WIFI connection method, terminal and router
A connection method and router technology, applied in the field of communications, can solve problems affecting users' normal network use, WIFI stealing, loss of network bandwidth resources, etc., and achieve the effects of avoiding WIFI stealing, ensuring network use, and protecting network bandwidth resources.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
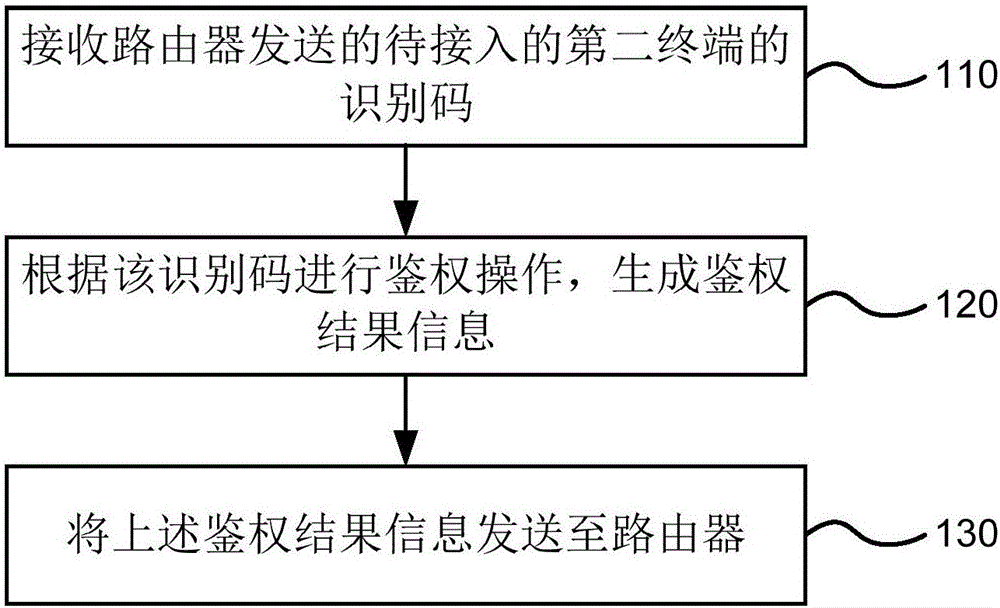
[0028] figure 1 It is a method flow chart of an embodiment of the WIFI connection method provided by the present invention. The execution subject of the method can be various terminal devices with administrator authority, such as smart digital products such as notebook computers, mobile phones, and Pads, or integrated devices or chips on these end devices. Such as figure 1 As shown, the WIFI connection method is applied to the first terminal, including the following steps:
[0029] S110. Receive the identification code of the second terminal to be accessed sent by the router.
[0030] When a new user's terminal (the second terminal to be connected) intends to join a certain WIFI network, it sends a connection request to the router of the network, and the connection request includes the identification code of the second terminal. The first terminal with administrator authority receives the identification code sent by the router. In the embodiment of the present invention, t...
Embodiment 2
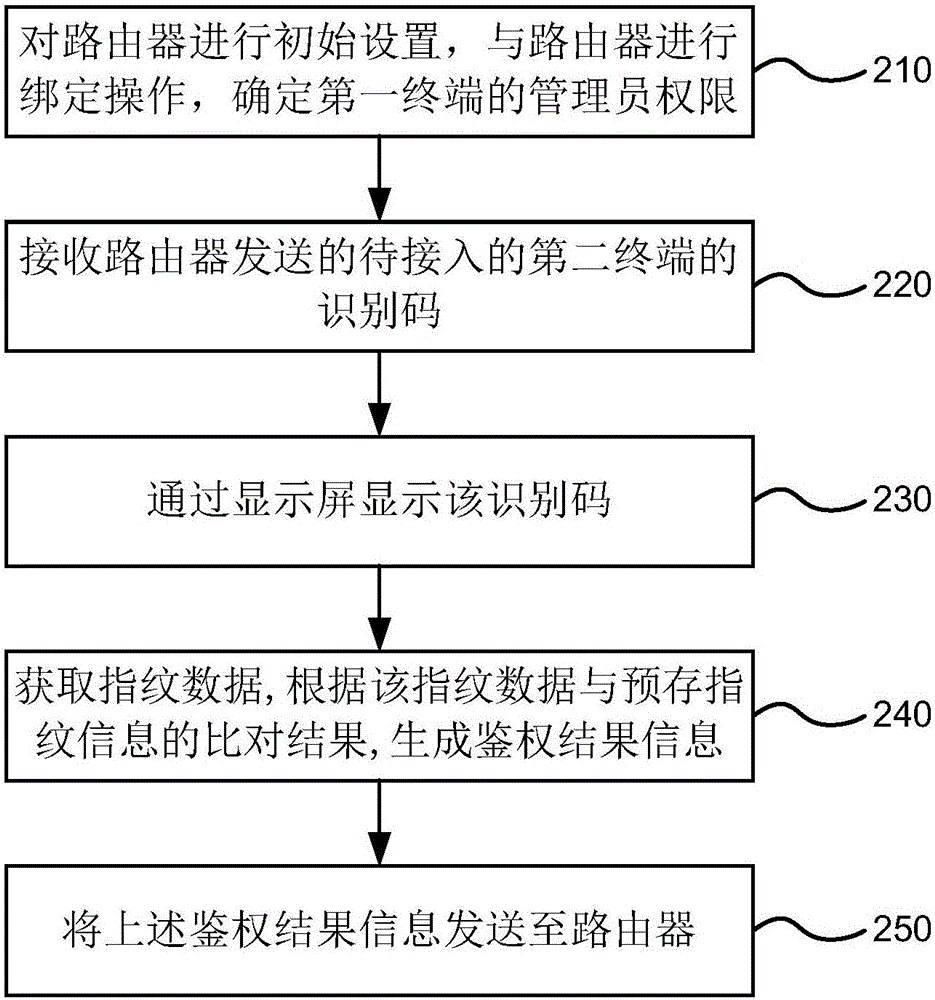
[0037] figure 2 It is a method flowchart of another embodiment of the WIFI connection method provided by the present invention. Such as figure 2 As shown, on the basis of the foregoing embodiments, the WIFI connection method provided in this embodiment may further include the following steps:
