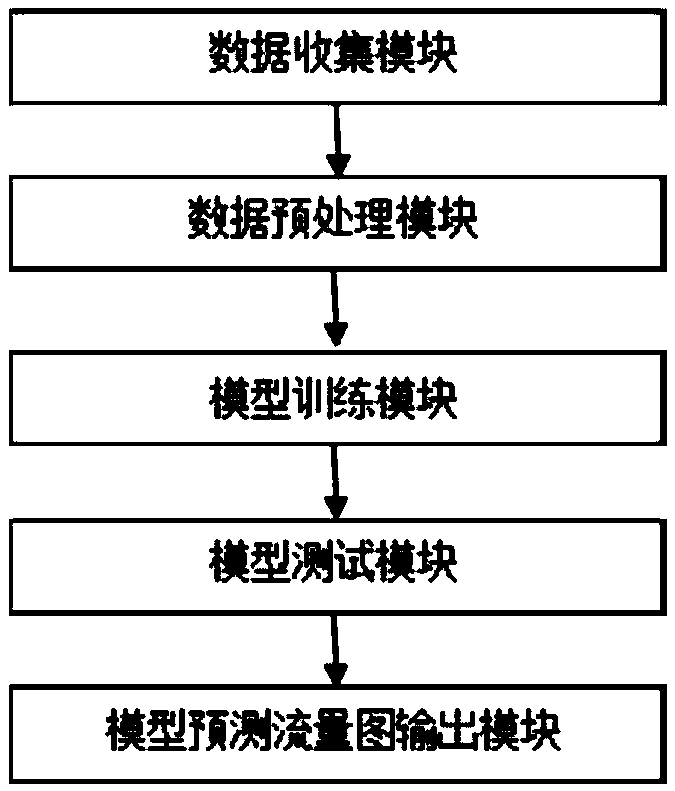
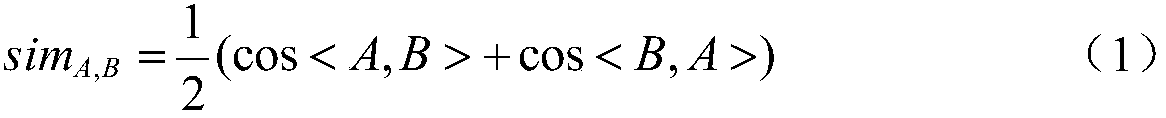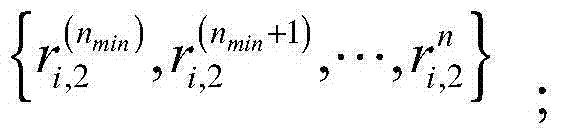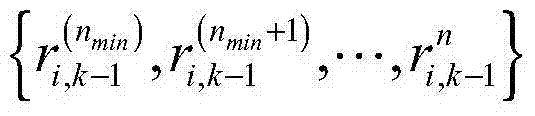Patents
Literature
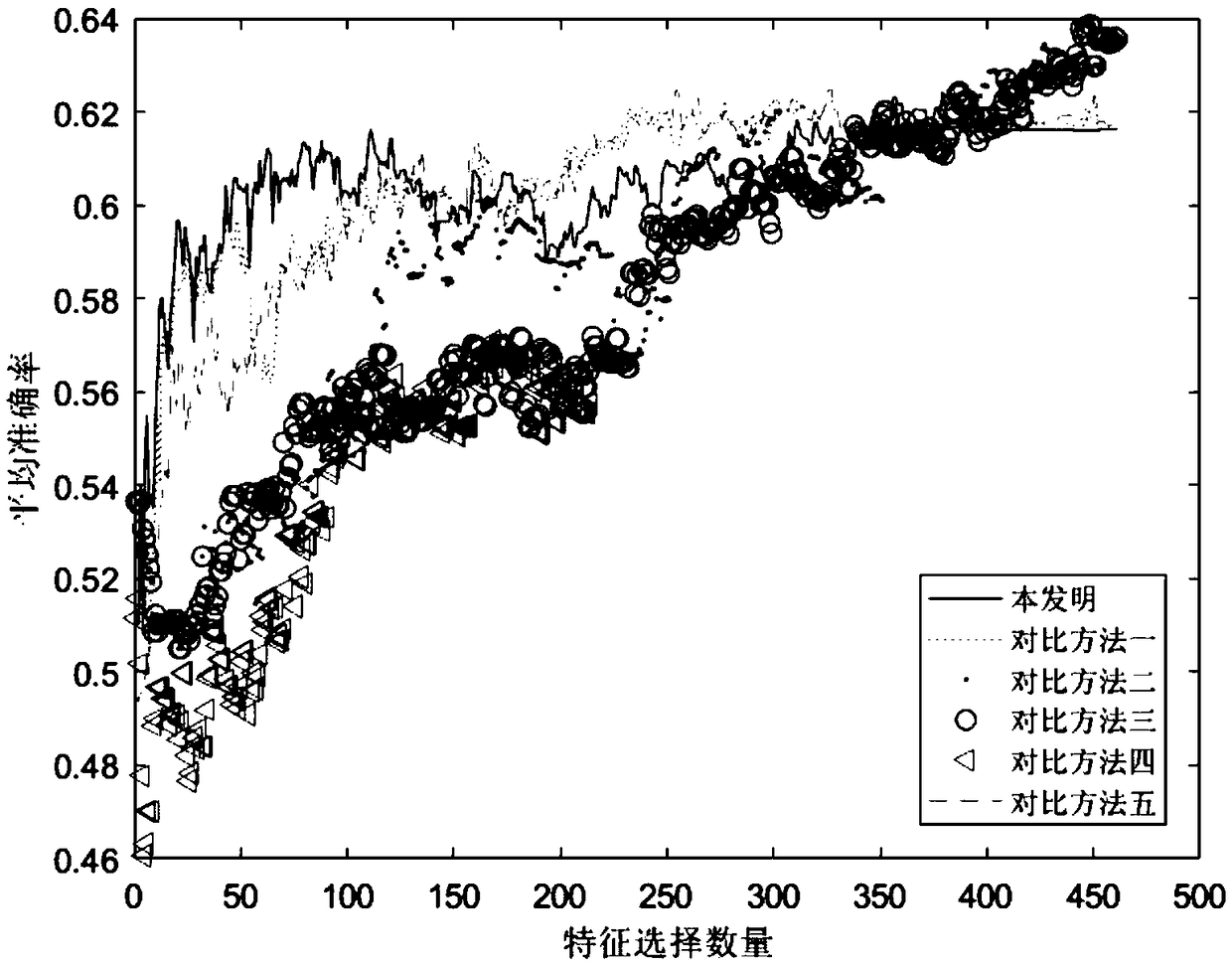
209results about How to "Reduce computing consumption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
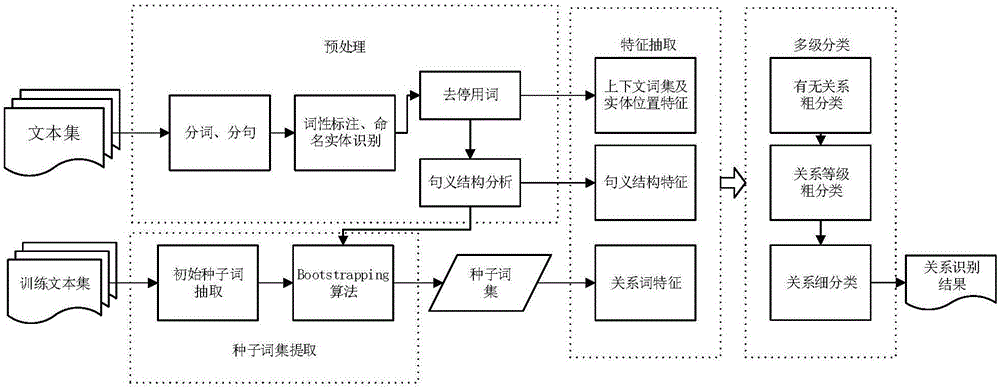
Distributed semantic and sentence meaning characteristic fusion-based character relation extraction method
InactiveCN106484675AImprove accuracyRealize automatic generationSemantic analysisSpecial data processing applicationsSemantic informationExtraction methods
The invention relates to a distributed semantic and sentence meaning characteristic fusion-based character relation extraction method, and belongs to the field of natural language processing. The method comprises the steps of firstly performing training in a small amount of marked corpora and a large amount of unmarked corpora by utilizing statistic word frequency features and a Bootstrapping algorithm to obtain a relational feature dictionary; secondly constructing a triple instance of a statement through an element distance optimization rule, and constructing a triple feature space by fusing distributed semantic information and semantic information; and finally performing true-false binary decision on a triple, and obtaining a character relation type by utilizing a confidence degree maximization rule. According to the method, automatic generation of the feature relation dictionary is realized; a conventional relational multi-class problem is converted into a triple true-false binary decision problem, so that a conventional machine learning classification algorithm is better adapted; and by utilizing the distributed semantic information, the accuracy of relational classification is improved.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
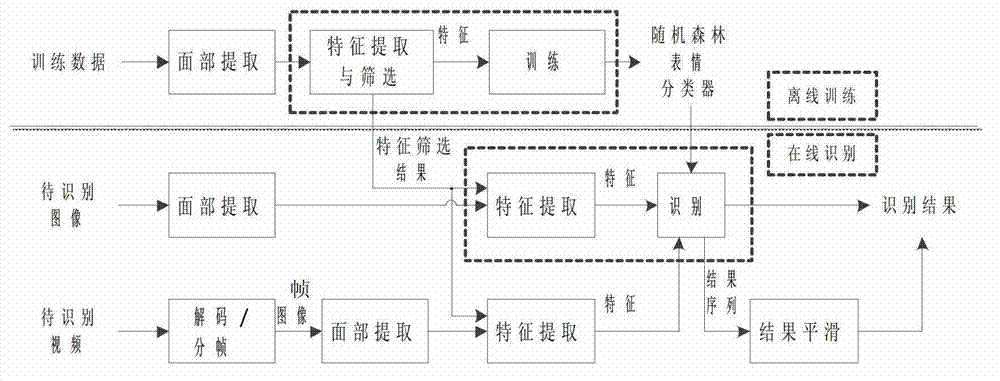
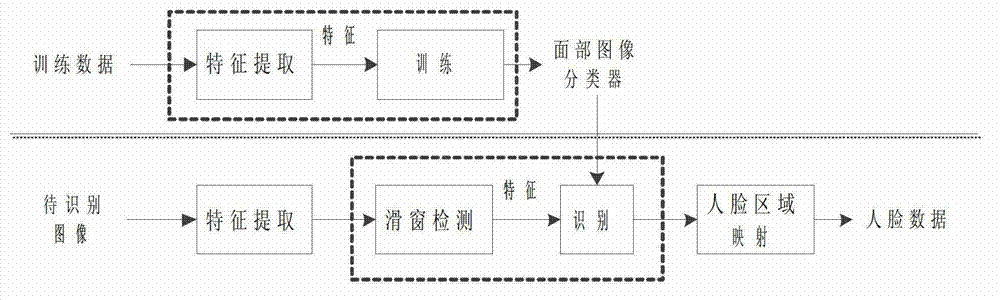
Method for identifying multi-class facial expressions at high precision
InactiveCN102831447AFast recognitionImprove accuracyCharacter and pattern recognitionGraphicsPersonal computer
The invention relates to a method for identifying multi-class facial expressions at a high precision based on Haar-like features, which belongs to the technical field of computer science and graphic image process. Firstly, the high-accuracy face detection is achieved by using the Haar-like features and a series-wound face detection classifier; further, the feature selection is carried out on the high-dimension Haar-like feature by using the Ada Boost. MH algorithm; and finally, the expression classifier training is carried out by using the Random Forest algorithm to