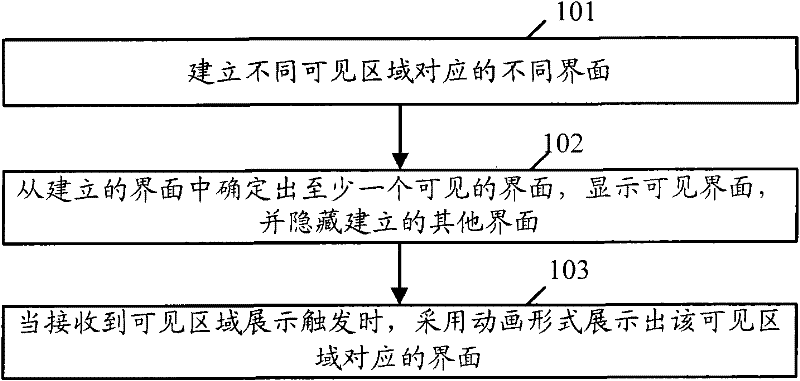
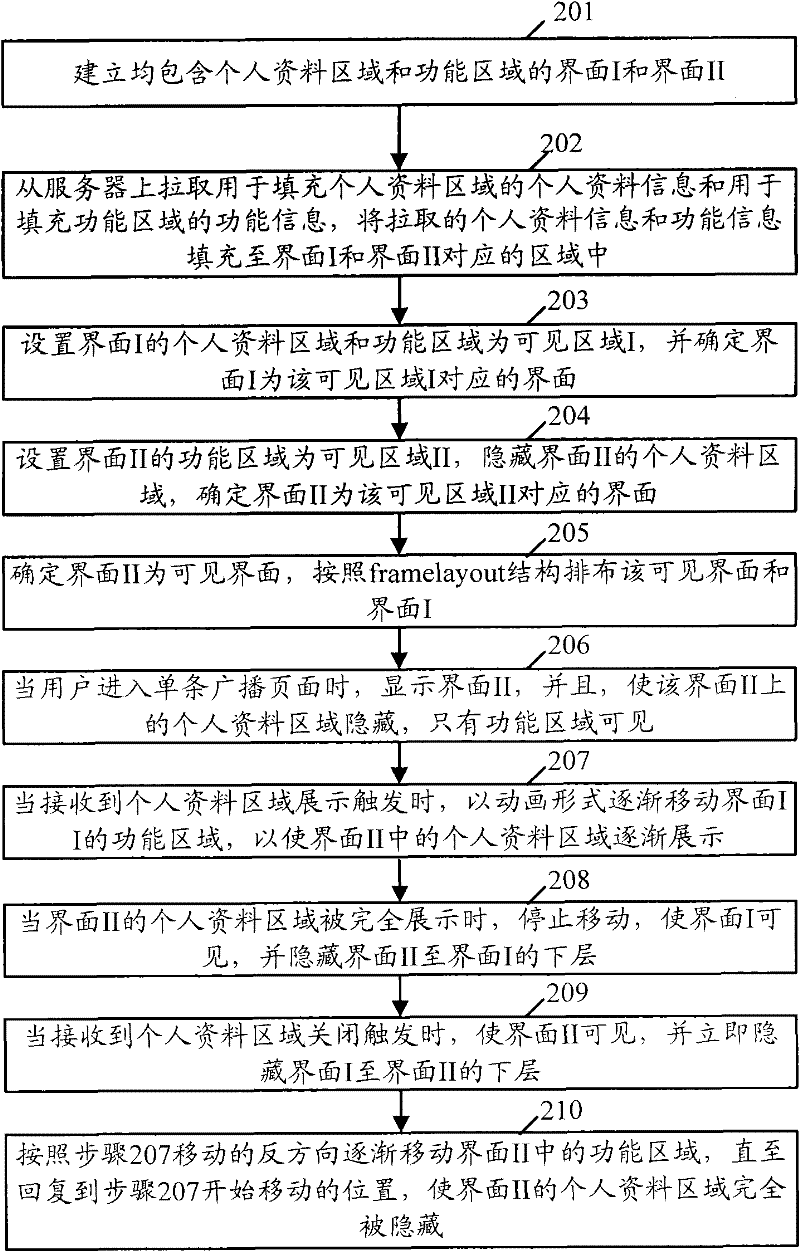
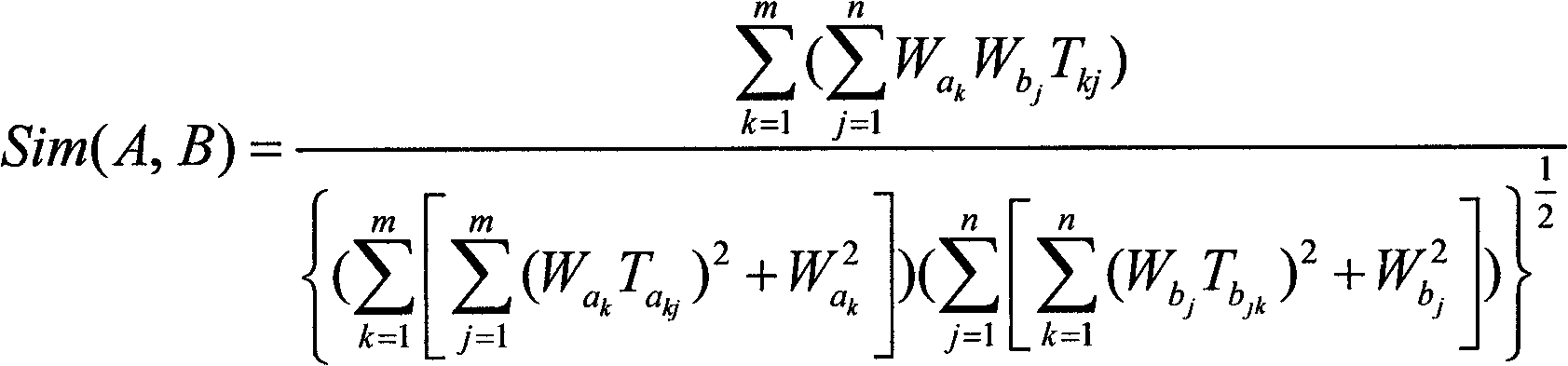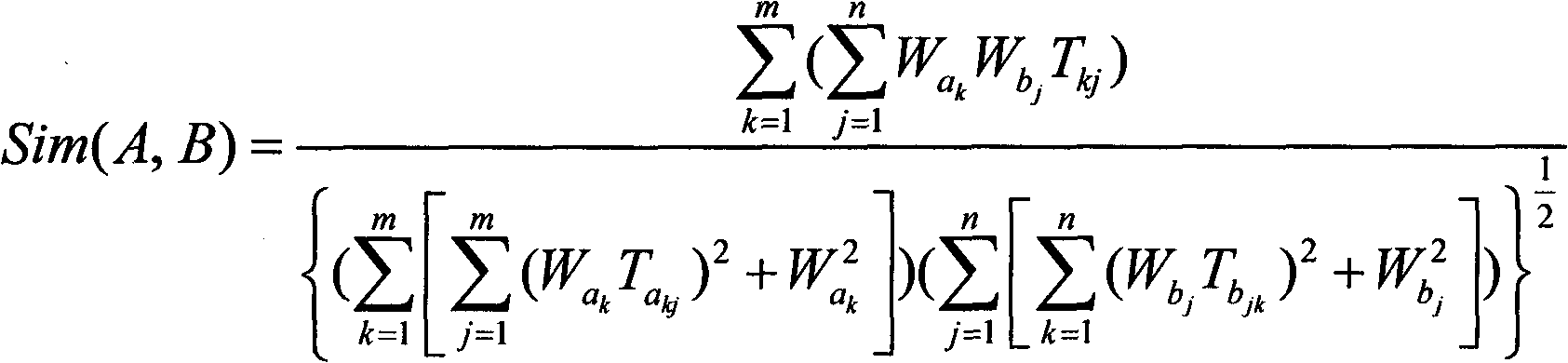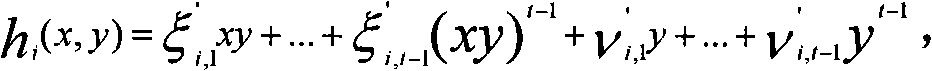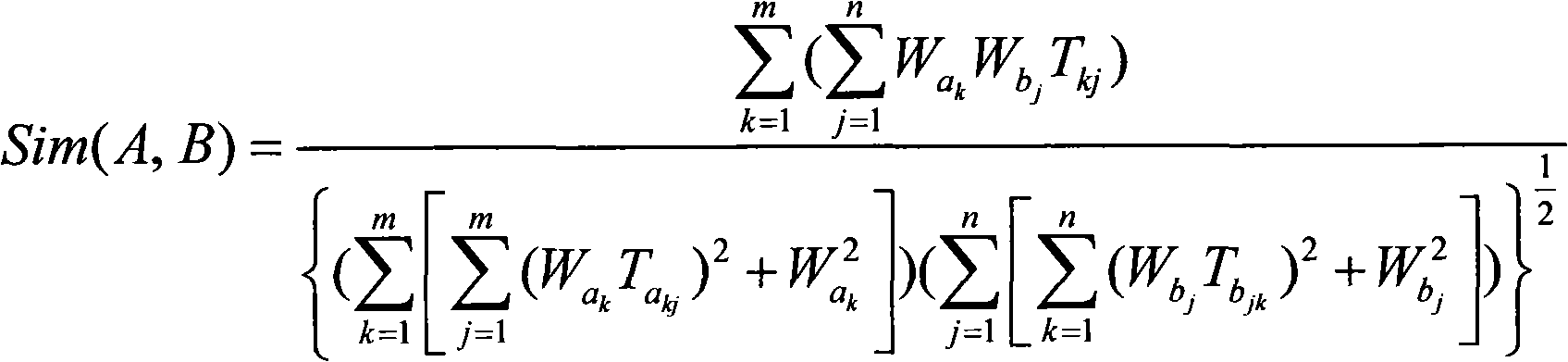Patents
Literature
91results about How to "Achieve correctness" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
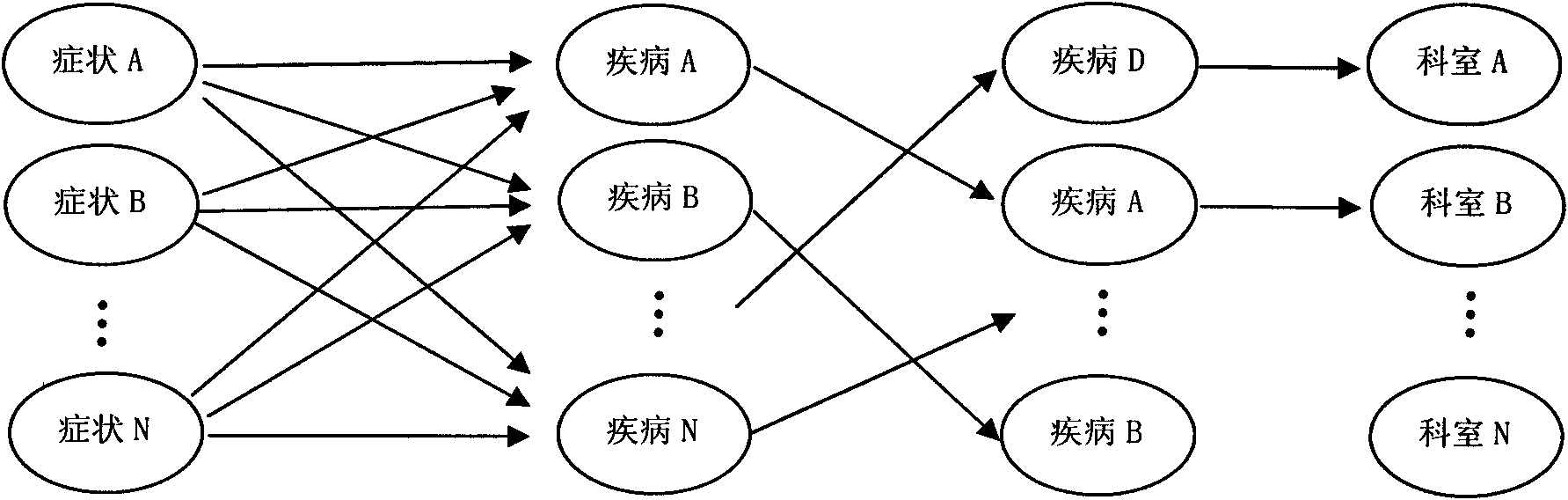
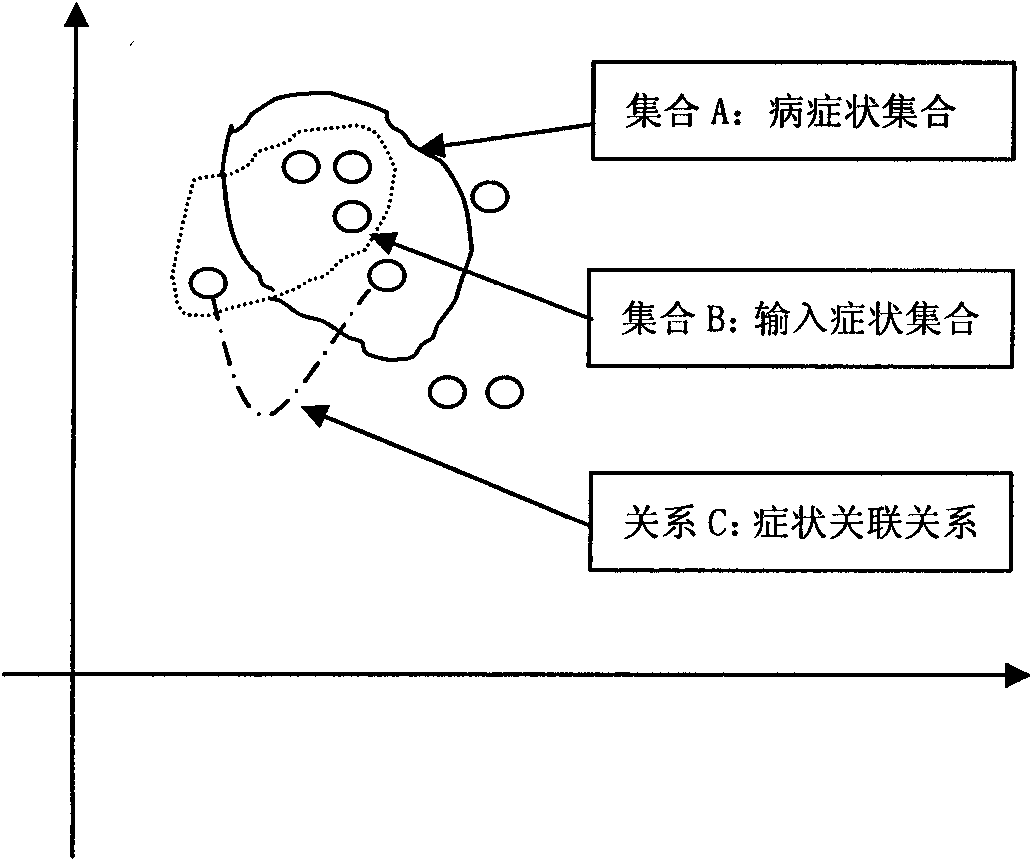
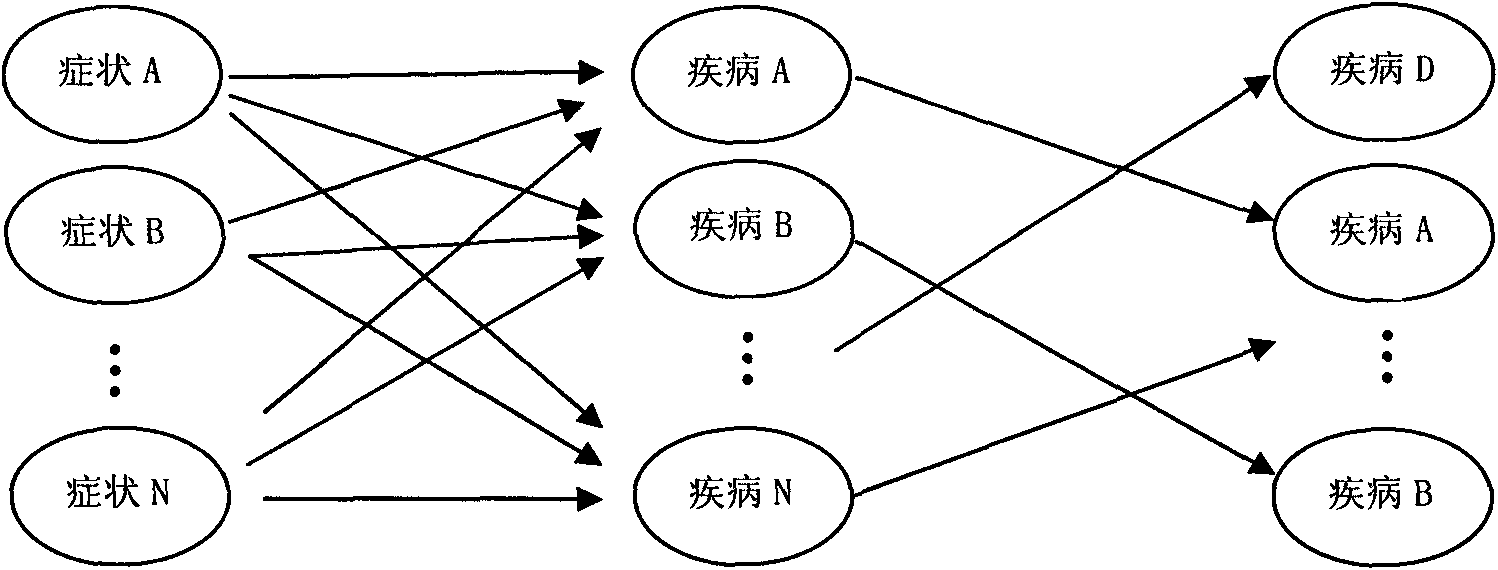
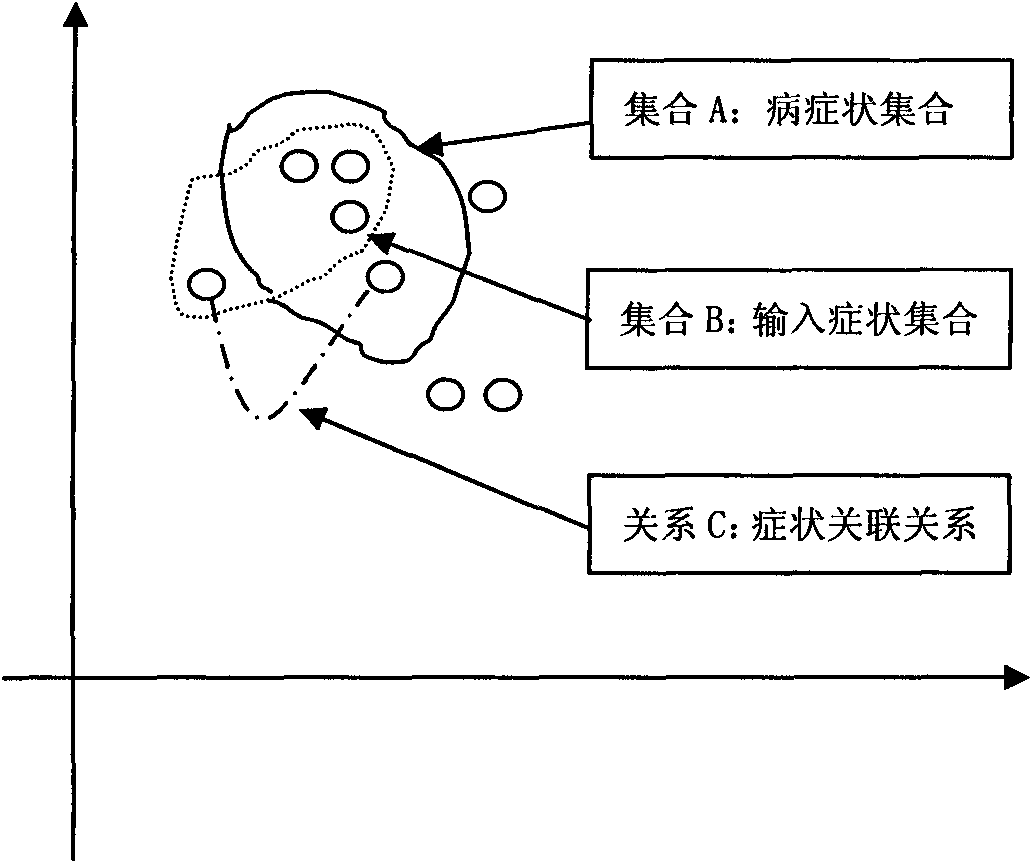
Hospital decision-making aiding method based on symptom similarity analysis
InactiveCN102156812AWeaken errors interfere with resultsAchieve correctnessSpecial data processing applicationsPatient modelInformation analysis
The invention provides a hospital decision-making aiding method based on symptom similarity analysis, belonging to the field of information analysis and decision-making aid. The method comprises the following steps: establishing a disease database, a symptom database, a department database and a correlating relationship; establishing a patient model for symptoms input by users, and calculating the similarity between the patient model and a disease model; and searching one department with corresponding suspected diseases in the department model to serve as hospital reference. The method has the advantages that an error interrupted result is weakened under a condition that a user takes an error symptom as a reasoning condition; a correct symptom participates in the reasoning operation by combining the correlating relationship between the error symptom and the convention symptoms according to the error symptom condition so as to realize the correctness and interruption resistance of reasoning; and a hospital department list is obtained by utilizing the mapping relationship between the disease and the department. The method can be used in electronic reception or health consulting systems, as well as in medical training or clinical reference.
Owner:中国医学科学院医学信息研究所
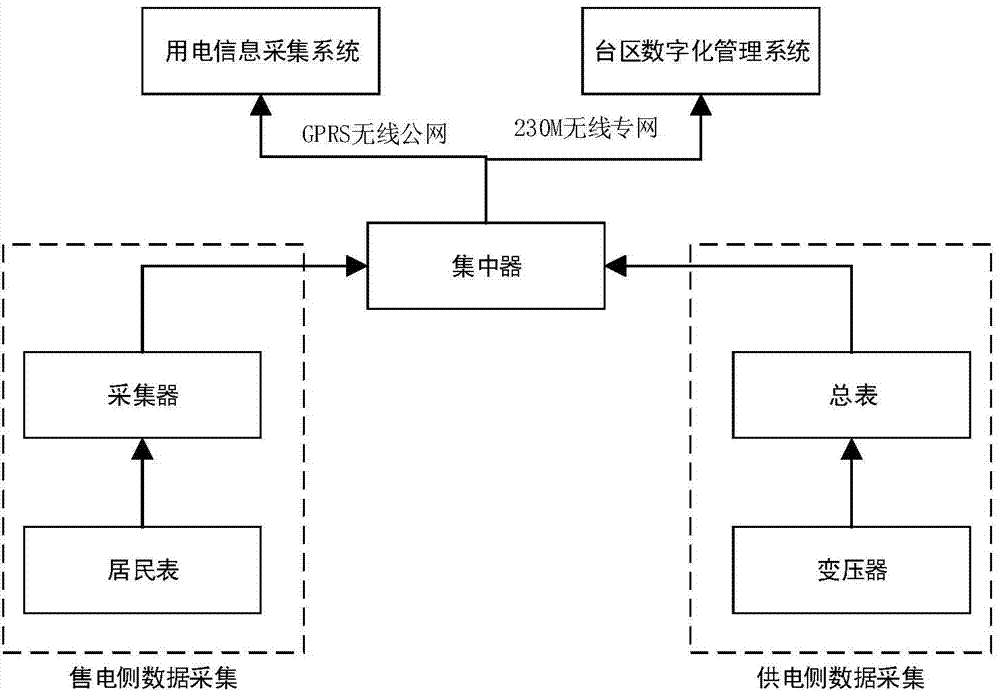
Multifunctional station line loss management system
InactiveCN104779699AHigh speedImprove effectivenessCircuit arrangementsInformation technology support systemElectric power systemTransformer
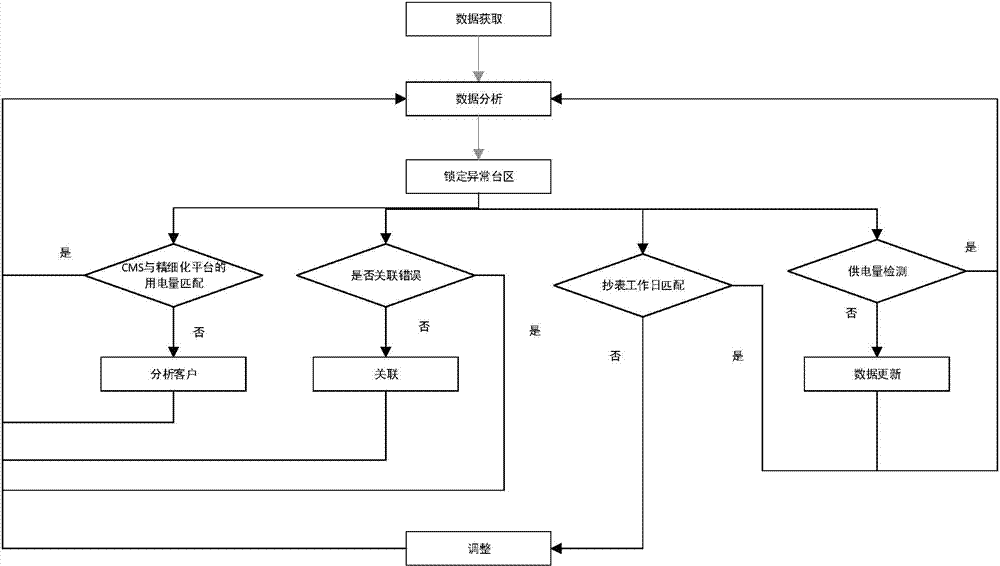
The invention discloses a multifunctional station line loss management system, and belongs to the field of power generation, power transformation or power distribution. The system comprises an existing transformer area digitalization management system, wherein the transformer area digitalization management system reads power supply and sale quantity information of each outgoing line or each user of a transformer substation to compute line loss; a list of line loss rates of the users in a previous month is exported from the transformer area digitalization management system; a line loss distinguishing data model is established to screen high line loss rate transformer areas; line loss data exception transformer areas are locked; the users in the line loss data exception transformer areas are counted according to power quantity differences of the users during flat and peak load periods; and exceptional power utilization periods are automatically distinguished by comparing the power quantity differences during the flat and peak load periods. The system can increase a distinguishing success rate of transformer area / station line loss factors, can progressively improve an integral line loss control level of transformer areas / stations by virtue of a spiral rising working mode, can gradually reduce an integral line loss rate of a regional power supply network, and can be widely applied to the field of operation analysis and power utilization management of power systems.
