Method and device for shielding unauthorized users from starting software
A user-unauthorized technology, applied in computer security devices, internal/peripheral computer component protection, program/content distribution protection, etc., to ensure security and effectiveness, and avoid illegal reading
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
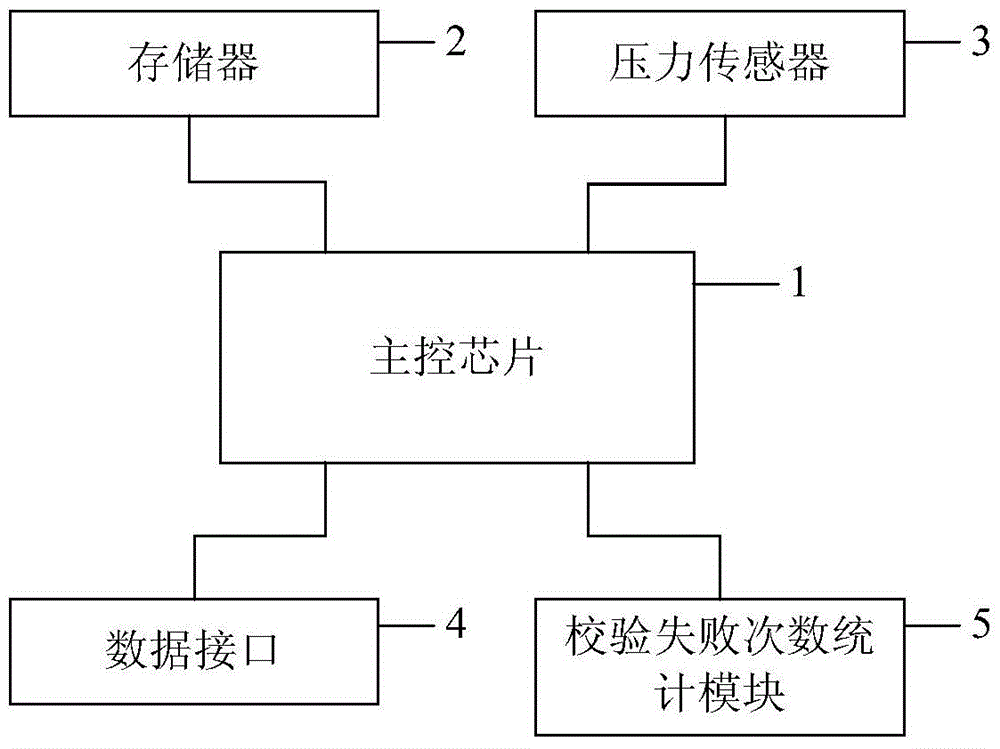
[0033] like figure 1 As shown, the present invention provides a device for shielding unauthorized users from starting software. In this embodiment, the device is a USBKEY, which mainly includes a main control chip 1, a memory 2 and a pressure sensor 3 respectively connected to it. , data interface 4, counting module 5 of times of verification failures.
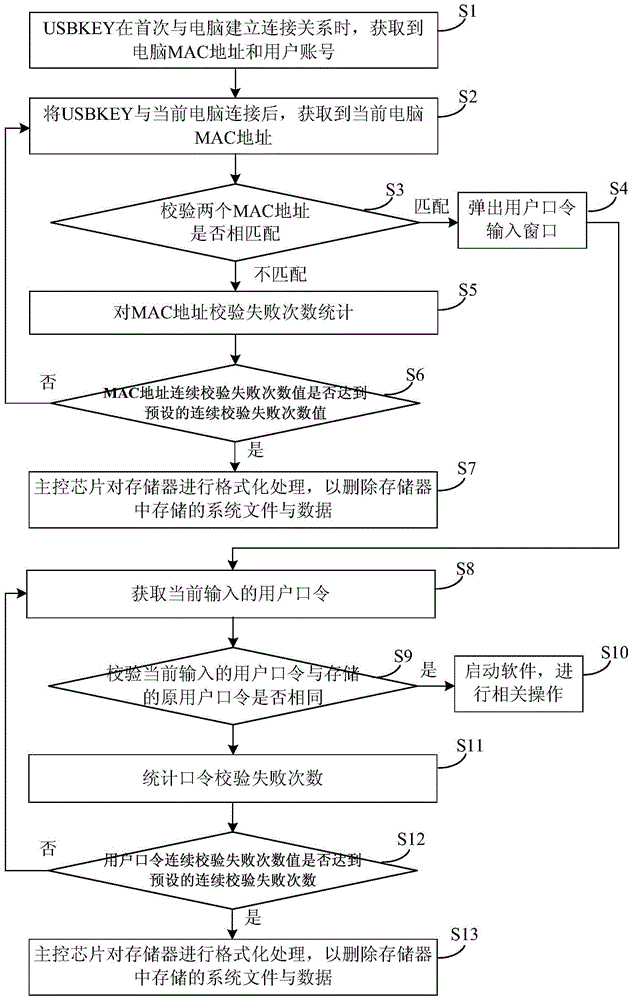
[0034] The data interface is a USB Mini interface. When the USBKEY establishes a connection relationship with the computer for the first time, the transmission obtains the computer MAC address through the driver software in the computer. When the USBKEY establishes a connection relationship with other computers, the transmission obtains the current computer MAC address through the driver software in the current computer. In addition, when the current computer MAC address is the same as the original computer MAC address stored in the memory, it is used to transmit the currently input user password to the USBKEY.
[0035] The ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com