Patents
Literature
197 results about "Event tracking" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
An overview of Event Tracking. Event tracking is an advanced feature and requires working with our open API and knowledge of programming language. Event Tracking is a flexible feature that allows you to collect data on a wide variety of contact behavior. You can create an event for any activity on your website or app and assign it a value.
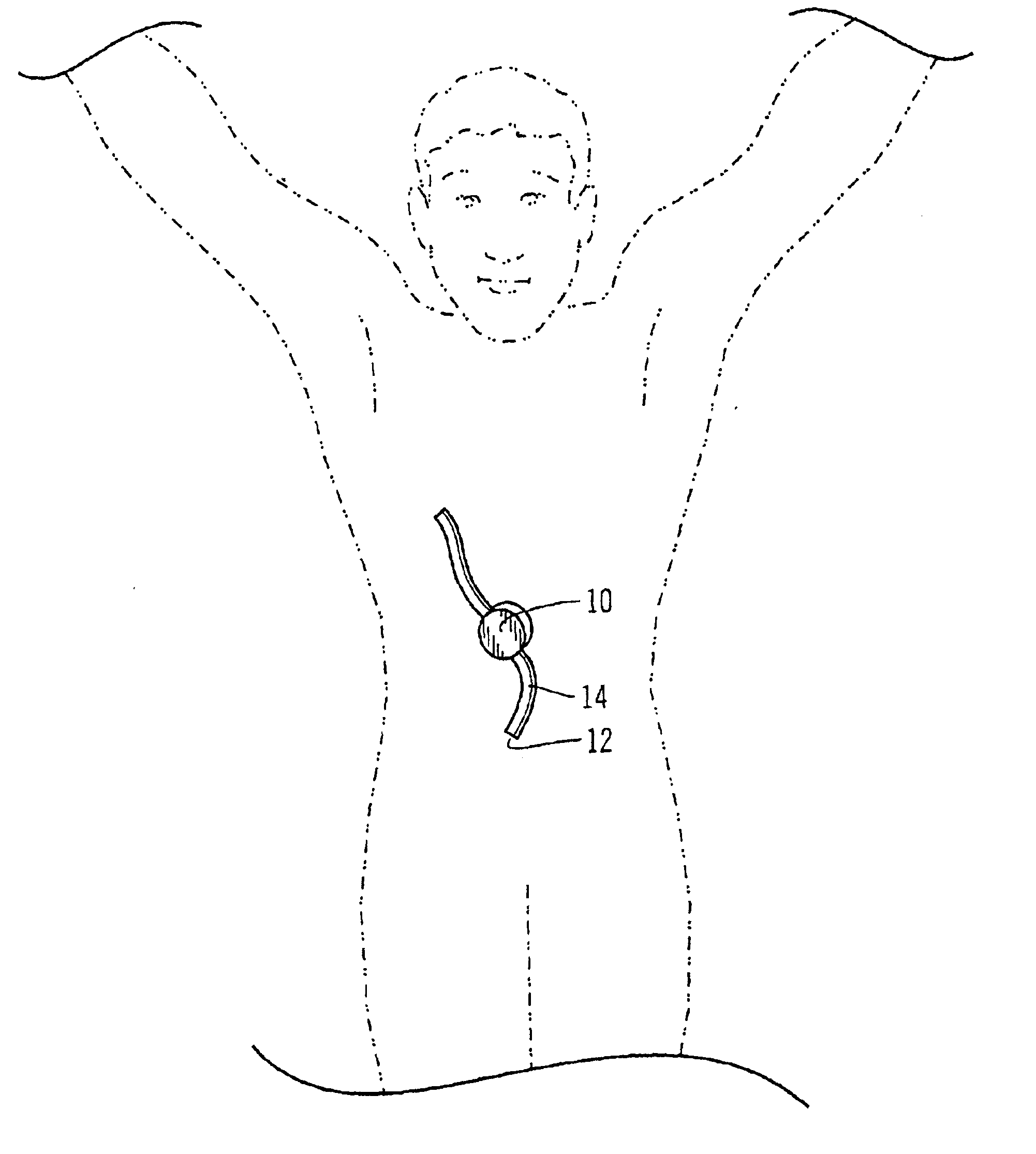
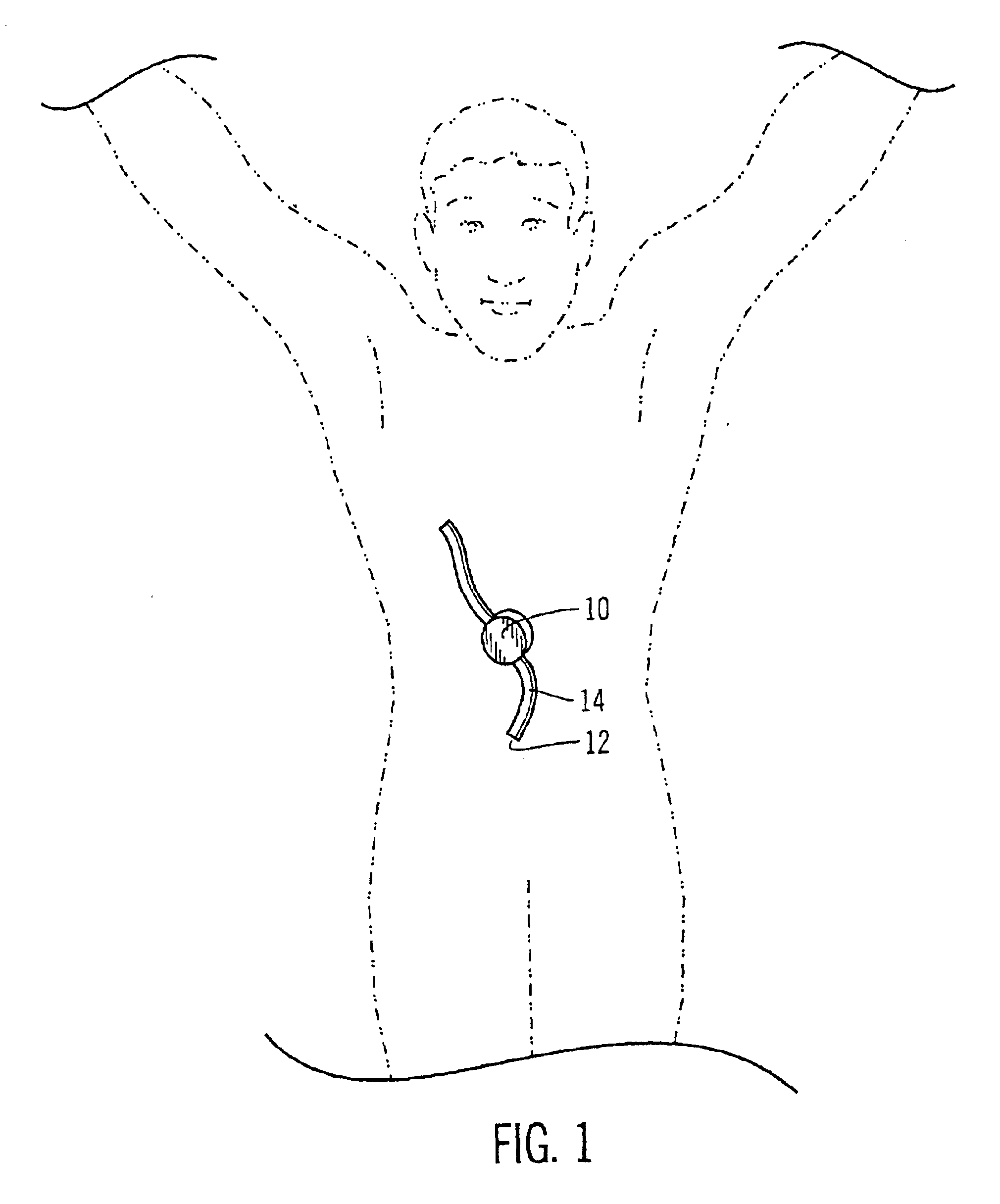
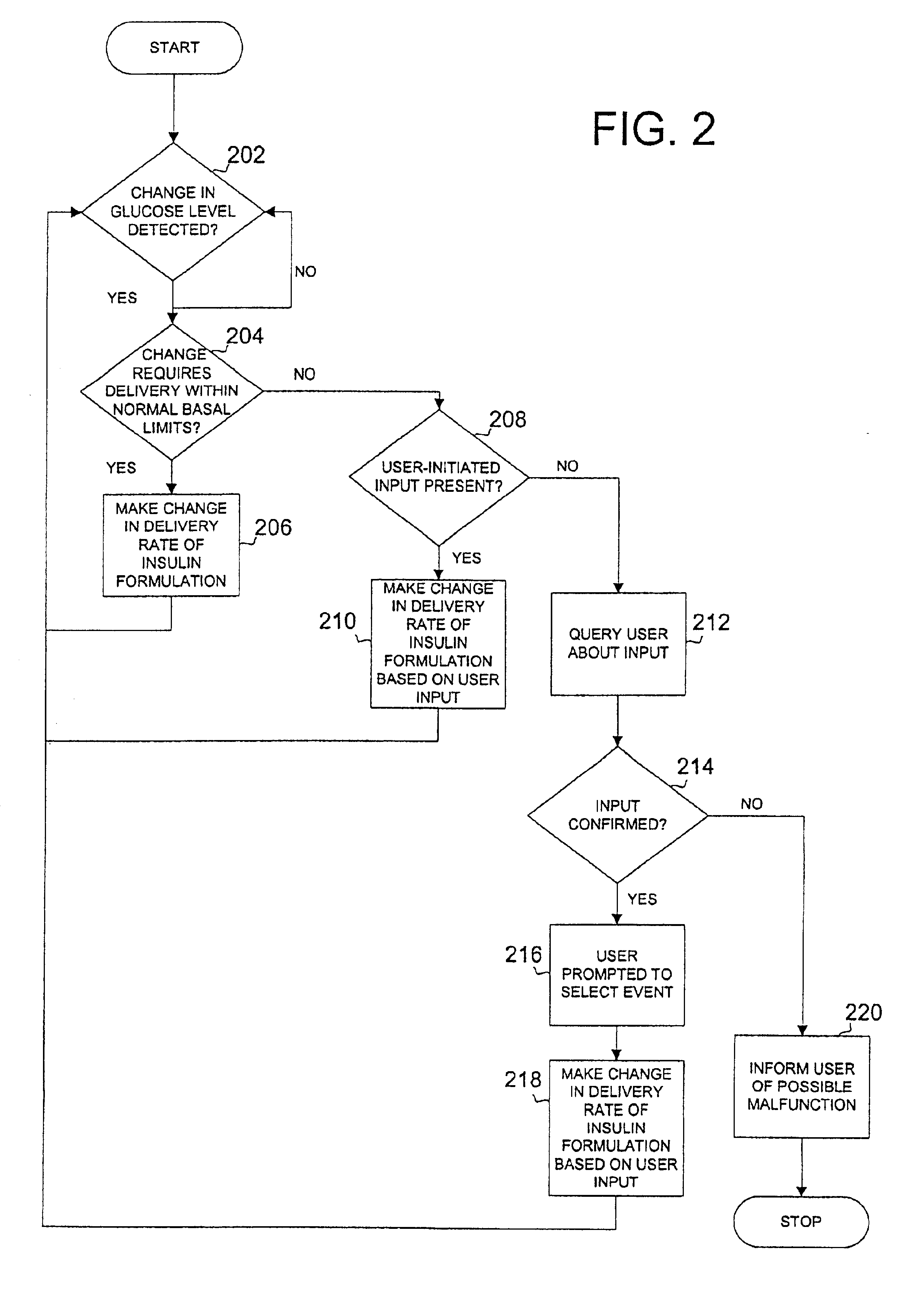
Safety limits for closed-loop infusion pump control
A system and process for providing safety limits on the delivery of an infusion formulation by an infusion pump system in response to a sensed biological state. The safety limits may comprise user-initiated event signals corresponding to events that may significantly affect the biological state. The safety limits may further comprise user-initiated event ranking signals for respective events which specify a degree, quantity, or measure for the respective event. The user-initiated event and event ranking signals may be communicated to a computing element associated with the infusion pump by an associated communication device having a user interface which comprises a plurality of user-selectable operators for entering information about the events and event rankings.
Owner:MEDTRONIC MIMIMED INC
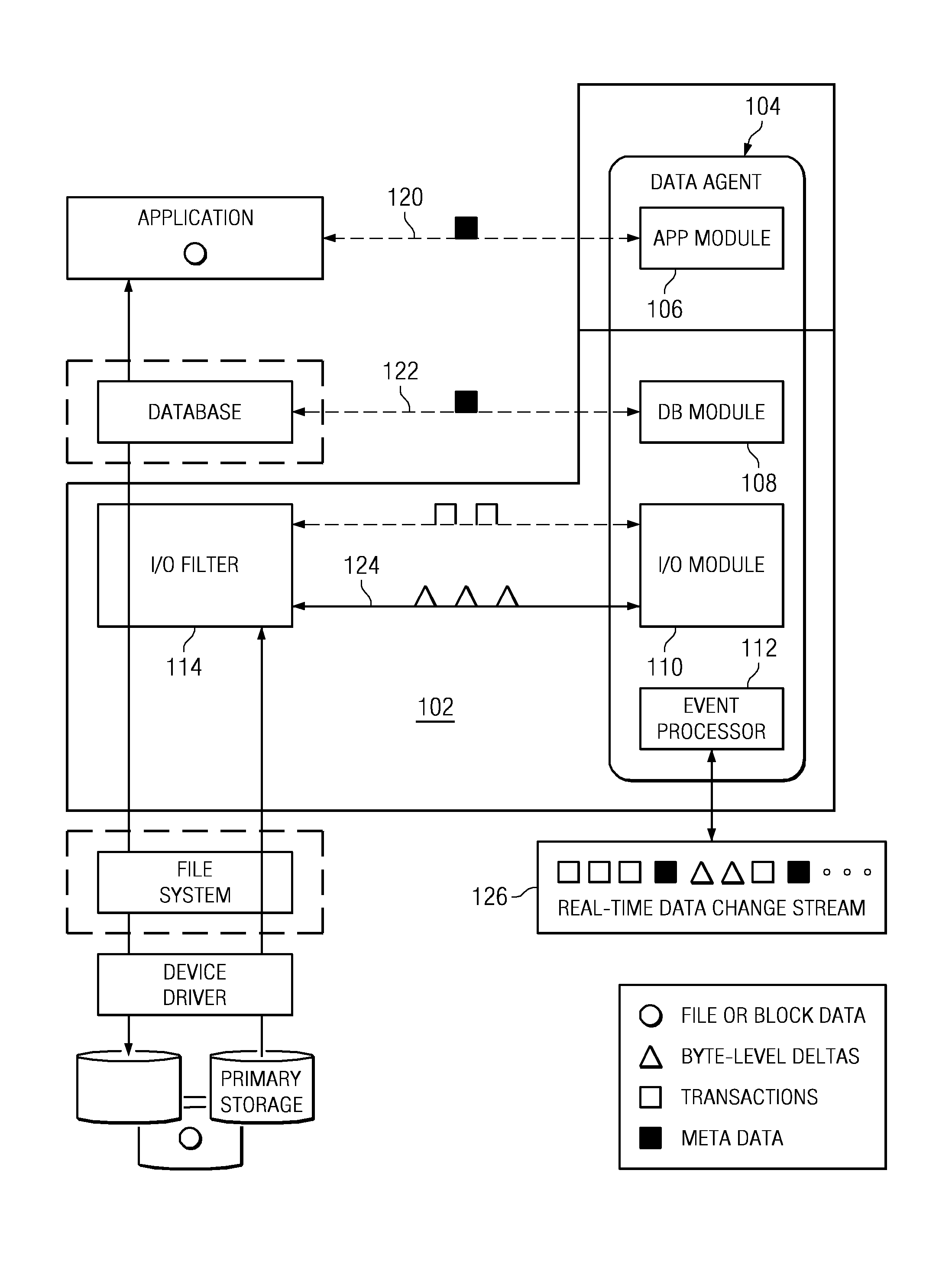
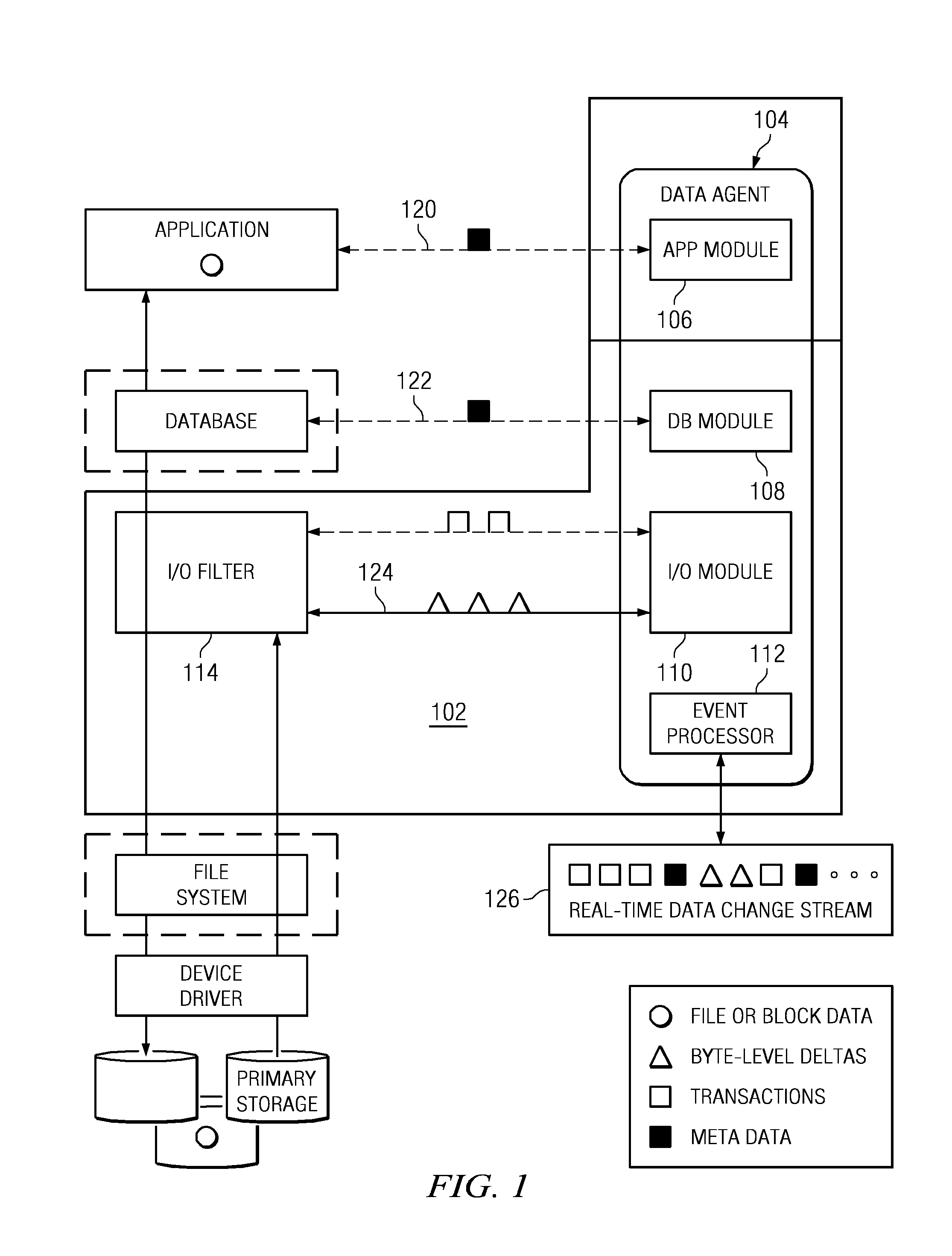
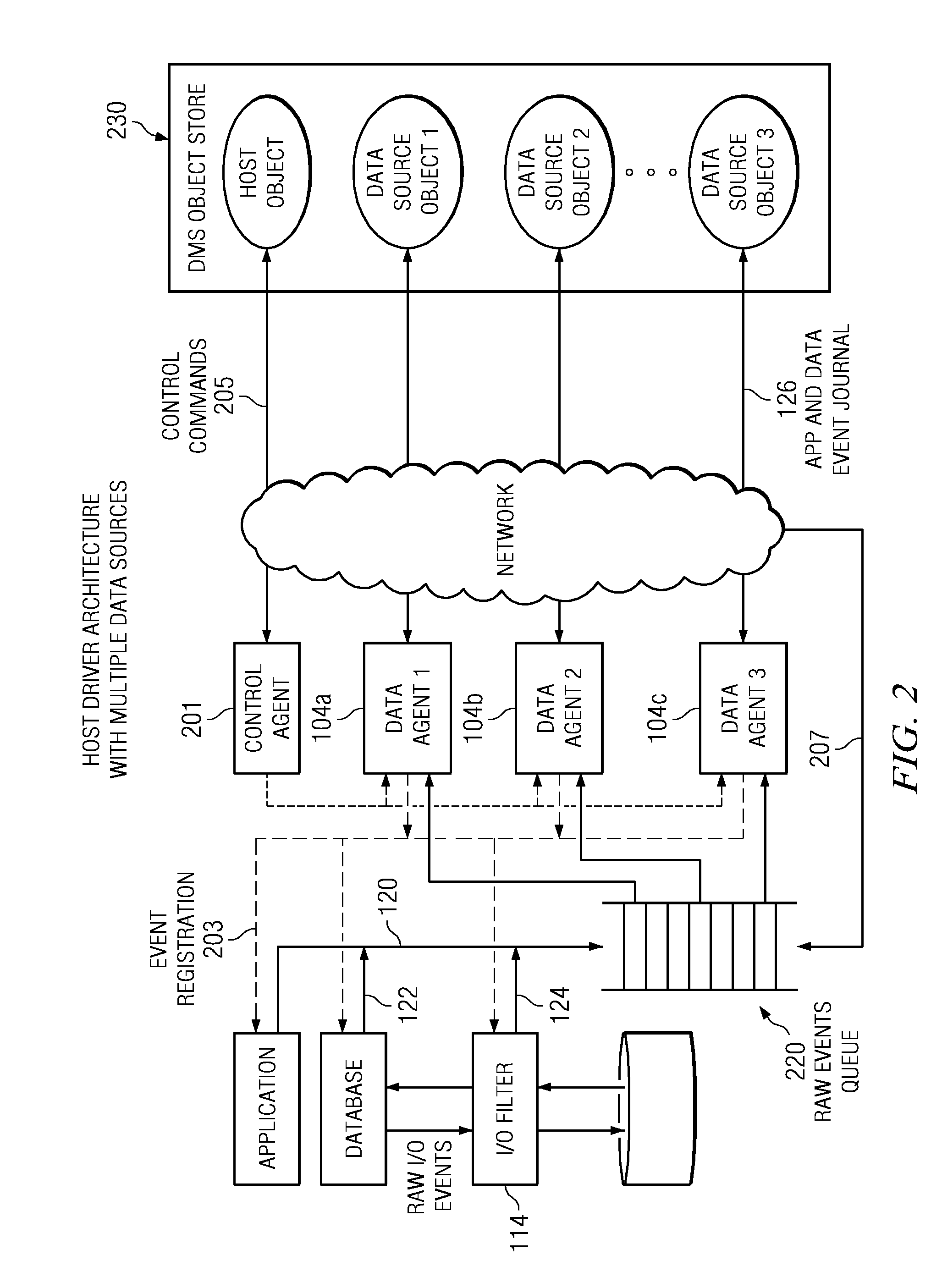
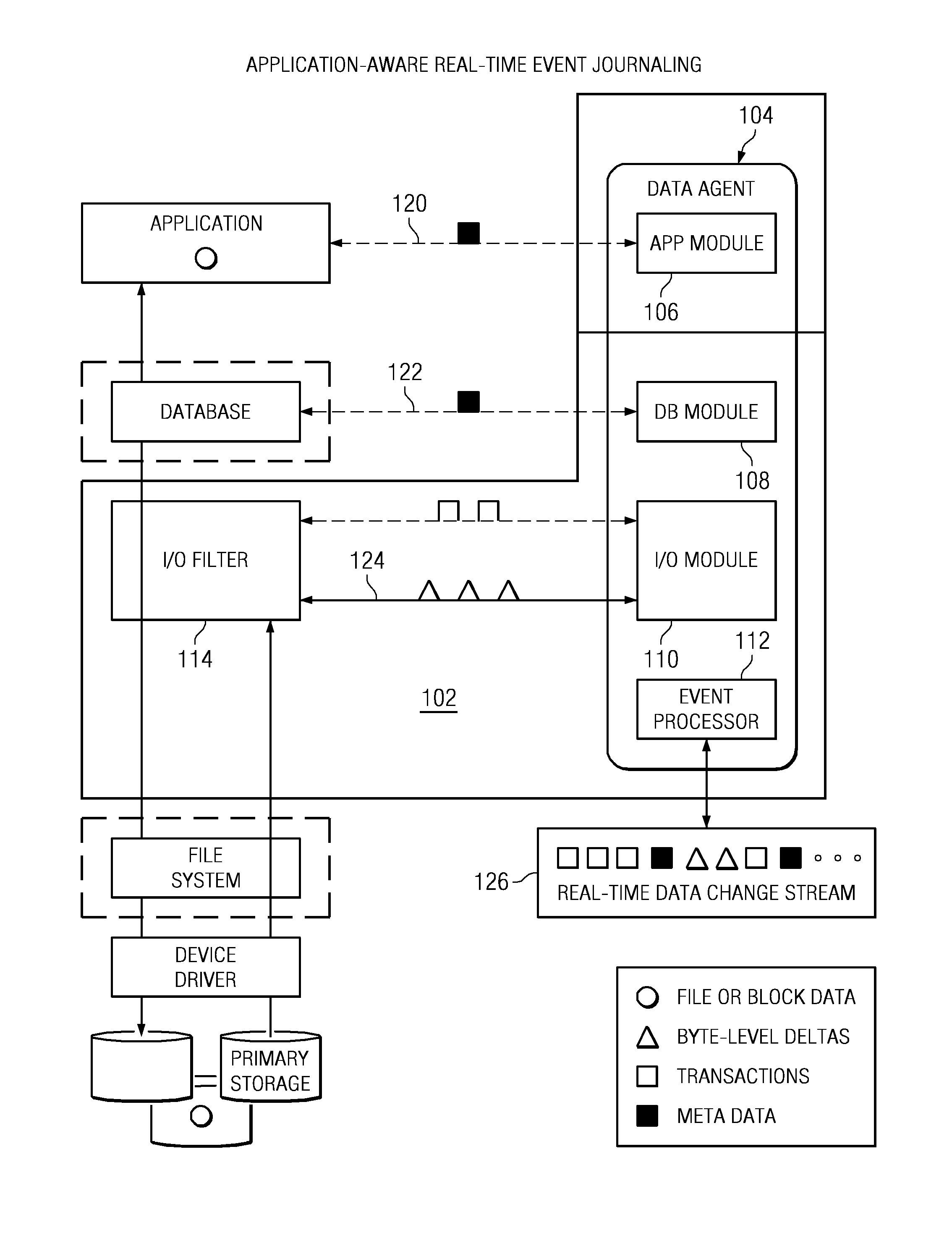
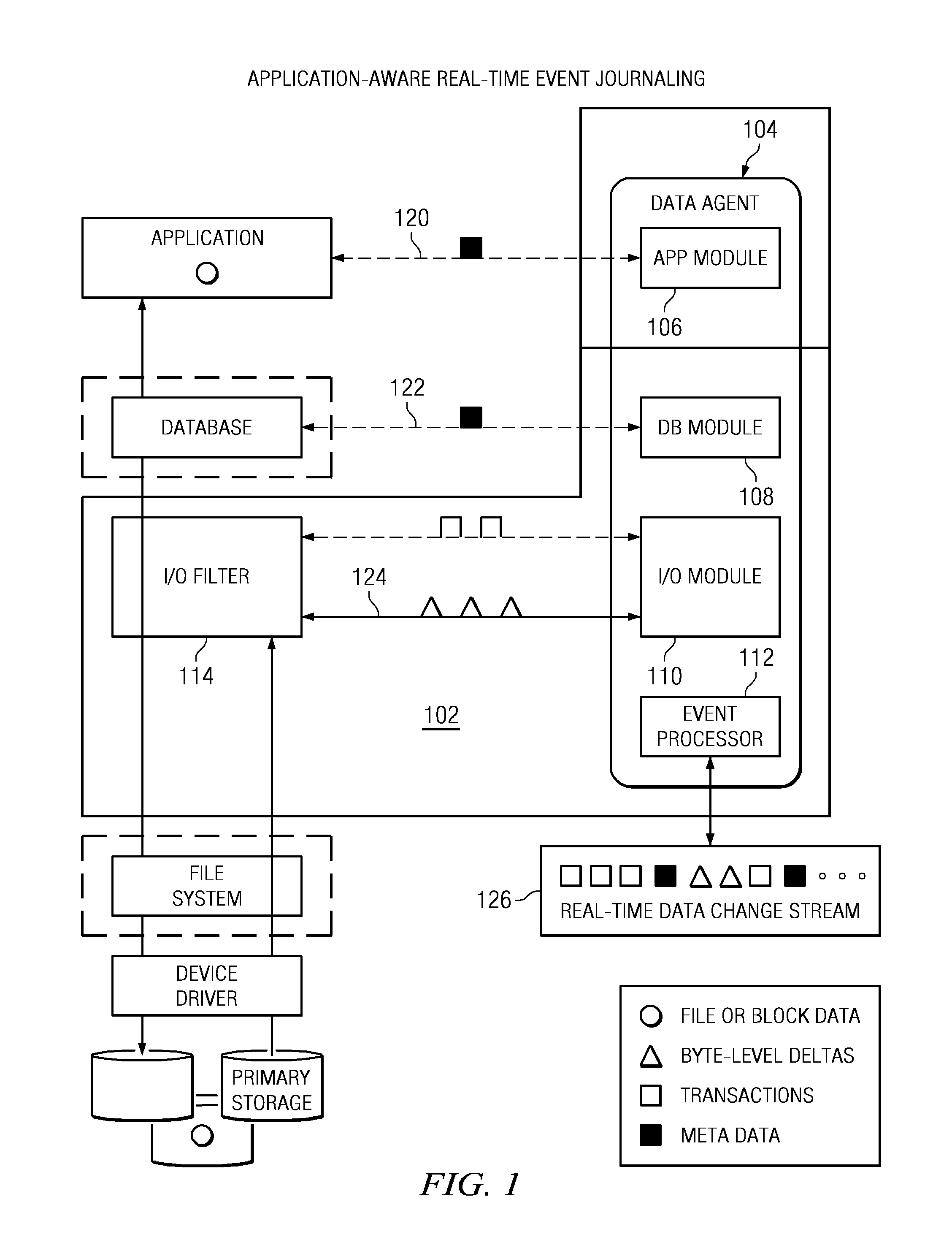
Recovering a database to any point-in-time in the past with guaranteed data consistency
ActiveUS8364648B1Digital data processing detailsStructured data retrievalTransaction dataData management
A data management method wherein a real-time history of a database system is stored as a logical representation and the logical representation is then used for any point-in-time recovery of the database system. More specifically, a method for capturing transaction data, binary data changes, metadata, and events, and for tracking a real-time history of a database system according to the events. The method enables tracking and storing of consistent checkpoint images of the database system, and also enables tracking of transaction activities between checkpoints. The database system may be recovered to any consistent checkpoint or to any point between two checkpoints.