Owner:SHANGHAI MUNICIPAL ELECTRIC POWER CO
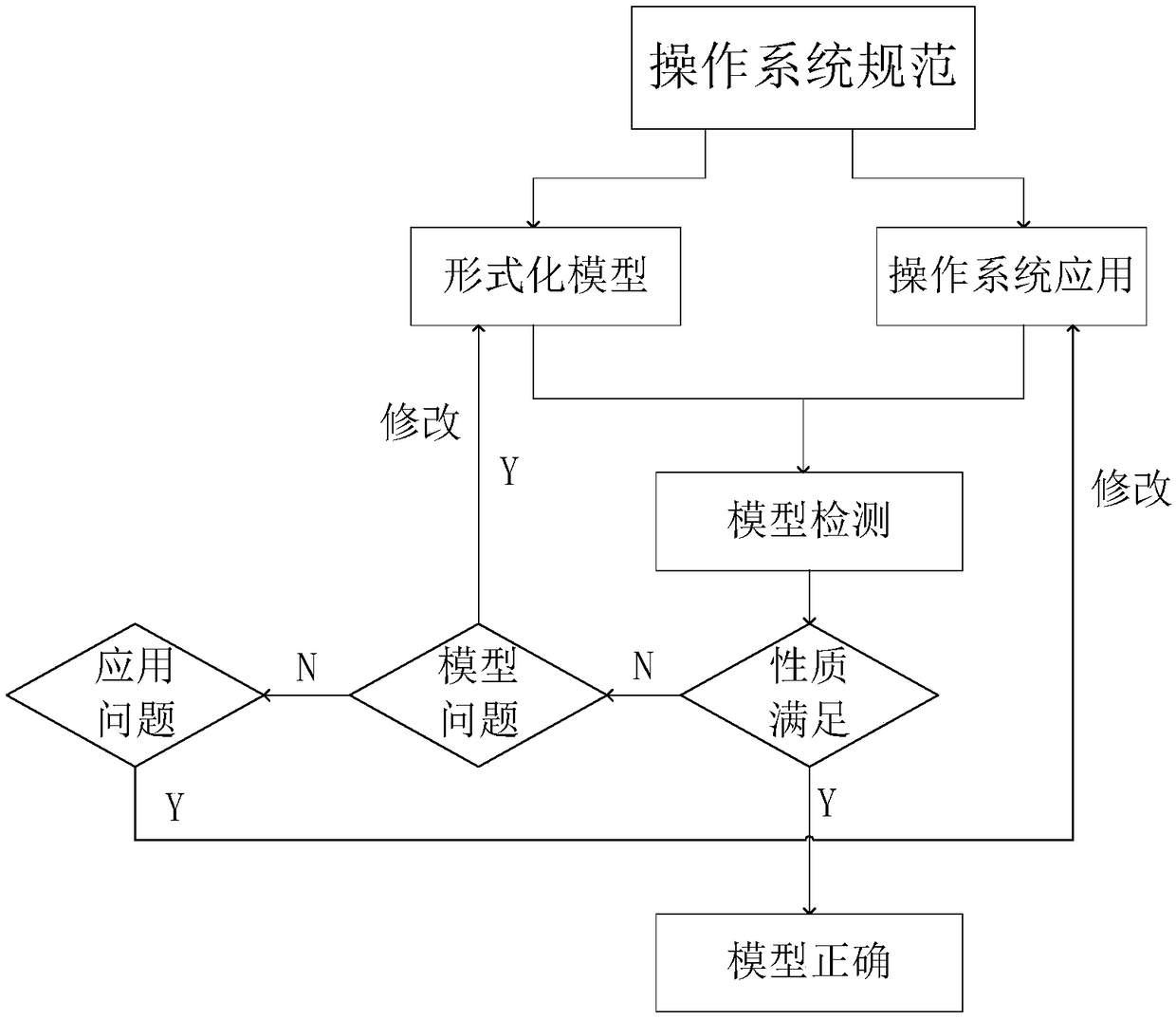
Operation system specification formal verification and test method
ActiveCN108509336AAchieve correctnessSoftware testing/debuggingCode compilationConstraint specificationPre conditioning
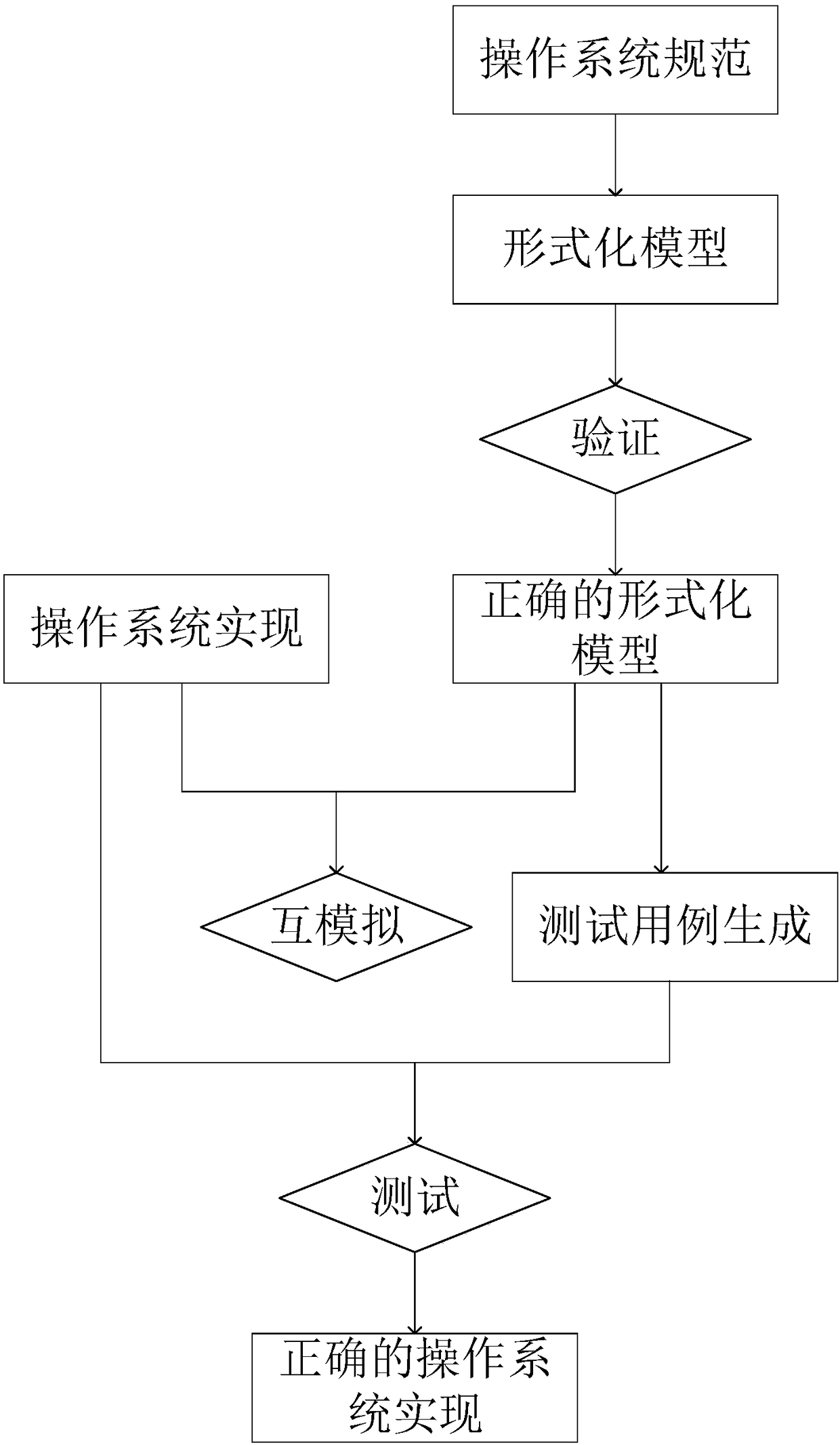
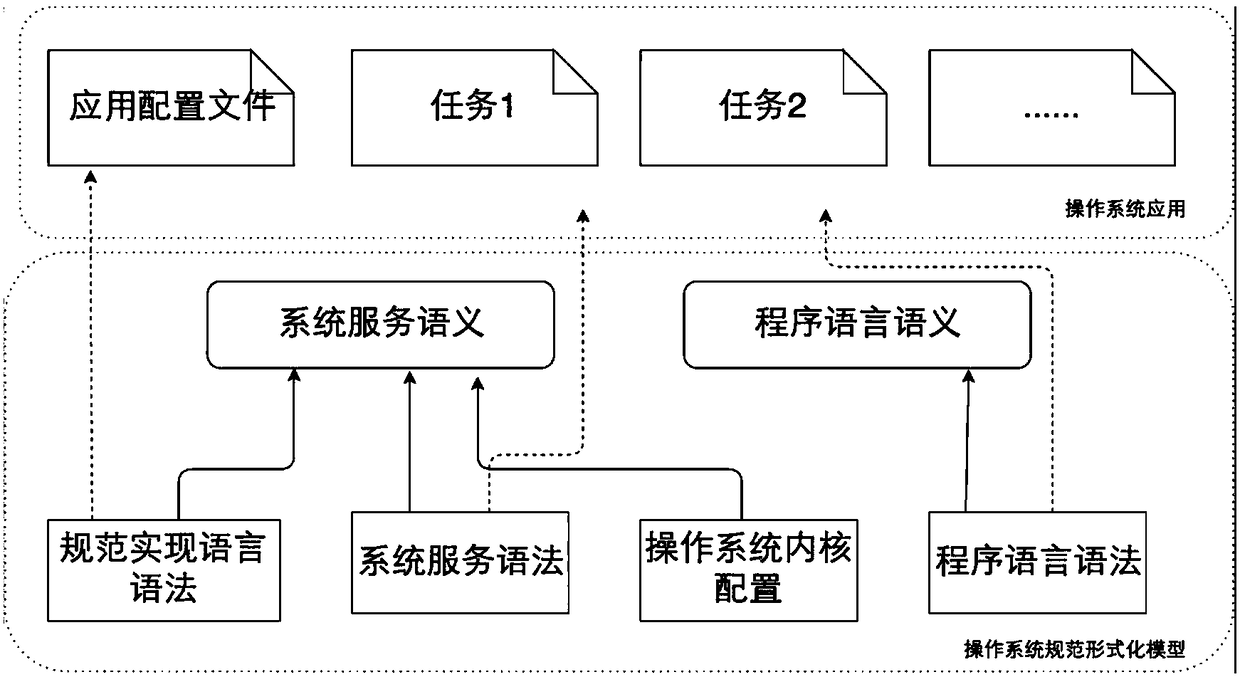
The invention discloses an operation system specification formal verification and test method. The method comprises the steps of firstly extracting constraints of pre-conditions and post-conditions about system service execution in operation system specifications; according to the extracted constraint specifications, building a formal semantic model; verifying the formal semantic model and an operation system application, and if the verification is not passed, correcting the formal semantic model or the operation system application, until the formal semantic model and the operation system application meet the specifications; automatically generating a test case realized by an operation system kernel from the correct formal semantic model by using a model check method; testing the correctness of operation system kernel implementation; and executing the verified application in the formal semantic model and the operation system kernel implementation, extracting two executive tracks, comparing the consistency of the two executive tracks by applying a mutual simulation method, and if the two executive tracks are inconsistent, correcting the operation system kernel implementation until the operation system kernel implementation is correct. The method is applied to formal verification of the operation system specifications and test of the operation system kernel implementation, thereby improving the security and reliability of an operation system.
Owner:EAST CHINA NORMAL UNIVERSITY
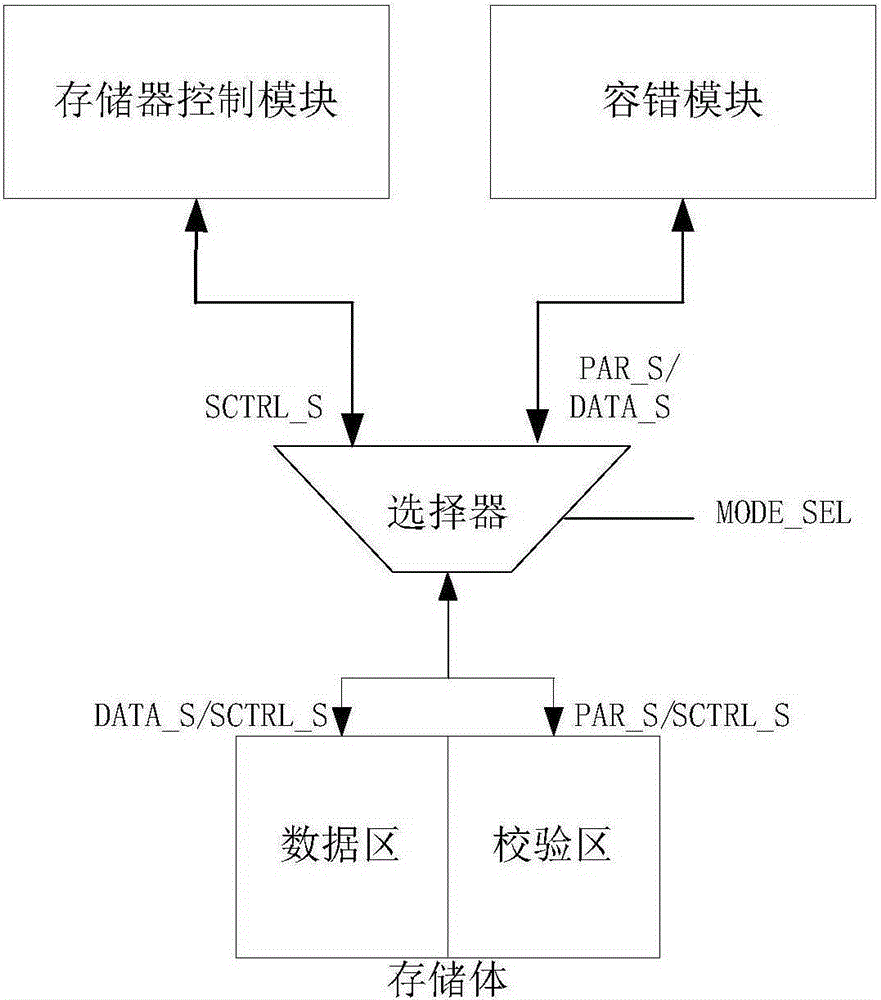
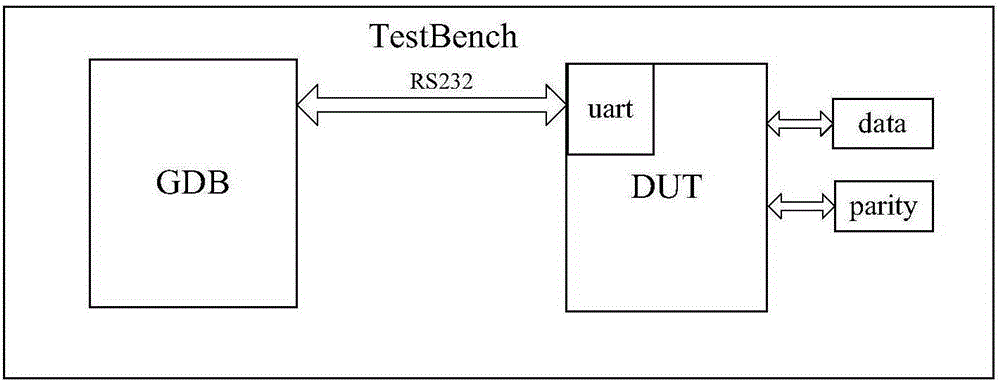
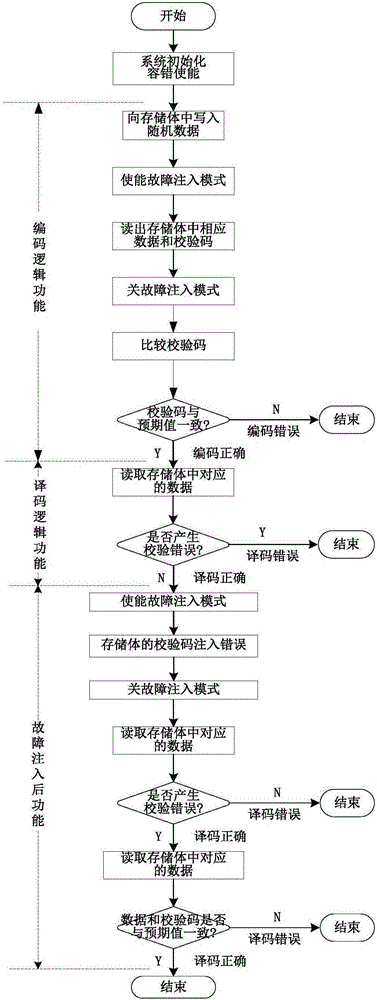
Automatic verification platform and method for on-chip memory management unit fault-tolerant structure
ActiveCN105185413AAchieve correctnessAchieve reliabilityStatic storageSpecial data processing applicationsComputer architectureStacking fault
The invention provides an automatic verification platform and method for an on-chip memory management unit fault-tolerant structure. The automatic verification platform and method can conduct random fault injection verification on the fault-tolerant structure and are high in verification coverage rate. The platform comprises a debugging host and a to-be-tested host connected through a serial port. The debugging host is used for flow control verification, encoding result checking, fault injection, decoding result checking in the verification process, and monitoring and debugging of a processor. The on-chip memory stack fault-tolerant structure is integrated in the to-be-tested host and used for generation of check codes, decoding verification after decoding logic and fault injection and loading of an automatic verification program for the memory stack fault-tolerant structure. The memory stack fault-tolerant structure comprises a memorizer control module, a fault-tolerant module, a selector and a memory stack. The memorizer control module and the fault-tolerant module conduct read-write control over the memory stack through the selector to control the working mode and the failure mode of the on-chip memory stack fault-tolerant structure.
Owner:NO 771 INST OF NO 9 RES INST CHINA AEROSPACE SCI & TECH
Deviation symptom description-oriented automatic computer-aided diagnosis method
InactiveCN102184314AWeaken errors interfere with resultsAchieve correctnessSpecial data processing applicationsDecision-makingInformation analysis
The invention provides a deviation symptom description-oriented automatic computer-aided diagnosis method, belonging to the field of information analysis and aid decision making. The deviation symptom description-oriented automatic computer-aided diagnosis method comprises the steps of: firstly, establishing a disease library and a symptom library and an incidence relation between the disease library and the symptom library, establishing a patient model by using symptoms input by a user, carrying out similarity calculation with the disease model, reasoning and sequencing suspected diseases. The invention has the advantages that the accuracy of a fault interference result is reduced under the condition of using the symptoms mistaken by the user; and according to the fault symptom condition, by combining with the incidence relation among the conventional symptoms, the right symptoms participate in reasoning and operating, and thus reasoning correctness and anti-interference are realized. The invention can be used in an electronic triage or health counseling system, and also used in medical training or clinical reference.
Owner:中国医学科学院医学信息研究所
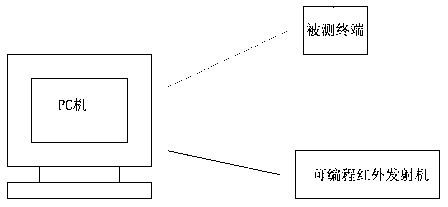
Automated testing method suitable for remote control products
ActiveCN103345446AImprove production efficiencyReduce difficulty of useSoftware testing/debuggingRemote controlComputer terminal
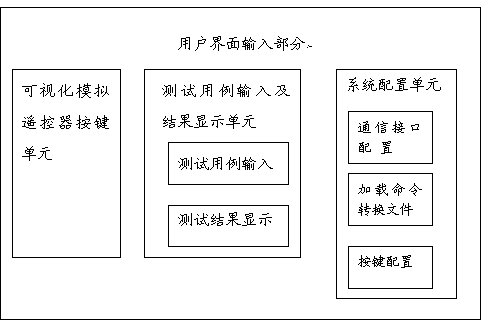
The invention discloses an automated testing method suitable for remote control products. The automated testing method comprises the following steps that (1) a testing background program is edited, the background program is operated on a background computer, the testing background program can generate testing cases or load testing case documents, and a tested terminal and a computer communication port are connected or the tested terminal and a programmable infrared transmitter are connected with the computer communication port respectively; (2) the background program transmits the testing cases through the computer communication port, the tested terminal executes the testing cases and feeds the operating result of the testing cases back to the background computer, and the background computer compares the operating result of the fed-back testing cases with an expected result and displays the comparative result. The automated testing method suitable for the remote control products achieves automated testing of the remote control products and avoids waste of manpower and material resources.