complete the expression identification. Compared with the prior art, the method can reduce training and identifying time while increasing the multi-class expression identification rate, and can implement the parallelization conveniently to increase the identification rate and meet the requirement of real-time processing and mobile computing. The method can identify the static image and the dynamic image at a high precision, is not only applicable to the desktop computer but also to the mobile computing platforms, such as cellphone, tablet personal computer and the like.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
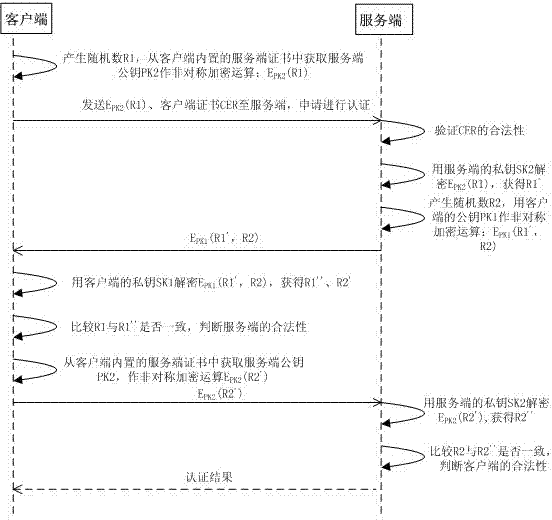
Rapid identity authentication method based on C/S mode
InactiveCN103491094AReduce computing consumptionReduce network data transmission consumptionUser identity/authority verificationClient-sideEncryption
The invention provides a rapid identity authentication method based on a C / S mode. The rapid identity authentication method based on the C / S mode comprises the steps that (1) a client and a server generate respective random numbers in sequence, carry out encryption on the random numbers, send the encrypted random numbers to each other, carry out another encryption on decrypted random number data of the opposite side, and send the encrypted random number data back to each other, and in the process, the server carries out legitimacy authentication on identity information of the client, and encryption processing is carried out after the client passes through the authentication; (2) the client and the server carry out decryption on the returned data to obtain the random numbers which are processed through encryption protection transmission, comparison is carried out between the random numbers and the random numbers generated by the client, comparison is carried out between the random numbers and the random numbers generated by the server, and the client and the server pass through bidirectional identity authentication when the random numbers and the random numbers generated by the client and the server are consistent. According to the rapid identity authentication method based on the C / S mode, the legitimacy authentication processing process of the client to certificates of the server in the process of authentication is omitted, the process is simple, the process of authentication is rapidly optimized, safety can be ensured, and the rapid identity authentication method based on the C / S mode is especially applicable to the identity authentication processing process of a mobile terminal when the mobile terminal which is limited in terminal operation resource and network transmission capacity is connected to an application system.