Owner:QUEST SOFTWARE INC
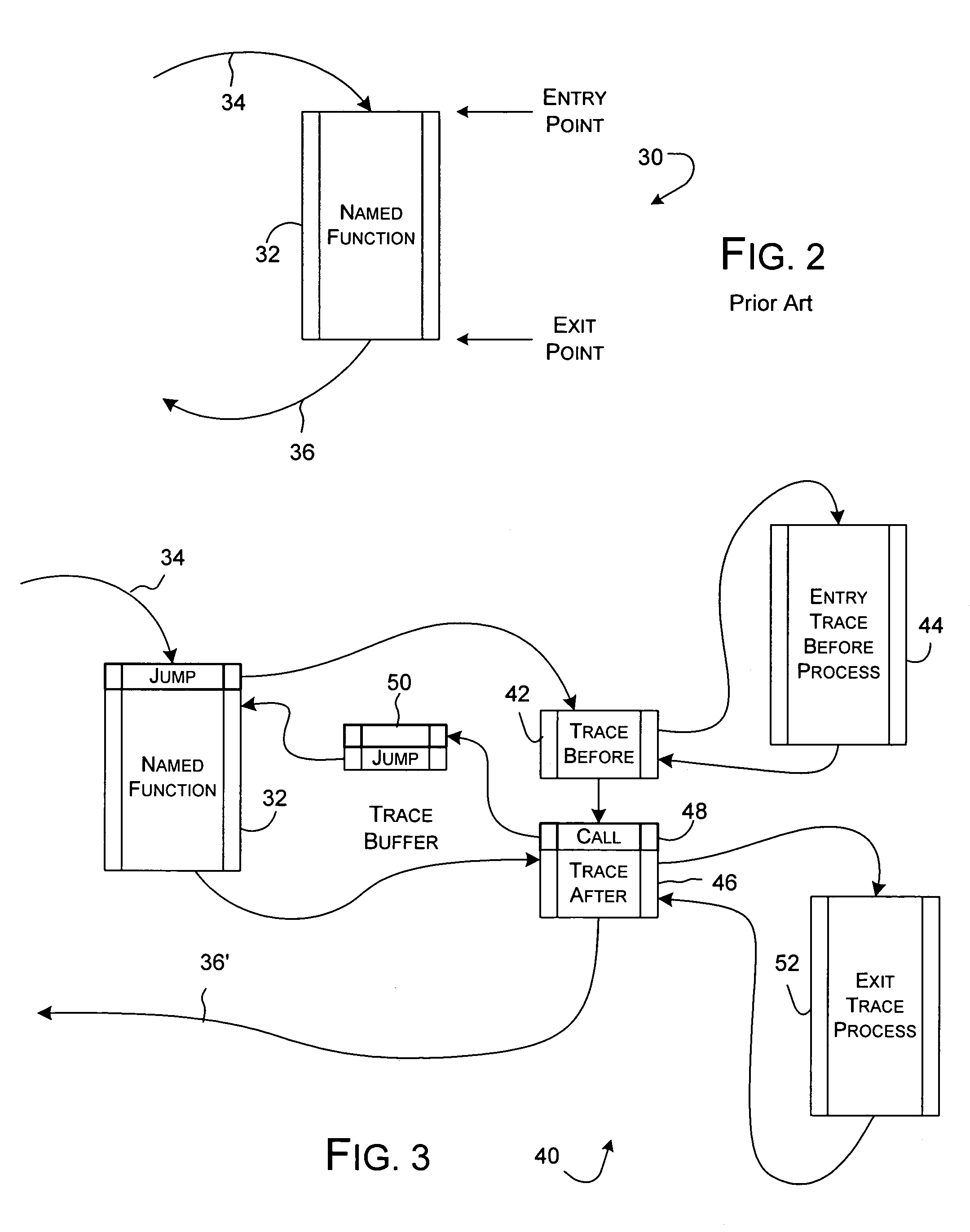
Dynamic instrumentation event trace system and methods
InactiveUS7047521B2Performance impact is minimalMaximize discriminating detectionHardware monitoringSoftware testing/debuggingDynamic instrumentationParallel computing
Program code loaded for execution by a computer can be dynamically instrumented to collect event data by inserting an instruction at a trace point within the program code as loaded in a memory space of a computer, where the trace point corresponds to the beginning of a predefined function of the program selected for event tracing. The instruction provides for the direction of the execution of said computer to a function proxy routine, which includes a call to an instance of the predefined function. Event data is collected in connection with the calling of the instance of the predefined function.
Owner:LYNX SOFTWARE TECH
Event trace conditional logging
ActiveUS20070255979A1Reduce in quantityImprove relevanceError detection/correctionEvent trackingOperating system
Owner:MICROSOFT TECH LICENSING LLC
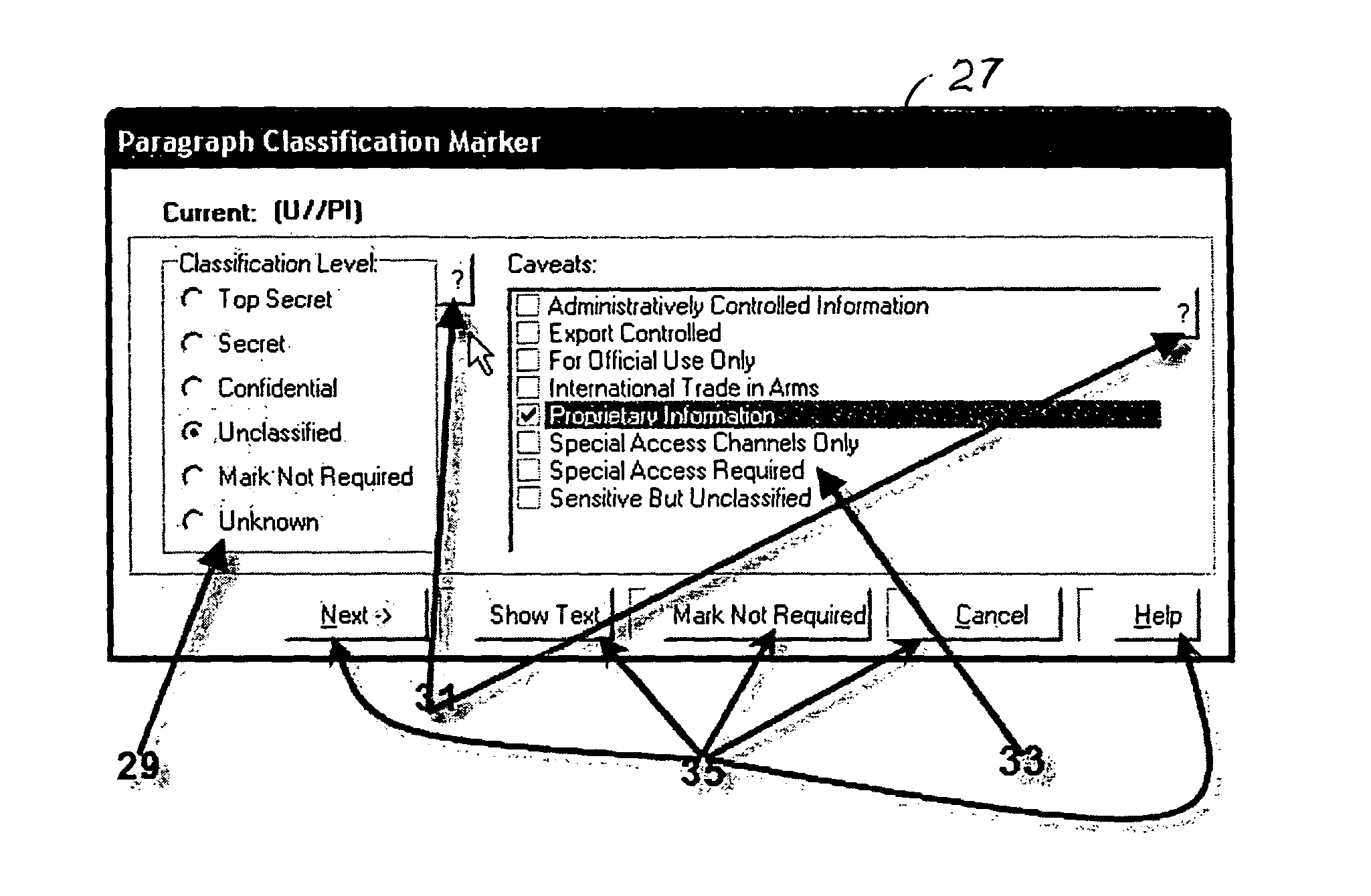
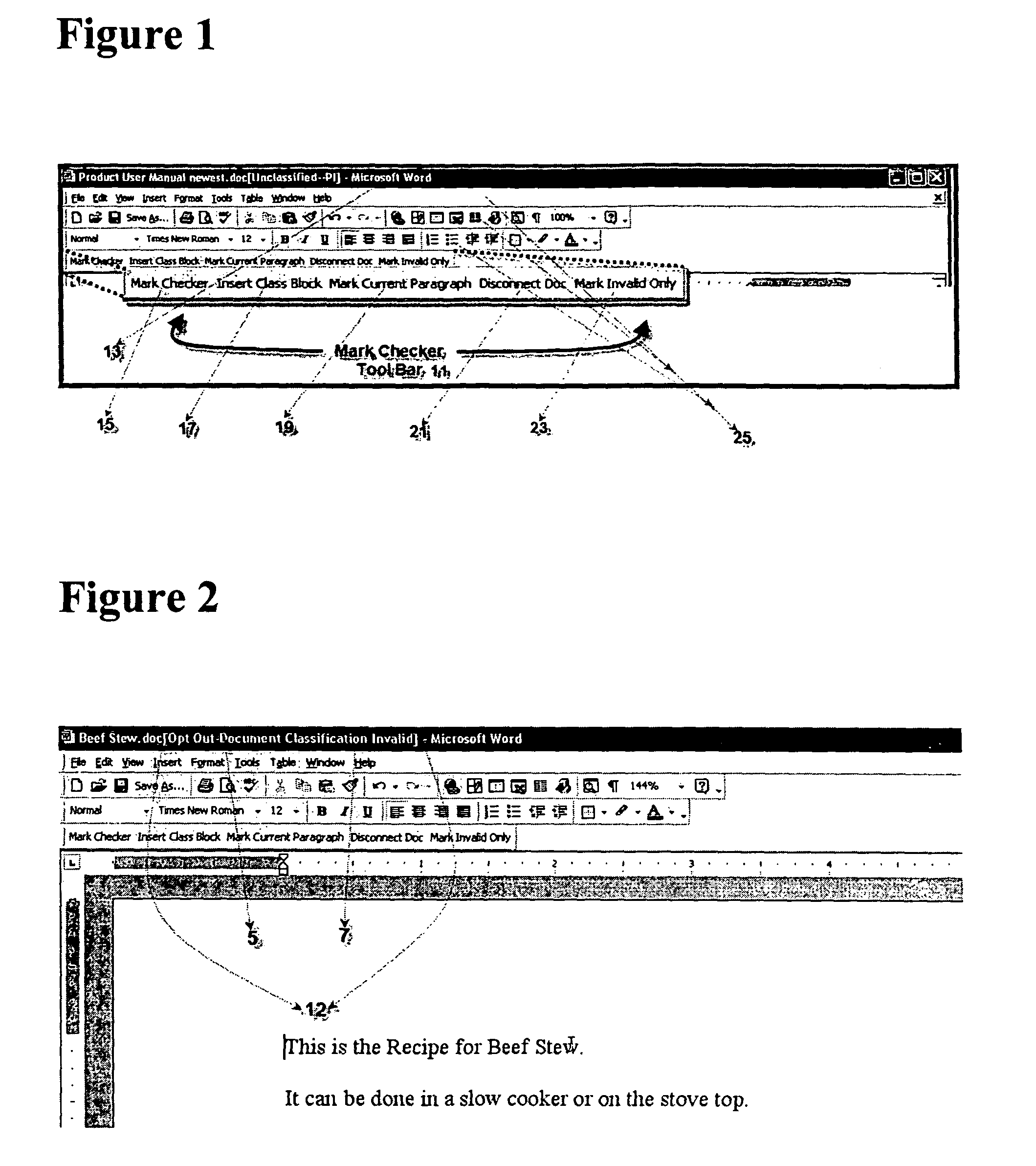
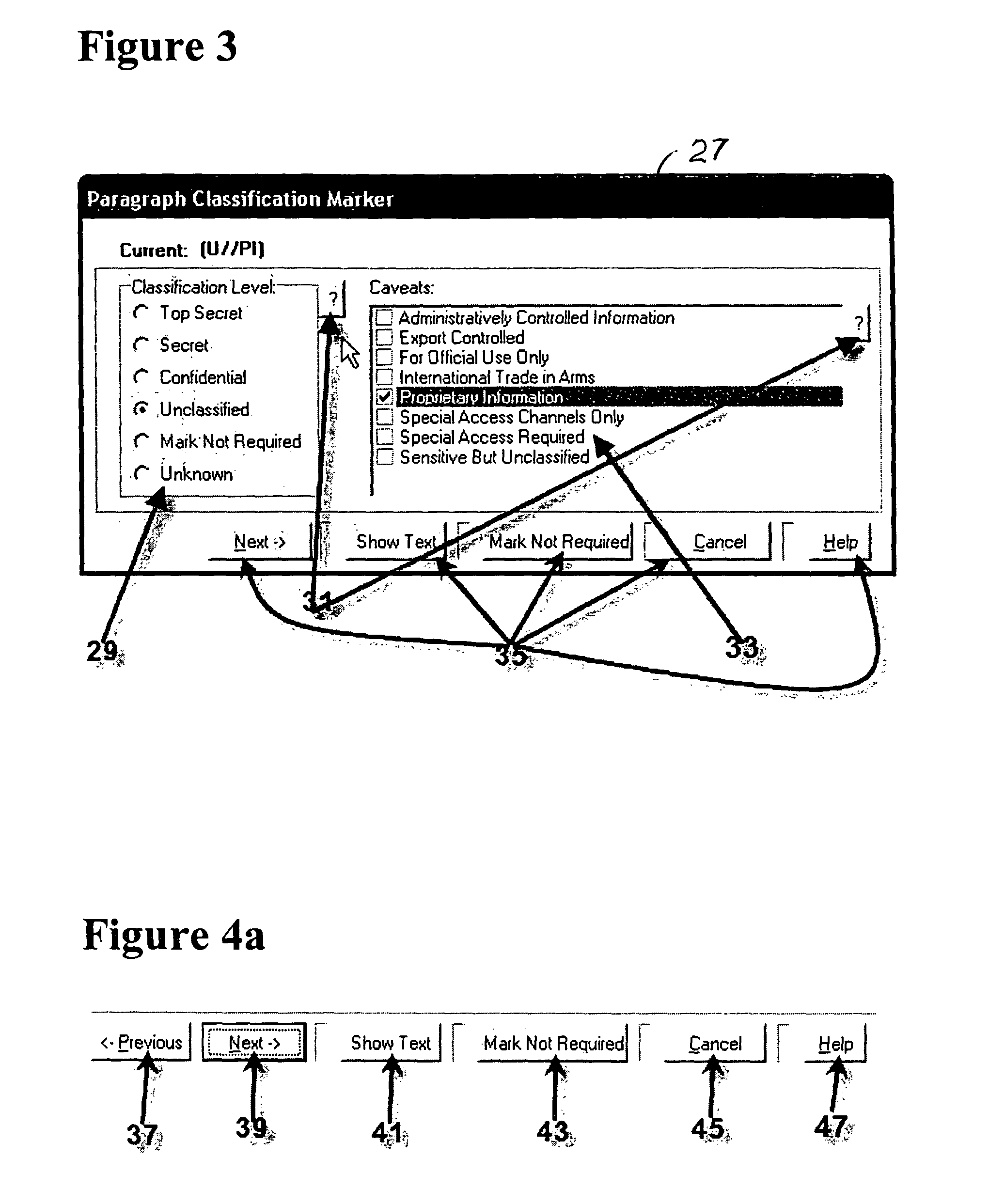
Method for providing customized and automated security assistance, a document marking regime, and central tracking and control for sensitive or classified documents in electronic format
ActiveUS7958147B1Guarantee capacityPositive determinationDigital data information retrievalDigital data processing detailsOff the shelfDocumentation procedure
A software engine runs in a compatible mode with off-the-shelf word processors, e-mail programs and presentation development software and other document development software. The software engine is used for the security classification of sensitive or national security classified information in electronic and resultant hard copy document formats. The software engine ensures that the individual considers all informational portions of a document, that appropriate document marks are employed, that document marks in their electronic format are persistent and that all necessary information, such as classification guides, standards and security regulations, provided by the organization to classify information is at hand and immediately available. In addition to the document sensitivity or classification determination and marking support, the software engine tracks and controls documents and the electronic media storing documents. It also provides warnings and alarms, ad hoc document security analysis and reporting capability to system security administrators with respect to document or network events or captured information that may be indicative of risk to the information requiring protection. The software also provides the ability for an organization to centrally establish and control a security classification or sensitivity marking hierarchy for automated security classification support.
Owner:TURNER JAMES LUKE +1
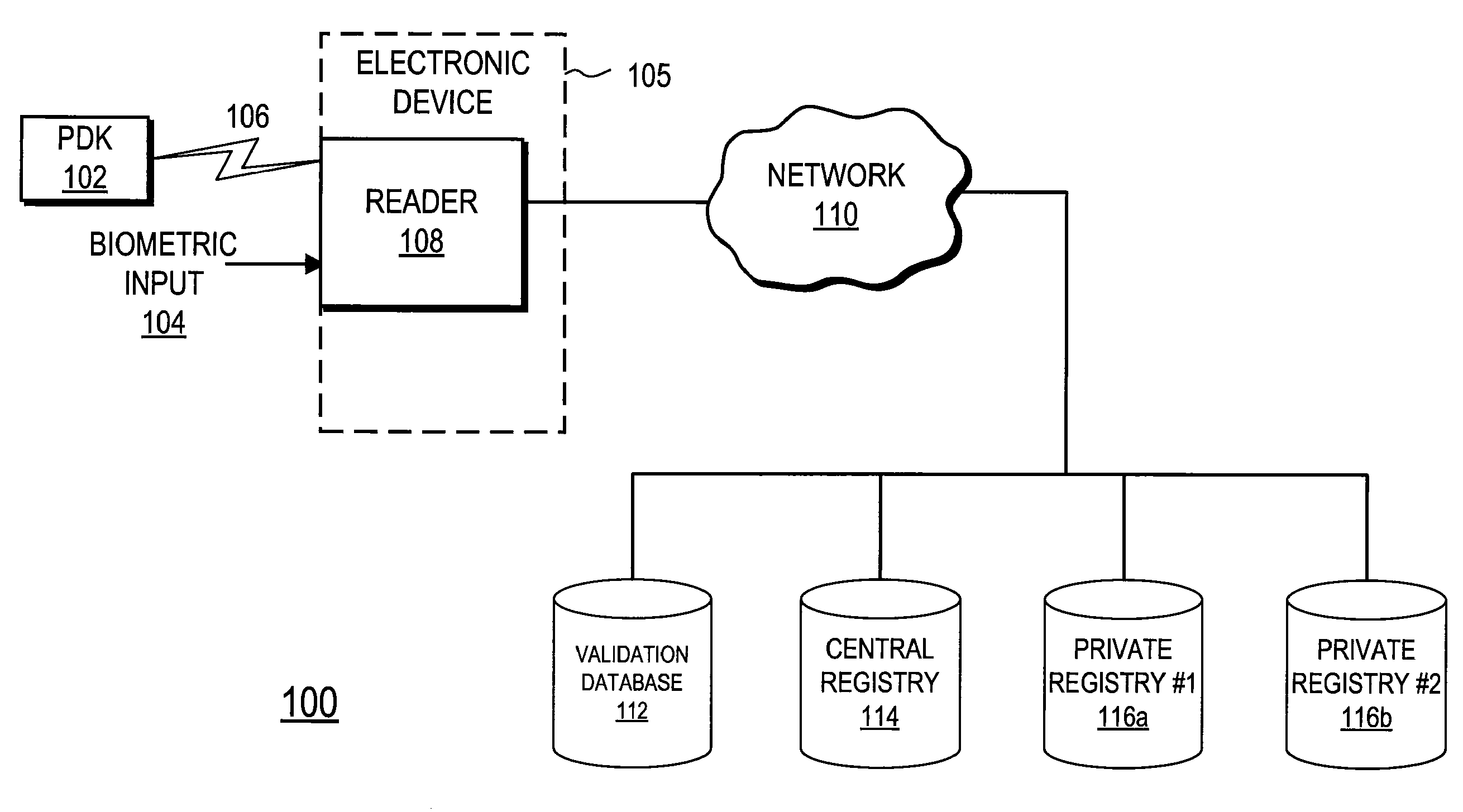
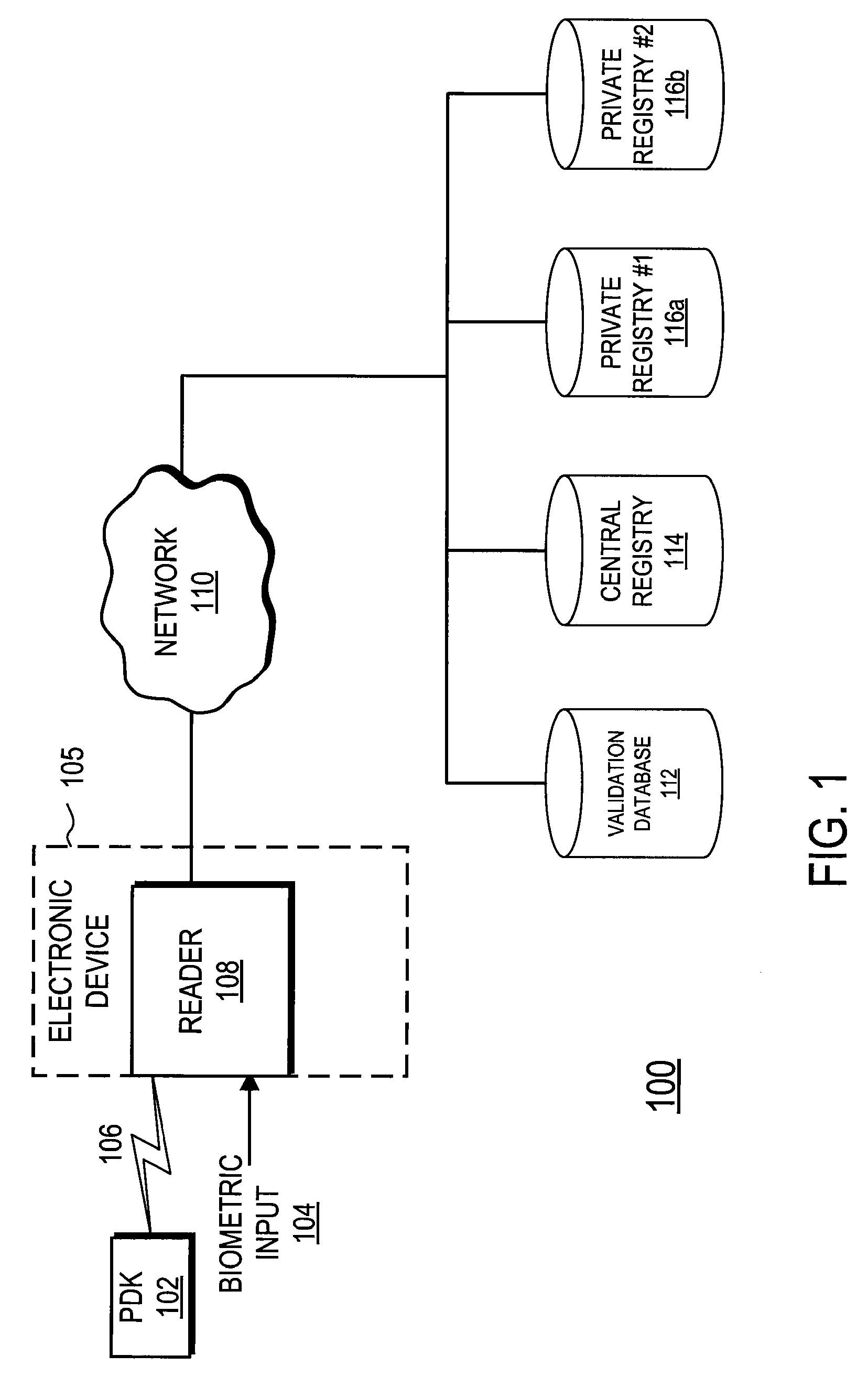
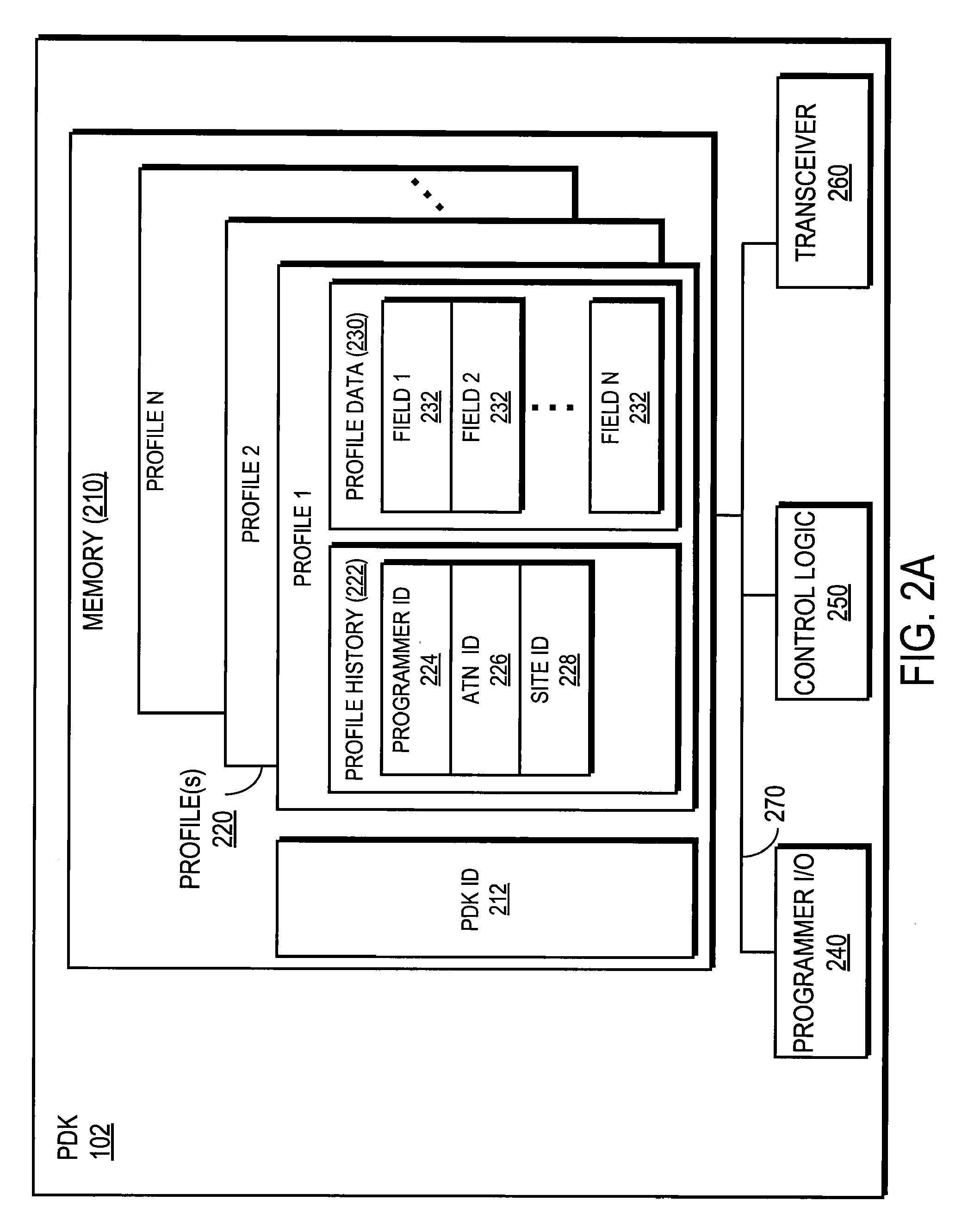
Tracking System Using Personal Digital Key Groups
ActiveUS20080149705A1Efficient and highly reliable customer trackingReliable trackingDiscounts/incentivesDigital data processing detailsSpecific functionEvent tracking
A system and method provides efficient and highly reliable customer tracking. A Personal Digital Key (PDK) is associated with and carried by a user. The PDK wirelessly communicates with a receiver / decoder circuit (RDC) that can be coupled to a variety of electronic devices. The RDC authenticates the PDK based on received data and stores information to track customers and provide improved service. A PDK can be assigned to one more groups of PDKs based on the received data. Specific functions can then be executed based on the group assignments. In a casino environment, the system enables functions such as group gaming, back betting, event tracking, and notification services.
