Virtual-machine-technology-based data security input and submission method and system
A technology of technical security and safe input, which is applied in the field of enhancing the security of network identity authentication by inputting account passwords on computers, and can solve problems such as doubts about the security of online transaction behaviors, lack of universal adoption, and excessive filtering of firewall feature codes, etc., to solve network problems. The effect of the game account being stolen
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
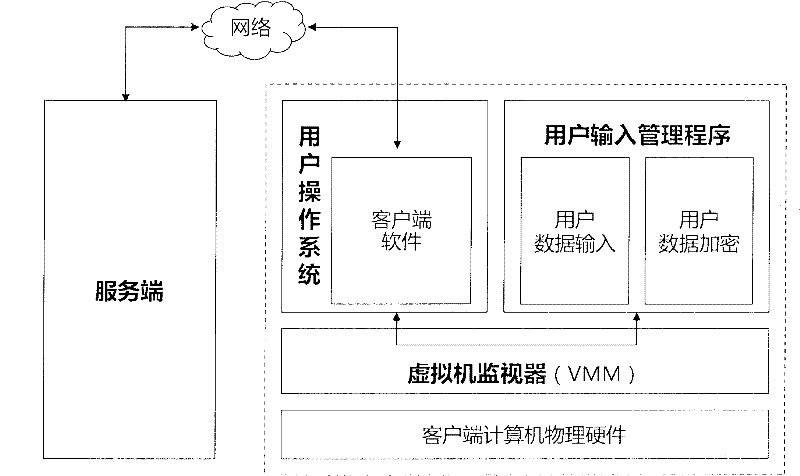
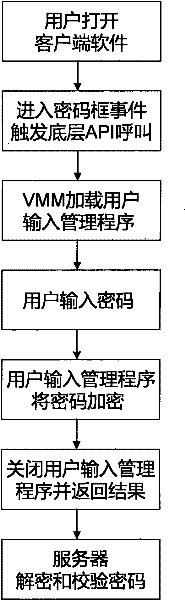
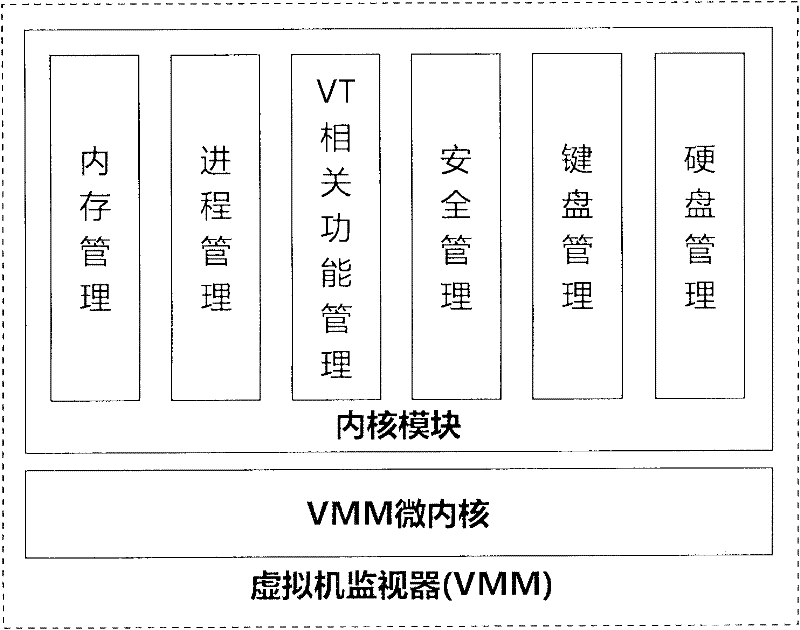
[0036] To facilitate an understanding of the principles and features of the present invention, the following description refers to the implementation of an exemplary embodiment. Specifically, the present invention is described for using Windows 2000 and above operating systems as user operating systems, and using a computer configured with a CPU supporting Intel VT technology as a device scenario. In addition, the present invention is described for online game login of.
[0037] It should be understood, however, that this is not the only embodiment in which the invention may be practiced. On the contrary, the present invention can be applied to various different operating systems, such as Linux operating system; can be applied to different hardware environments, such as disposing the computer that AMD supports hardware-assisted virtualization CPU; Scenarios that use account passwords to log in, such as website forum logins, instant messaging software logins, stock software lo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com