Information processing method and device
An information processing method and equipment technology, which is applied in the field of network security, can solve problems such as multiple heterogeneous executives' consistent collaborative attack vulnerabilities, computer equipment user losses, etc., so as to avoid illegal operations and ensure safe and stable operation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
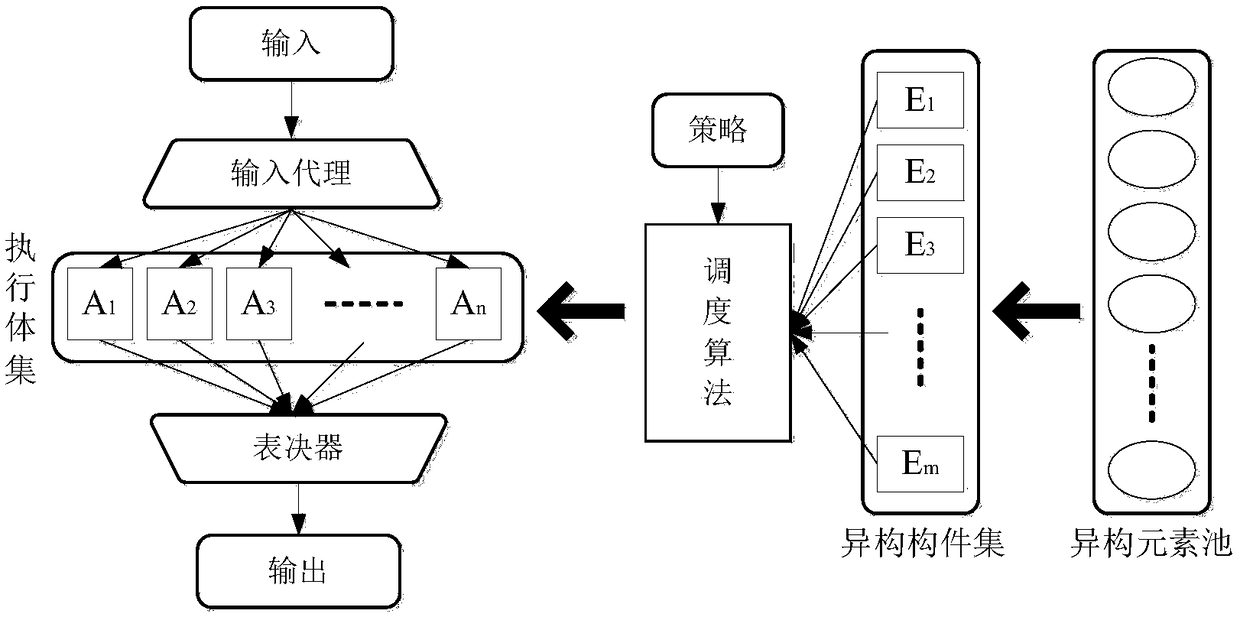
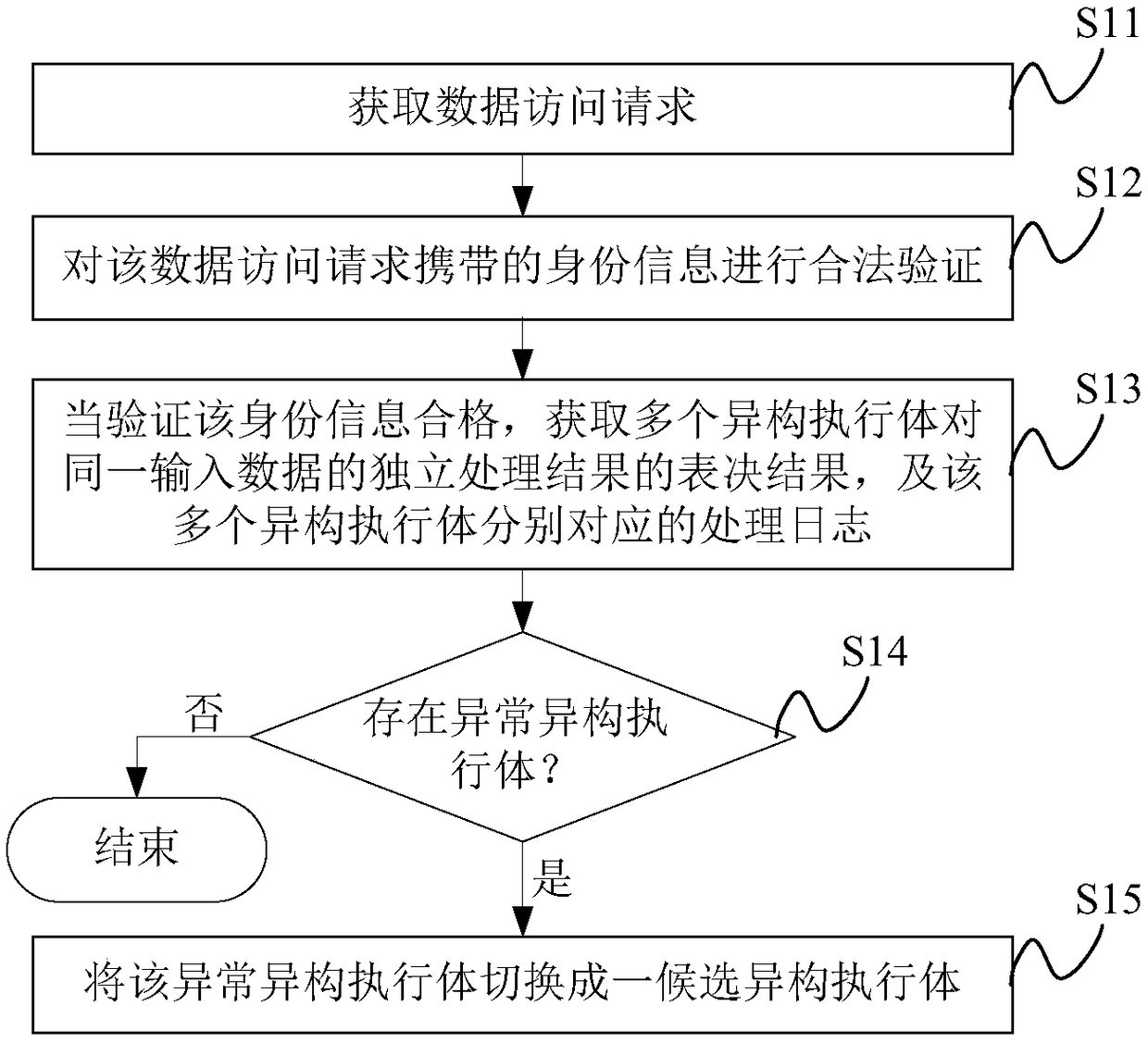
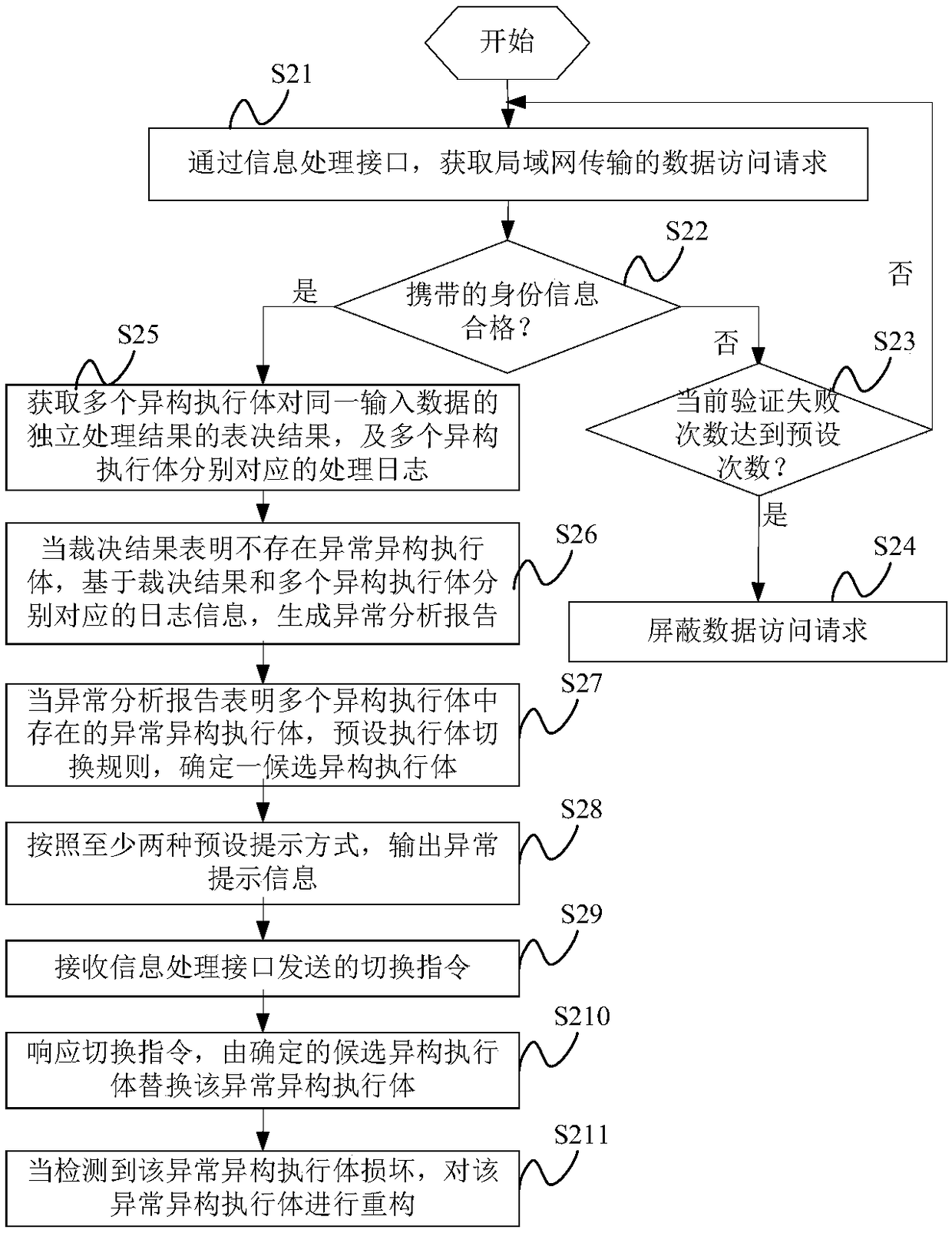
[0054] The inventors of the present invention have found that: in the mimic defense system based on Dynamic Heterogeneous Redundancy (DHR), since the heterogeneous executive bodies in the Dynamic Heterogeneous Redundancy architecture can be independent of each other, there is a certain degree of The components are the same, and there are no strict reliability and security requirements for heterogeneous executives, allowing heterogeneous executives to "poisonously carry bacteria". Once the configuration in the system is wrong, it is difficult to overcome the influence of uncertain factors and form a consensus However, its mimic defense system cannot detect and deal with such vulnerabilities, that is, the defense function of the system fails, which will lead to attackers obtaining some of the computer equipment's Sensitive data or administrator privileges, leading to a complete compromise of the system of the computer device.
[0055]Among them, system management configuration e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com