Owner:成都三零瑞通移动通信有限公司
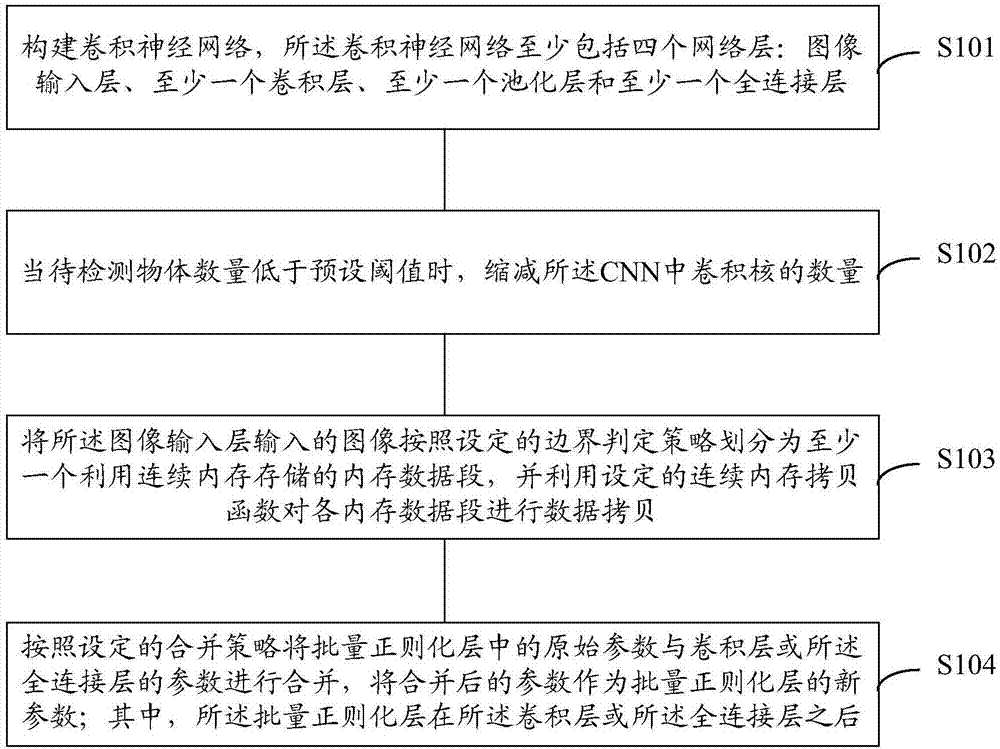
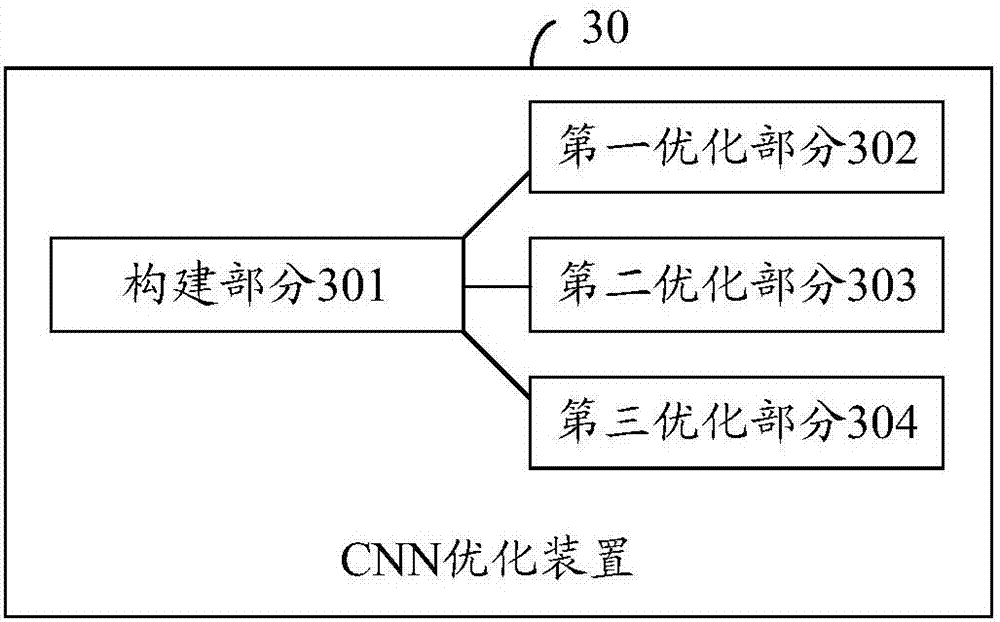
Optimization method and device of convolutional neural network (CNN) and computer storage medium
The embodiment of the invention discloses an optimization method and device of a convolutional neural network (CNN) and a computer storage medium. The method includes: constructing the convolutional neural network, wherein the convolutional neural network includes at least four network layers of an image input layer, at least one convolutional layer, at least one pooling layer and at least one fully connected layer; decreasing the number of convolution kernels in the CNN when the number of to-be-detected objects is less than a preset threshold value; dividing an input image of the image inputlayer into at least one memory data segment, which is stored by utilizing continuous memory, according to a set border determination strategy, and utilizing a set continuous memory copy function to carry out data copying on each memory data segment; and merging original parameters in a batch normalization (BN) layer and parameters of the convolutional layer or the fully connected layer according to the set merging strategy, and using merged parameters as new parameters of the batch normalization layer, wherein the batch normalization layer is after the convolutional layer or the fully connected layer. Calculation consumption in carrying out detection through the CNN is reduced.
Owner:MIDEA GRP CO LTD
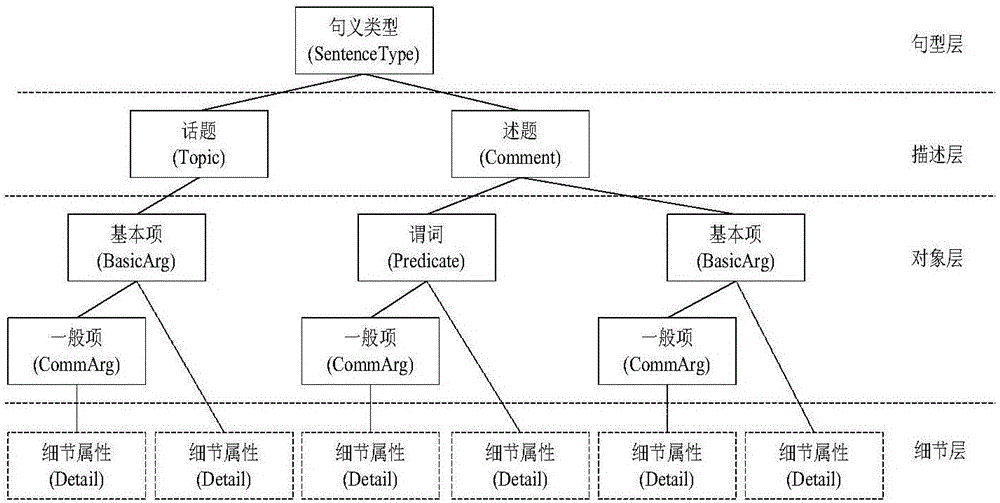
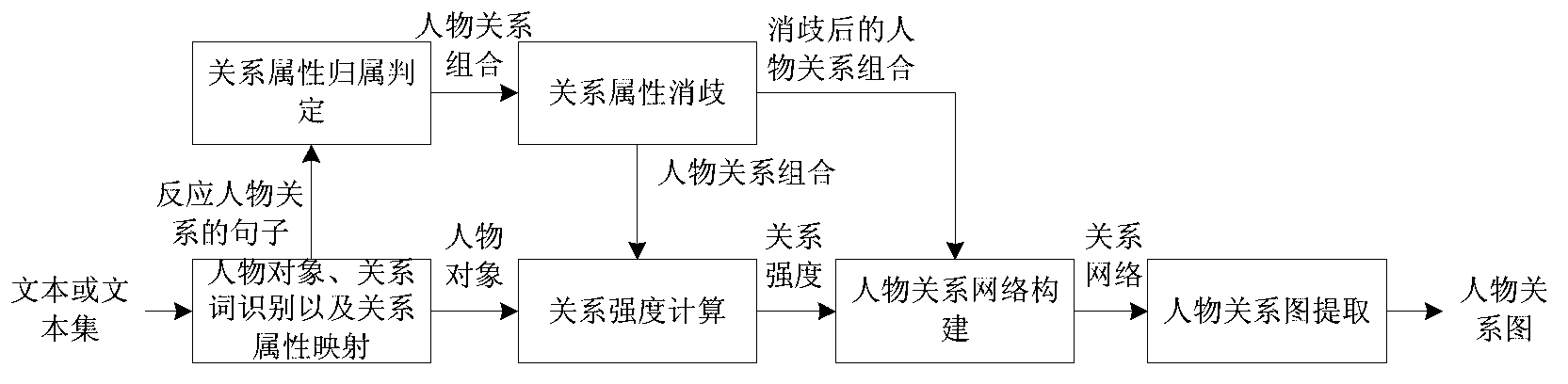
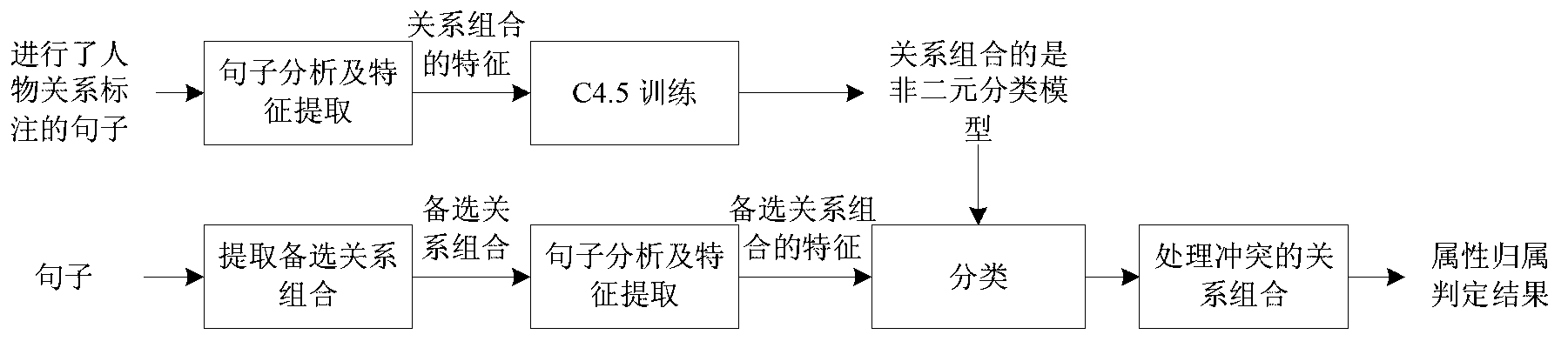
Method for automatically extracting character relations from text set
InactiveCN103235772AFast recognitionImprove accuracySpecial data processing applicationsRelation graphApplicability domain