Owner:四川九洲投资控股集团有限公司
System for automatic testing USB compatibility
InactiveCN101059770ATo achieve the purpose of speed conversionReduce labor costsError detection/correctionSleep stateComputer compatibility
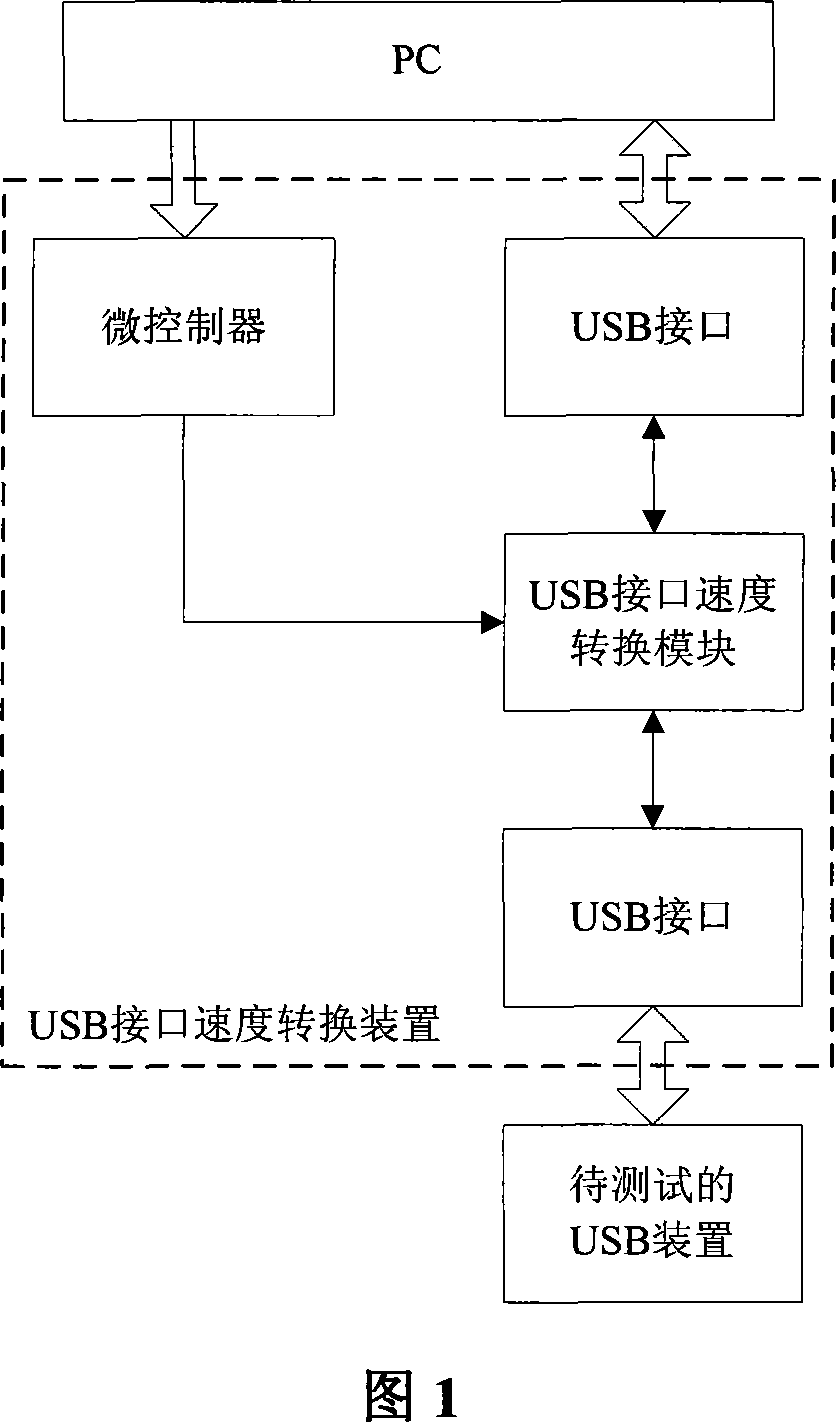
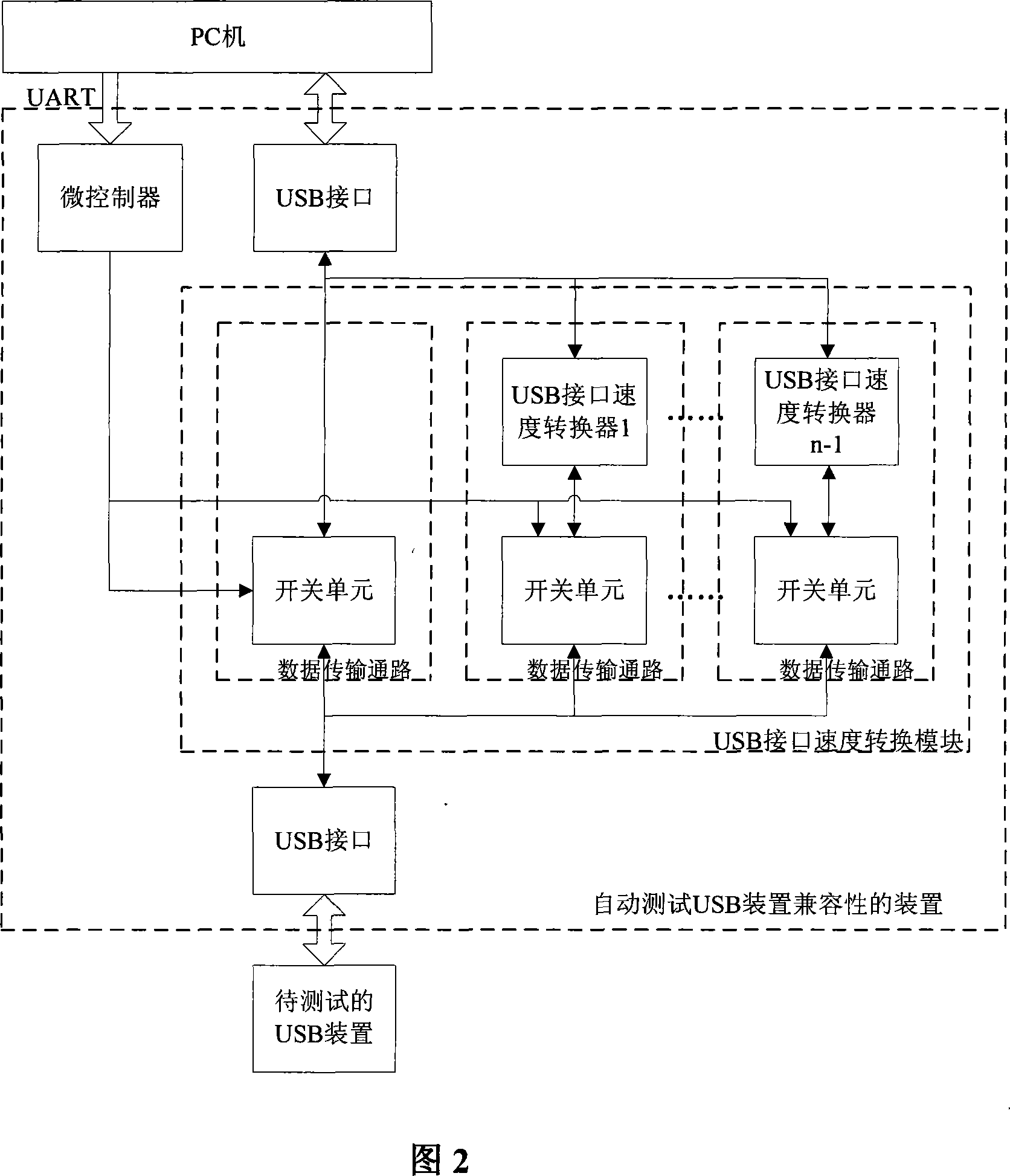
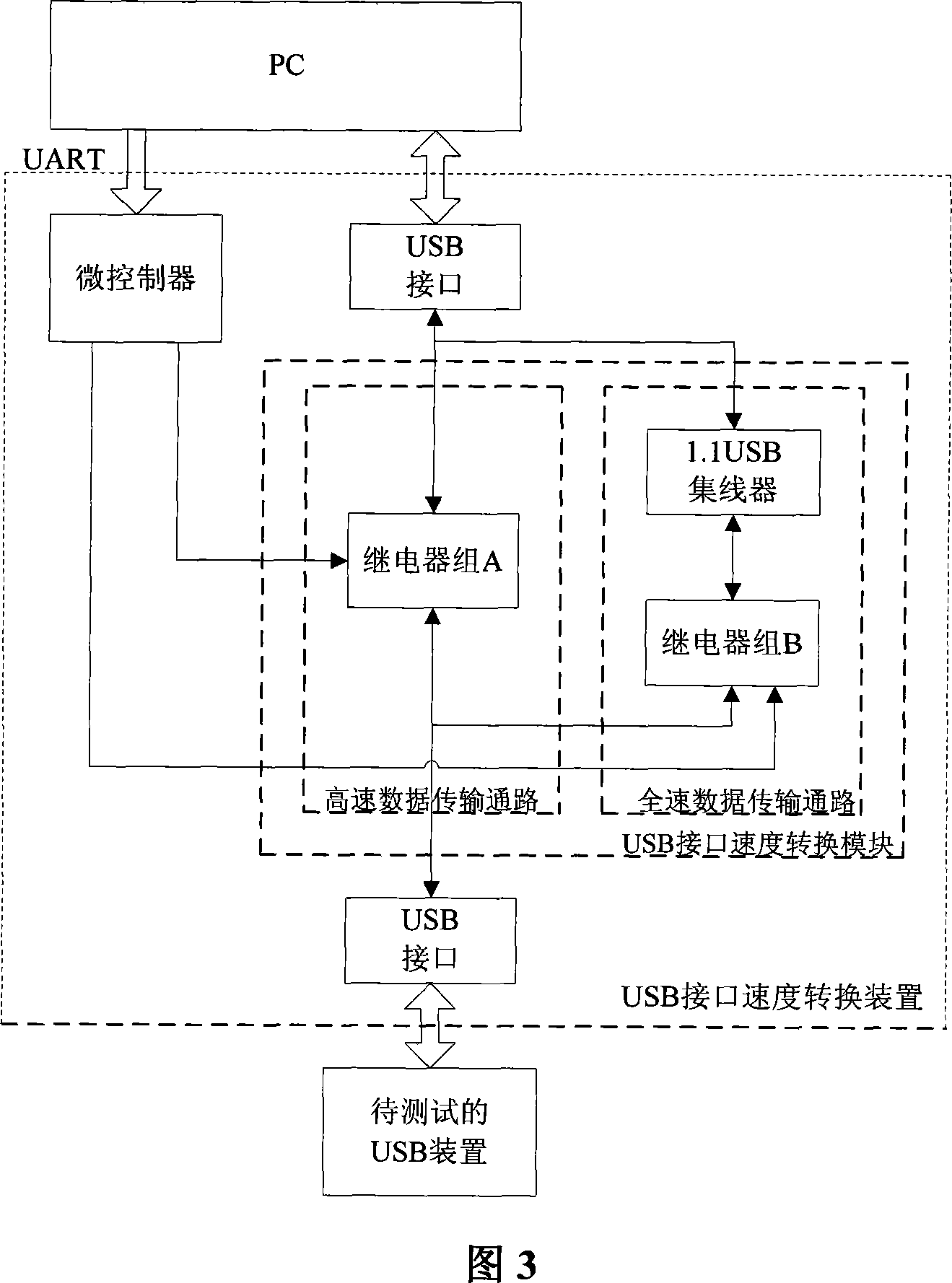
The invention provides a system for automatically testing the compatibility of USB device, which uses a USB interface speed convert module based on the control command of PC to convert the USB interface speed, to test the compatibility of USB device under different USB interface speeds. Compared with artificial USB compatibility test, the invention reduces cost, improves efficiency, simplifies operation, and resolves the problem that the transmitted video flow may be delayed, mistake color, shifts image, and discontinuously display image when the PC is returned to normal state from wait / sleep state or the USB device is plugged several times.
Owner:VIMICRO CORP
Data reading method and device, electronic equipment and storage medium
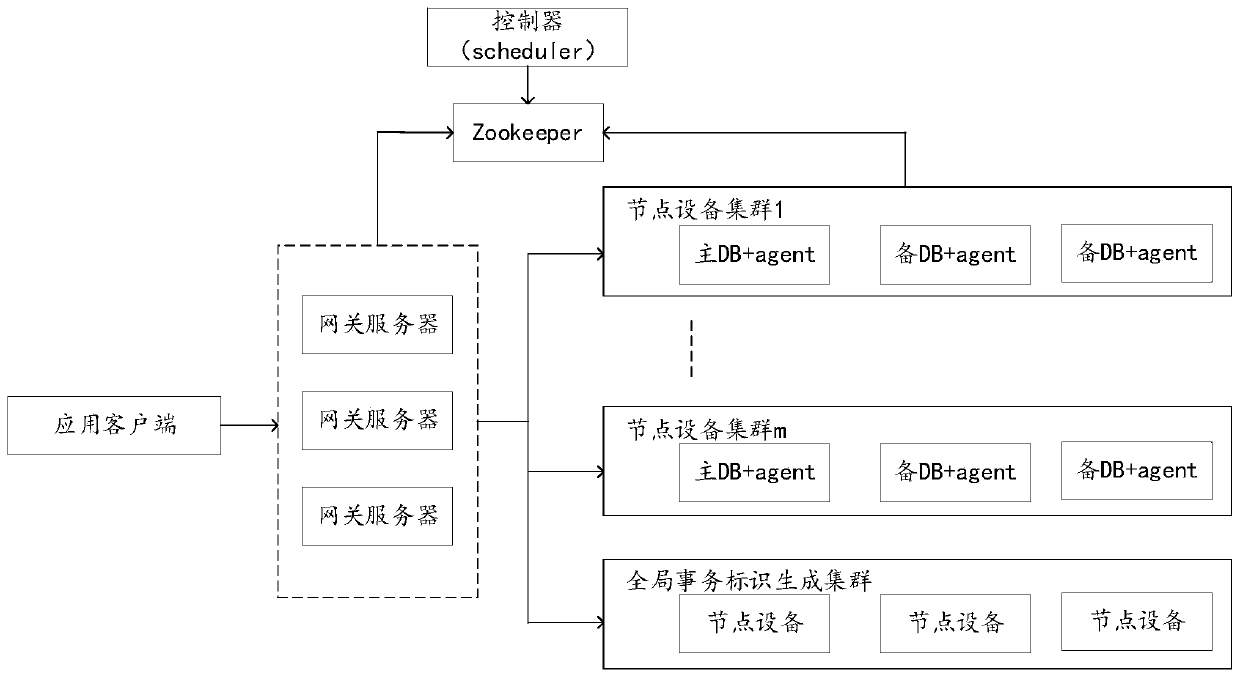
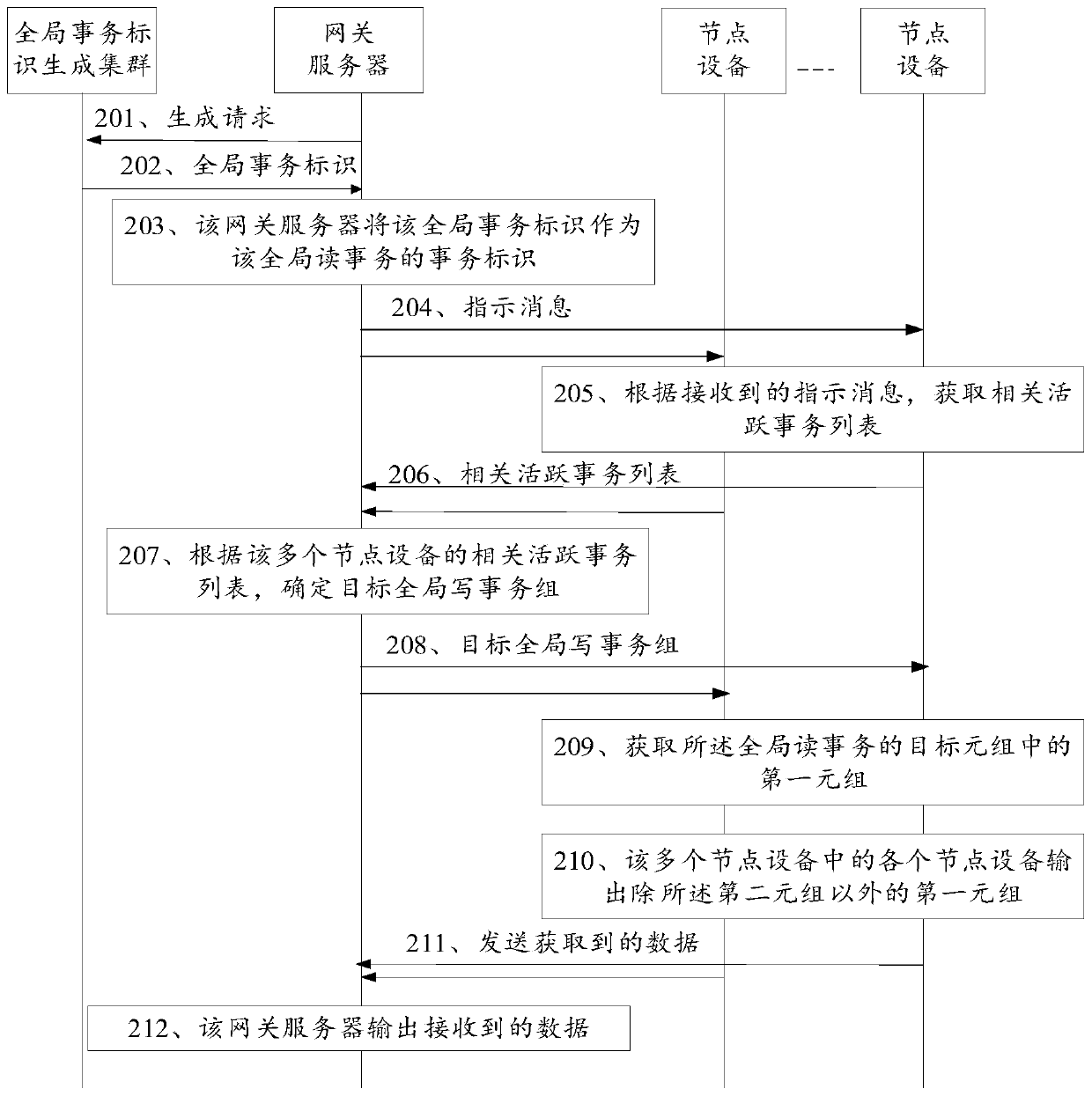
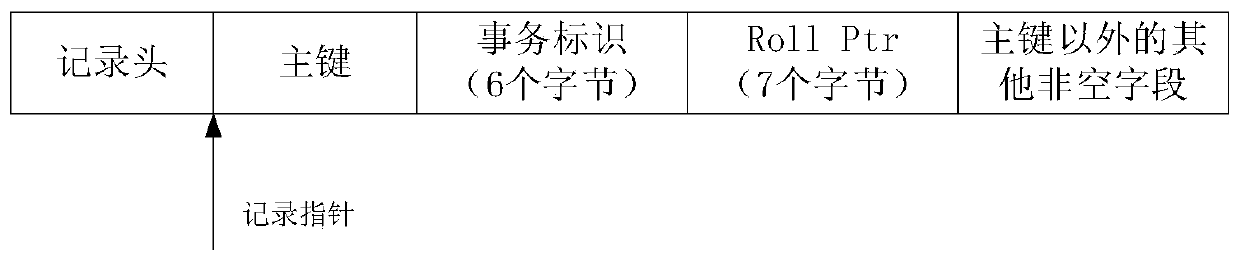
ActiveCN109710388ATransactionally consistentAchieve consistencyDatabase updatingDatabase distribution/replicationExternal dataElectric equipment
The invention discloses a data reading method and device, electronic equipment and a storage medium, and belongs to the technical field of databases and big data. The embodiment of the invention provides a method. The method comprises the following steps: finding out a plurality of node devices at the moment when a current global read transaction occurs; the method is based on MVCC, common pointswith transaction consistency are provided; equivalently, only data submitted before the current moment is read; the method can be regarded as a real-time reading process, in the data reading process,the data which are not submitted when the current global read transaction occurs are eliminated; according to the method and the device, when the current global read transaction occurs, only the submitted data when the current global read transaction occurs is read, so that the global write transaction which may cause transaction inconsistency is eliminated, the read data has transaction consistency, the external data consistency of the database system is realized, and the correctness of data reading can also be realized.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Electric connector
ActiveCN103390816AFirmly connectedEasy to operateCoupling contact membersTwo-part coupling devicesElectrical connectionStructural engineering
The invention discloses an electric connector which comprises a male plug and a female socket, wherein the male plug comprises a battery cell bar, a battery cell bar protective casing, a pressure-resistant housing, first reset springs, a battery cell bar positioning sleeve and a housing connector; the female socket comprises an electric socket, an electric socket filling bar, a pressure-resistant housing, a sleeve, a sleeve connector, a pressing block, second reset springs, springs and a housing connector; the battery cell bar comprises a first framework, first conducting rings and first cable cores; and the electric socket comprises a second framework, second conducting rings and second cable cores. According to the electric connector, mechanical connection is realized through matching of a drill tool male connector and a drill tool female connector, information channel connection is realized through contacted matching of the first conducting rings and the second conducting rings, and connection of short sections of downhole tools is completed in a working site, so that the electric connector is fast, convenient and reliable in connection, and can prevent the first reset springs and the second reset springs from interfering cables during compression and reset; and meanwhile, rigidity compensation is achieved through third springs, so that the battery cell bar and the electric socket of the electric connector are protected from being damaged.
Owner:SICHUAN HONGHUA PETROLEUM EQUIP
Multi-hop wireless network topology simulation system for supporting heterogeneous multi-channel
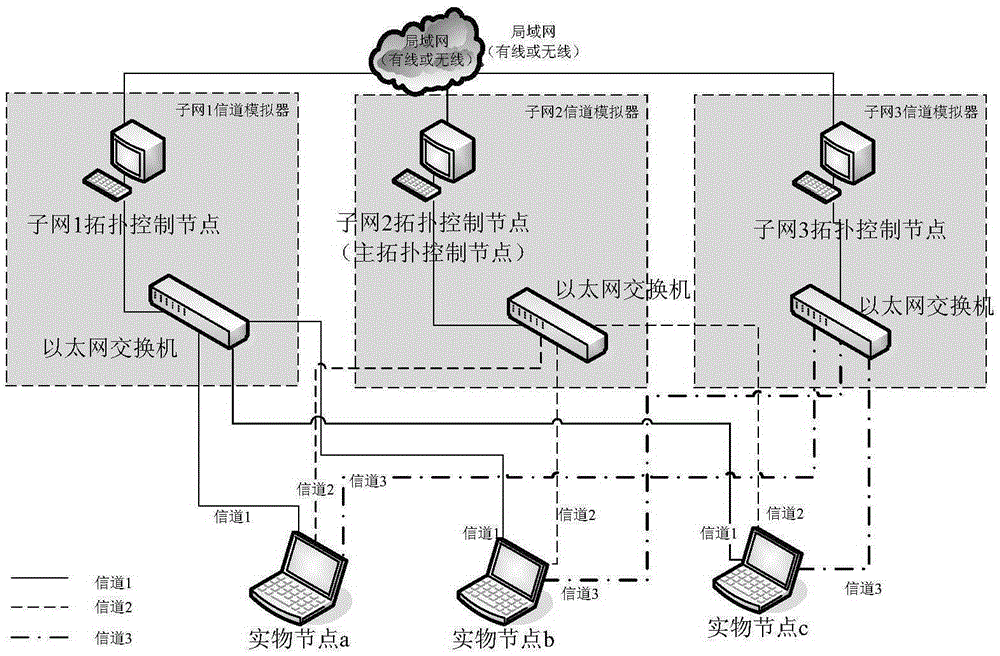
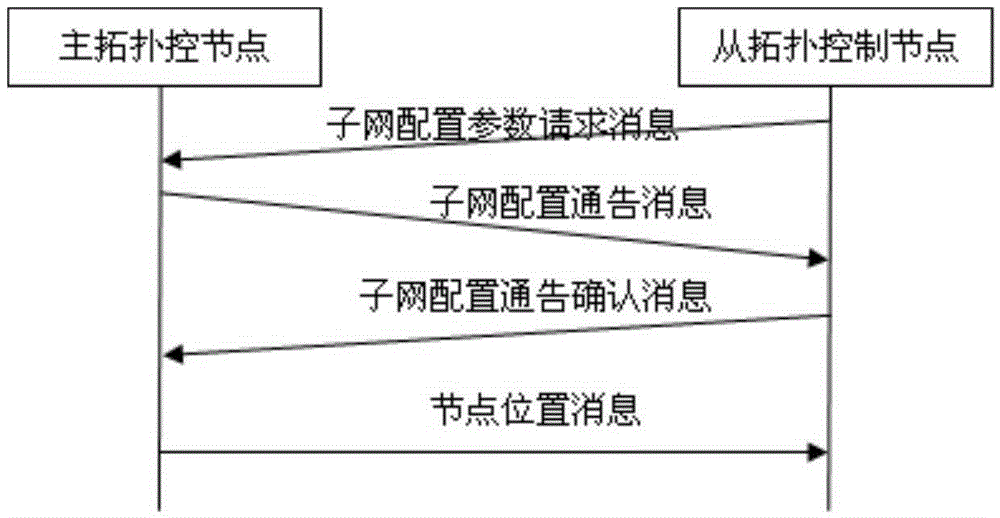
InactiveCN105337833AEasy to implementEnsure consistencyNetwork topologiesNetworks interconnectionTopology controlLocal area network
The invention discloses a multi-hop wireless network topology simulation system for supporting a heterogeneous multi-channel. The multi-hop wireless network topology simulation system comprises a plurality of heterogeneous channel subnet simulators; each heterogeneous channel simulator consists of an Ethernet switch and a topology control node, and is used for simulating the wireless multi-hop topology simulation of each type of heterogeneous channel subnets, and is accessed to each entity device via a virtual local area network, and is communicated with the topology control nodes; each topology control node is connected via a network, and is used for controlling and managing the topology relationship and the communication relationship of each subnet; a main topology control node is also in charge of generating, maintaining and managing position information and the like of the entity devices; each topology control node operates under an Ethernet promiscuous mode, and determines the data forwarding of the entity devices according to the topology relationship so as to complete the simulation and performance recording of various network topology structures in the multi-hop wireless network.
