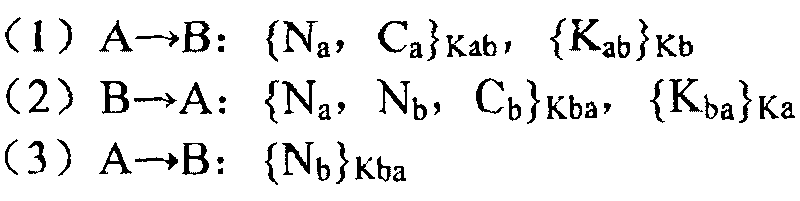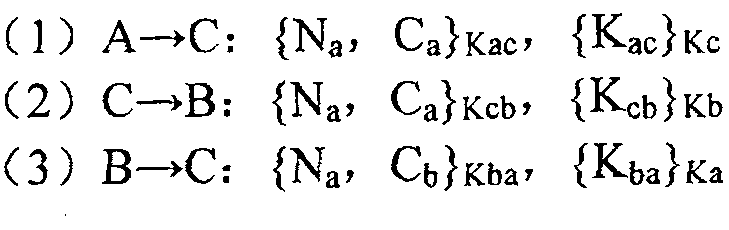Method for ensuring data exchange safety
A data exchange and security technology, applied in secure communication devices, digital transmission systems, user identity/authority verification, etc., can solve the problem of inability to effectively adapt to the security requirements of e-government, failure to implement access control functions between nodes, poor cost and flexibility, etc. problems, to avoid the key agreement process, achieve legitimacy, and ensure the effect of efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
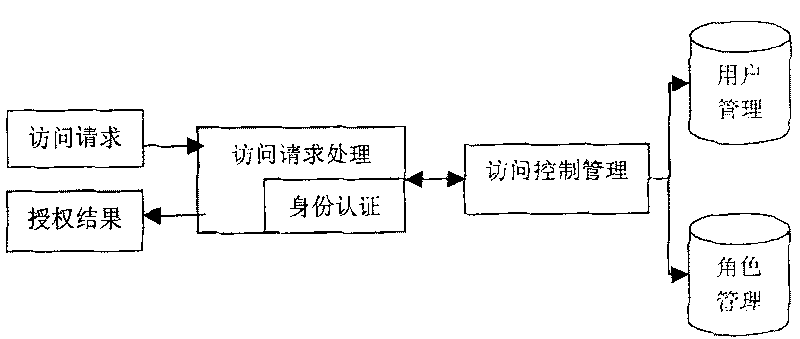
[0045] In order to solve the security problem encountered in the process of data exchange, the present invention proposes a new method for ensuring the security of data exchange. The method includes three parts: connection establishment, access control, and application data transmission; the establishment of connection mainly completes identity authentication and transmission key negotiation between the two parties; access control mainly manages the user's access to the application system; application data transmission mainly completes the reliability of application data transmission to ensure data integrity.
[0046] The following describes how the present invention ensures data exchange security from three aspects of connection establishment, access control and application data transmission.
[0047] 1. Establish a connection:
[0048] During the data exchange process, the exchange parties establish a reliable connection with each other through a three-way handshake. Below...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com