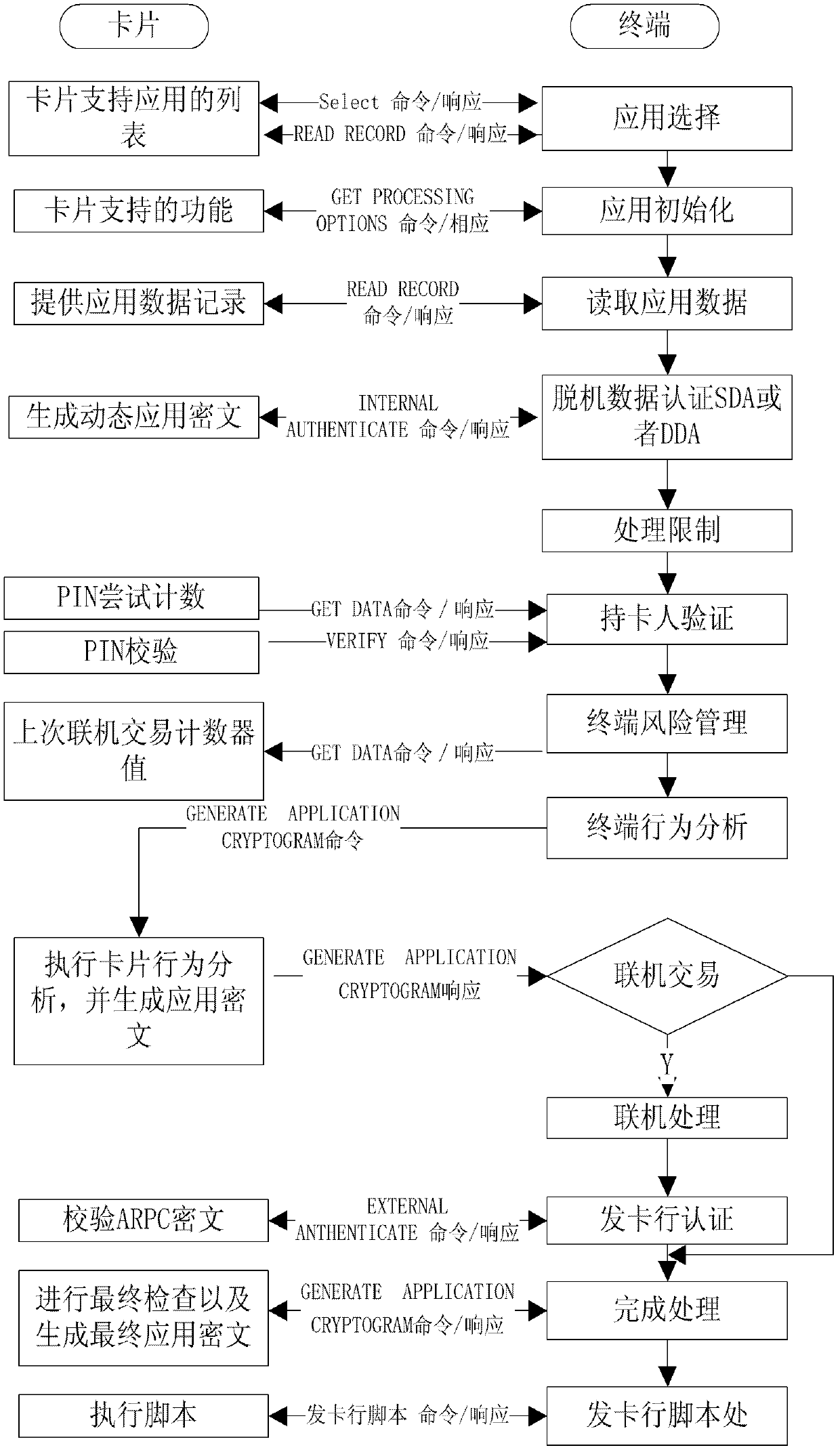
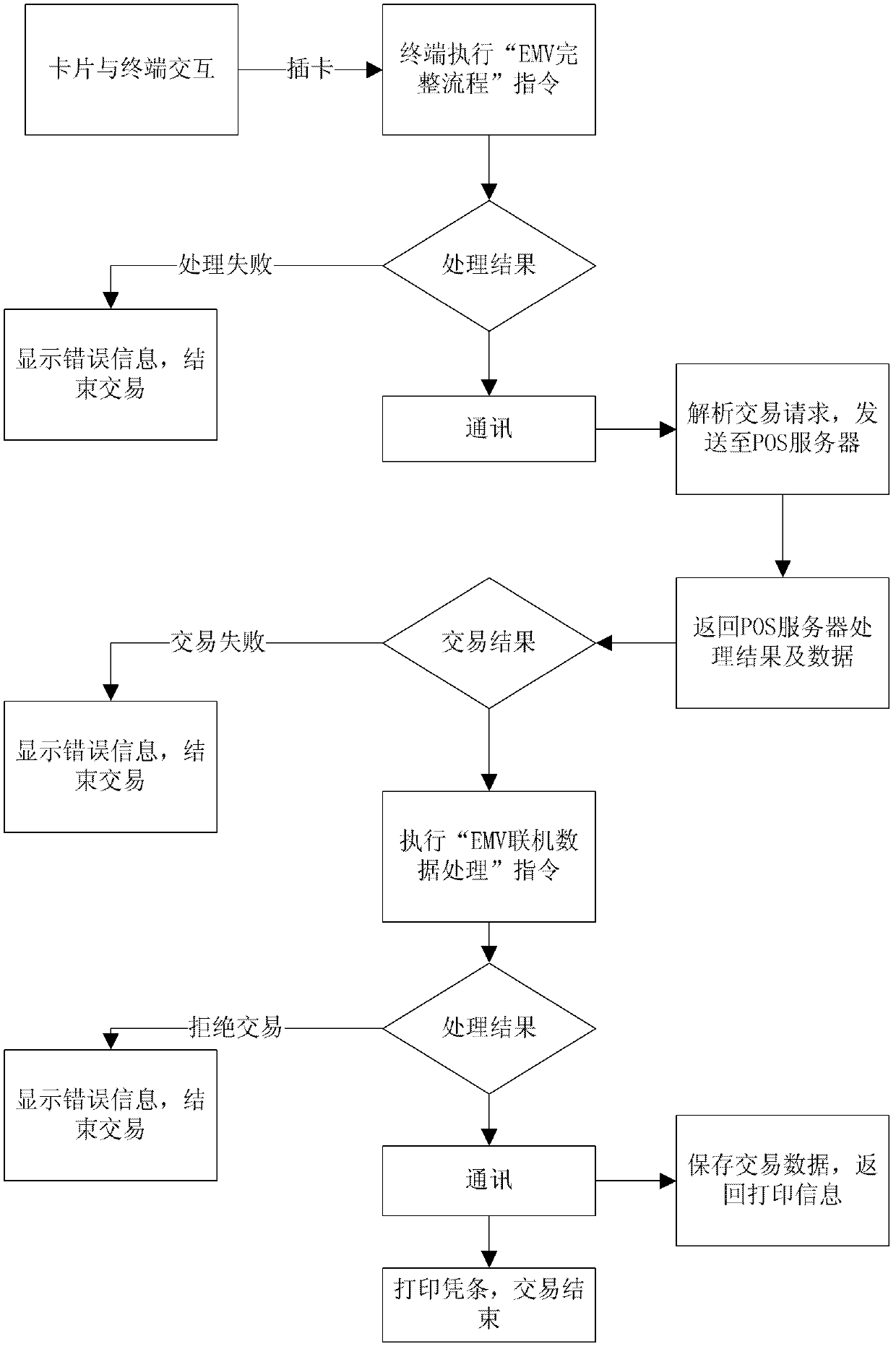
Telephone payment terminal trading method and telephone payment terminal system
ActiveCN102629355AAchieve legitimacyAchieve conveniencePoint-of-sale network systemsFinancial transactionComputer terminal
The invention provides a telephone payment terminal trading method and a telephone payment terminal system. The telephone payment terminal trading method is characterized by: firstly, executing a first instruction, completing interaction between the terminal and an IC card and outputting trading request data; sending the trading request data to a telephone payment gateway, and after analyzing, sending to a POS server, wherein the POS server carries out trading processing and determines whether the trading is successful, if the trading is successful, returning an on-line data result and if the trading is not successful, ending the trading; executing second instruction and processing the on-line data result; according to a trading authentication result and a parameter set in the card, determining whether to reject the trading; if the trading is rejected, displaying error information and ending the trading, if the trading is accepted, sending trading result data to the telephone payment gateway, wherein the telephone payment gateway stores the trading result data sent by the terminal and returns trading slip data. By using the above mode, IC card trading can be realized on the telephone payment terminal.