Owner:PLA UNIV OF SCI & TECH
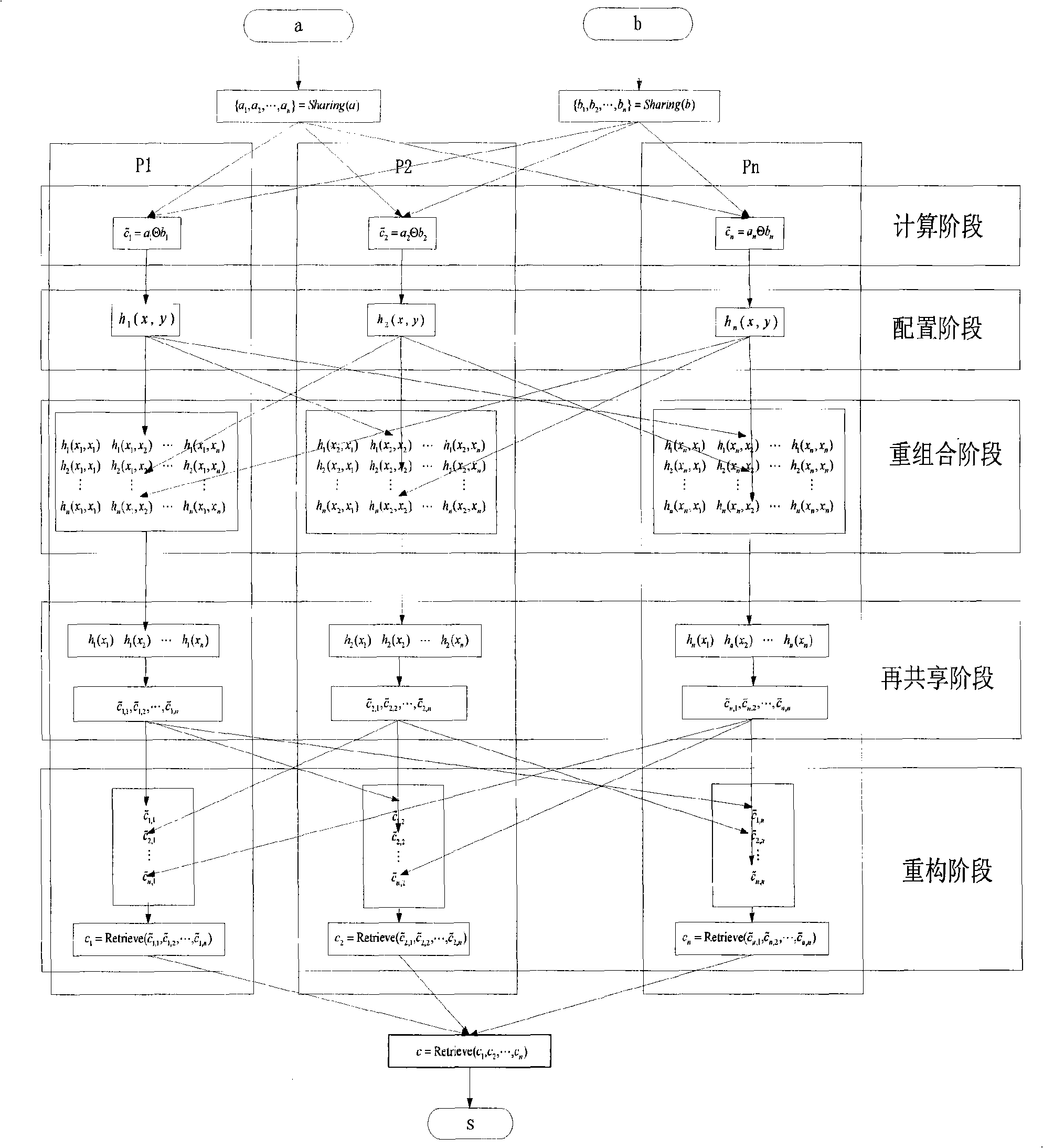
Construction method of division protocol based on cryptology in distributed computation
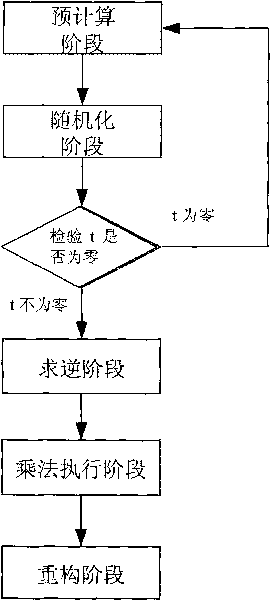
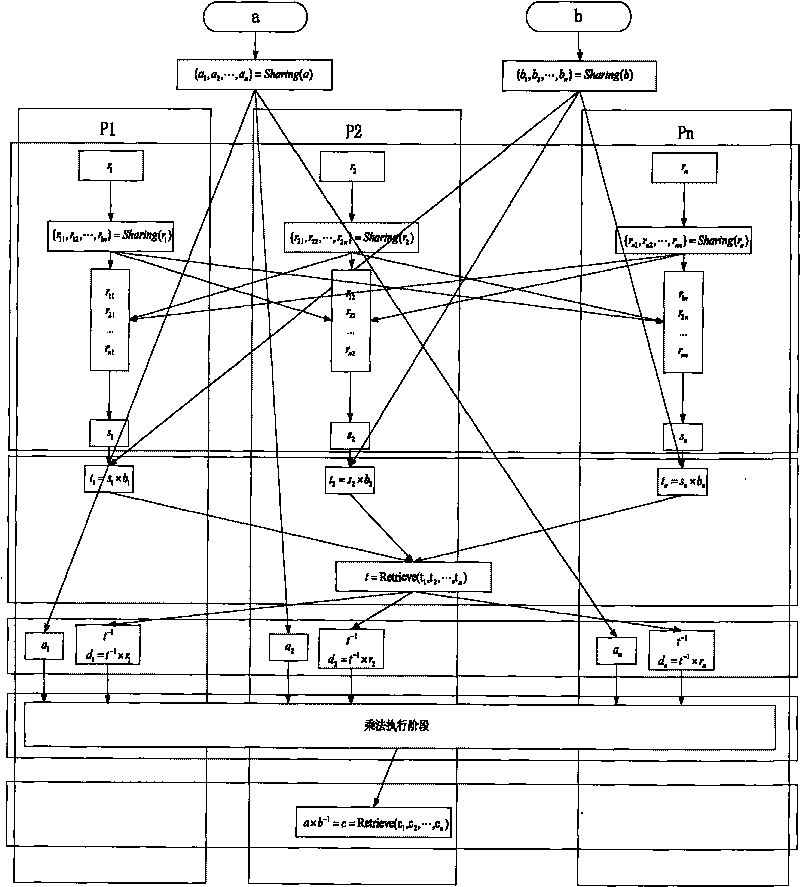
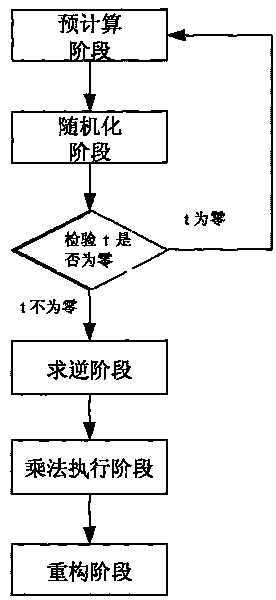
InactiveCN101729554AEasy to implementReduce computational complexityKey distribution for secure communicationFault toleranceCipher
The invention discloses a construction method of a division protocol based on cryptology in distributed computation, belonging to the field of information safety. The formation method is characterized in that (1) each member who participates in the computation dependently selects a random number and sends the shared value of the random number to all parties for local hybrid operation so as to obtain a public random shared value; (2) each member randomizes the sharing of an input secret value b by using the public random shared value and reconstructs the randomizing value of the secret value btogether; (3) each member inspects whether a randomizing result of the secret value b is inverse or not, if so, the member solves an inverse element of the randomizing value of the secret value b andthen de-randomizes the inverse element to obtain the inverse sharing of the secret value b by utilizing the public random shared value; (4) each member utilizes the obtained inverse sharing of the secret value b and a sharing executive multiplication protocol of a secret value a to obtain the sharing of the a / b; and (5) each member reconstructs a real computing result by mutually exchanging the obtained sharing of the a / b. The invention has the characteristics of high efficiency, fault tolerance and safety.
Owner:PEKING UNIV
Realization method and system of multi-packet data network connection
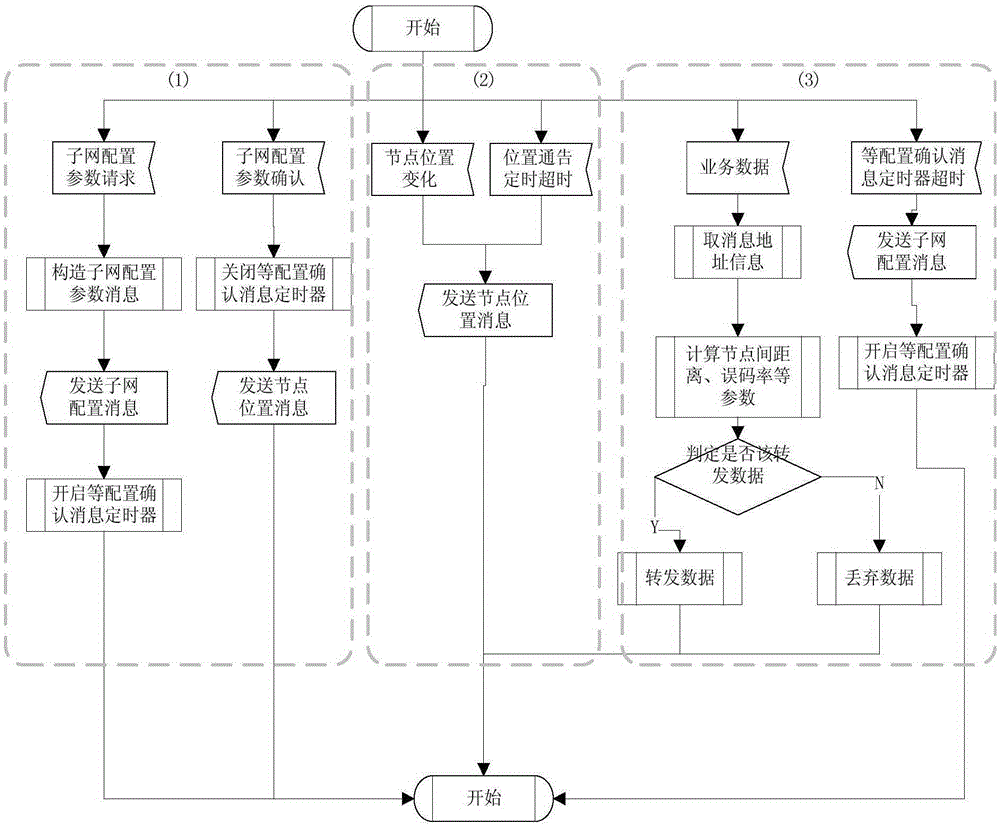
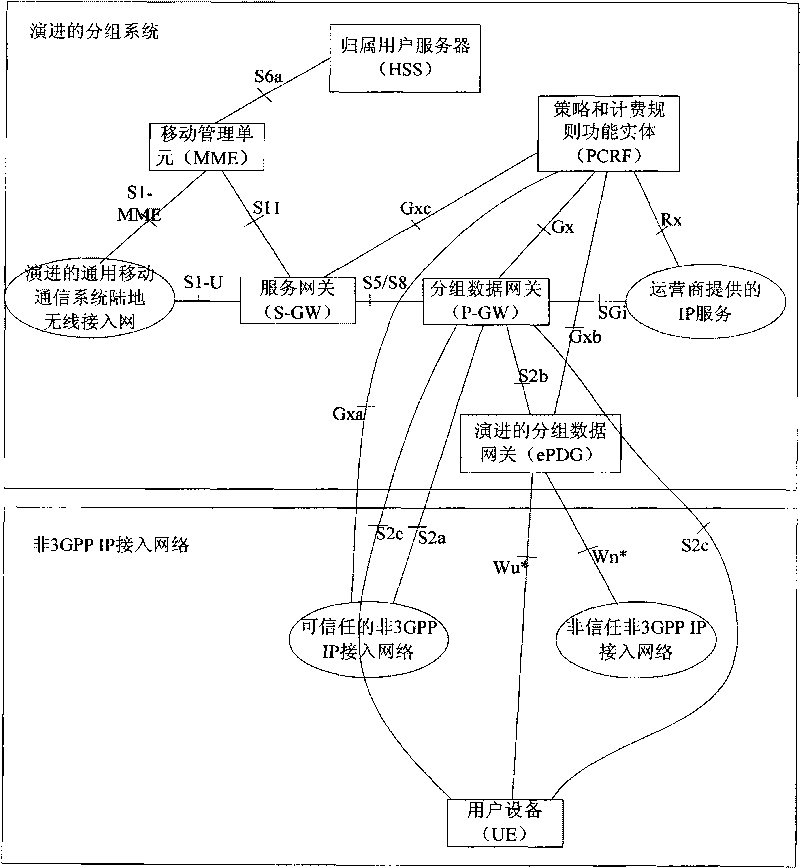
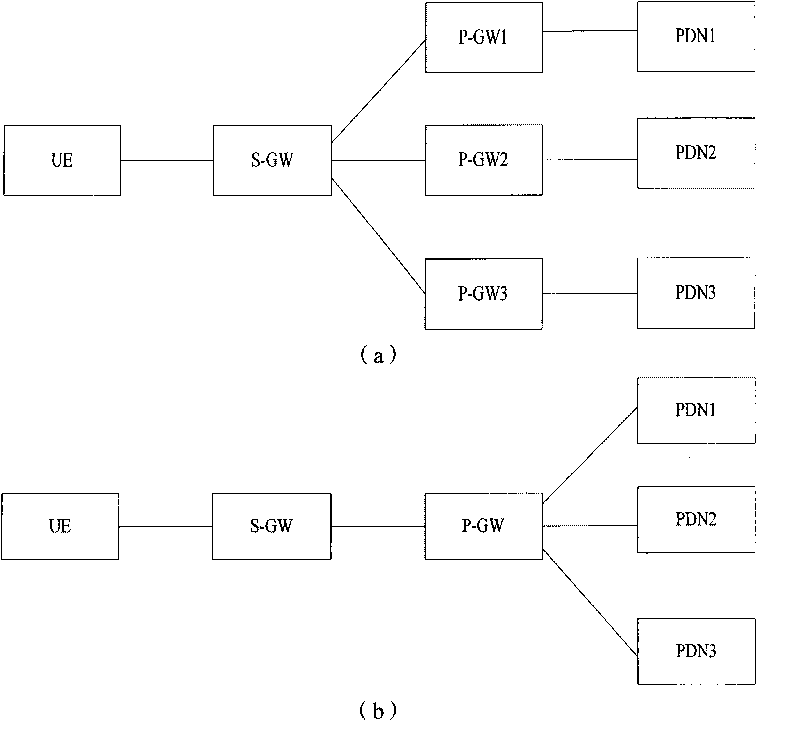
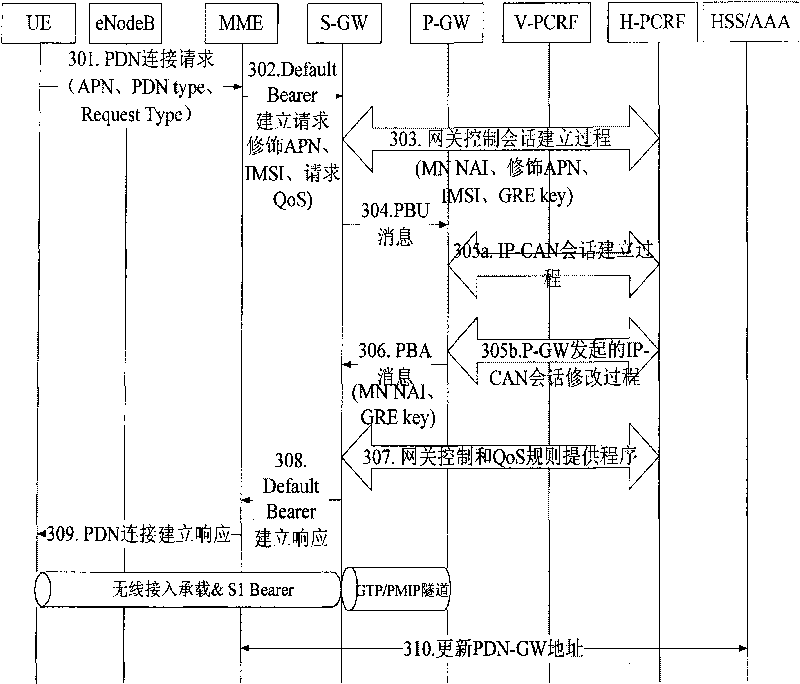
InactiveCN101730071AAchieve correctnessGuaranteed correctnessConnection managementNetwork data managementAccess networkNetwork connection
The invention provides a realization method of multi-packet data network (PDN) connection, comprising the following steps: when multi PDN connection is reestablished, network equipment stores a PDN connection distinguishing identifier for distinguishing PDN connection into a home subscriber server (HSS); and when an access network is handed off, the network equipment obtains the corresponding PDN connection distinguishing identifier from the HSS to reestablish connection of all the PDN. The realization method and system of the invention can ensure that multi PDN connection can be still reestablished when user equipment undergoes cross access network handoff, and can realize accuracy of data routing.
Owner:ZTE CORP
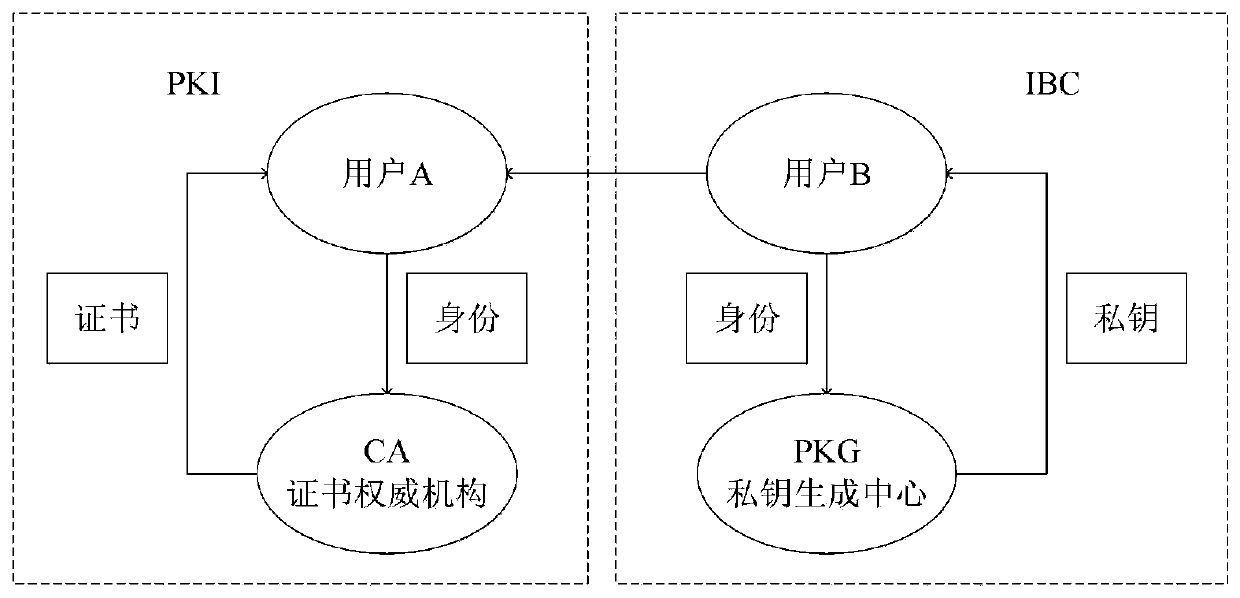
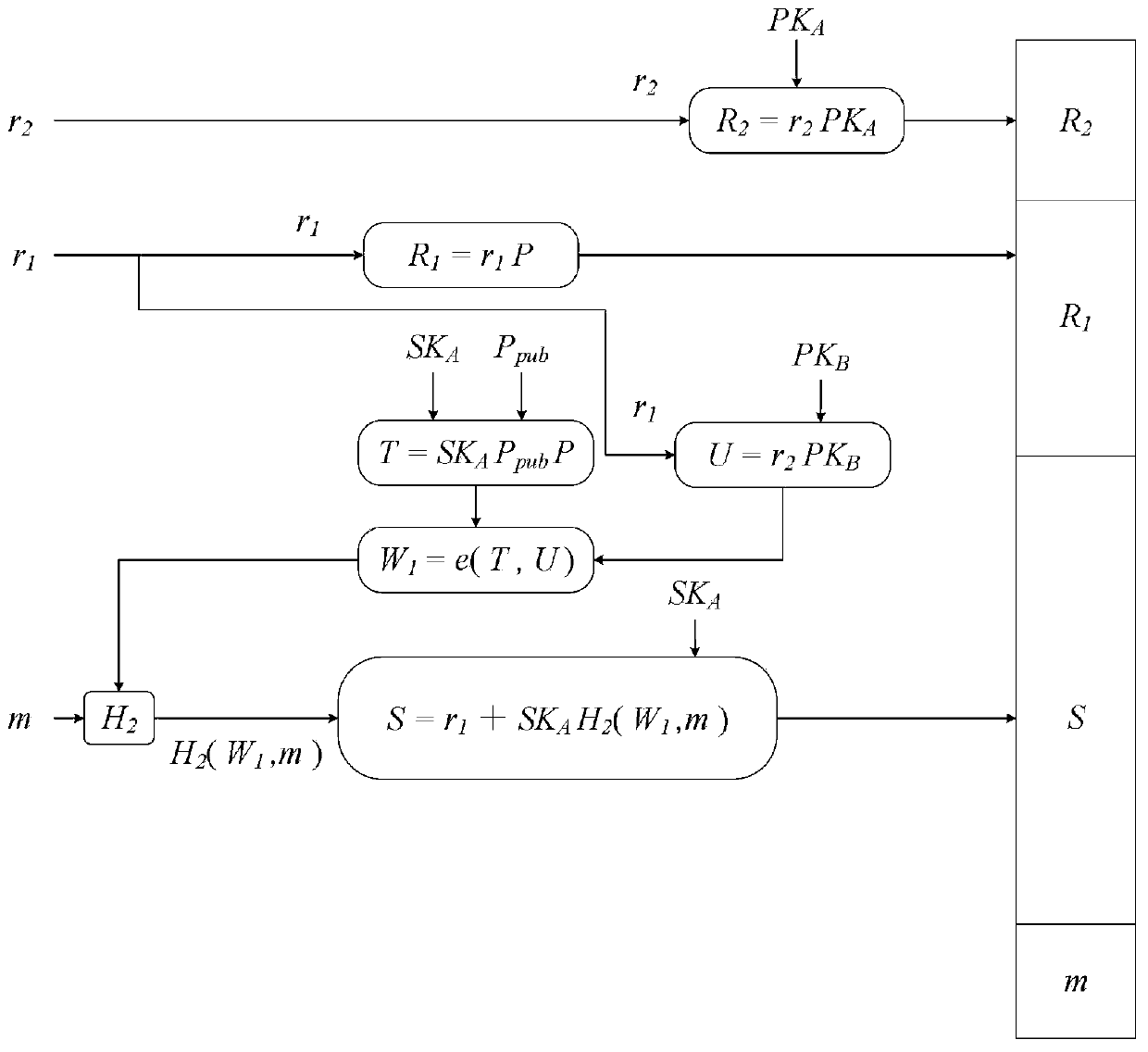
Secure bidirectional heterogeneous digital signature method between PKI and IBC
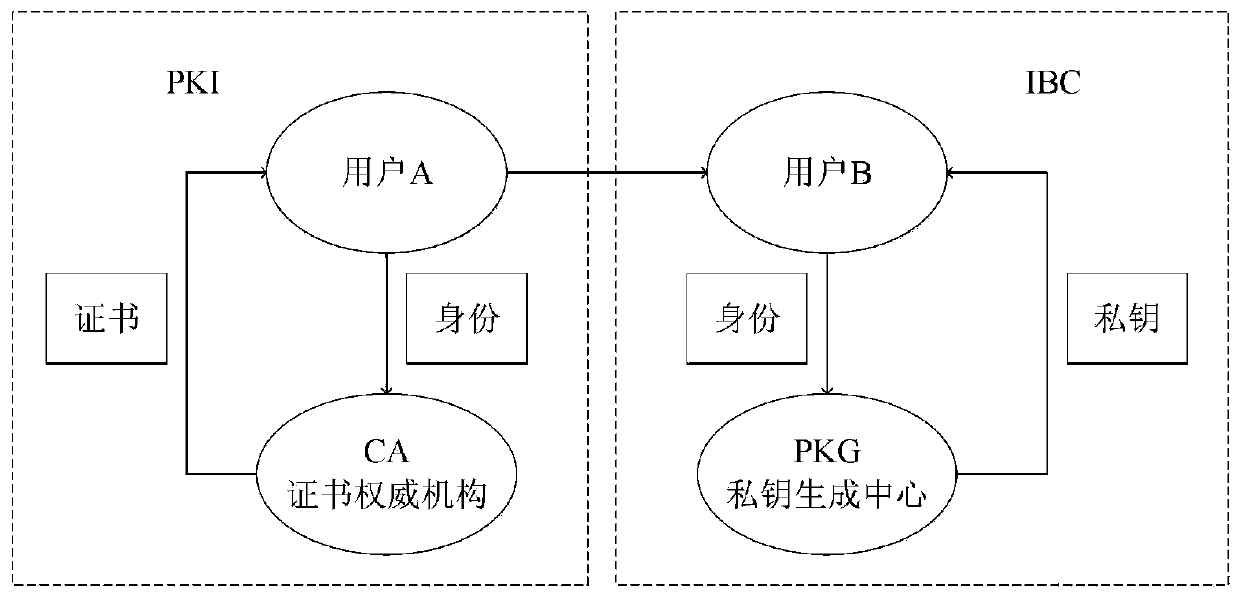
ActiveCN111342973AManagement issues do not existImplement digital signatureUser identity/authority verificationInternet privacyDigital signature
The invention discloses a secure bidirectional heterogeneous digital signature method between a PKI and an IBC. System parameters are generated through a private key generation center, and the systemparameters are disclosed; the user in the public key infrastructure environment and the user based on the identity encryption environment generate a public key and a private key respectively; whereinthe user in the public key infrastructure environment is a signer, the user based on the identity encryption environment is a verifier, the signer generates a signature and sends the signature to theverifier, and the verifier verifies the signature, passes the verification and accepts the message, otherwise, refuses to accept the message; wherein the user based on identity encryption is a signer,the user in the public key infrastructure environment is a verifier, the signer generates a signature and sends the signature to the verifier, and the verifier verifies the signature, passes the verification and accepts the message, otherwise, refuses to accept the message. According to the invention, the safety, correctness, non-repudiation and unforgeability of communication between the publickey infrastructure and the user based on the identity encryption environment are protected, and the safety and privacy requirements are met.