Owner:PROXENSE
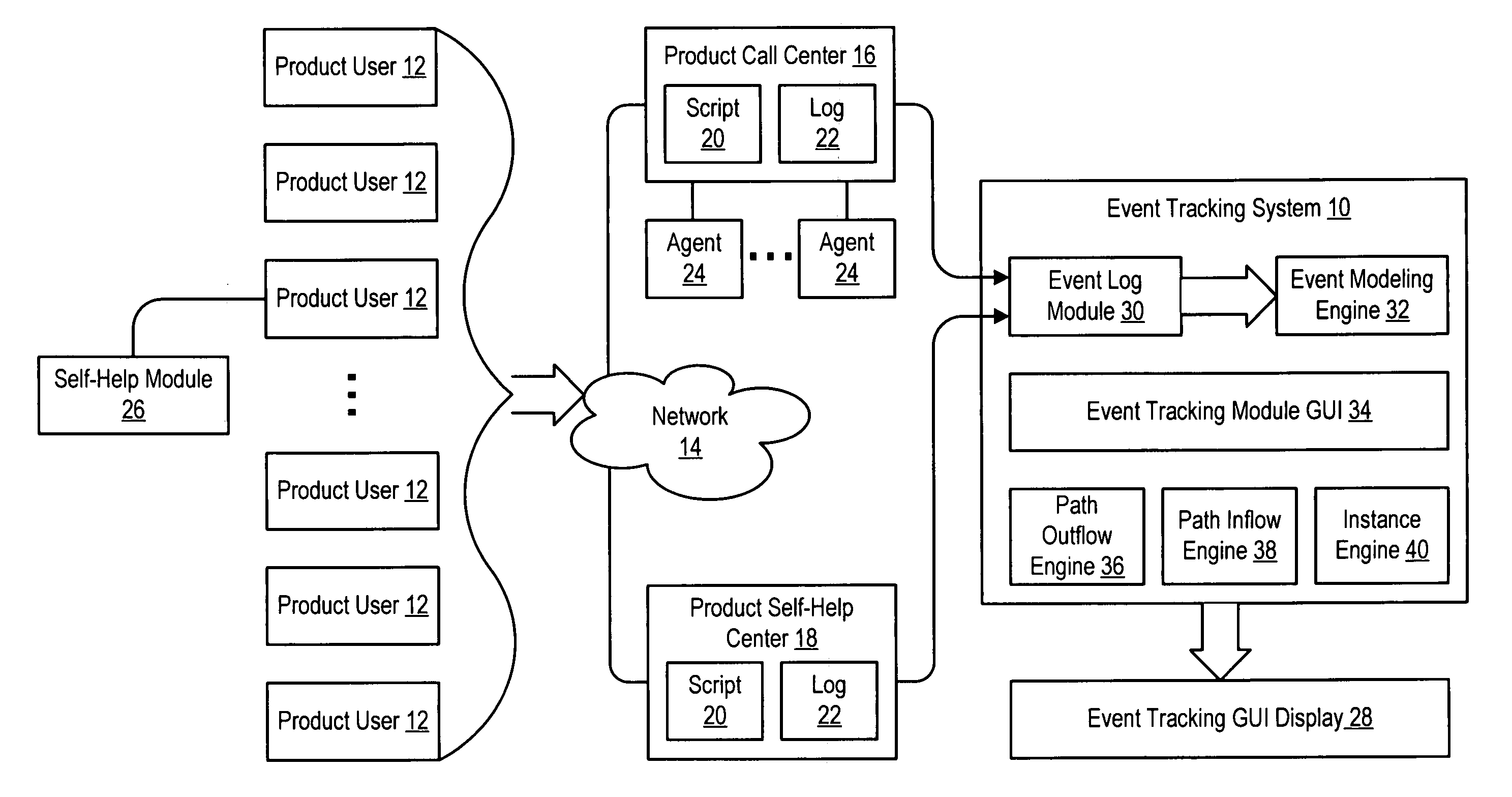
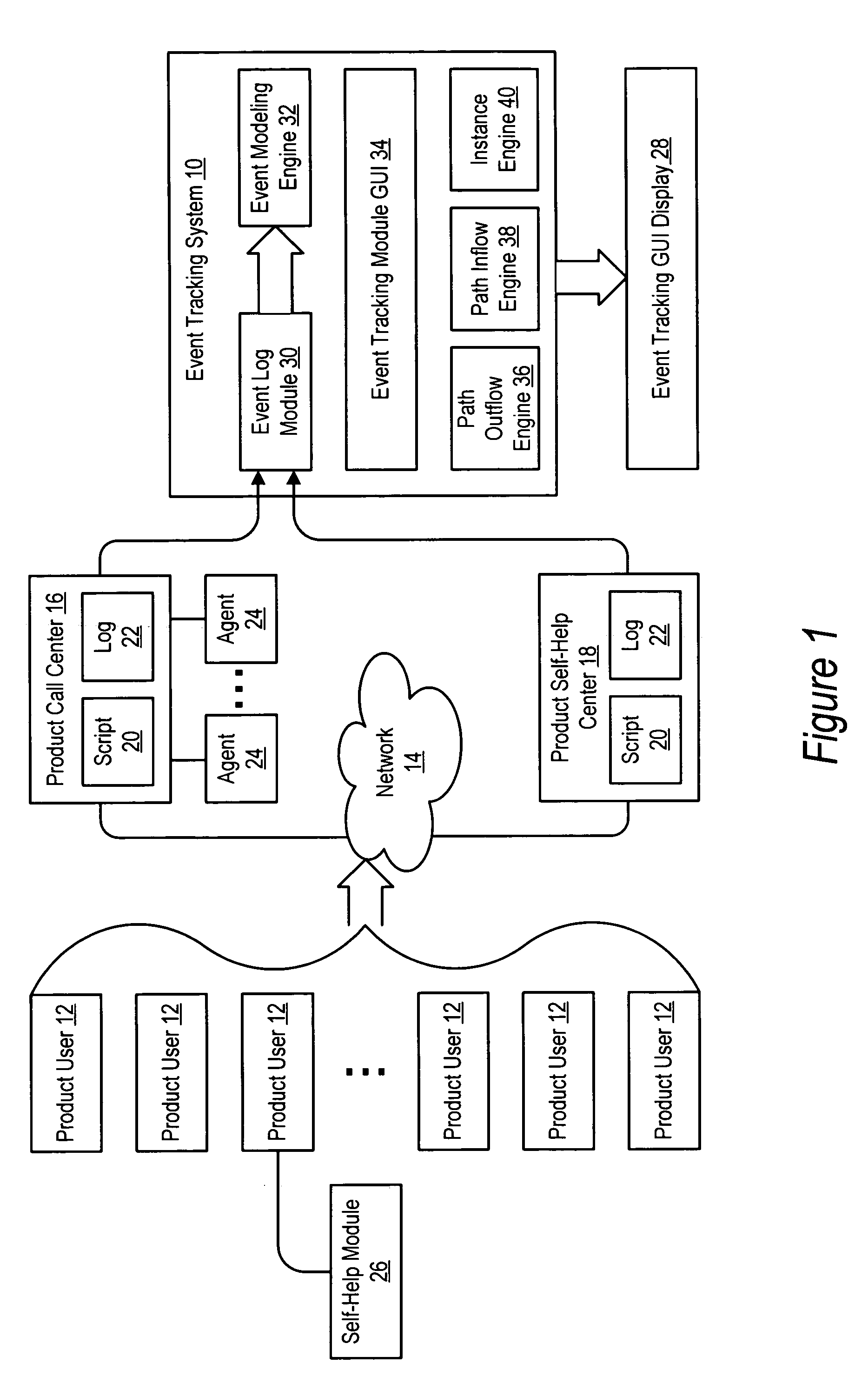
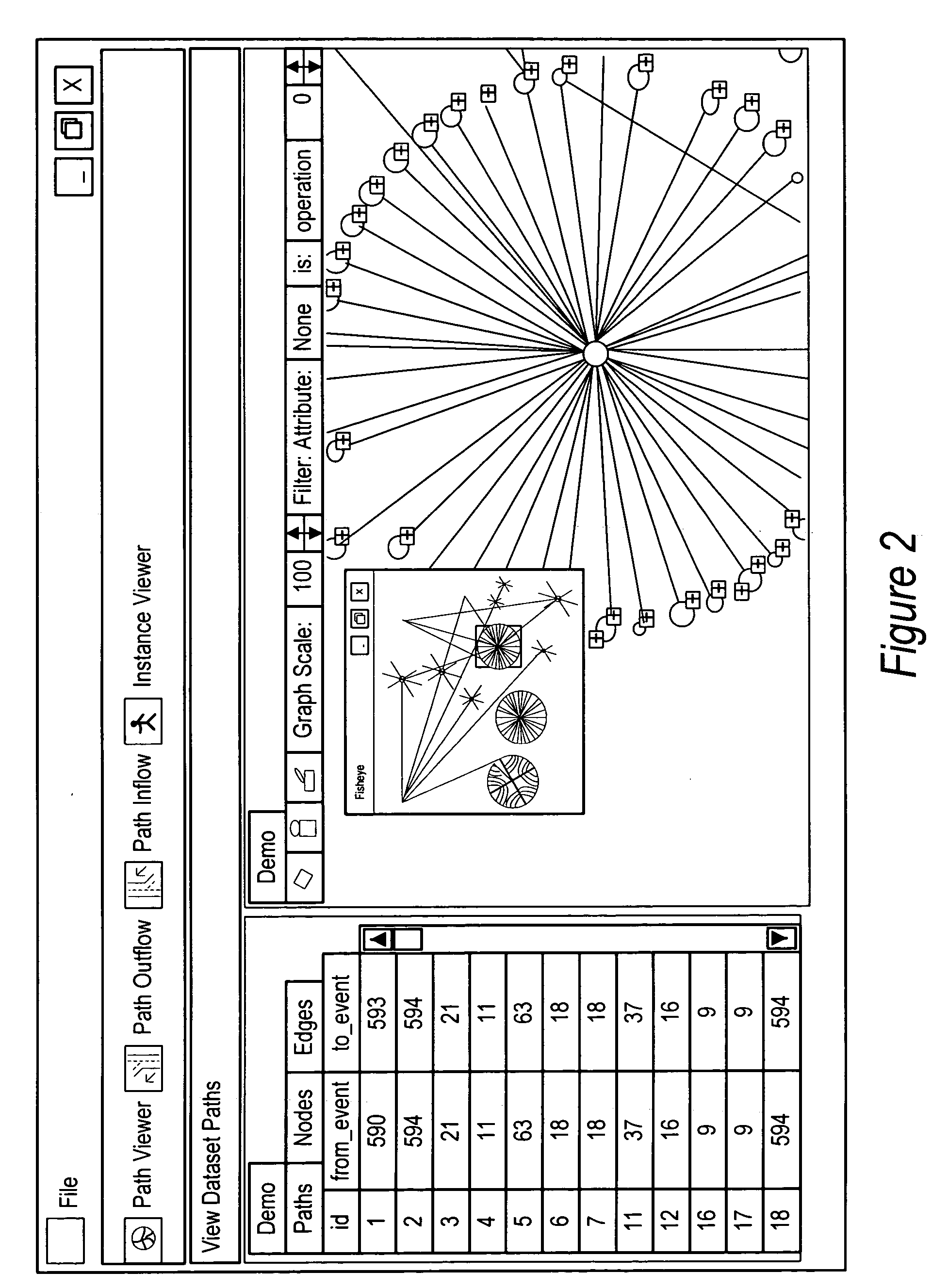
System and method for event tracking across plural contact mediums
InactiveUS20050125276A1Improve customer interactionReduce disadvantagesMarketingSpecial data processing applicationsGraphicsDirected graph
An event tracking system tracks customer interactions to obtain product information that are made across plural contact mediums and displays an intuitive directed graph for analysis of the customer interactions. Each customer interaction is logged at each contact medium with a labeled reference associated with the content of the interaction, a time stamp and an identifier for the product or product user. An event modeling engine analyzes the log to identify contact sessions as contacts by the same identifier within a predetermined time so that an event tracking graphical user interface module prepares each contact session for display as a path of nodes interconnected by edges. Selected directed graph characteristics are highlighted, such as transitions from one contact medium to another or contact session volumes associated with an edge that have a relative volume compared with other contact sessions.
Owner:DELL PROD LP
Event Tracking and Velocity Fraud Rules for Financial Transactions
InactiveUS20110016052A1Reducing third-party processing feeReduce processing timeFinanceProtocol authorisationThird partyFiltering rules
A fraud rule can be applied to a transaction according to a first authorization parameter. The transaction is passed to a filtering rule which is applied to the transaction according to a second authorization parameter. The filtering rule can approve the transaction for processing or pass the transaction on to a third party analysis. The fraud and filtering rules can apply the same analysis to the transaction with the exception of the authorization parameters. The fraud rule and filtering rules can analyze historical attributes of a consumer account.
Owner:VISA INT SERVICE ASSOC
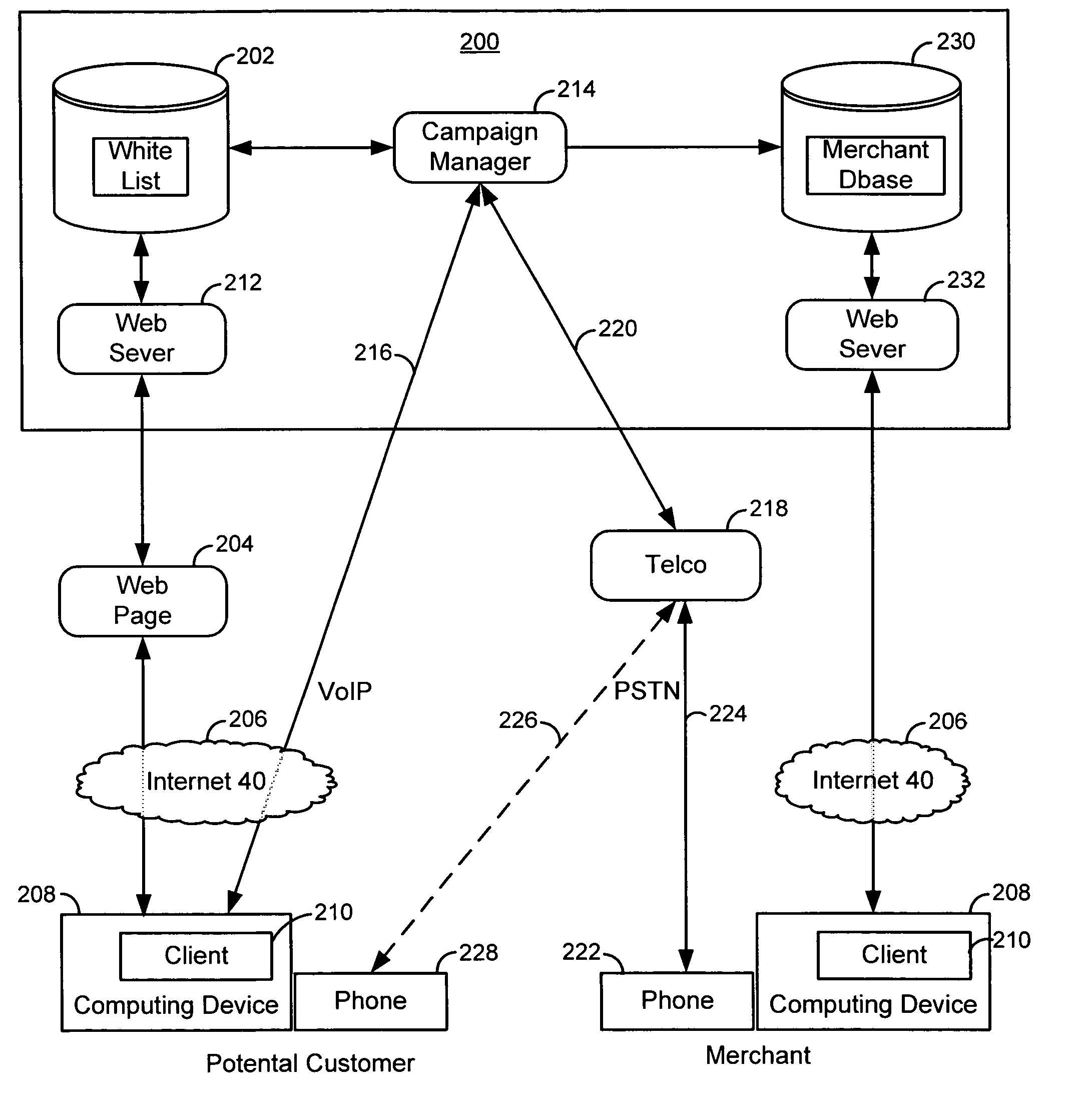
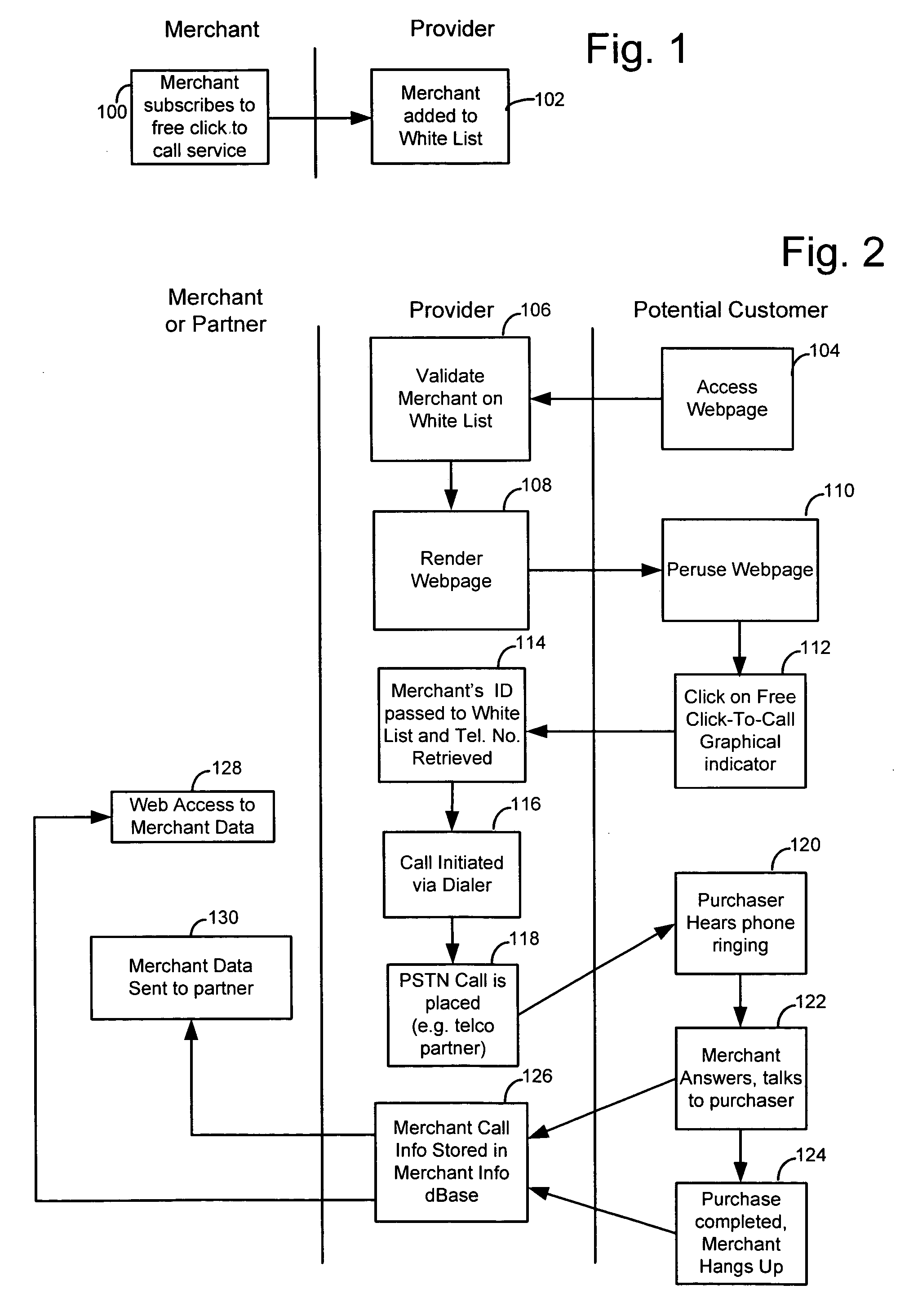
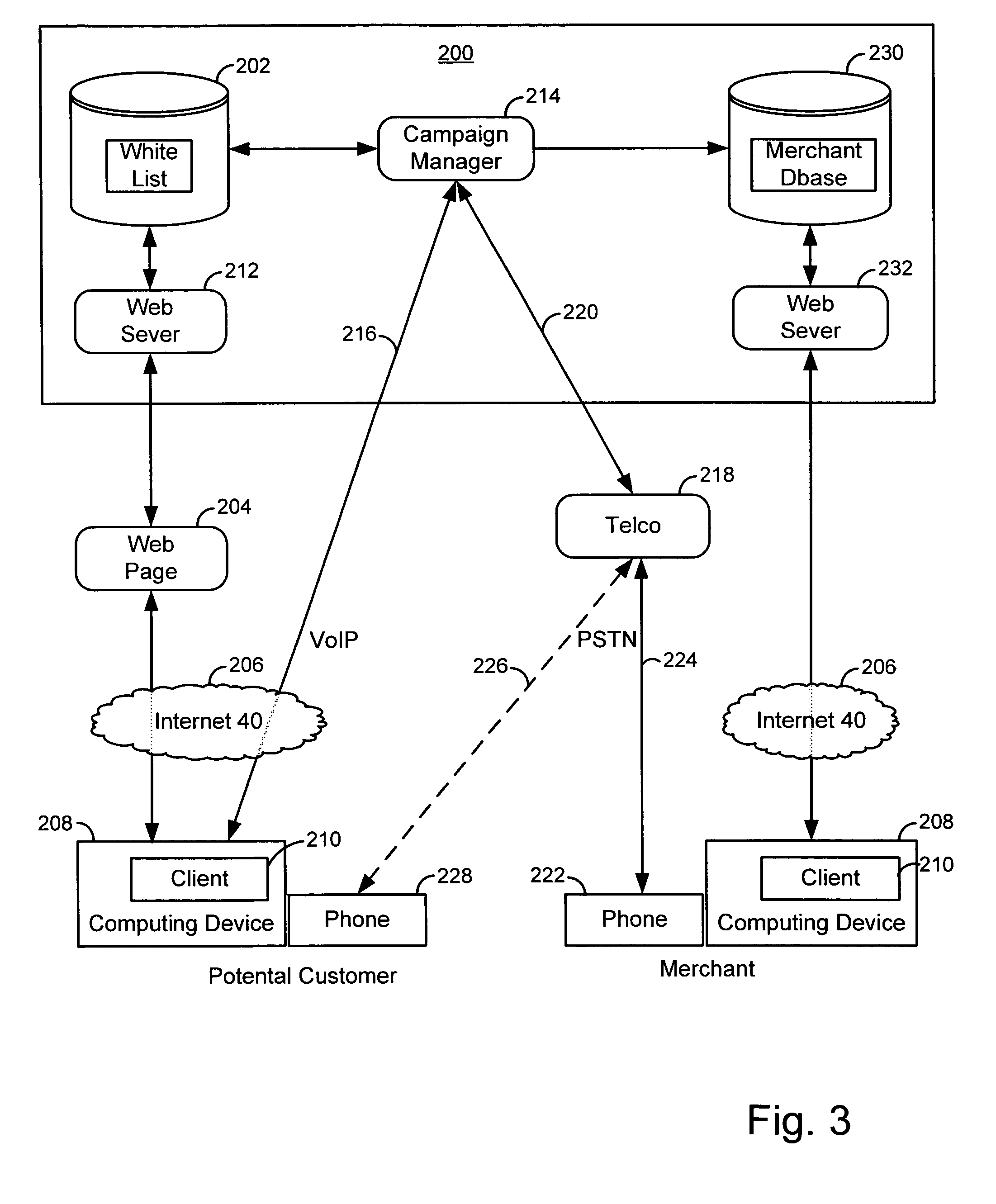
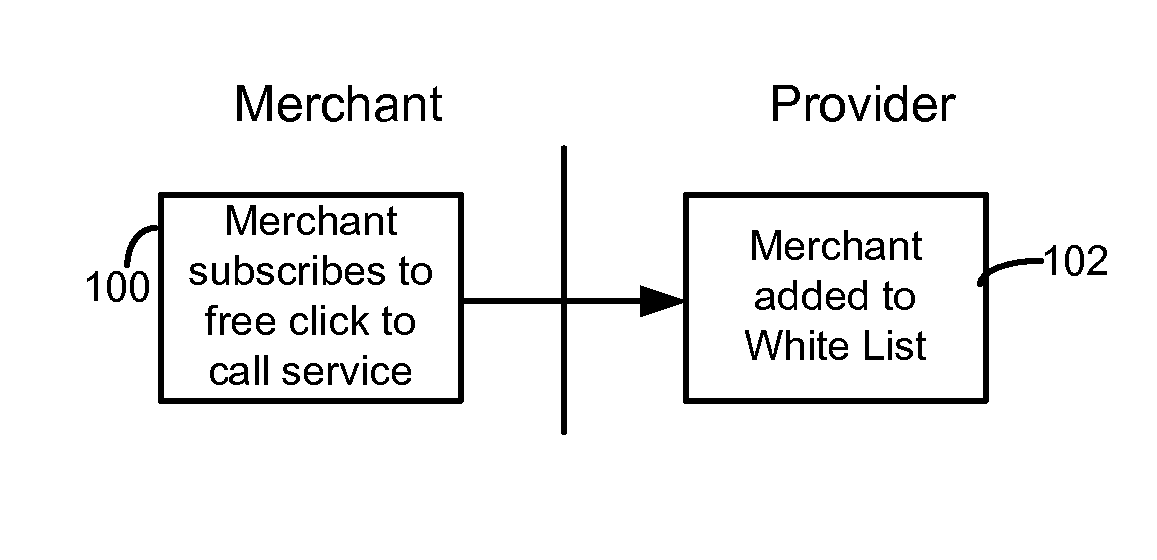
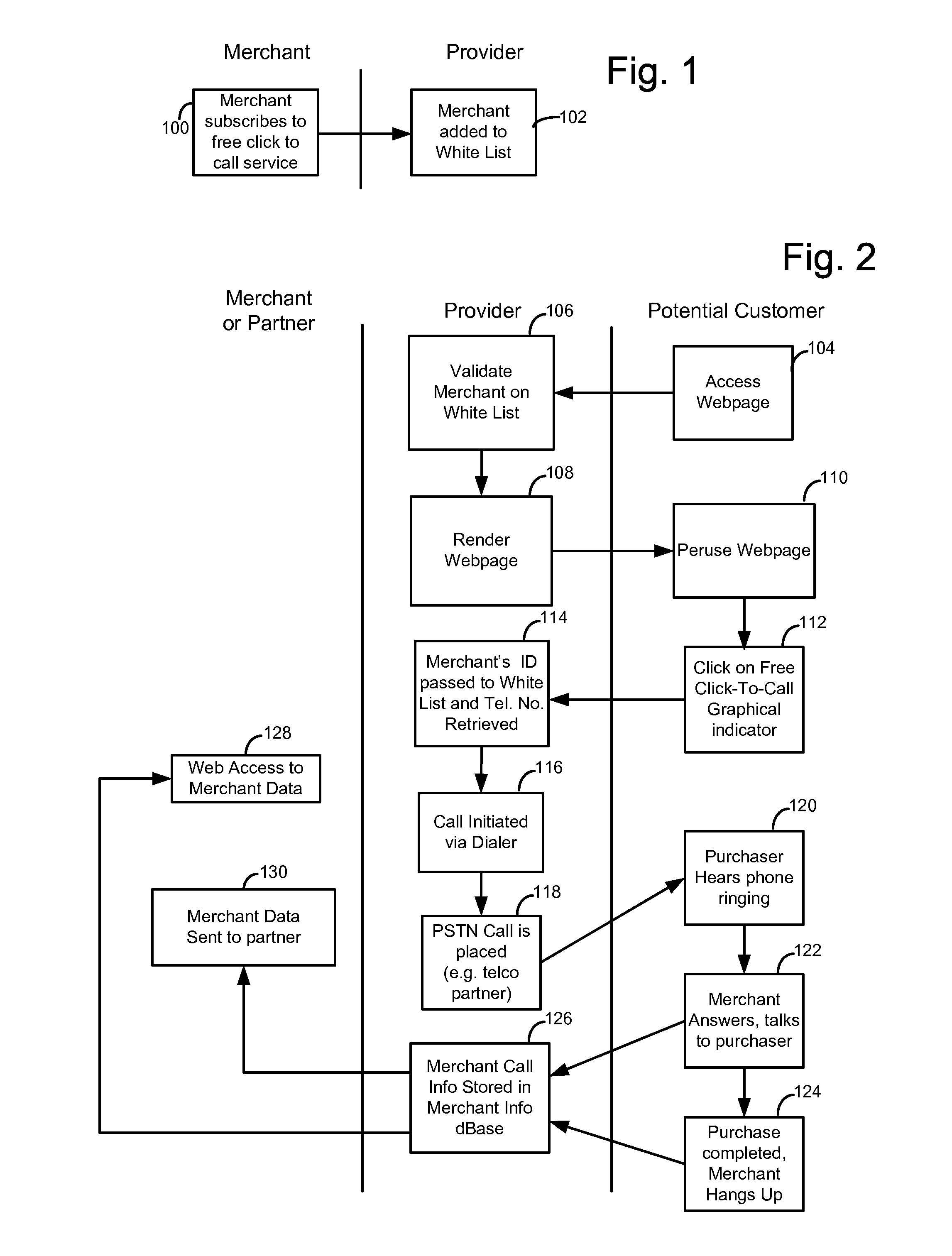
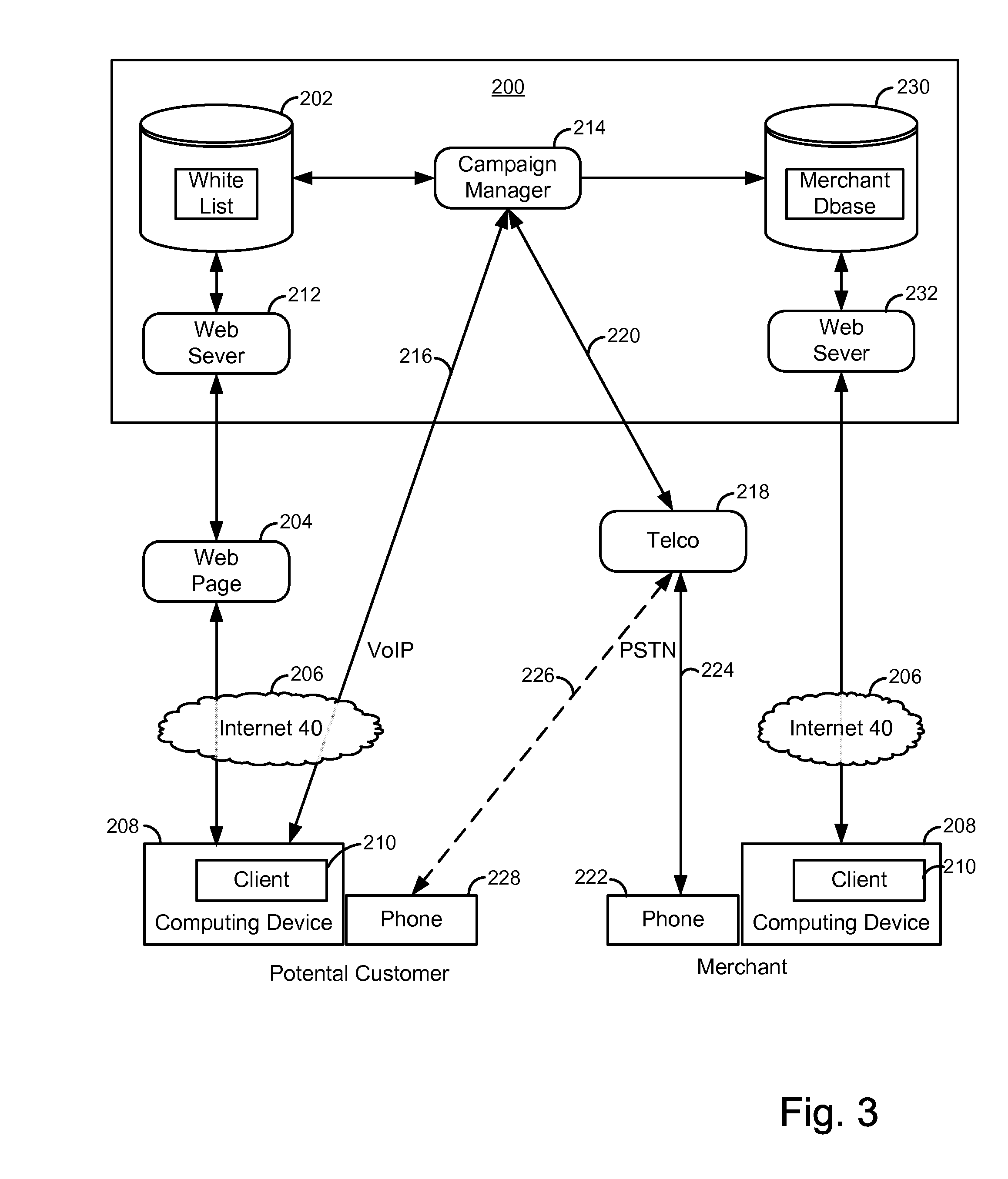
Merchant powered click-to-call method
ActiveUS20070112656A1Easy to returnEnhancing predictability and scalability and cost-effectivenessFinanceAdvertisementsExtensibilityCost effectiveness
A method is disclosed for enhancing the predictability, scalability and cost effectiveness of online advertising with voice over IP connectivity and event tracking technologies. A service provider maintains a list of merchants who have offered to pay for customer VoIP calls to their establishment. The service provider maintains a real time connection with this merchant list and renders an advertisement in a distinguishing way in real time. A potential customer who views this advertisement on a web page may establish a VoIP call session with a merchant by selecting a free click-to-call link on the web page. When the customer places the call, the service provider pays for the call. Merchants in turn pay the service provider for displaying the ads that generated the calls on a price per call, price per impression or fixed fee basis.