The invention relates to a method for automatically extracting character relations from a Chinese text or a text set, and belongs to the technical field of computer science and information extraction. In the method, by means of sentence meaning model characteristics, the relation attribute affiliation is determined; the character relations scattered in the text or the text set are automatically extracted by combining methods such as relation attribute disambiguation, character relation strength calculation and the like; and the character relations are organized by a character relation network, and the character relations comprising character relation attributes and the relation strength are displayed in a character relation graph manner. According to the method, sentence meaning model characteristics are introduced, so that the accuracy of the method for extracting entity relations is improved, and the method for extracting the character relations is enriched. Besides, as the number of texts about a central character in the text set is increased, the method can extract character relations of the central character more accurately and comprehensively, and the application range is wider.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
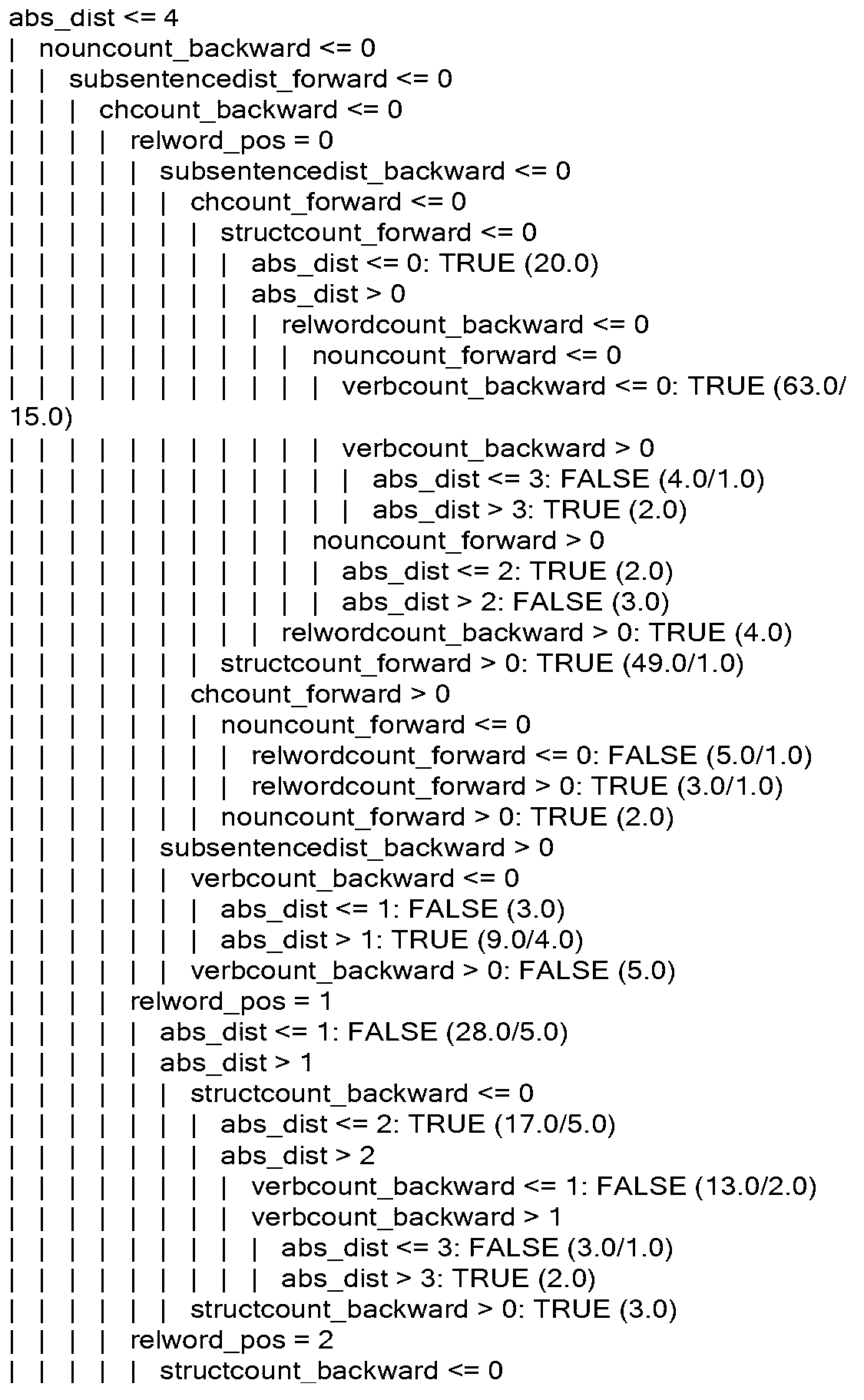
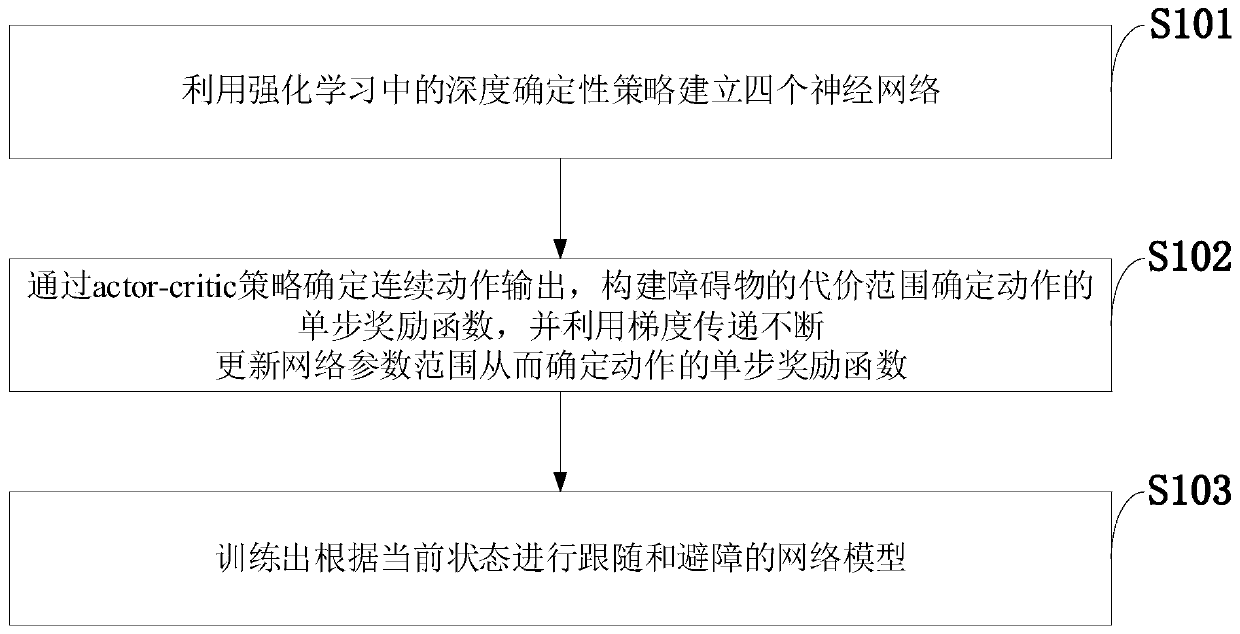
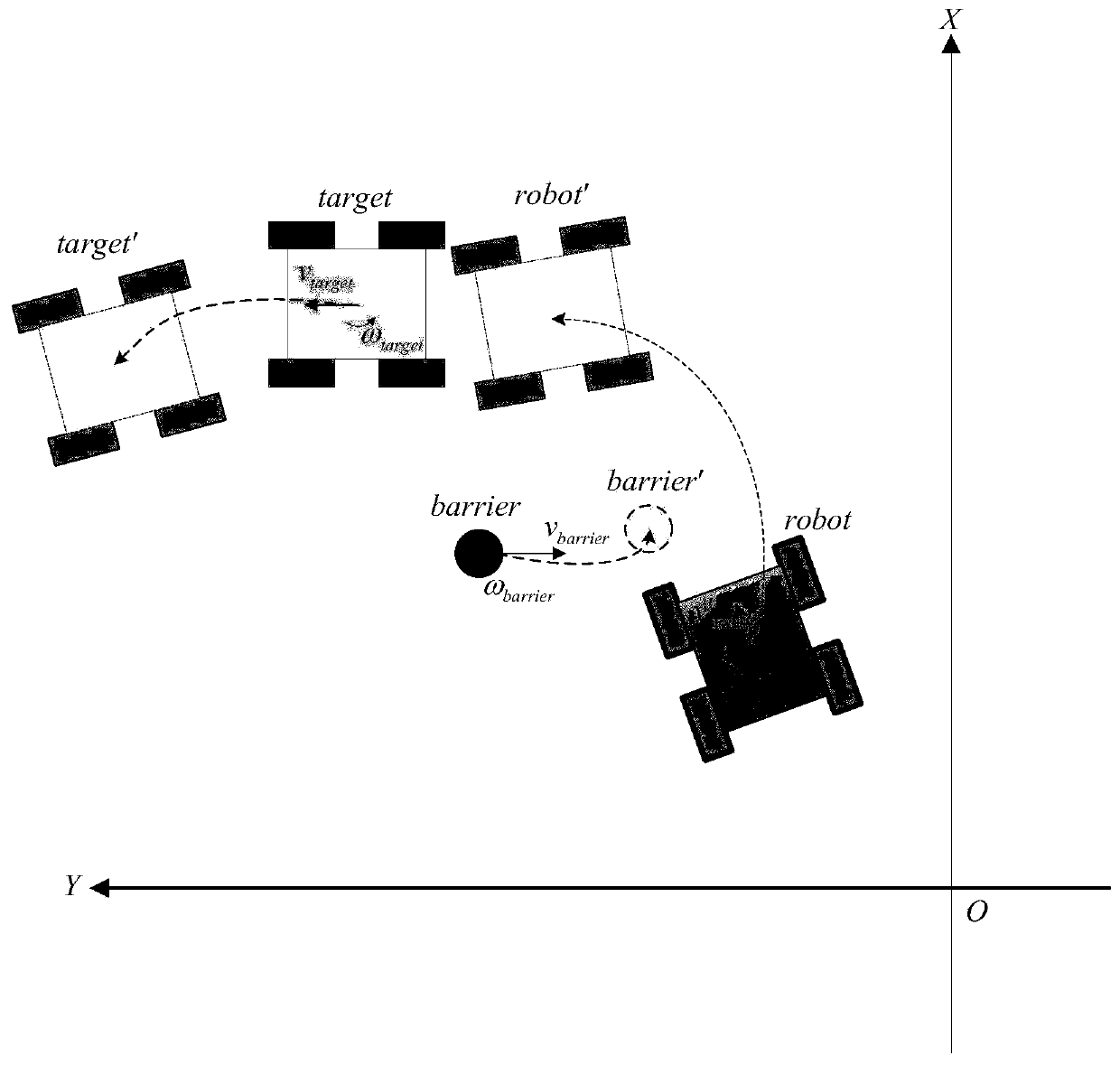
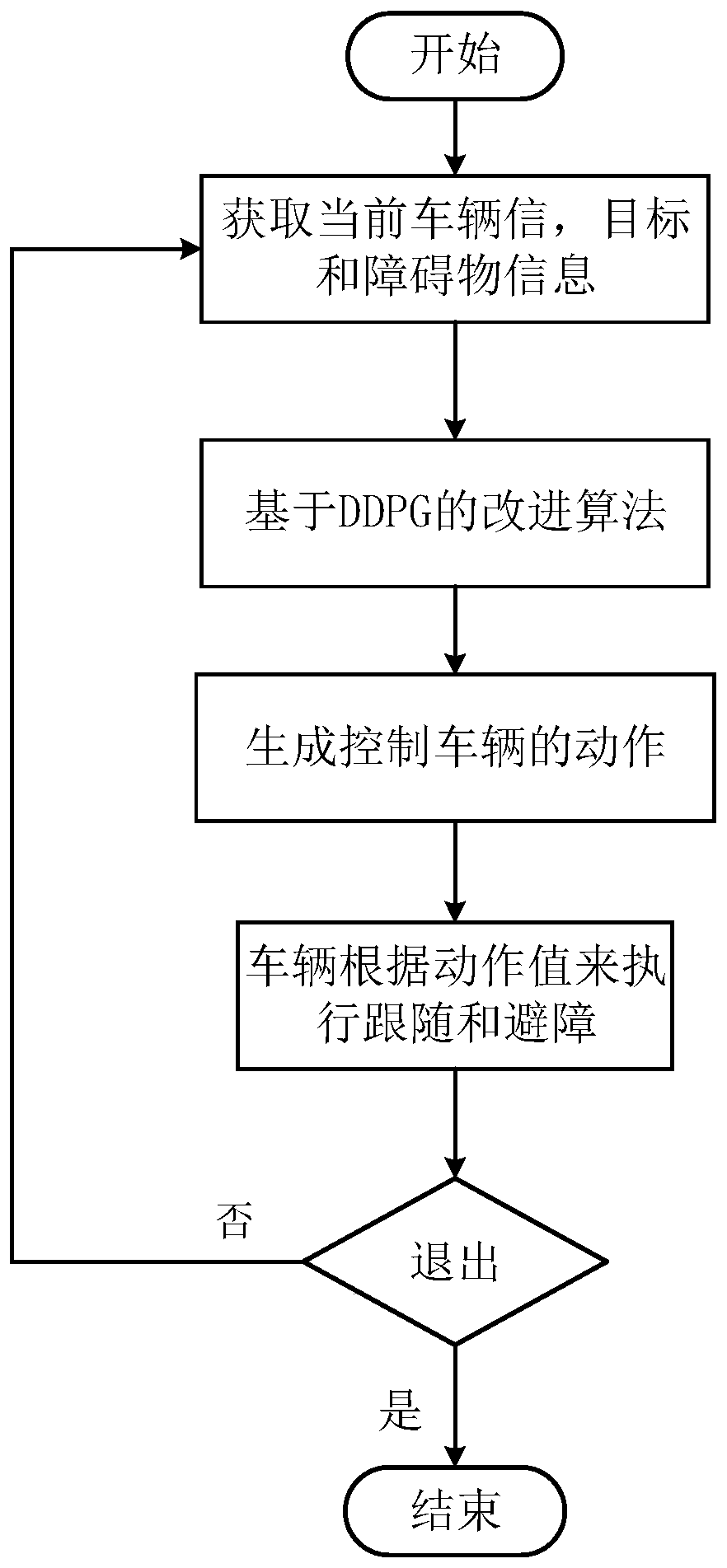
Target following and dynamic obstacle avoidance control method for speed difference slip steering vehicle
ActiveCN110989576ACompatible with sports characteristicsSimple definitionInternal combustion piston enginesPosition/course control in two dimensionsEngineeringNetwork model