Owner:SOUTH CENTRAL UNIVERSITY FOR NATIONALITIES
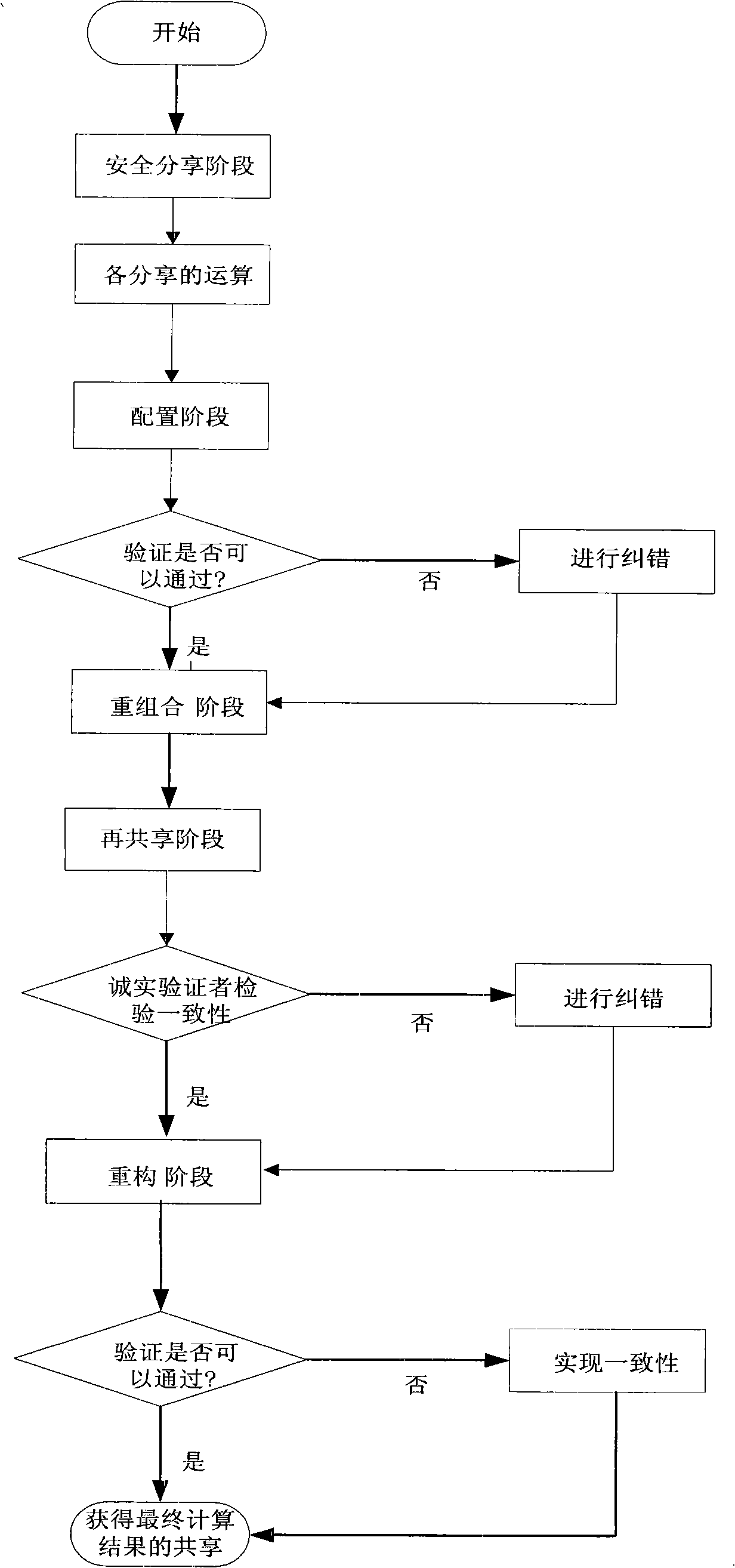
Cryptography distributed calculation and step-by-step verification method with fault-tolerant function
InactiveCN101325596AAchieve efficiencyTo achieve fault toleranceError preventionAccess structureTheoretical computer science
The invention discloses a fault tolerant cryptography distributed computing and multiple step testing method which belongs to the distributed computing field. The method comprises: 1) each member carries out the shared operation separately; 2) every member generates stochastic polynomial according to the required access structure and exchanges the datum induced from the stochastic polynomial; 3) every member generates combined stochastic polynomial by the received stochastic polynomial data together; 4) the result of step1) is re-shared by the combined stochastic polynomial and the re-shared result is distributed to every member; 5) each member further combines and reconstructs the receives re-shared data to gains the final result and a new re-share; 6) every member reconstructs the true result by exchanging the new re-share. The invention is a fault-tolerant and high efficient method with protocol safety, solves the problems of mass traffic and low efficiency in traditional algorithm and assures the continuity in secure computation.
Owner:PEKING UNIV
Rock mass RBI and RQD index measuring method
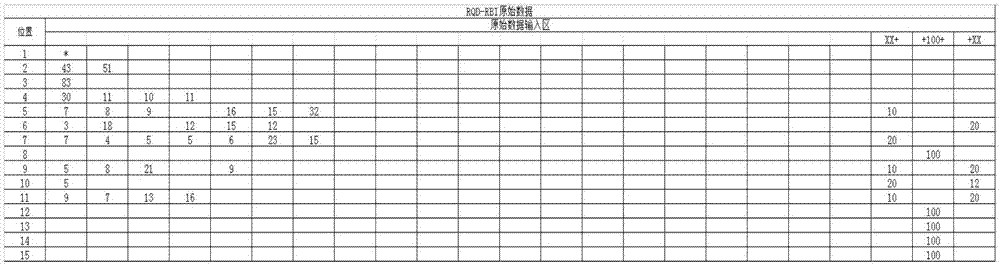
InactiveCN106874251AAccurate measurementGood repeatabilityComputation using non-contact making devicesText processingAnalysis methodMass analysis
The invention relates to the field of rock mass analysis, and provides an RQD and RBI based rock mass structural characteristic analysis method. An engineer can rapidly analyze a rock mass at a designated zone. The method comprises the steps that piles are arranged on an adit every one meter, and the piles are numbered in sequence; the rock mass between every two adjacent piles is adopted as a measuring unit, and the length of the rock mass at the 1-meter band course position inside each measuring unit is measured and recorded in sequence; an electronic spreadsheet is used for storing rock mass length data larger than or equal to 3 cm; the electronic spreadsheet stores data according to M rows and N columns, wherein M is determined by the starting and ending pile numbers of the adit, N is equal to 24, the first column is a pile number row, the 22nd-24th columns are XX+,+XX+ and +XX columns, and the XX+,+XX+ and +XX columns are used for storing data of crossing units; a calculation program is opened for performing RQD or RBI analysis. The method is applicable to adit rock mass analysis.
Owner:CHINA HYDROELECTRIC ENGINEERING CONSULTING GROUP CHENGDU RESEARCH HYDROELECTRIC INVESTIGATION DESIGN AND INSTITUTE
Migration data verification method for power dispatching automation system
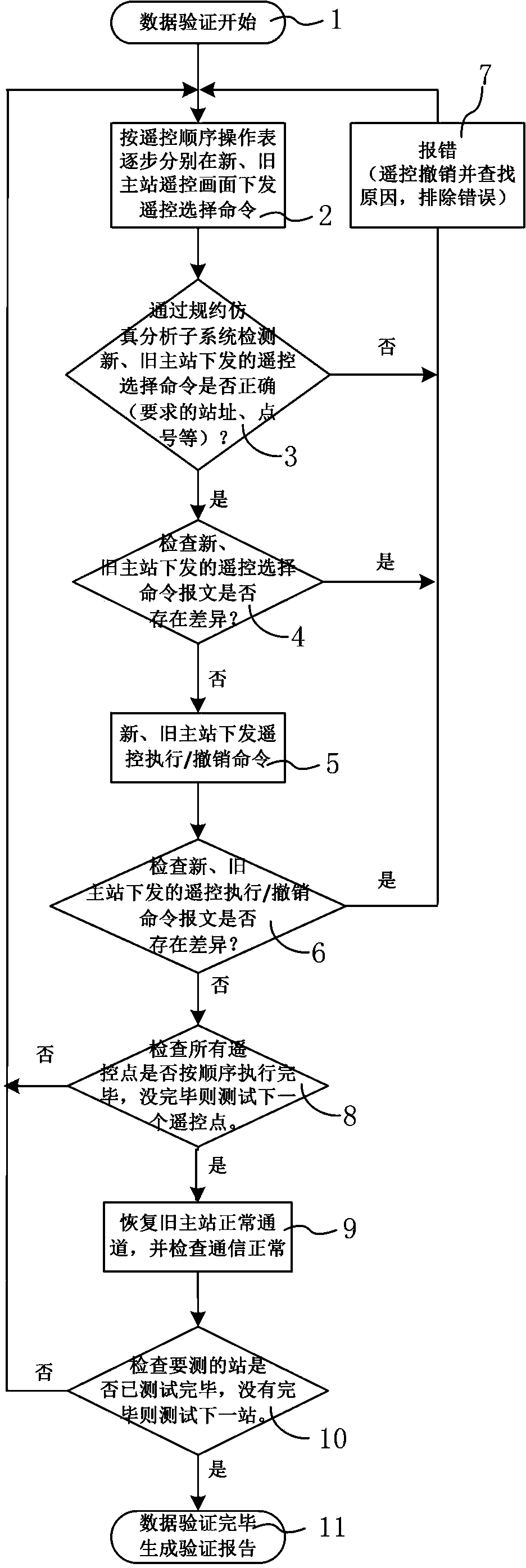
The invention discloses a migration data verification method for a power dispatching automation system. The migration data verification method comprises the steps of selecting a new master station and an old master station corresponding to service migration of the power dispatching automation system, selecting some to-be-verified substation in the old master station, disconnecting a normal communication channel of the to-be-verified substation and the old master station and establishing a corresponding analog substation, enabling remote control points to be selected in the new master station and the old master station for the analog substation and serve as current remote control points, sequentially issuing a remote control selection command, a remote control execution command or a remote control revocation command according to the current remote control points, collecting original data of issued commands of the current new master station and the current old master station through the analog substation, checking and comparing the original data to finish data verification of every remote control point, and finally restoring the normal communication channel of the to-be-verified substation and the old master station. The migration data verification method can guarantee migration of the power dispatching automation system between the new master station and the old master station, and has the advantages of being quick in verification speed, high in verification efficiency, good in verification accuracy, and simple and practical.
Owner:STATE GRID CORP OF CHINA +1
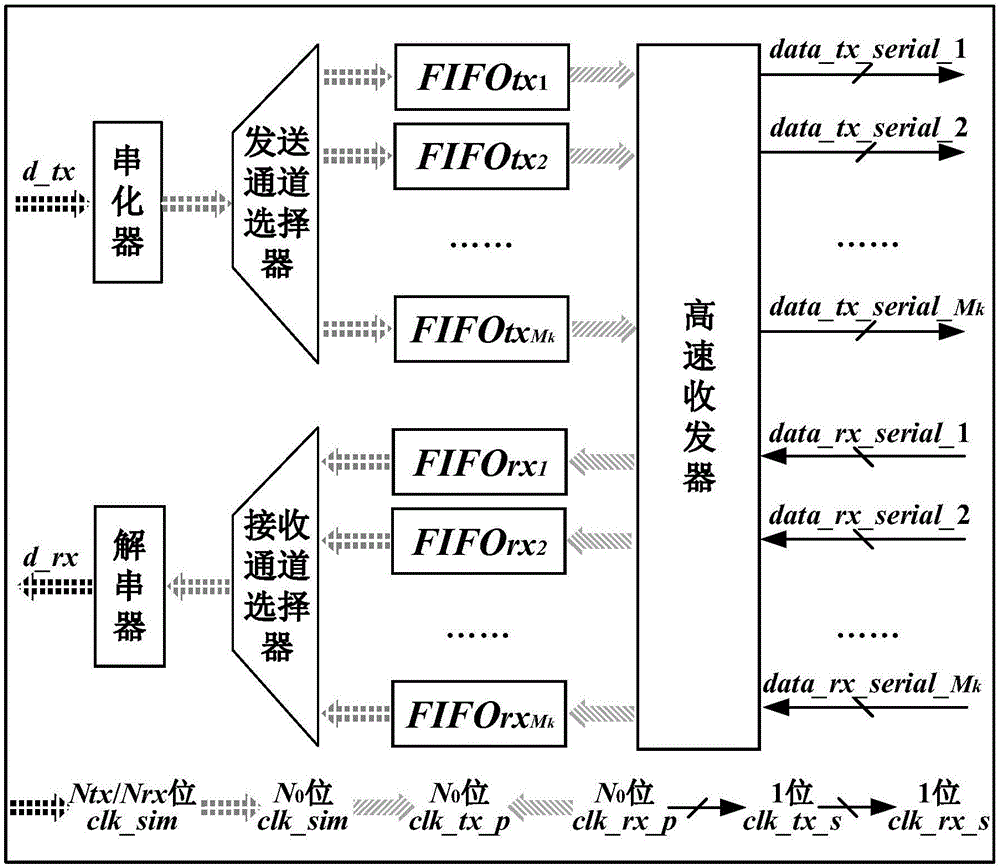
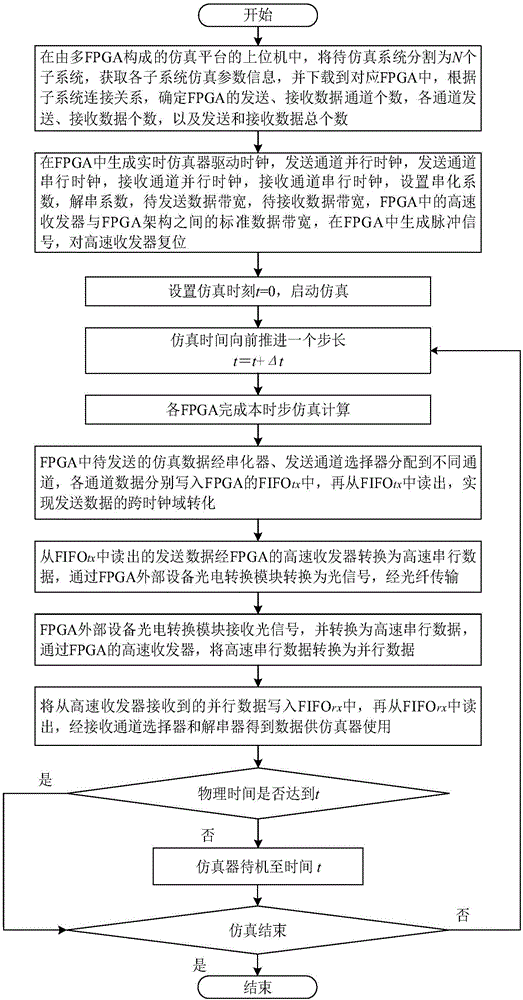
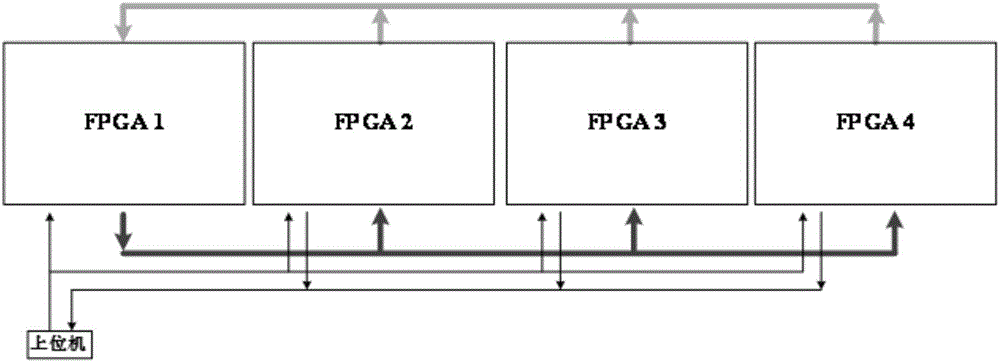
Method for designing internal interface of real-time emulator of active power distribution network based on multi-FPGA (field programmable gate array)
InactiveCN106844256AGuaranteed stabilityGuaranteed versatilityElectric digital data processingComplete dataTransceiver
A method for designing an internal interface of a real-time emulator of an active power distribution network based on multi-FPGA (field programmable gate array) comprises the following steps: 1) downloading information of each subsystem into the corresponding FPGA and initializing parameters of the internal interface; 2) setting emulation time t to be equal to 0 and starting emulation; 3) propelling the emulation time forwards by one step length, wherein t is equal to t plus delta t; 4) performing emulation calculation on each FPGA; 5) after performing serialization and channel distribution on to-be-transmitted data of each FPGA, converting the data into high-speed serial data by a high-speed transceiver and transmitting to the target FPGA; 6) receiving the high-speed serial data and converting into parallel data by the high-speed transceiver to further complete data splicing and deserialization; and 7) judging whether the emulation time reaches emulation ending time or not, ending emulation if the emulation time reaches the emulation ending time, otherwise, returning to the step 3). By the method, correctness and high efficiency of data communication in the emulator are realized while stability and universality of the internal interface of the emulator are guaranteed, and foundation is laid for real-time emulation of the active power distribution network based on multi-FPGA.