Owner:MICROSOFT TECH LICENSING LLC
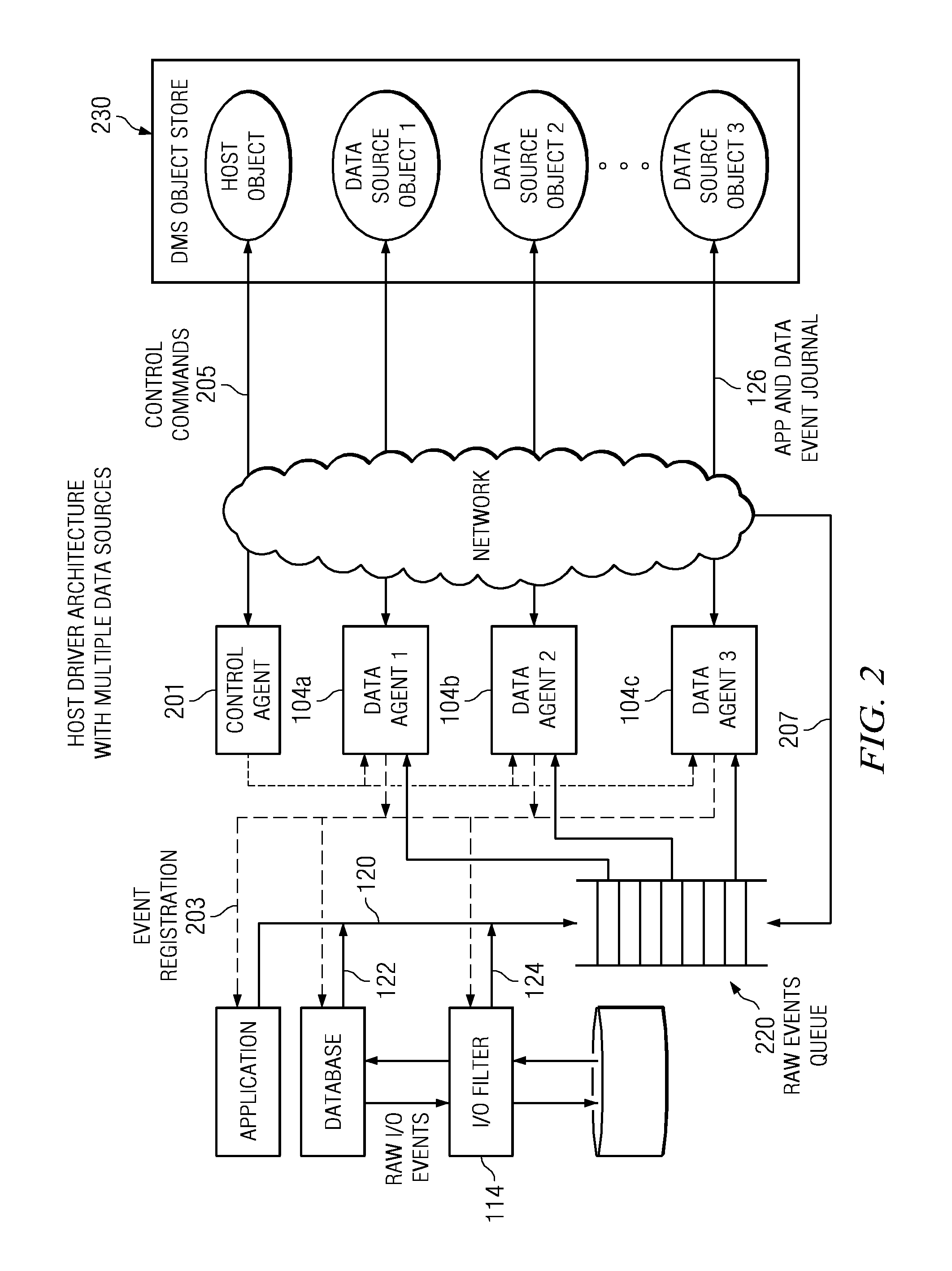
Tracing method and apparatus for distributed environments
Owner:NETWORK APPLIANCE INC
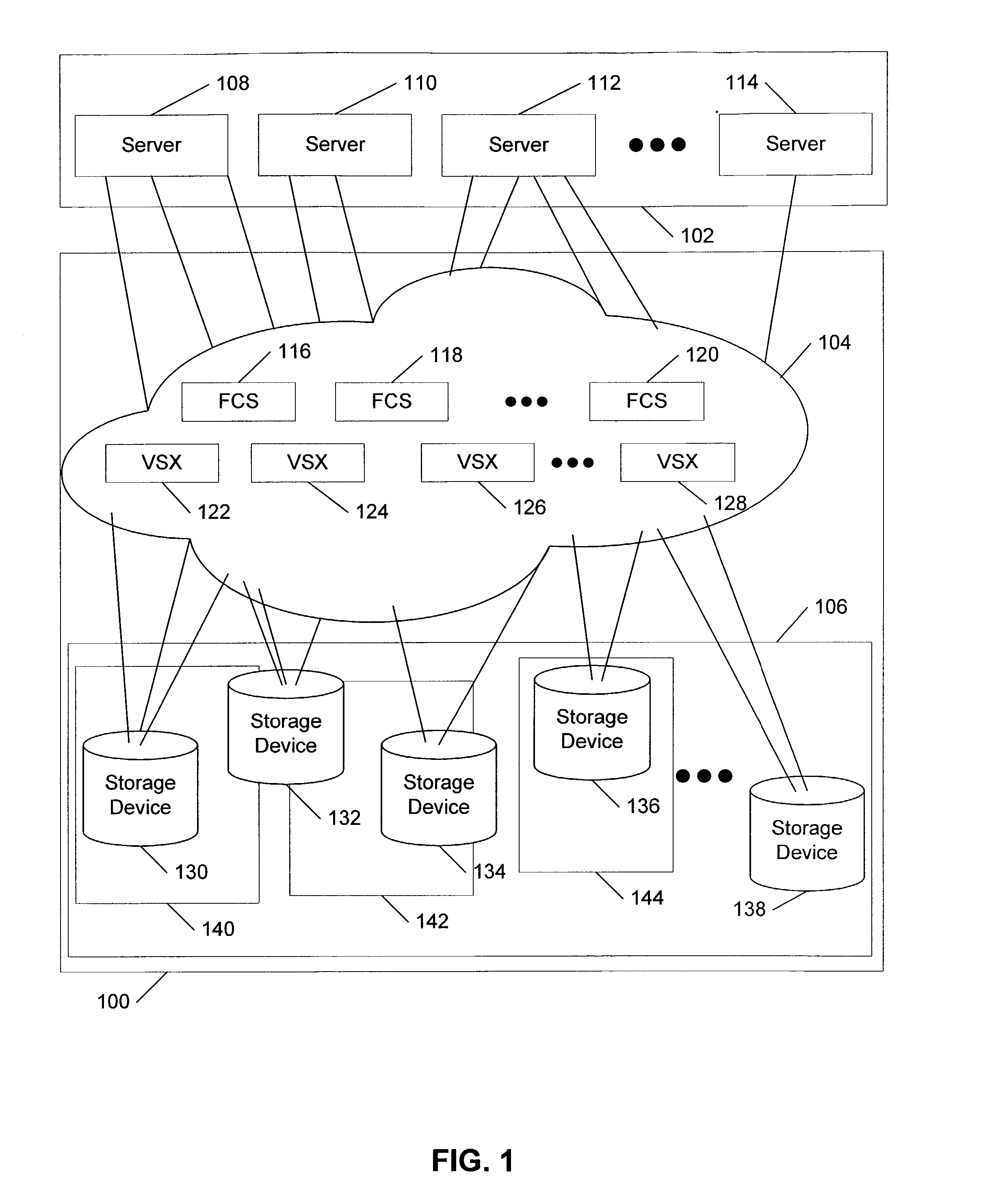
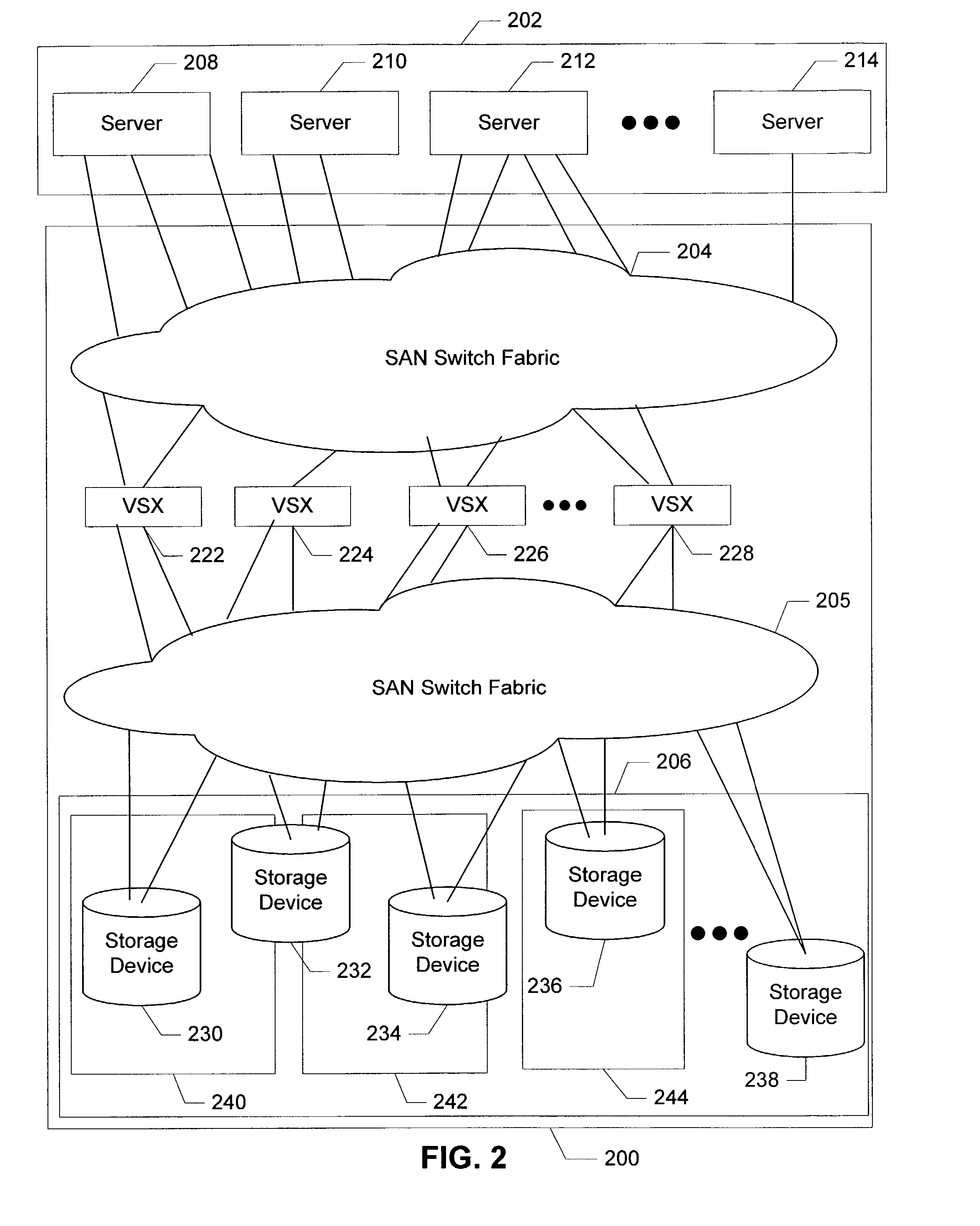
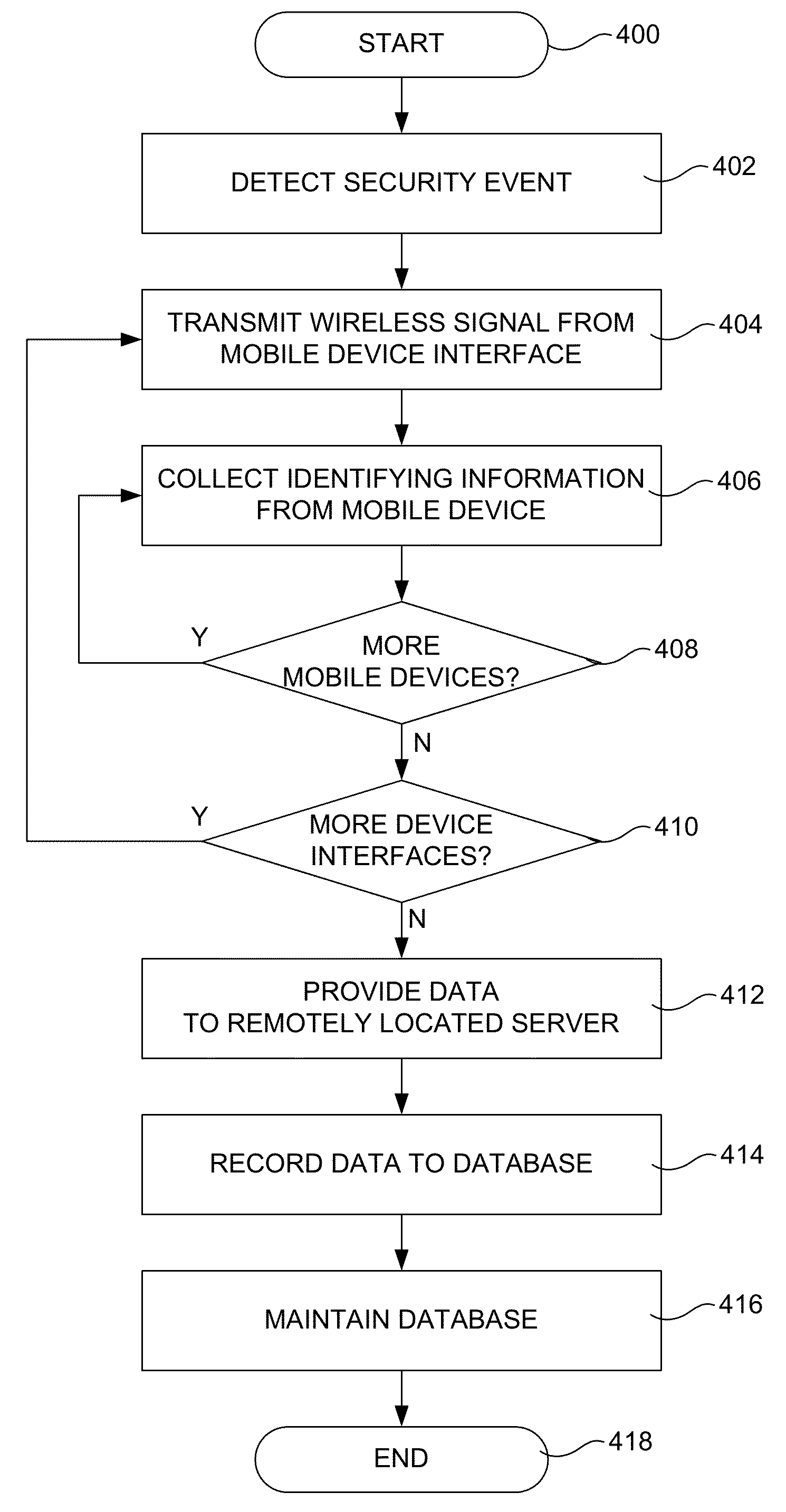
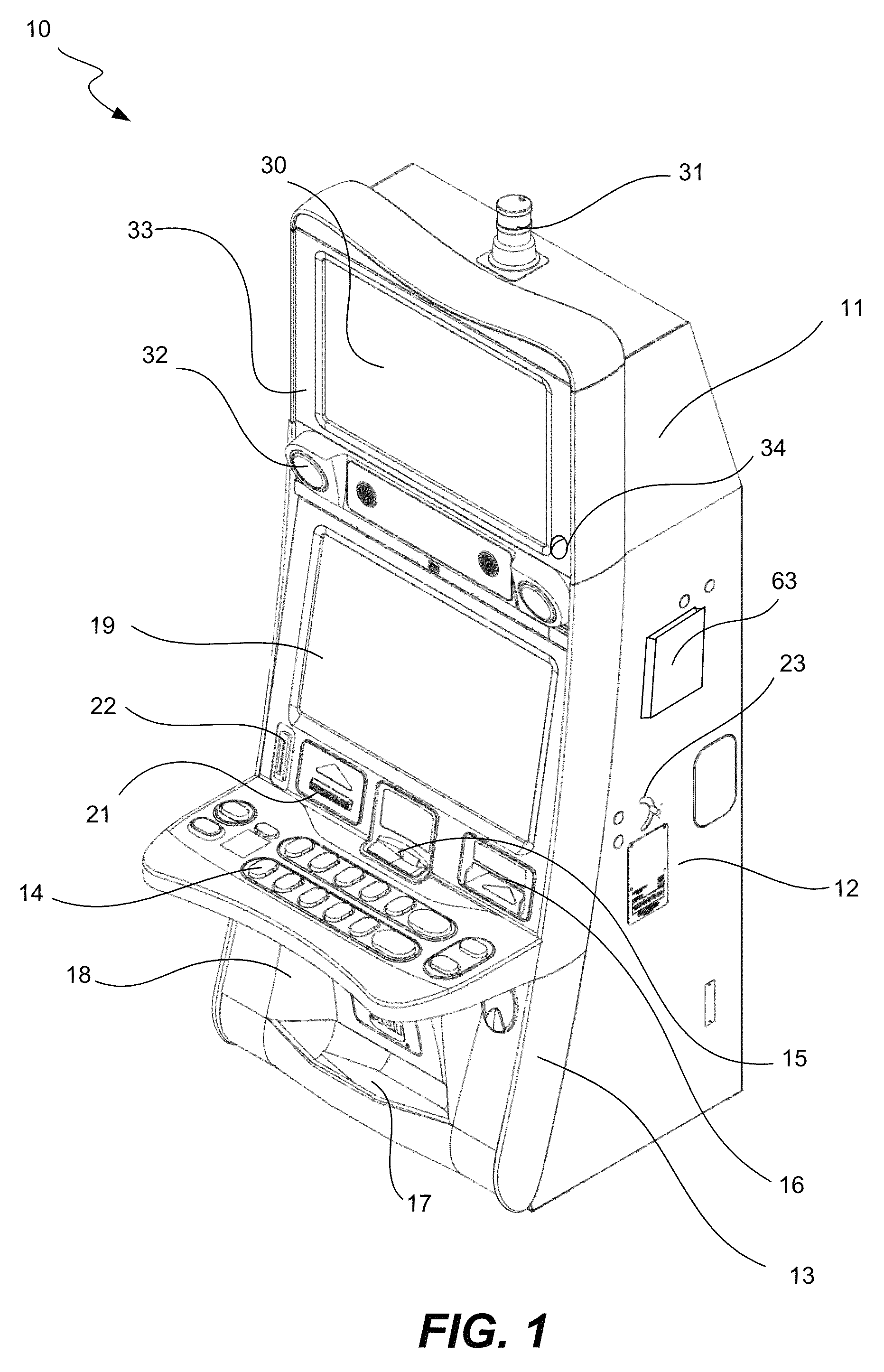
Mobile device to security event association in gaming environments
ActiveUS8876595B2Useful purposeEasy to trackApparatus for meter-controlled dispensingVideo gamesEvent trackingMobile device detection
A system that tracks information related to security events in a gaming environment includes a plurality of gaming machines, a database storing data regarding security events, and a security event tracking server in communication with the gaming machines and database. Each gaming machine can have an electronic tracking device adapted to detect wirelessly identifying information from portable electronic devices proximate the gaming machine with respect to the occurrence of a security event at or near the gaming machine. The server includes a processor configured to receive information regarding security events and mobile device identifying information, associate the security events with the identifying information, and store the associated security events and identifying information to the database. Mobile device identifying information can be detected passively without any affirmative input by any user of the mobile devices. Patterns of repeated mobile device detections associated with multiple security events can be determined.
Owner:IGT
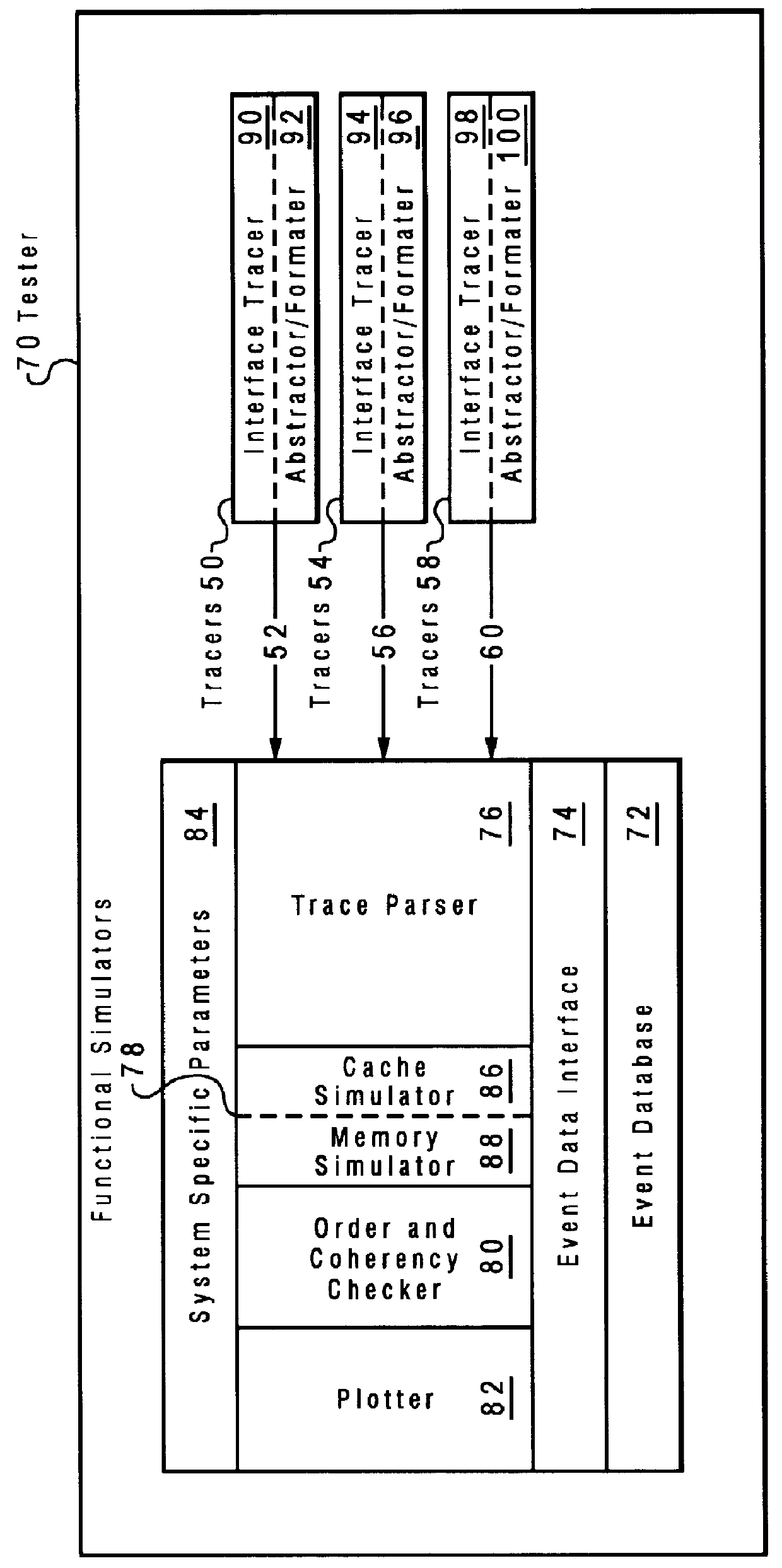
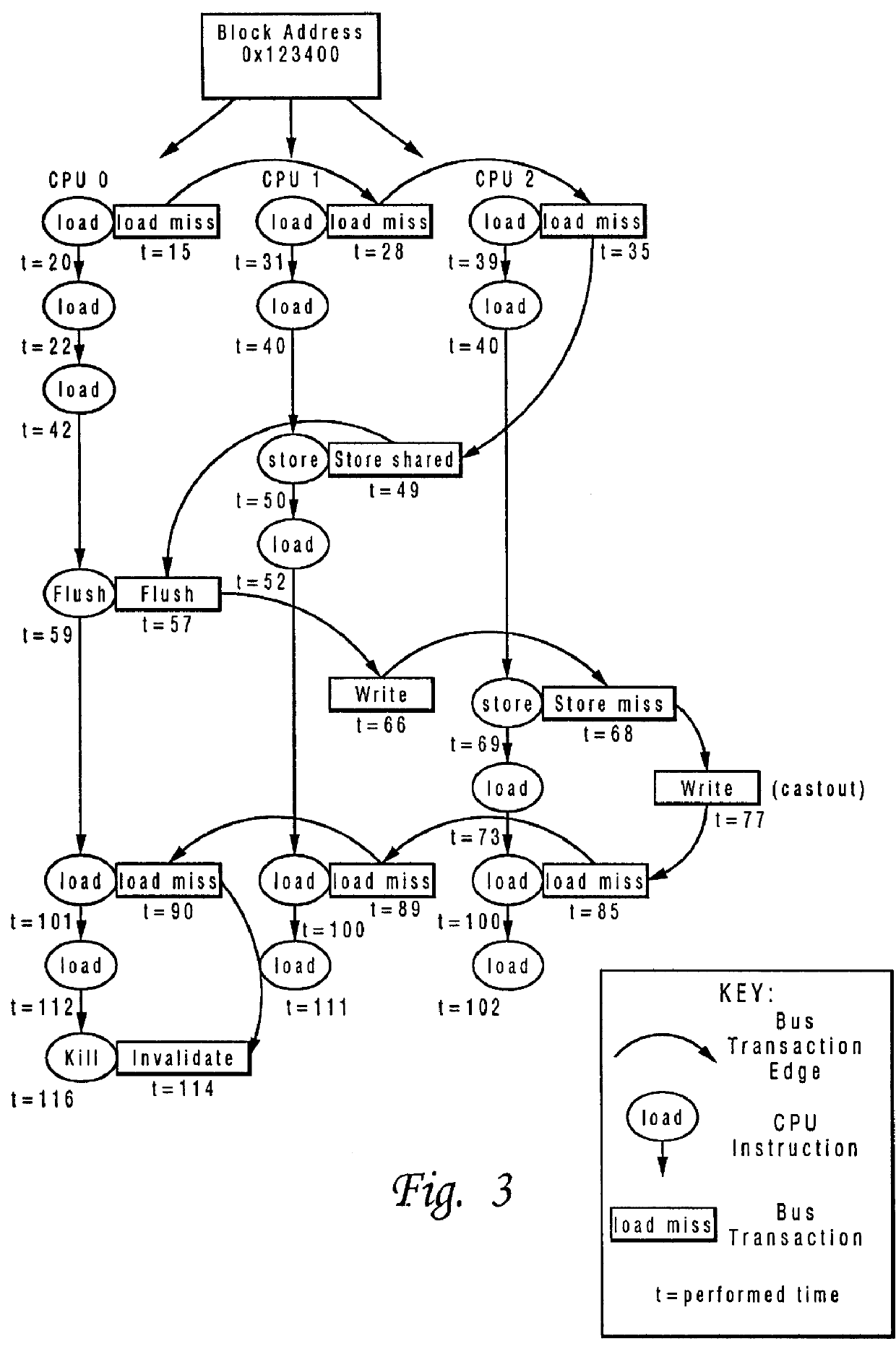
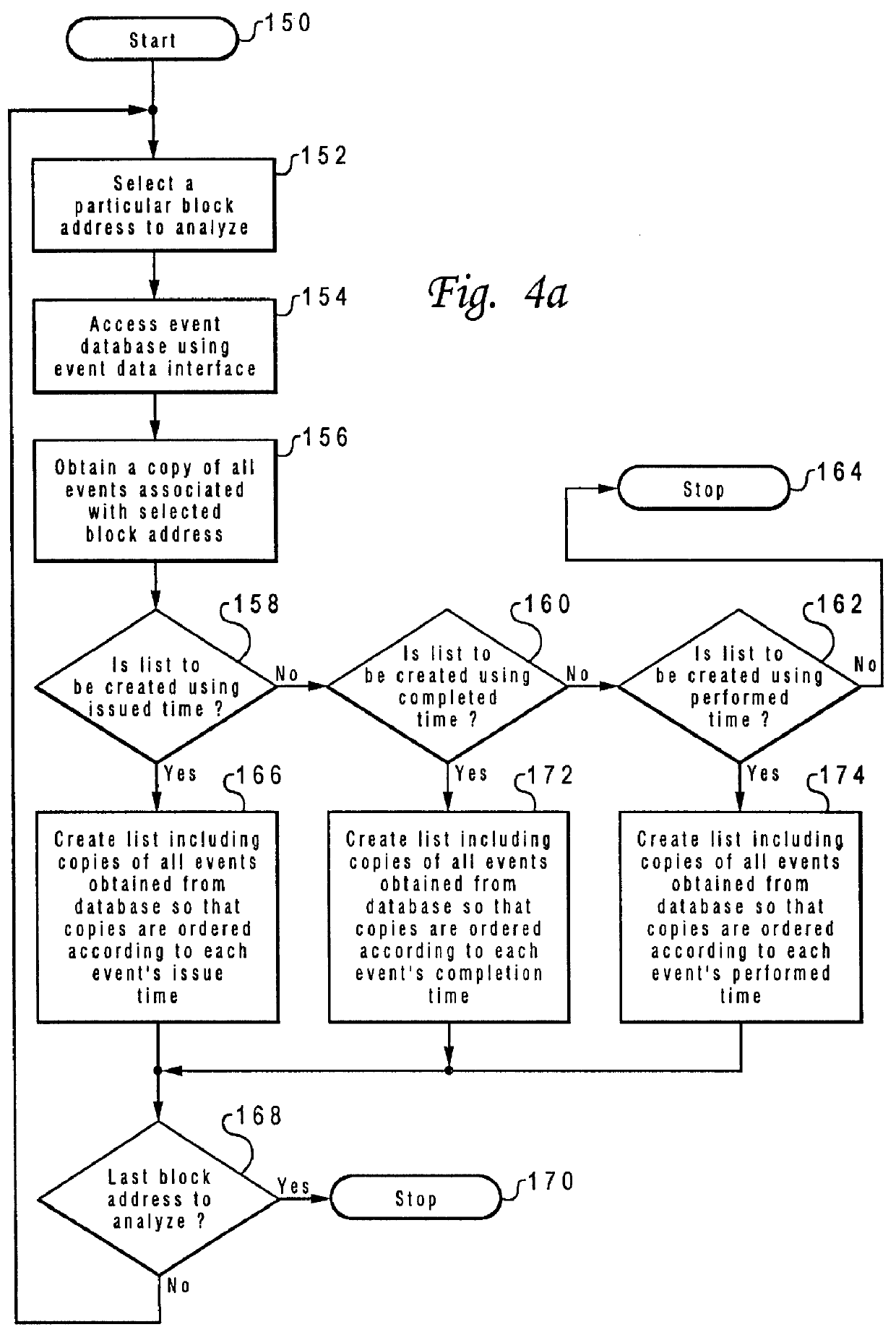
Method and system for testing a multiprocessor data processing system utilizing a plurality of event tracers
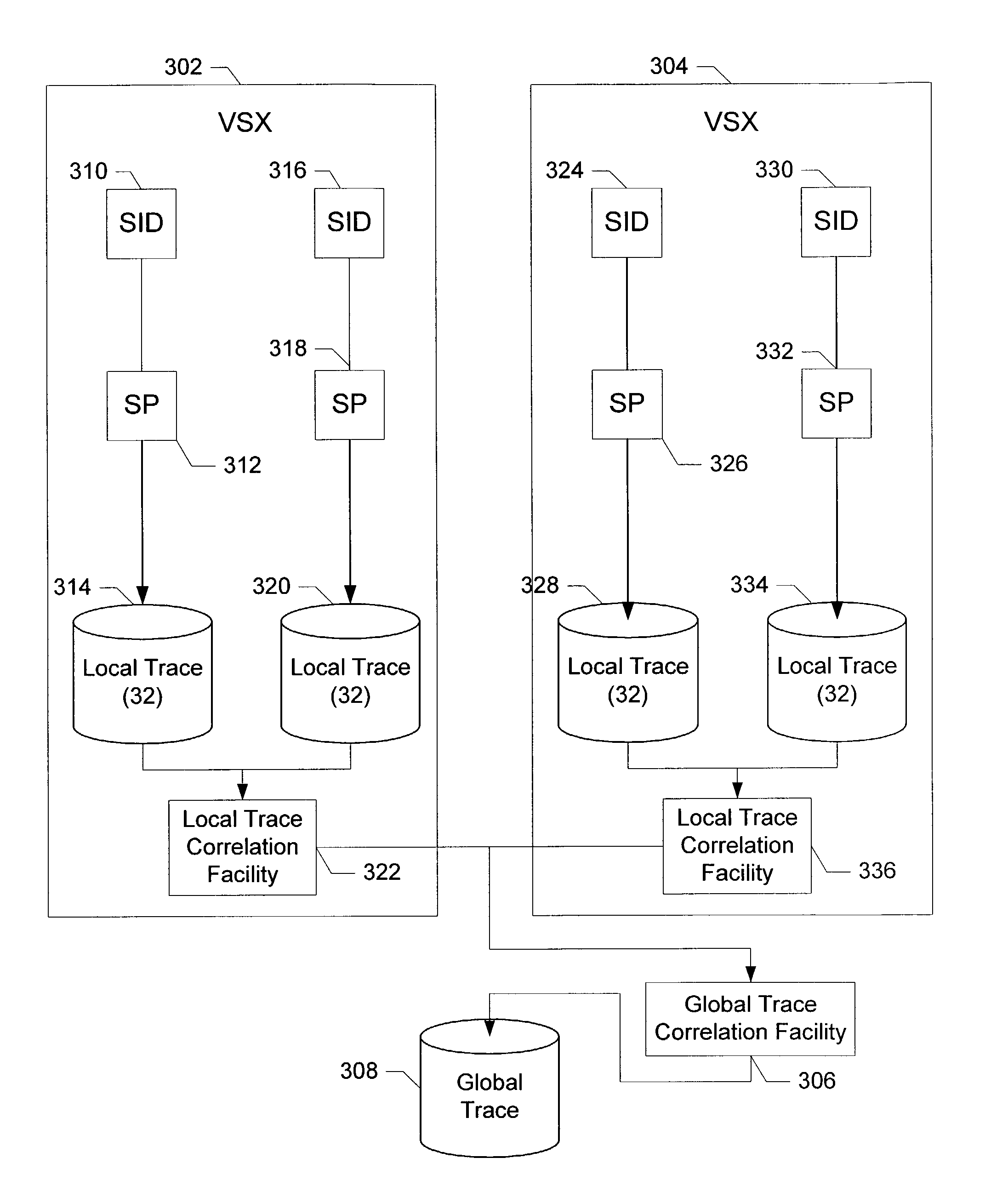
A multiprocessor data processing system includes a shared main memory and a plurality of processors connected to the memory utilizing a system bus. Data is transferred utilizing the system bus. The plurality of processors include a first processor and a second processor. The first processor includes a first cache, and the second processor includes a second cache. The multiprocessor data processing system executes a test program. During execution of the test program, a first and a second trace are generated. The first trace is generated by monitoring all events occurring at a first location within the system. The second trace is generated by monitoring all events occurring at a second location within the system. Each event is associated with a time of occurrence of that event. The first trace includes each event which was monitored at the first location and the time associated with each event. The second trace includes each event which was monitored at the second location and the time associated with each event. The first and second traces are stored and utilized to determine if the multiprocessor data processing system is operating correctly.