The invention belongs to the technical field of unmanned driving, and discloses a target following and dynamic obstacle avoidance control method for a speed difference slip steering vehicle, and the method comprises the steps: building four neural networks through employing a depth determinacy strategy in reinforcement learning; constructing a cost range of the obstacle so as to determine a single-step reward function of the action; determining continuous action output through an actor-critic strategy, and updating network parameters continuously through gradient transmission; and training a network model for following and obstacle avoidance according to the current state. According to the method, the intelligence of vehicle following and obstacle avoidance is improved, and the method canbetter adapt to an unknown environment and well cope with other emergencies. the complexity of establishing a simulation environment in the reinforcement learning training process is reduced. By utilizing a neural network prediction model trained in advance, the position and posture of each step of the target vehicle and the obstacle can be obtained according to the initial position and posture ofthe target and the obstacle and the action value of each step, so that the simulation accuracy and efficiency are improved.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
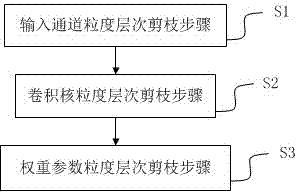
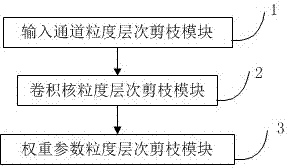
Network model compression method and device based on multi-granularity pruning
InactiveCN107368885AReduce computing consumptionBiological neural network modelsGranularityAlgorithm
The present invention provides a network model compression method based on multi-granularity pruning, which includes one or two or three steps of the following steps: input channel granularity level pruning step, adopting unimportant element pruning method, input channel of network