Smart card and USB combined equipment and method of self-destroy forillegal access and try to pass valve value
A composite device and illegal access technology, which is applied in the direction of recording carriers used by machines, instruments, and electronic digital data processing, etc., can solve the problems of data without any access control, non-applicable confidentiality requirements, and non-existent self-destruction. To achieve the effect of strong confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
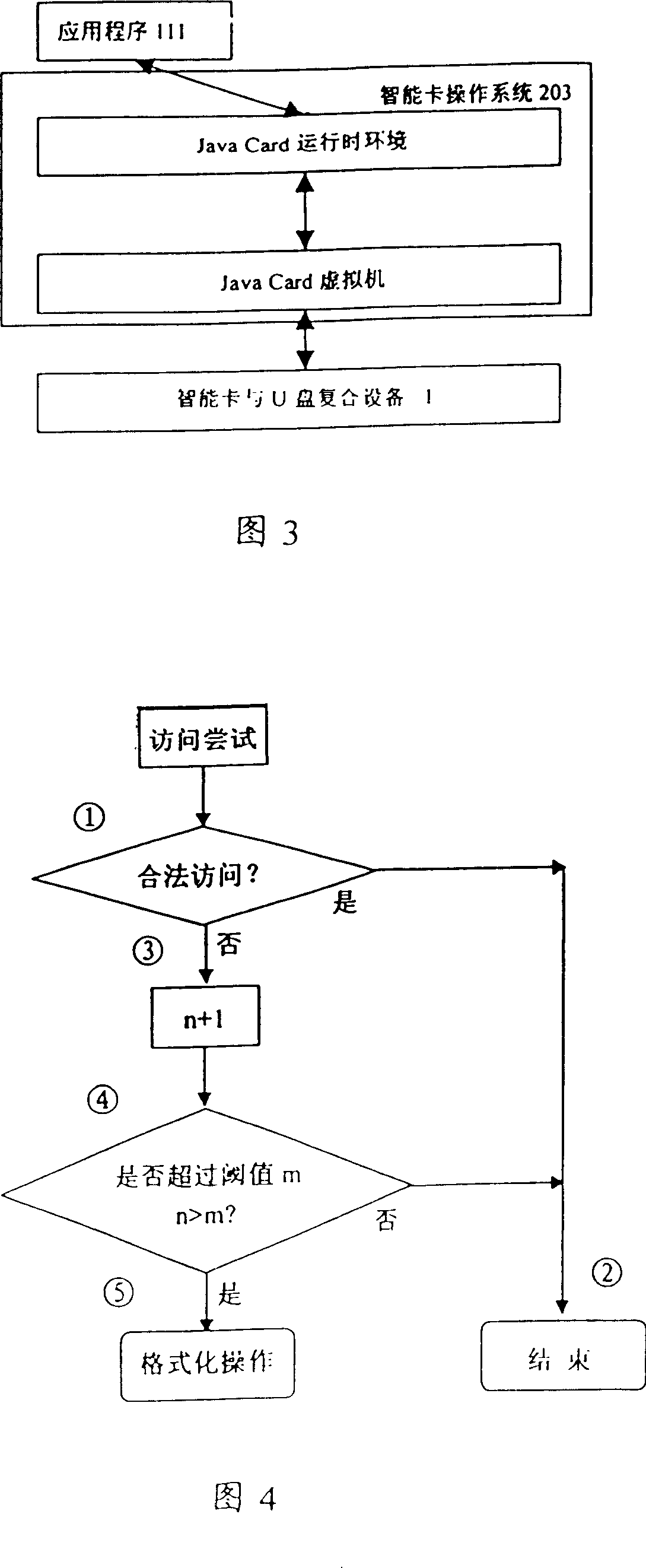
[0027] The so-called "self-destruction" function means that the operating system can audit access attempts. When the unsuccessful access attempts exceed a certain threshold, the system will automatically format the storage space of the U disk to prevent the confidential data stored on the U disk from being destroyed. Unauthorized reading or copying is suitable for occasions that require high confidentiality.
