Safe address allocation method, detecting device, detecting equipment and detecting system
A technology of detection device and distribution method, applied in the field of data communication, can solve the problems of difficulty in being discovered, control failures such as inspection and binding, and inability to discover access equipment, and achieve the effect of preventing illegal operations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
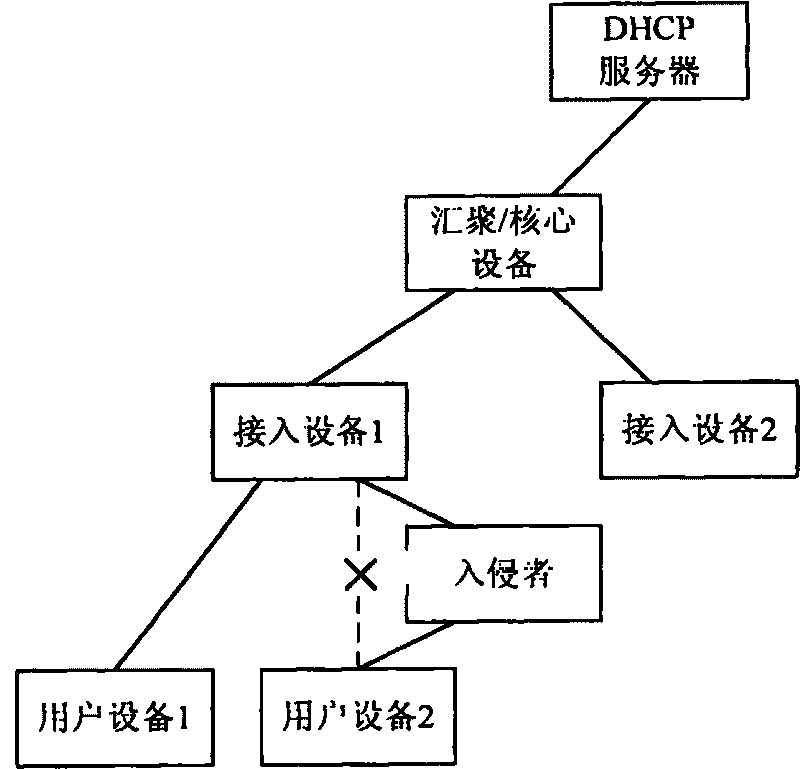
[0057] The purpose of the embodiments of the present invention is to provide a safe address assignment method, detection device, detection equipment, user equipment, DHCP server and a safe address assignment system, so that the DHCP server can safely assign an IP address to a DHCP client to prevent illegal Users steal IP addresses and MAC addresses of legal users to conduct illegal operations.
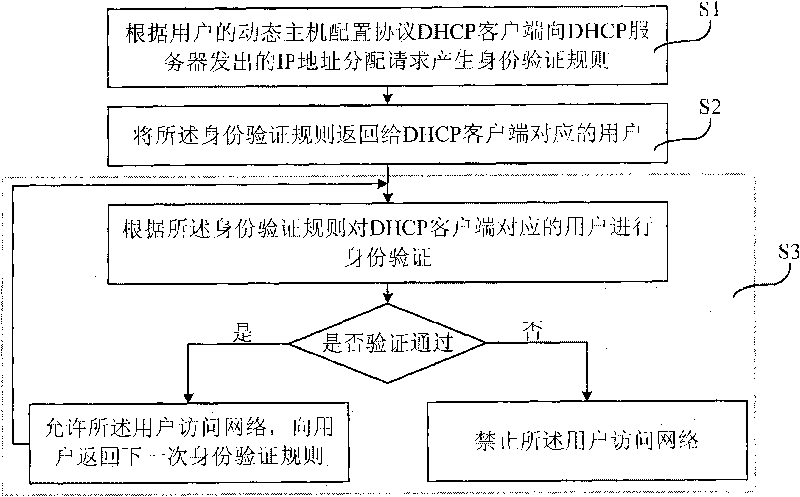
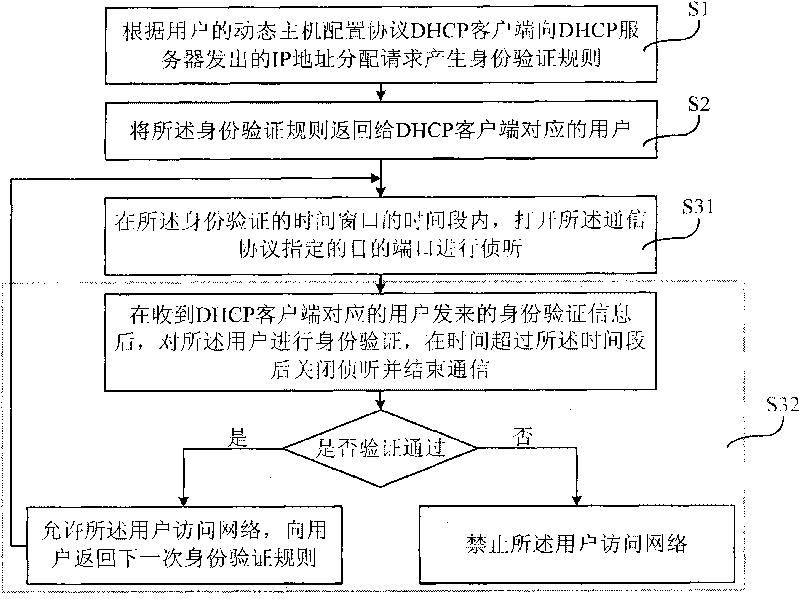
[0058] The following describes the embodiments of the present invention in conjunction with the accompanying drawings. The embodiments of the present invention provide a secure address allocation method, figure 2 A schematic diagram of Embodiment 1 of a secure address allocation method of the present invention is given, and the method includes:
[0059] Step S1, generating identity verification rules according to the IP address allocation request sent by the user's Dynamic Host Configuration Protocol DHCP client to the DHCP server;
[0060] Step S1 may specifically be: generating an ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com