Authentication method and device for reinforced software
An authentication method and authentication device technology, applied in the field of Internet security, can solve problems such as inability to effectively distinguish the source of service requests, inability to perform effective protection, and inability to protect data access
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
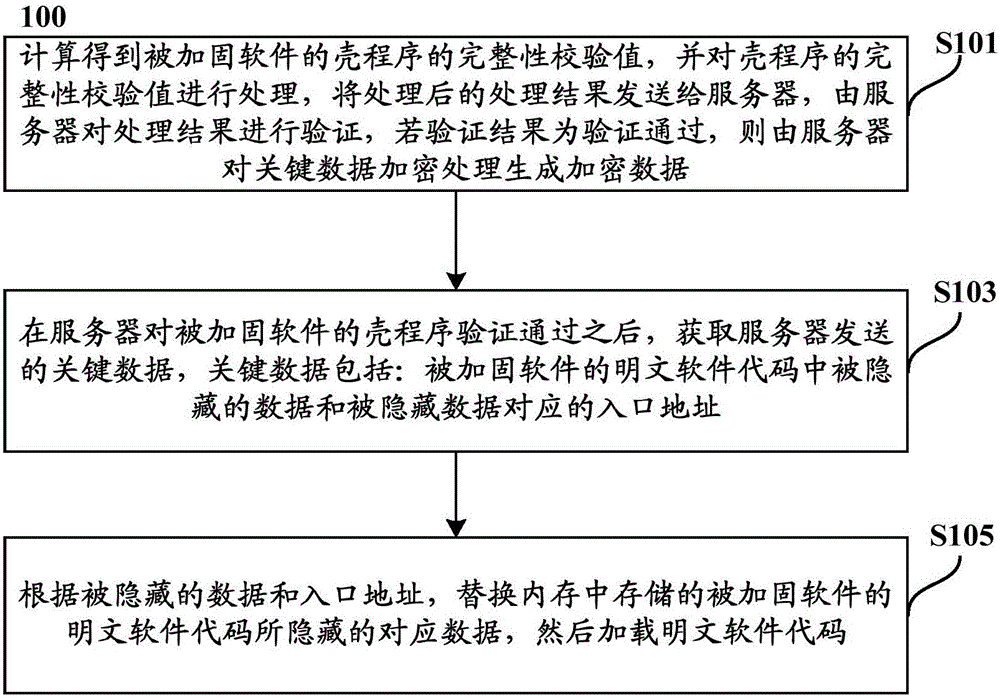
[0089] According to one aspect of the present invention, there is provided a method of authentication of hardened software, which is applied to a mobile terminal, such as figure 1 As shown, the authentication method 100 includes:
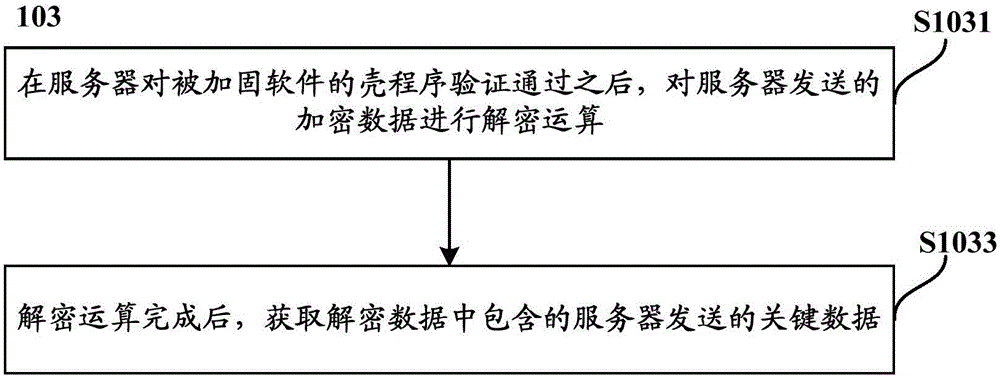
[0090] Step S103, after the server passes the verification of the shell program of the hardened software, obtain the key data sent by the server, the key data includes: the hidden data in the plaintext software code of the hardened software and the entry address corresponding to the hidden data;
[0091] Step S105 , according to the hidden data and the entry address, replace the corresponding data hidden by the plaintext software code of the hardened software stored in the memory, and then load the plaintext software code.
[0092] Through the authentication method of the reinforced software provided by the embodiment of the present invention, the key data provided by the server can be obtained, and according to the entry address corresponding to th...
