Attack event tracing method and device, electronic equipment and storage medium
An attack event and attacker technology, applied in the field of network security management, can solve the problems such as the inability to effectively trace the source of APT attacks, the difficulty of accurately locating the attacker, and the ability to save equipment for a long time.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
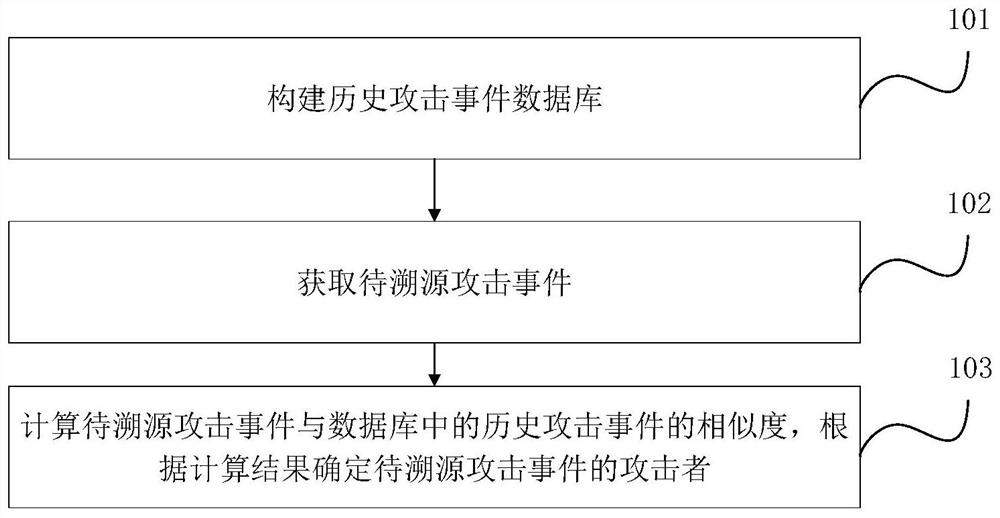
[0024] Figure 1(a) is a flow chart of the method for tracing the source of an attack event provided by Embodiment 1 of the present invention. This embodiment is applicable to the case of tracing the source of an APT attack event. This method can be implemented by the device for tracing the source of an attack event in the embodiment of the present invention. For execution, the device may be implemented in software and / or hardware. As shown in Figure 1(a), the method specifically includes the following operations:
[0025] Step 101, constructing a database of historical attack events.
[0026] Wherein, the historical attack event database includes multiple historical attack events, and the dimension information of each historical attack event and known attackers.
[0027] Specifically, in this embodiment, a historical attack event database can be constructed based on recently captured historical attack events, and the dimension information and attackers of each historical even...
Embodiment 2
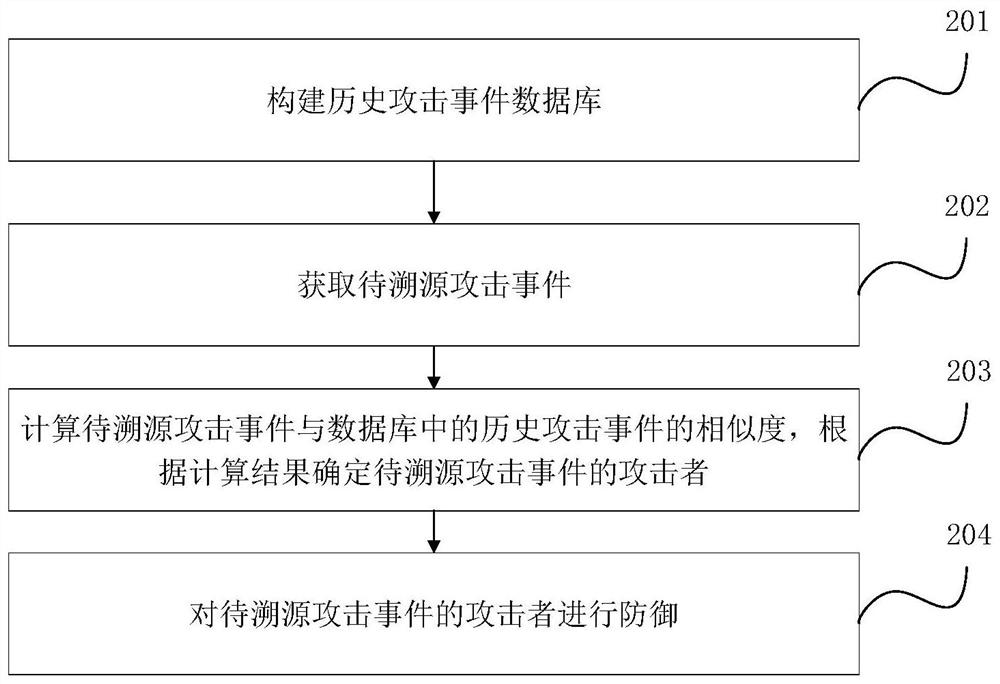
[0049] figure 2 The flow chart of the method for tracing the source of an attack event provided by Embodiment 2 of the present invention is based on the above-mentioned embodiment in Embodiment 1. In this embodiment, after the attacker of the attack event to be traced is determined, the attack event to be traced is also included. attackers to defend against. Correspondingly, the method in this embodiment specifically includes the following operations:
[0050] Step 201, constructing a database of historical attack events.
