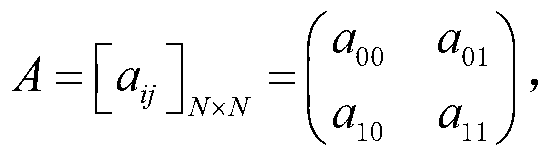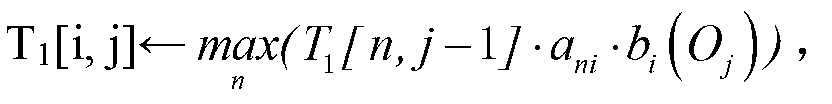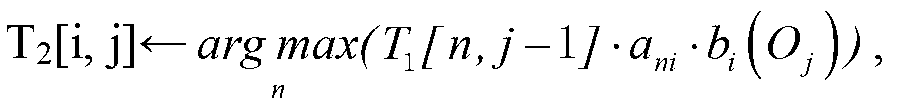Patents
Literature
50 results about "Event tracing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
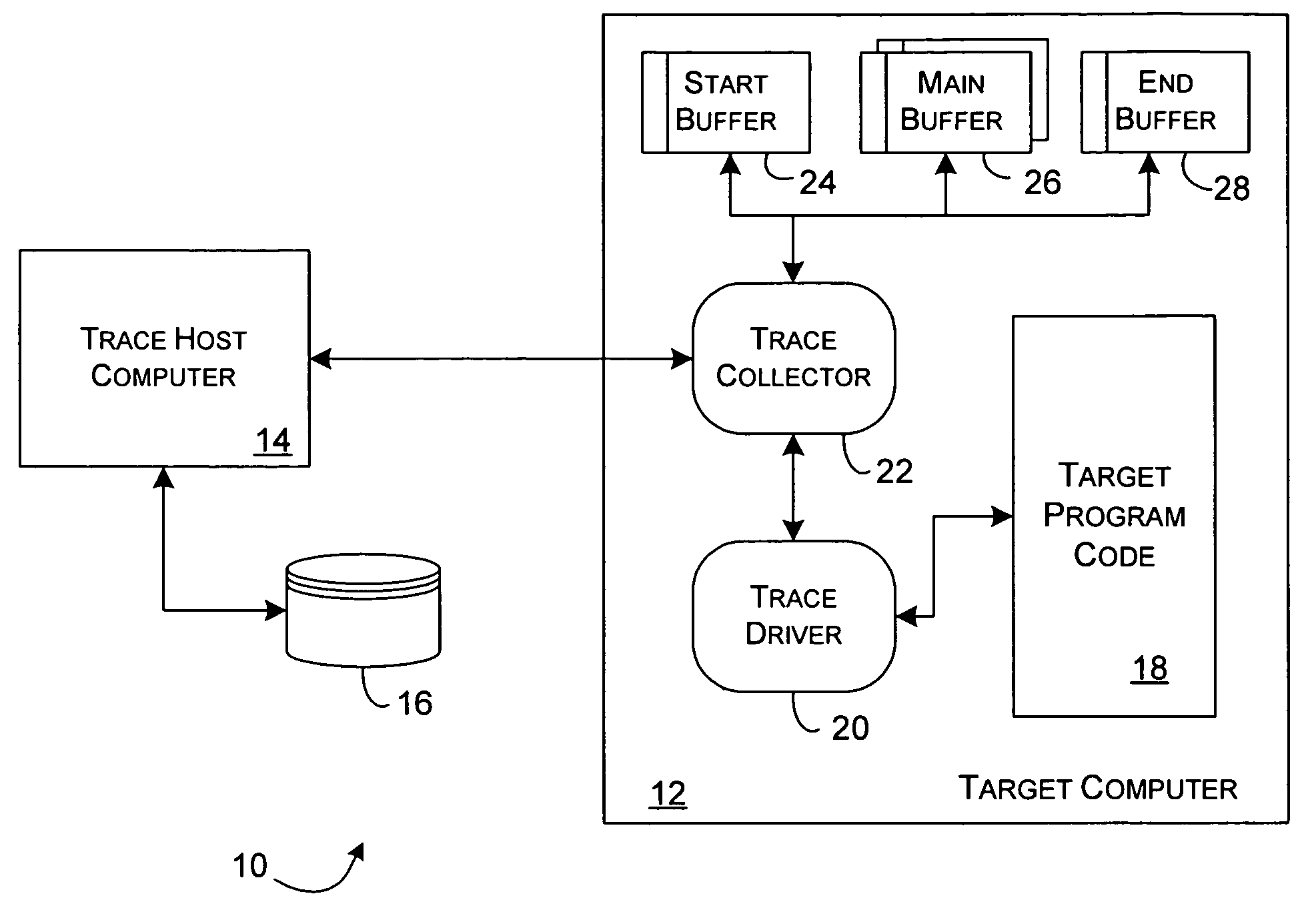
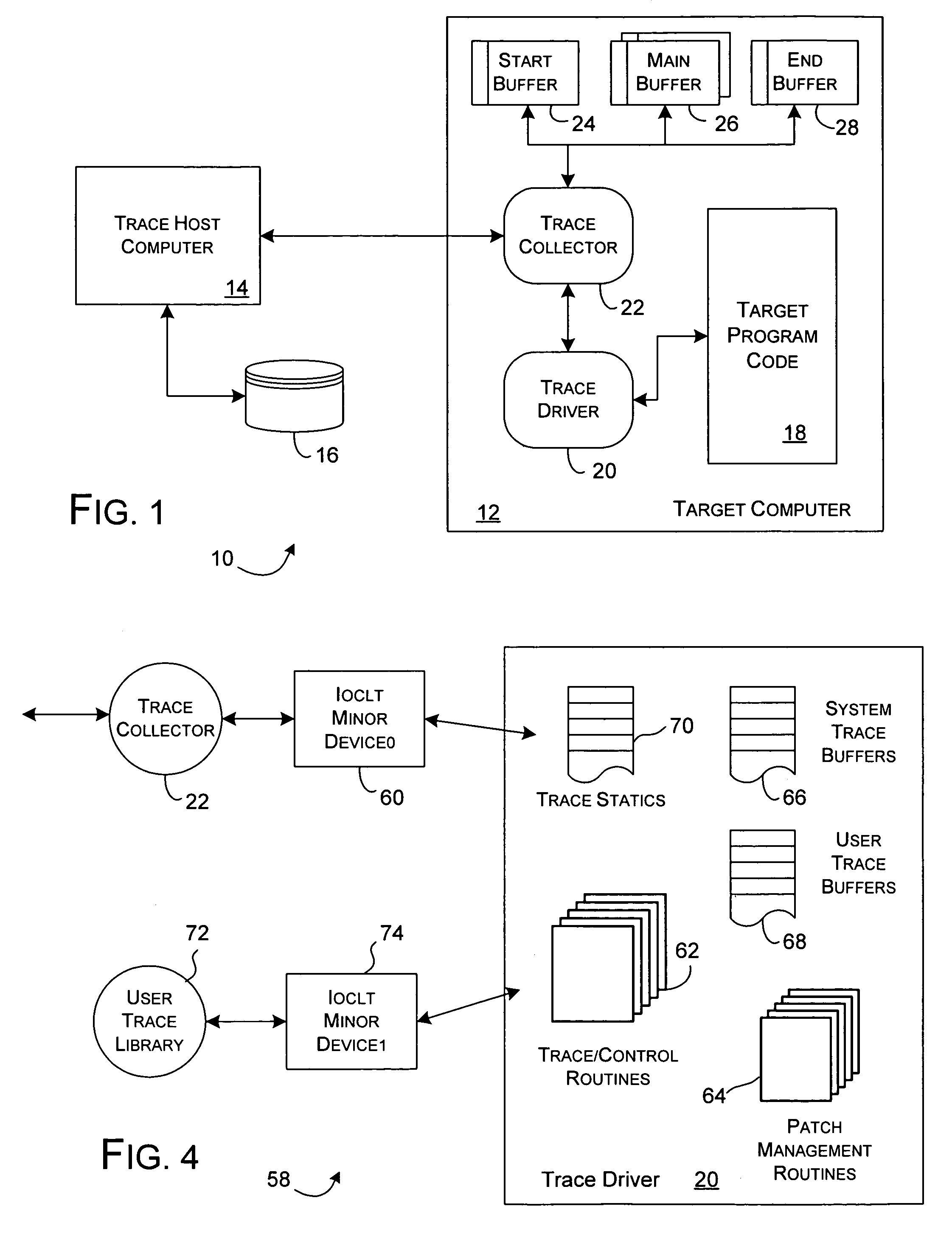
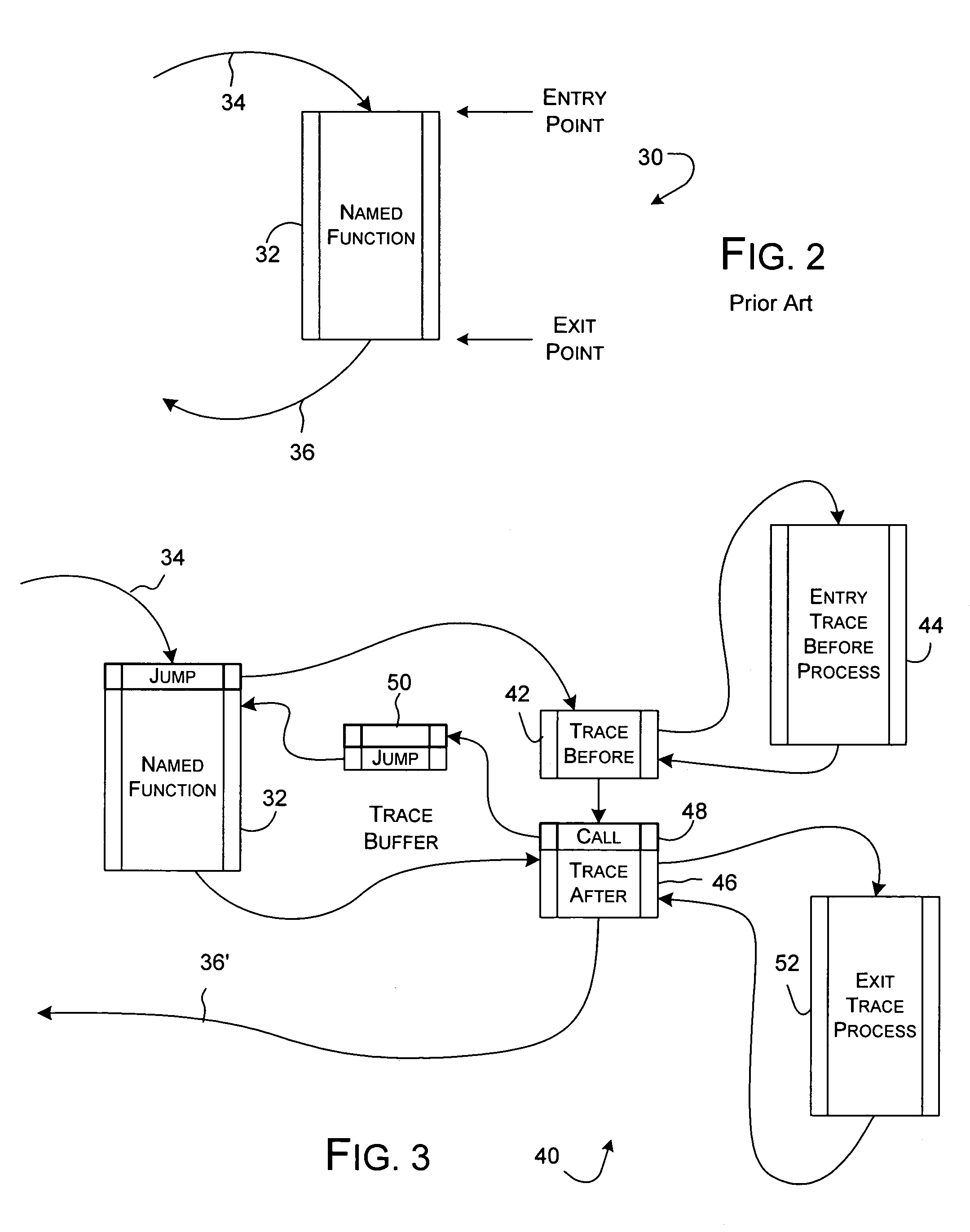
Dynamic instrumentation event trace system and methods
InactiveUS7047521B2Performance impact is minimalMaximize discriminating detectionHardware monitoringSoftware testing/debuggingDynamic instrumentationParallel computing
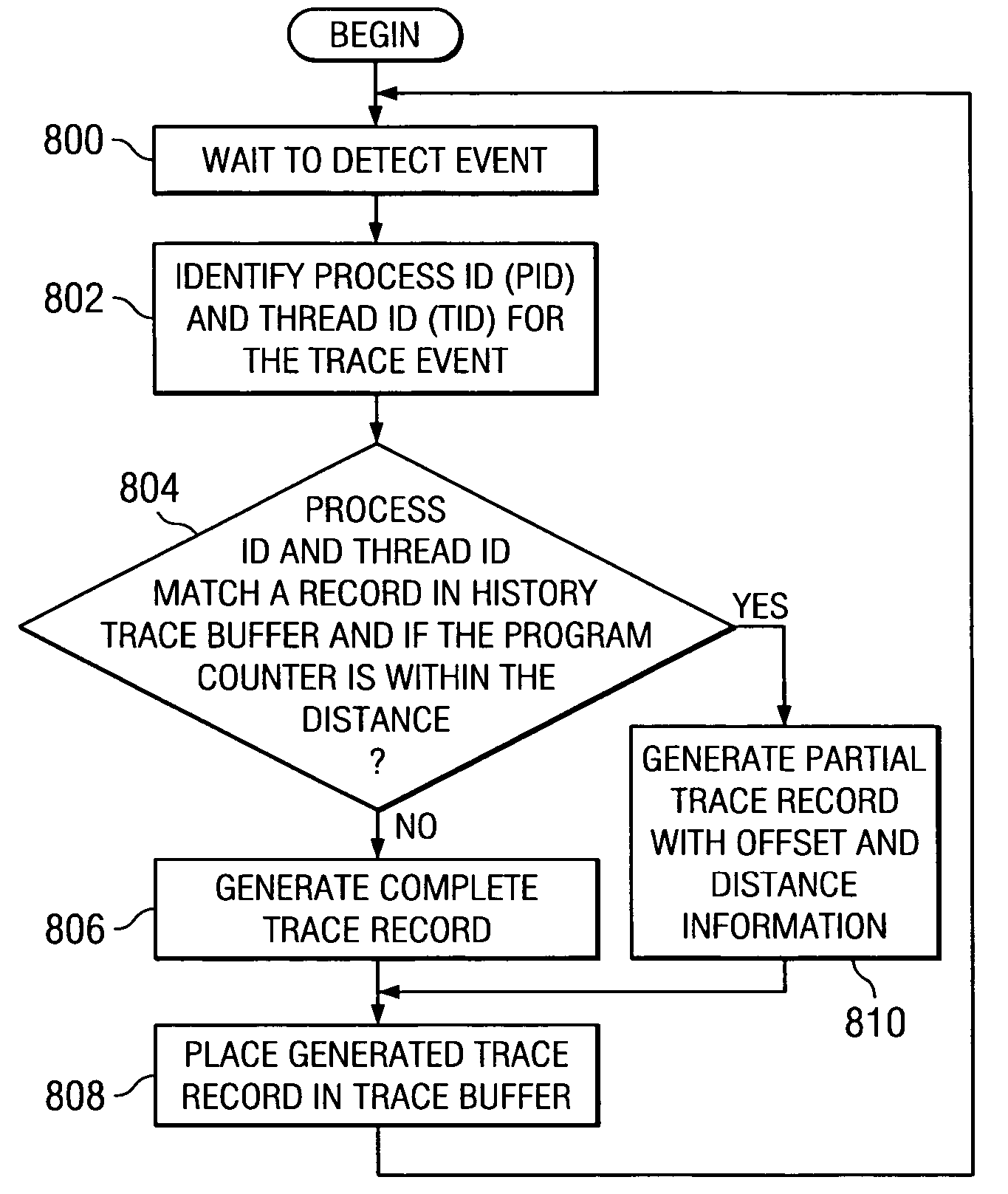
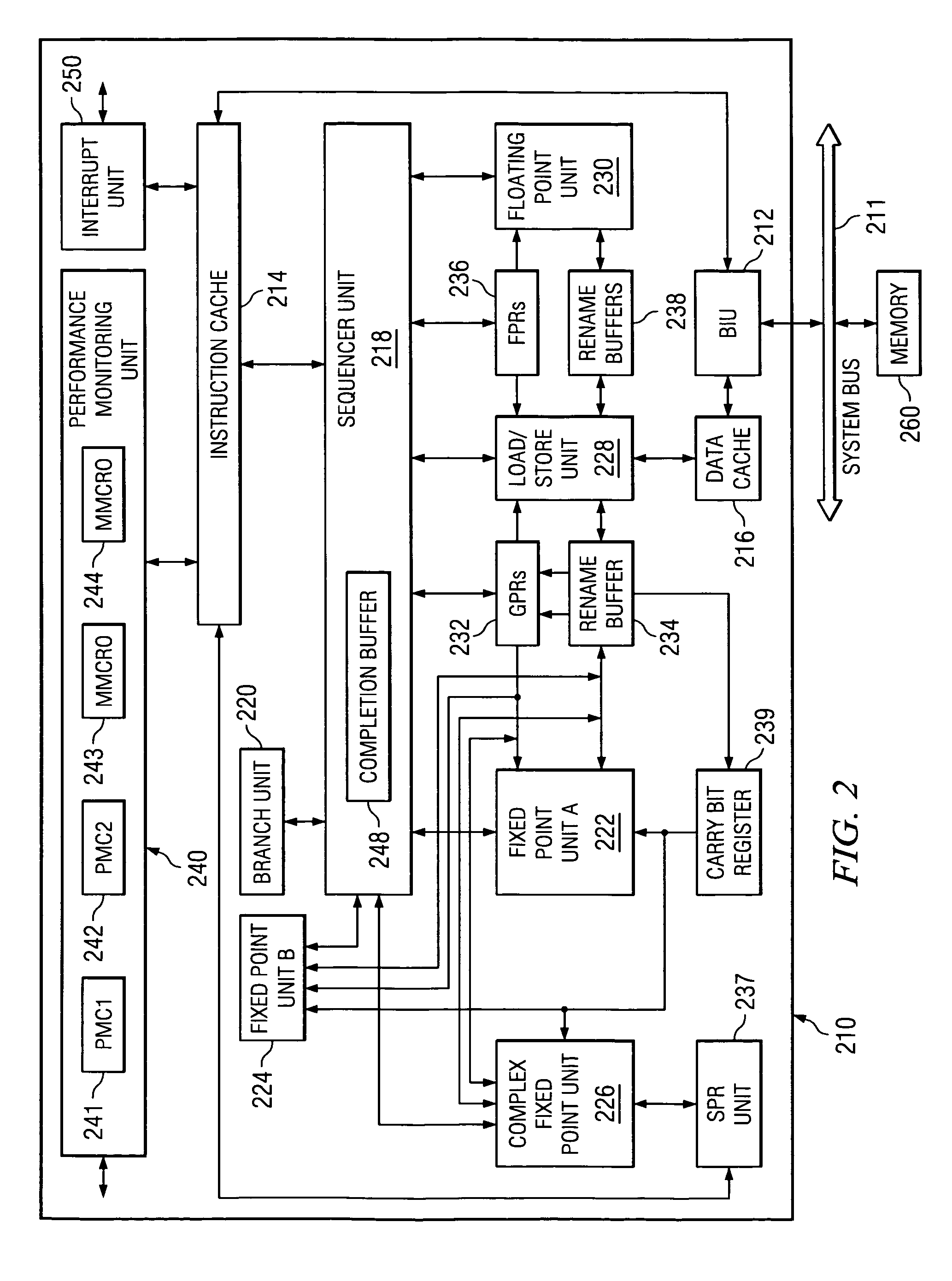
Program code loaded for execution by a computer can be dynamically instrumented to collect event data by inserting an instruction at a trace point within the program code as loaded in a memory space of a computer, where the trace point corresponds to the beginning of a predefined function of the program selected for event tracing. The instruction provides for the direction of the execution of said computer to a function proxy routine, which includes a call to an instance of the predefined function. Event data is collected in connection with the calling of the instance of the predefined function.
