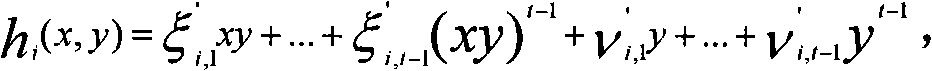Cryptography distributed calculation and step-by-step verification method with fault-tolerant function
A distributed computing and fault-tolerant technology, applied in the direction of error prevention, digital transmission system, electrical components, etc., can solve the problems of active attack, unable to support computing, and not considering the continuity of computing, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
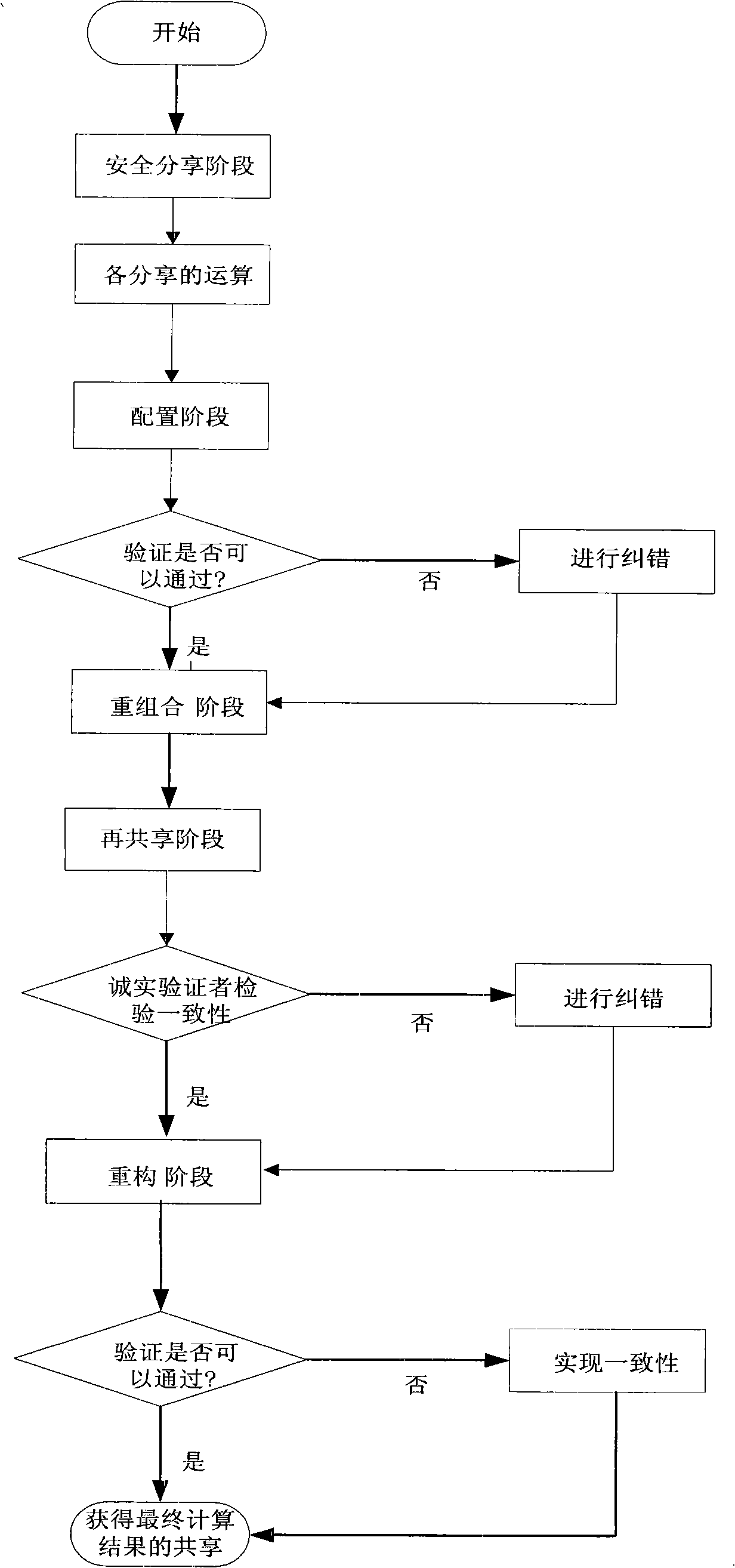
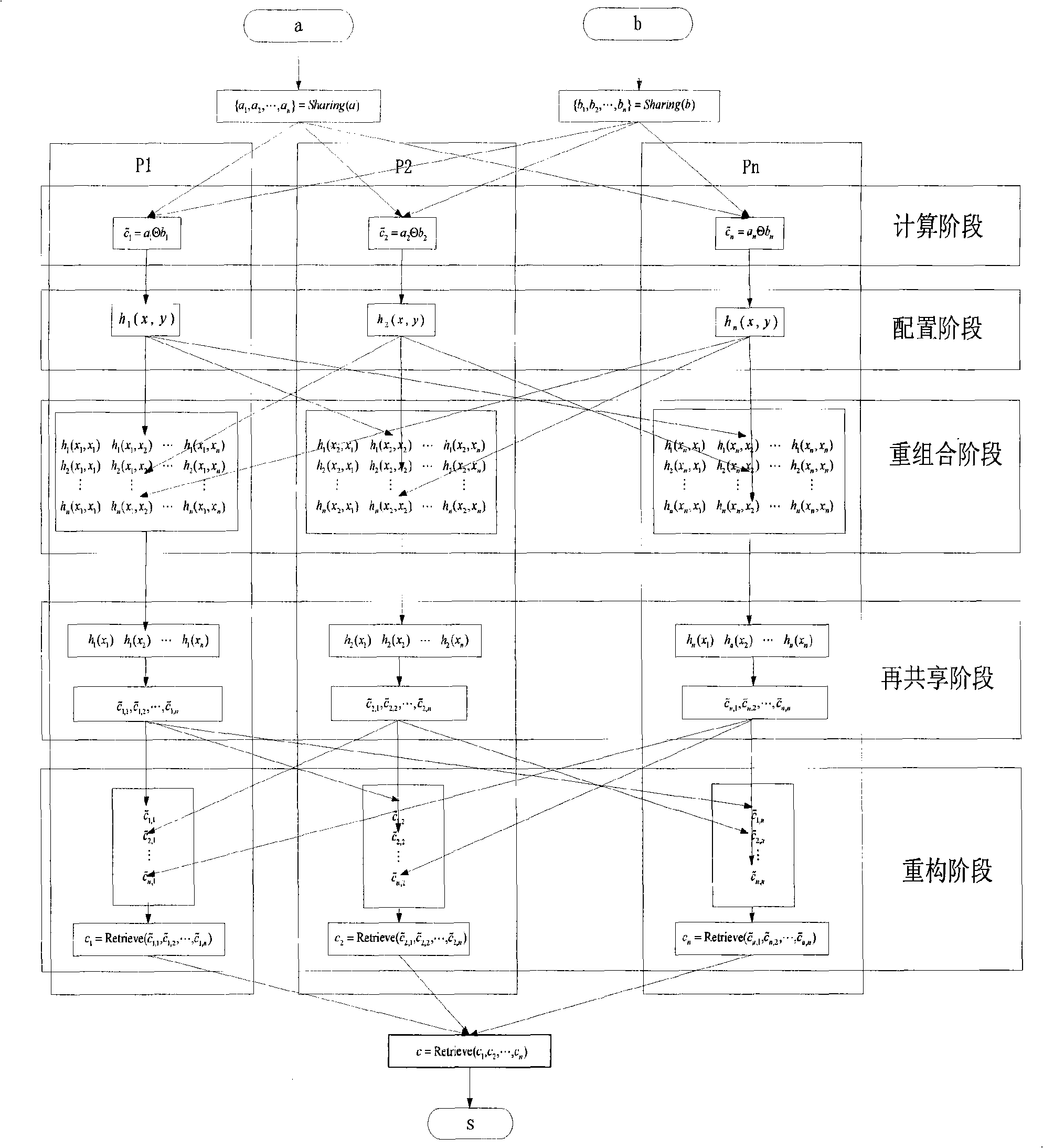
[0066] The operation process in the present invention will be further described below in conjunction with specific embodiments and schematic diagrams. This process is applicable to other distributed algebraic operations, such as addition, subtraction, multiplication, multiplication, division, and exponentiation.
[0067] In this embodiment, it is assumed that there are n members participating in the calculation, there is a link between any two members, and assuming that the network delay is negligible, each member has a unique identity ID i , and the identity can be expressed as a positive number x i used for calculations. At the same time, it is assumed that there may be at most t members in the above system that can be controlled by the adversary or have equipment or network failures, and satisfy n≥3t+1.
[0068] In order to realize multi-party computing, it is first necessary to distribute the confidential computing input to each member. Here, a sharing scheme based on t-d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com