Owner:FUJIAN LANDI COMML EQUIP CO LTD
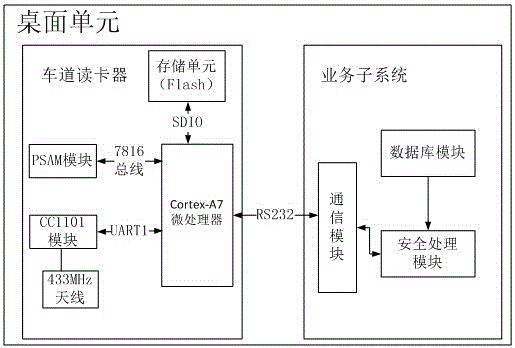
Desktop unit and safety method applied to path identification system
InactiveCN106407819AAchieve legitimacyAchieve effectivenessDigital data protectionInternal/peripheral component protectionRadio frequencyCard reader
The invention discloses a desktop unit and a safety method applied to a path identification system. A lane card reader in the desktop unit comprises a Cortex-A7 micro-processor module, a PSAM safety authentication module, a storage unit, a CC1101 radio-frequency module and an antenna; and a service sub-system comprises a communication module, a database module and a safety processing module. The lane card reader in the desktop unit is equipped with the PSAM safety authentication module; valid path identification information, coordinate fitting information and the like are stored in a database of the service sub-system; therefore, validity judgement of a vehicular unit is realized; validity judgement of a path identifier in the vehicular unit is realized; effective judgement of the path identifier in the vehicular unit is realized; and the safety of the system is improved through a series of safety interaction rules with other equipment in the system.
Owner:TIANJIN 712 COMM & BROADCASTING CO LTD
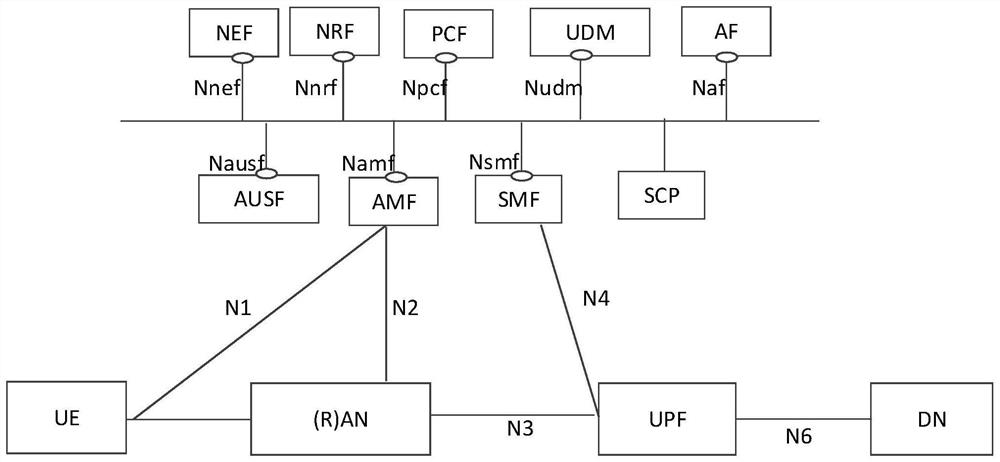
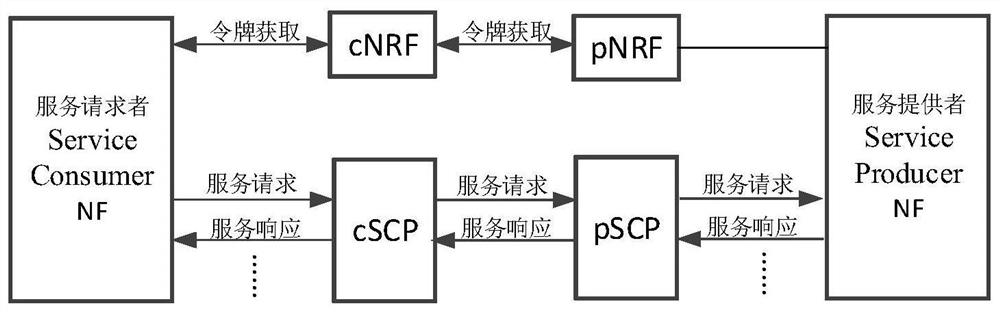
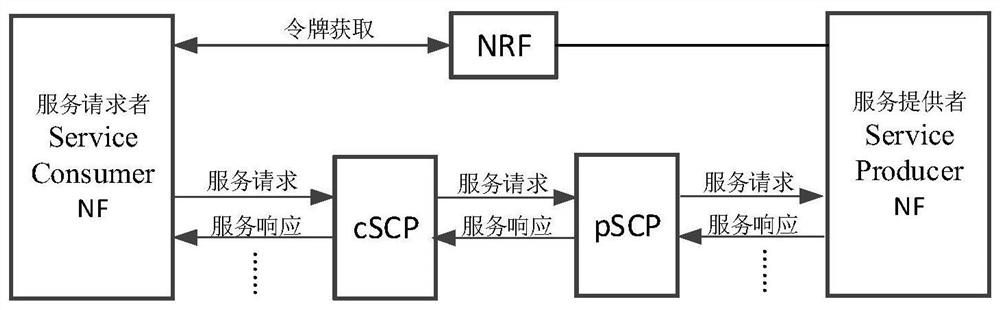
Servitization architecture authorization method
ActiveCN112822678AAchieve legitimacyUser identity/authority verificationSecurity arrangementService providerNetwork element
The embodiment of the invention discloses a service architecture authorization method and device. The method comprises the steps: generating a token by a first network storage function network element after receiving a token request, and writing the service communication proxy (SCP) certificate information in the token by the first network storage function; returning the token carrying the certificate information to a sender of the token request; receiving a service request by the service provider network function, wherein the service request carries a token containing the SCP certificate information or carries the token and a certificate information verification result; if the service request does not contain a certificate information verification result, verifying the certificate information of the SCP by the service provider network function; and if the verification result is successful, continuing the authorization process. According to the technical scheme, the problem that after a service communication agent is introduced, the network function of a service provider cannot verify the certificate information in the token can be solved.