model The unimportant elements in the granularity level of the network model are pruned; the convolution kernel granularity level pruning step uses the unimportant element pruning method to prune the unimportant elements in the granularity level of the convolution kernel of the network model; the weight parameter granularity level In the pruning step, an unimportant element pruning method is used to prune unimportant elements in the granularity level of the weight parameters of the network model. Compared with the prior art, the present invention can effectively solve the problem of network model compression by pruning multiple levels of granularity.
Owner:BEIJING ICETECH SCI & TECH CO LTD
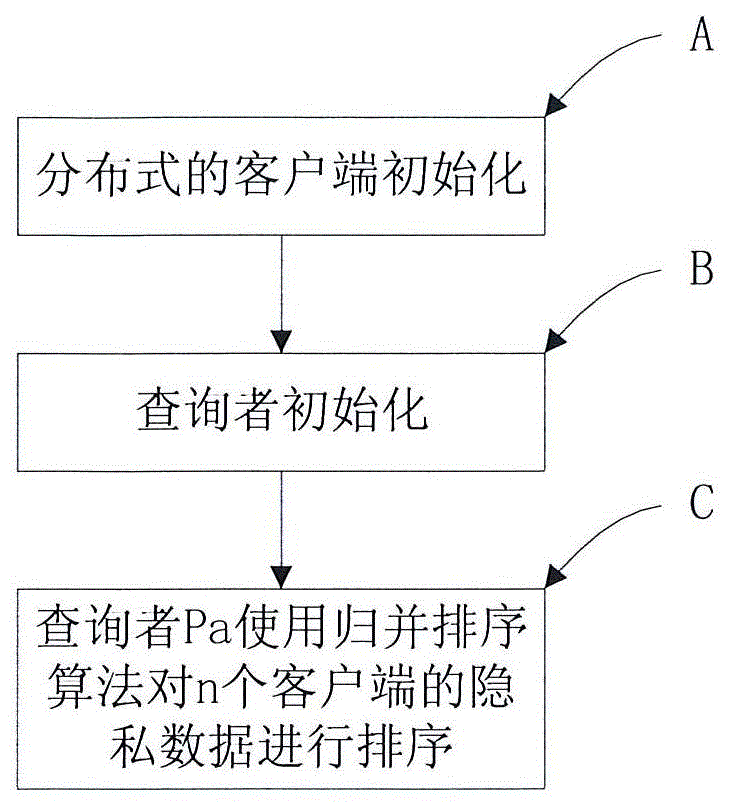
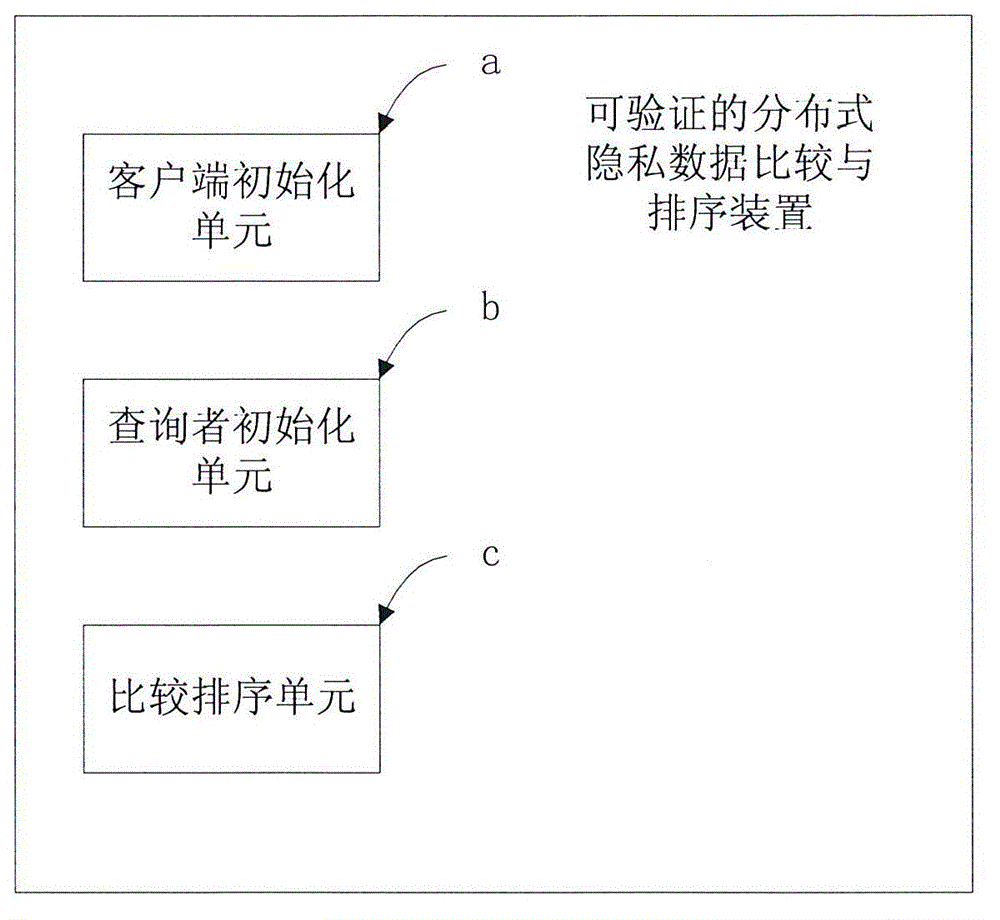
Verifiable distributed privacy data comparing and sorting method and device
The invention relates to the field of secure multi-party computation, in particular to a verifiable distributed privacy data comparing and sorting method and a device. The method and the device have the beneficial effects that through the steps of sorting the privacy data of n client sides by using a distributed client side initialization, inquirer initialization and inquirer Pa use merge sorting algorithm and the like; aiming at the situation that the data is stored on a large quantity of distributed nodes, a ceterless mode is completely adopted in the whole inquiry process by utilizing a digital signature and a semi-homomorphic encryption system; all the client side data is encrypted by using a client side public key and is only decrypted by a client side private key to ensure data privacy; and through a verification mechanism, all client sides can not input false data and can also not affectedly behave the comparing and sorting results.