Embodiment 2
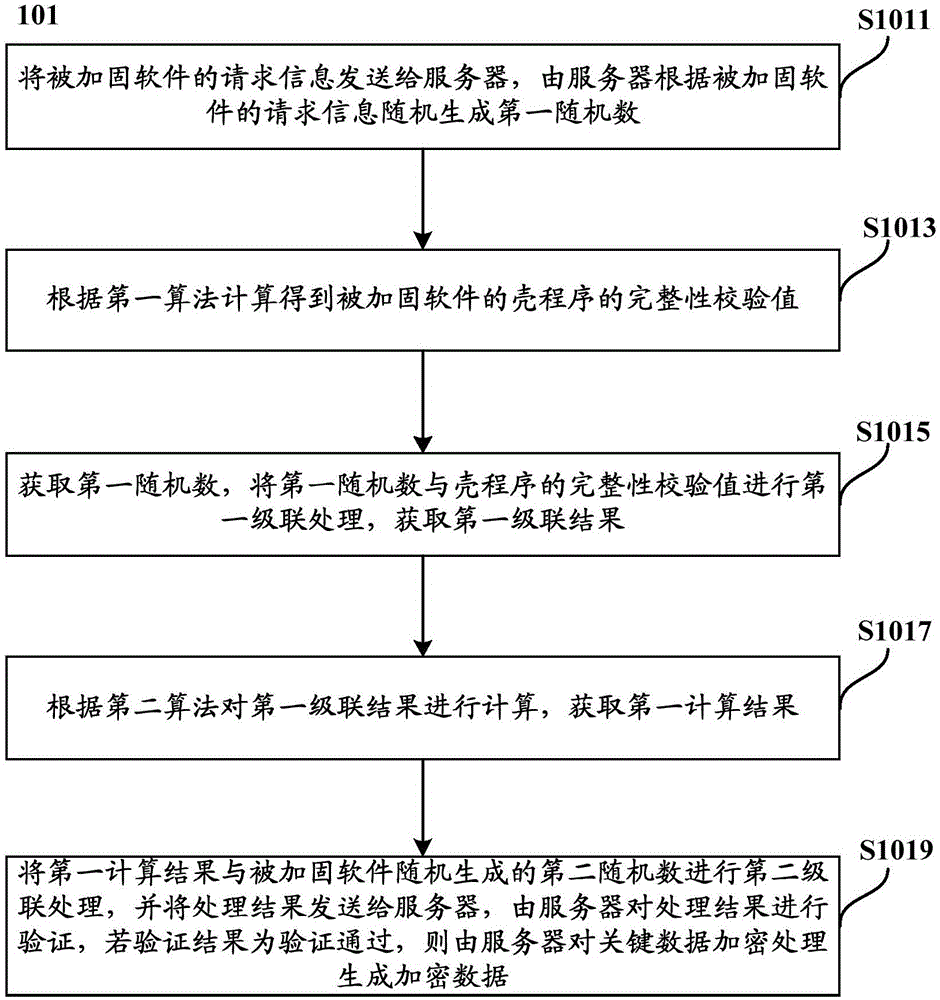
[0113] According to another aspect of the present invention, there is also provided an authentication method of hardened software, which is applied to a server, such as Figure 5 As shown, the authentication method 500 includes:
[0114] Step S501, obtaining the processing result sent by the hardened software, and verifying the integrity check value of the shell program of the hardened software;
[0115] Step S503, if the verification result is that the verification is passed, then encrypt the key data, and send the encrypted data generated by encryption to the hardened software. The key data includes: the hidden data and the hidden data in the plaintext software code of the hardened software. The entry address corresponding to the data.
[0116] Wherein, in the embodiment of the present invention, the integrity check value of the shell program of the reinforced software is first verified to ensure the integrity of the shell program and effectively prevent the shell program f...
Embodiment 3
[0133] According to another aspect of the present invention, there is also provided an authentication device with hardened software, which is applied to a mobile terminal, such as Figure 8 As shown, the authentication device 800 includes:
[0134] The acquiring module 803 is configured to acquire key data sent by the server after the server passes the verification of the shell program of the hardened software, and the key data includes: the hidden data in the plaintext software code of the hardened software and the entry address corresponding to the hidden data ;
[0135] The replacement module 805 is used to replace the corresponding data hidden by the plaintext software code of the hardened software stored in the memory according to the hidden data and the entry address, and then load the plaintext software code.
[0136] Among them, such as Figure 8 As shown, in the embodiment of the present invention, the authentication device 800 also includes:
[0137] The processin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com