Construction method of division protocol based on cryptology in distributed computation
A technology of distributed computing and construction methods, applied in key distribution, can solve the problems of network attack defense and countermeasures, achieve the correctness and legitimacy of the algorithm, overcome the huge communication volume and low computational complexity Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
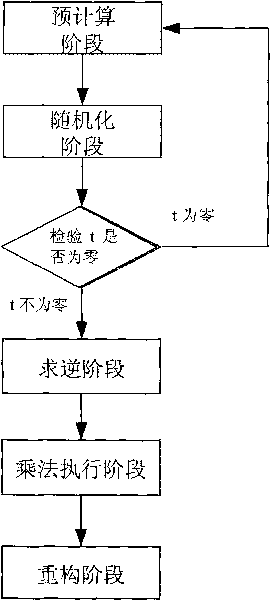
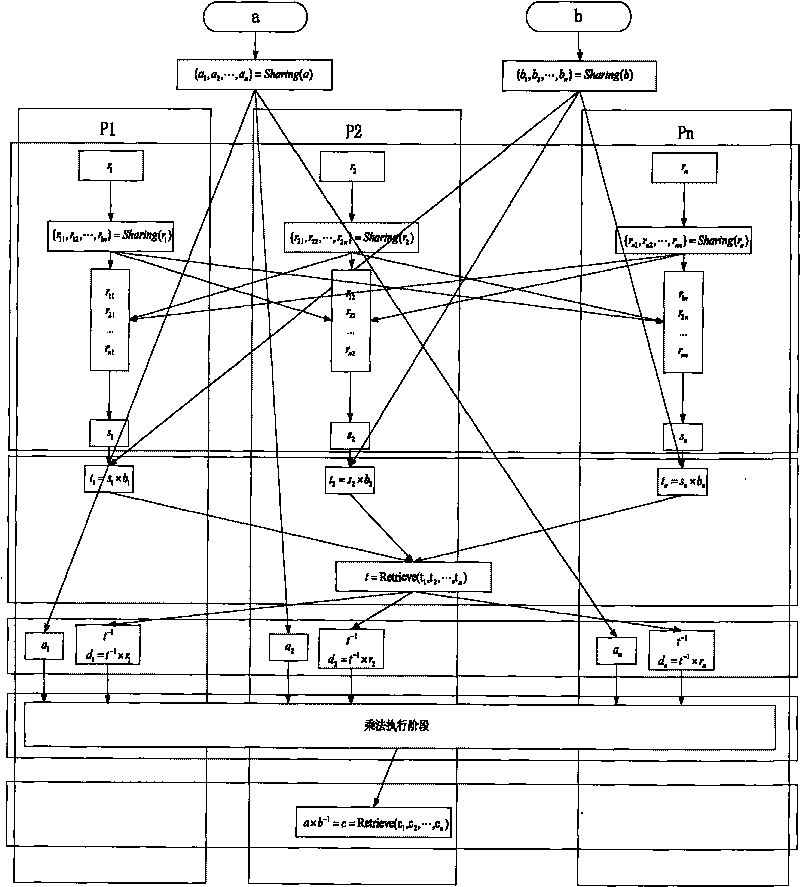
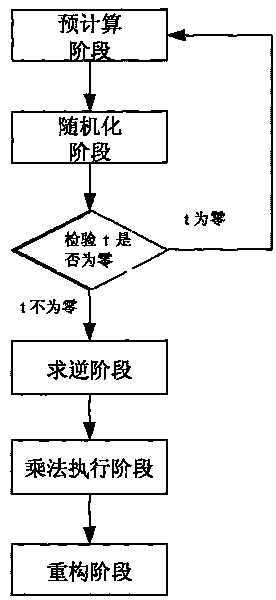
[0044] The division protocol construction method in the present invention will be further described below in conjunction with specific embodiments and schematic diagrams.
[0045] Under the condition of secure multi-party computing, the traditional computing method is based on the Byzantine consensus agreement, and the communication volume between members is relatively large. Our computing is based on linear secret sharing.
[0046] Linear Sharing and Refactoring: In Domain G q , given a secret value s, the sender randomly selects t-1 (t≤n) random numbers (r 1 , r 2 ,...,r t-1 ), forming the equation f s (x)=s+r 1 x+…+r t-1 x t-1 . For any member P in secure multi-party computation i (where i∈[1,n], n is the total number of members), with identity ID i , then the shared value of the secret s obtained by the member is c i = f s (ID i ). If there are m(m≥t) members who want to share {s 1 ,s 2 ,...,s m} to restore the original secret value s, then we can solve ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com