Owner:LYNX SOFTWARE TECH
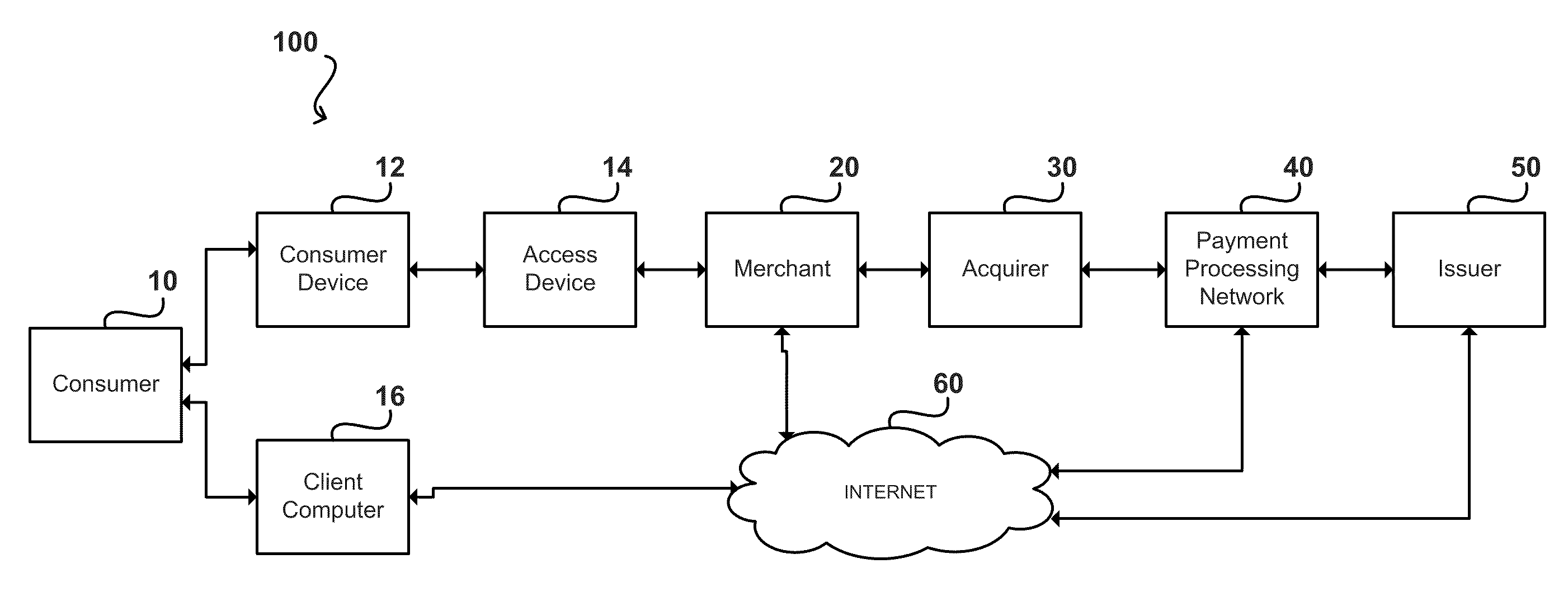
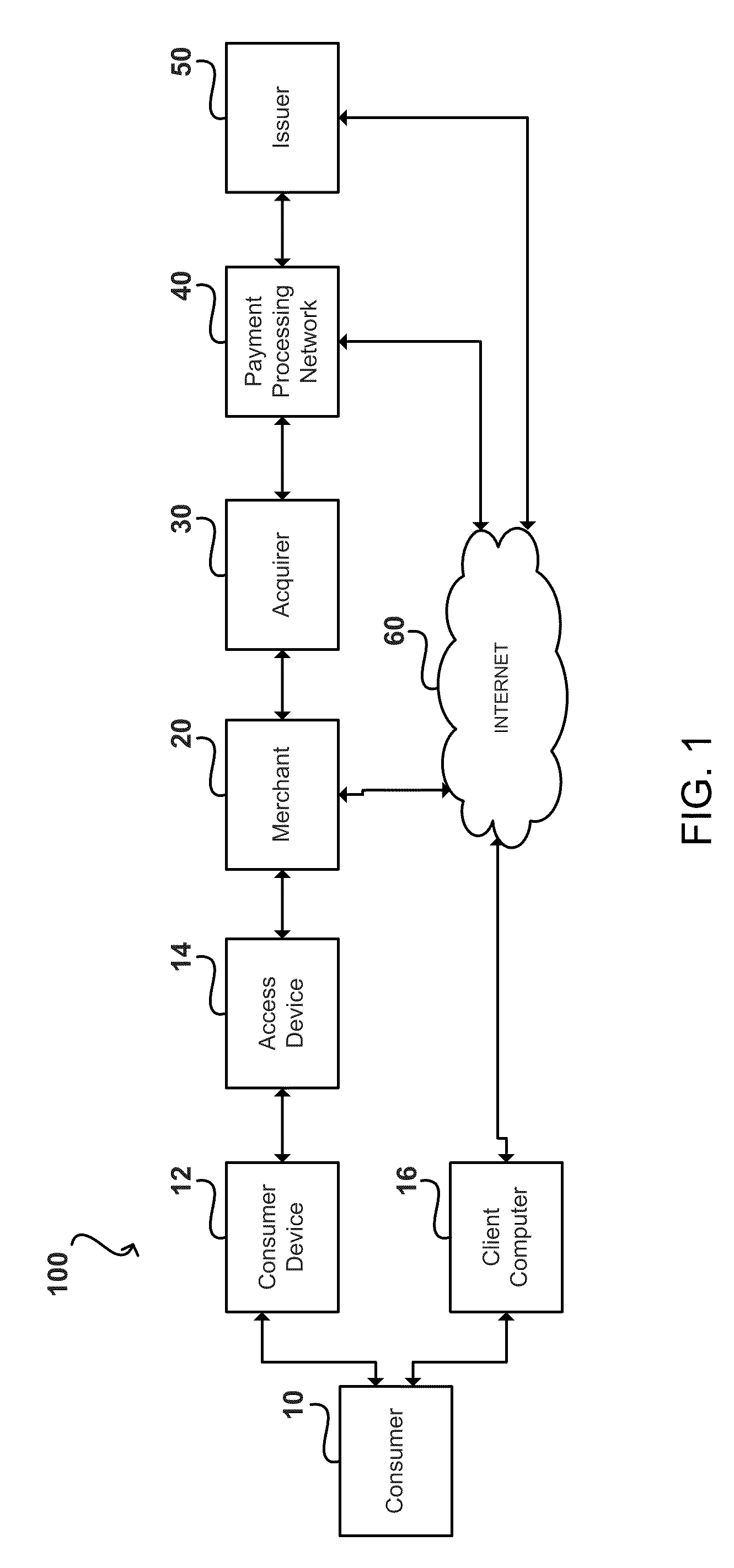
Event Tracking and Velocity Fraud Rules for Financial Transactions
InactiveUS20110016052A1Reducing third-party processing feeReduce processing timeFinanceProtocol authorisationThird partyFiltering rules
A fraud rule can be applied to a transaction according to a first authorization parameter. The transaction is passed to a filtering rule which is applied to the transaction according to a second authorization parameter. The filtering rule can approve the transaction for processing or pass the transaction on to a third party analysis. The fraud and filtering rules can apply the same analysis to the transaction with the exception of the authorization parameters. The fraud rule and filtering rules can analyze historical attributes of a consumer account.
Owner:VISA INT SERVICE ASSOC
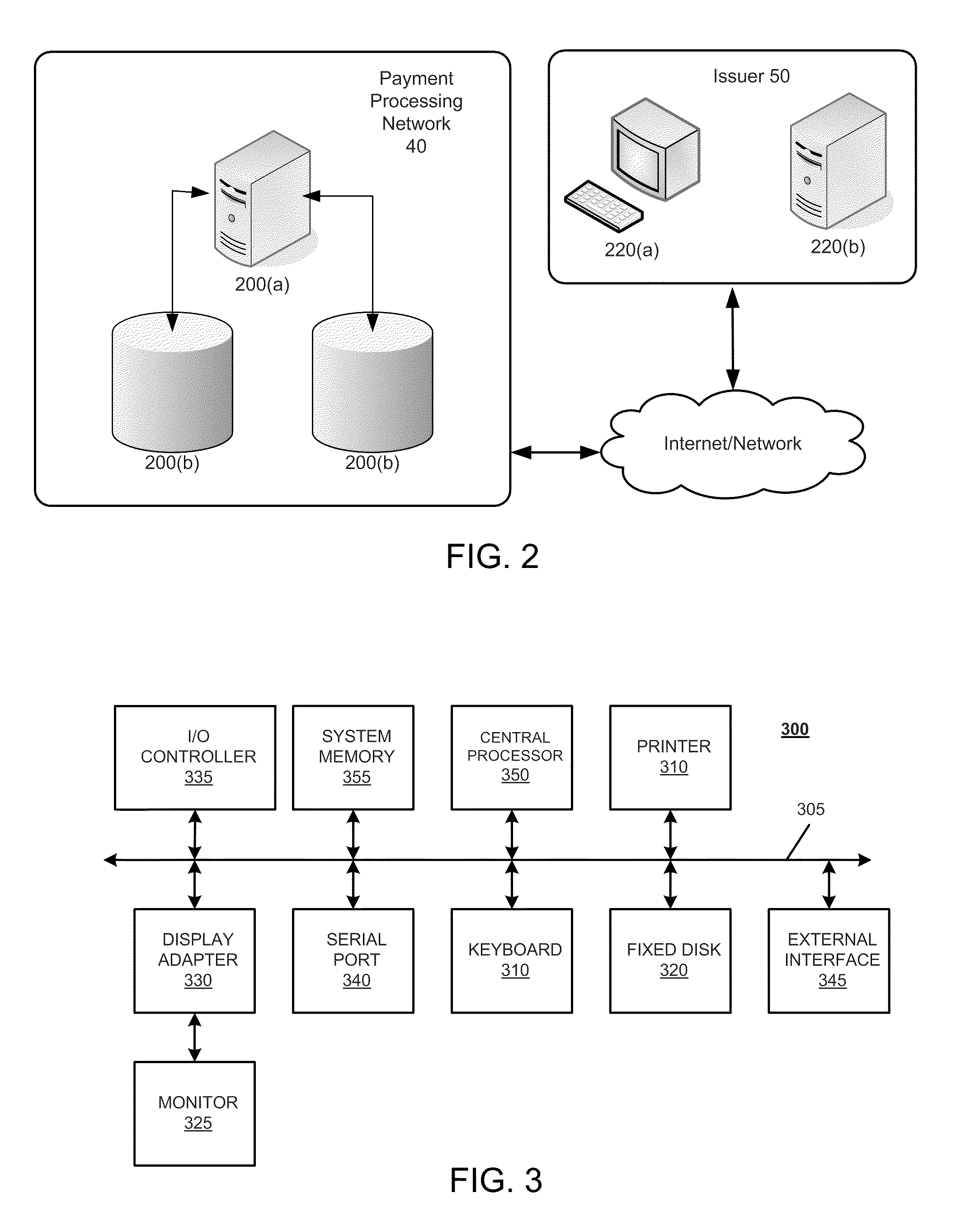
Processor core power event tracing
ActiveUS9910475B2Hardware monitoringPower supply for data processingParallel computingEvent tracking
Owner:INTEL CORP
People searching method and system based on face and human body identification
InactiveCN107292240AAvoid detectionAvoid trackingBiometric pattern recognitionHuman bodyFace detection
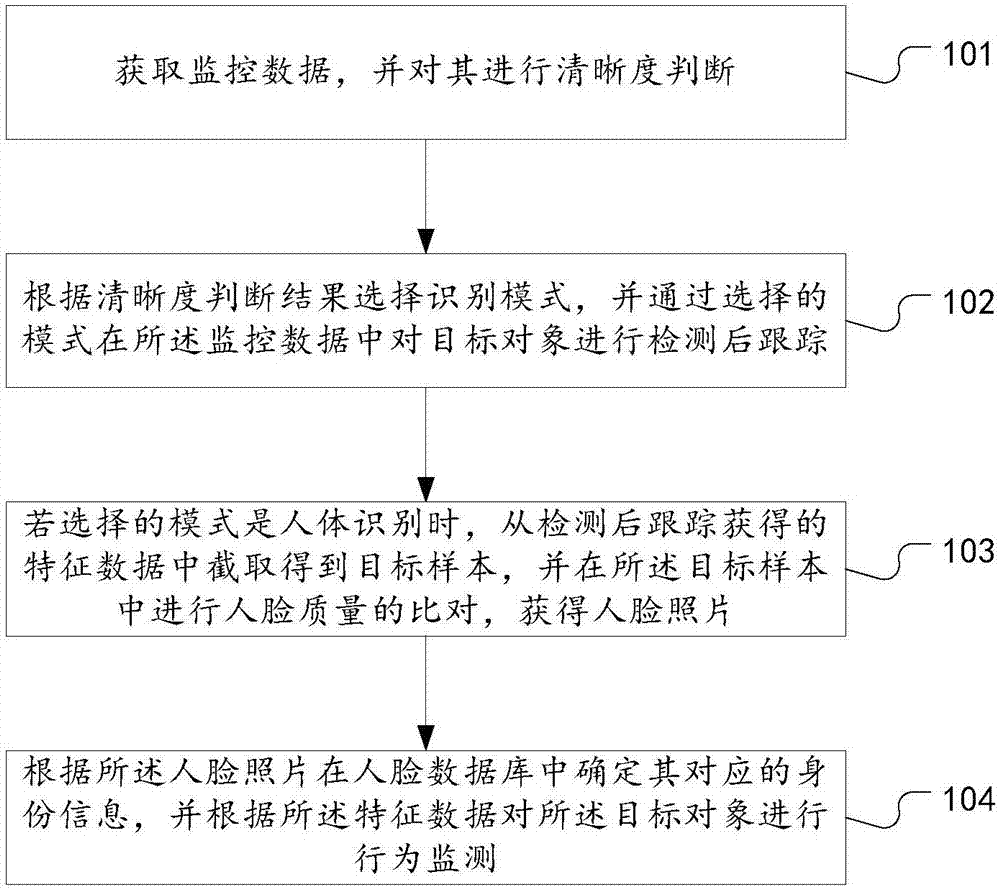
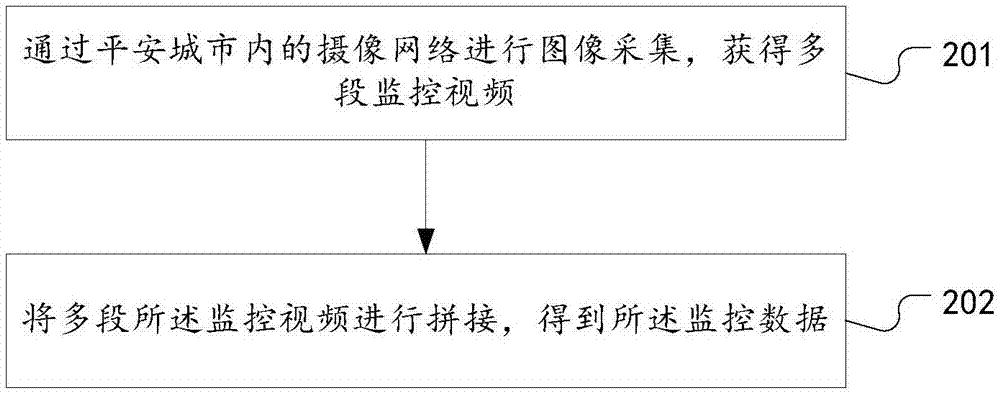
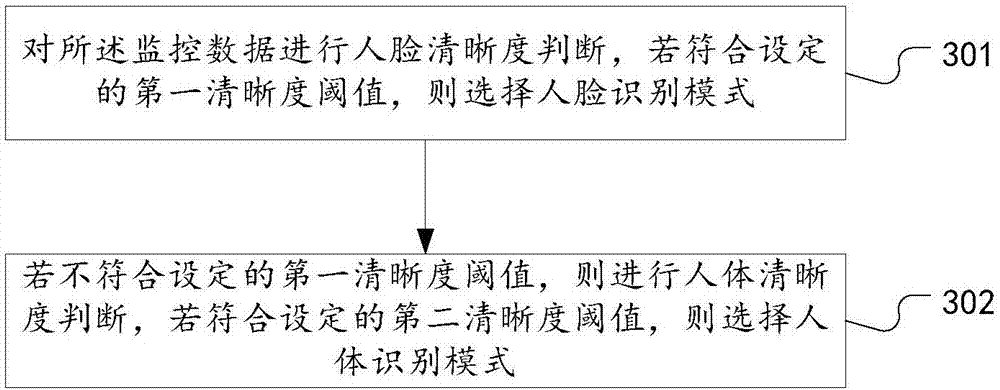
The invention discloses a people searching method and system based on face and human body identification; the method selects an identification mode from two identification modes through sharpness determinations, thus providing options for the identification modes, and effectively improving the identification performance; the method uses a human body identification mode to carry out after-detection tracking, thus preventing face identification failure caused by an unclear face, realizing face detection and tracking of a target person, improving the city safety level without changing hardware, and saving modification costs; the method uses the human body identification to realize ID authentication and behavior monitoring, thus reducing ID authentication and monitoring failure probability, and improving post-event tracing back capability; the searching system comprises a data determination unit, a mode selection unit, and a human body identification unit; the human body identification unit also comprises a face obtaining module and a behavior detection module; beneficial effects of the method and system are realized.
Owner:深圳市深网视界科技有限公司
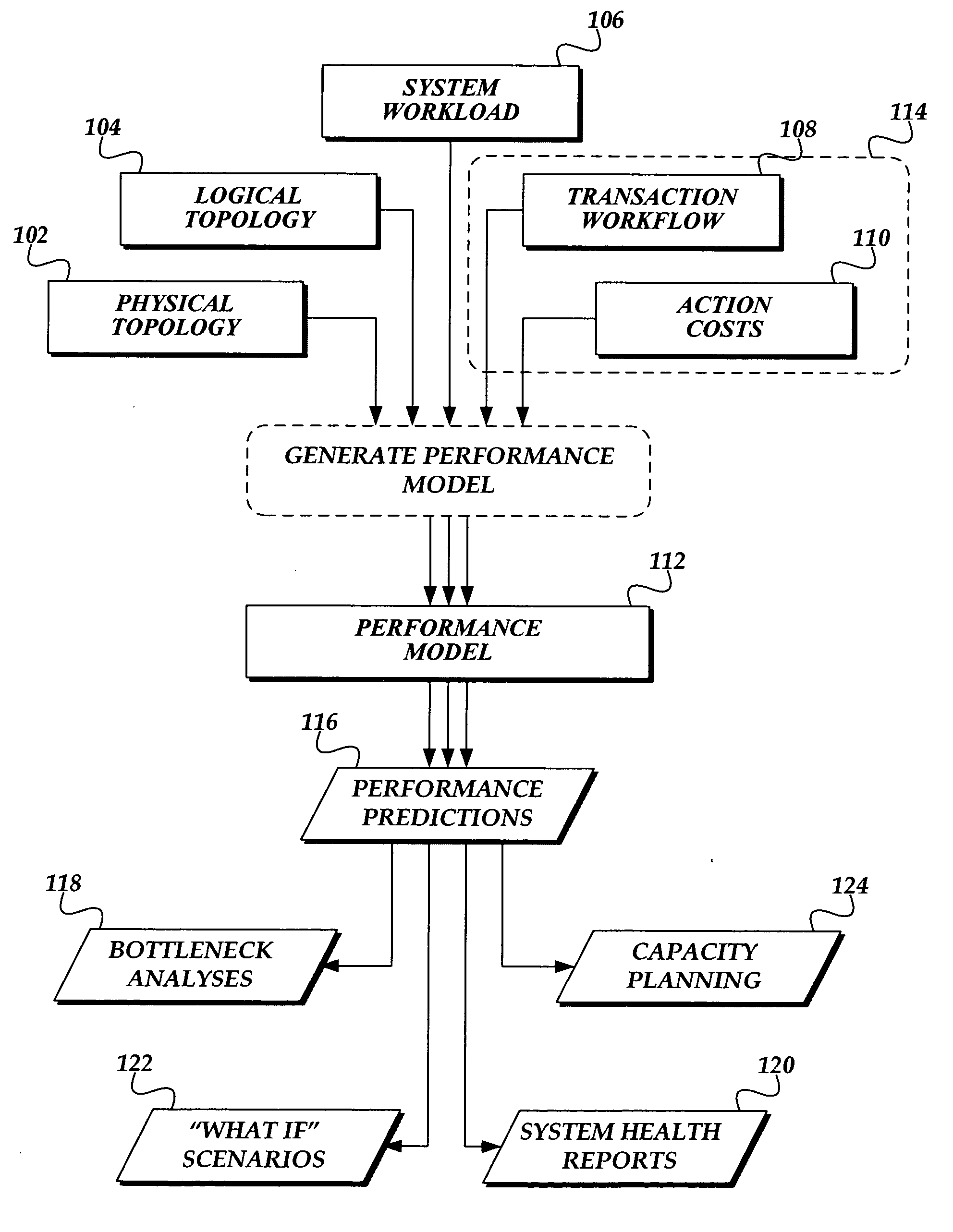
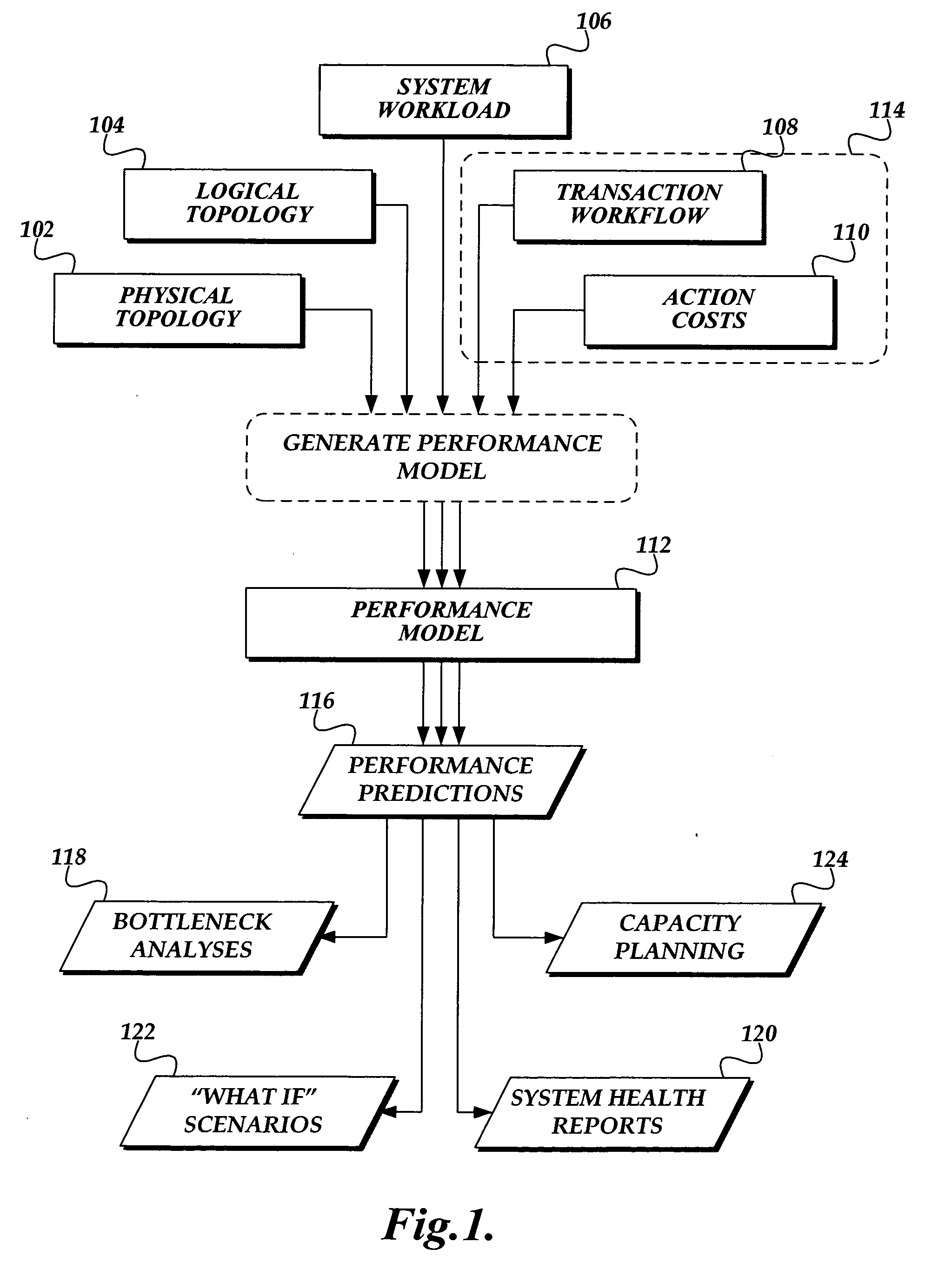
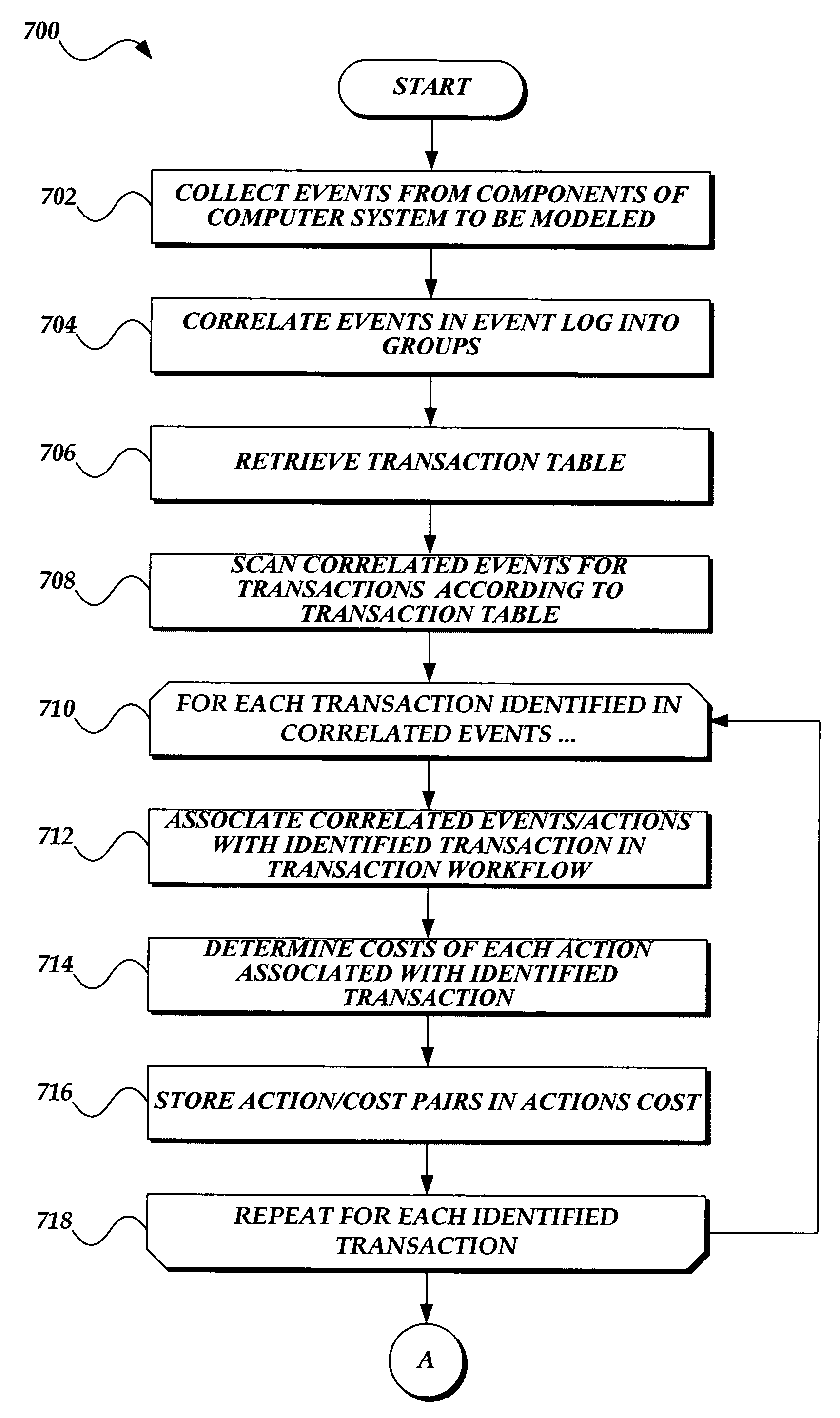
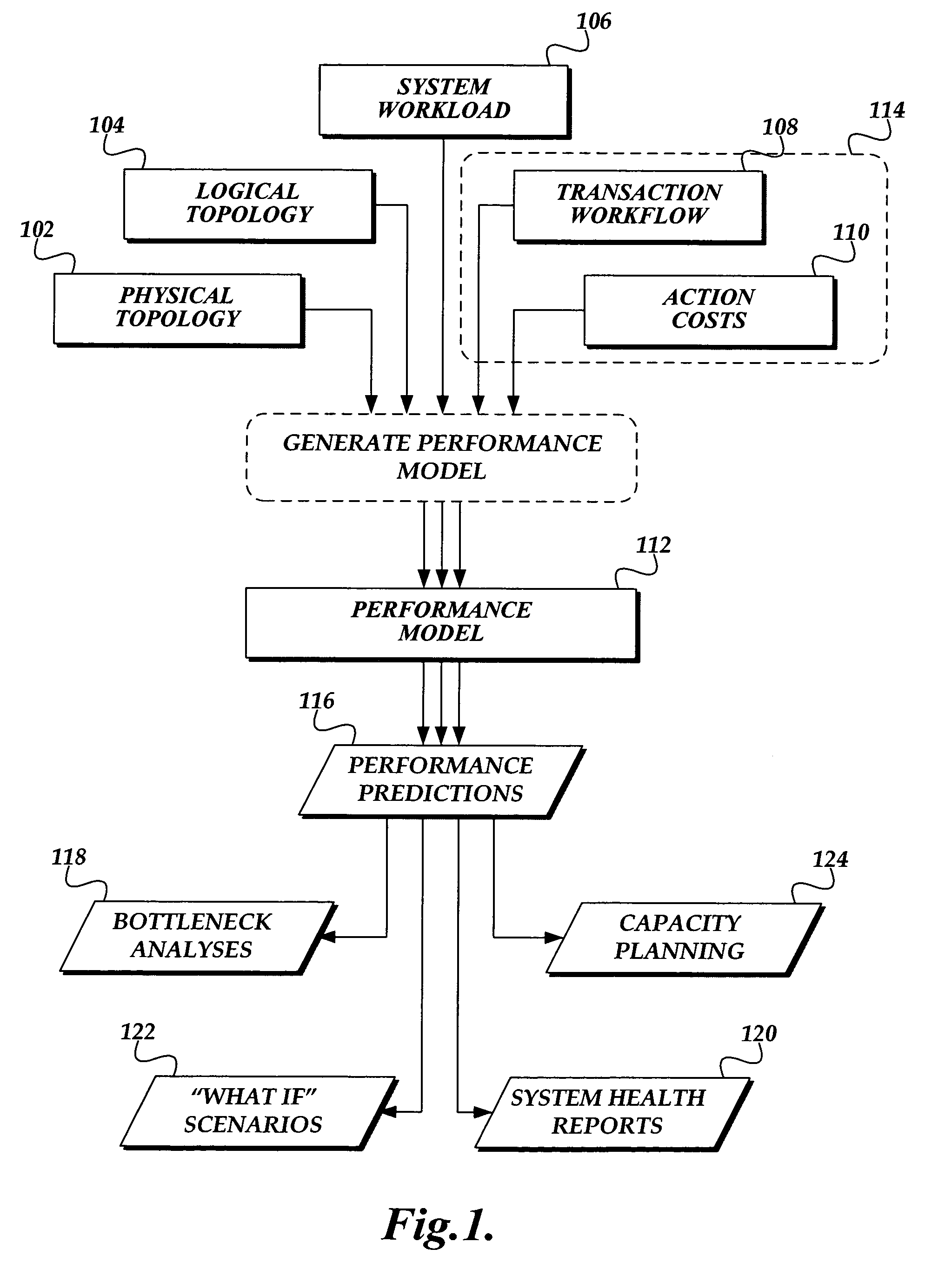
Generating static performance modeling factors in a deployed system
ActiveUS20060288149A1Office automationSpecific program execution arrangementsSubject matterStatic performance
A computing system for determining performance factors for using in performance modeling of a deployed subject system, is presented. The computing system includes a plurality of software components comprising the subject system. Each of the components is susceptible to event tracing while executing on the computing system. The computing system includes a tracing component. The tracing component is configured to trace events of the components of the subject system as they execute. The computing system includes a transaction identification table. The transaction identification table comprises starting and ending actions for transactions performed by the subject system. The computing system also includes a transaction identification component that identifies actions from traced events, identifies related actions corresponding to a transaction according to the starting and ending actions in the transaction identification table, and stores the related actions in the transaction workflow data store.