Owner:HUAWEI TECH CO LTD
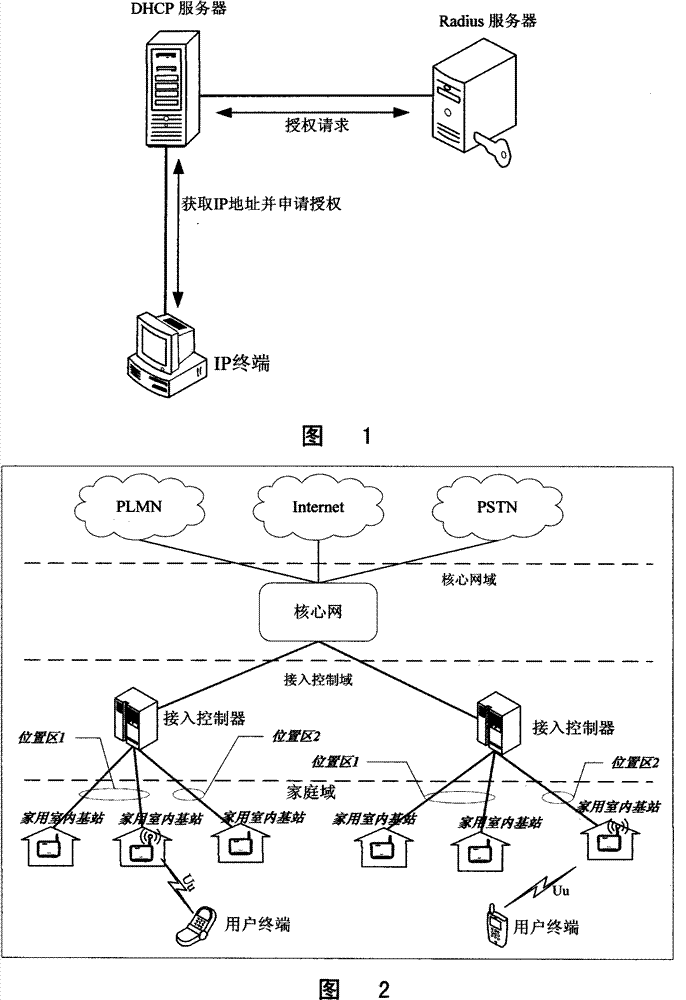
Managing method for switching in mobile communication home use indoor base station
ActiveCN101447973BAchieve legitimacyAchieve self-managementData switching by path configurationInformation interoperabilityRelevant information
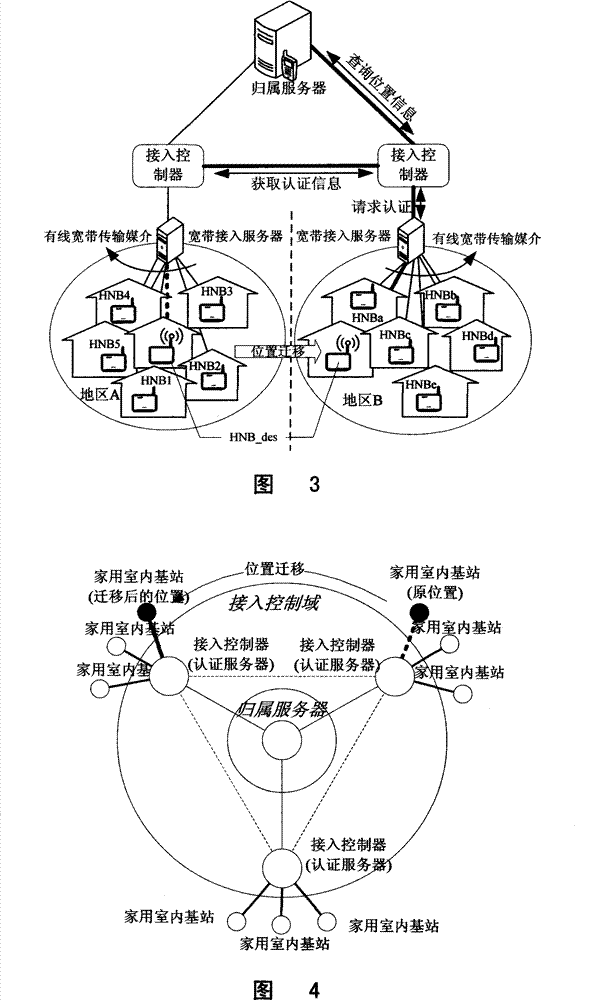
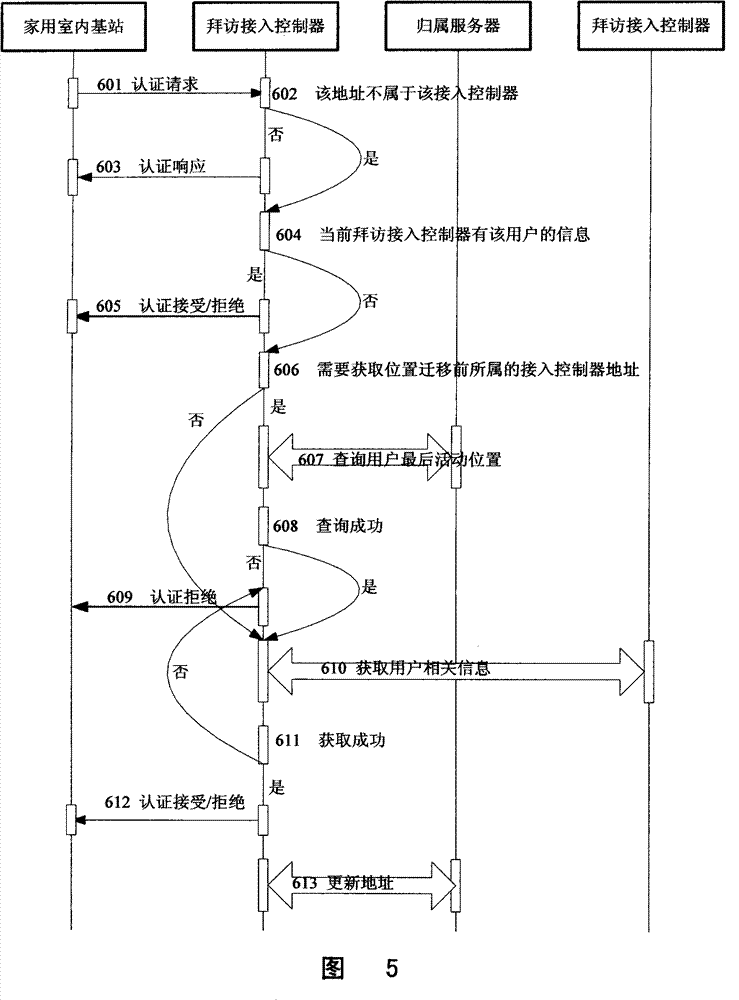
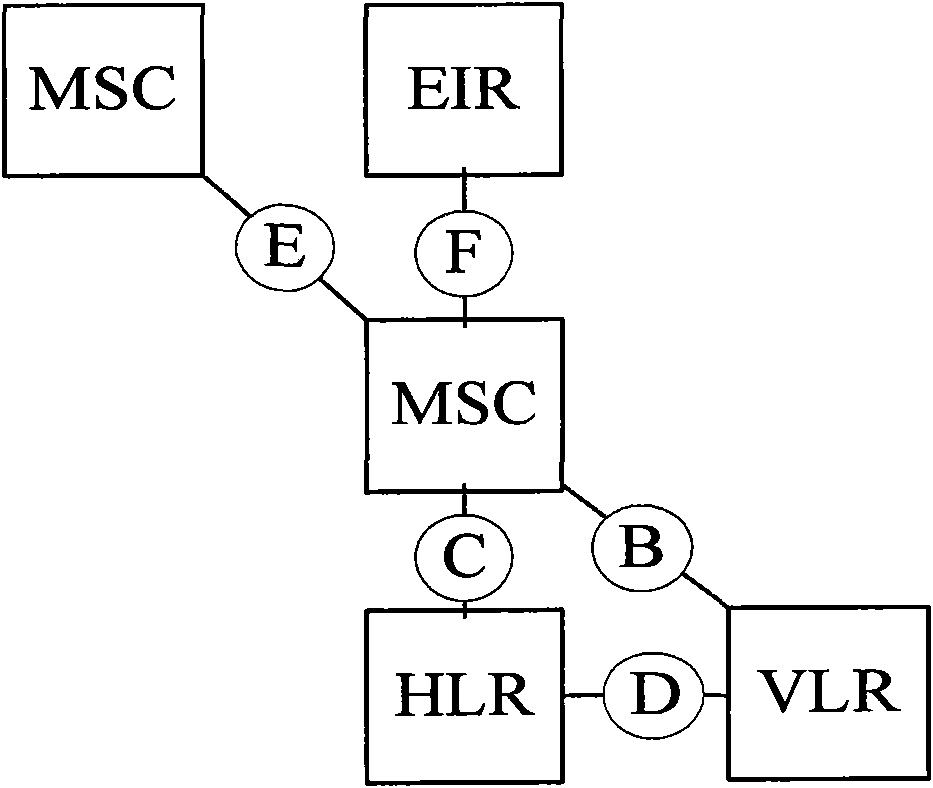
The invention relates to a method for switching in and managing a mobile communication home use indoor base station, which is characterized in that a home use indoor base station is switched into an access controller by a wired broadband network, establishes upper and lower hierarchical information intercommunication relation with a belonging server in the network of the home use indoor base station by the access controller, and establishes information communication interchange intercommunication relation with other access controller by the belonging server. Information communication is carried out by interlamination inquiry and same layer acquiring form; namely, when the geographic position of the home use indoor base station is moved from the administrative area of the access controller to the administrative area of the other access controller, the new access controller acquires relative information of the home use indoor base station from a visiting access controller before position moving. The home use indoor base station enters into the administrative area of the new access controller in the premise of without manual intervention, thus realizing intelligent moving of the home use indoor base station.