[0038] S210. Initially configure the router, perform a binding operation with the router, and determine the administrator authority of the first terminal.
[0039] When initializing the router, you can select a terminal to bind with the router, and determine the administrator authority of the terminal.
[0040] S220. Receive the identification code of the second terminal to be accessed sent by the router.
[0041] S230, displaying the identification code through a display screen.
[0042] After the first terminal receives the identification code of the second terminal to be accessed, it can trigger an administrator authentication interface, and the administrator (the holder of the...
Embodiment 3
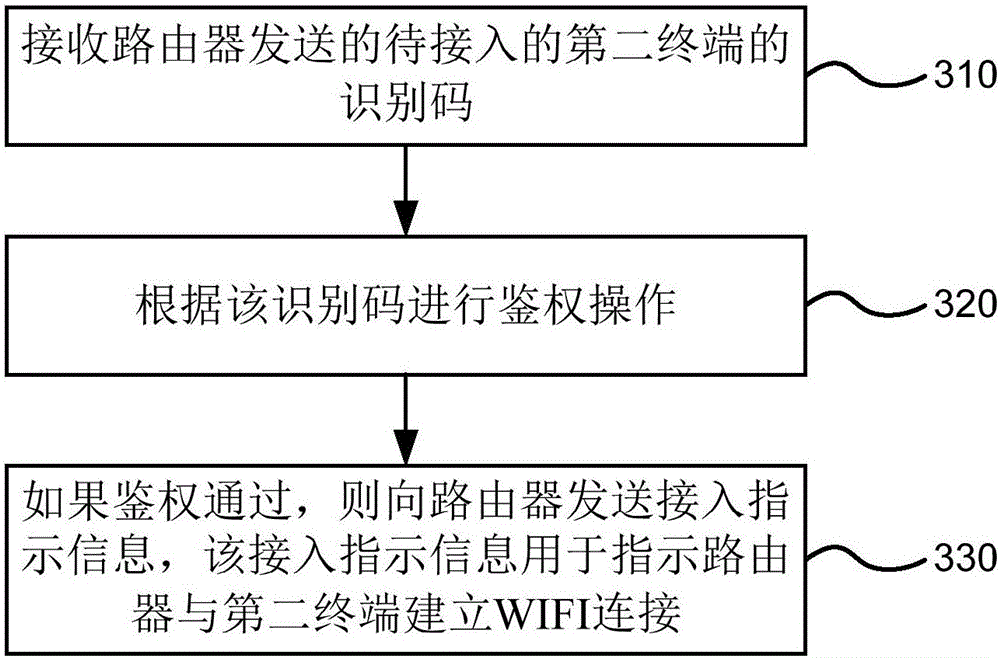
[0050] image 3 It is a method flow chart of another embodiment of the WIFI connection method provided by the present invention. The execution subject of the method may be a terminal with administrator authority, or a device or chip integrated on the terminal with administrator authority. Such as image 3 As shown, the WIFI connection method is applied to the first terminal, including the following steps:
[0051] Step 310, receiving the identification code of the second terminal to be accessed sent by the router;
[0052] When a new user's terminal (second terminal) intends to join a certain WIFI network, it sends a connection request to the router of the network, and the connection request includes the identification code of the second terminal. The first terminal with administrator authority receives the identification code sent by the router. In this embodiment of the present invention, the identification code of the second terminal may be a MAC address of a computer or...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com