Owner:MICROSOFT TECH LICENSING LLC
Detection method used for Webshell
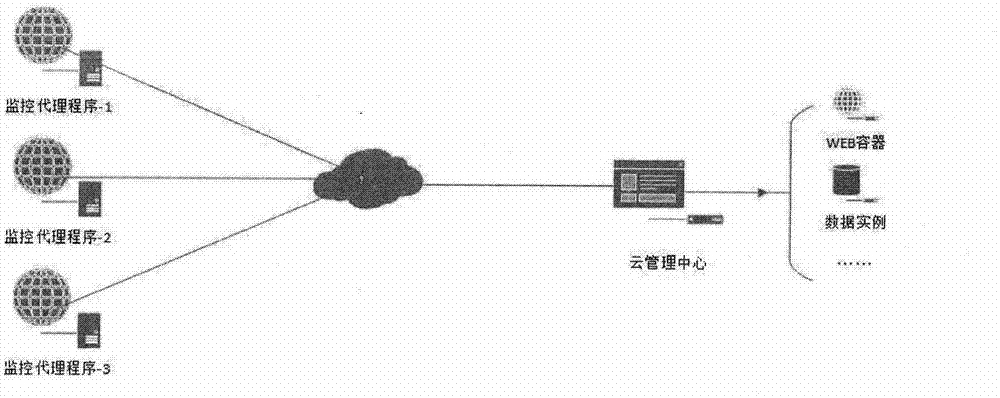
InactiveCN104765883ADetermine securityRapid positioningTransmissionSpecial data processing applicationsFull life cycleWeb service
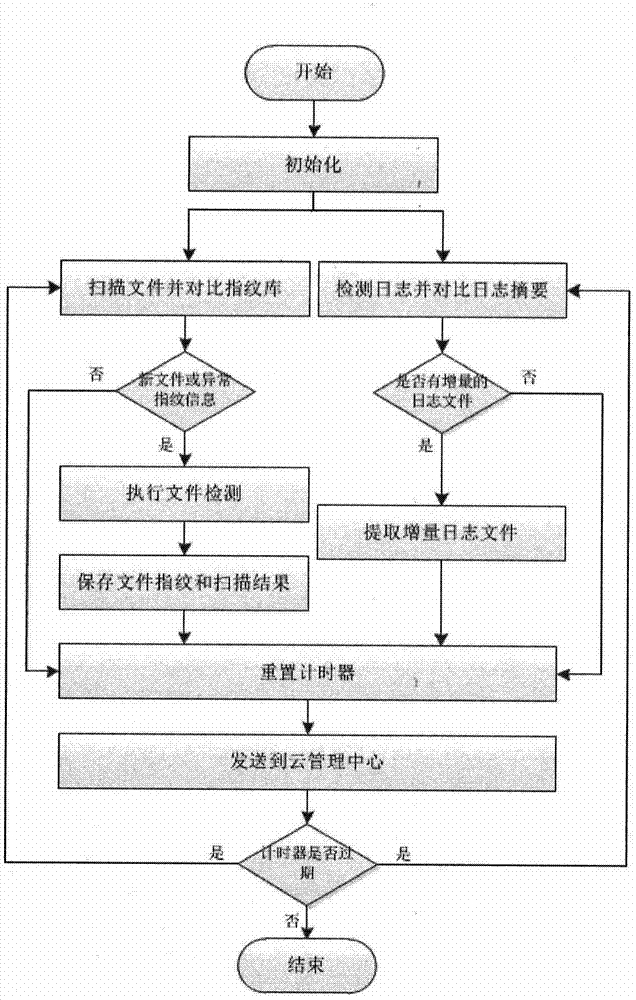
The invention discloses a comprehensive detection method used for Webshell. The detection method is a high-order WEB file detection method which supports combination of multiple detection means, covers the full-life cycle of a website and can achieve pre-event detection, in-event warning and after-event tracing in order to solve the security problems of website Trojan embedding and website invisible back door implanting and perform website file security audit. Through installing a monitoring agent program on a WEB server, WEB file detection results are dynamically sent to a cloud management enter so that a comprehensive risk analysis can be performed on the results, and the cloud management center performs the comprehensive analysis according to data of multiple sources and establishes a statistics model for each file for dynamically detecting the changes of the files, so that WEB file risk management is achieved.
Owner:CEPO BEIJING INFORMATION TECH CO LTD
Event tracing with time stamp compression
InactiveUS7346476B2Amplifier modifications to reduce noise influenceDigital computer detailsTime compressionImproved method
An improved method, apparatus, and computer instructions for generating trace data. In response to detecting a new trace event, a determination is made as to whether the new trace event occurred at an expected period of time with respect to a prior trace event. A time stamp in the trace data is placed in response to a determination that the new trace event did not occur at the expected period of time, wherein time stamps occurring at the expected period if time are eliminated from the trace data and wherein compression of the trace data occurs.
Owner:IBM CORP
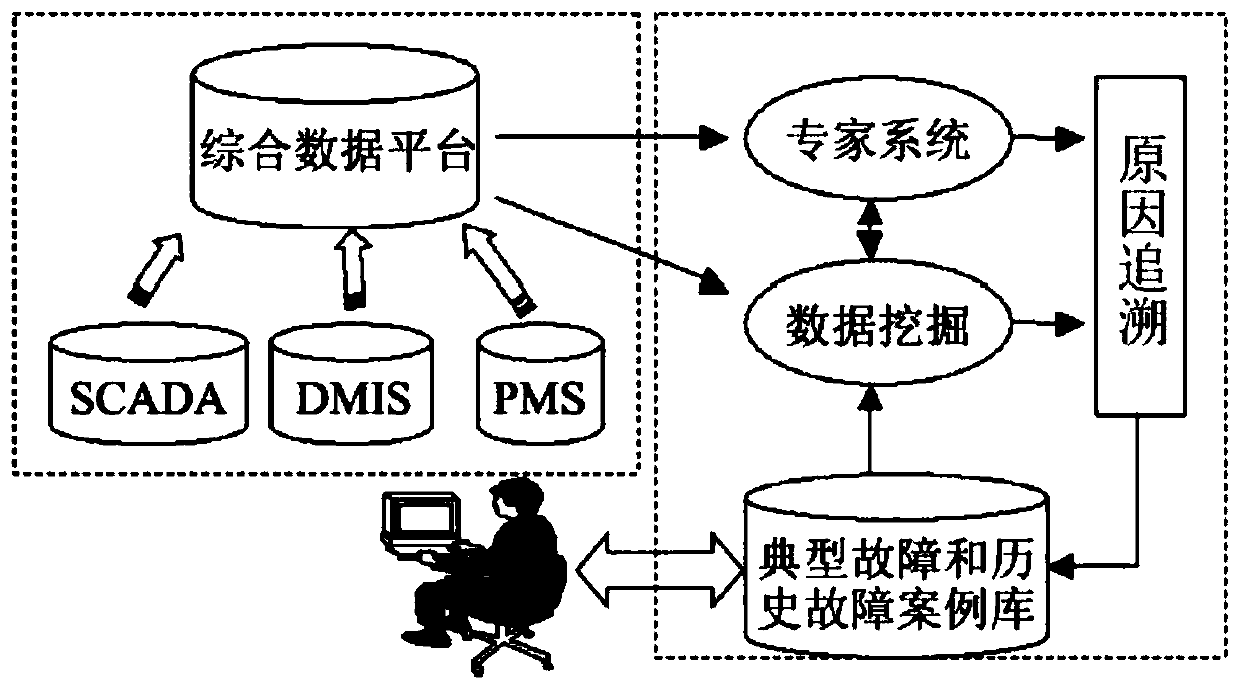
A power grid accident correlation reason backtracking method based on data mining and visualization
PendingCN109726246AQuick judgmentEasy to handleData processing applicationsVisual data miningData dredgingElectric power system
The invention relates to a power grid accident correlation reason backtracking method based on data mining and visualization, and belongs to the field of intelligent retrieval. The method comprises the following steps: S1, data mining; S2, accident event tracing retrieval; S3, displaying a tracing process in combination with a lexicon association rule; When the electric power system is in an operation state, if the system has a problem, the action information of the protection device can transmit the related information of the fault to the dispatching center; Fault information is imported intoan intelligent analysis system fault data mining algorithm is established, fault data can be analyzed, fault characteristics can be extracted, historical accident event data can be collected, mesh topology display can be carried out according to other operation information associated with the elements, and scheduling personnel can be assisted to investigate accident events, so that the system operation personnel can quickly judge and process power system faults.
Owner:GUIZHOU POWER GRID CO LTD
Event tracing with time stamp compression
InactiveUS20060212244A1Amplifier modifications to reduce noise influenceDigital computer detailsImproved methodEvent tracking
An improved method, apparatus, and computer instructions for generating trace data. In response to detecting a new trace event, a determination is made as to whether the new trace event occurred at an expected period of time with respect to a prior trace event. A time stamp in the trace data is placed in response to a determination that the new trace event did not occur at the expected period of time, wherein time stamps occurring at the expected period if time are eliminated from the trace data and wherein compression of the trace data occurs.
Owner:IBM CORP
Event map construction method and device and electronic equipment
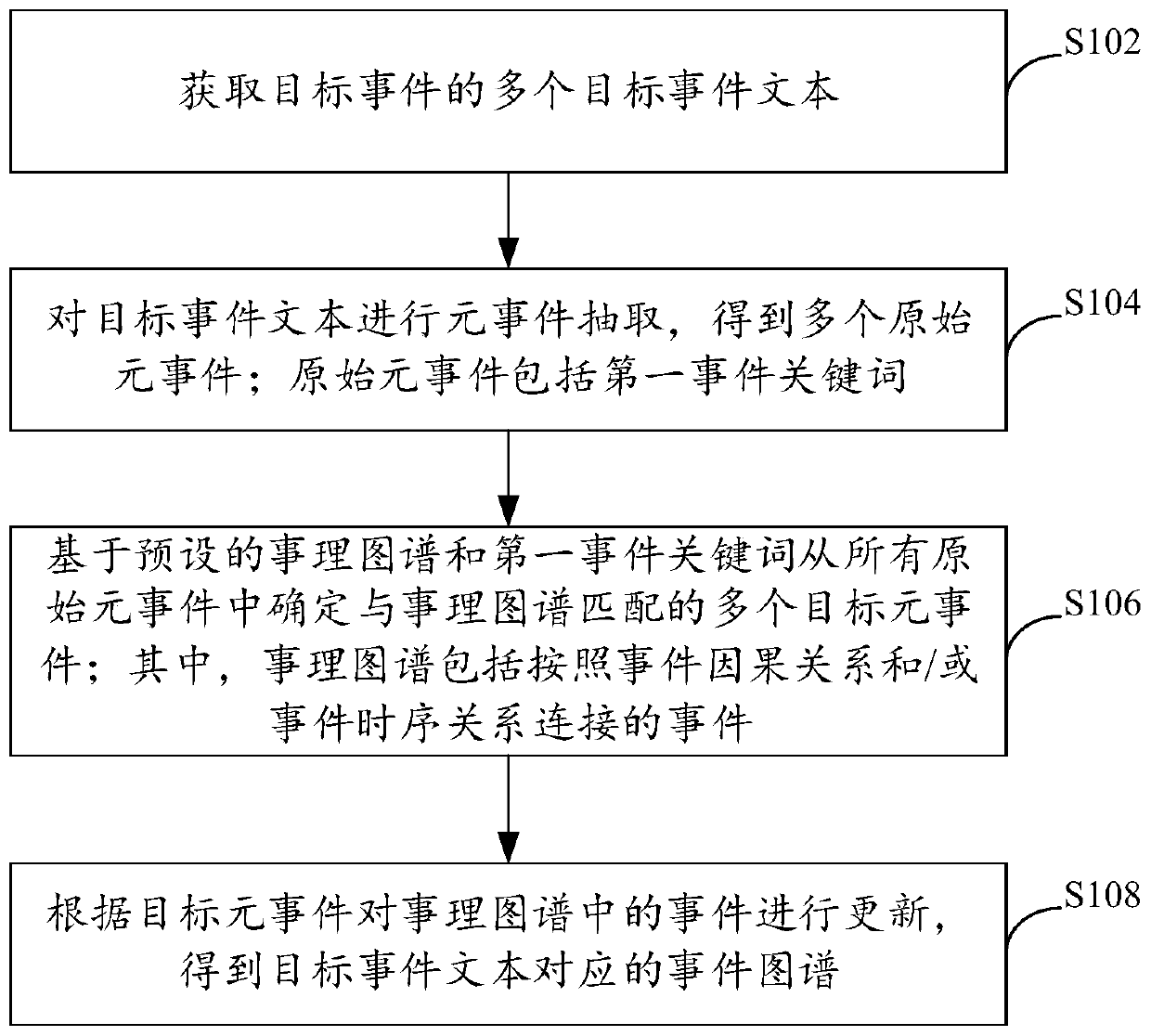
ActiveCN110781317AAchieve traceabilityImprove acquisition efficiencyWeb data indexingNatural language data processingInformation miningEvent graph
The invention provides an event map construction method and device, and electronic equipment, and relates to the technical field of information mining, and the method comprises the steps of obtainingmultiple target event texts of a target event; performing meta-event extraction on the target event text to obtain a plurality of original meta-events; wherein the original meta event comprises a first event keyword; determining a plurality of target meta-events matched with the fact map from all the original meta-events based on the preset fact map and the first event keyword; wherein the cause map comprises events connected according to an event causal relationship and / or an event time sequence relationship; and updating the events in the cause map according to the target meta-event to obtain an event map corresponding to the target event text. According to the invention, the complexity of generating the event graph can be reduced, and the obtaining efficiency and event tracking capability of the event graph are improved.
Owner:BEIJING MININGLAMP SOFTWARE SYST CO LTD
Intelligent key box
The invention discloses an intelligent key box which comprises a box body and a storage cavity. The box body comprises a shell, a power source, a password input device, a controller and an opening-closing execution mechanism, the opening-closing execution mechanism and the storage cavity are positioned inside the shell, the shell comprises a front faceplate, a rear faceplate and a shaft portion, the front faceplate and the rear faceplate are rotatably connected through the shaft portion, and the password input device is embedded in the front faceplate and used for inputting passwords or recognition features; the intelligent key box further comprises a storer and a communication module, and the password input device, the power source, the opening-closing execution mechanism, the storer and the communication module are electrically connected with the controller and positioned in the shell. Used passwords can be changed, increased or deleted at any time, so that convenience and safety in password sharing can be realized. Further, the intelligent key box can memorize unlocking time and used passwords, and a basis is provided for event tracing.
Owner:POPULIFE TECH LLC
Processor core power event tracing
ActiveUS20160179166A1Hardware monitoringPower supply for data processingParallel computingEvent tracking
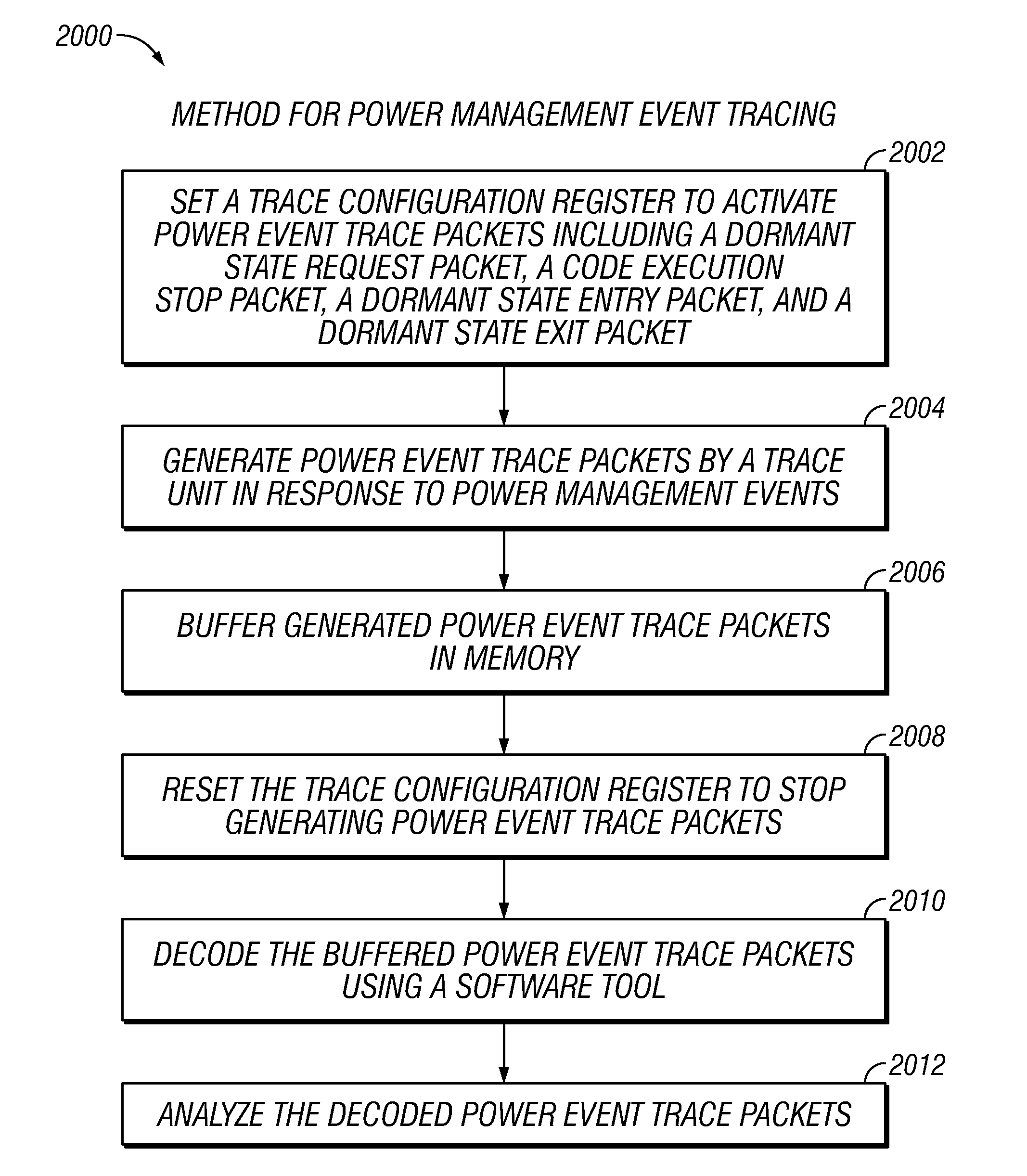
A processor includes a trace unit to monitor activity by the processor and generate trace packets indicative of the activity by the processor. The trace packets may include four additional packets for processor event tracing including: a dormant state request packet, a code execution stop packet, a dormant state entry packet, and a dormant state exit packet.