Owner:IBM CORP
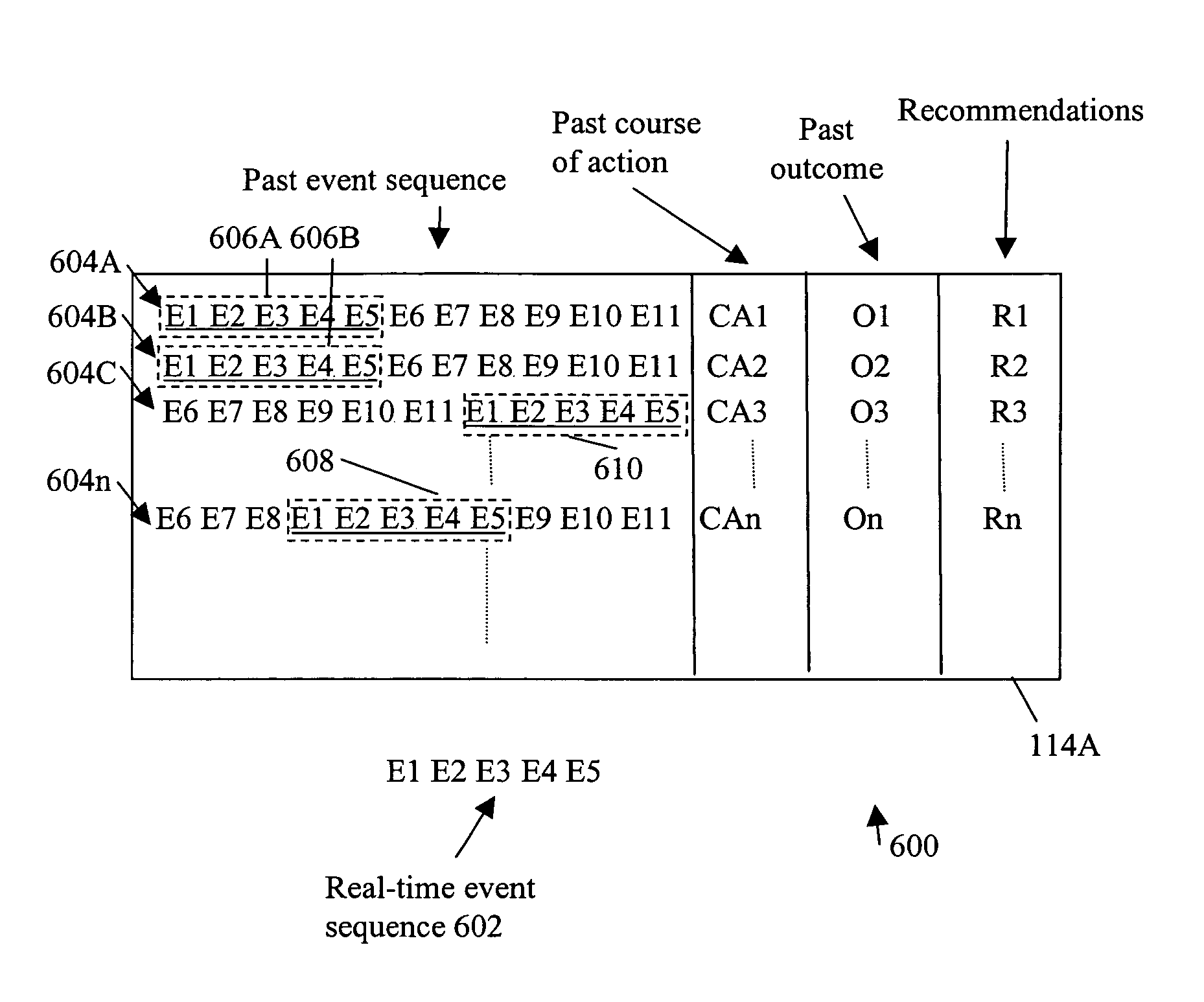
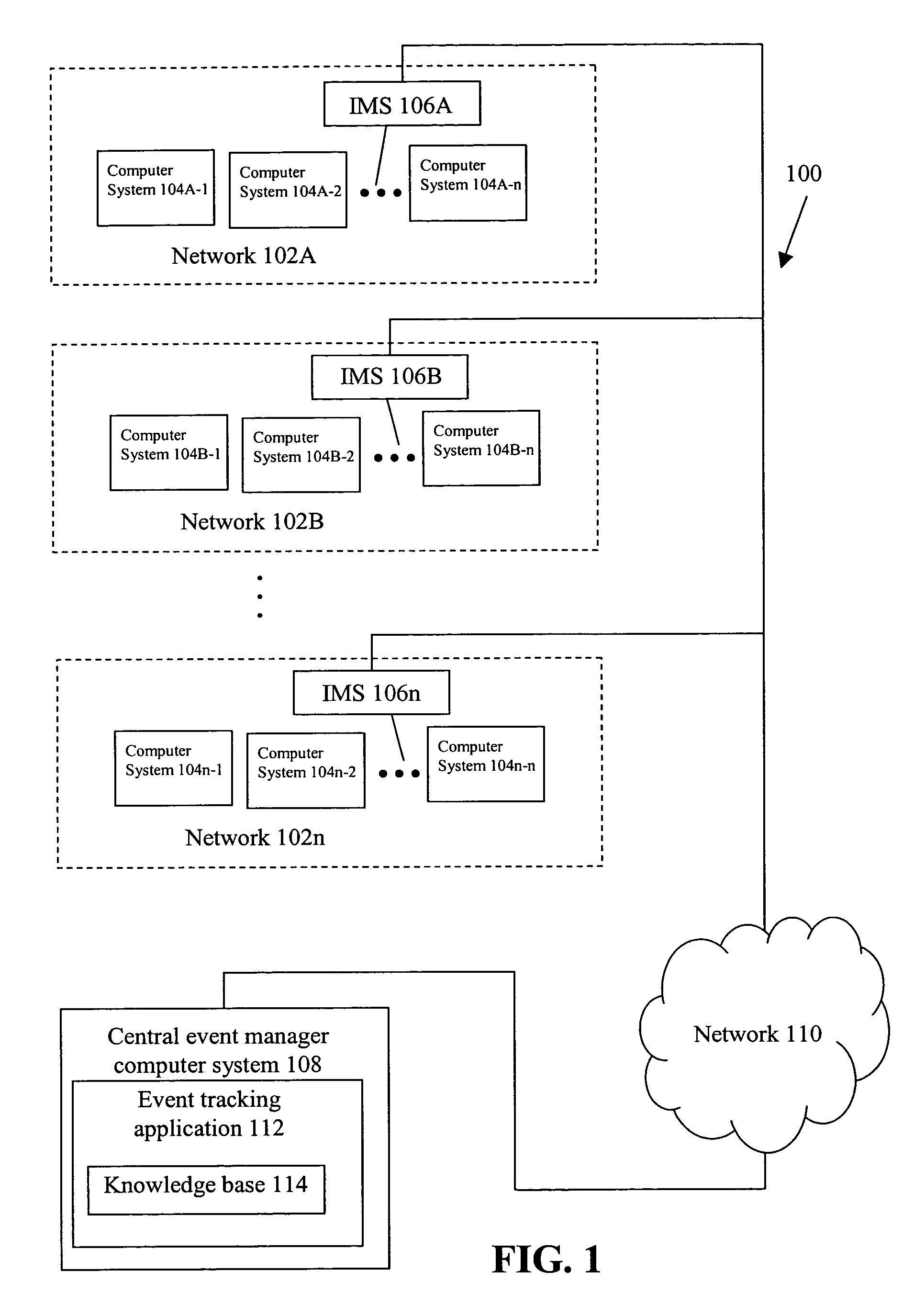
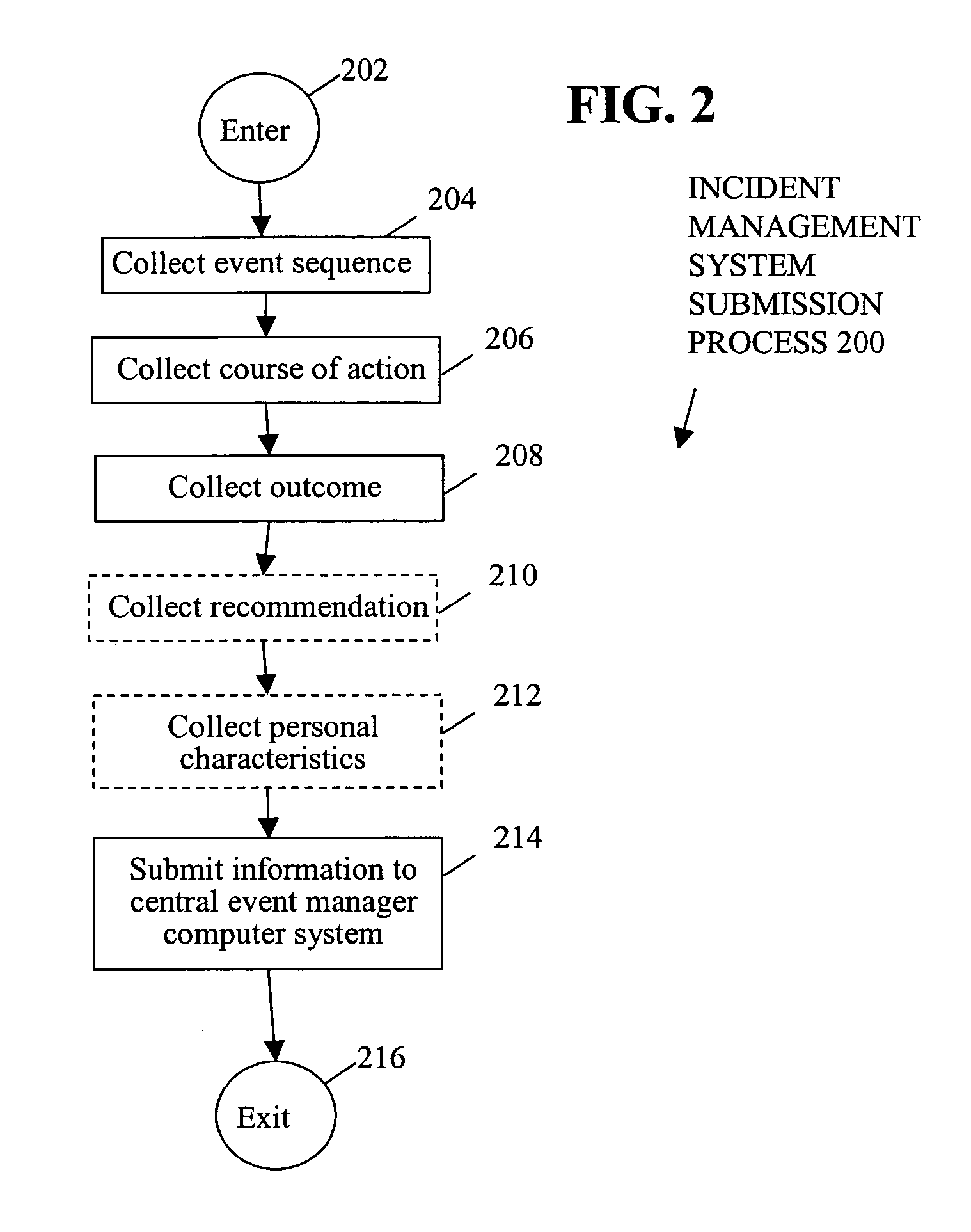
Subjective and statistical event tracking incident management system
A method includes logging past event sequences in a knowledge base, receiving a real-time event sequence, comparing the real-time event sequence to the past event sequences to determine a predicted event sequence for the real-time event sequence, and providing the predicted event sequence, a suggested course of action with predicted outcome, and a recommendation of a user who previously encountered the event sequence. In the above manner, use of subjectively characterized and / or raw historic data to match real-time event sequences provides users with both subjective advice from those who had previously faced similar conditions as well as raw statistical predictions as to what is expected to come next. This allows the users to take a course of action that results in the most desirable outcome.
Owner:CA TECH INC
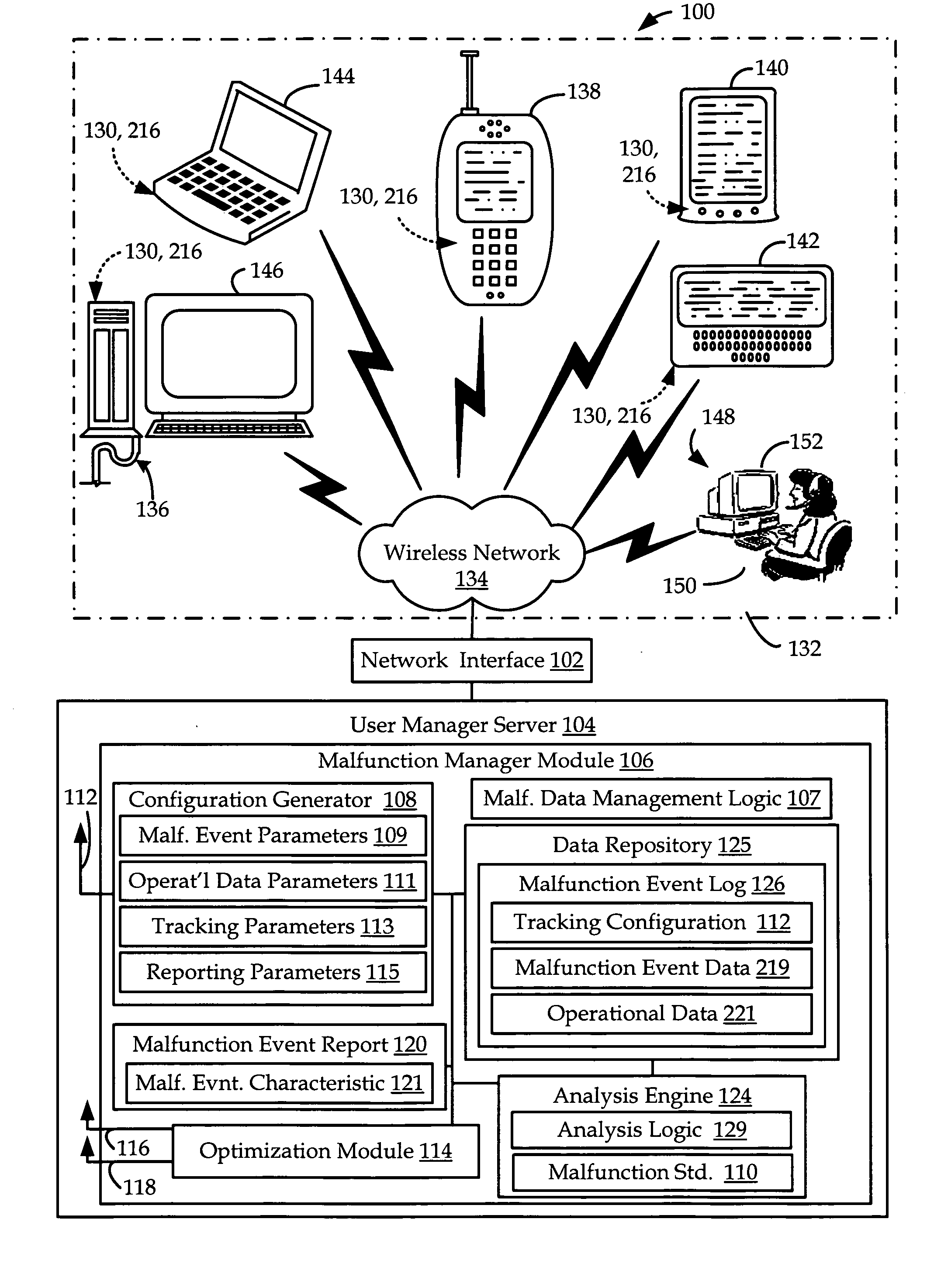
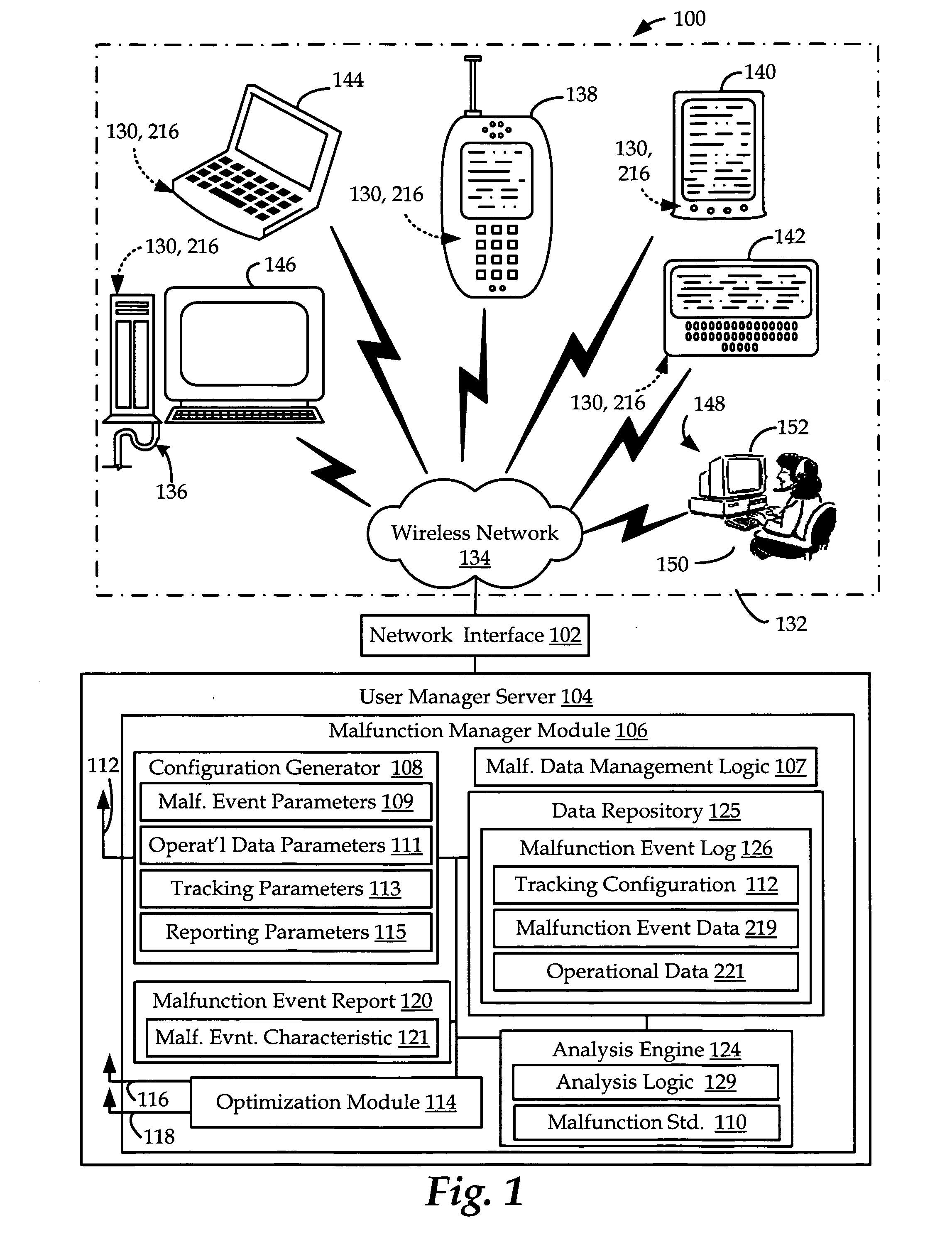
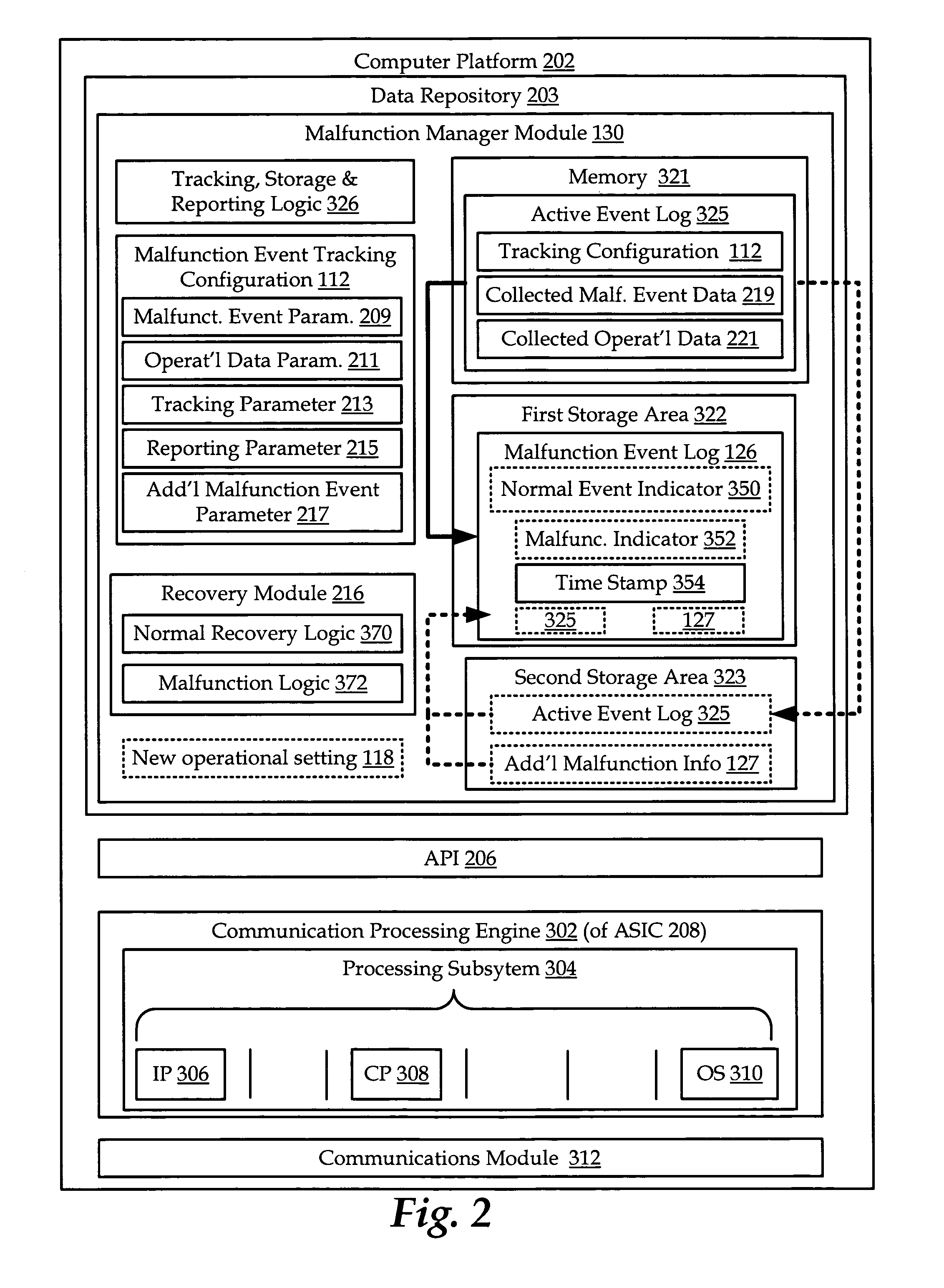
Apparatus and methods for managing malfunctions on a wireless device
ActiveUS20060211415A1Radio/inductive link selection arrangementsTransmission monitoringEvent dataInformation Harvesting
Apparatus and methods for managing predetermined malfunction events in a wireless device operating in a wireless communications network. Malfunction event data and operational data are recorded by the wireless device based on a selected malfunction event tracking configuration. Further, a recovery module associated with the wireless device operates to attempt to recover information leading up to and including the malfunction event. The collected information may be transmitted to a user manager in the form of a malfunction event log. The malfunction event log may be analyzed to characterize the malfunction, and is particularly useful for determining the sequence and identity of events leading to the malfunction, including a crash, freeze and reset.
Owner:QUALCOMM INC
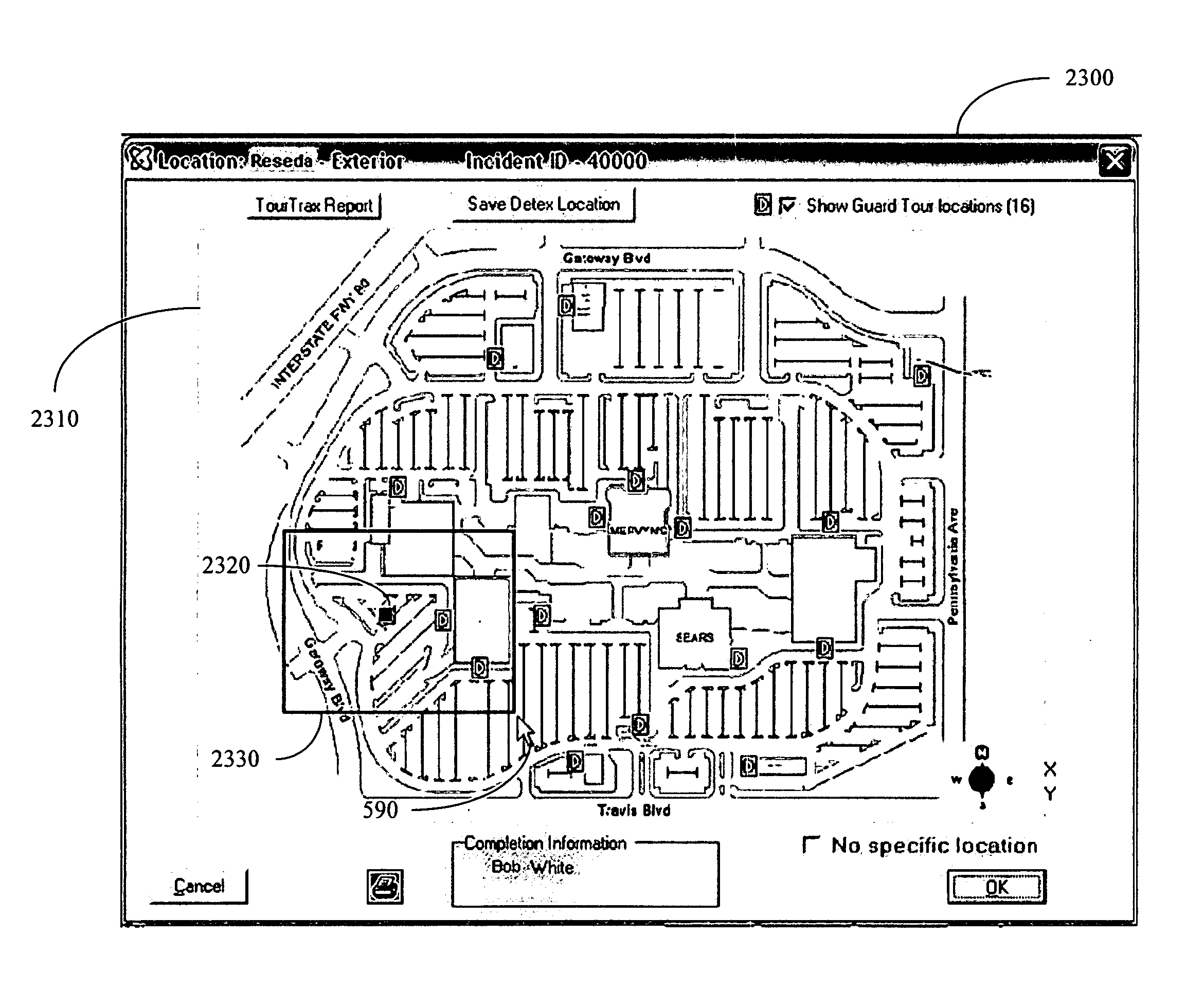
Incident tracking systems and methods
InactiveUS8549028B1Avoid it happening againDigital data information retrievalData processing applicationsDate RangeComputer science
Various embodiments of the present invention are related to incident tracking systems and methods. A method allows for receiving input that specifies an incident at a facility, defining a search area adjacent to a position of the incident, and displaying one or more other incidents that occurred at the facility within the search area. A further method allows for dynamically plotting, each time a search area is changed on a map of a facility and an associated date range is indicated, positions on the map within the search area so as to indicate where incidents have occurred at the facility within the date range. Another method allows for receiving input that specifies a name of a person associated with an incident at a facility, and automatically flagging the person as being of interest if the person has been involved in one or more other incidents at the facility.
