System and method for protecting content data
A content data and database technology, applied in digital transmission systems, transmission systems, usage of multiple keys/algorithms, etc., can solve the problem that copyright owners cannot manage user permissions according to their wishes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
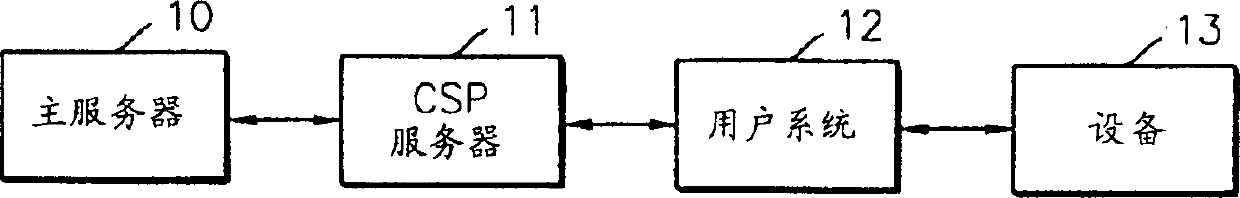
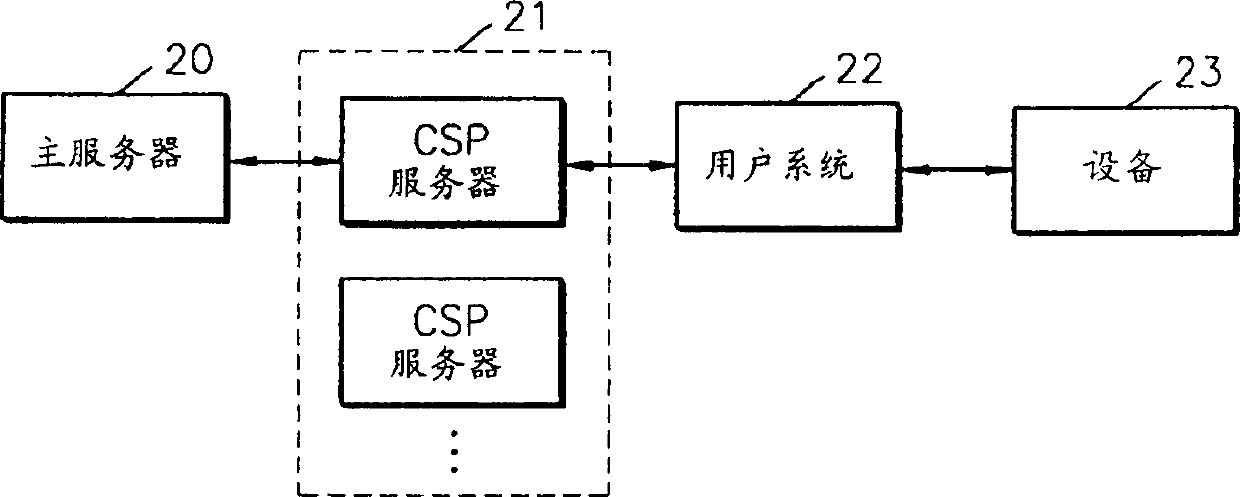
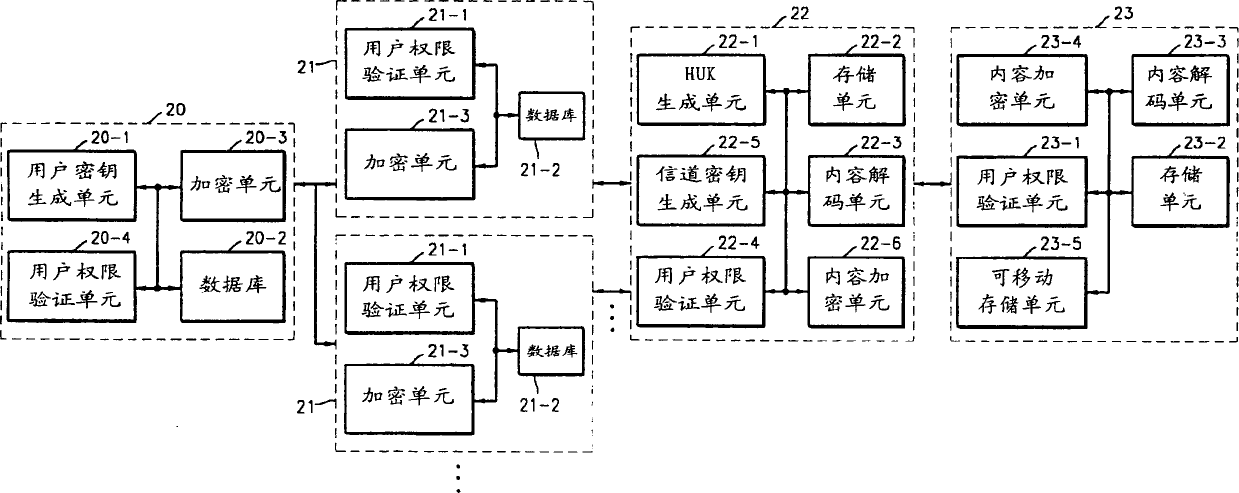
[0030] In the present invention, four keys are used in encrypting and decrypting content data, which will be explained before explaining the present invention in detail.
[0031] First, generate a user key in the master server. The encryption method of the present invention uses an asymmetric encryption.
[0032] The main server generates a public key for encrypting content data and a private key for decrypting encrypted content data.
[0033] The public key is sent to the content providing server to encrypt the content data, while the private key is sent to a user system to decrypt the encrypted content data. A user key is generated in the main server using the registered user's specific information such as ID, password, resident registration number, and the like.
[0034] Second, a master unit key (HUK) is generated in the user system. The HUK is generated using user system-specific information, and each user system has a different HUK. The HUK is generated by combining ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com