Owner:INTEL CORP
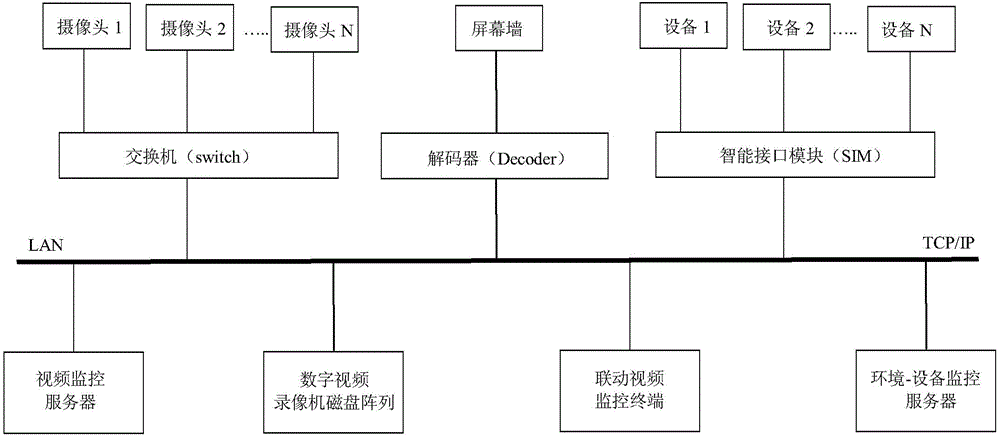
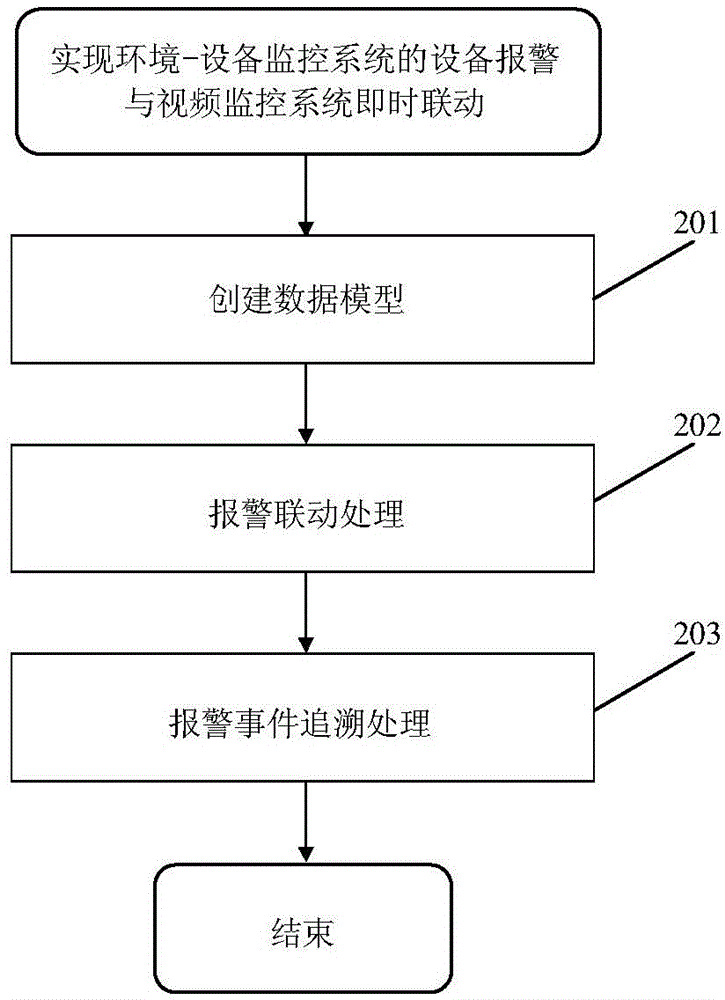
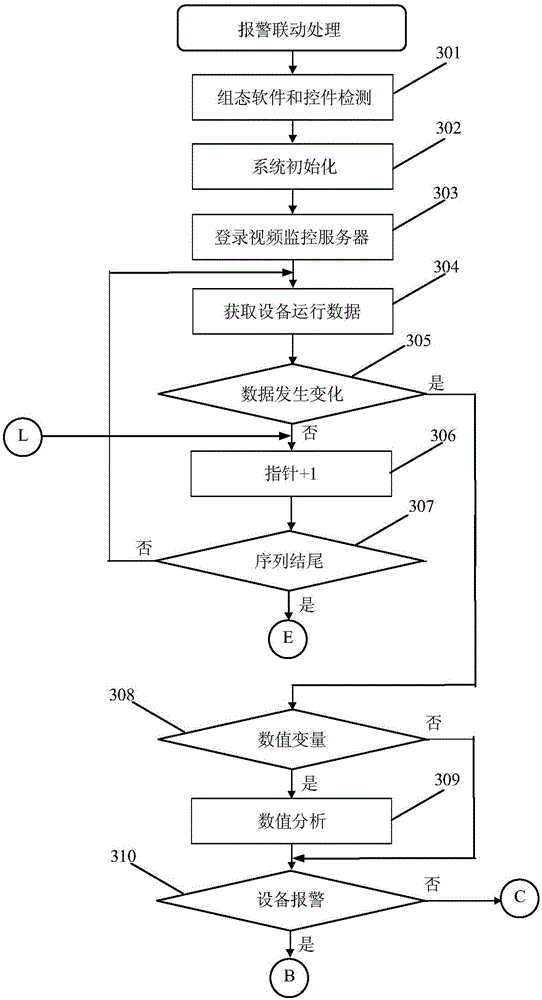
Method for achieving environment device monitoring system warning and video monitoring system linkage
InactiveCN104092976AStrong real-timeWide audienceClosed circuit television systemsVideo monitoringMonitoring system
The invention relates to a method for achieving environment device monitoring system warning and video monitoring system linkage. The method comprises a first step of creating a data model for monitoring point locations, decoders and dynamic operation data according to running modes and data structures of an environment device monitoring system and a video monitoring system; a second step of adopting time-sharing operation, performing circulating scanning of all monitoring point locations, obtaining device operation data, and performing system warning linkage processing according to data analysis results; and a third step of finishing single monitoring point location event tracing or multiple monitoring point location event recurrence through operation of selecting warning event table data lines and play windows. According to the method, real-time monitoring of operation data and a warning state of the environment device monitoring system and video channel control management of the video monitoring system can be finished, workers can timely and accurately learn about actual conditions of incident places, and a function of real-time linkage of device and sensor warning and the video monitoring system is achieved.
Owner:兰捷尔智能科技有限公司
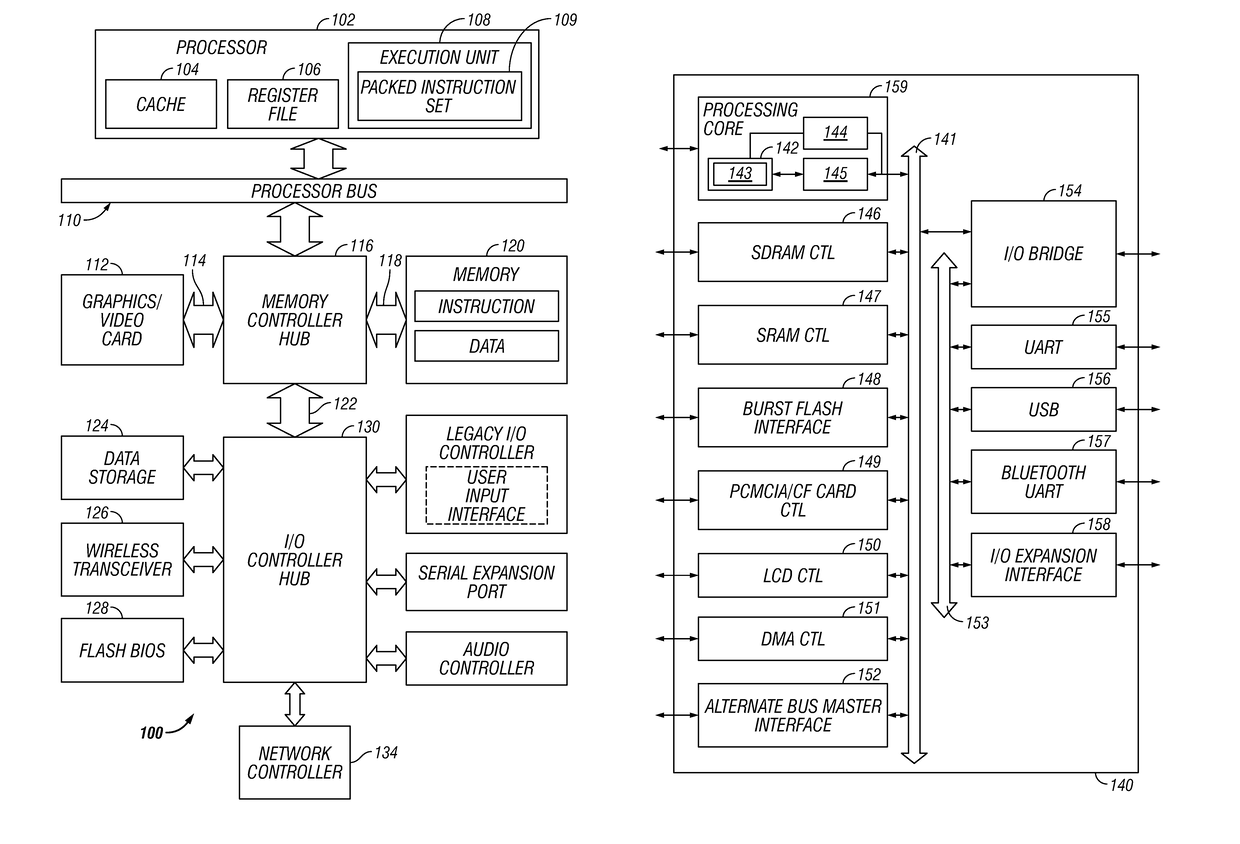
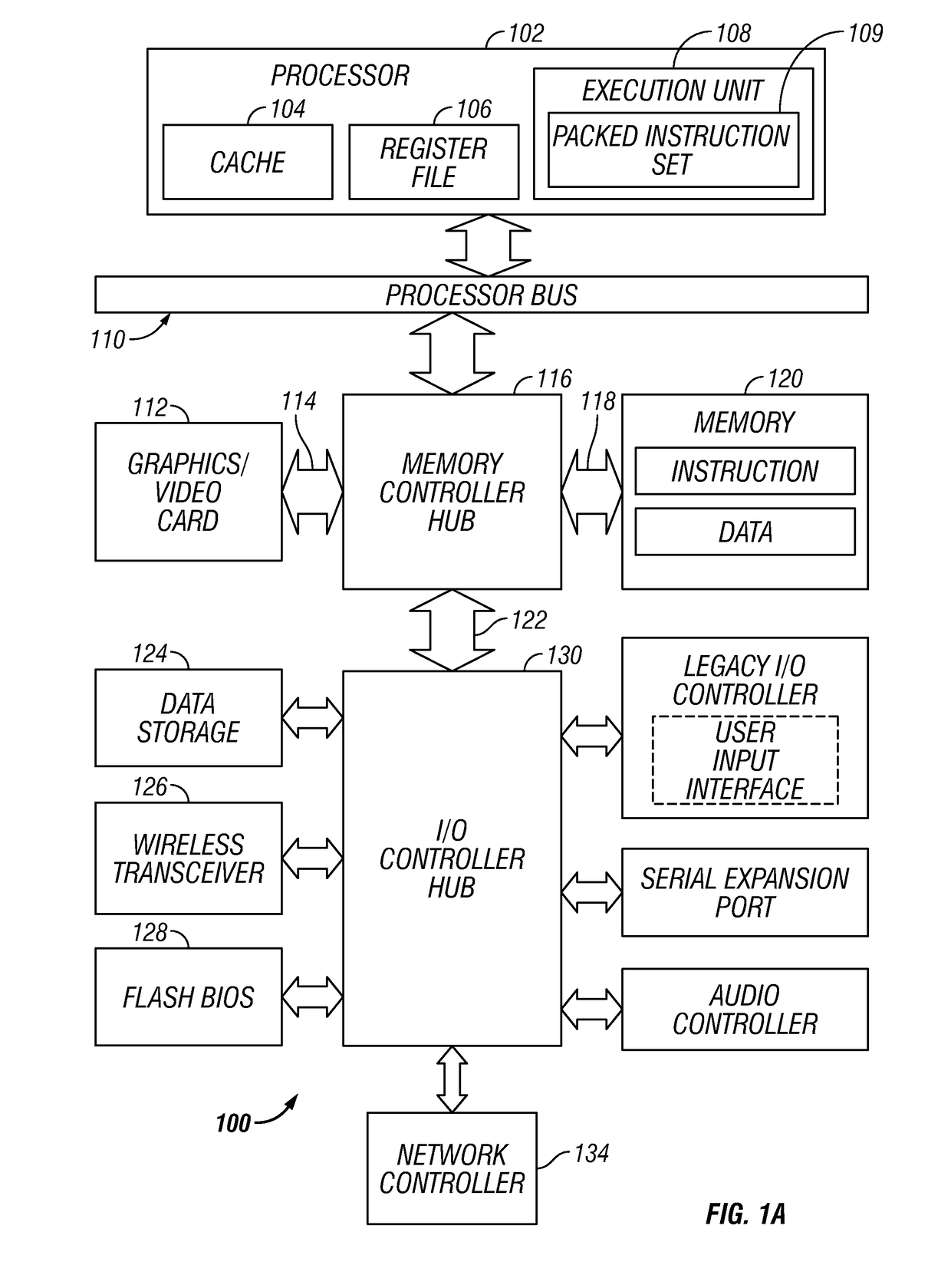
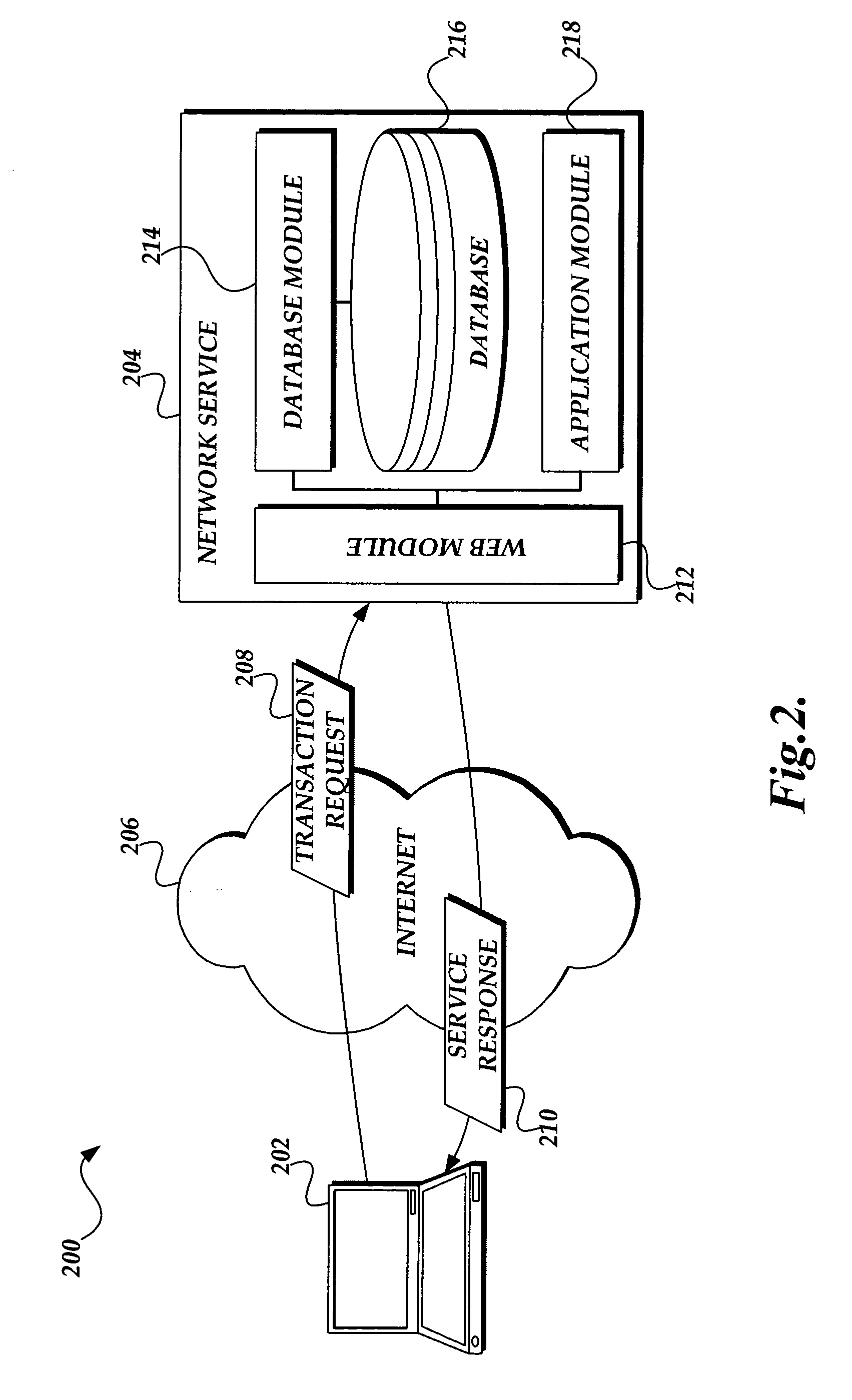
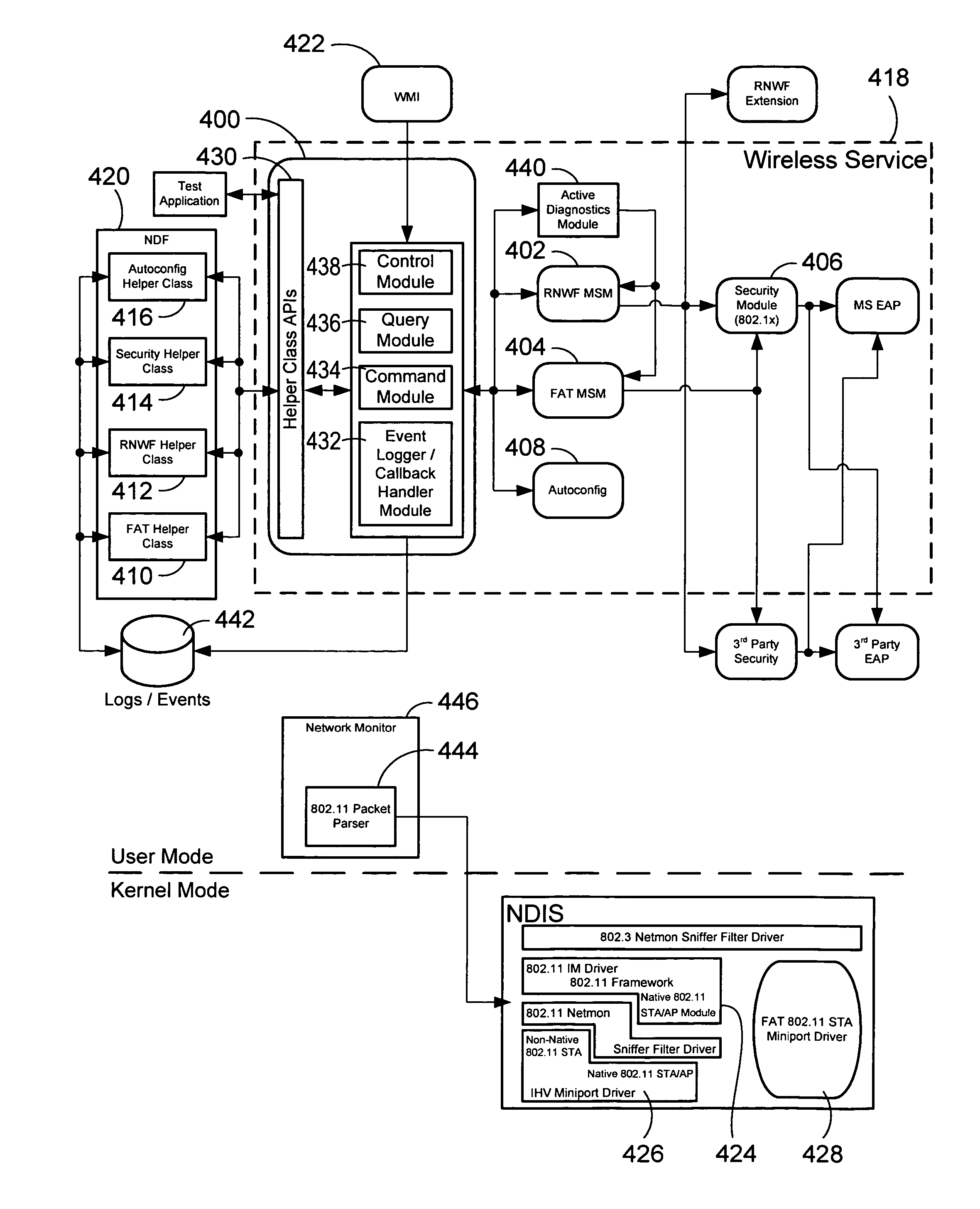
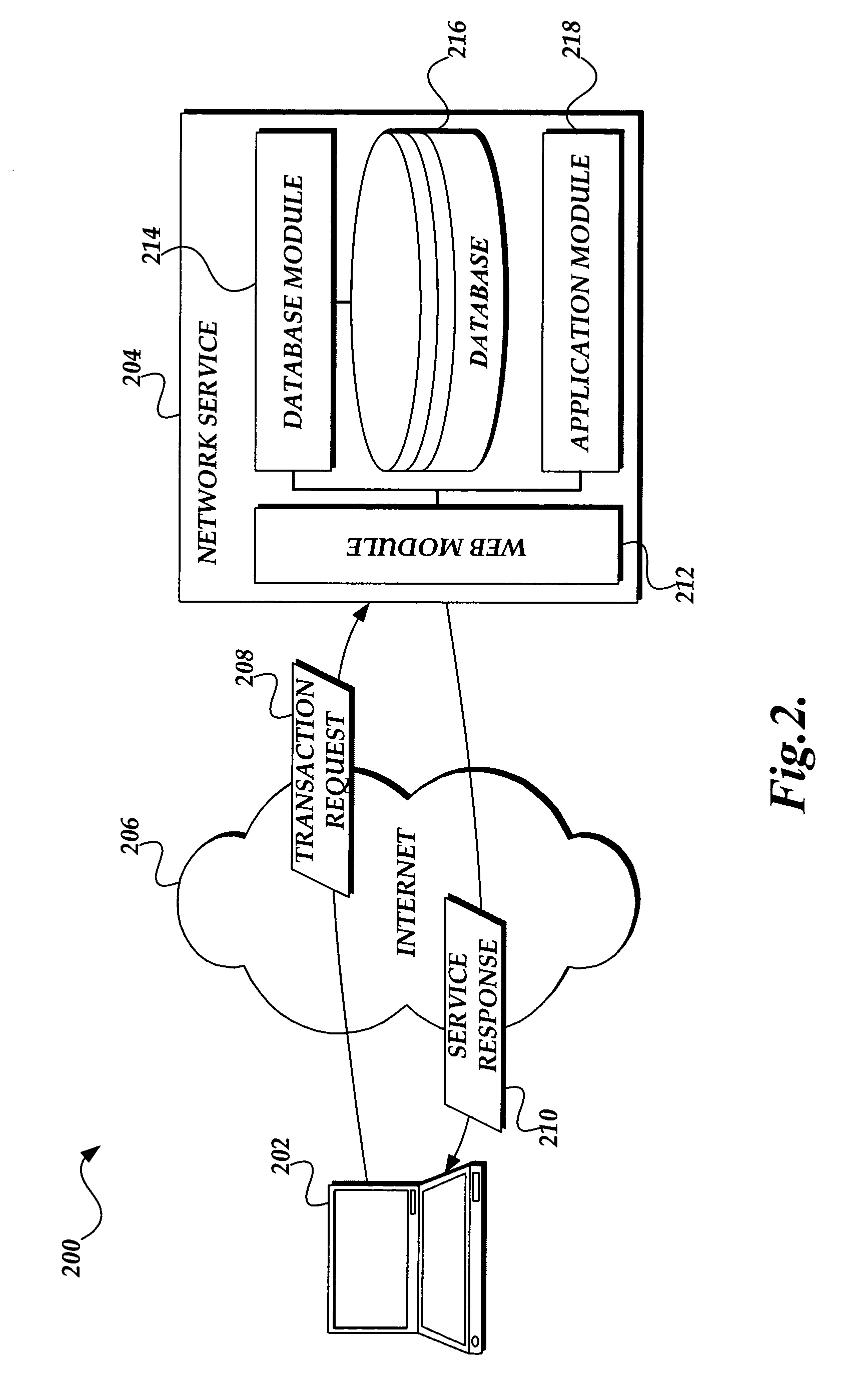
Method and apparatus for performing wireless diagnostics and troubleshooting
A wireless diagnostics framework that is non-intrusive and stays out of the way of a user is presented. In the case of a failure, prescriptive guidance is provided and / or the framework possibly automatically fixes the problem. The framework includes a wireless diagnostics module that interacts with the operating system's diagnostics framework, helper classes, and wireless components to collect and log wireless diagnostic events and notifications, and issues queries and requests for active diagnostics. The helper classes perform diagnosis and troubleshooting fore their expertise areas based on the information provided by the wireless diagnostics module. The wireless diagnostics module includes an application program interface for communicating with helper classes, an event listener module that provides an event tracing application program interface to in-process modules, an active diagnostics module that issue active packet test requests to a media specific module, and query modules that issue information query requests to media specific modules.