Owner:CASE GLOBAL
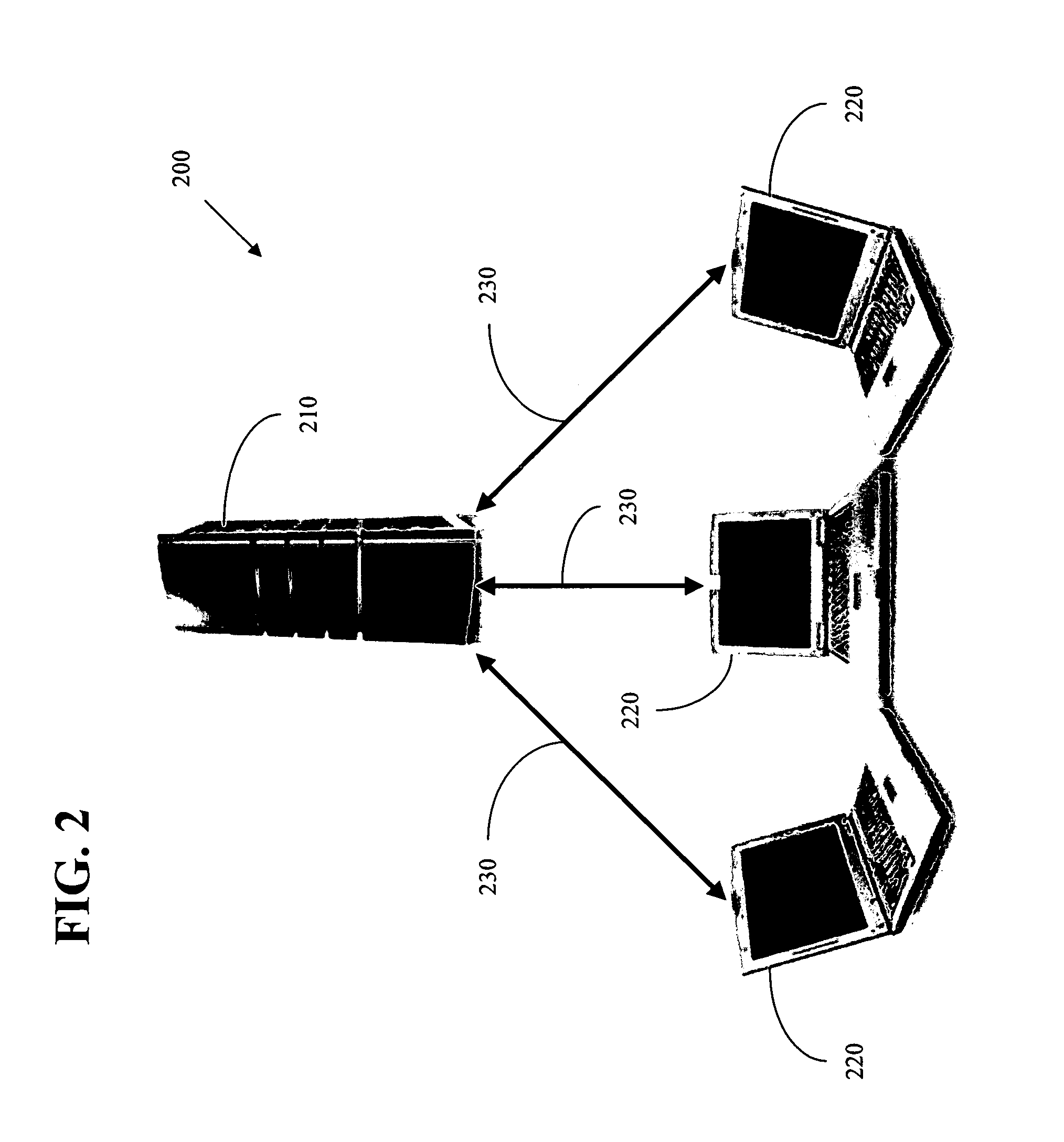
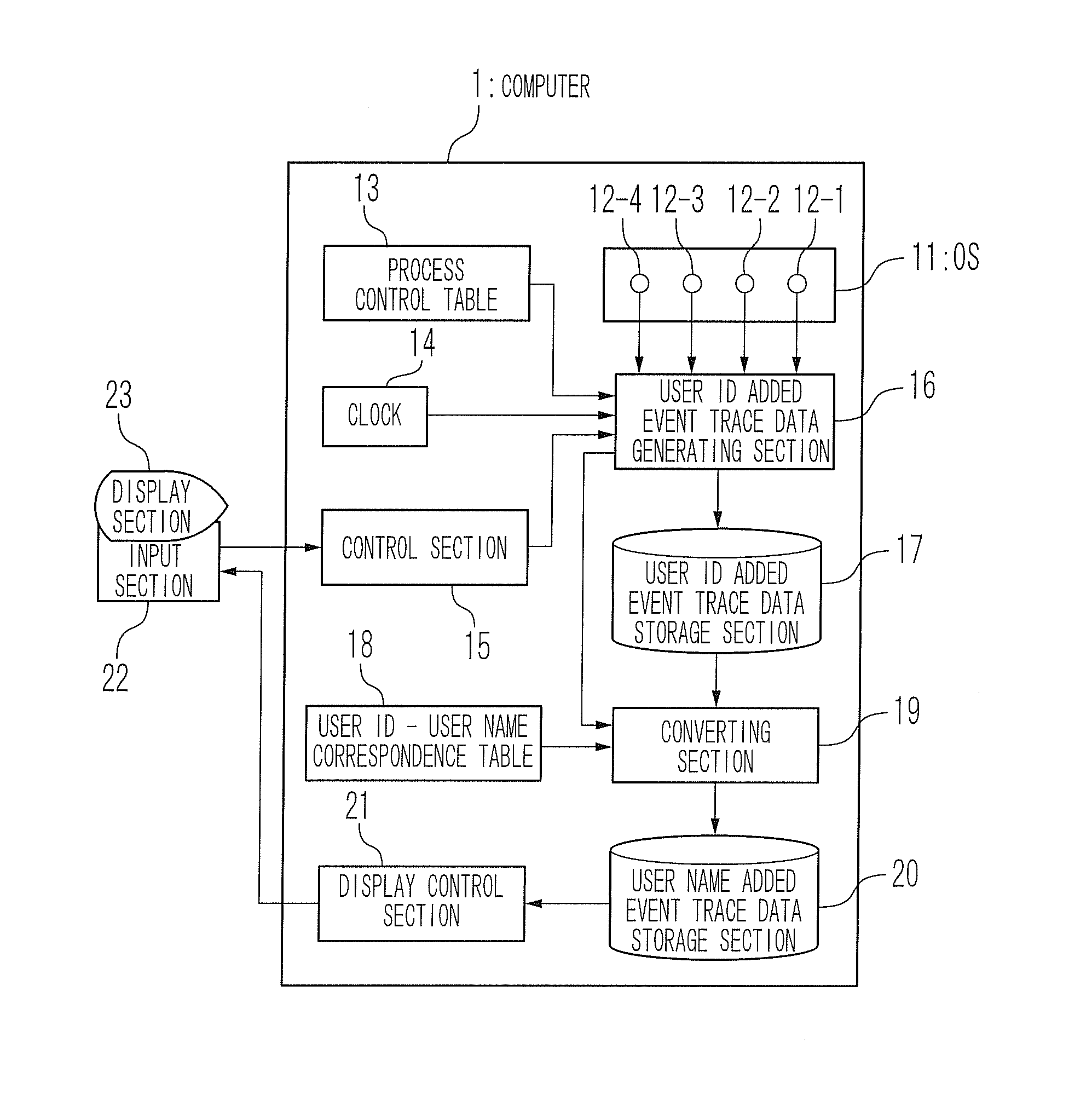
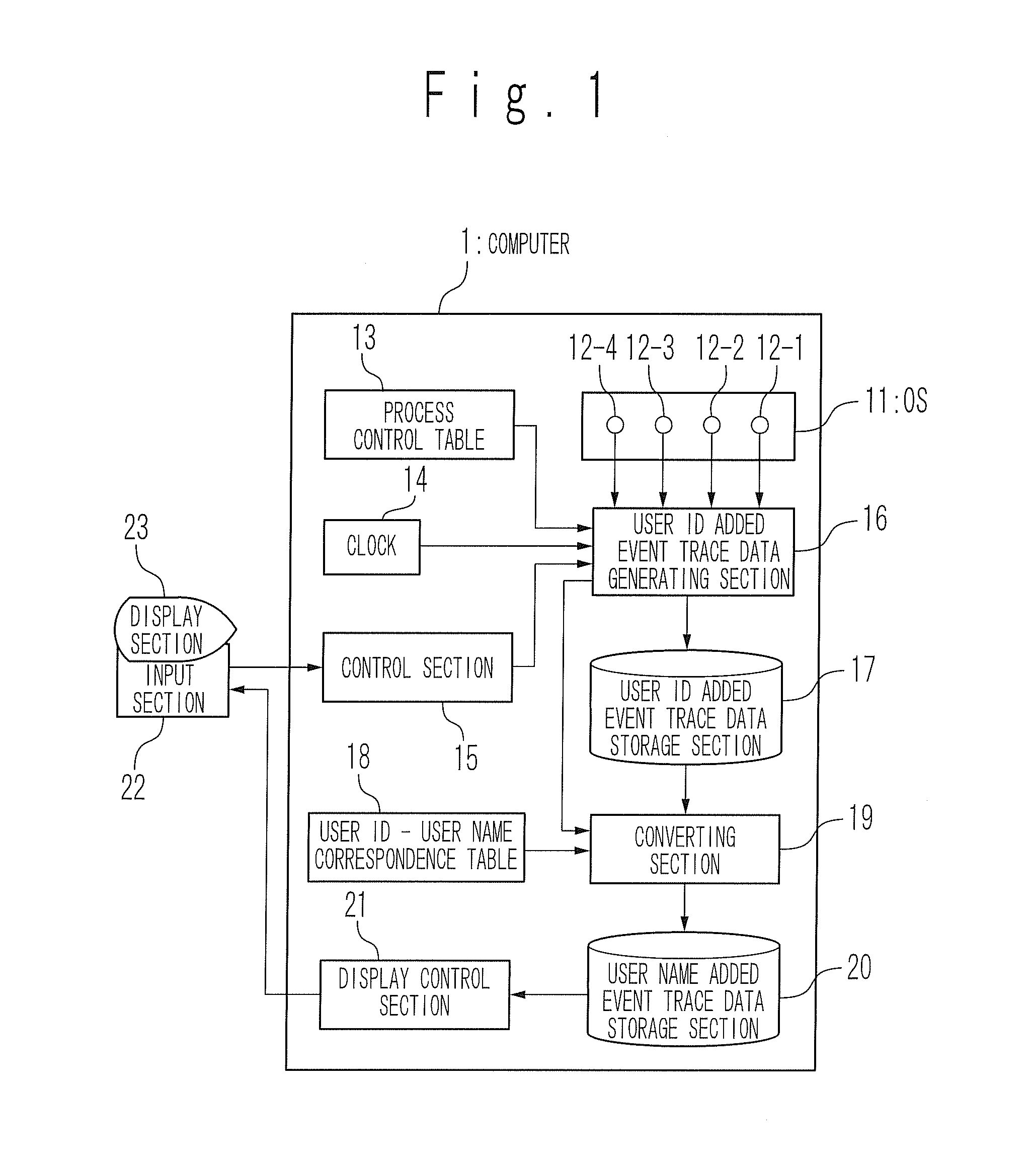
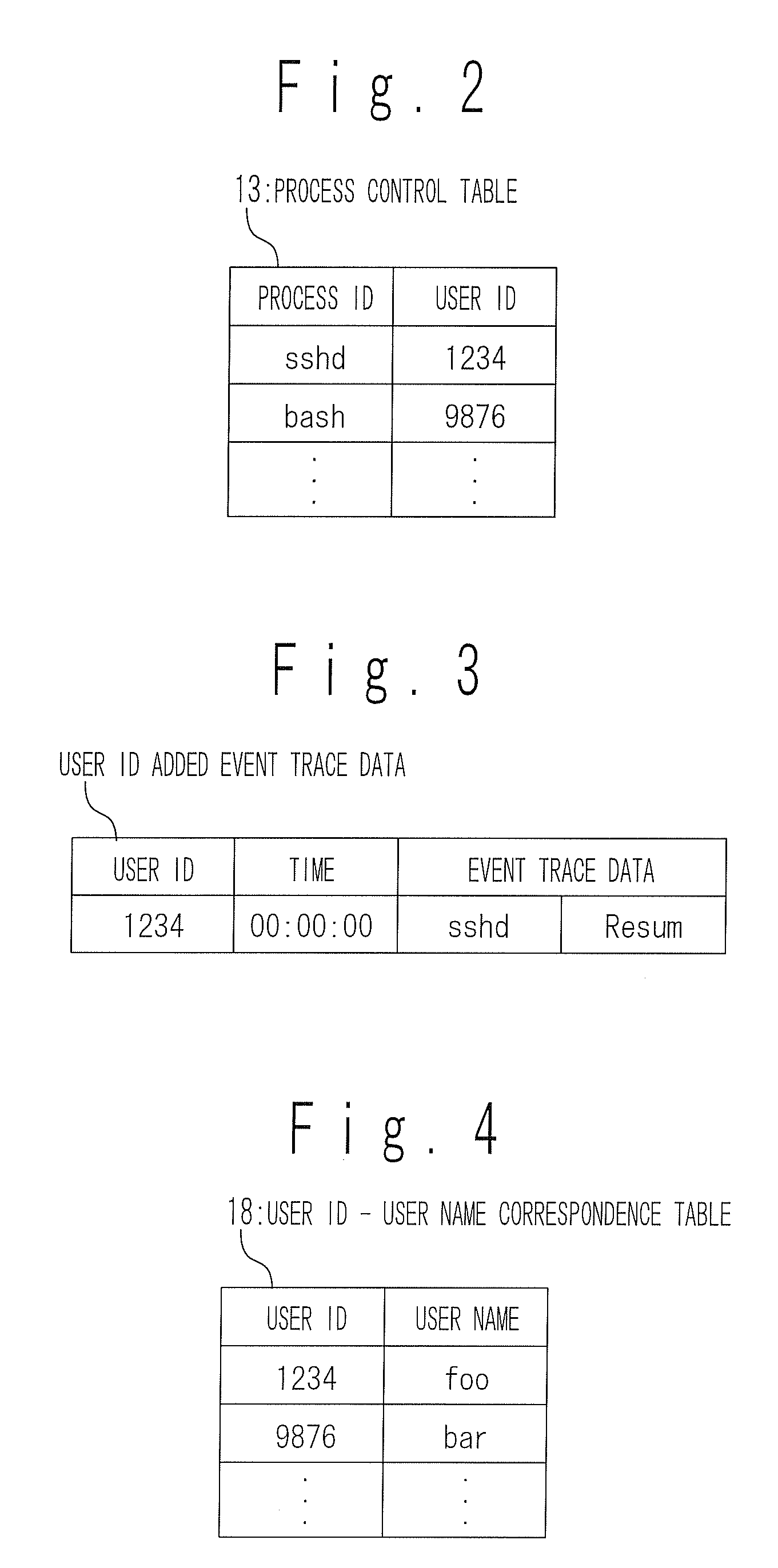
Apparatus and method for displaying process operation
InactiveUS20080209443A1Sure easyError detection/correctionMultiprogramming arrangementsUser identifierEvent tracking
A process operation display apparatus includes a storage section configured to store a process control table in which a set of a process ID of a process and a user ID of a user is written. An event trace data outputting section detects events of about execution start and execution end of an executed process and generates an event trace data based on a process ID of the executed process and the detected events. A user ID added event trace data generating section generates a user ID added event trace data in which a set of the event trace data and the user ID corresponding to the process ID contained in the event trace data is written, by referring to the process control table based on the process ID. A display control section displays a set of the process ID of the executed process and the user ID of the user who instructed the execution of the executed process on a display unit based on the user ID added event trace data.
Owner:NEC CORP
Recovering a database to any point-in-time in the past with guaranteed data consistency
ActiveUS8712970B1Digital data processing detailsStructured data retrievalTransaction dataData management
A data management method wherein a real-time history of a database system is stored as a logical representation and the logical representation is then used for any point-in-time recovery of the database system. More specifically, a method for capturing transaction data, binary data changes, metadata, and events, and for tracking a real-time history of a database system according to the events. The method enables tracking and storing of consistent checkpoint images of the database system, and also enables tracking of transaction activities between checkpoints. The database system may be recovered to any consistent checkpoint or to any point between two checkpoints.
Owner:QUEST SOFTWARE INC
Method and apparatus for controlling an electronic device
InactiveUS20160180801A1Improve the environmentImprove convenienceAcquiring/recognising eyesCathode-ray tube indicatorsControl electronicsHuman–computer interaction
Owner:SAMSUNG ELECTRONICS CO LTD
Event Tracking and Messaging System and Method
InactiveUS20130024492A1Data processing applicationsMultiple digital computer combinationsComputerized systemFacsimile
The various implementations of the present invention are provided as a network computer system configured to allow for the tracking and reporting of user-specified events, including but not limited to, performance metrics and attendance data. This network computer system provides a user interface that allows a user to create metrics to be monitored, view and update event-related information, and to configure and review various pre-programmed and ad hoc reports so the users can monitor and evaluate performance metrics over time. Further, a wide variety of user and system generated alerts and messages or message events can be configured, allowing for automated and manual messaging related to the attendance or performance metrics that are being monitored. Alerts can be provided via email, non-electronic mail, telephone, SMS, facsimile, social networking sites and services (such as “tweets”), etc. In at least one implementation of the present invention, a computer-implemented method of tracking and reporting student performance and attendance-related events for an educational environment is provided.
Owner:PARLANT TECH
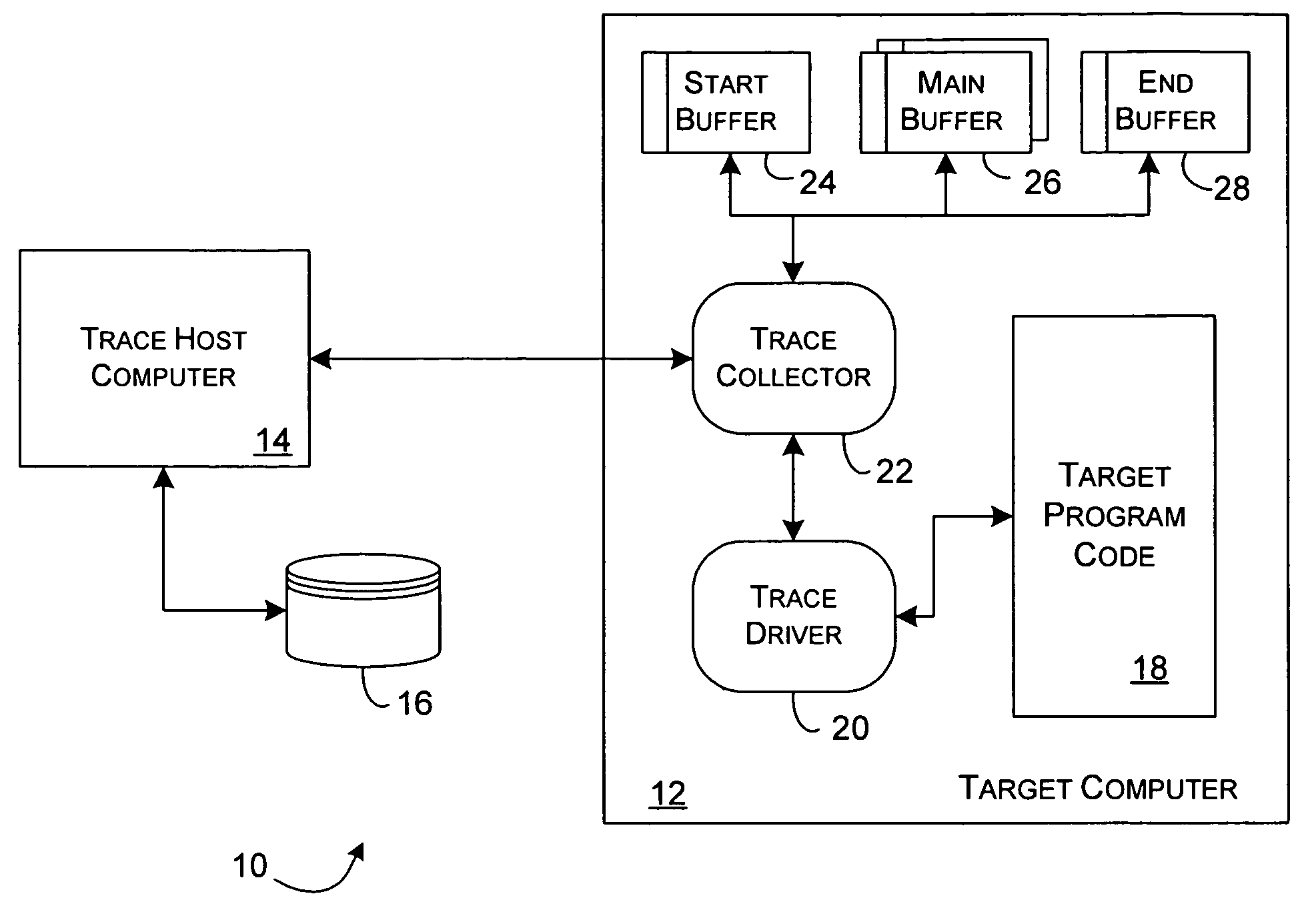
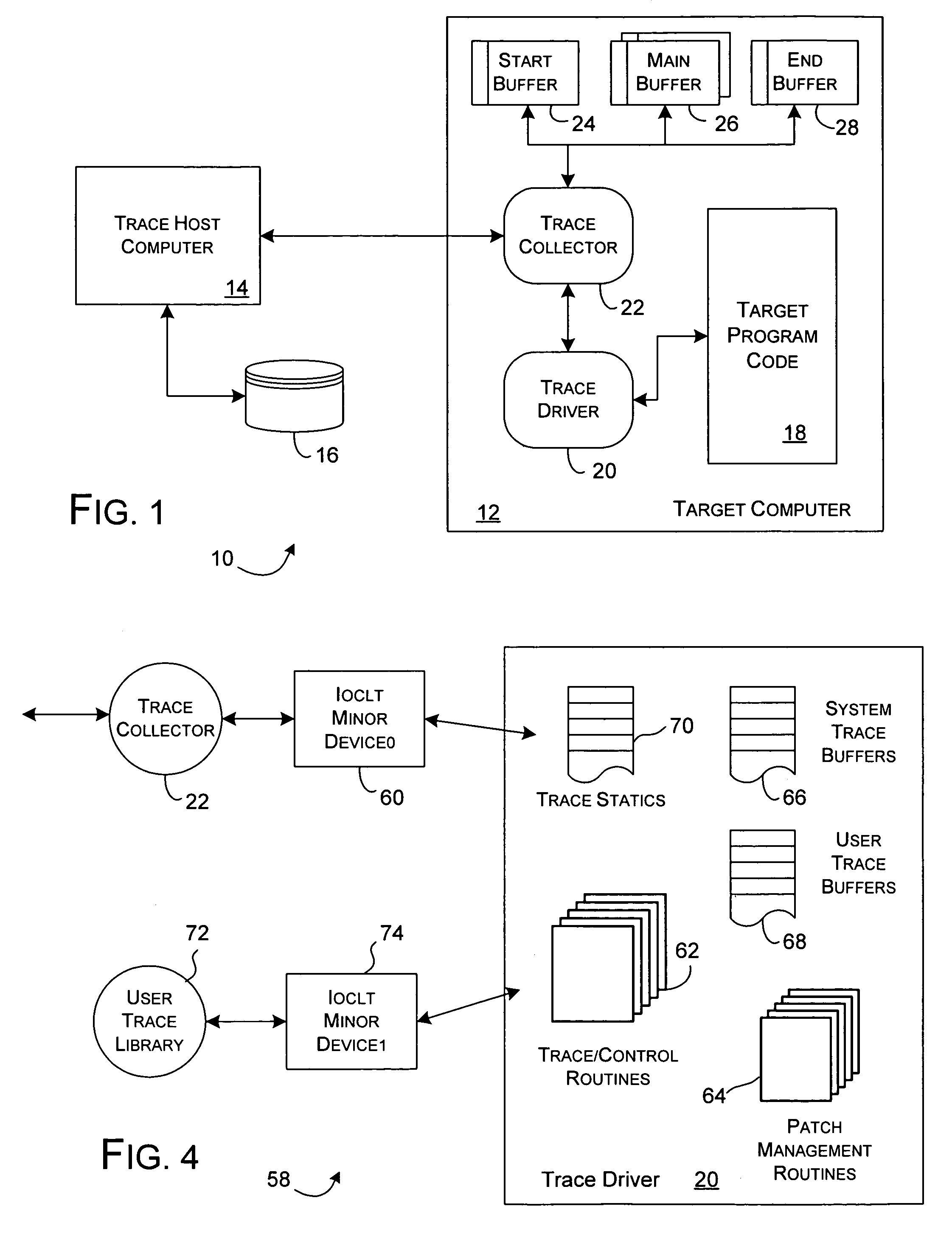
Methods and apparatus for accessing trace data
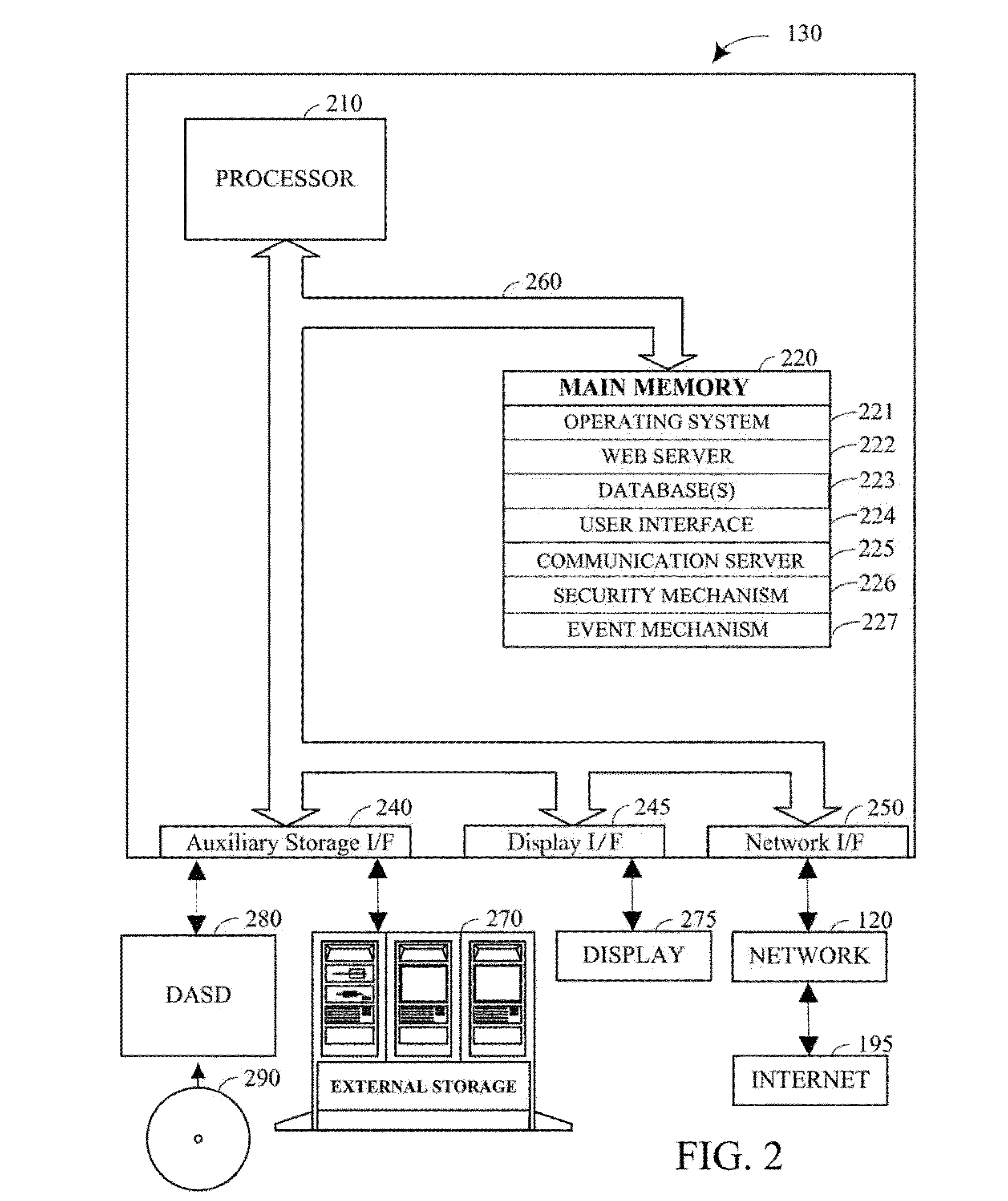
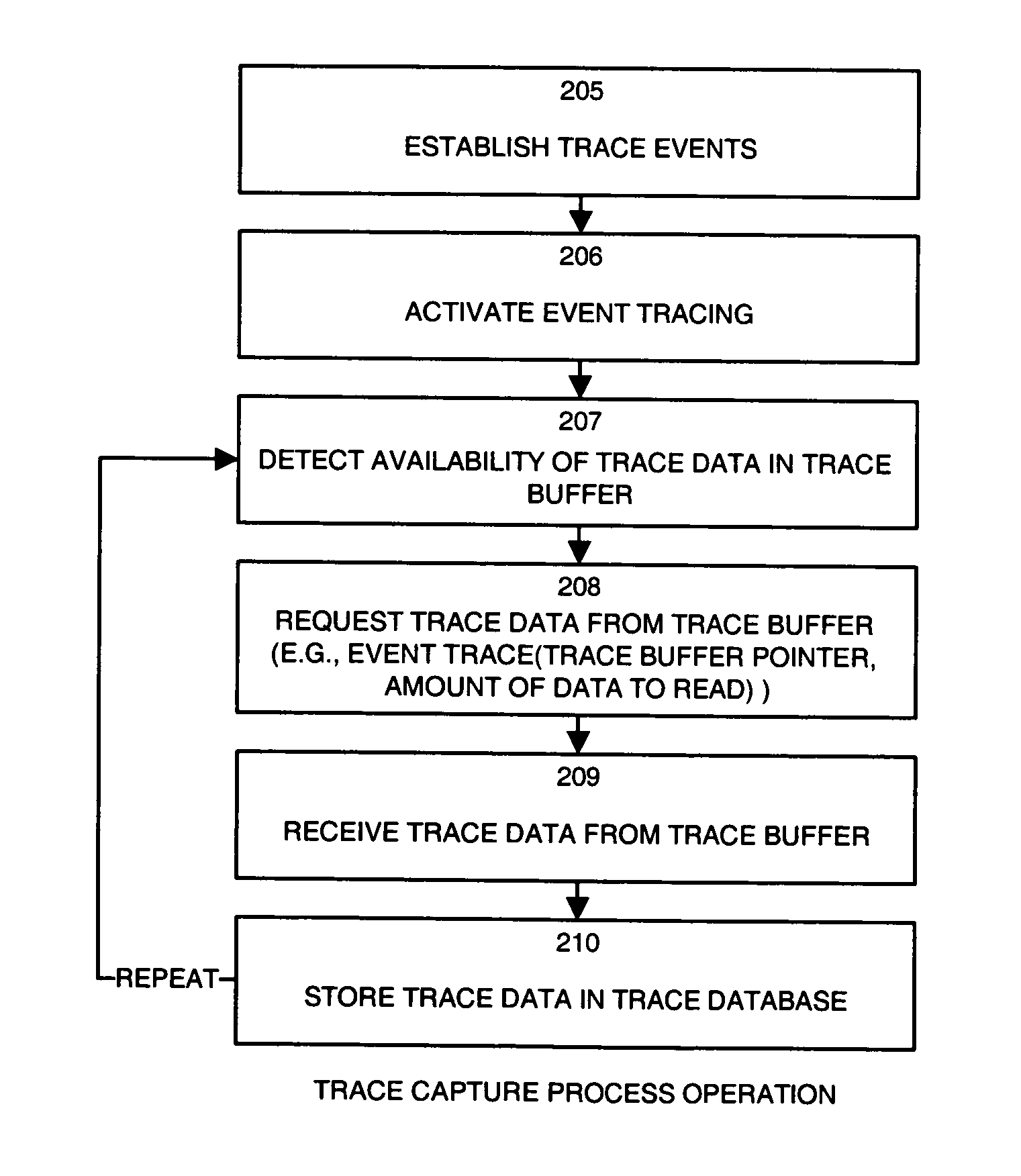
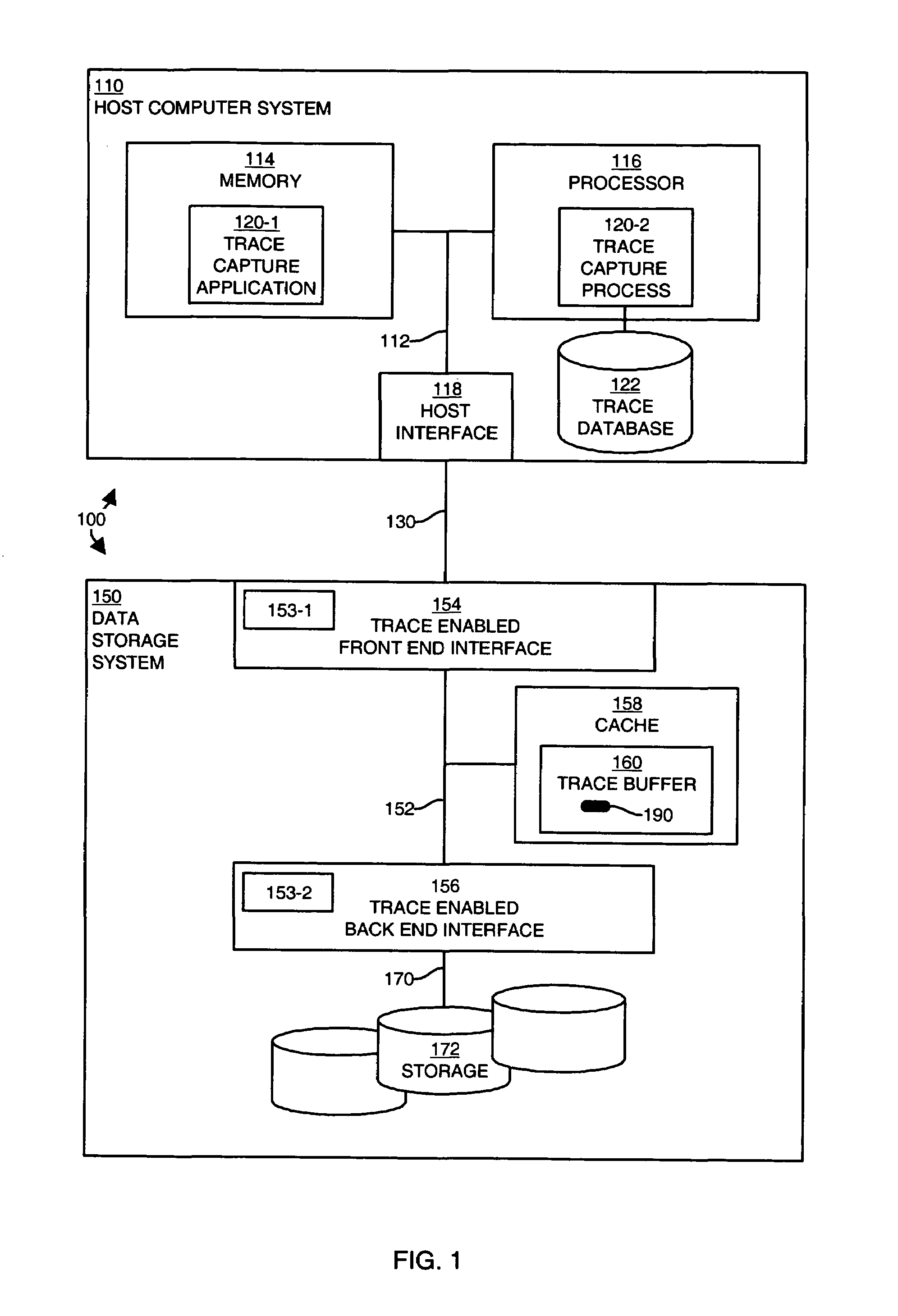
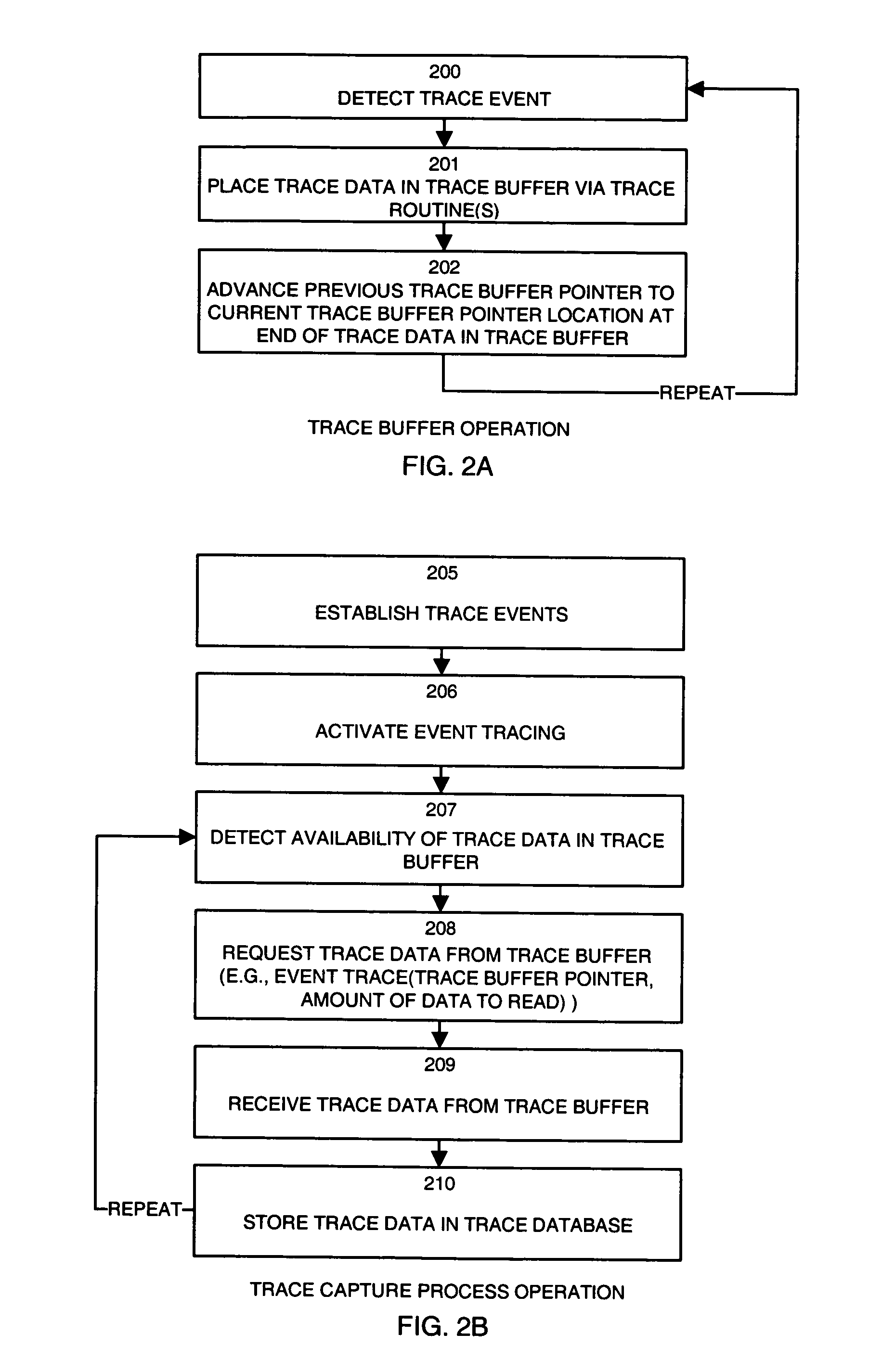
InactiveUS7260692B1Reduce in quantityOvercome deficienciesHardware monitoringSoftware testing/debuggingData accessSystem call
A system provides mechanisms and techniques to retrieve trace data from a trace buffer residing in a data storage system. The software program operating on a processor within the data storage system operates in trace mode to produce trace data in the trace buffer upon occurrence of trace events. An event trace routine operates in response to a system call to access the trace buffer and return either a current value of a trace buffer pointer or the current trace buffer pointer as well as trace data read from the trace buffer beginning at a location and in an amount as specified in the system call to the event trace routine. The trace capture process can operate either within the data storage system or preferably on a remote host computer system to access trace data in the trace buffer in the data storage system by using the event trace routine. The trace capture process can periodically query the event trace routine with a frequency determined by an adaptive timing algorithm in order to detect the addition of trace data to the trace buffer. Upon detecting such a condition, the trace capture process can use the event trace routine to retrieve the trace data from the trace buffer. The trace capture process can also detect if trace data is written beyond the end of the trace buffer and can perform the proper sequence of trace data access operations using the event trace routine in order to provide continuous remote access to all trace data produced in the trace buffer.
Owner:EMC IP HLDG CO LLC
Visual real-time monitoring operation and maintenance method and device of distributed system