Owner:TIANJIN UNIV
Method and device for exhibiting information by utilizing animation
Owner:TENCENT TECH (SHENZHEN) CO LTD
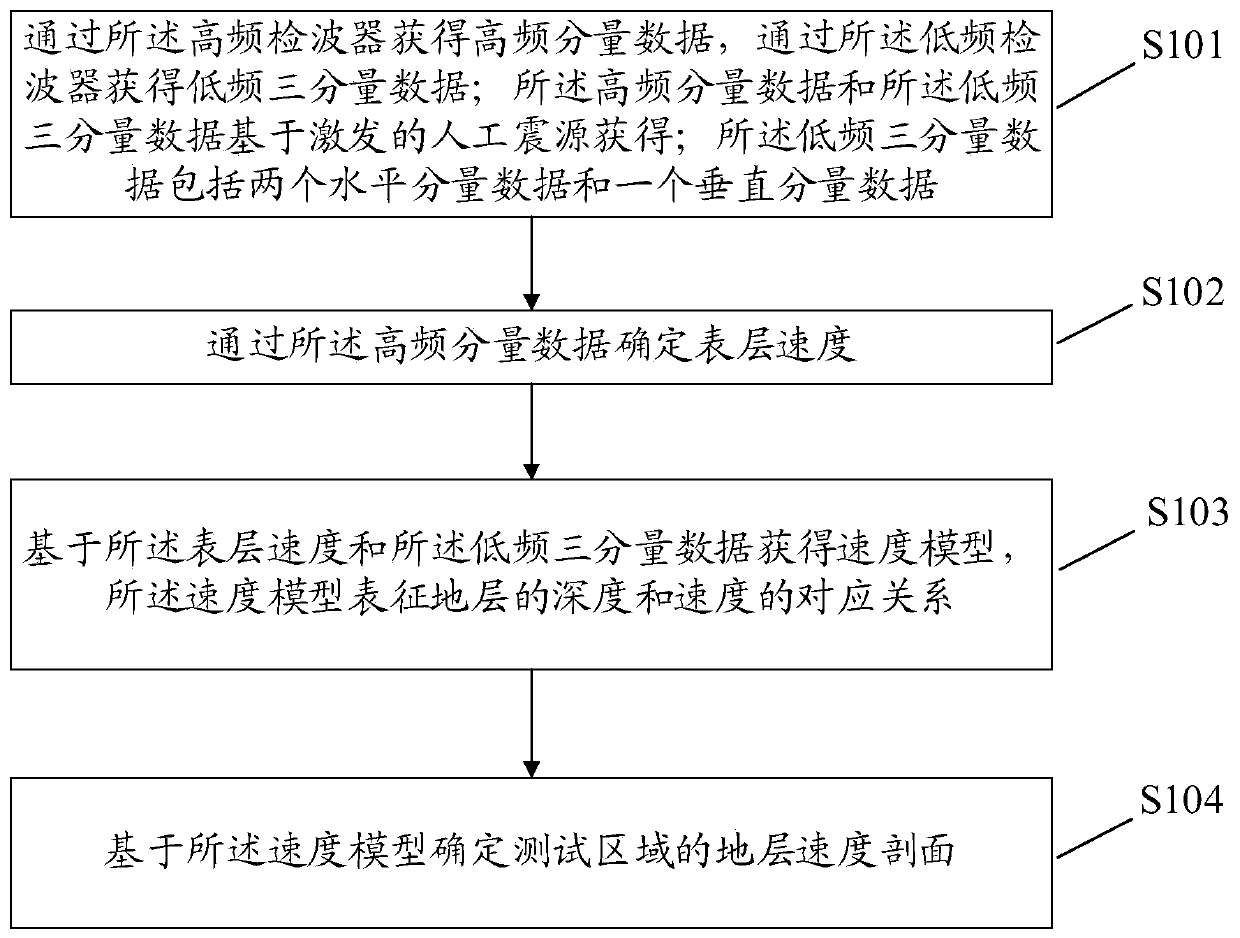
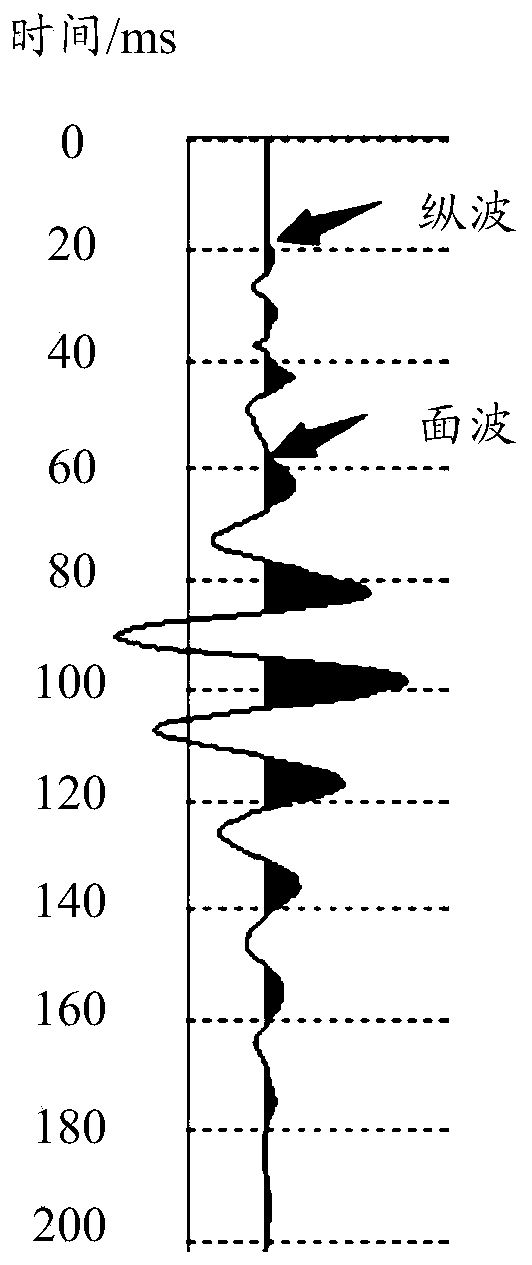
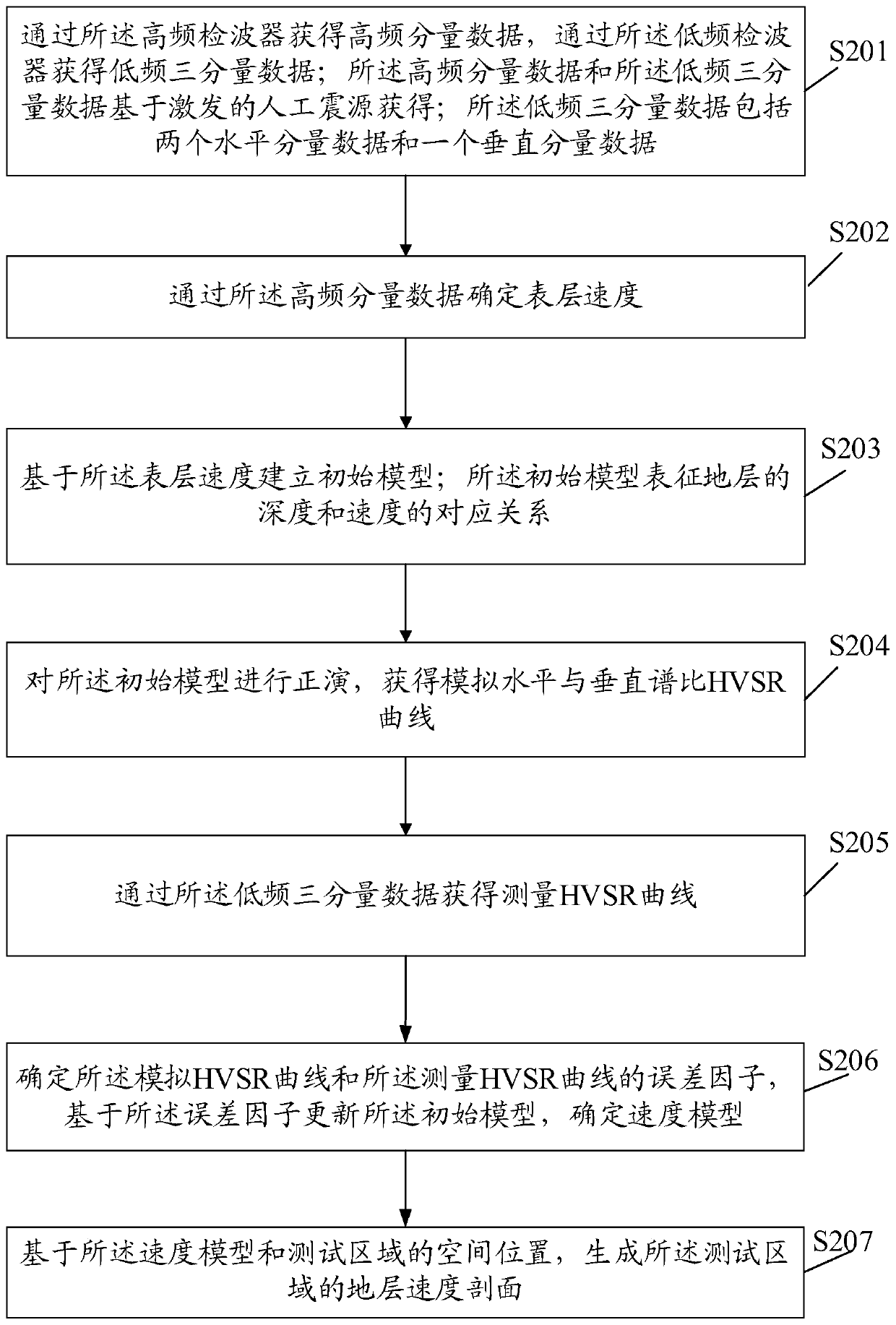
Geological exploration detecting method and device and storage medium
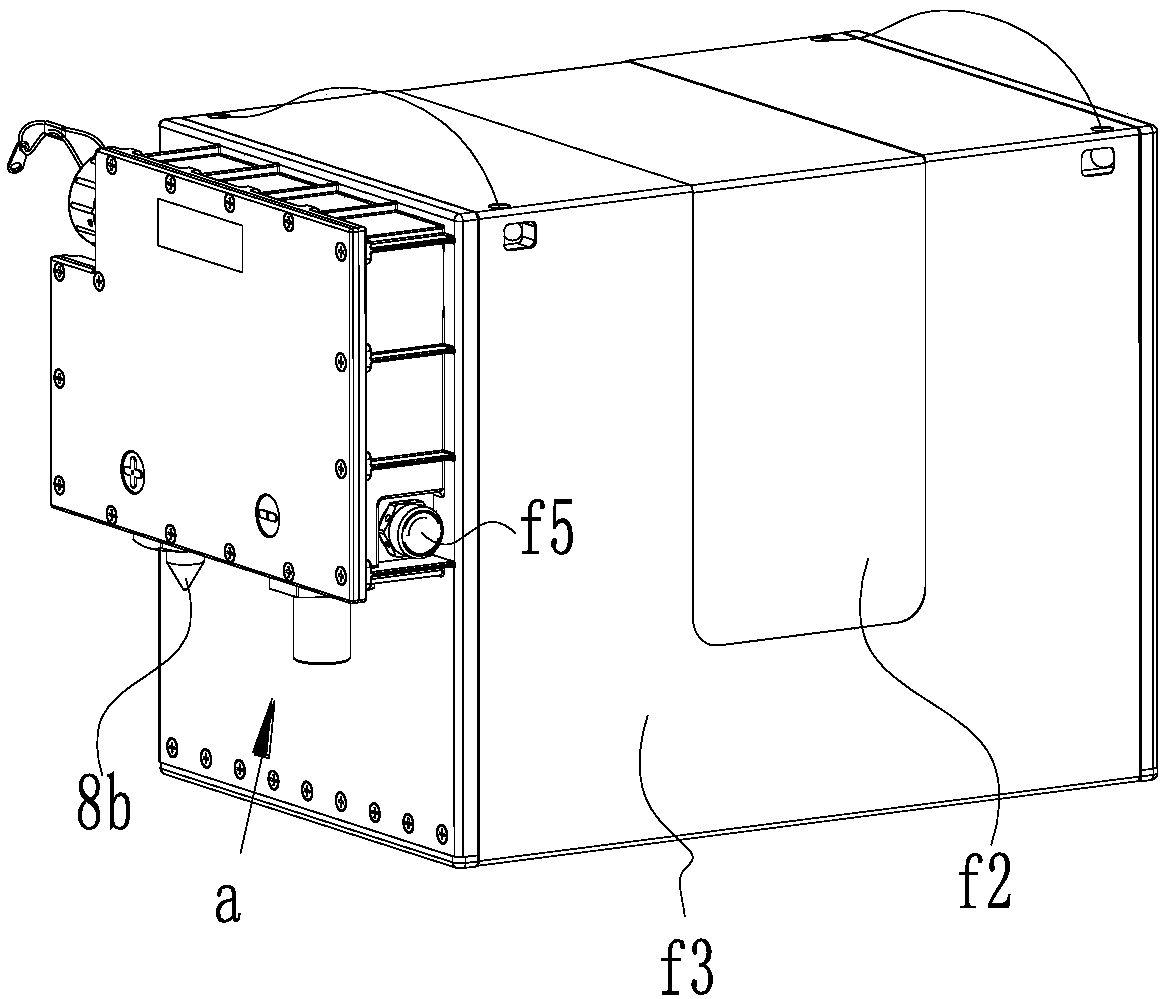
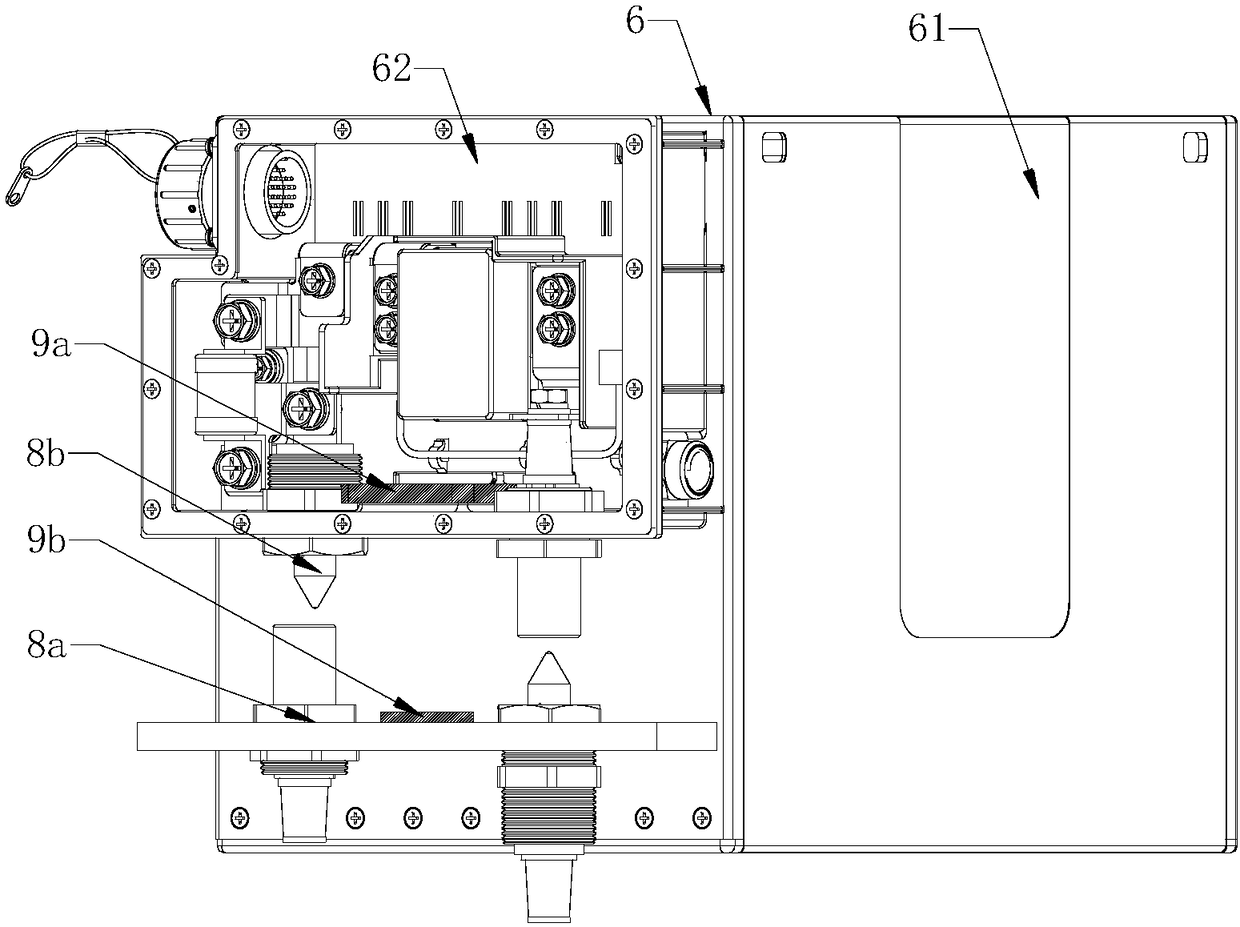
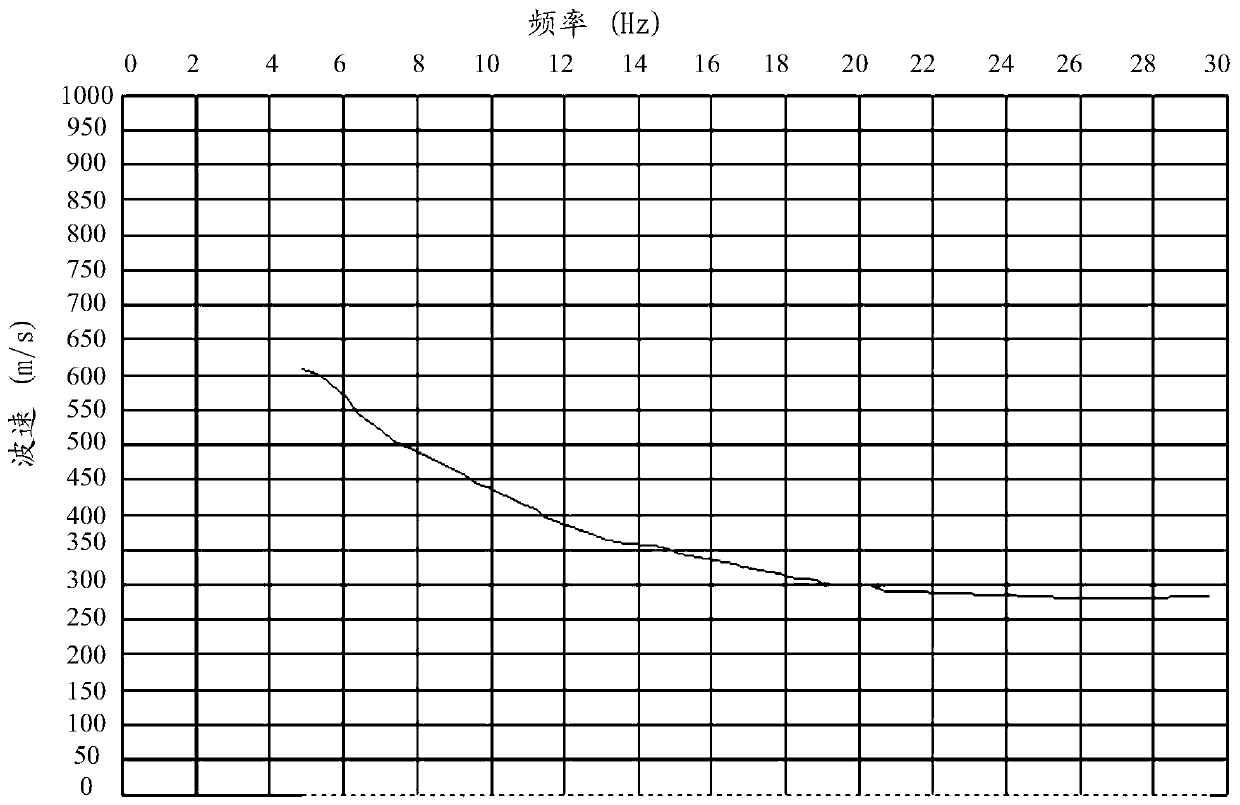
The embodiment of the invention discloses a geological exploration detecting method and device and a storage medium. The method is applied to a four-component collecting device including a high-frequency detector for collecting high-frequency component data and a low-frequency detector for collecting low frequency three-component data. The method comprises: step one, acquiring high-frequency component data by the high-frequency detector and acquiring low-frequency three-component data by the low-frequency detector; to be specific, acquiring the high-frequency component data and the low-frequency three-component data based on an excited artificial source and enabling the low-frequency three-component data to contain two horizontal component data and one vertical component data; determiningthe velocity of a surface layer by using the high-frequency component data; acquiring a velocity model characterizing a corresponding relationship between the depth and velocity of the stratum based on the surface layer velocity and the low-frequency three-component data; and determining a velocity profile of the stratum of a testing area based on the velocity model.
Owner:CHINA RAILWAY SIYUAN SURVEY & DESIGN GRP
Cluster-type play control system and method as well as management center of system
ActiveCN103391456APrevent tamperingAvoid substitutionSelective content distributionControl systemComputer science
The invention relates to a cluster-type play control system and method as well as a management center of the system. The system comprises a management center and a media paly terminal, wherein the management center is used for manufacturing and generating a program list and providing media and fingerprints of the media which correspond to the program list, and the content of the list program comprises the fingerprints of the media; and the media play terminal is used for acquiring the program list, the media and the media fingerprints which belong to the terminal, calculating the fingerprints of the acquired media and comparing the calculated media fingerprints, the fingerprints of the acquired media and the media fingers contained in the program list, so that the correctness verification of downloaded files is realized. According to the cluster-type play control system and the method as well as the management center of the system, the program list and the media fingerprints are generated, and the program list comprises the fingerprints of the media, so that the correctness of the media in the whole centralized announcement process can be guaranteed to an extremely large extent.
Owner:XIAN NOVASTAR TECH
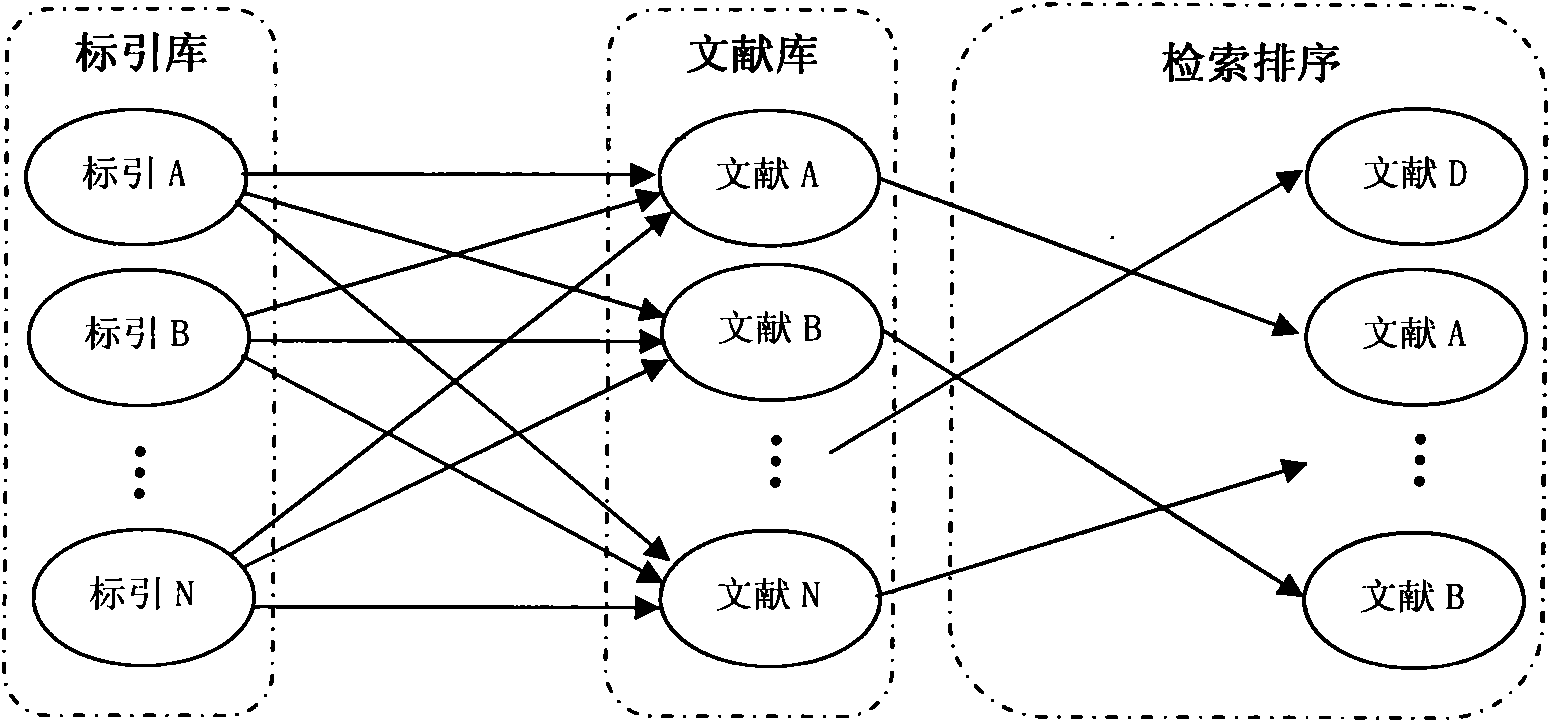
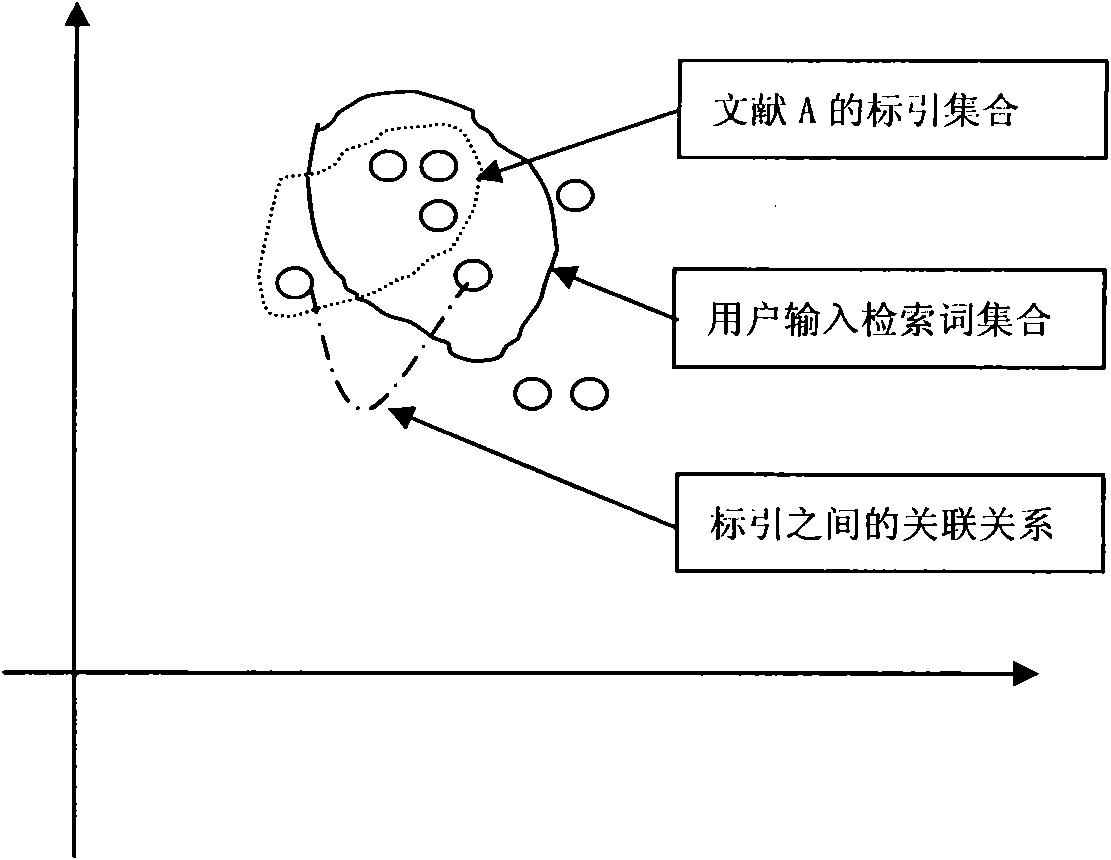
Information search sequencing method based on index association relation
InactiveCN102163222AAchieving correctness and noise immunityWeaken errors interfere with resultsSpecial data processing applicationsPaper documentDocument preparation
The invention discloses an information search sequencing method based on an index association relation, which belongs to the field of information analysis and aid decision making. The method comprises the following steps of: creating a document database and an index library, and creating the association between the document database and the index library; taking related search terms of each document as the indexes of the document to form a document model of the document; before searching, forming a search model with the set of all the search terms, namely the indexes, provided by users; and calculating the similarity between the search model and the document model of each document in the document database, sequencing the documents in a descending order, and providing the sequenced documents for the users as the final search result. The information search sequencing method based on the index association relation has the benefit that the interference of the errors on the result can be weakened under the circumstance of taking the mistaken indexes as reasoning conditions, by integrating the prior association relation between the indexes, the correct indexes can participate in the reasoning operation according to the wrong index conditions, and consequently, the correctness and the interference immunity of the reasoning can be implemented.
Owner:中国医学科学院医学信息研究所
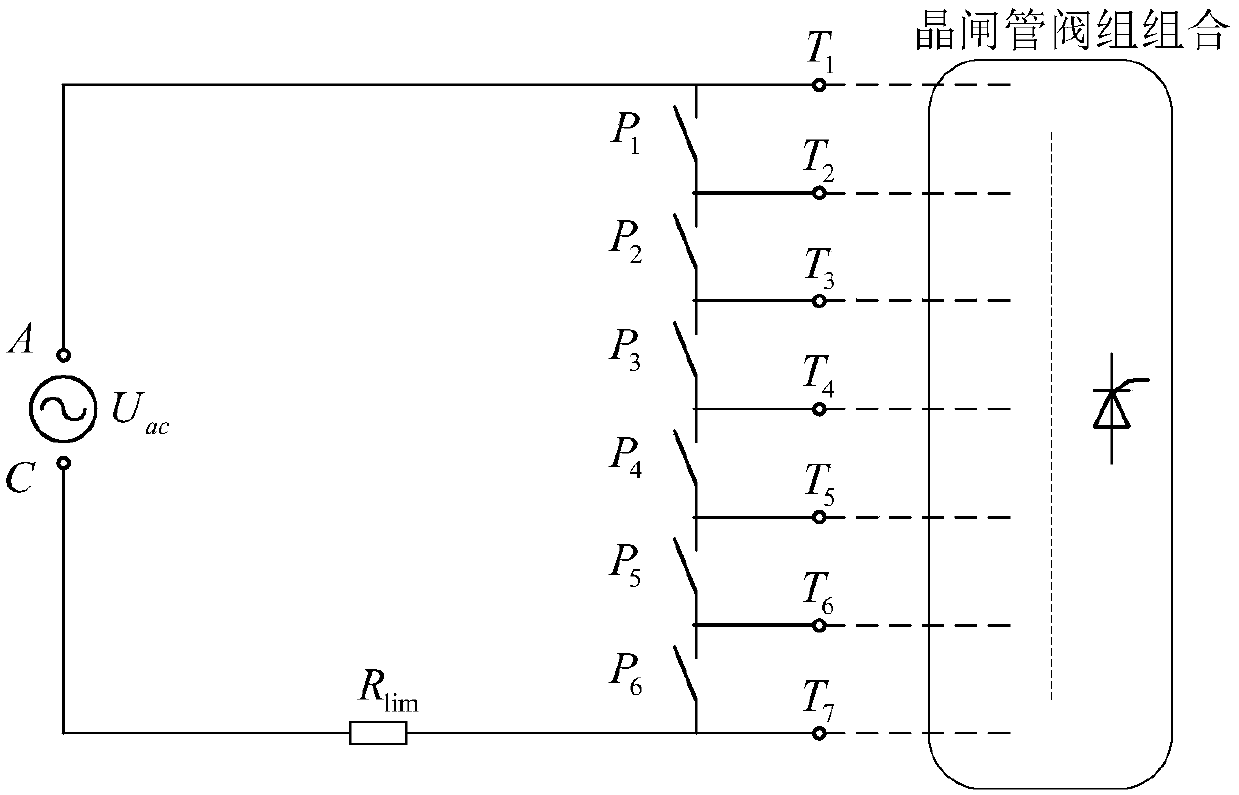
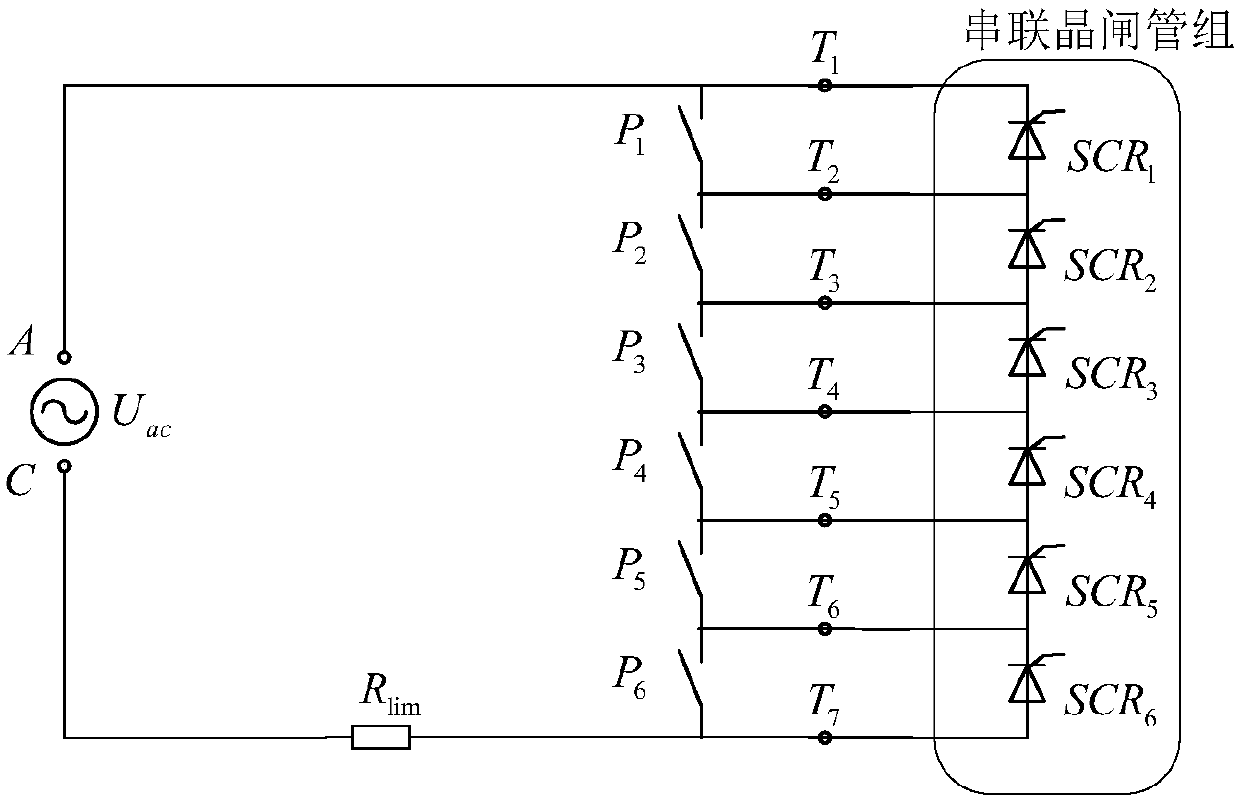
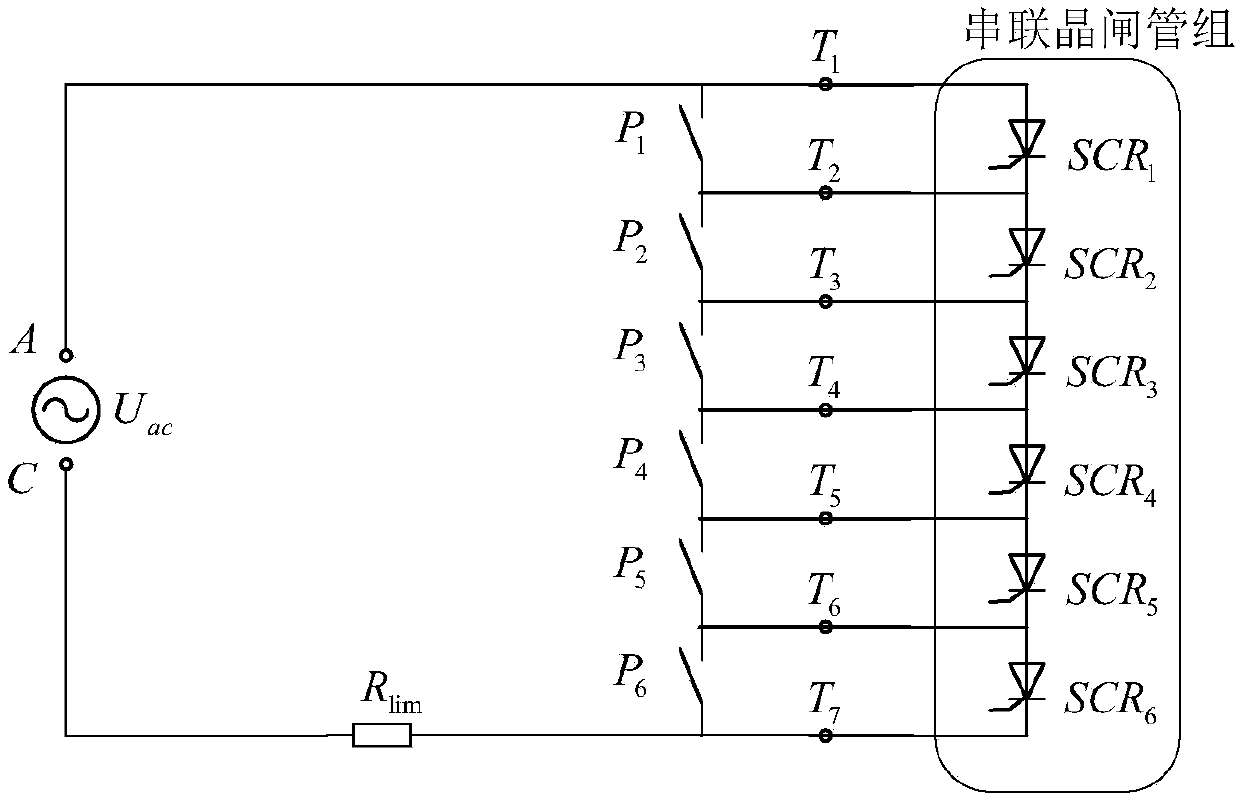
Method for testing small current of thyristors and pulse trigger loops thereof
ActiveCN109581176AImplement testPrecise positioningElectronic circuit testingIndividual semiconductor device testingElectrical resistance and conductanceCurrent limiting
The invention discloses a method for testing small current of thyristors and pulse trigger loops thereof. According to the method, a small current test loop is built through applying a test AC power supply outside an AK electrode of a tested thyristor and connecting a current-limiting resistor in series. When the test AC power supply applied to the AK electrode of the thyristor achieves a forwardvoltage peak, a pulse trigger loop of a static variable-frequency starting system valve control device conducts the tested thyristor, so that the tested thyristor is theoretically conducted for 1 / 4 ofa period; and through detecting the conduction time of the tested thyristor, judgment can be carried out to determine whether the tested thyristor and the pulse trigger loop thereof work normally ornot. The method is capable of correctly positioning abnormal thyristor element positions.
