Method for performing identity authentication and file encryption and decryption based on fingerprint UsbKey
An identity authentication, encryption and decryption technology, applied in the field of identity authentication and file encryption and decryption based on fingerprint UsbKey, can solve the problems of small cracking, easy password cracking, and troublesome application operation, so as to improve the identification method and realize encryption protection. , the effect of easy authentication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
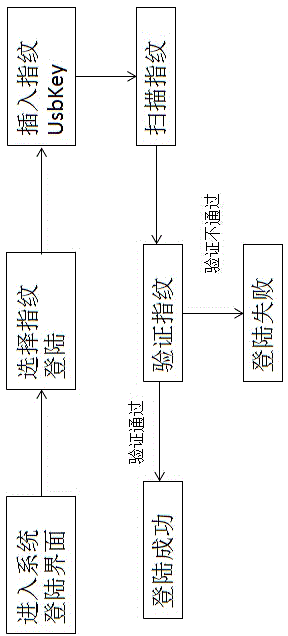
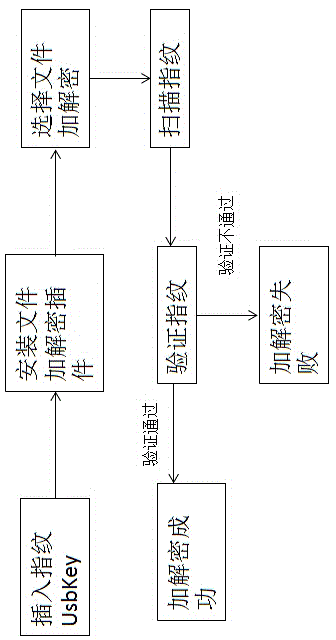
[0034] The present invention will be described in detail below through specific embodiments and accompanying drawings. The present invention is a method for identity authentication and file encryption and decryption based on fingerprint UsbKey. In the server security environment, since the password and key file are stored in the server file, it is easy to forget or lose. Once lost, it may not be possible to log in. to the security management platform or unable to use encrypted files, causing losses to customers. Therefore, in the process of identity authentication and file encryption and decryption, using the fingerprint of the administrator will not cause the situation of forgetting and losing, and if the administrator changes, it can be reconfigured through the UsbKey management software, realizing safe and convenient Identity authentication and file encryption and decryption methods.
[0035] Working principle of the present invention:
[0036] 1. During identity authenti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com