Owner:MEDIATEK INC
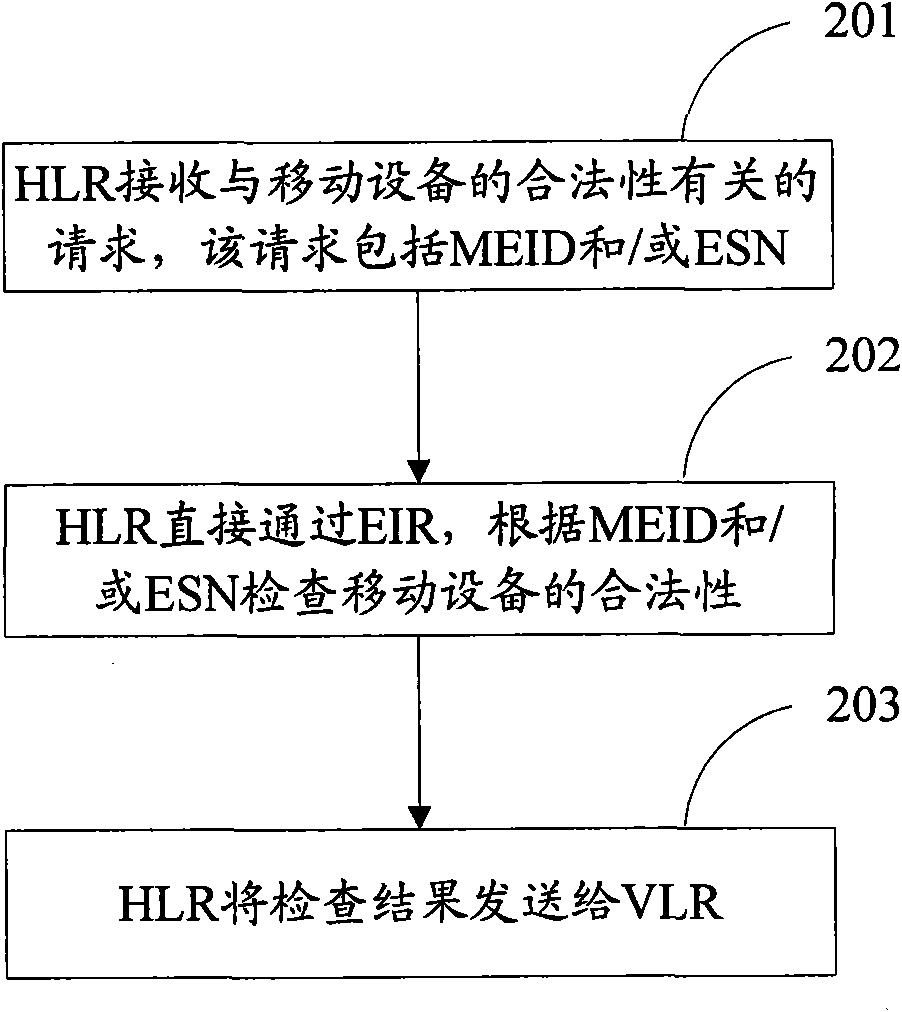
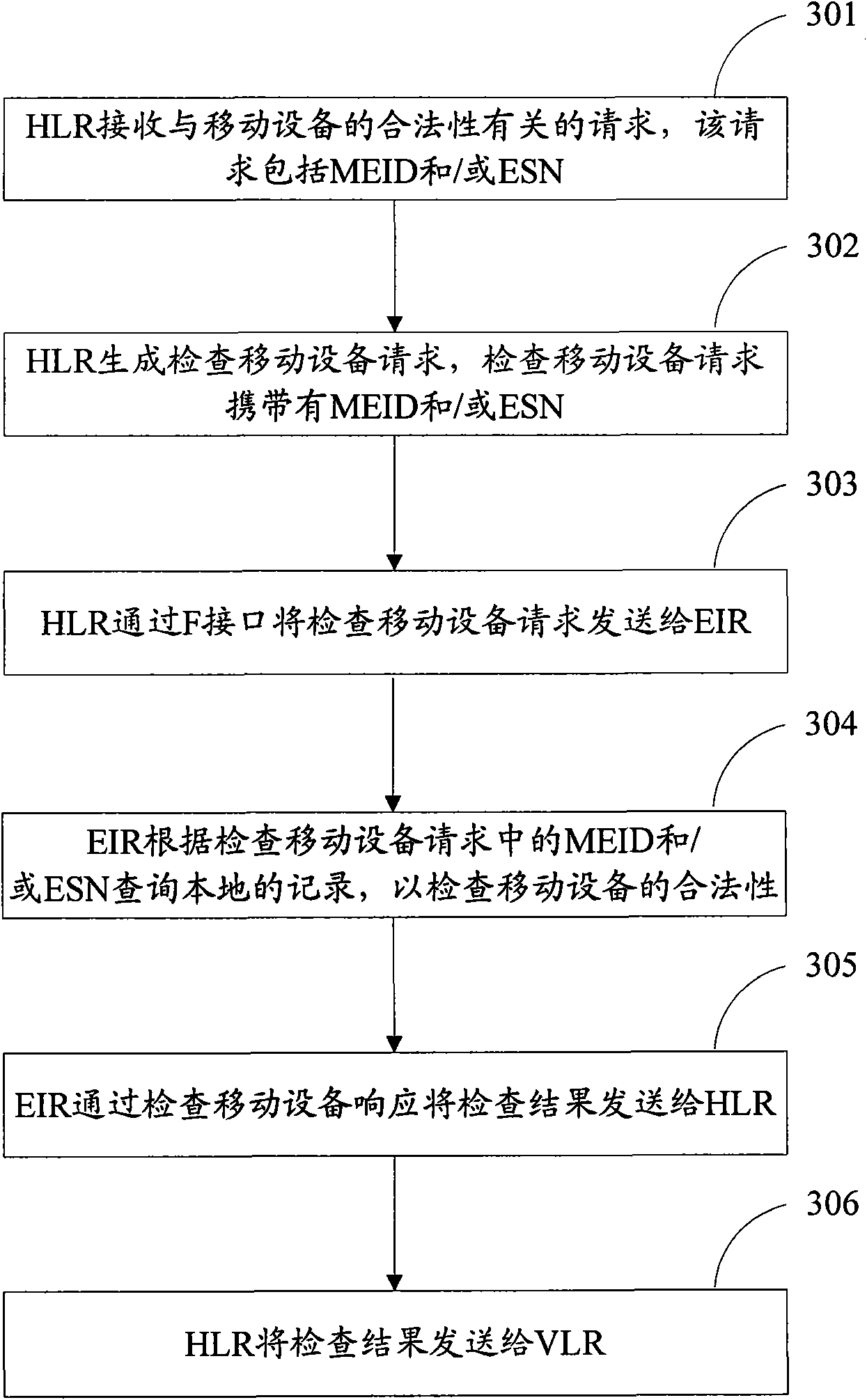
Method for detecting Mobile device and device
InactiveCN101577898AAchieve legitimacySave signaling resourcesNetwork data managementMobile deviceComputer science
The invention discloses a method for detecting a mobile device, aiming at realizing legitimate detection of the mobile device. The method comprises the following steps: HLR receives requests related to the legitimacy of the mobile device; the requests comprise MEID and / or ESN; HLR directly detects legitimacy of the mobile device according to MEID and / or ESN via EIR and sends the detection results to VLR. The invention further discloses HLR and EIR for realizing the method of the invention.
Owner:ZTE CORP
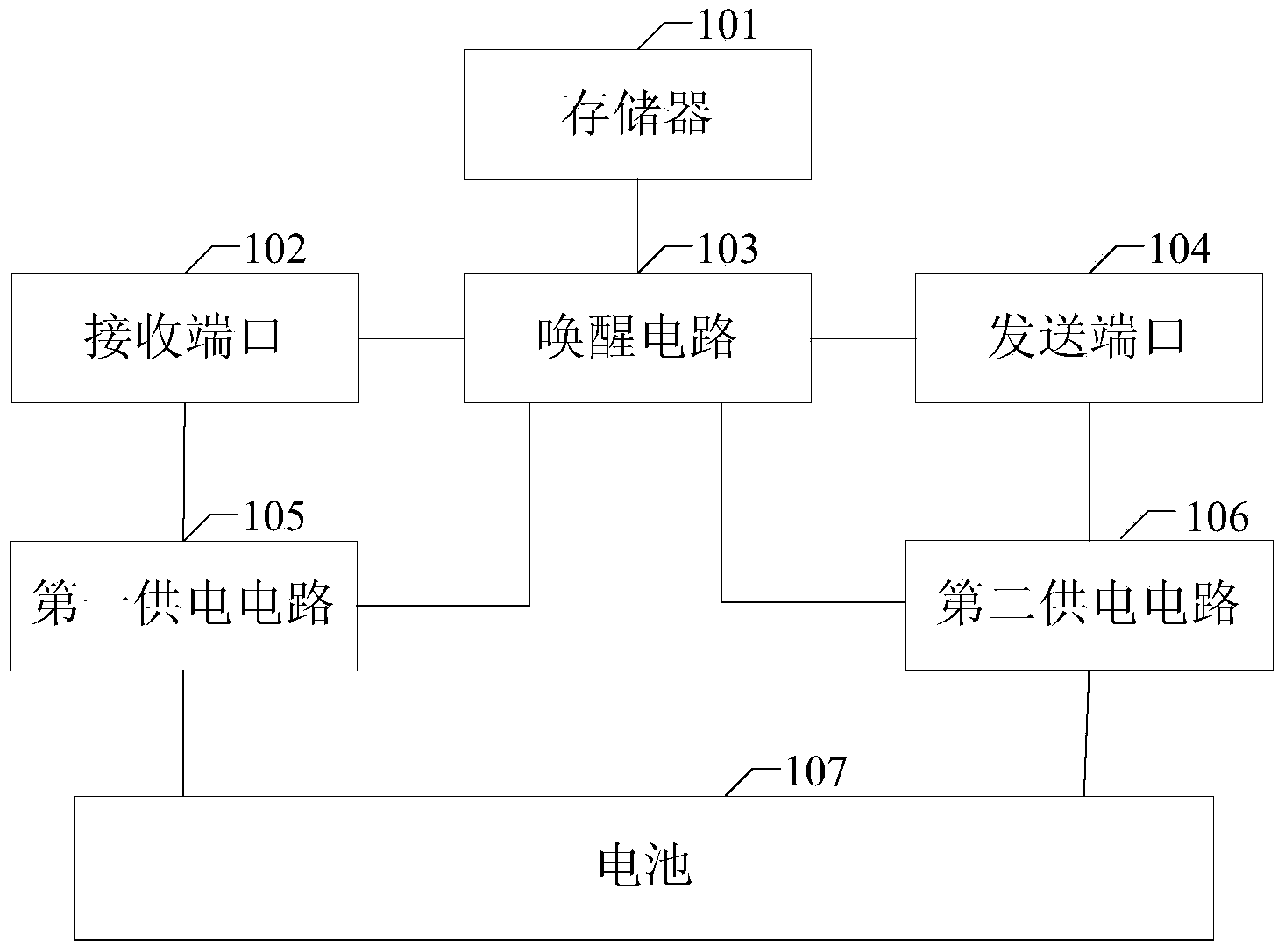
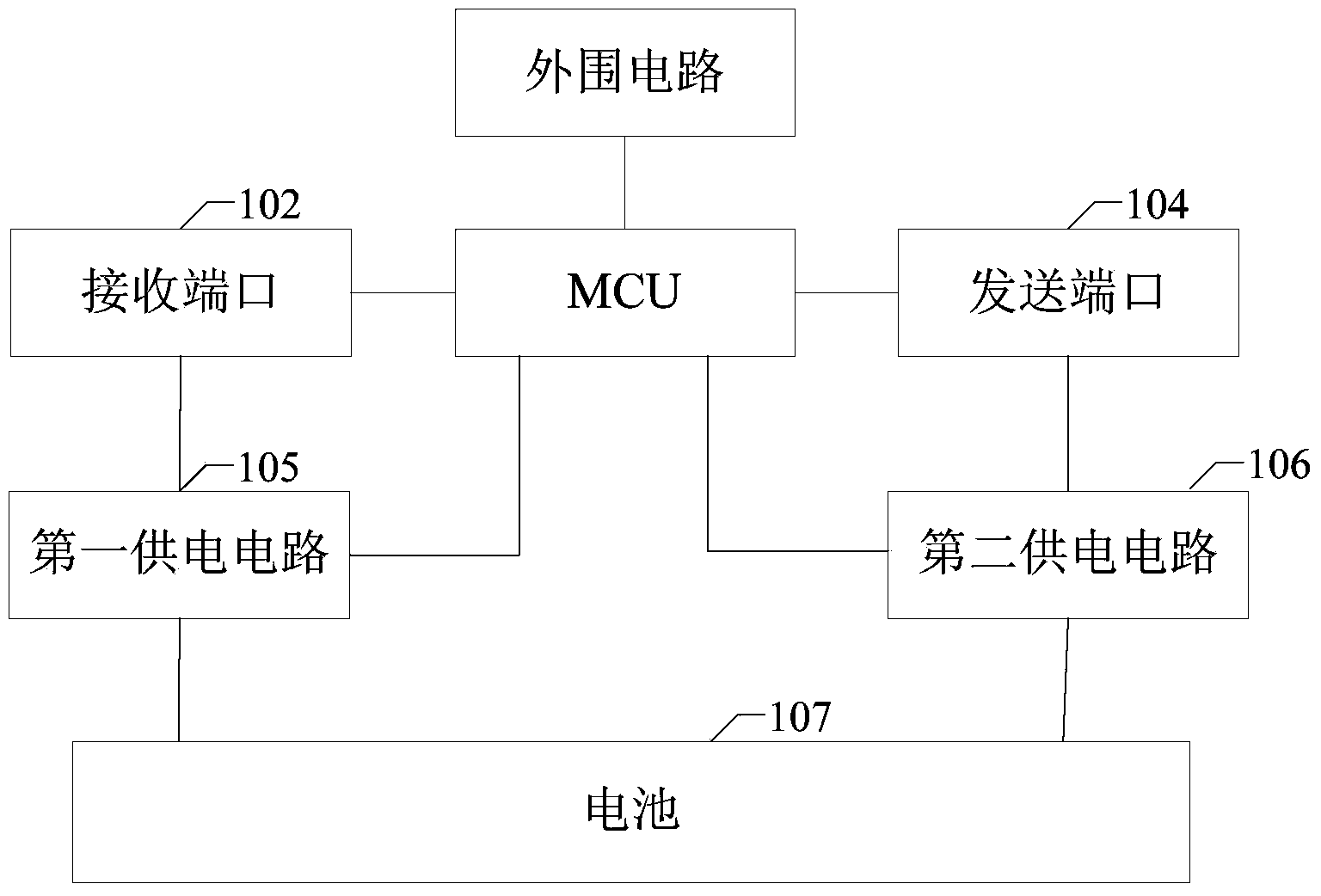
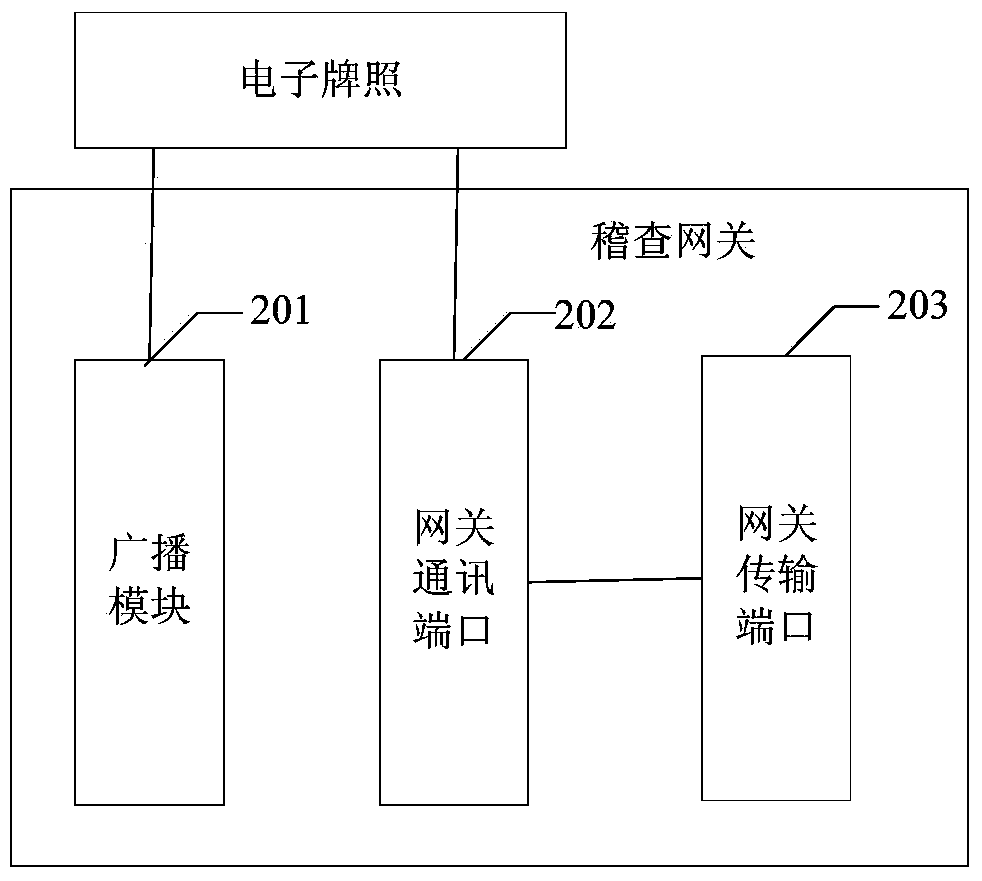
Electronic license plate, inspection gateway and information monitoring system
InactiveCN103778586ACheck legalityMonitoring implementationData processing applicationsSensing record carriersEngineeringInformation monitoring
