Code morphing-based binary code obfuscation method
A binary code and code technology, applied in the field of computer software security, can solve problems such as poor protection effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
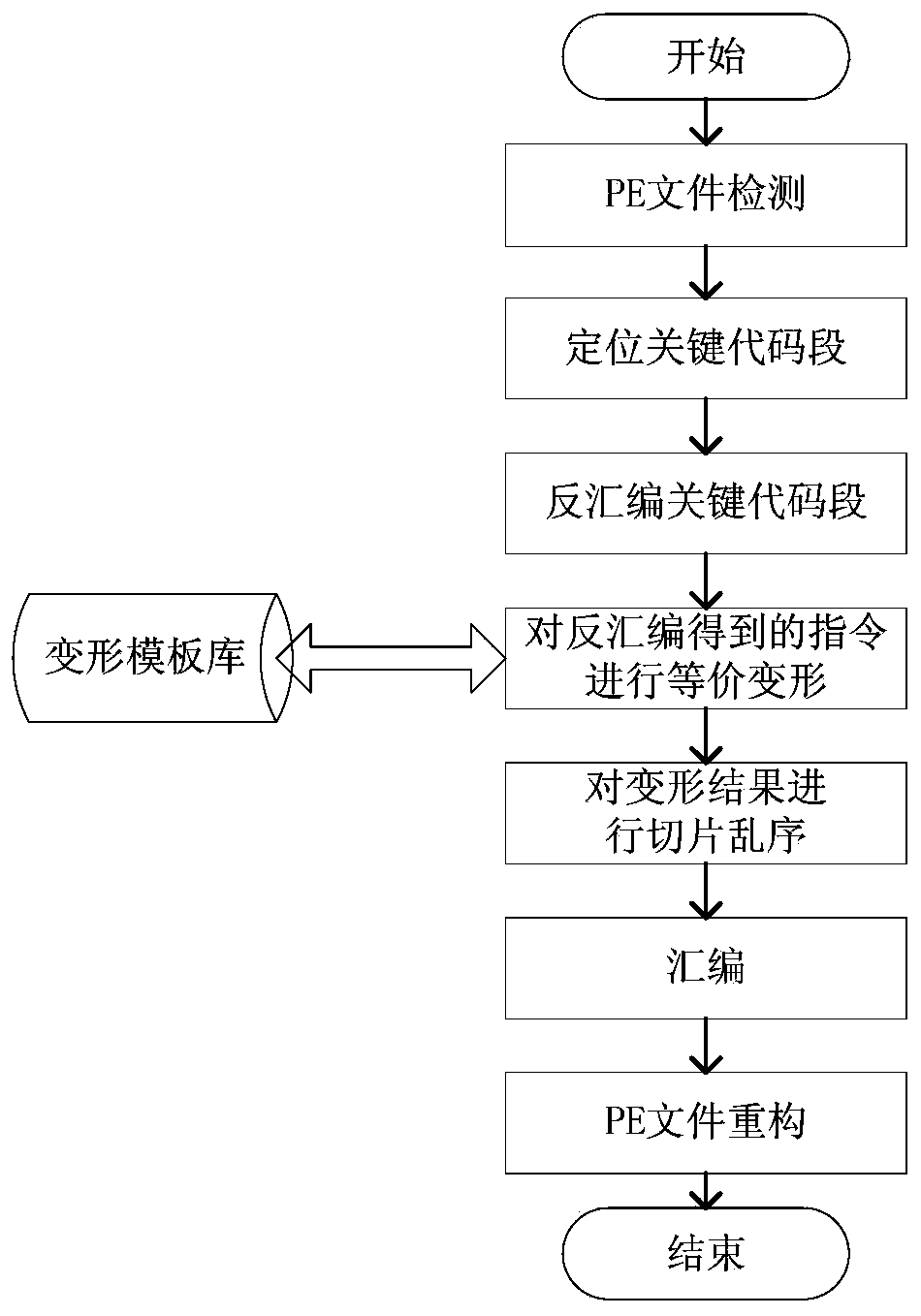
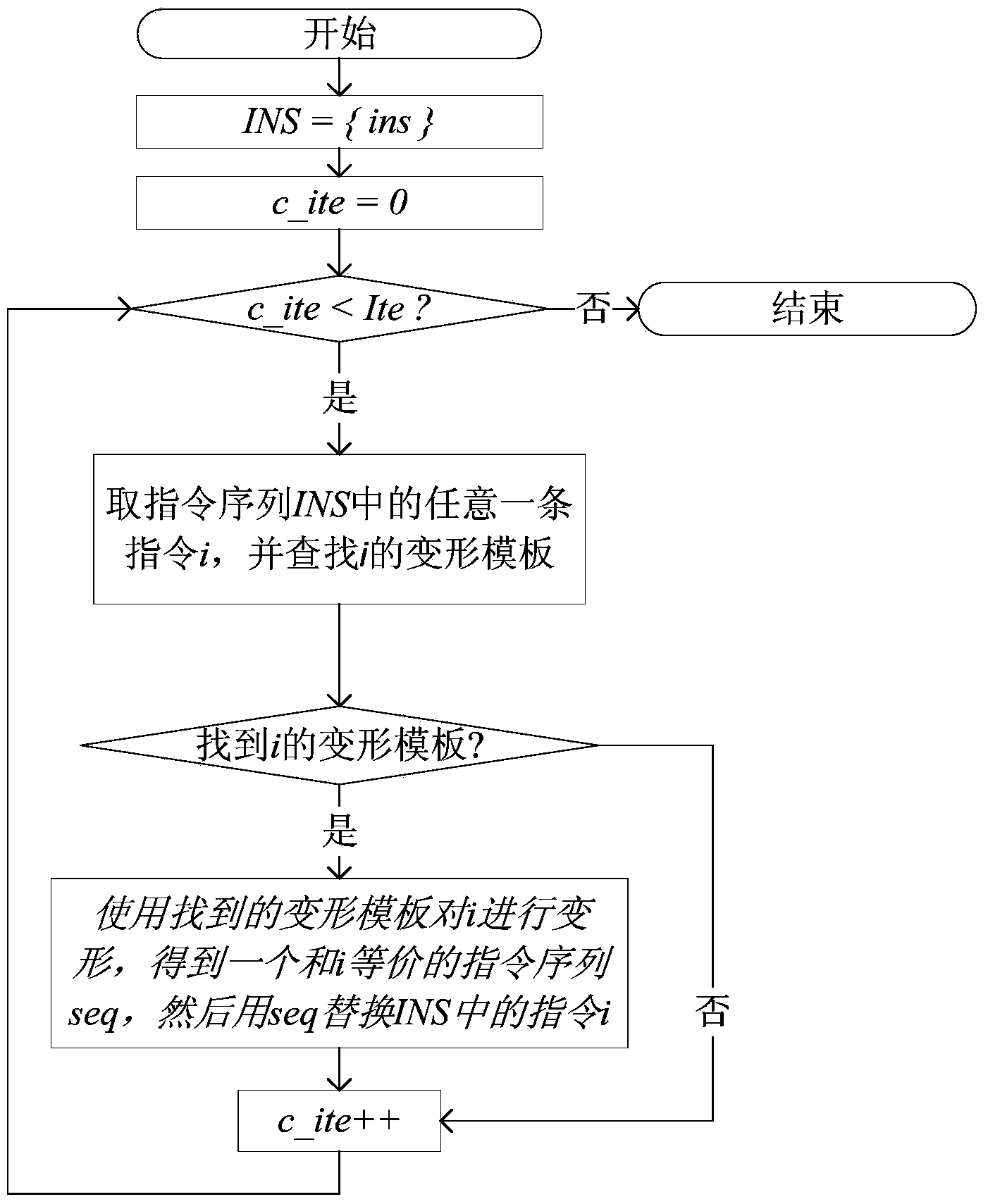
[0063] Such as figure 1 Shown, the binary code obfuscation method based on code distortion of the present invention, carries out according to the following steps:
[0064] Step 1, determine the deformation template library
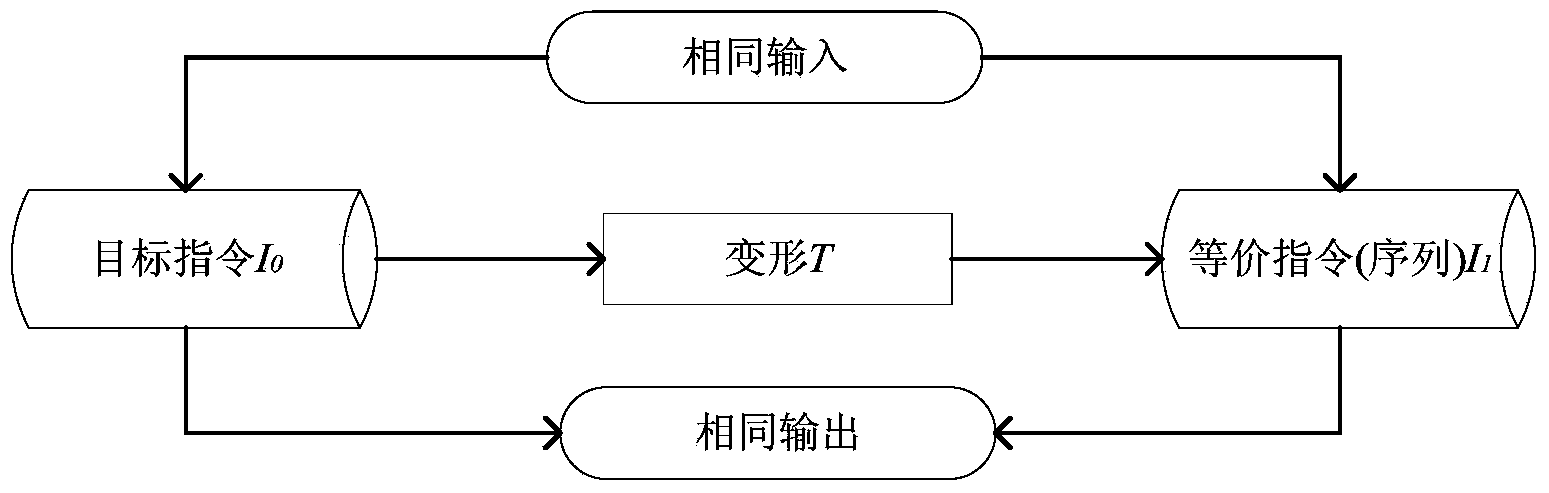
[0065] The deformation template is a function, the input of which is the target instruction to be transformed, and the output is an instruction or instruction sequence which is functionally equivalent to the target instruction. The deformation template is composed of equivalent instruction pairs, and the equivalent instruction pair is a binary group0 ,I 1 >, where I 0 is a target instruction, I 1 refers to a target instruction or a sequence of instructions, and I 0 and I 1 Satisfied: In the case of the same input (that is, the instruction operating environment, including registers, stack space, and memory data), respectively execute I 0 and I 1 , will get the same output as figure 2 shown. Table 1 gives examples of 5 equivalent instruction pairs....
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com