Owner:MICROSOFT TECH LICENSING LLC
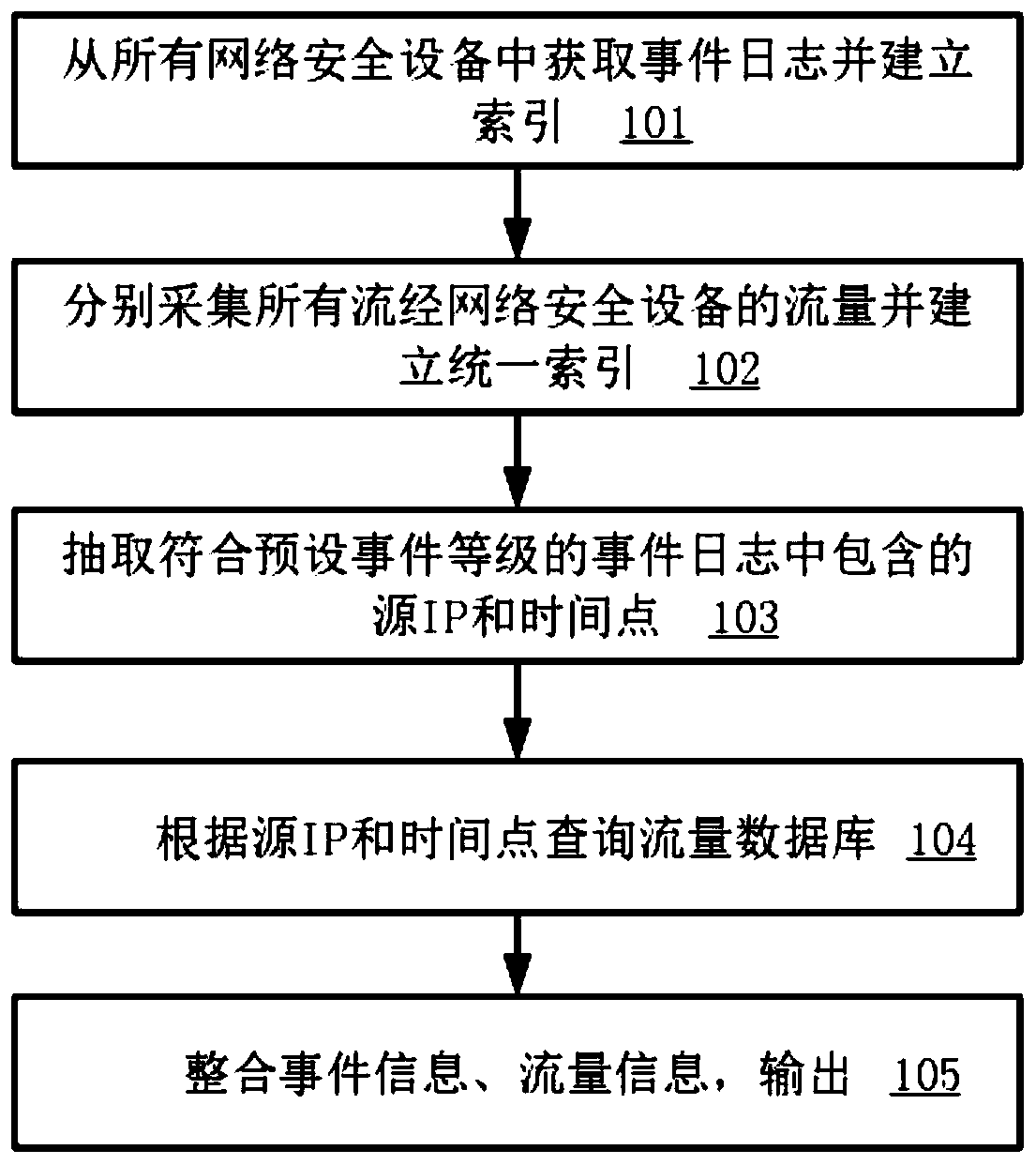
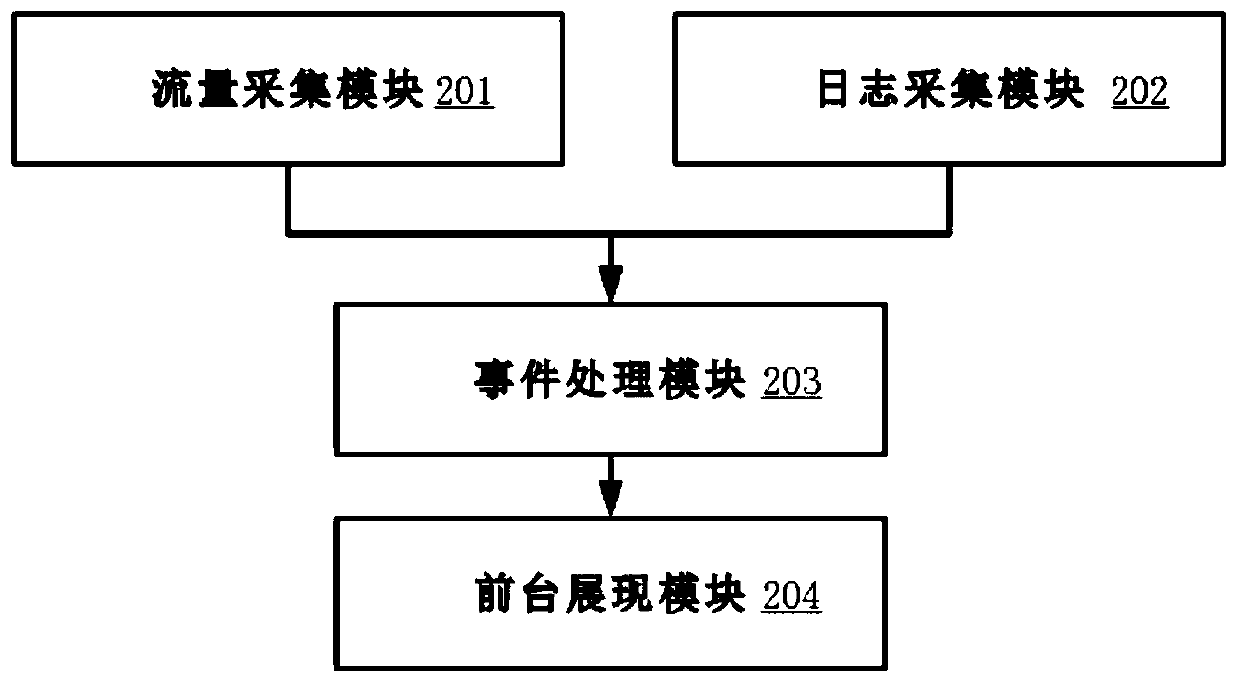
Network system event tracing method and system based on log and flow collection
The invention relates to an information security technology. A network system event traceability method and system based on log and flow collection can be provided, and the method comprises the steps:obtaining network access and network exit flow data of all network safety equipment in a flow mirroring mode at a core switch through a distributed log collection method, and storing the network access and network exit flow data in a flow database of each collection instance; adopting a centralized log collection method to collect logs generated by each network security device; filtering and processing the collected logs, and storing the logs in a log database; extracting an IP and occurrence time of the log identifier, and retrieving all flow data of the IP at an event occurrence time pointand within a period of time after the event occurrence time point in a flow database; aggregating presentation data. According to the embodiment of the invention, the problems that the source is difficult to trace and the attack means cannot be analyzed after the attack event occurs are solved, and a specific attack path and an attack target can be displayed according to the corresponding event.
Owner:浙江高信技术股份有限公司
Infection control quality event quick positioning and tracing-back method based on RFID
ActiveCN103345590ATroubleshoot Analytical DifficultiesAchieve positioningSpecial data processing applicationsData miningApplication areas
The invention provides an infection control quality event quick positioning and tracing-back method based on an RFID. According to the method, historical information in a system database is set up to form a sample, modeling is conducted for the treating process through application domain knowledge and sample knowledge, and then learning of the sample and a process model is utilized to set up a hidden Markov probability relationship for the process model. When the system obtains quality event information, event and reason positioning is conducted through a probability model, event tracing-back suggestions are output to a user according to the reason of the event, the user conducts sampling inspection on objects with the same treating information as a quality event target, and object tracing-back is conducted according to the practical inspection condition, namely, taking back and retreatment are conducted on objects with the same quality problem.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Generating static performance modeling factors in a deployed system
ActiveUS7747986B2Office automationSpecific program execution arrangementsSubject matterStatic performance
A computing system for determining performance factors for using in performance modeling of a deployed subject system, is presented. The computing system includes a plurality of software components comprising the subject system. Each of the components is susceptible to event tracing while executing on the computing system. The computing system includes a tracing component. The tracing component is configured to trace events of the components of the subject system as they execute. The computing system includes a transaction identification table. The transaction identification table comprises starting and ending actions for transactions performed by the subject system. The computing system also includes a transaction identification component that identifies actions from traced events, identifies related actions corresponding to a transaction according to the starting and ending actions in the transaction identification table, and stores the related actions in the transaction workflow data store.
Owner:MICROSOFT TECH LICENSING LLC
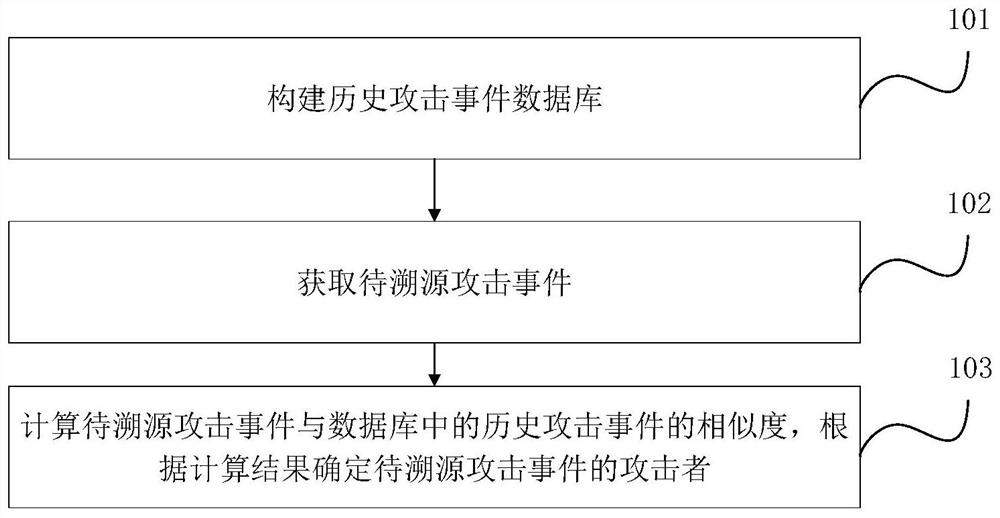
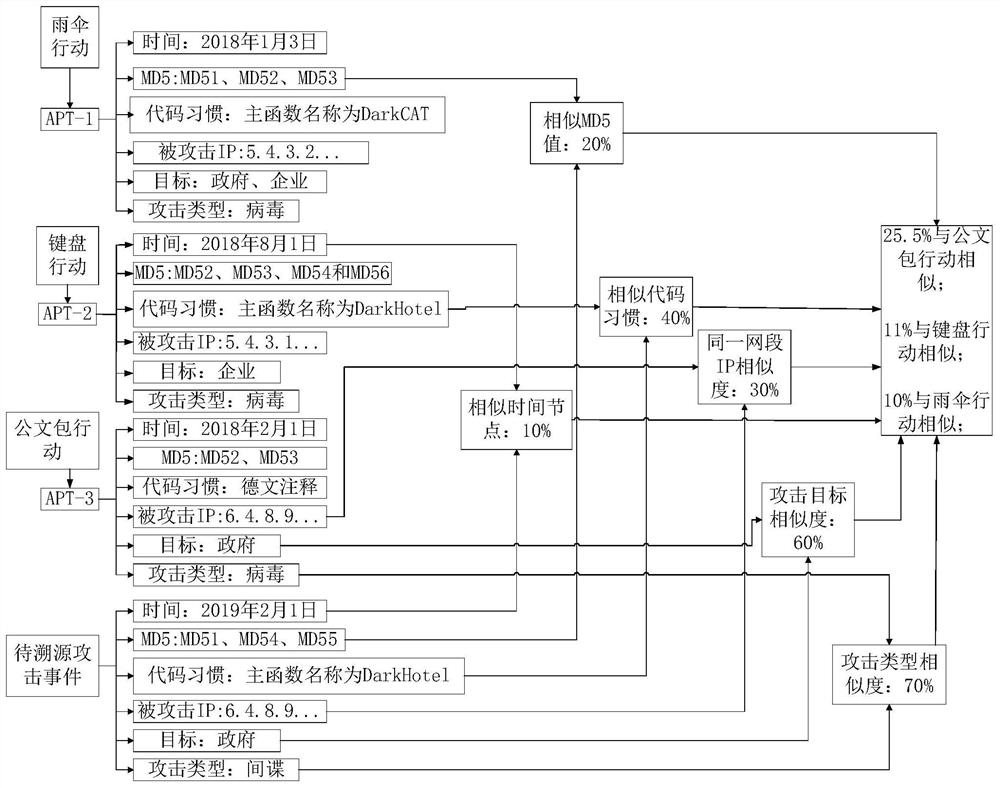
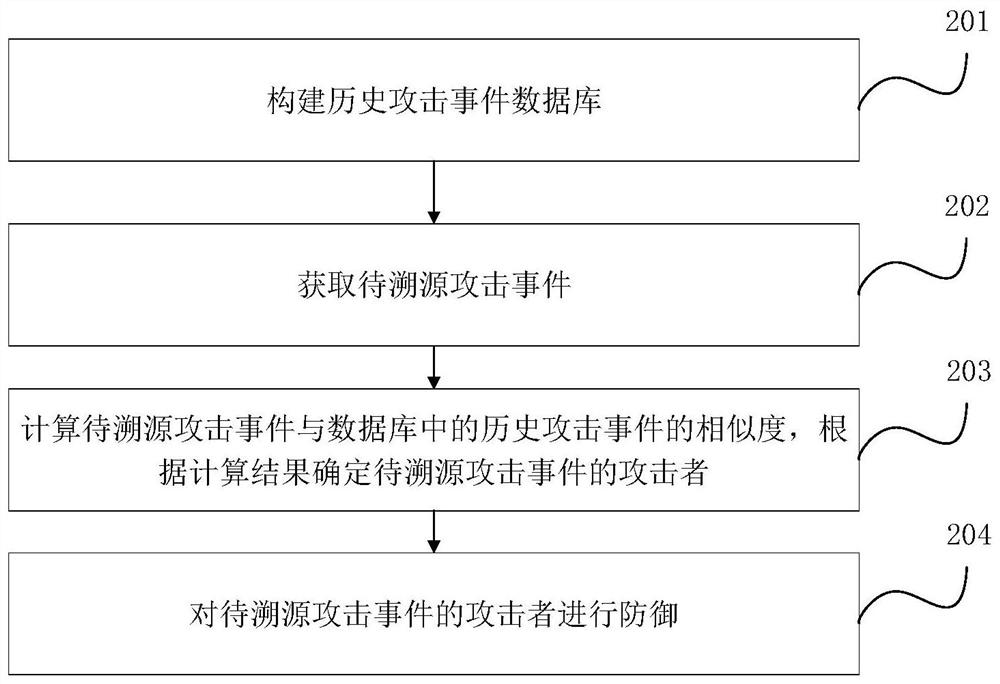
Attack event tracing method and device, electronic equipment and storage medium
The embodiment of the invention discloses an attack event tracing method and device, electronic equipment and a storage medium. The method comprises the steps that a historical attack event database is constructed, and the historical attack event database comprises a plurality of historical attack events, dimension information of each historical attack event and known attackers; obtaining a to-be-traced attack event; and calculating the similarity between the to-be-traced attack event and historical attack events in a database, and determining an attacker of the to-be-traced attack event according to a calculation result. According to the invention, the database is constructed in advance according to a plurality of known historical attack events of an attacker, and the attacker of the attack event to be traced is determined by calculating the similarity between the attack event to be traced and the historical attack events in the database, so that the attacker corresponding to the attack event to be traced is accurately and efficiently determined.
Owner:EVERSEC BEIJING TECH
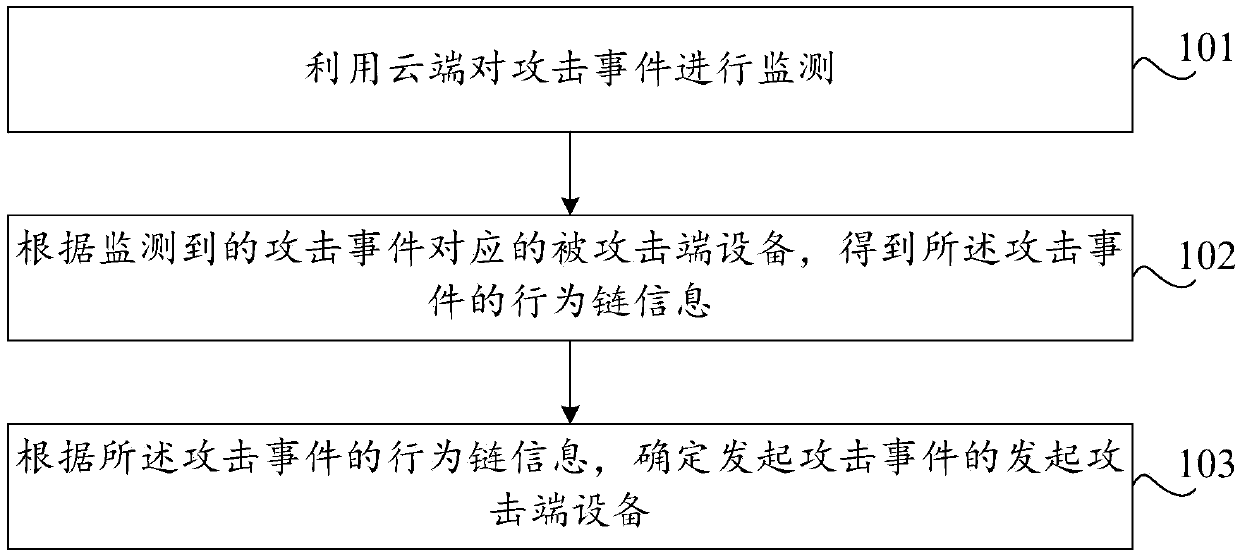
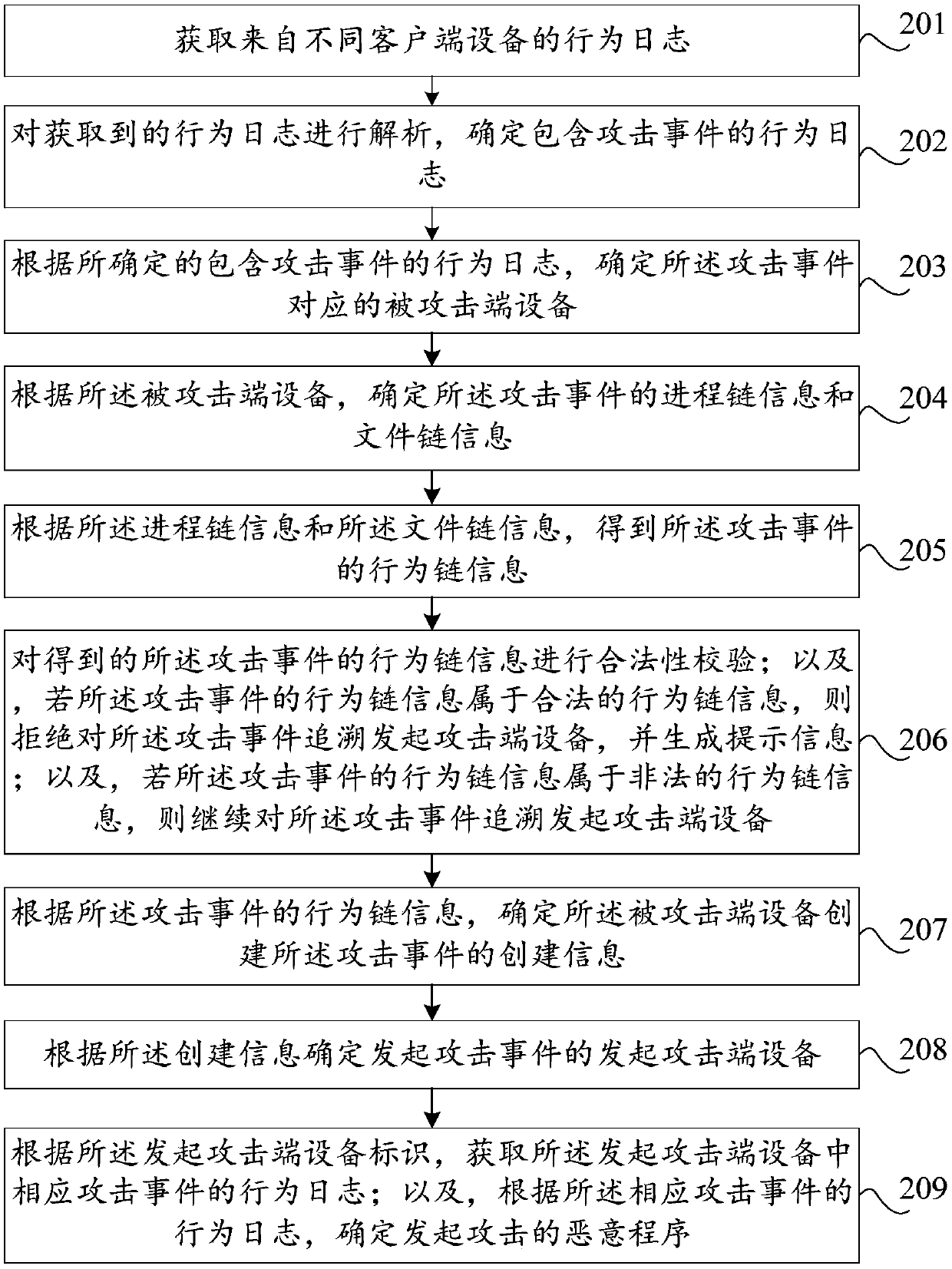
Attack event tracing method and device, storage medium and computer equipment
ActiveCN109600387AReduce professional requirementsLow costData switching networksEvent tracingComputer security
The invention discloses an attack event tracing method and device, a storage medium and a computer device. The method comprises the steps: monitoring an attack event by using a cloud; acquiring behavior chain information of the attack event according to an attacked end device corresponding to the monitored attack event; and determining attack initiating end equipment which initiates the attack event according to the behavior chain information of the attack event. The attack initiating end of the attack event can be rapidly determined according to the determined attack initiating end equipment,the tracing success rate and accuracy are improved, and a scientific basis is provided for follow-up security defense work. Meanwhile, the professional requirement for operation and maintenance personnel is lowered, and the personnel cost is lowered.