The invention discloses an electronic license plate, an inspection gateway and an information monitoring system. The electronic license plate comprises a memorizer, a receiving port, an awakening circuit, a sending port, a first power supply circuit and a second power supply circuit, wherein the memorizer stores information to be monitored, the distance between the receiving port and the inspection gateway is set within the setting range, the receiving port receives the awakening broadcast transmitted by the inspection gateway and transmits the broadcast to the awakening circuit, and the first power supply circuit is connected with the receiving port and the awakening circuit and provides power for the receiving port and the awakening circuit. After receiving the awakening broadcast, the awakening circuit is communicated with the second power supply circuit and transmits the information to be monitored to the sending port. After the second power supply circuit conducts power supply, the sending port transmits the received information to be monitored to the inspection gateway. According to the electronic license plate, the inspection gateway and the information monitoring system, when the distance between the inspection gateway and the electronic license plate is within the set range, the electronic license plate can receive the awakening broadcast and transmits the information to be monitored, otherwise, the electronic license plate enters in the dormant state, the consumption of the electric quantity is reduced, and the service life is prolonged.
Owner:ZHEJIANG TENDENCY TECH
Position locating and verifying methods and system of wireless access device and attribution server
ActiveCN101674566BAchieve legitimacyAchieving detection legitimacyNetwork topologiesSecurity arrangementAccess networkIp address
The embodiment of the invention discloses a position locating method of a wireless access device, comprises the following steps: inquiring a CLF according to an IP address of an AP so as to acquire an ALLI of an AP access network, wherein the ALLI is used for identifying a line position of the AP access network; and confirming the position of the AP by an ALLI identifier. Meanwhile, the inventionalso provides a position verifying method of the wireless access device, comprising the following steps: inquiring the CLF according to the IP address of the AP so as to acquire the ALLI of the AP access network; and when the acquired ALLI of the AP access network is same as a stored ALLI of the AP access network, the position of the AP does not change. The embodiment of the invention also provides an attribution server and a system which can accurately locate and verify the position of the AP, thereby realizing the validity for the position detection of the AP.
Owner:HUAWEI TECH CO LTD
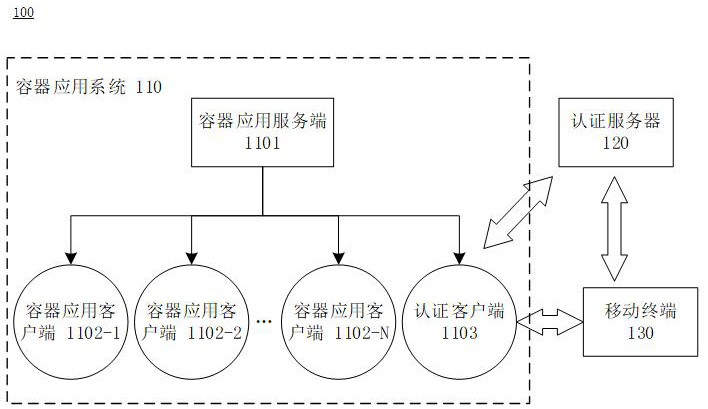
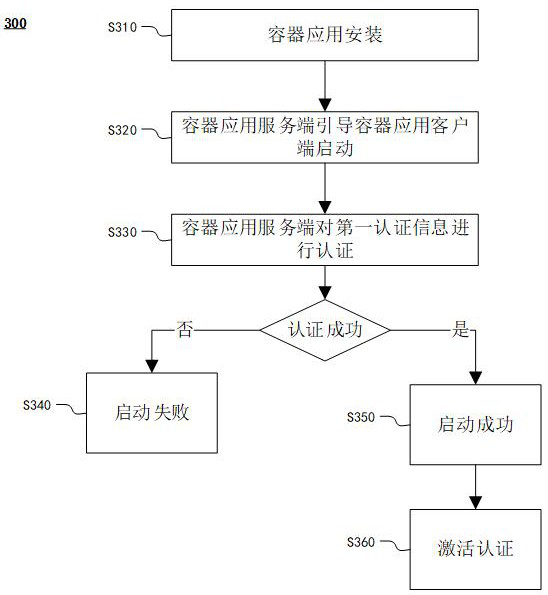
Container application authentication method and system, computing device and readable storage medium
ActiveCN112988333AAvoid the disadvantages of arbitrary copyingAvoid startingComputer security arrangementsSoftware simulation/interpretation/emulationApplication serverEngineering
The invention discloses a container application authentication method, which is suitable for being executed in a container application authentication system. The container application authentication system comprises an authentication server and a container application system, the container application system comprises a plurality of container application clients, a container application server and an authentication client, and the method comprises the following steps: starting the container application clients, generating a first authentication message at the container application client; authenticating the first authentication message through the container application server; if the first authentication message passes the authentication, determining that the container application client is successfully started; the authentication client obtaining the activation sequence code input by the user and authenticating the activation sequence code through the authentication server; if the activation sequence code passes the authentication, the authentication server sending authorization information to the authentication client; and the authentication client activating the container application client according to the authorization information. The invention also discloses a corresponding system, a computing device and a readable storage medium.