[0051] Step 202, acquiring the attack event to be traced.
[0052] Step 203, calculating the similarity between the attack event to be traced and the historical attack events in the database, and determining the attacker of the attack event to be traced according to the calculation result.
[0053] Step 204, defend against the attacker of the attack event to be traced.
[0054] Specifically, after the attacker corresponding to the attack event to be tra...
Embodiment 3
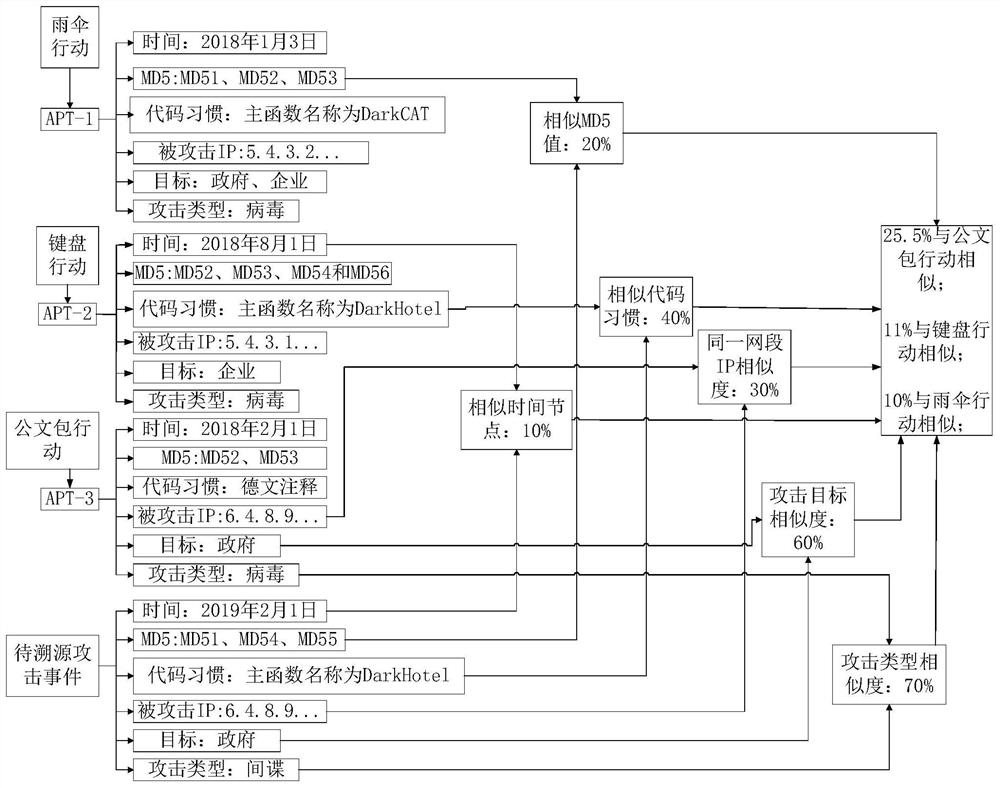
[0057] image 3 It is a structural schematic diagram of an attack event source tracing device provided by Embodiment 3 of the present invention, the device includes: a historical attack event database construction module 310 , an attack event acquisition module 320 to be traced and an attacker source tracing module 330 .
[0058] The historical attack event database construction module 310 is used to construct the historical attack event database, wherein the historical attack event database contains a plurality of historical attack events, and the dimension information of each historical attack event is known to the attacker; the attack event acquisition module to be traced 320, used to obtain the attack event to be traced; the attacker source tracing module 330, used to calculate the similarity between the attack event to be traced and the historical attack events in the database, and determine the attacker of the attack event to be traced according to the similarity calculat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com