Owner:NARI TECH CO LTD
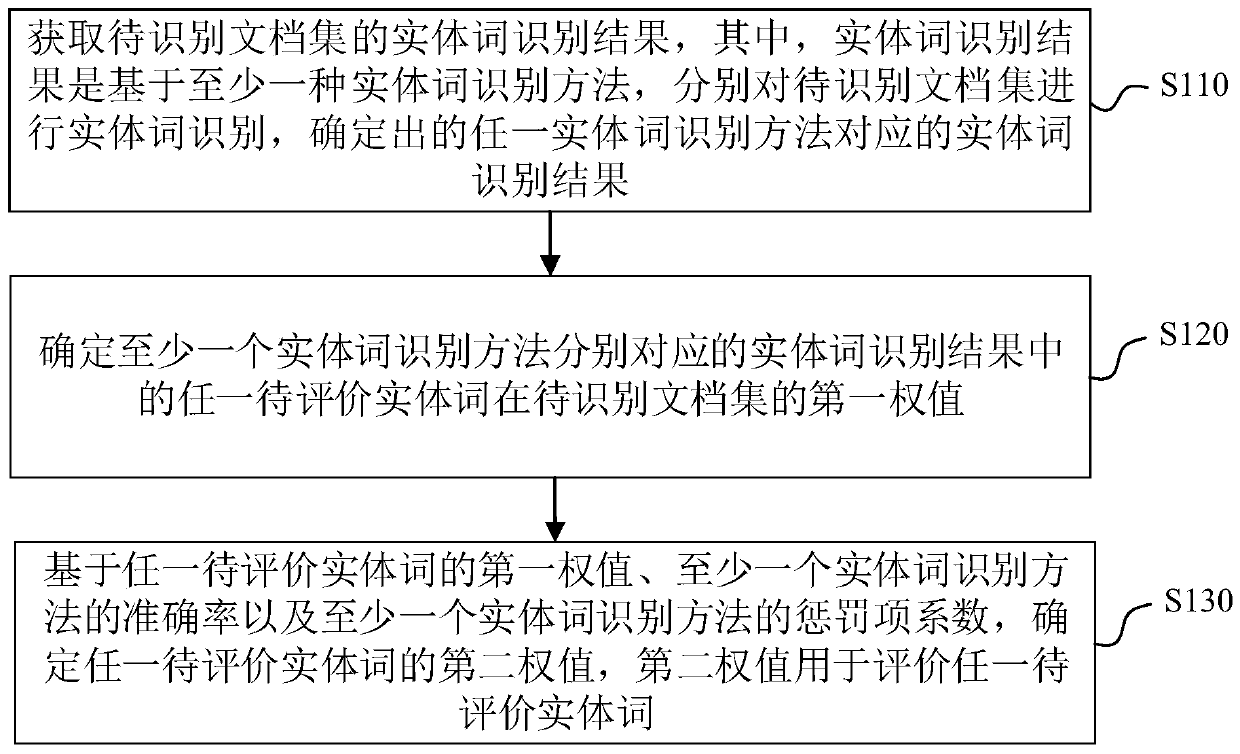
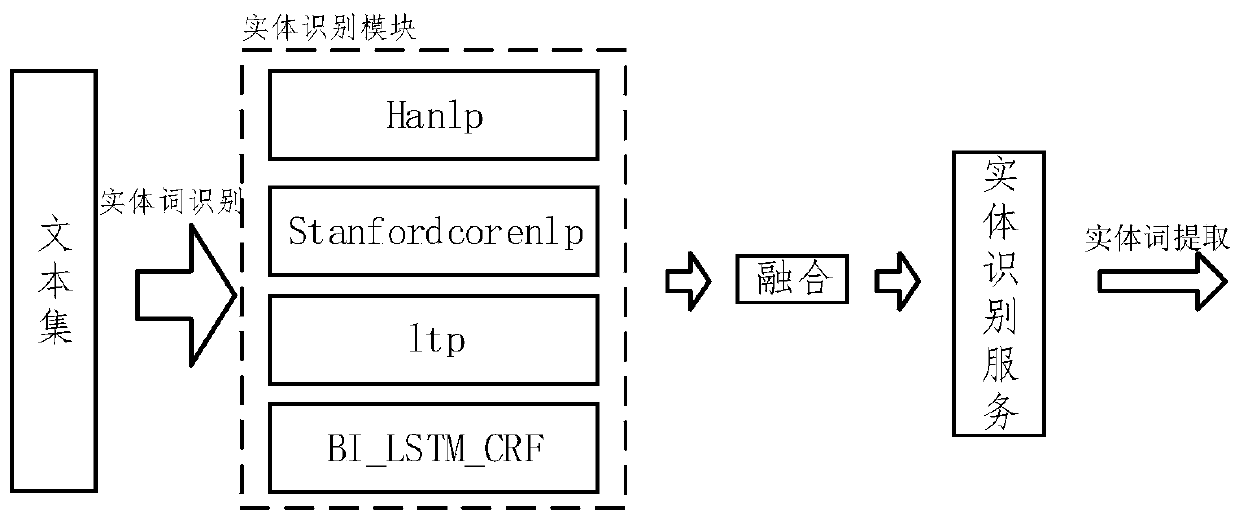
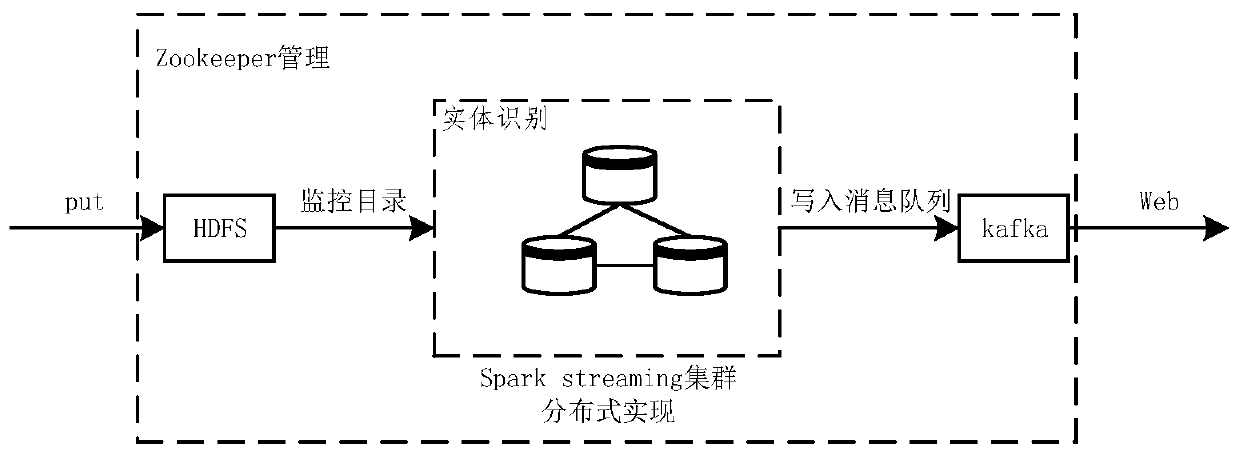
Entity word recognition result evaluation method, device and equipment and entity word extraction system
PendingCN109726400AImprove accuracyEasy to identifyDigital data information retrievalSpecial data processing applicationsPenalty coefficientWord recognition
The embodiment of the invention provides an entity word recognition result evaluation method, device and equipment and an entity word extraction system. The method comprises: acquiring an entity wordrecognition result of a to-be-recognized document set, wherein the entity word recognition result is an entity word recognition result corresponding to any determined entity word recognition method byconducting entity word recognition on the to-be-recognized document set on the basis of at least one entity word recognition method; Determining a first weight of any to-be-evaluated entity word in the entity word recognition result corresponding to the at least one entity word recognition method in the to-be-recognized document set; And determining a second weight of any entity word to be evaluated based on the first weight of any entity word to be evaluated, the accuracy of the at least one entity word recognition method and the penalty coefficient of the at least one entity word recognition method, the second weight being used for evaluating any entity word to be evaluated. According to the scheme of the embodiment, the correctness of the entity word recognition result is judged through the second weight, and the entity word recognition effect is effectively improved.
Owner:XINHUANET CO LTD
Block chain data sharing method and device based on LWE-CPABE and storage medium
The invention discloses a block chain data sharing method and device based on LWE-CPABE and a storage medium, and the method comprises the following steps: a data visitor sets an access control strategy, generates a master key and a public key based on the access control strategy, sends the public key to a block chain for storage, the master key entrusts a key center for storage, and the public key entrusts the key center for storage. Data to be published are encrypted into a ciphertext, the ciphertext is uploaded to the third-party storage, and the third-party storage sends a ciphertext storage address to the block chain; the data user obtains the master key from the key center, then synthesizes the master key into a user attribute key, and decrypts the obtained ciphertext by using the user attribute key to complete data sharing; according to the method, the security and the efficiency of data sharing are relatively high, the access control strategy can be conveniently updated, the calculation amount in the updating process is small, and more key space cost and encryption time cost are saved.
Owner:YUNNAN UNIVERSITY OF FINANCE AND ECONOMICS +1
Detection method of jumper wire sequence of antenna
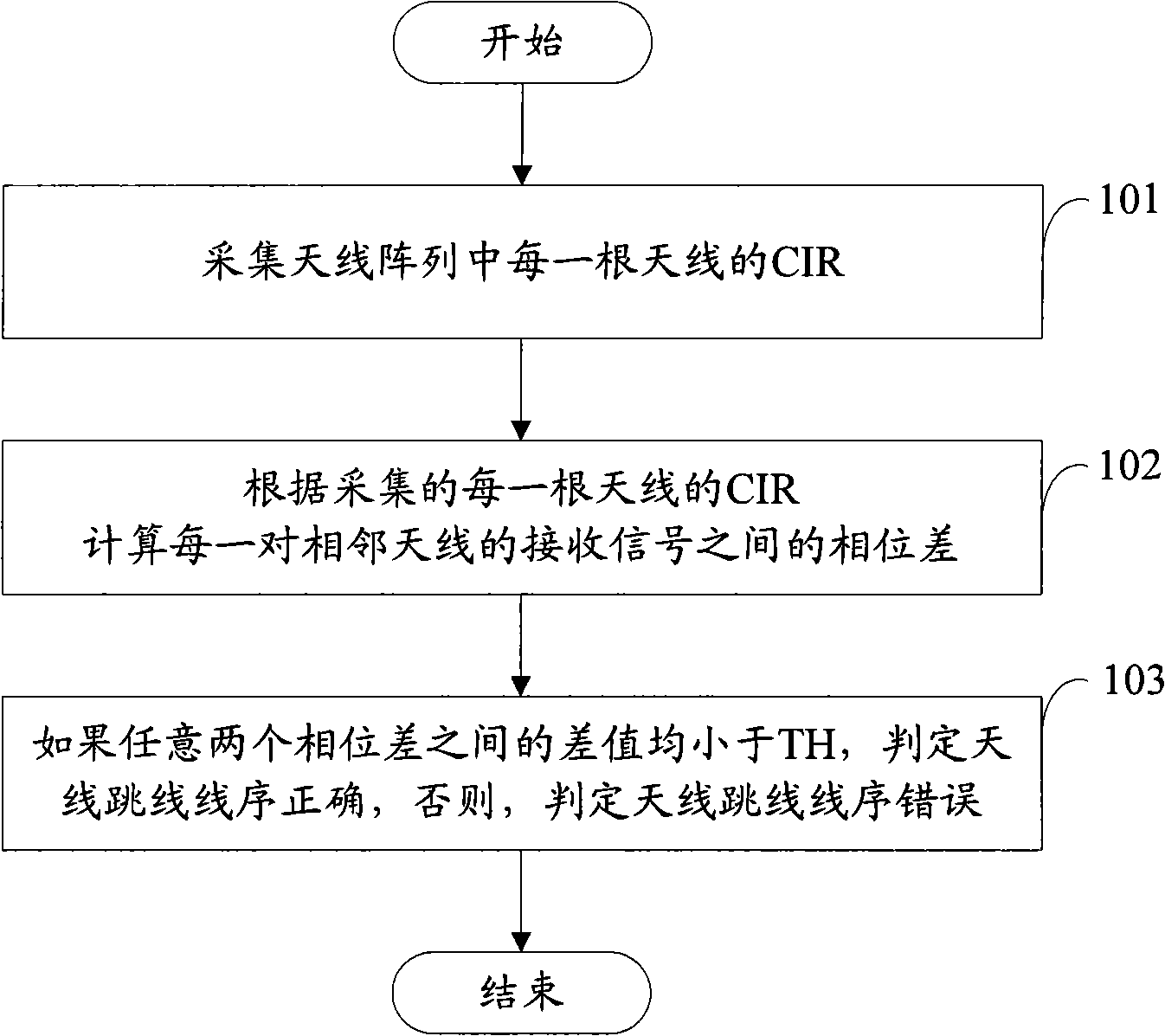
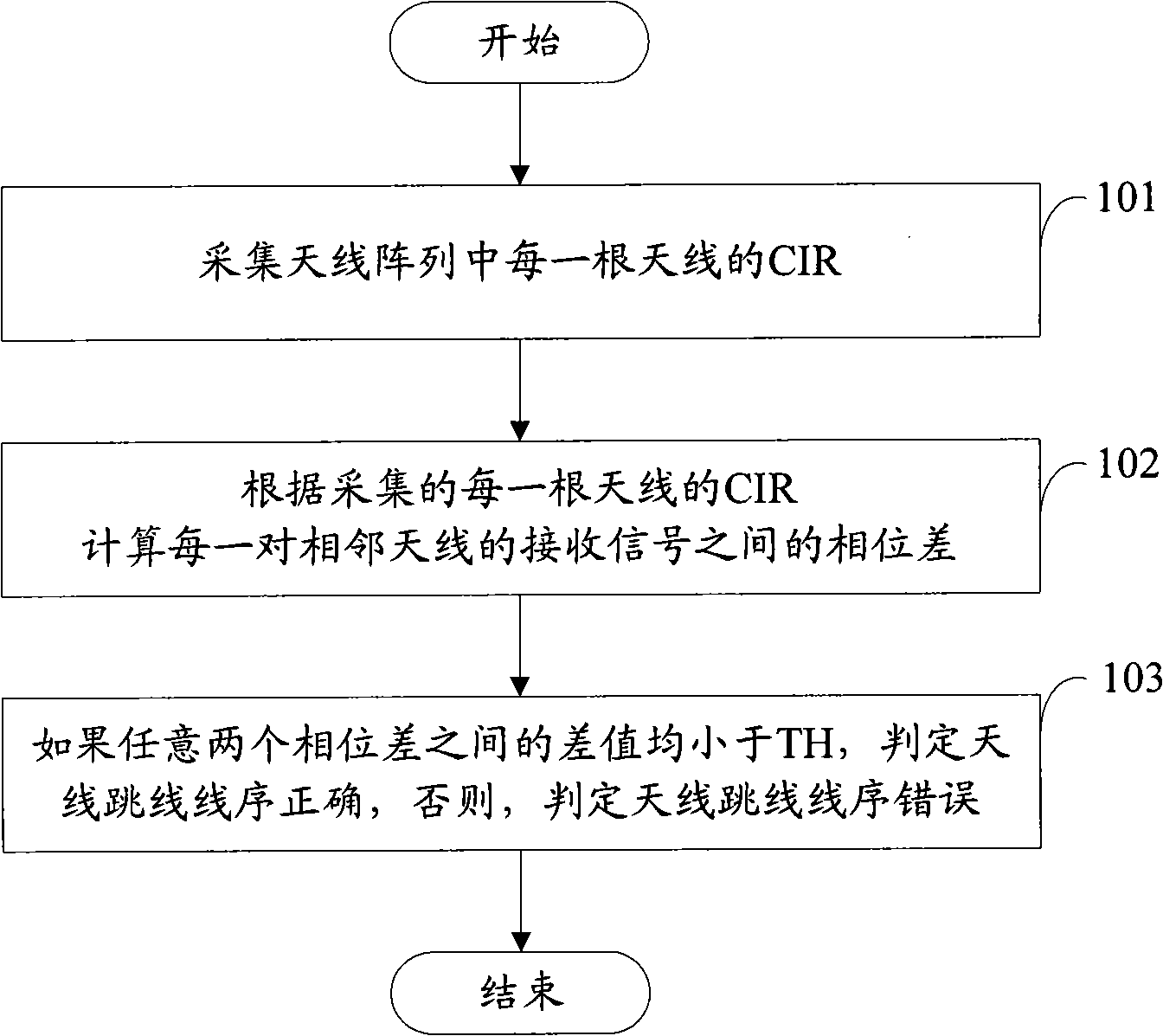
InactiveCN101989872AAchieve correctnessSpatial transmit diversityError prevention/detection by diversity receptionChannel impulse responsePhase difference
The invention discloses a detection method of the jumper wire sequence of an antenna, comprising the following steps of: previously setting a first threshold value; after an antenna array is completely installed, firstly acquiring the CIR (Channel Impulse Response) of each antenna in the antenna array; then calculating the phase difference between received signals of each pair of adjacent antennae according to the acquired CIR of each antenna; finally judging according to the difference value between the phase differences; if the difference value between any two phase differences is less thanthe first threshold value, judging that the jumper wire sequence of the antenna is accurate; and if not, judging that the jumper wire sequence of the antenna is wrong. The invention can be used for realizing the detection of the accuracy of the jumper wire sequence of the antenna.