Owner:无锡绿野千传科技有限公司
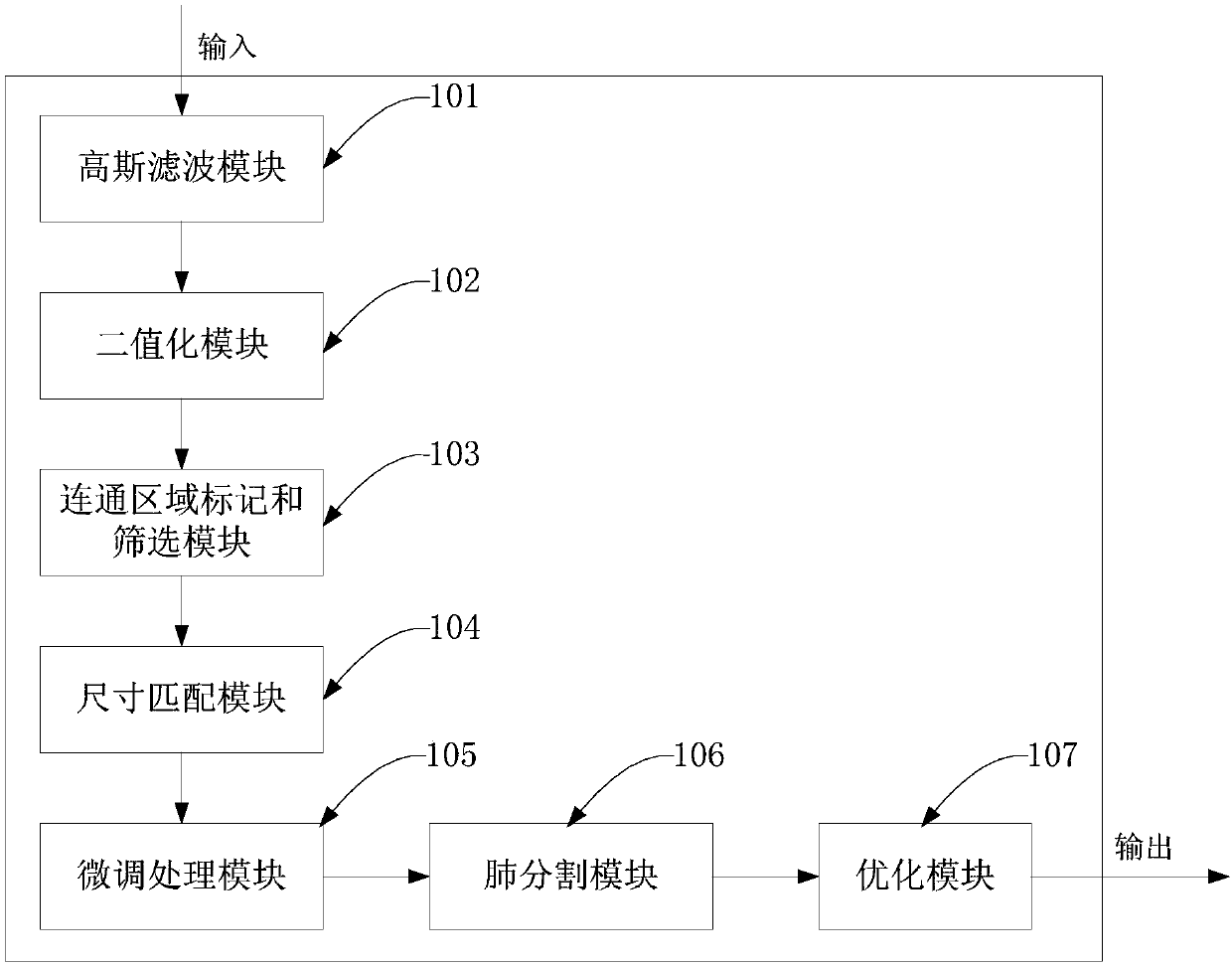
Lung segmenting device of 3D (three-dimensional) U-Net network based on mixed coarse segmentation features
ActiveCN108053417AImprove Segmentation AccuracyReduce computing consumptionImage enhancementImage analysisConditional random fieldComputed tomography
The invention discloses a lung segmenting device of a 3D (three-dimensional) U-Net network based on mixed coarse segmentation features. The lung segmenting device comprises a lung 3D binary image generating module, a lung segmenting module and an optimizing module, wherein the lung 3D binary image generating module is used for sequentially performing Gaussian filtering, binaryzation, marking of communication areas and screening, size matching and trimming on an original lung CT (computed tomography) slice so as to generate a lung 3D binary image; the lung segmenting module is used for calculating an original lung CT image and the lung 3D binary image by the trained 3D U-Net network, and outputting a segmenting probability map; the optimizing module is used for calculating the segmenting probability map by a conditional random field, and outputting the final lung segmenting result. The lung segmenting device has the advantage that while the higher segmenting accuracy is produced, the lower calculation consumption and memory consumption can be guaranteed.
