Uniform identity authentication method based on social characteristics in power cloud system
An identity authentication and power cloud technology, applied in the field of mobile communications, can solve problems such as forgotten user accounts or passwords, high requirements for system administrators, and inability to apply identity authentication, etc., to achieve low user participation, improve security, and increase resources. The effect of utilization
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0015] The specific implementation of the present invention will be further explained in detail below in conjunction with the accompanying drawings.
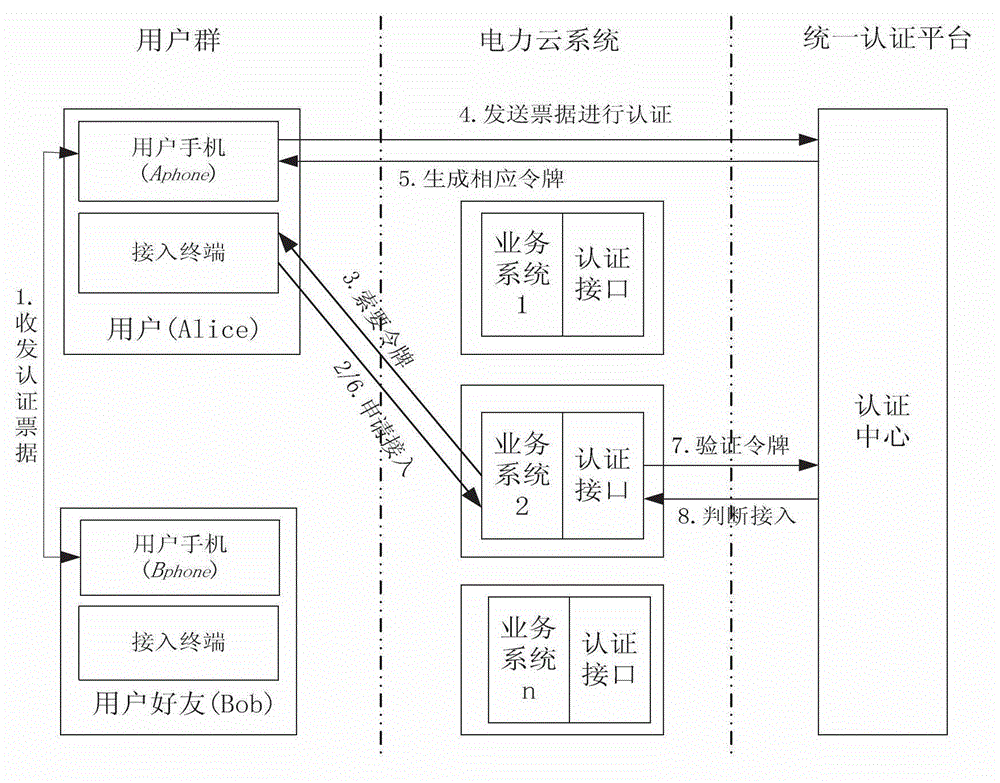
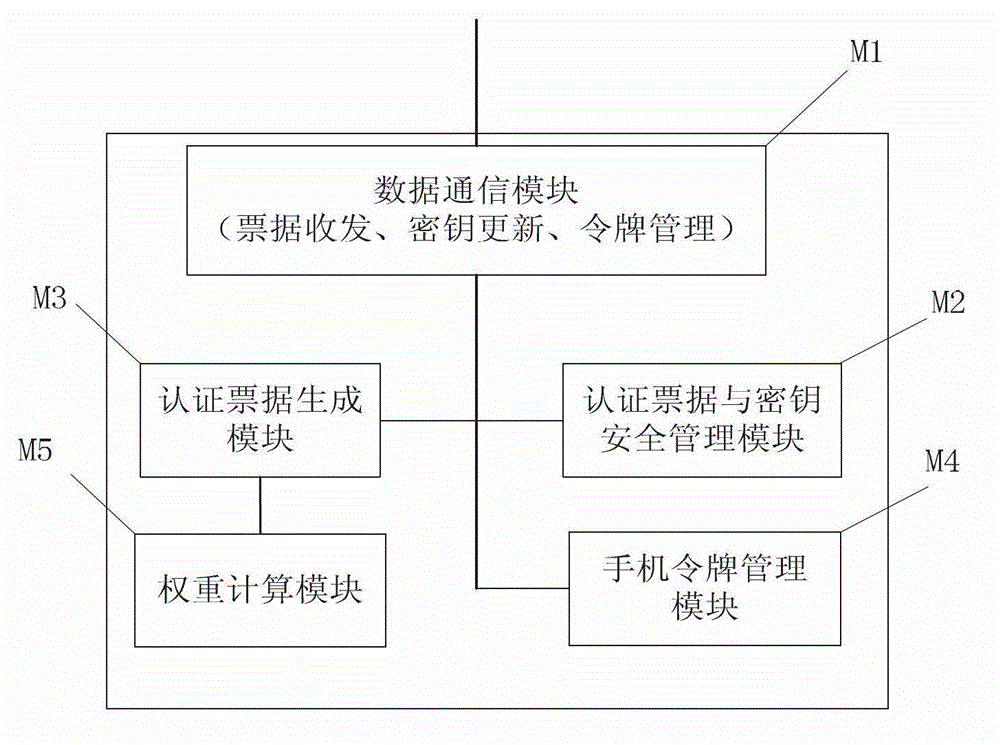
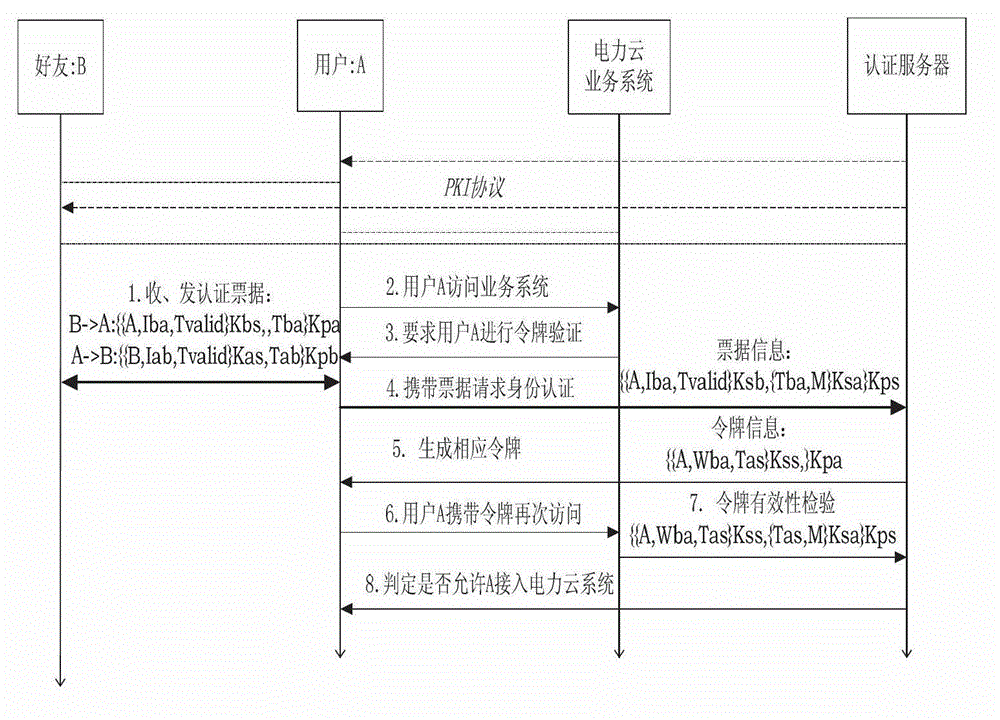
[0016] like figure 1 Shown is the system structure diagram of the present invention. It includes: user Alice and the user's mobile phone friend group, user Alice includes the user's access terminal (such as PC) and user mobile phone A phone , the user friend group such as Bob also includes these two parts; the power cloud system includes different business systems and their corresponding authentication interfaces; the unified authentication platform includes a PKI server and an application server. like figure 2 Shown is a schematic diagram of the principle of the mobile phone (including the user's mobile phone and the friend's mobile phone), including: data communication module (M1), ticket and key security management module (M2), authentication ticket generation module (M3), token management module (M4 ), weight calculation...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com