Owner:TD TECH COMM TECH LTD
Wireless communication-based distributed type automobile battery power supply control system and method
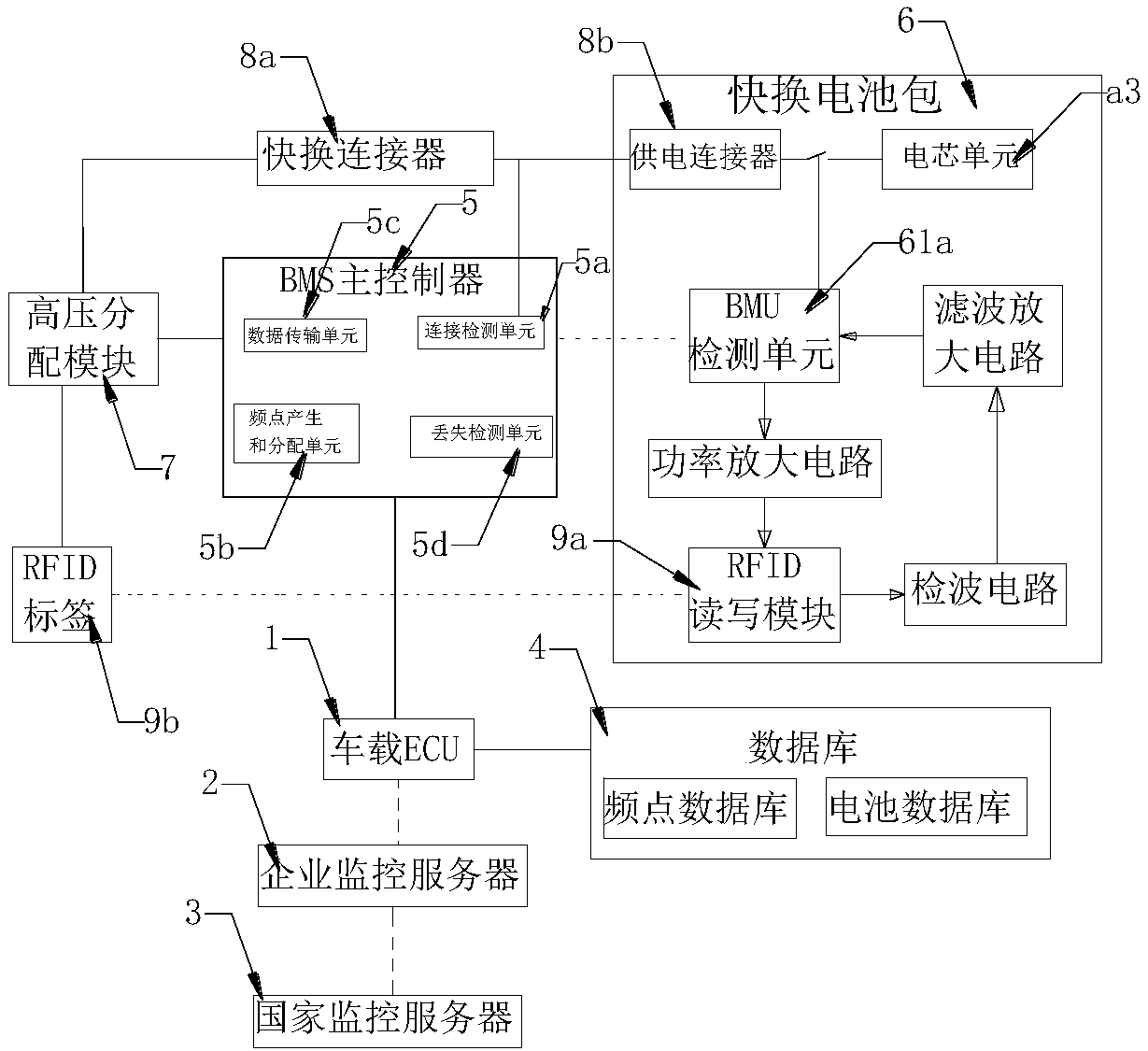
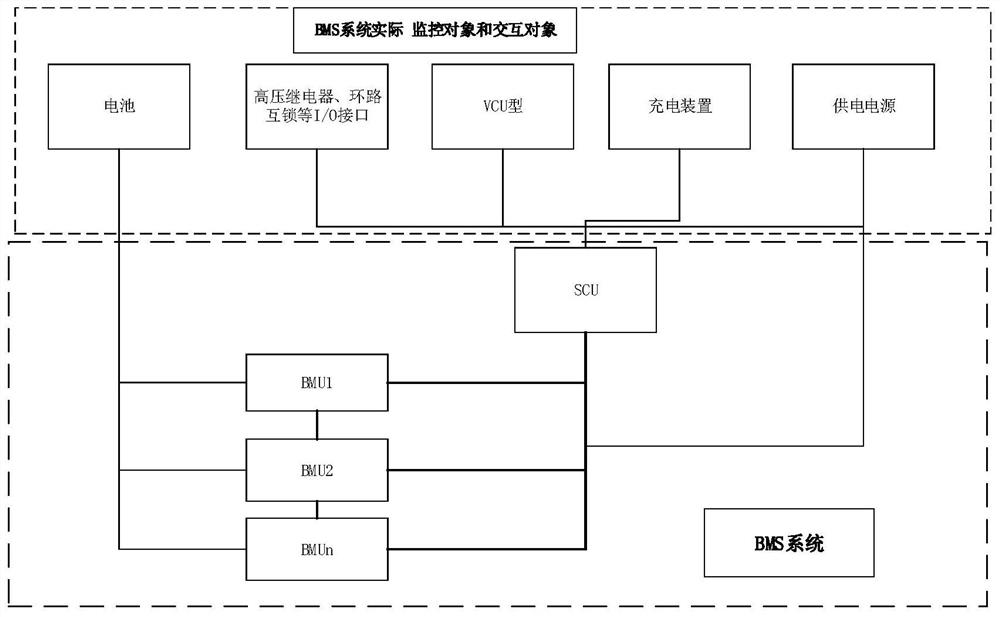
PendingCN108155320AGuaranteed reliabilityEnsure safetyBatteries circuit arrangementsSecondary cells charging/dischargingControl systemMaster controller
The invention discloses a wireless communication-based distributed type automobile battery power supply control system and method. The wireless communication-based distributed type automobile batterypower supply control system comprises a vehicle-mounted ECU (electronic control unit) which is connected in a wireless mode with an enterprise monitoring server, and the enterprise monitoring server is connected with a wireless mode with a national monitoring server and connected with a database; the vehicle-mounted ECU is connected with a BMS (battery management system) master controller; the BMSmaster controller is used for establishing wireless connection with a quick-change battery pack according to the frequency point data of the database and acquiring the battery pack data of the quick-change battery pack, and the battery pack data is transmitted to the national monitoring server through the vehicle-mounted ECU and the enterprise monitoring serer. The wireless communication-based distributed type automobile battery power supply control system achieves real-time uploading of the battery pack data to the enterprise monitoring server and the national monitoring server and further achieves battery pack data monitoring. The quick-change battery pack is high in power storage capacity, good in portability and reliable and safe in electric connection, and through random frequency divided connection, achieves communication independence and small interference.
Owner:力帆科技(集团)股份有限公司
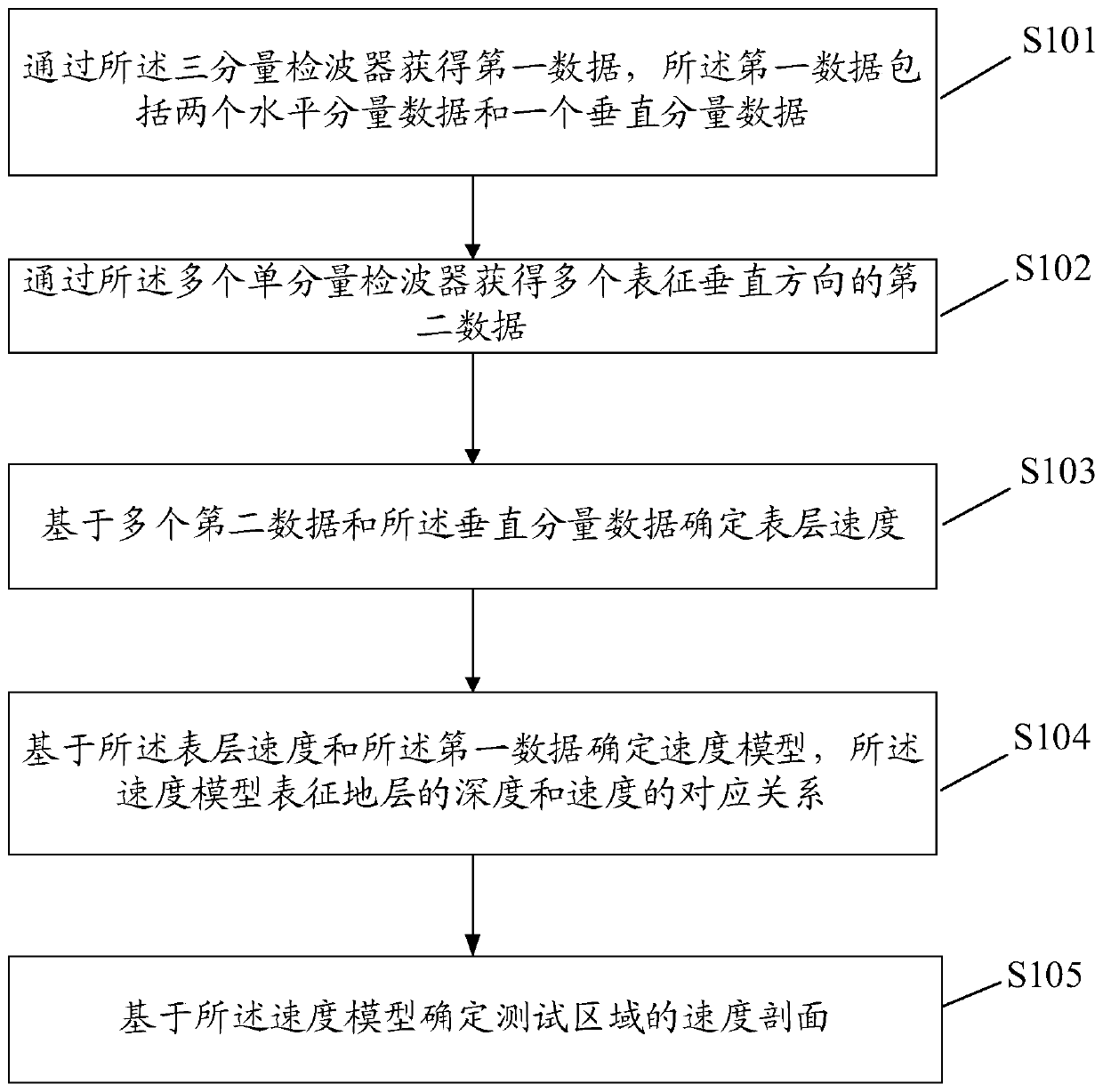
Seismic noise imaging exploration method and apparatus, and storage medium
The embodiment of the invention discloses a seismic noise imaging exploration method and apparatus, and a storage medium. The method is applied to an exploration system including a three-component detector and a plurality of single-component detectors; and the plurality of single-component detectors are arranged on the circumference using the location of the three-component detector as the center.The method comprises: acquiring first data, including two horizontal component data and one vertical component data, of by the three-component detector; acquiring a plurality of second data characterizing a vertical direction by the plurality of single-component detectors; determining the velocity of a surface layer based on the plurality of second data and the vertical component data; and determining a velocity model that characterizes a correspondence relationship between the depth and velocity of the stratum according to the surface layer velocity and the first data; and determining a velocity profile of the testing area based on the velocity model.
Owner:CHINA RAILWAY SIYUAN SURVEY & DESIGN GRP
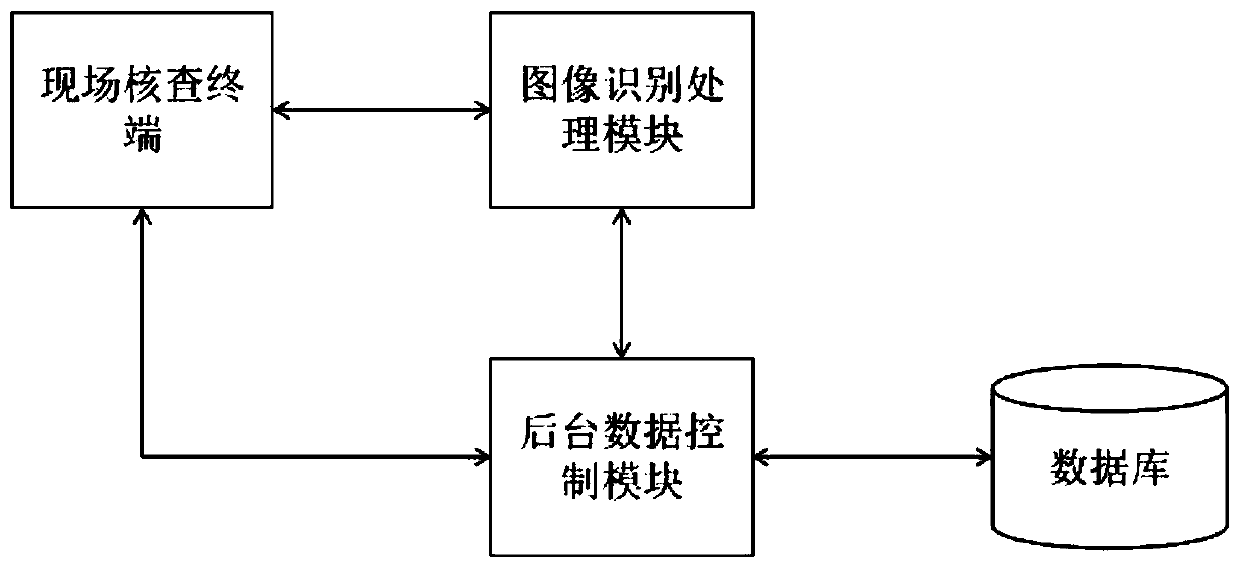
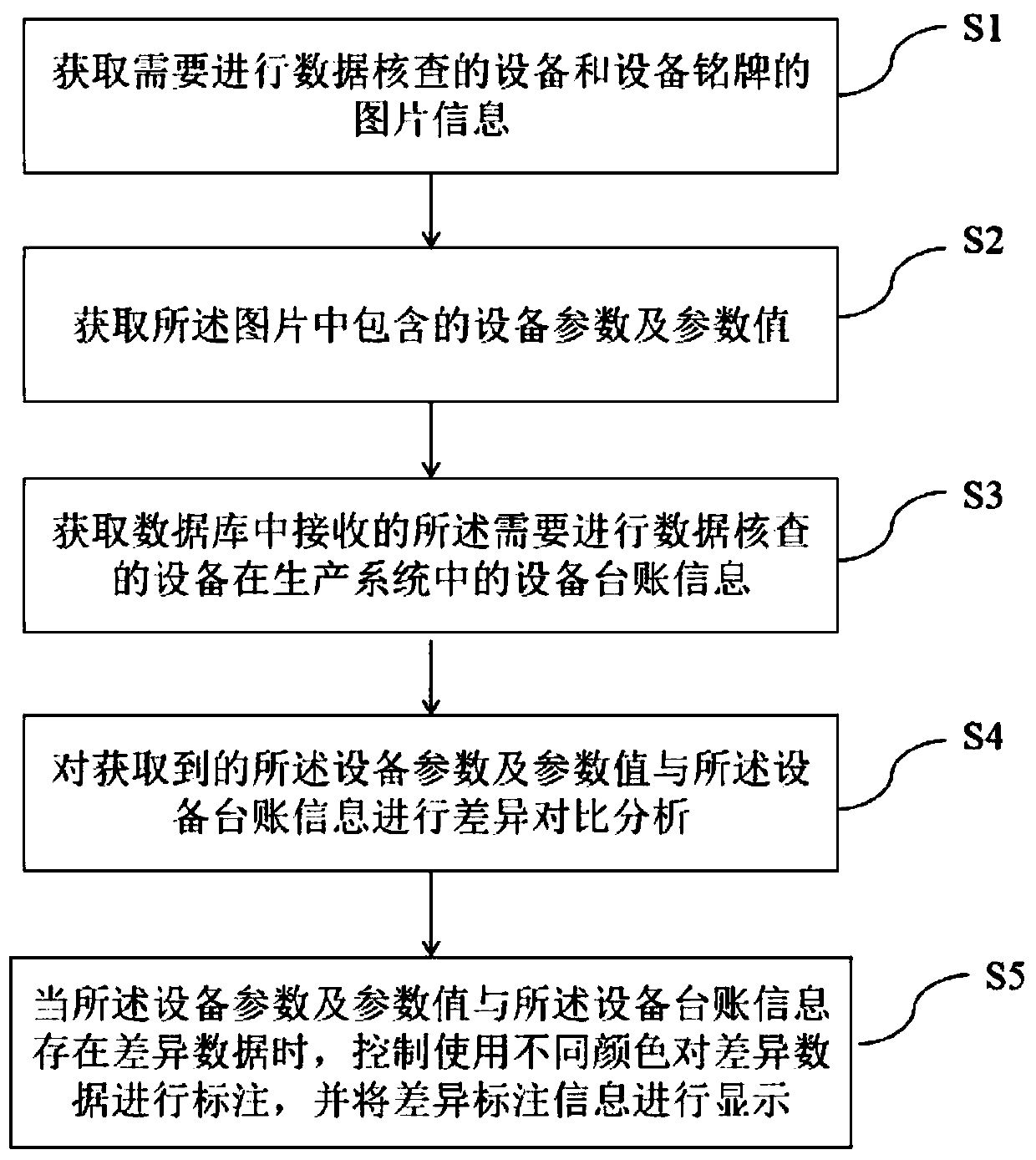
Power equipment data checking method and system based on image recognition
InactiveCN110287935AReduce workloadAchieve correctnessData processing applicationsDatabase management systemsSource Data VerificationPower equipment
The embodiment of the invention provides a power equipment data checking method based on image recognition. An image recognition processing module is used for carrying out image recognition on acquired image information of equipment and the equipment nameplate which need to be subjected to data verification and analyzing the image recognition content. The relationship matches with the equipment standing book information in the existing system. A background data control module is used for carrying out difference comparison analysis on the obtained equipment parameters and parameter values and the equipment standing book information. The method has the advantages that equipment data correctness and integrity are checked and marked, data difference is marked, rectification is facilitated, workload of manual data checking and data input is reduced, the problem of low data quality caused by personnel input errors is avoided at a data source, the data management level is integrally improved, and a basis is provided for effective data management.
Owner:云南电网有限责任公司信息中心
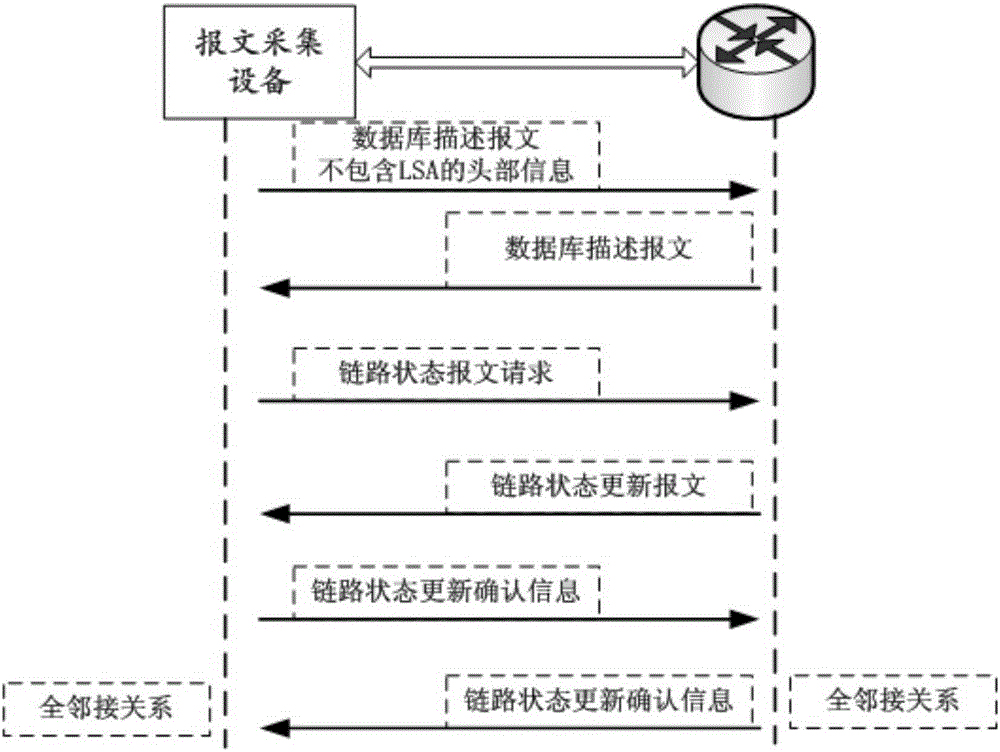
Internet protocol version 6 (IPv6) based open shortest path first (OSPF) network routing information passive collection method and system
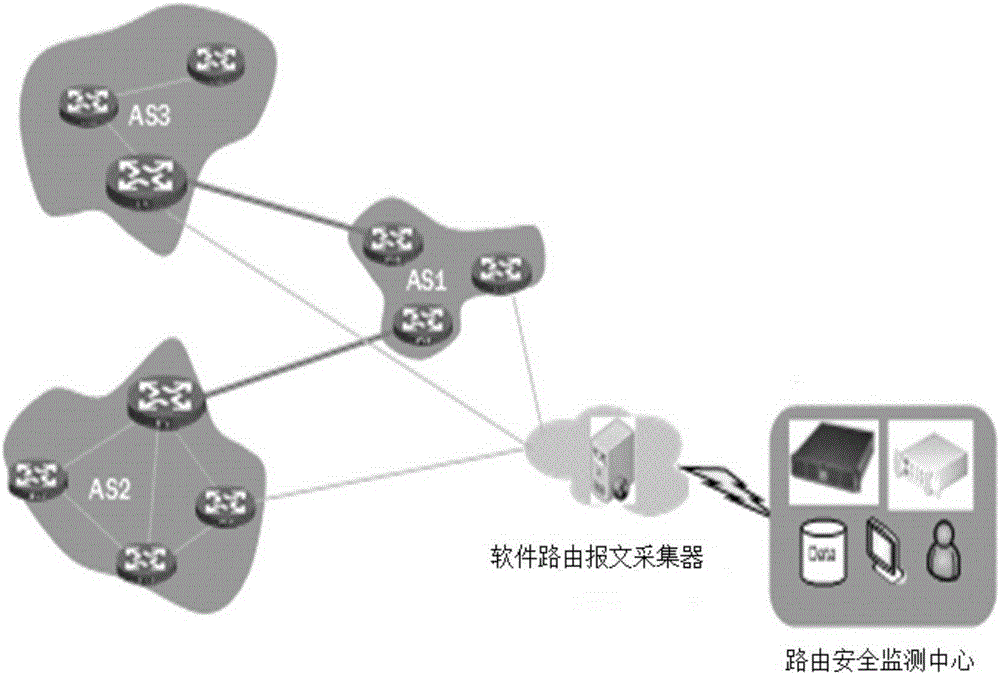
InactiveCN105306362AGuaranteed real-timeGuarantee the independence of message informationData switching networksIp addressWeb environment
The invention relates to the technical field of network measurement, and more particularly to an internet protocol version 6 (IPv6) based open shortest path first (OSPF) network routing information passive collection method and system. The method comprises steps that an adjacency relation between routers in an IPv6 network is established, only a Hello message is sent between the routers so as to maintain a necessary adjacency relation, when a certain router receives link state advertisement information, the router directly sends the link state advertisement information to an adjacent router; and if the OSPF network in the IPv6 network is a multi-autonomous domain OSPF network, a full adjacency relation is established between a collection device and the router in each autonomous domain, and a tag is arranged at the head of a collected message, wherein the tag identifies the IP address of a sender of the collected message, and an autonomous system (AS) number, in which the collected message is, is determined according to the correspondence between the IP address and the AS number. According to the method, the OSPF routing information of the ASs of a plurality of autonomous domains is collected; and the method can collect information in a passive manner, does not affect the network environment, and can collect information in real time.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Hardware-in-loop closed-loop test method and system for battery management system
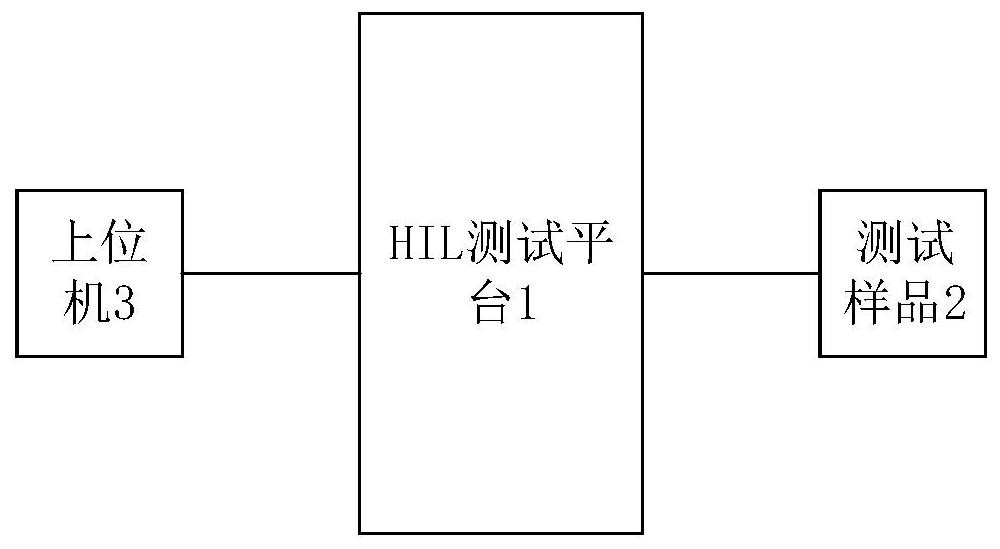
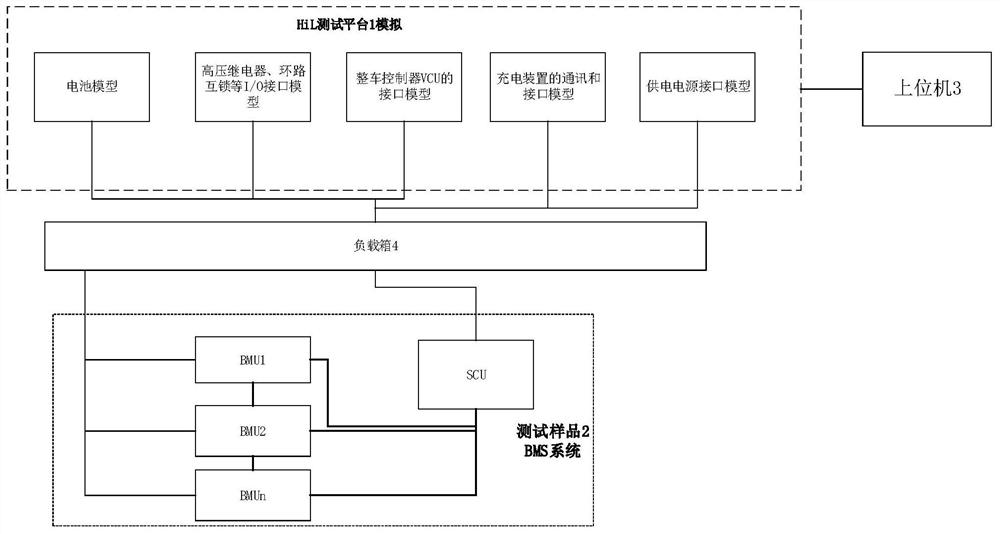
InactiveCN113253700AImprove closed loop rateImprove product designProgramme controlElectrical testingTest sampleTest platform
The invention relates to the field of battery management system testing, in particular to a hardware-in-loop closed-loop test method and system for a battery management system. The hardware-in-loop closed-loop test method for the battery management system comprises the steps of S1, connecting a test sample and an HIL test platform; S2, configuring a real-time external hardware interface by using Configuration Desk of the dSPACE, wherein the real-time external hardware interface is used for managing a signal path between external hardware and the model, and setting I / O and models of monitored and controlled objects based on dSPACE; and S3, generating codes from the I / O and the models of the monitored and controlled objects set in the step S3, downloading the codes to an HIL test platform through the ControlDesk of dSPACE to carry out signal interaction test, and recording experimental data. The method has the beneficial effects that the closed-loop rate of the BMS hardware simulation HIL test can be improved by setting various models of the monitored and controlled objects.
Owner:HEFEI GUOXUAN HIGH TECH POWER ENERGY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com