Owner:QI AN XIN SECURITY TECH ZHUHAI CO LTD +1
Informatization management method, device and system
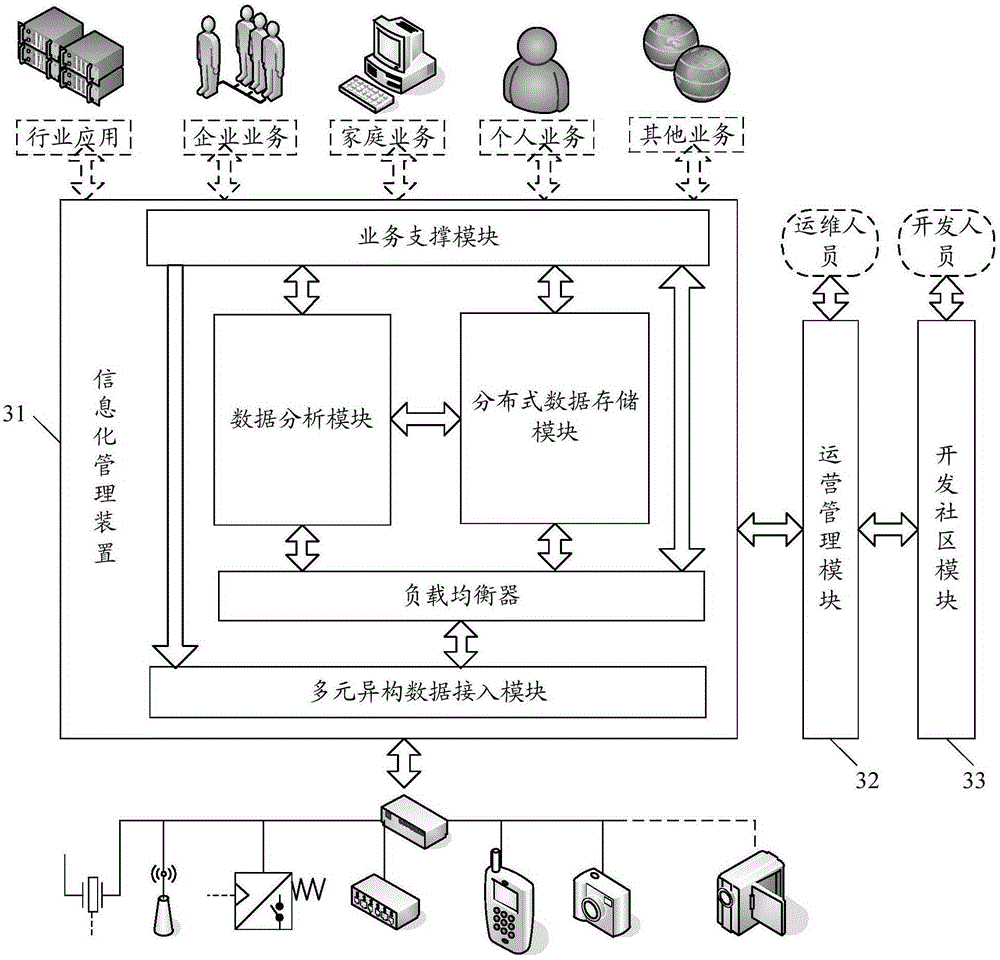
ActiveCN106452815ARealize real-time monitoring and managementRealize online debuggingData switching networksInformatizationTerminal equipment
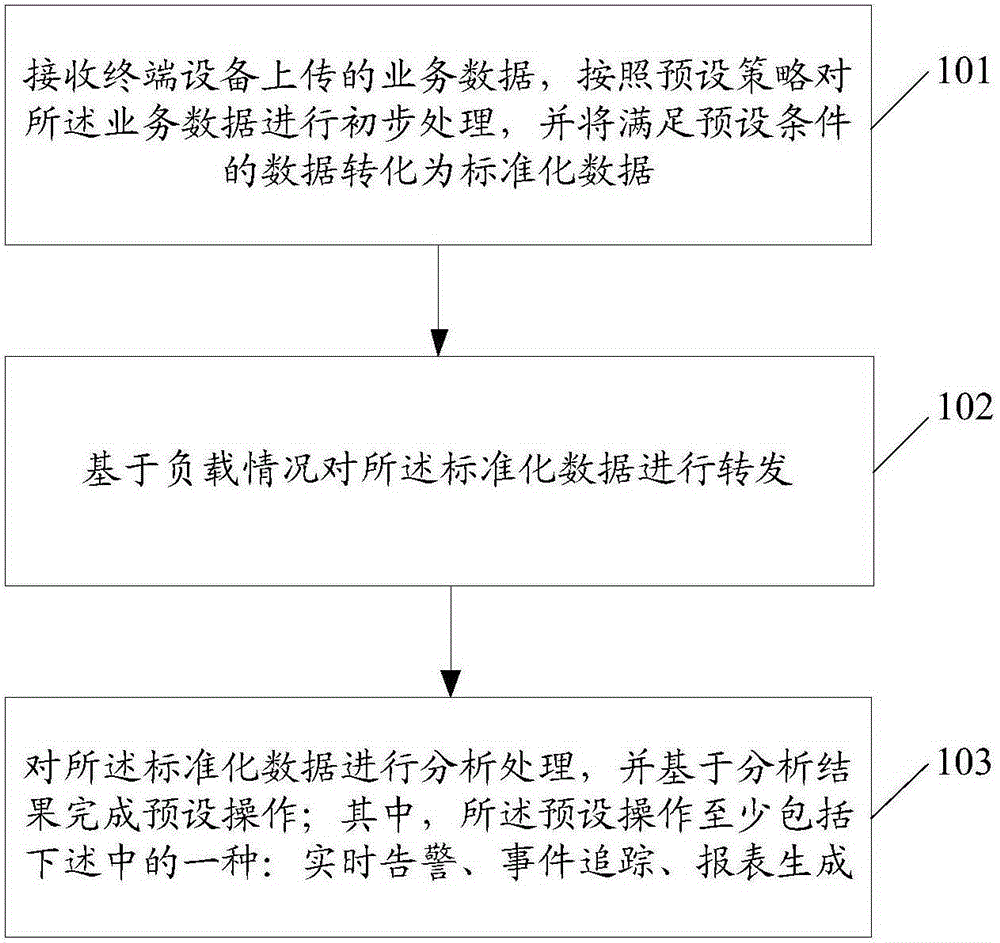
The invention discloses an informatization management method. The method comprises the steps that service data uploaded by terminal equipment are received, the service data are preliminarily processed according to the preset strategy, and the data meeting the preset conditions are converted into standardized data; the standardized data are forwarded based on the condition of loading; and the standardized data are analyzed and preset operation is completed based on the analysis result, wherein the preset operation at least includes one of the following: real-time alarming, event tracking and report generation. The invention also discloses an informatization management device and system. With application of the technical scheme, integrated intelligent management and support of "cloud-management-terminal" can be provided so that the real-time monitoring and management, online debugging and control functions of the terminal equipment can be realized, and the complexity of the framework of the internet of things and interdisciplinary applications can be reduced.
Owner:CHINA MOBILE M2M
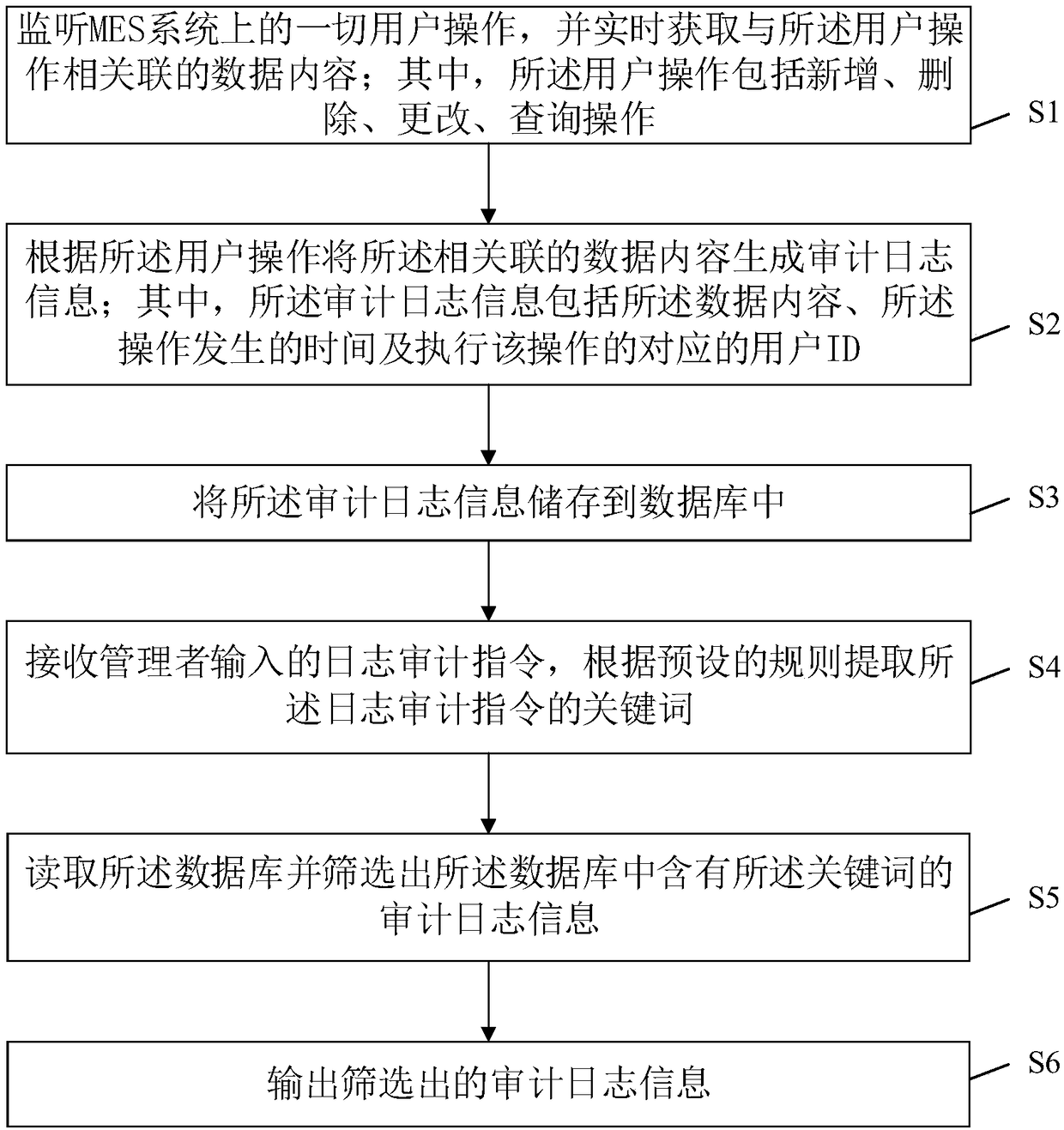
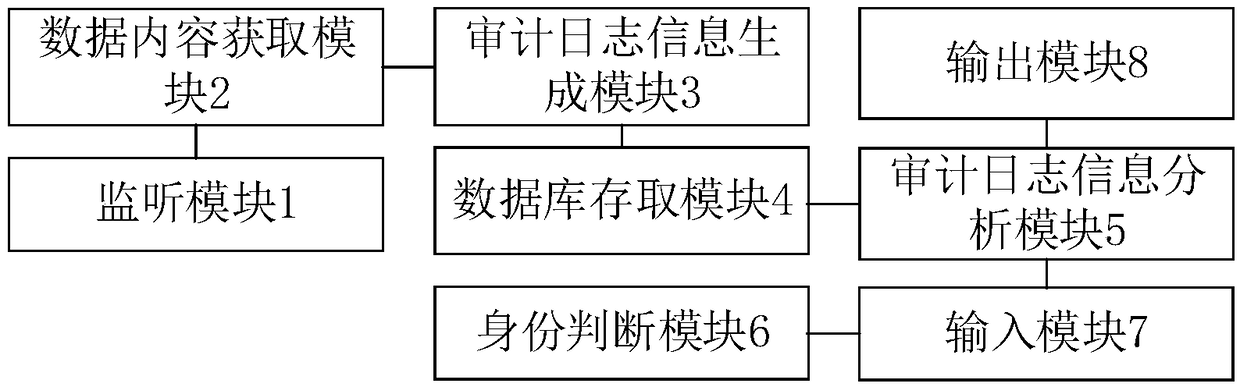
An audit tracking method and system for an MES system
The invention discloses an audit tracking method and system for an MES system, and the method comprises the steps: monitoring all user operations on the MES system, and obtaining the data content associated with the user operations in real time; generating audit log information from the associated data content according to the user operation, wherein the audit log information comprises the data content, the operation occurrence time and a corresponding user ID for executing the operation; Storing the audit log information into a database; receiving a log auditing instruction input by a manager, and extracting a keyword of the log auditing instruction according to a preset rule; Reading the database and screening audit log information containing the keywords in the database; and outputtingthe screened audit log information. According to the invention, the functions of recording and analyzing the user operation of the MES system and facilitating the manager to look up the audit log information are realized, and the supervision strength and the post-event tracing strength on the user operation are effectively improved.
Owner:广州中浩控制技术有限公司
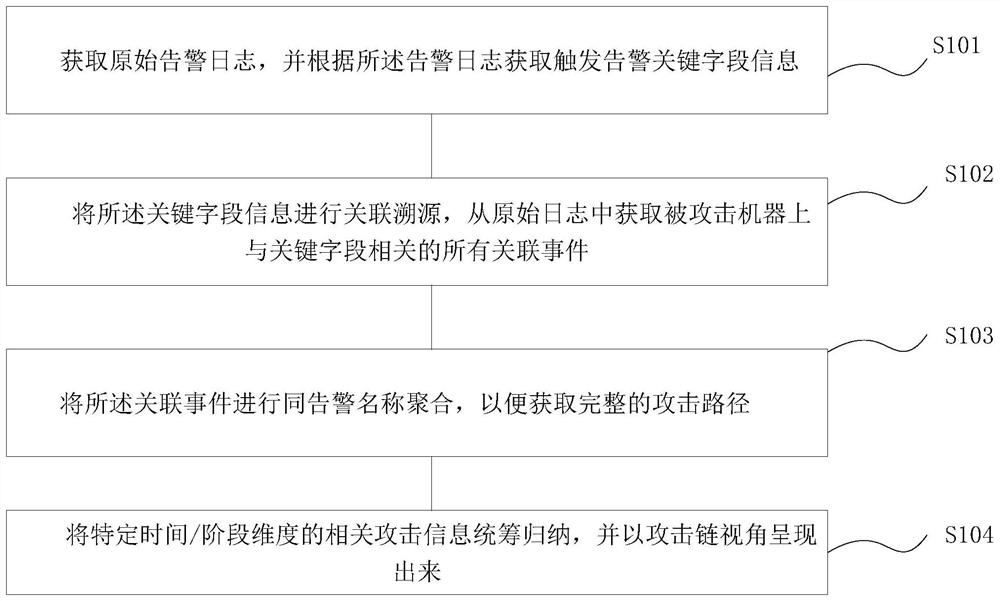
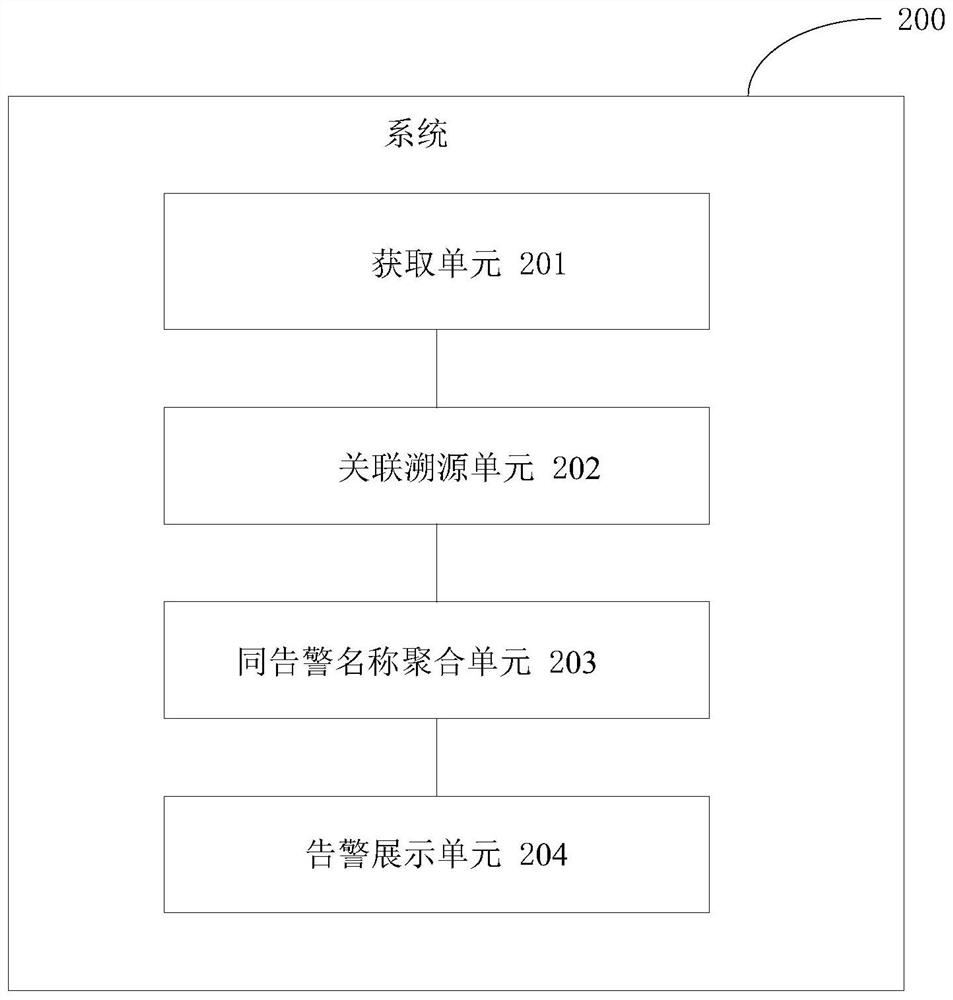
Attack event tracking and tracing method and system, terminal and storage medium
The invention provides an attack event tracking and tracing method and system, a terminal and a storage medium, and the method comprises: obtaining an original alarm log, and obtaining key field information triggering an alarm according to the alarm log; performing associated tracing on the key field information, and obtaining all associated events related to a key field on an attacked machine from an original log; aggregating the associated event with an alarm name to obtain a complete attack path; and summarizing related attack information of a specific time / stage dimension, and presenting the related attack information in an attack chain view angle. According to the invention, association traceability is carried out through the abnormal log alarm information of the attack event, the safety alarm logs are used as clues to be stringed to form real safety events, scattered safety events are associated, and the technical problems that due to existing safety alarm log checking, the laborcost is high, the tracking and tracing efficiency is low, and the tracking and tracing accuracy cannot be guaranteed are solved.
Owner:BEIJING GAS GRP
System for detecting and evaluating human-brain activity
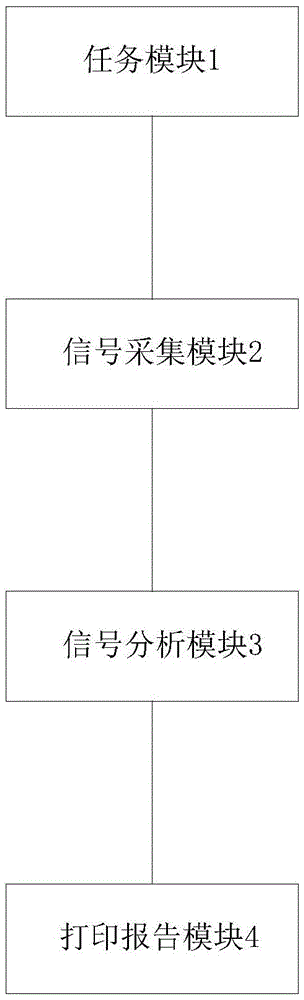
The invention provides a system for detecting and evaluating the human-brain activity, and relates to the field of brain-science information obtaining. The system comprises a signal collecting module, a signal analysis module, a task module and a report printing module. The task module is used for giving acting control orders to a tested person; the signal collecting module is respectively used for collecting blood flow signals and electroencephalogram signals of the brain during acting and transmitting the blood flow signals and the electroencephalogram signals to the signal analysis module; the signal analysis module is used for carrying out event tracing processing on the blood flow signals and the electroencephalogram signals, generating the analysis result of the brain activity according to the processed data and outputting printing signals corresponding to the analysis result to the report printing module; the report printing module is used for displaying the corresponding analysis result of the brain activity according to the received printing signals, and therefore the brain activity level and neuron damaged parts are directly and accurately obtained.