ActiveCN107729214AEasy to understandQuick analysisHardware monitoringOperational systemData information
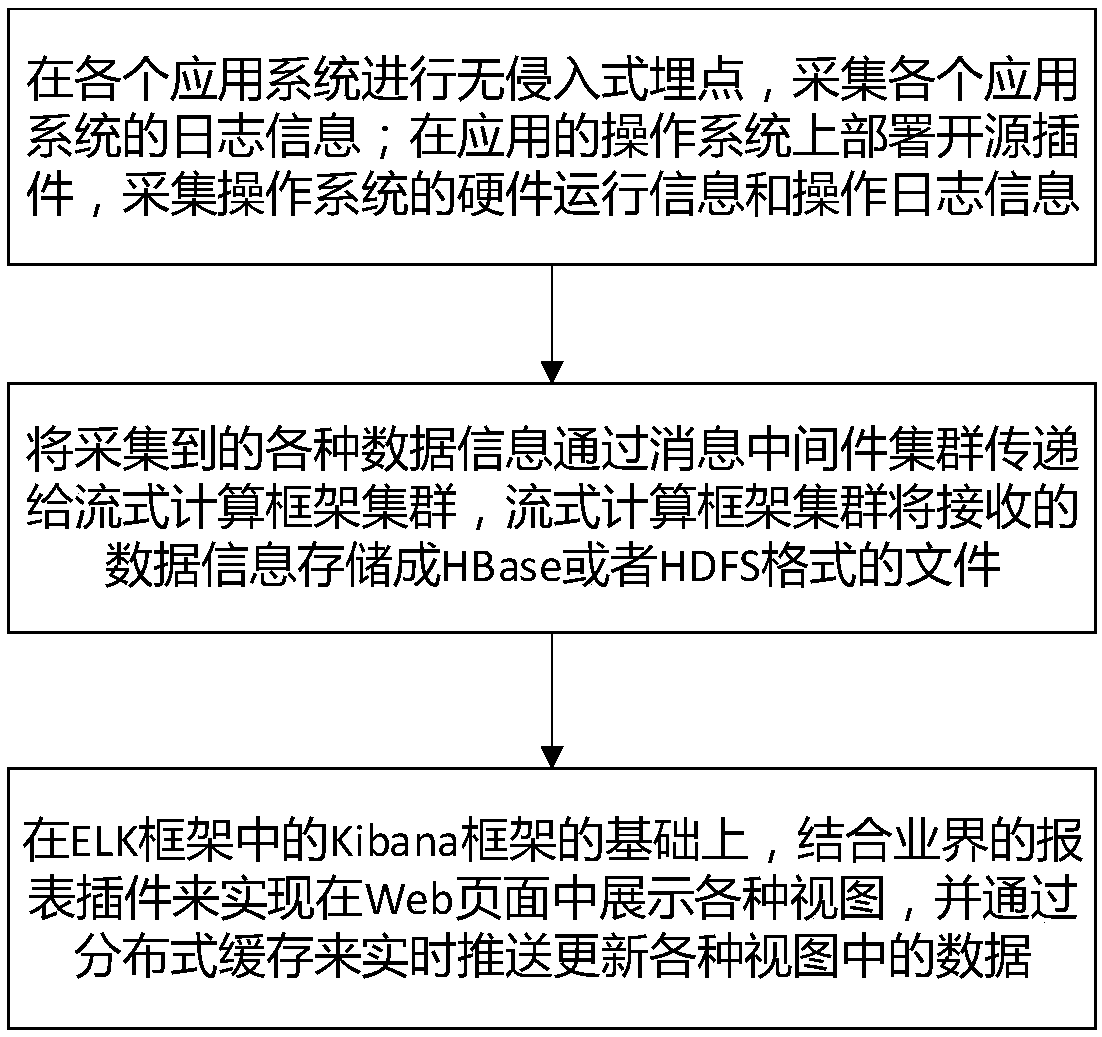
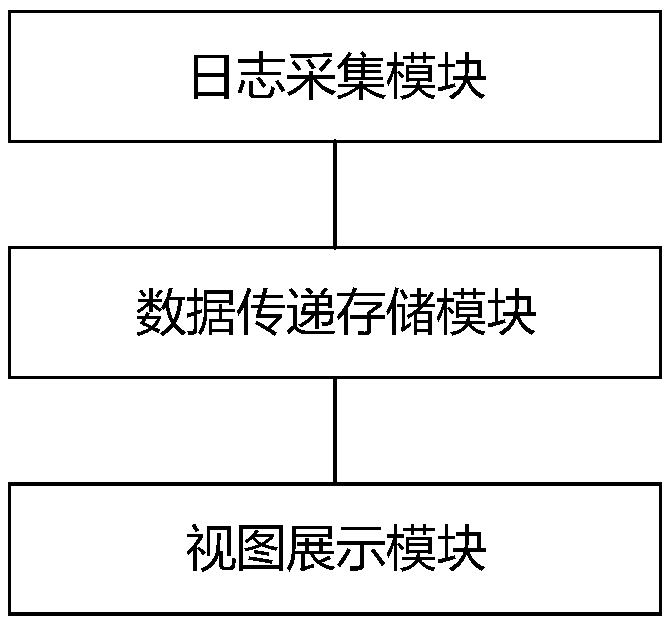
The invention provides a visual real-time monitoring operation and maintenance method of a distributed system. The method comprises the steps that noninvasive event tracking is conducted in each application system, and log information of each application system is collected; open-source plug-ins are deployed on an operating system of applications, and hardware running information and operation loginformation of the operating system are collected; the collected various data information is transmitted to a stream-oriented computation framework cluster through a message-oriented middleware cluster, and the stream-oriented computation framework cluster stores the received data information into a file in an HBase or HDFS format; based on a Kibana framework in an ELK framework, it is achieved that various views are displayed in a Web page with the combination of report plug-ins in the industry, and data in the views is pushed and updated in real time through distributed caches. The visual real-time monitoring operation and maintenance method has the advantages that the operation and maintenance difficulty of the distributed system is greatly reduced, the operation and maintenance efficiency of a distributed application is improved, and a strong guarantee is provided for construction, deployment, operation, maintenance, upgrading, reconstruction and other processes of the system.
Owner:中电福富信息科技有限公司
User behavior data collection system based on mobile phone APP and control method thereof
PendingCN106933472AIncrease flexibilityTimely data supportInput/output processes for data processingEngineeringData collecting
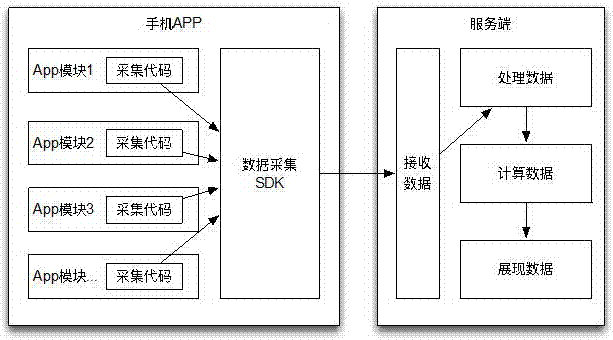
The invention discloses a user behavior data collection system based on a mobile phone APP and a control method thereof. The user behavior data collection system has a remarkable advantage at the aspect of burying point of a mobile phone APP. After the technical scheme free from burying point is utilized, the developer needs not to insert a code in advance for a widget on APP and the developer can perform visual operation on a to-be-tracked widget at a server end and can track a trigger event for an appointed widget after the APP is published. An APP image acquiring technique is utilized to effectively solve different problems of the original code burying point, including difficulty in maintaining after burying point, easiness in making mistake by manually burying point, long waiting time for APP coming into market, and the like, so that the efficiency of user behavior analysis of the APP is greatly increased.
Owner:南京西桥科技有限公司
Event tracking processing method and device, computer device and storage medium
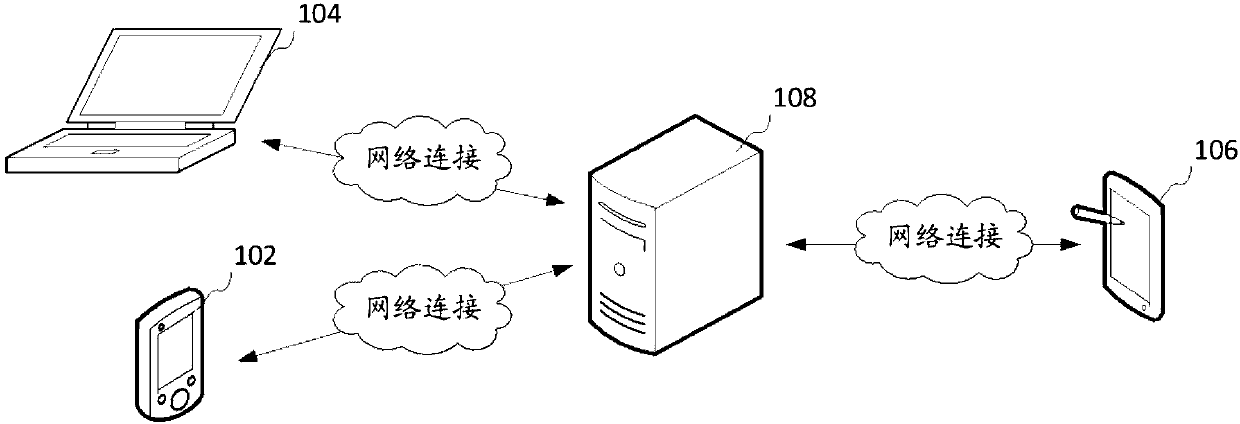
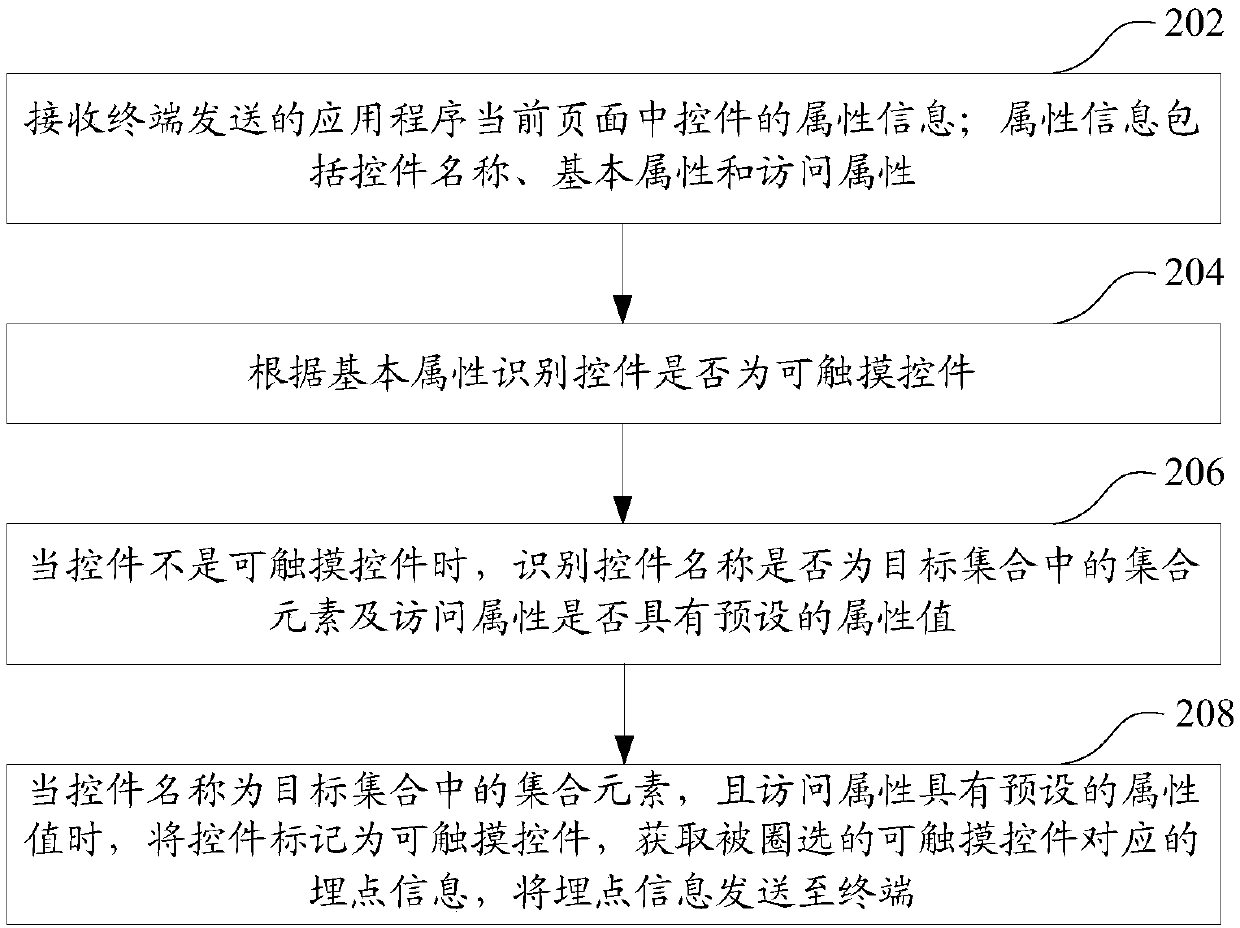
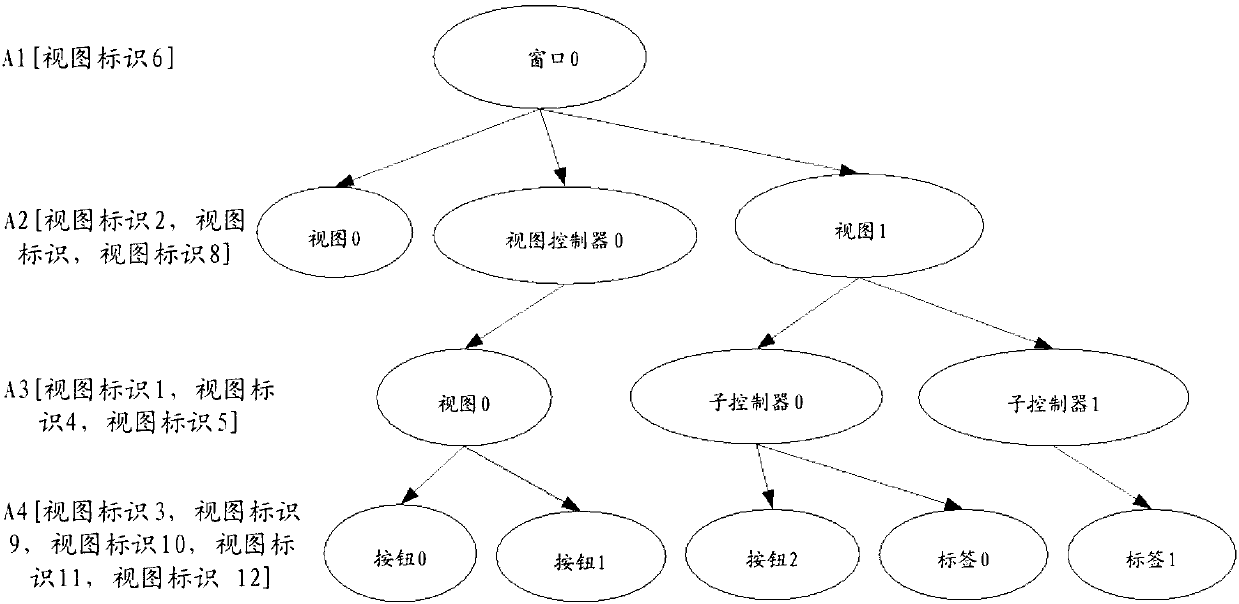
ActiveCN107818162ASpecial data processing applicationsWeb data browsing optimisationApplication softwareEvent tracking
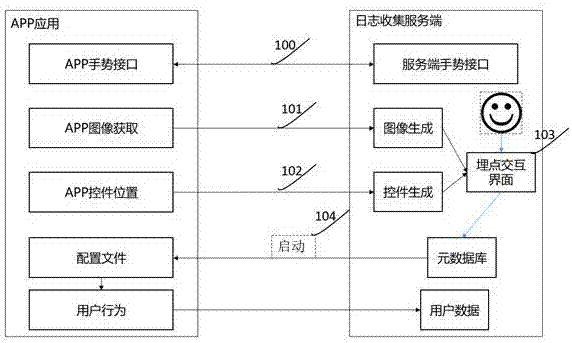
The invention relates to an event tracking processing method and device, a computer device and a storage medium. The method comprises the steps of receiving the attribute information, sent by a terminal, of a control in the current page of an application program, wherein the attribute information comprises the control name, the essential attribute and the accessing attribute; according to the essential attribute, identifying the control is a tangible control or not; when the control is not the tangible control, identifying whether the control name is a set factor in a target set or not and whether the accessing attribute has a preset attribute value or not; when the control name is the set factor in the target set, and the accessing attribute has the preset attribute value, labeling the control as the tangible control, obtaining selected event tracking information corresponding to the tangible control, and sending the event tracking information to the terminal. By means of the event tracking processing method, the precision of identifying the tangible control can be improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
Processor core power event tracing
ActiveUS9910475B2Hardware monitoringPower supply for data processingParallel computingEvent tracking
Owner:INTEL CORP
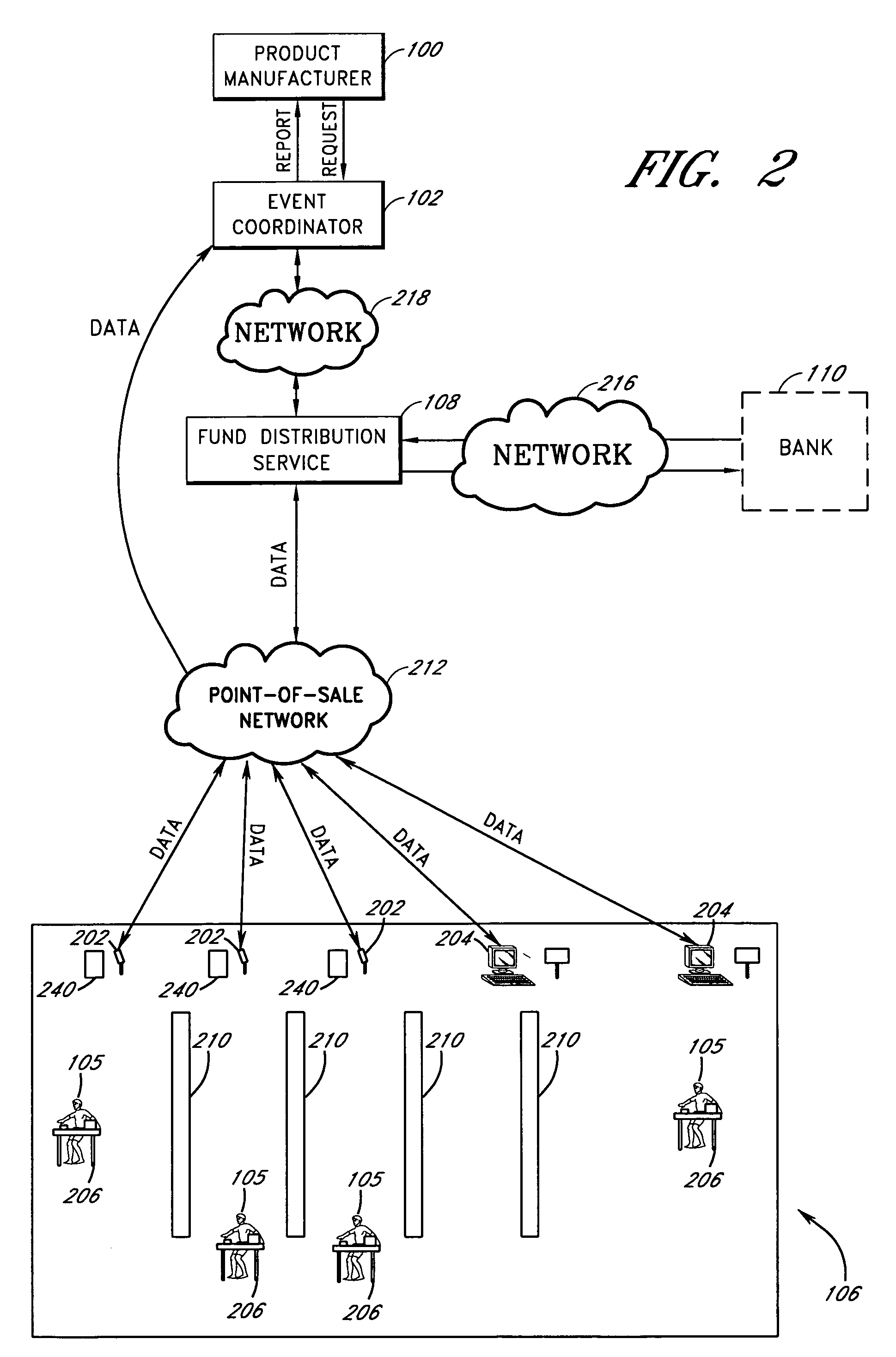
Promotional event tracking system
InactiveUS7797191B2Credit registering devices actuationUser identity/authority verificationTime informationEvent data
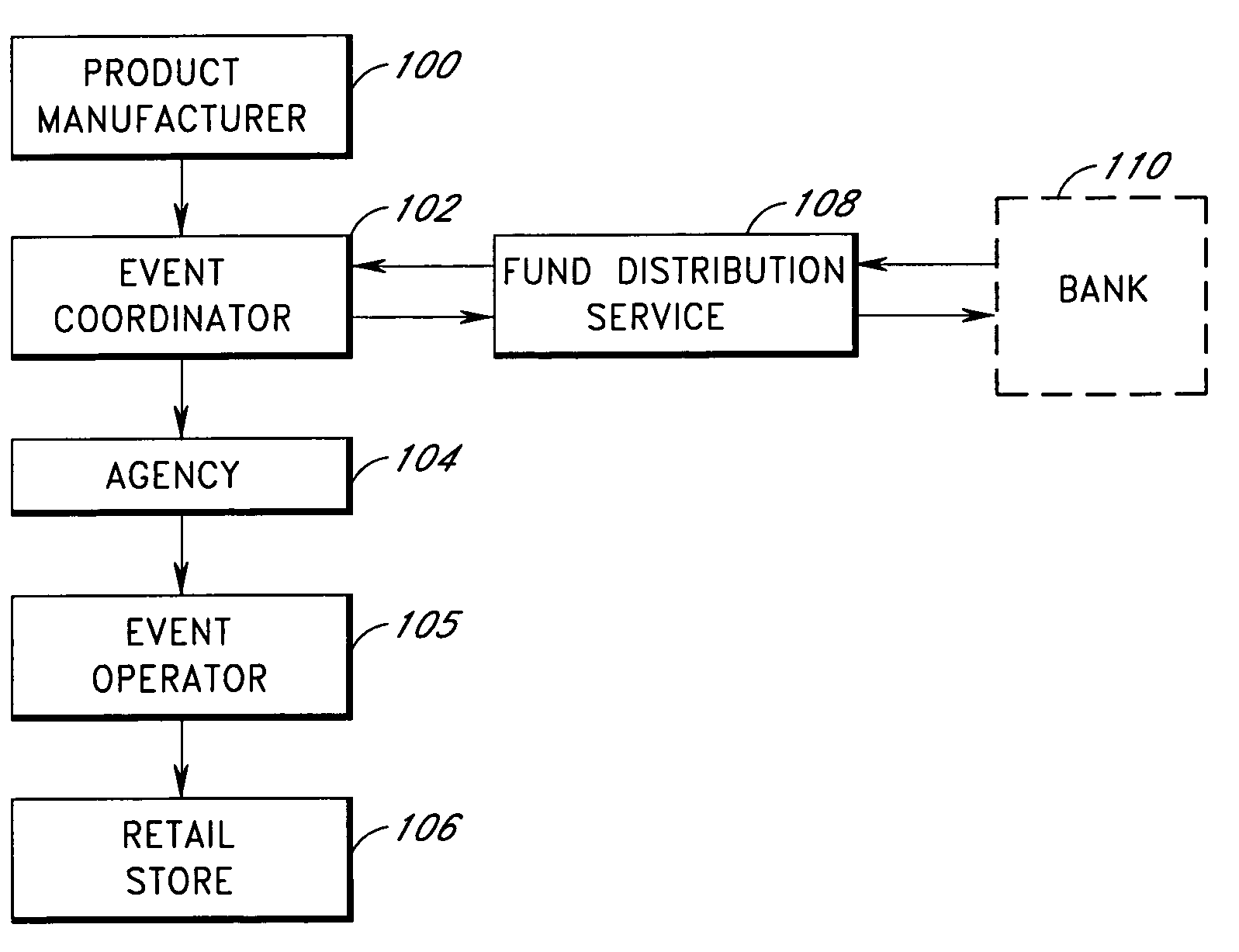
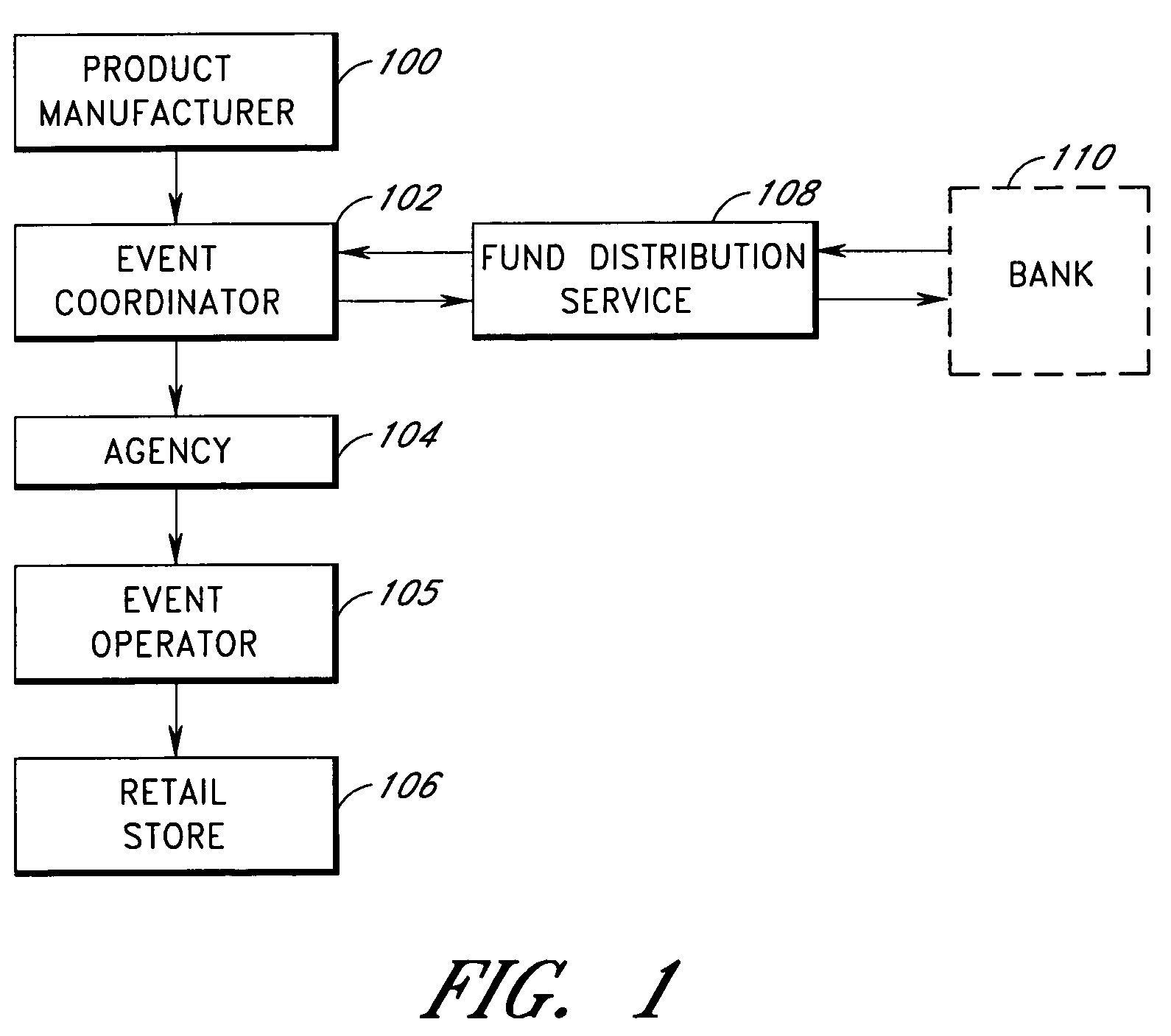
This invention relates to the methods of coordinating and tracking product and service demonstrations. An event coordinator directs event operators to conduct a product or service demonstration event. The event coordinator provides event operators with cards, such as debit cards, credit cards, or smart cards, to purchase items needed for the demonstration. The event operator contacts a card administration system to activate the card. The card administration system verifies that the provided card ID and event ID are valid, and associates an authorized budget of the demonstration event with the card. The event operator then purchases items with the card, and conducts demonstrations. Event data is provided to the parties involved in the demonstration such as a product manufacturer or service provider, the event coordinator, a staffing agency, the event operator, and a retail store. The event data includes, for example, items purchased for demonstration using the card, items purchased by customers during the demonstrations, and time information.
