External data transmission method for cloud computing system
A technology for external data and transmission methods, applied in the information field, can solve problems such as inability to meet security requirements, and achieve the effects of increasing difficulty and cost, preventing illegal copying, and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
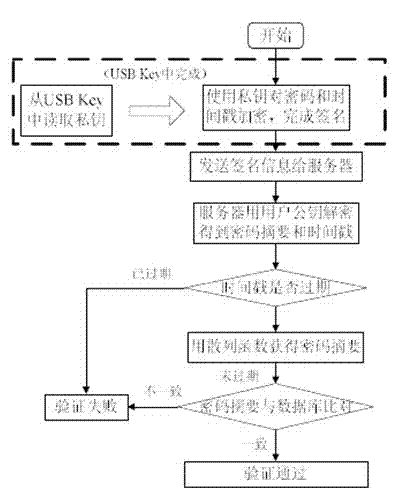
[0019] The external data transmission method of the cloud computing system of the present invention is a USB device-based identity authentication and data encryption method with higher security.
[0020] An embodiment of this technical solution requires USB Key, a hardware device with a USB interface, whose shape is no different from that of a common U disk, but its internal structure is not so simple. The processor, random access memory RAM and the operating system solidified in the read-only memory can store the user's private key, use the built-in signature algorithm to realize the authentication of the user's identity, ensure the security of the data, and achieve the purpose of identifying the identity of the authorized person. The USB Key completes the encryption operation in the card, which ensures the security of the key and prevents the illegal copying of the key. At the same time, combined with the physical anti-tampering technology, it greatly increases the difficulty...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com