Owner:崔天利
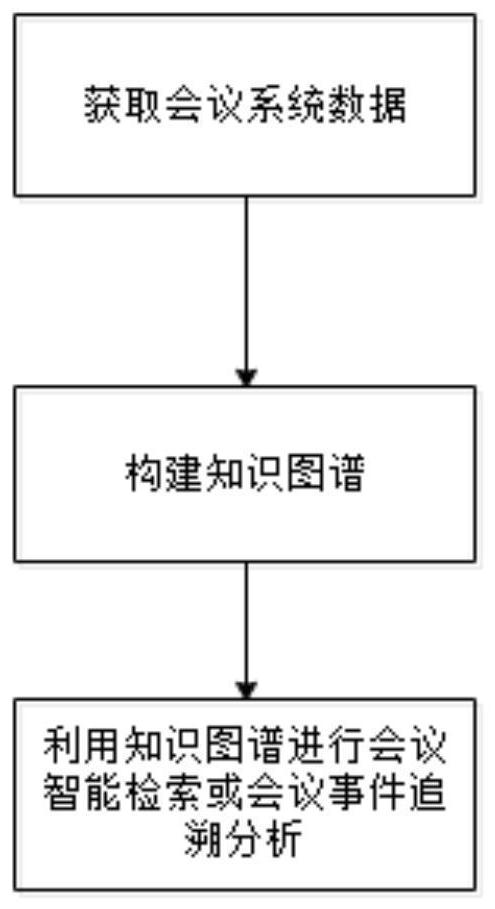
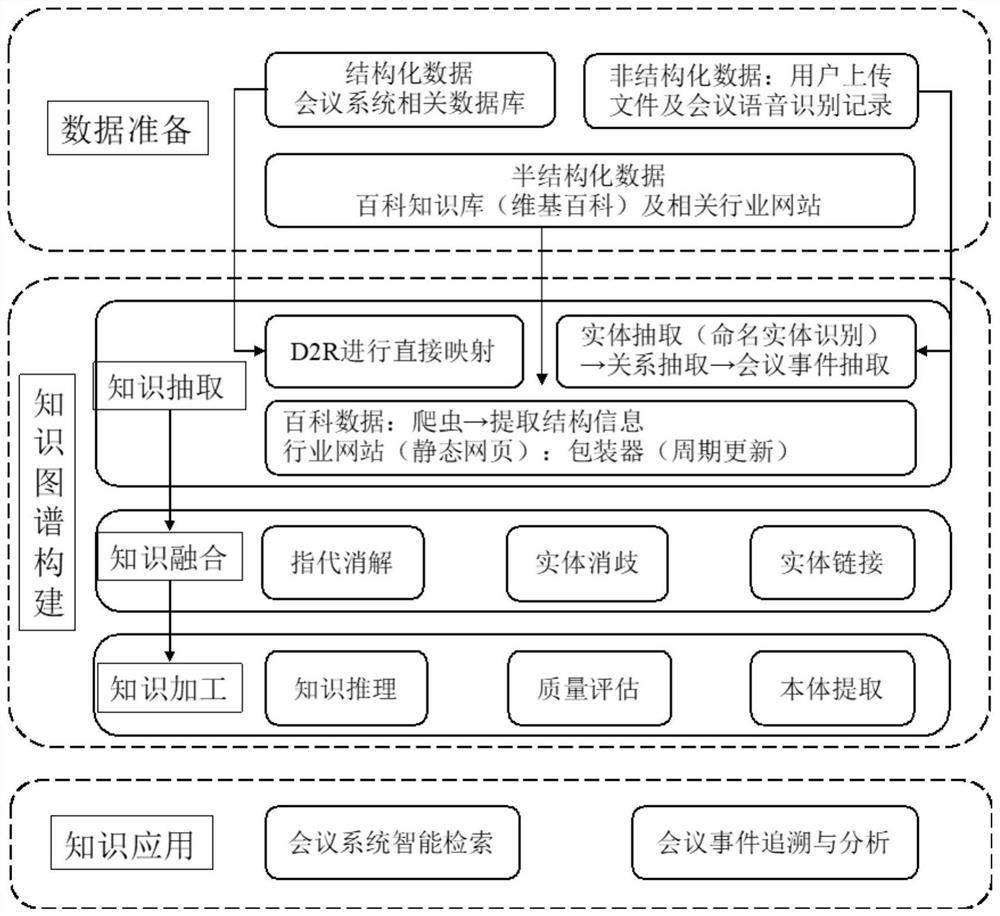
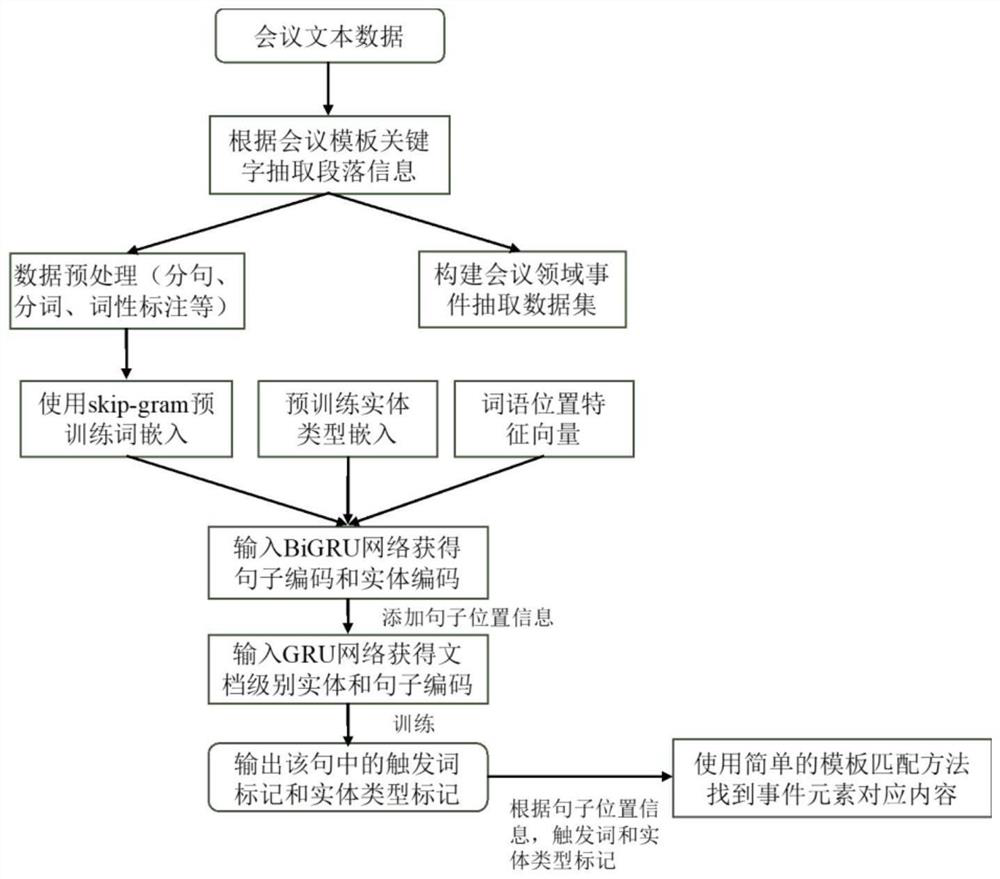
Event tracing-oriented intelligent conference analysis method
PendingCN111782800AImprove accuracySemantic analysisSpecial data processing applicationsEngineeringKnowledge graph
The invention relates to the technical field of artificial intelligence information, and in particular relates to an event tracing-oriented intelligent conference analysis method. The method comprisesthe steps of obtaining conference system data; constructing a knowledge graph; and carrying out intelligent conference retrieval or conference event tracing and analysis by utilizing the knowledge graph. Compared with the prior art, the invention provides an intelligent conference analysis method for time tracing, and further provides a knowledge graph construction method in the field of conference systems of multi-source heterogeneous data. Different types of conferences can be flexibly targeted; knowledge of a specific field is extracted from an existing open encyclopedia knowledge base; the knowledge graph for a specific conference type is constructed in combination with file data and the like provided by a conference, meanwhile, the constructed knowledge graph can help to improve theaccuracy of conference summary content and improve the accuracy of a retrieval result, and intelligent retrieval analysis can visualize the conference progress, personnel task implementation conditions and the like.
Owner:上海仪电(集团)有限公司中央研究院
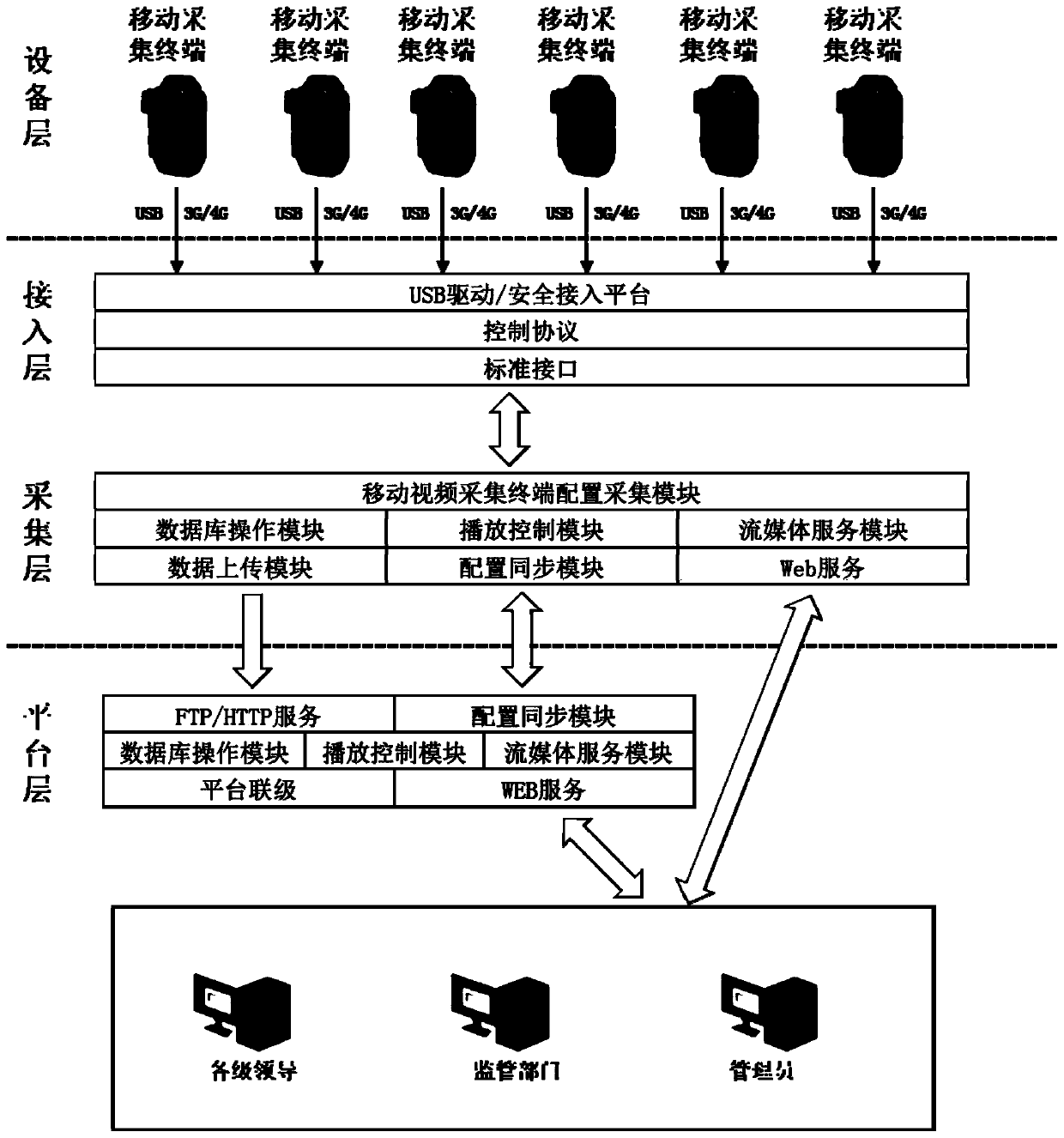
Video acquisition system for mobile operation visual regulation and control platform
InactiveCN110149493ARealize acquisitionFor long-term storageTelevision system detailsTelevision conference systemsButt jointSafety control
The invention discloses a video acquisition system for a mobile operation visual regulation and control platform, which can realize integrated use, management and safety control. The system comprisesan equipment layer, an access layer, an acquisition layer, a platform layer and a user layer, the video acquisition system is deployed in a graded manner. Data collected by the mobile collection terminal can be stored, published, retrieved, downloaded and the like; video recording marking, data analysis, evaluation and assessment and post-event tracing are realized; the video acquisition system isconnected to the mobile operation visual regulation and control platform through the access layer and is in butt joint with the mobile operation visual regulation and control platform, so that visualsupervision and management of field work tasks such as power transmission and transformation maintenance and line construction maintenance can be realized, and supervision data can be stored for a long time; and meanwhile, uploading video data provided by the platform is used as a data basis for work normative comparison and inspection of workers and a data evidence for on-site safety responsibility analysis. And popularization and application in the field of electric power overhaul are facilitated.
Owner:STATE GRID XINJIANG ELECTRIC POWER CO URUMQI ELECTRIC POWER SUPPLY CO
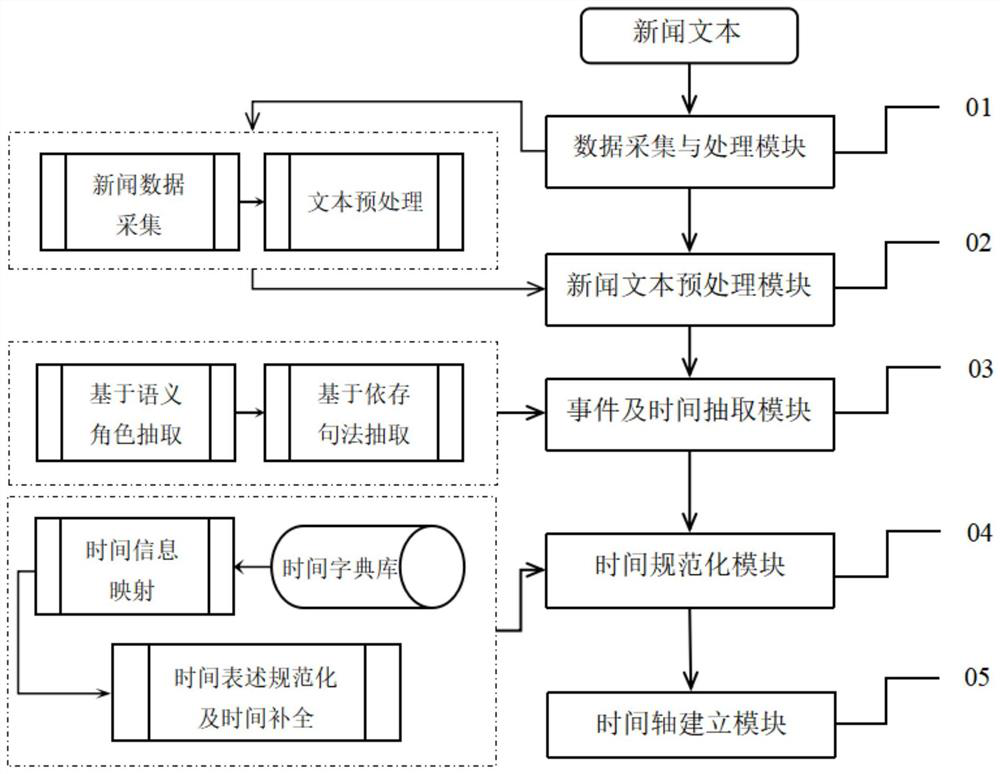
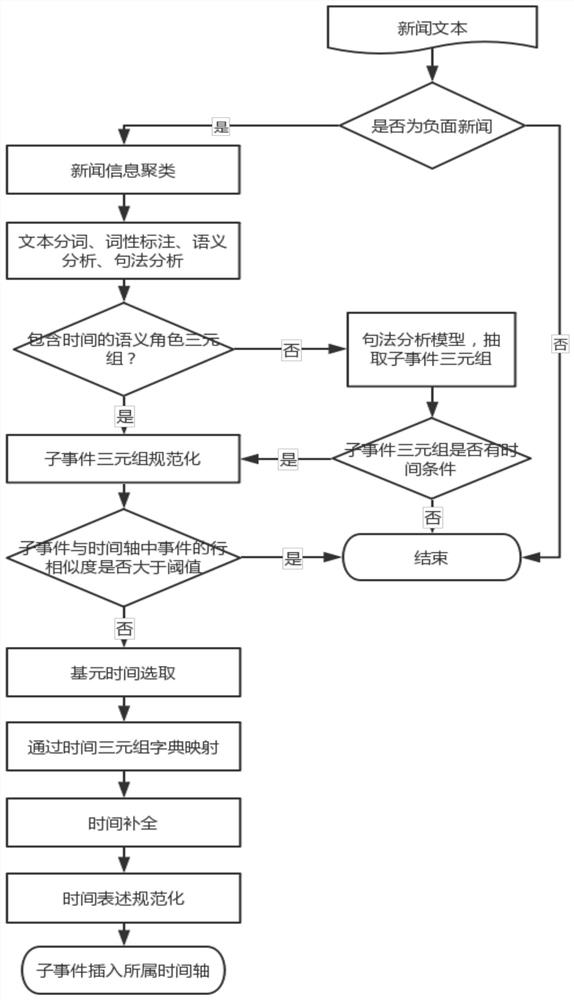
News text event and time extraction and standardization system for event tracking
The invention aims to provide a news text event and time extraction and standardization system for event tracking. The news text event and time extraction and standardization system comprises a data acquisition and processing module (01), a news text preprocessing module (02), an event and time entity extraction module (03), a time standardization module (04) and a time axis establishment module (05); the invention comprises the following steps: firstly, carrying out clustering, part-of-speech tagging and other preprocessing on texts, then carrying out sub-event extraction and standardizationon the processed texts, carrying out similarity detection on standardized sub-events, carrying out time extraction and standardization on non-repetitive events, and finally, inserting new sub-events into an event time axis to which the new sub-events belong so as to complete continuous tracking of the events. When the time is normalized, the selection of the primitive time is not only limited to the current text, but is continuously associated with the preorder event of the event, so that the primitive time acquired by the method is more accurate.
Owner:HANGZHOU XUJIAN SCI & TECH CO LTD
Block based incremental backup from user mode
ActiveUS9268647B1Input/output to record carriersFile access structuresIncremental backupOperating system
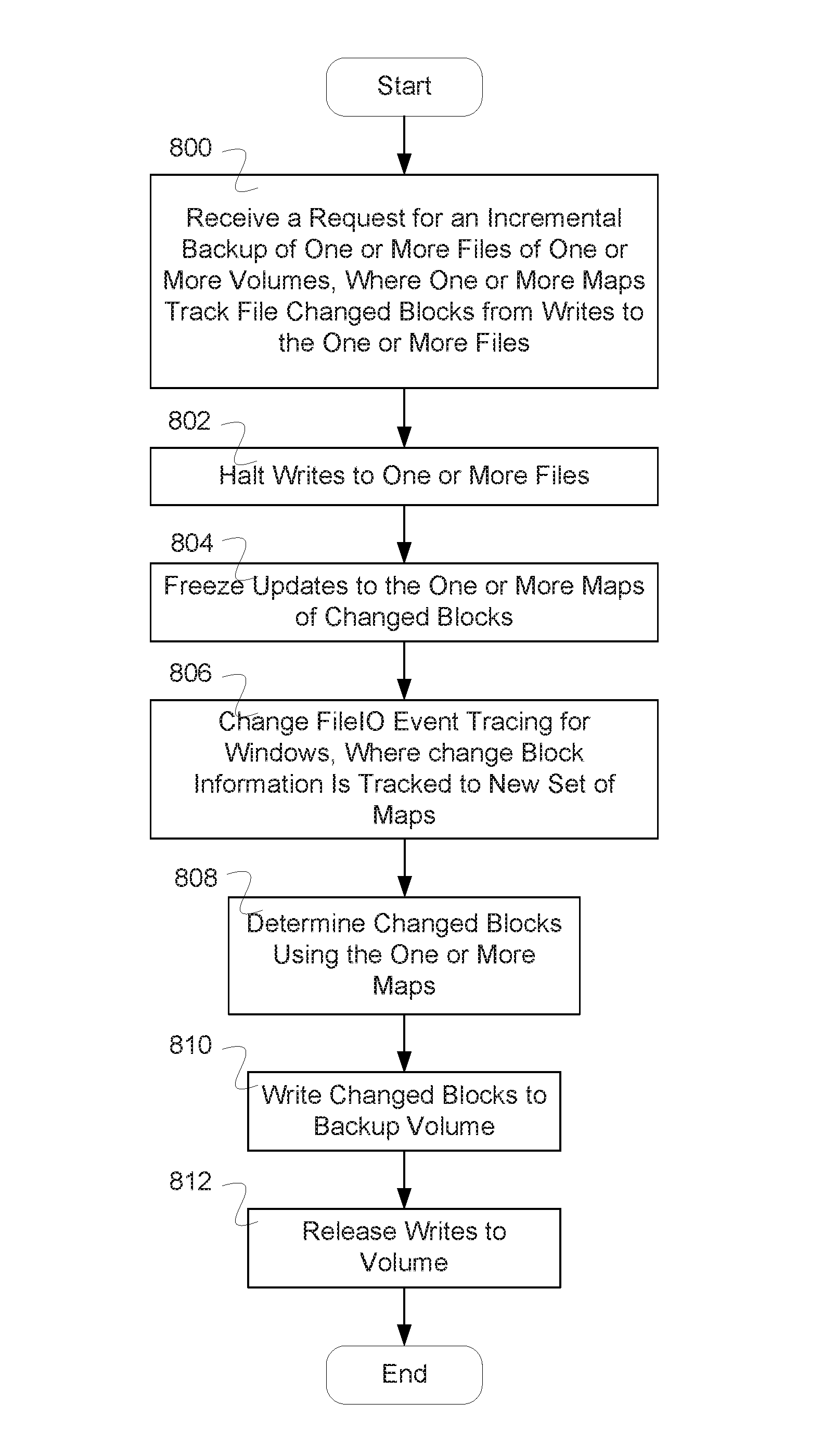
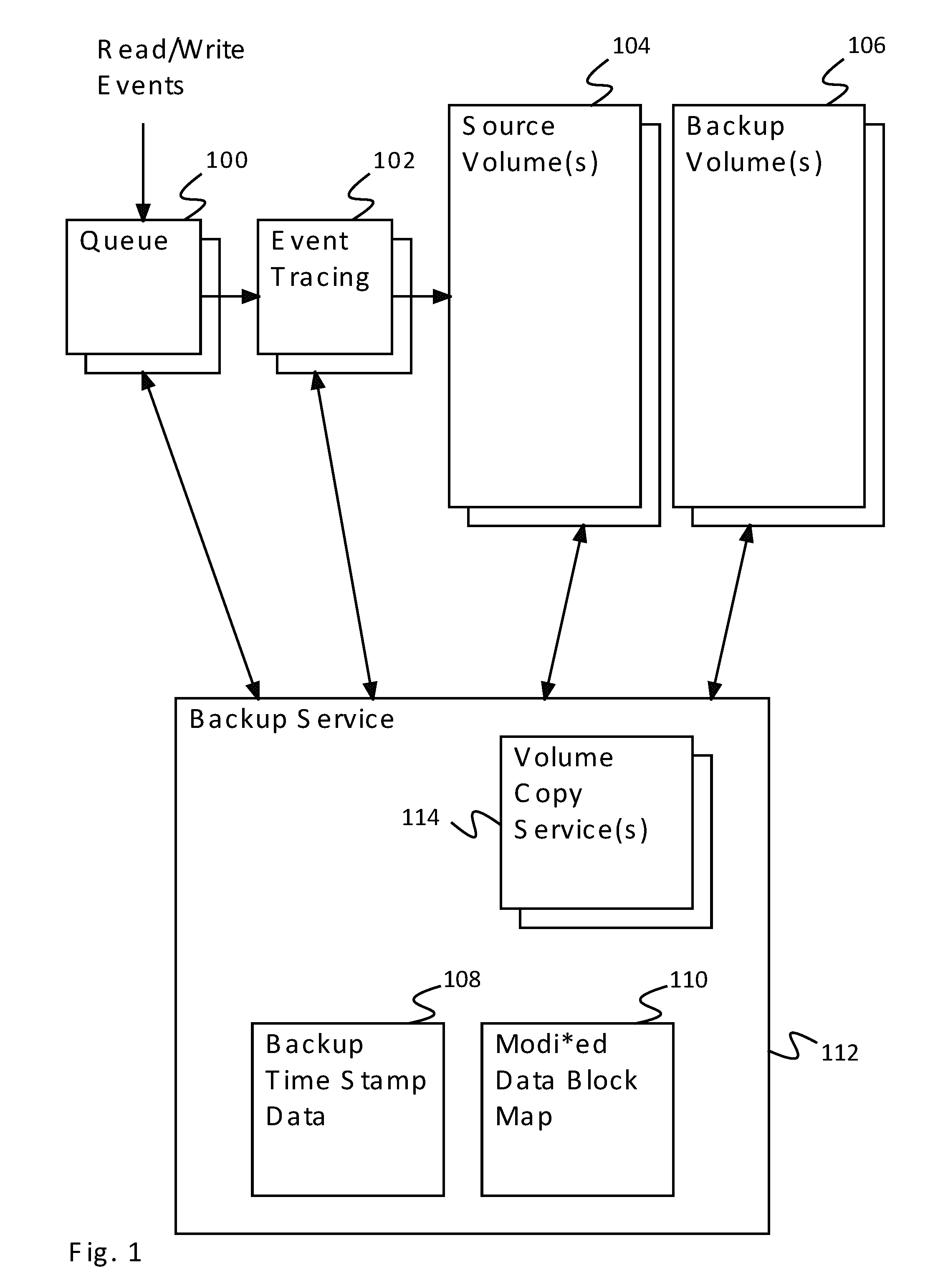
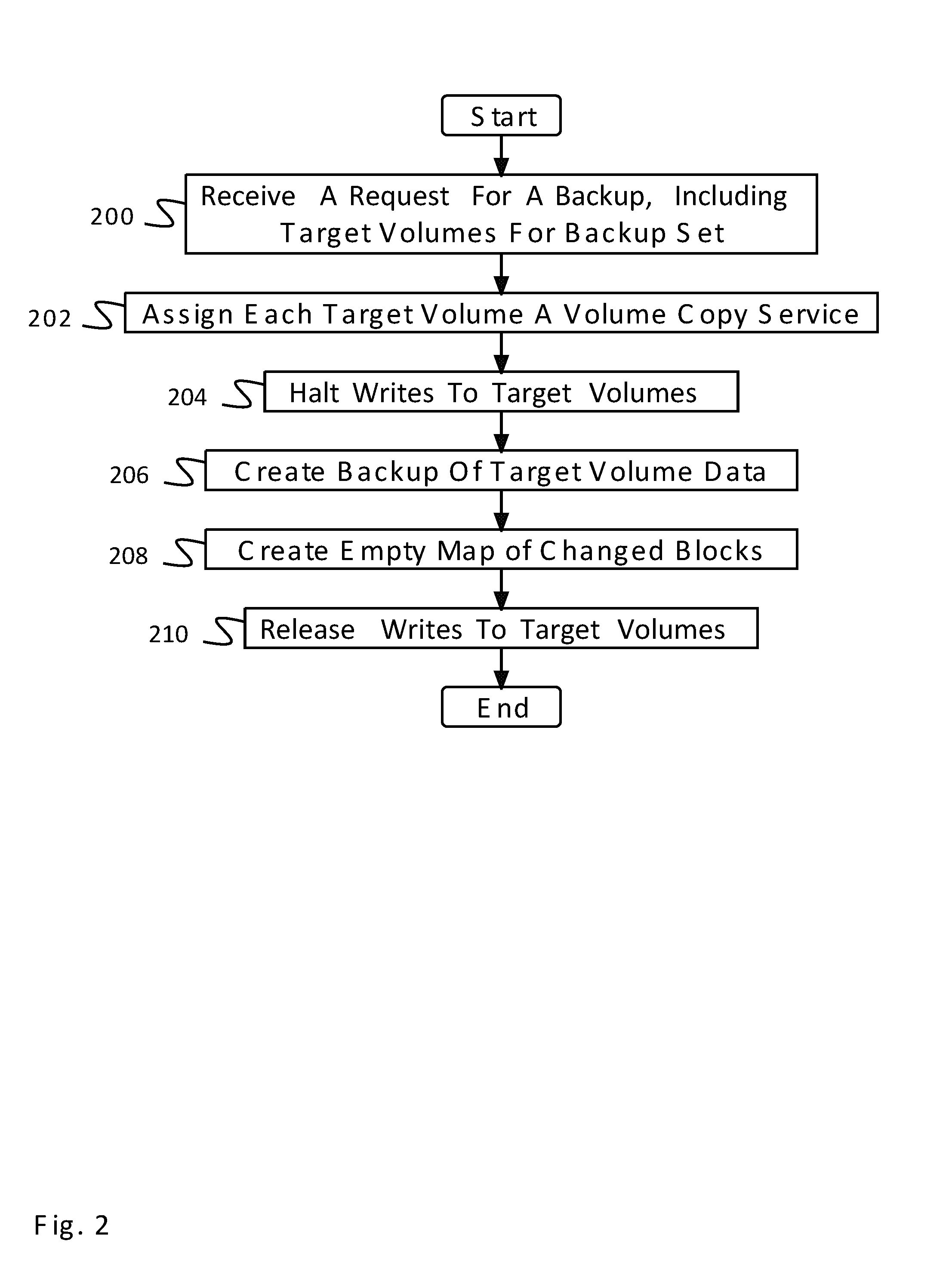
A system for incremental backup comprises a storage device and a processor. The processor is configured to: 1) start Event Tracing for Windows tracking, to track changed block information in one or more maps, where each of the one or more maps tracks writes indicated via a node; 2) receive request for an incremental backup of a volume of one or more volumes, wherein the one or more maps track changed blocks from writes to the volume; 3) halt writes to the volume and queue writes to the volume after halting; 4) freeze the one or more maps of changed blocks; change Event Tracing for Windows tracking, wherein the change block info is tracked to a new set of maps; 5) determine changed blocks using the one or more maps; 6) write changed blocks to a backup volume; and 7) release writes to the volume.