Owner:CYNTHIA COOK INC
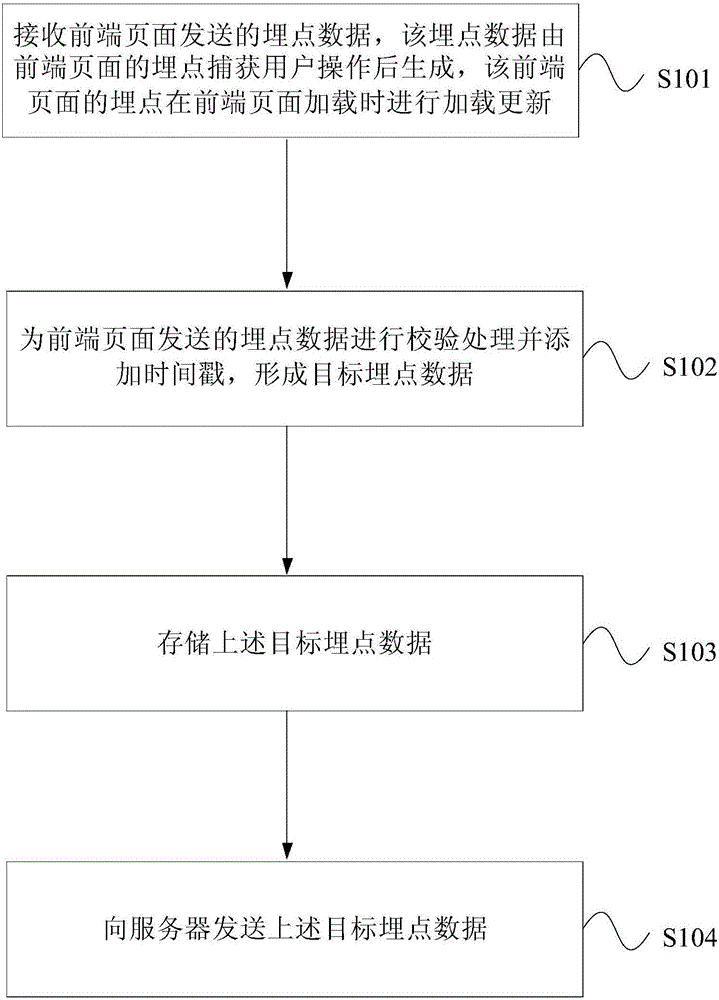
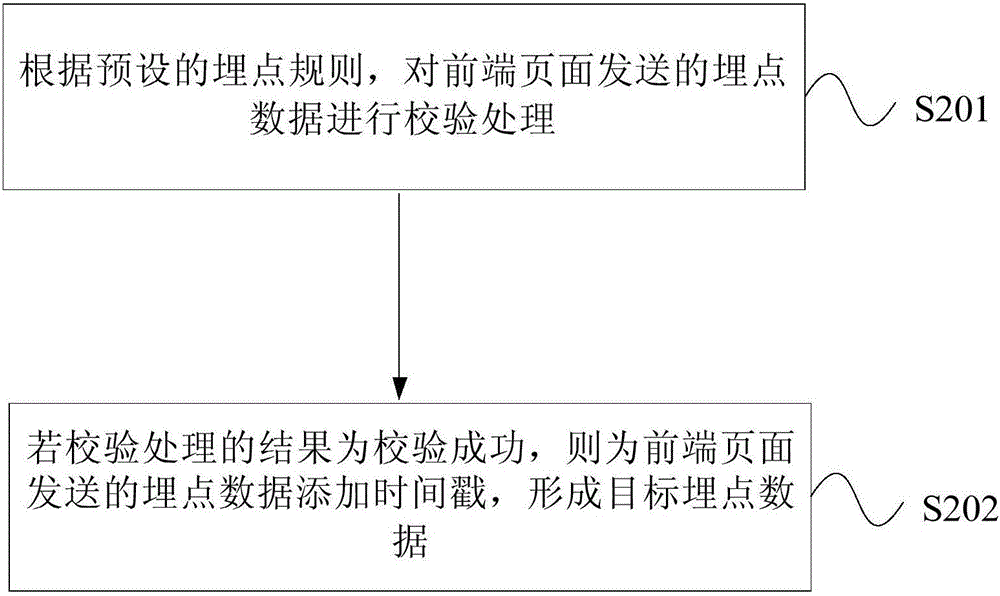
Event tracking point processing method and apparatus
The invention provides an event tracking point processing method and apparatus. The method comprises the steps of: receiving event tracking point data transmitted from a front-end page, wherein the event tracking point data is generated by an event tracking point in the front-end page and capturing a user operation, and the event tracking point in the front-end page updates the loading when the front-end page is loaded; verifying the event tracking point data transmitted from the front-end page and adding a timestamp to the event tracking point data transmitted from the front-end page to form the target event tracking point data; storing the target event tracking point data; sending the target event tracking point data to a server. According to the method and apparatus, the event tracking point is disposed in the front-end page, a corresponding code is downloaded from the server when the front-end page is loaded, and when the event tracking point is modified, the dynamic deployment of the event tracking point can be achieved by loading the front-end page.
Owner:BEIJING 58 INFORMATION TTECH CO LTD
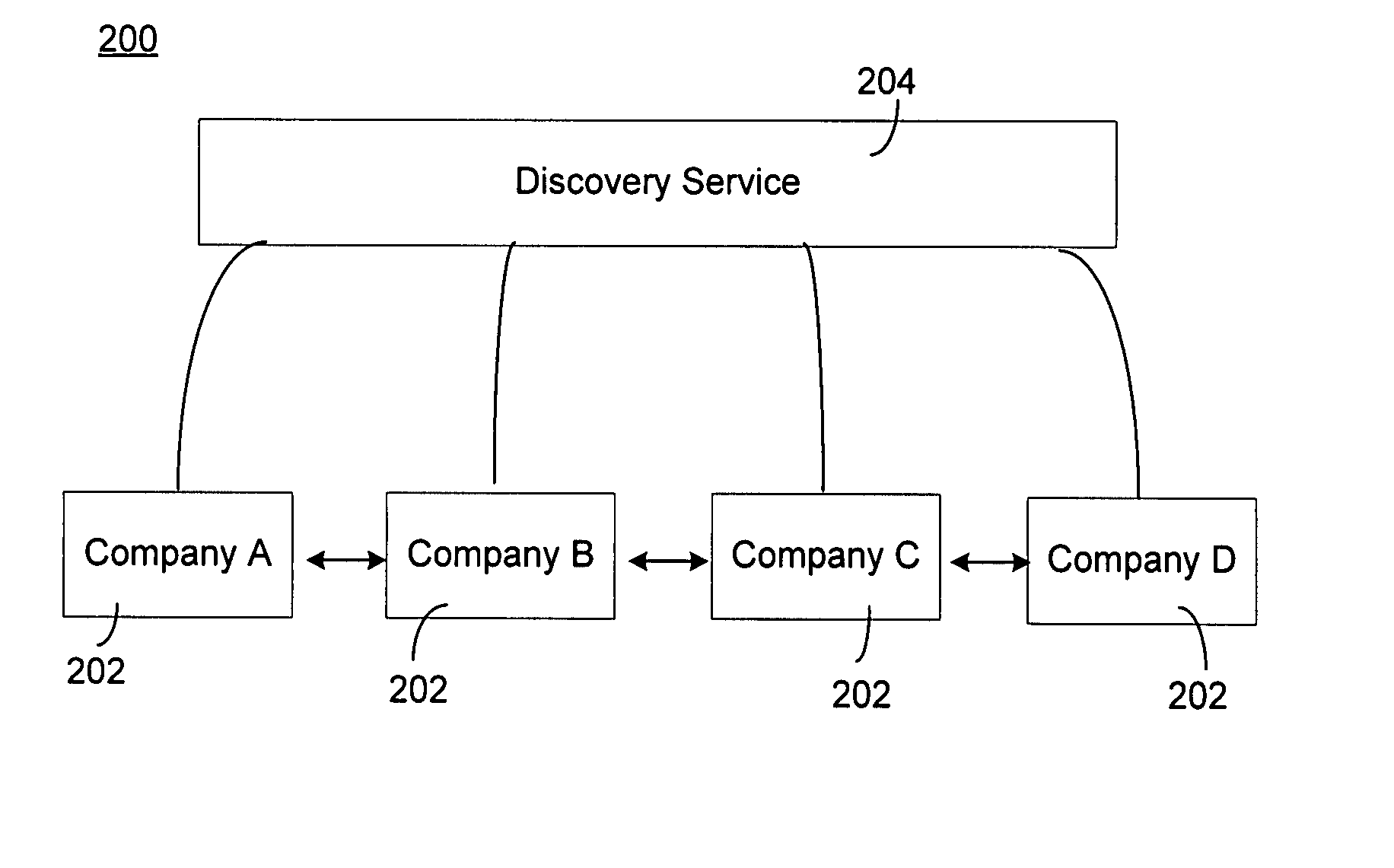
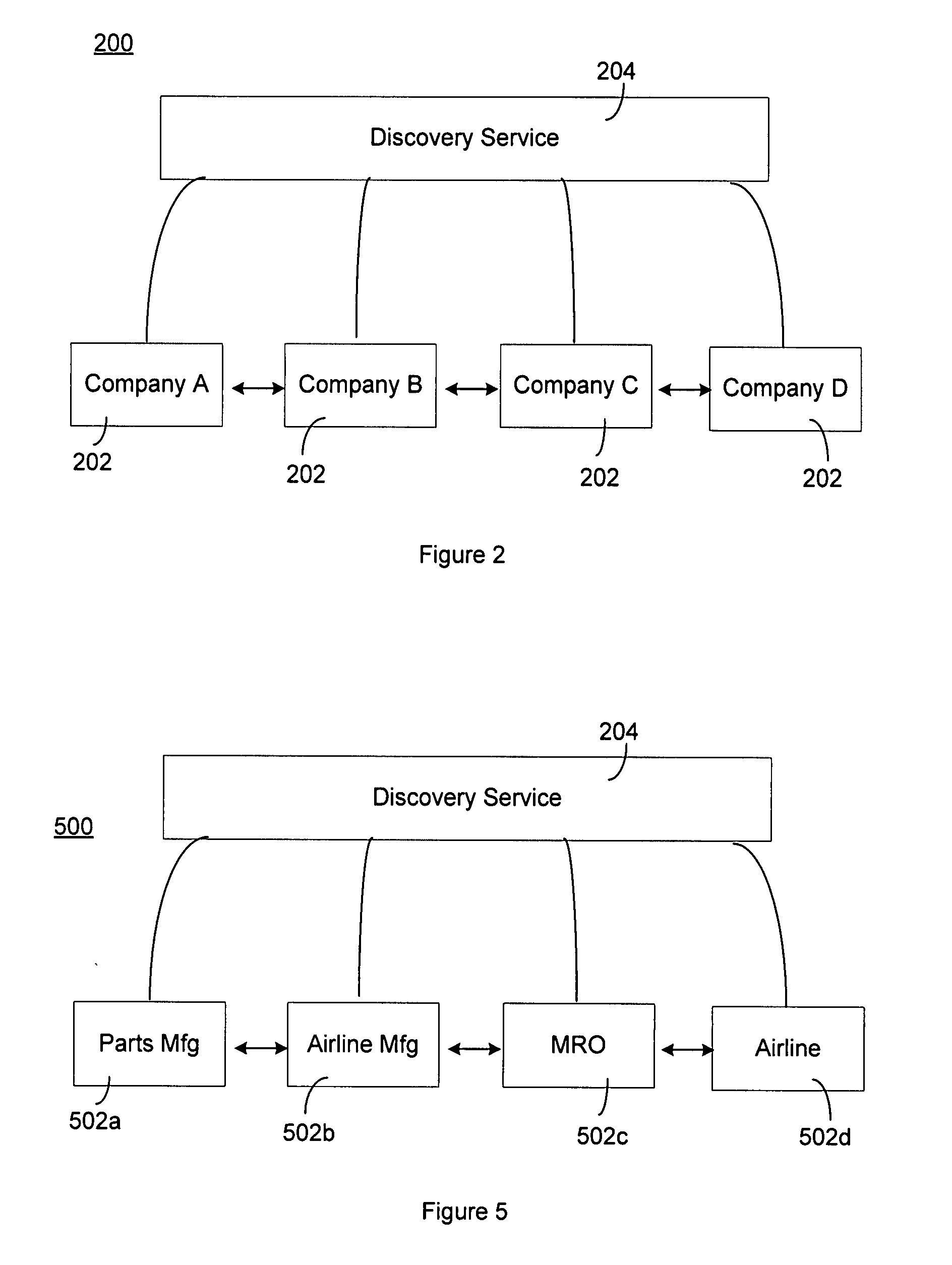
Supply Chain Discovery Services
ActiveUS20080109411A1Multiple digital computer combinationsLogisticsCommunication interfaceMultiple Partners
A discovery server is provided for tracking an object in a supply chain in accordance with a plurality of predefined events. The object is identifiable by an object identifier. The discovery server comprises the following elements. A communication interface is configured to communicate with each of a plurality of partners in the supply chain using a predefined protocol. A data store is configured to store events for the object, the events being received from the plurality of partners. Each event stored in the data store an object identifier, a life cycle step, a partner identifier and an timing identifier. Also, a processor is configured to search the data store in response to an inquiry regarding the object.
Owner:AFILIAS LTD
Merchant powered click-to-call method
InactiveUS20110310891A1Enhancing predictability and scalability and cost-effectivenessFinanceAdvertisementsOnline advertisingVoice over IP
A method is disclosed for enhancing the predictability, scalability and cost effectiveness of online advertising with voice over IP connectivity and event tracking technologies. A service provider maintains a list of merchants who have offered to pay for customer VoIP calls to their establishment. The service provider maintains a real time connection with this merchant list and renders an advertisement in a distinguishing way in real time. A potential customer who views this advertisement on a web page may establish a VoIP call session with a merchant by selecting a free click-to-call link on the web page. When the customer places the call, the service provider pays for the call. Merchants in turn pay the service provider for displaying the ads that generated the calls on a price per call, price per impression or fixed fee basis.
Owner:MICROSOFT TECH LICENSING LLC
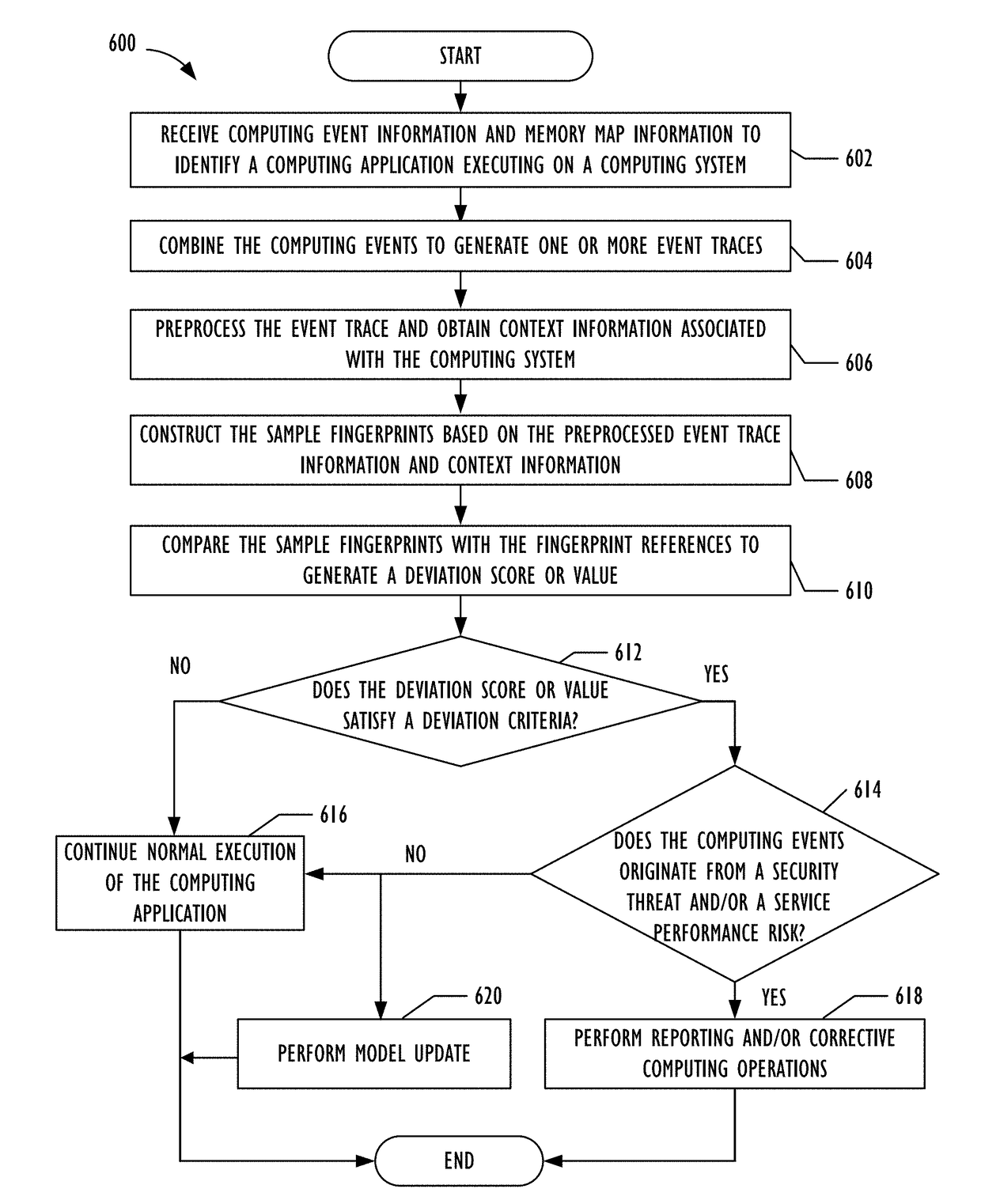
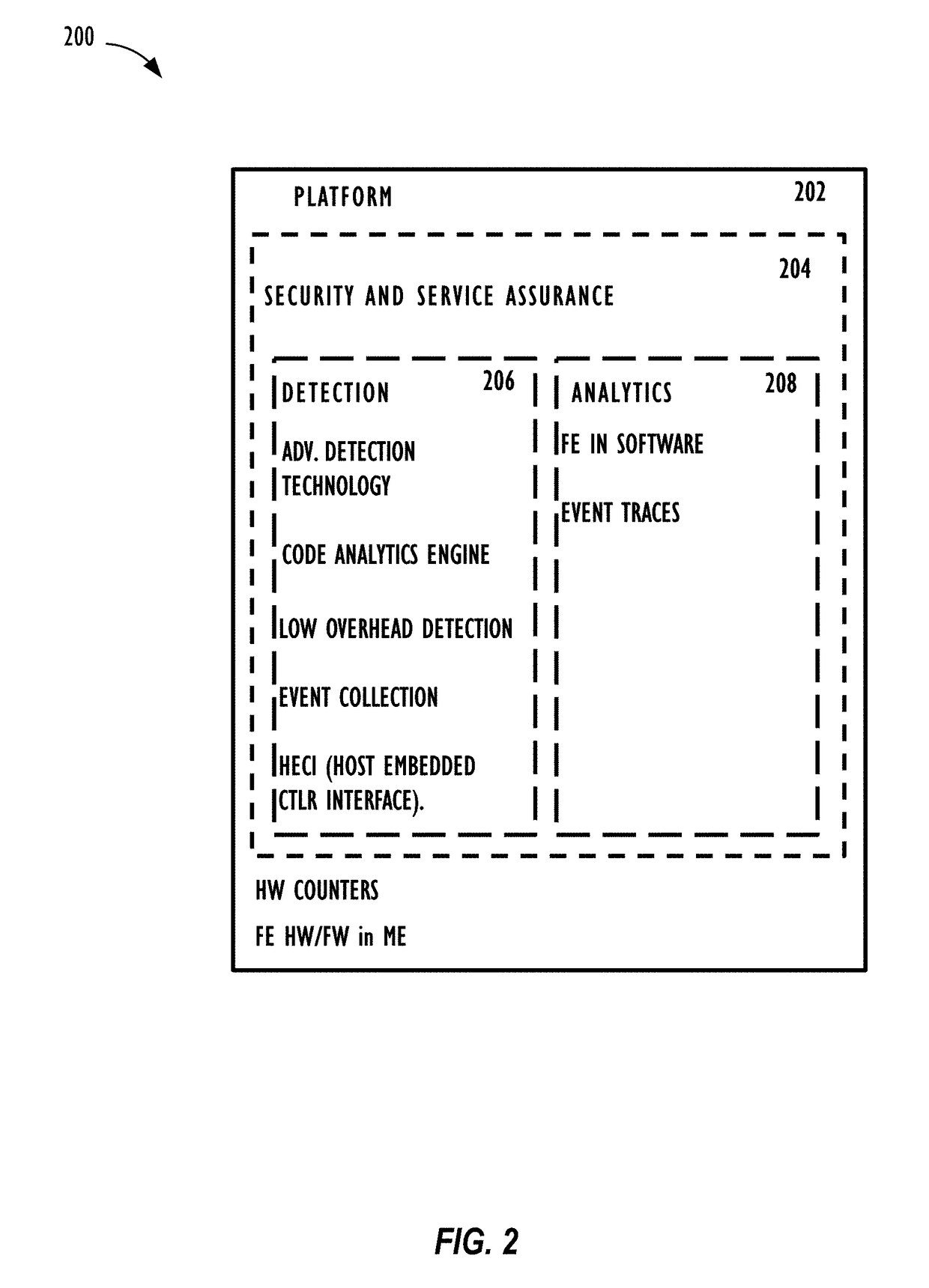
Service Assurance and Security of Computing Systems Using Fingerprinting
Providing detection of computing application malfunctions by performing at least the following: collecting a plurality of computing events that correspond to a computing application and a plurality of addresses associated with the plurality of computing events, generating an event trace that comprises the plurality of computing events and the plurality of addresses, constructing at least one sample fingerprint that represents a current behavior of the computing application using at least the event trace, comparing the at least one sample fingerprint with a behavior model that represents an expected operation of the computing application; and determining whether the computing application is malfunctioning based upon the comparison of the at least one sample fingerprint and the behavioral model.
Owner:MCAFEE LLC
Client complaint early-warning monitoring analyzing method based on text mining technology
The invention discloses a client complaint early-warning monitoring analyzing method based on text mining technology. The method comprises the steps of a text data standardizing step for converting recorded text data into data with a standard data format in a unified rule; and a standard data analysis early-warning step, analyzing the standard data format through establishing a complaint analysis grade clustering model, determining a risk grade according to the clustering result, and transmitting early-warning according to the risk grade. The complaint early-warning monitoring analyzing method satisfies a precondition of ensuring client satisfaction degree and furthermore has advantages of greatly reducing workload in manual sampling observation, effectively improving passive after-event tracking responsibility-determining management mode and facilitating before-event active server in a targeted manner, thereby realizing a professional management requirement for in-time response for client demands.
Owner:JIANGSU ELECTRIC POWER CO +2
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com