Method and system for identity authentication and encryption of industrial user
A technology for identity authentication and industrial users, applied in transmission systems, digital transmission systems, and key distribution, can solve problems such as the inability to guarantee the authenticity of data packets and low security of data transmission, to ensure operation rights, solve low security, The effect of ensuring safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
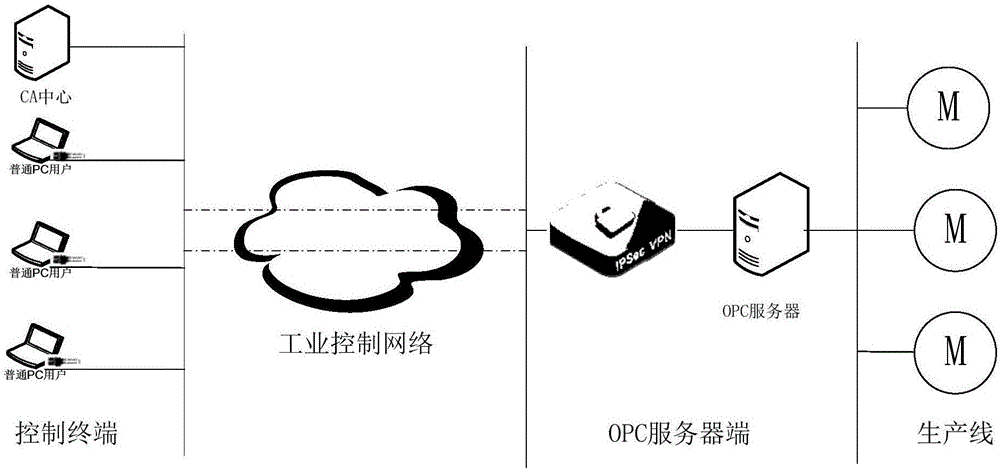
[0055] The system for implementing industrial user identity authentication and encryption in Embodiment 1 includes hardware devices and related software. Hardware devices include: encryption gateway, electronic key, user terminal equipment, authentication server; related software includes: client software and gateway software.
[0056] The client software is installed on the user terminal device. When using the client software, the user needs to insert an electronic key. Each electronic key can only be bound to one terminal device. The user terminal device can read data from the electronic key; the gateway device Two-way information exchange with user terminal equipment; two-way information exchange between user terminal equipment and authentication server.
[0057] The electronic key is uniformly managed by the certificate authority center. Each electronic key contains a user certificate and integrates the relevant encryption algorithm approved by the State Cryptography Admin...
Embodiment 2
[0071] The structure of the system for realizing industrial user identity authentication and encryption in Embodiment 2 is the same as that in Embodiment 1, the only difference is that the authentication server is an OCSP authentication server, and the user certificate adopts an online authentication method.
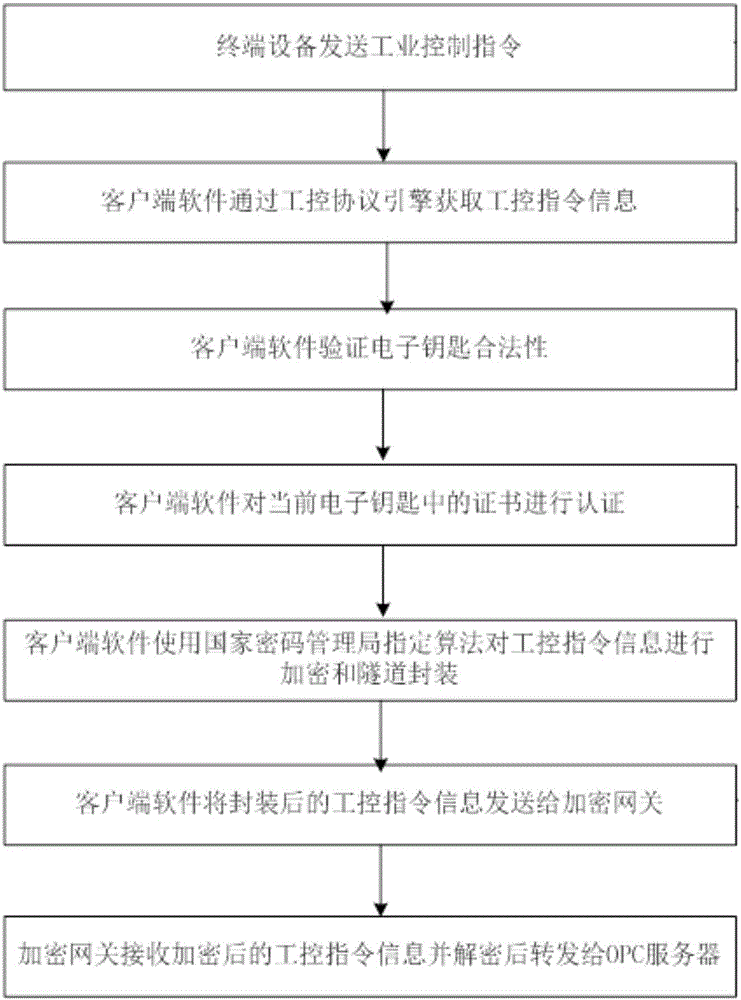
[0072] The flow of information transmission using the industrial user identity authentication and encryption system is as follows: figure 2 As shown, specifically:
[0073] Step 1: The user terminal device sends an industrial control command;
[0074] Step 2: The client software obtains the industrial control instruction information by using the industrial control protocol engine integrated in the client software;
[0075] Step 3: The client software calculates the hardware code of the user terminal device, and then reads the bound hardware code in the electronic key for comparison. If they are consistent, perform step 4; otherwise, terminate the current operation;
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com