Owner:EMC IP HLDG CO LLC
Public event tracking method and device, computer equipment and computer readable medium
PendingCN112328856AImprove efficiencyQuality improvementWeb data indexingSemantic analysisData displayEvent data
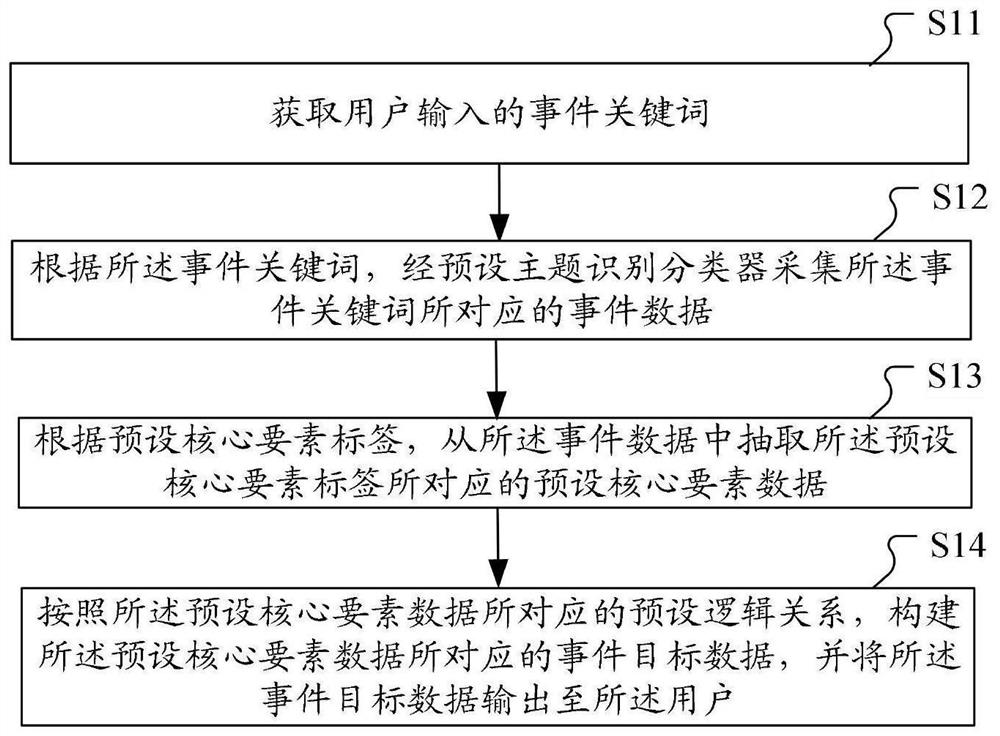
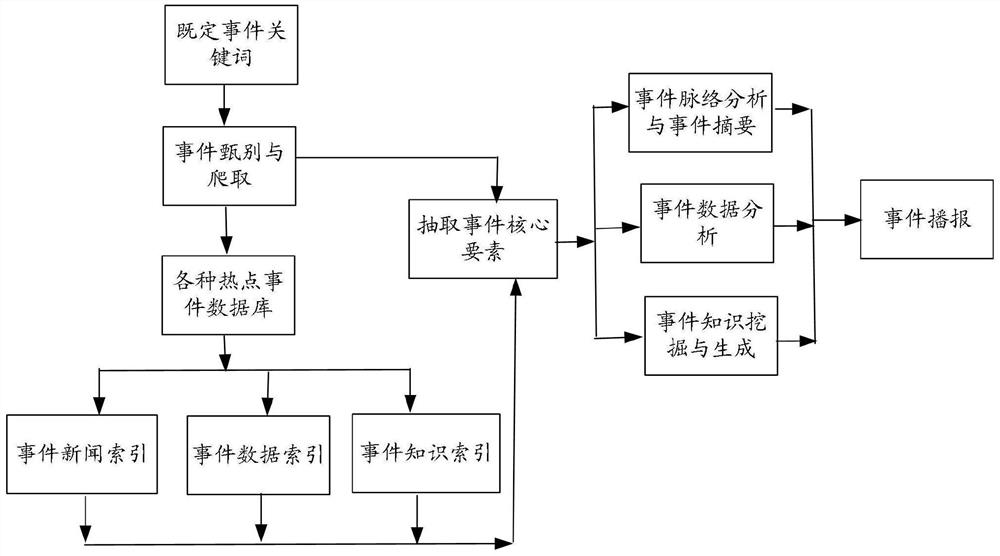
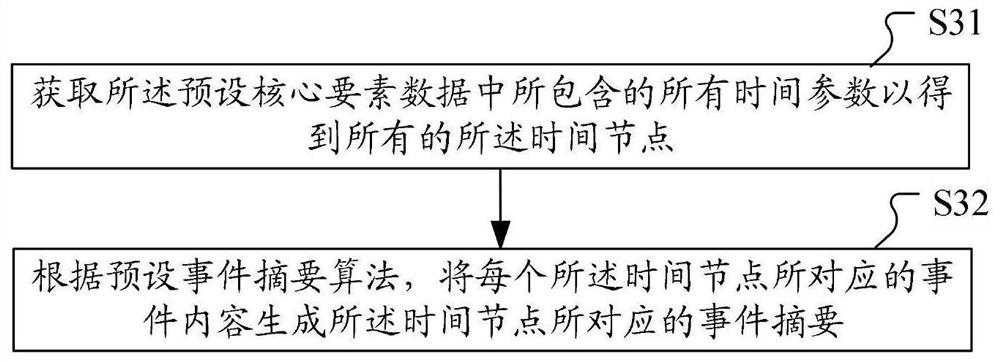
The invention belongs to the technical field of data display, and provides a public event tracking method and device, computer equipment and a computer readable storage medium. The method comprises the steps of obtaining event keywords input by a user, collecting event data corresponding to the event keywords through a preset theme recognition classifier according to the event keywords, extractingpreset core element data corresponding to the event data from the event data according to a preset core element label, and obtaining the event data corresponding to the event data according to the preset core element data. And according to a preset logic relationship corresponding to the preset core element data, constructing event target data corresponding to the preset core element data, and outputting the event target data to the user, so that large events can be tracked through keywords, the event tracking efficiency and quality are improved, and the manual event tracking cost is reduced.
Owner:CHINA PING AN LIFE INSURANCE CO LTD
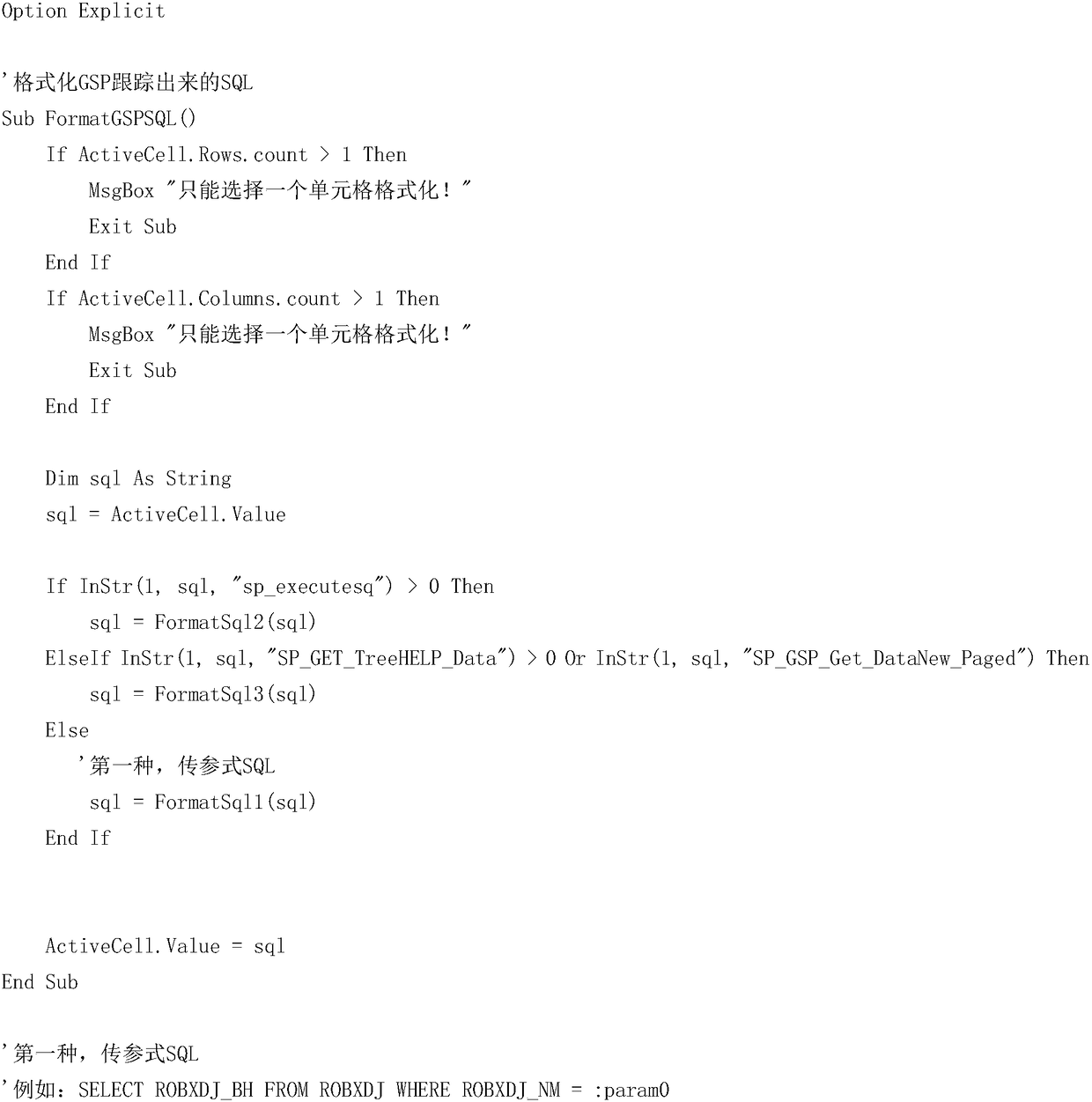
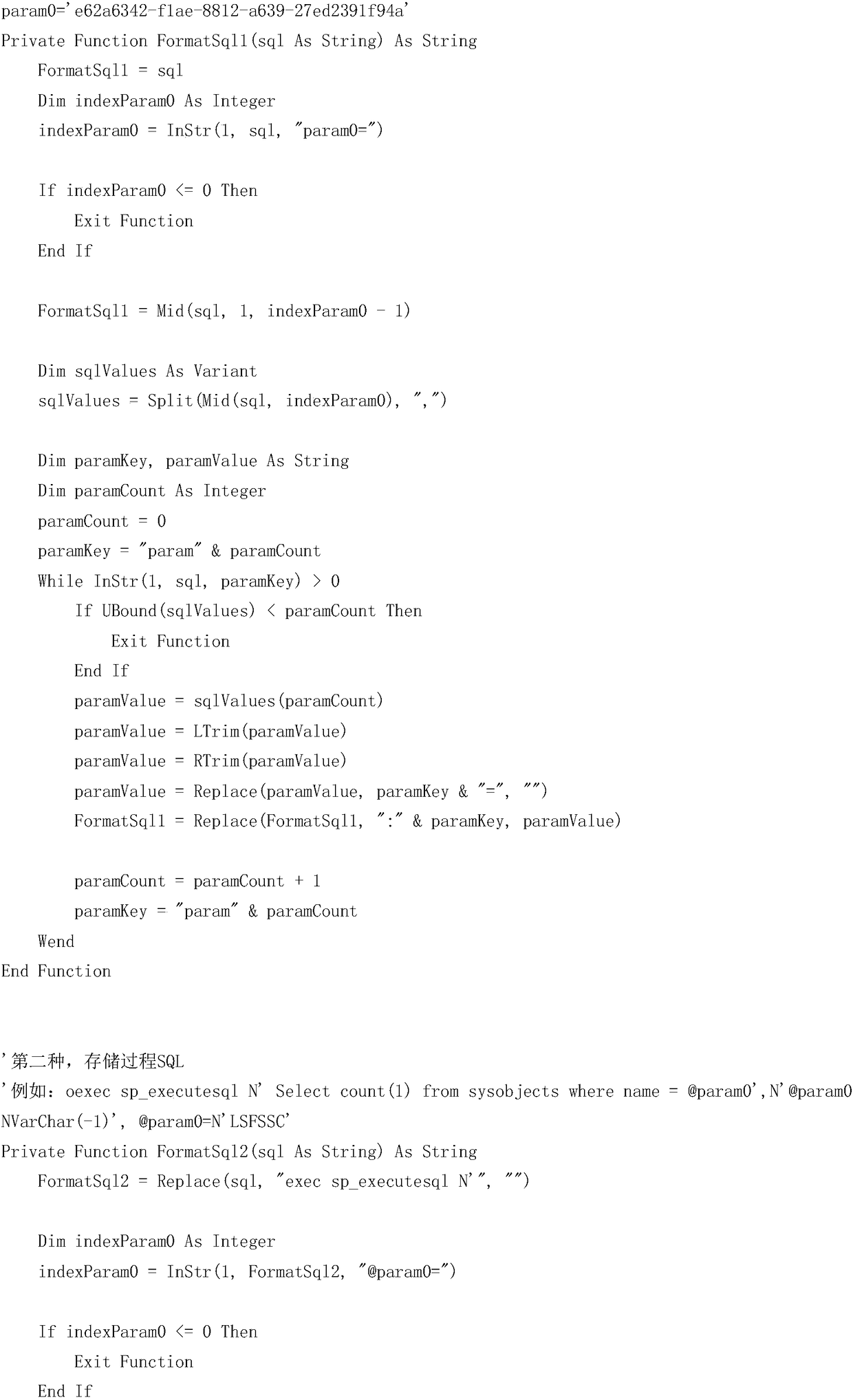
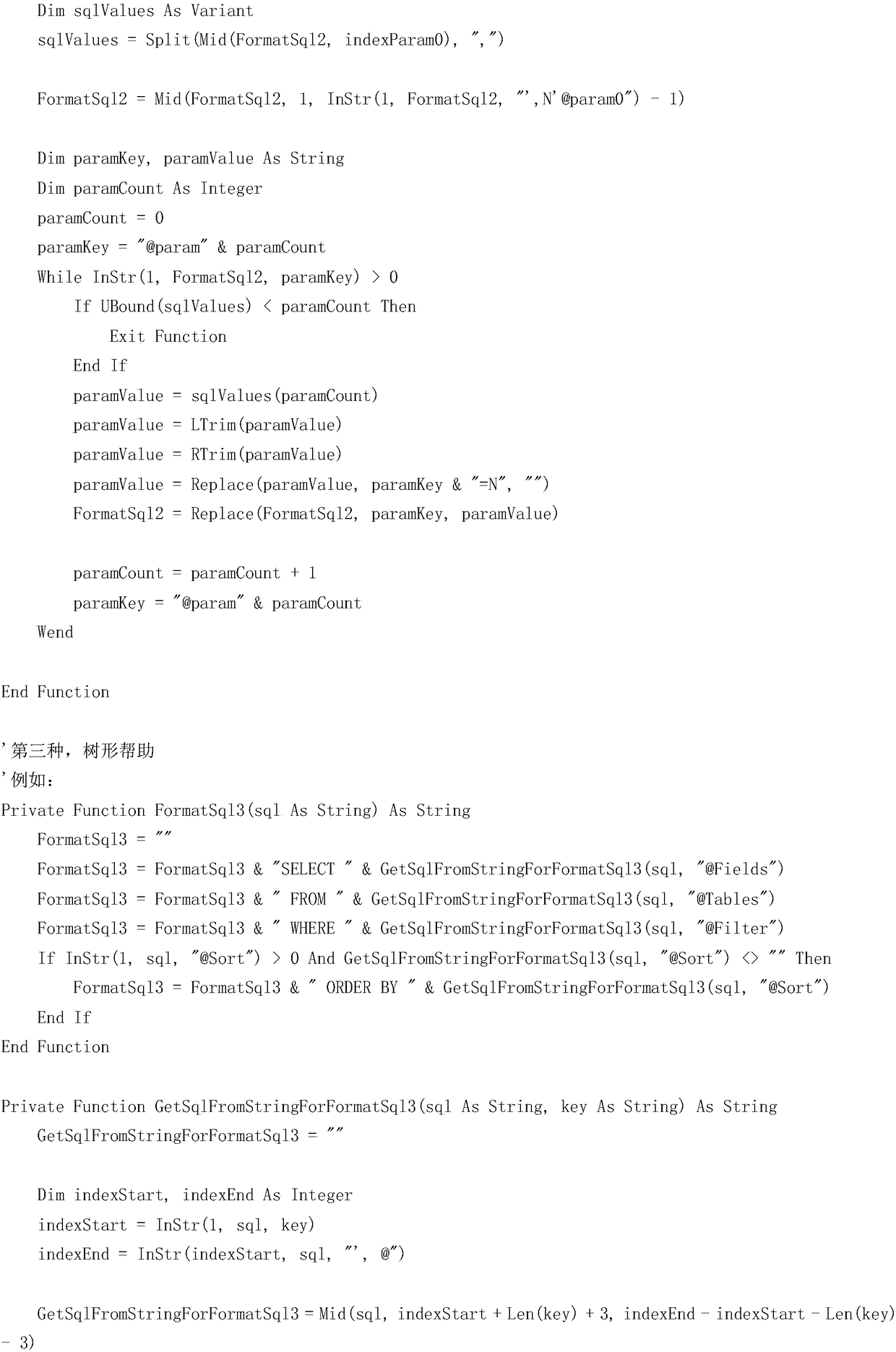
Implementation method for automatically converting and executing parameterized SQL based on Excel
InactiveCN108664236AImprove maintenance efficiencyReduce complicated stepsProgramming languages/paradigmsSpecial data processing applicationsSQLHuman language
The invention provides an implementation method for automatically converting and executing parameterized SQL based on Excel, belongs to technical field of computer applications, the performance of a automatic conversion SQL can help developers to execute the SQL language quickly, convert basic parameterized SQL, stored process SQL, tree help, etc, tracked by the event tracker into executable SQL quickly, and can connect the database to execute directly and check result. Project research and development and maintenance efficiency. The invention is good in use effect in EPR system project maintenance, and is also suitable for other systems.
Owner:SHANDONG INSPUR GENESOFT INFORMATION TECH CO LTD
Multi-source network security alarm event tracing and automatic processing method and device
The invention discloses a multi-source network security alarm event tracing and automatic processing method and device. The method comprises the following steps: acquiring security log data; identifying the IP of the security log data, and dividing the security log data into corresponding index categories according to the IP correspondence; when the index category is the Internet, acquiring an attack source IP; when the index category is a terminal, acquiring an attacked source IP; judging whether the attack source IP or the attacked source IP is forbidden or not according to a risk assessment result; and when the risk assessment result is a risk, controlling the firewall to forbid the attack source IP or the attacked source IP. The invention aims to provide the multi-source network security alarm event tracing and automatic handling method and device, so that the energy, the alarm missing report rate and the false alarm rate of security operation and maintenance personnel in handling the security alarm event are reduced, and the security alarm handling efficiency is improved.
Owner:INFORMATION & TELECOMM COMPANY SICHUAN ELECTRIC POWER
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com