Owner:武汉深之度科技有限公司
Construction method of division protocol based on cryptology in distributed computation
InactiveCN101729554BAchieve efficiencyTo achieve fault toleranceKey distribution for secure communicationFault toleranceRandomization
The invention discloses a construction method of a division protocol based on cryptology in distributed computation, belonging to the field of information safety. The formation method is characterized in that (1) each member who participates in the computation dependently selects a random number and sends the shared value of the random number to all parties for local hybrid operation so as to obtain a public random shared value; (2) each member randomizes the sharing of an input secret value b by using the public random shared value and reconstructs the randomizing value of the secret value btogether; (3) each member inspects whether a randomizing result of the secret value b is inverse or not, if so, the member solves an inverse element of the randomizing value of the secret value b andthen de-randomizes the inverse element to obtain the inverse sharing of the secret value b by utilizing the public random shared value; (4) each member utilizes the obtained inverse sharing of the secret value b and a sharing executive multiplication protocol of a secret value a to obtain the sharing of the a / b; and (5) each member reconstructs a real computing result by mutually exchanging the obtained sharing of the a / b. The invention has the characteristics of high efficiency, fault tolerance and safety.
Owner:PEKING UNIV
Electronic evidence storage and collection system and method based on block chain
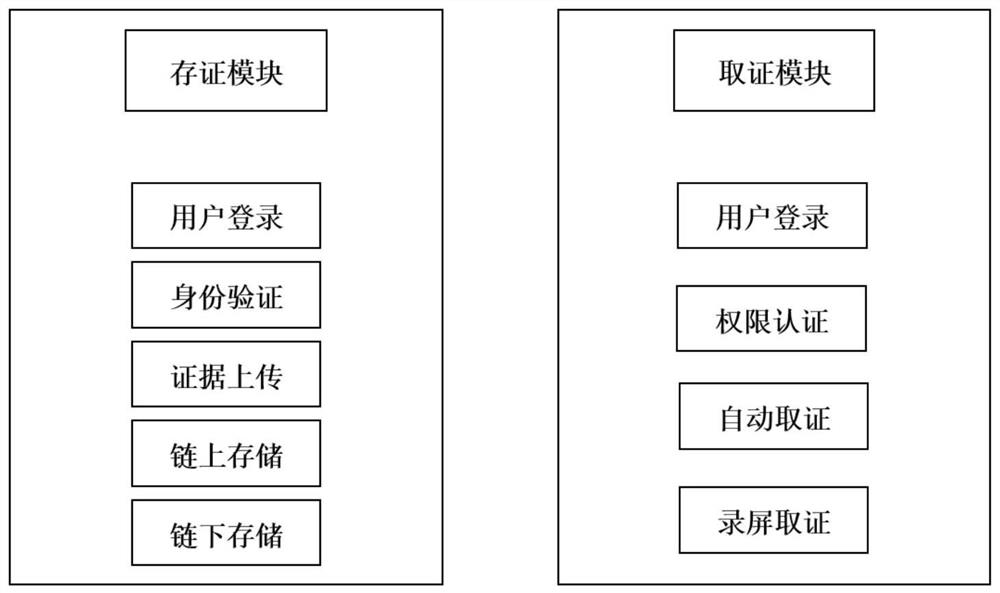
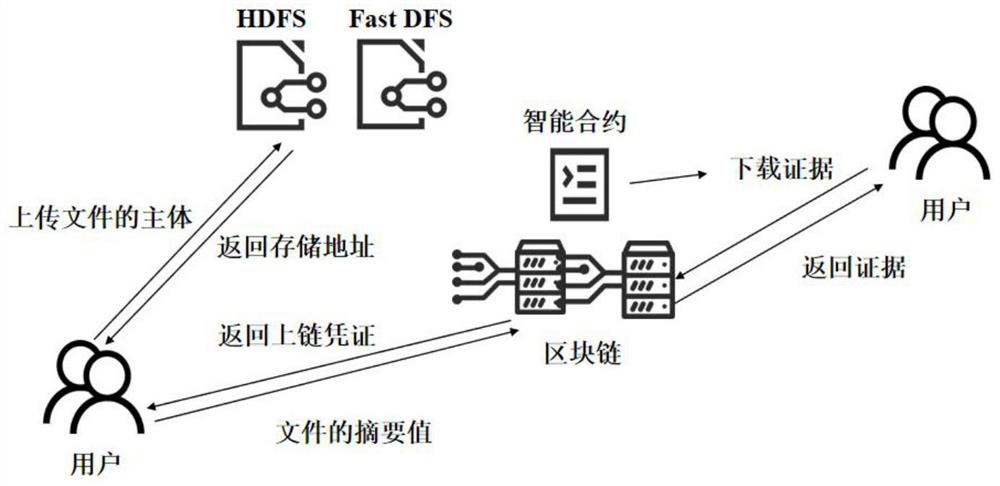
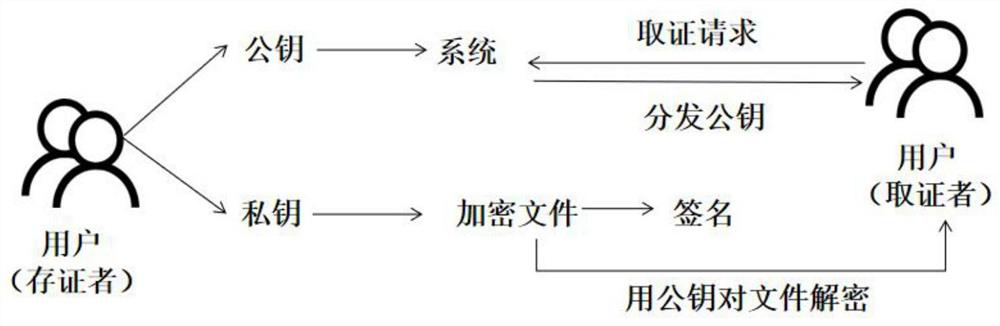
PendingCN114666353AReduce storage pressureImprove storage efficiencyTelevision system detailsColor television detailsStorage efficiencyDistributed File System
The invention discloses an electronic evidence storage and collection system and method based on a block chain. The system comprises an evidence storage module and an evidence collection module. The evidence storage module comprises a first user login module, an identity verification module, an evidence uploading module, an on-chain storage module and an off-chain storage module; the evidence obtaining module comprises a second user login module, an authority authentication module, an automatic evidence obtaining module and a screen recording evidence obtaining module. Various evidences are uploaded through the evidence storage module, and the main body part of the file is stored in the distributed file system under the chain through the on-chain storage module and the off-chain storage module, so that the block chain storage pressure is relieved, and the storage efficiency of the system is improved. According to the method, evidence obtaining operation is performed through the evidence obtaining module, illegal users are filtered through the authority authentication module, automatic downloading and storage of evidences are realized through automatic evidence obtaining and screen recording evidence obtaining, screen recording recording is performed on the whole evidence obtaining process, and the whole recording process is uploaded to the block chain, so that legality and security of the whole electronic evidence obtaining process are realized.
Owner:NANJING UNIV OF POSTS & TELECOMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com