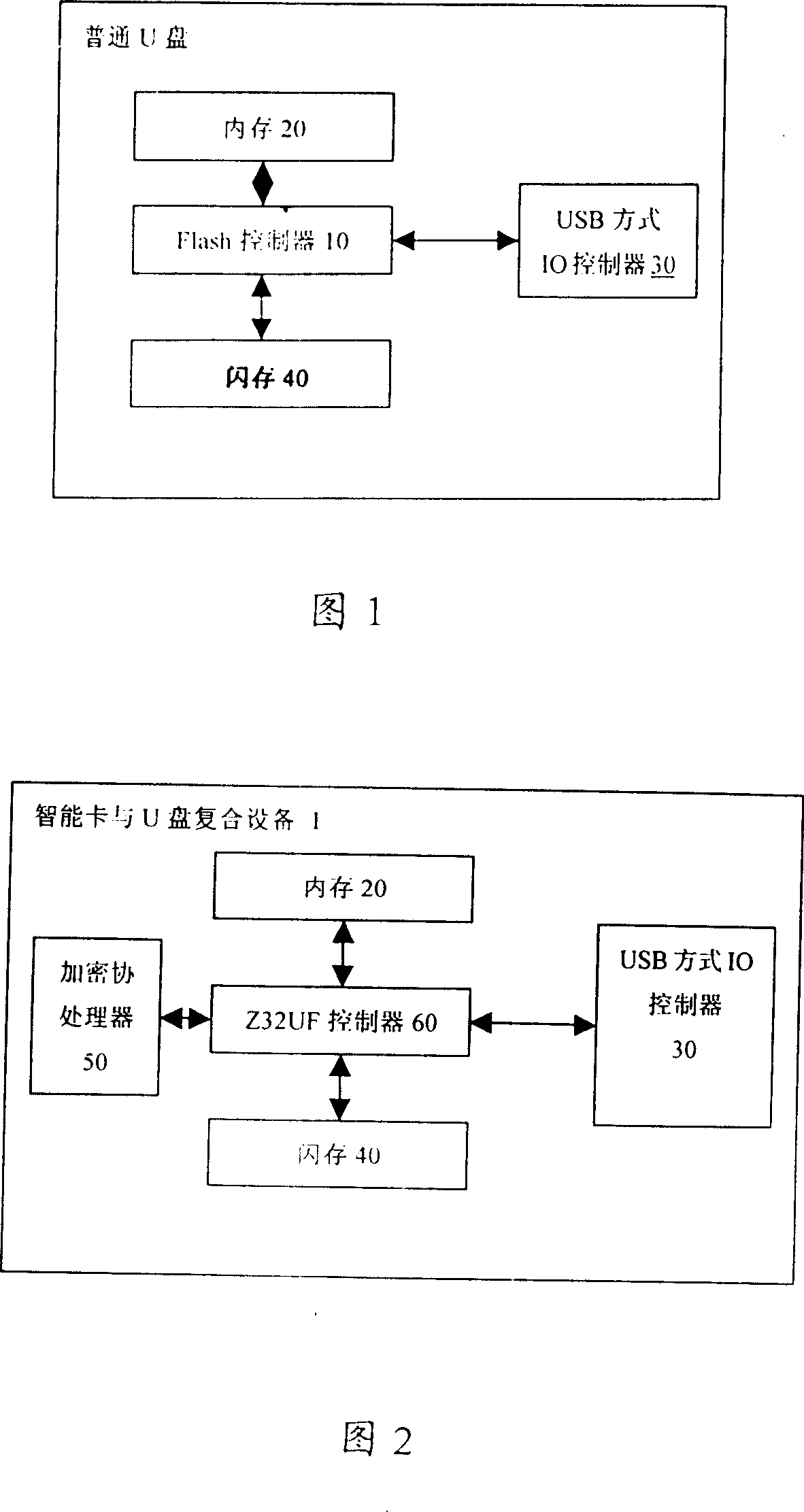
[0028] The implementation of the self-destruct function is based on the following three conditions:
[0029] 1) The smart card operating system 203 on the smart card and U disk composite device controls USB access;
[0030] 2) The self-destruction program 111 on the smart card operating system 203 completes the logical judgment that the number of times of unauthorized access exceeds the threshold, and realizes the destruction action;
[0031] 3) The hardware chip of the smart card and U disk composite device adopts an encryption coprocessor 50 and a Z32UF security contr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com