Owner:ZHEJIANG UNIV
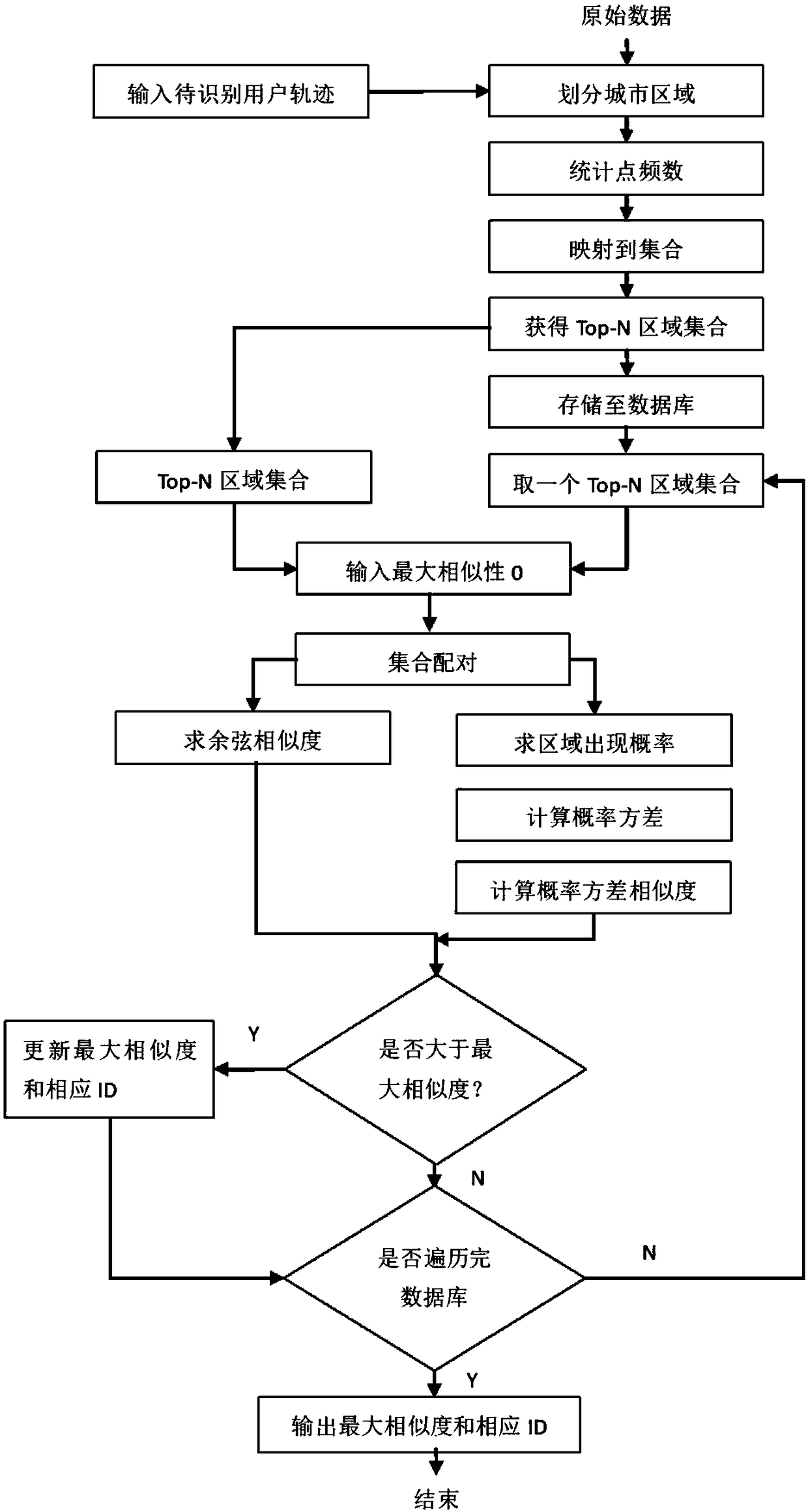
User identity recognition method based on moving trajectory similarity comparison
ActiveCN108536851AImplement lookupReduce computing consumptionData processing applicationsCharacter and pattern recognitionPattern recognitionIdentity recognition
The invention discloses a user identity recognition method based on moving trajectory similarity comparison. Firstly, a city is divided into a longitude and latitude network, the frequency of trajectories appearing in each grid is counted, and grids with the number of points exceeding a threshold value Vp is mapped to a set; the similarity of two paired trajectories is calculated; finally a candidate threshold value Vr is set, namely Top-N sequences with the number of appearing areas exceeding Vr form a candidate set, and a trajectory Top-N sequence which is most similar to the trajectory of ato-be-identified object is matched in a pre-stored trajectory Top-N sequence set. Compared with a traditional method of directly calculating frequency distribution vectors, the areas which frequentlyappear have stronger regularity, so that the calculated amount is significantly reduced without sacrificing the accuracy of recognition.
Owner:WUHAN UNIV
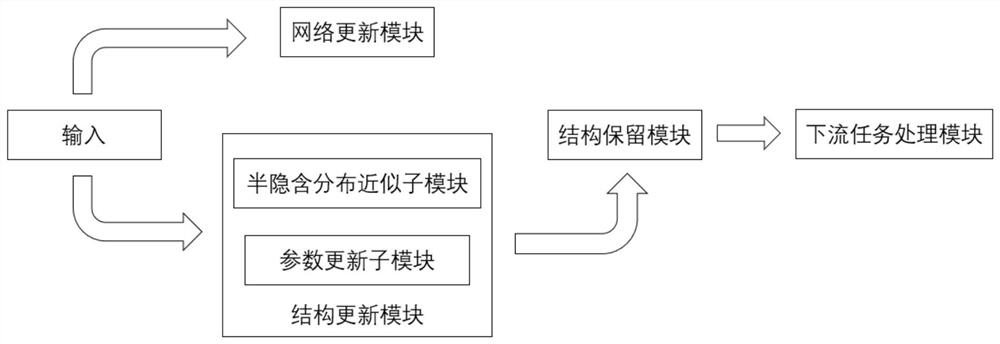
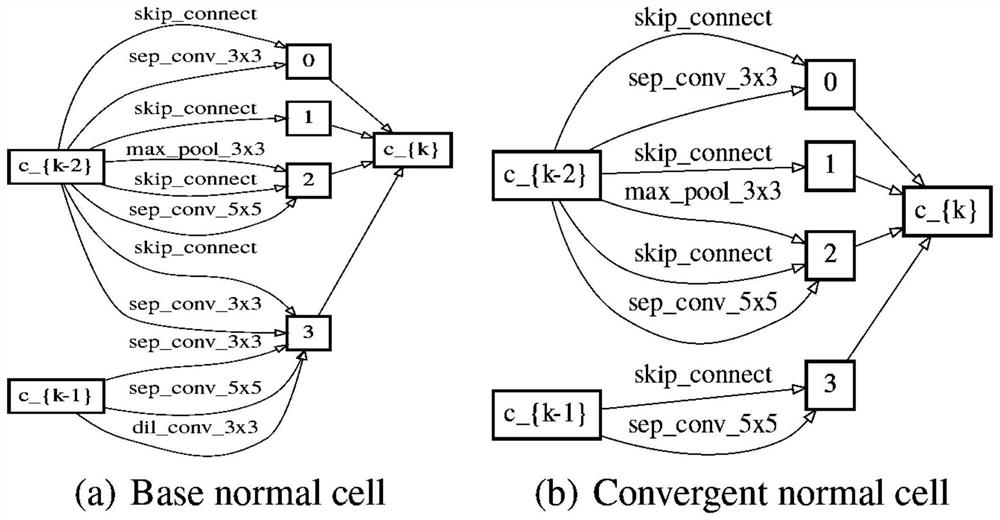
Hierarchical network structure search method, device and readable storage medium
ActiveCN111860495AGuarantee stabilityImprove performanceCharacter and pattern recognitionNeural architecturesComputation complexityImaging processing
The invention provides a hierarchical network structure search method, a device and a readable storage medium. The method comprises the steps of S1, constructing a super network; S2, acquiring image data and taking the image data as training data of network parameters and structure parameters of the super network; S3, generating a feature map, calculating a cross entropy loss function of the network parameters, and updating the network parameters of the super network; S4, generating a feature map and a KL divergence loss function, calculating a cross entropy loss function of the structure parameters to obtain a semi-implicit variational discard loss function, training and updating the structure parameters of the super network and obtaining a discard probability; s5, updating the basic unitby using the discard probability, and updating the annealing parameter; s3 to S5 are repeated, and the network parameters and the structure parameters are updated; s6, obtaining a final network. Themethod greatly reduces the search time and reduces the calculation complexity while guaranteeing the higher performance, guarantees the search stability and practicality, can be used in the fields ofimage target detection and classification, and improves the image processing speed.
Owner:SHANGHAI JIAO TONG UNIV
Resident traffic flow prediction system and prediction method thereof
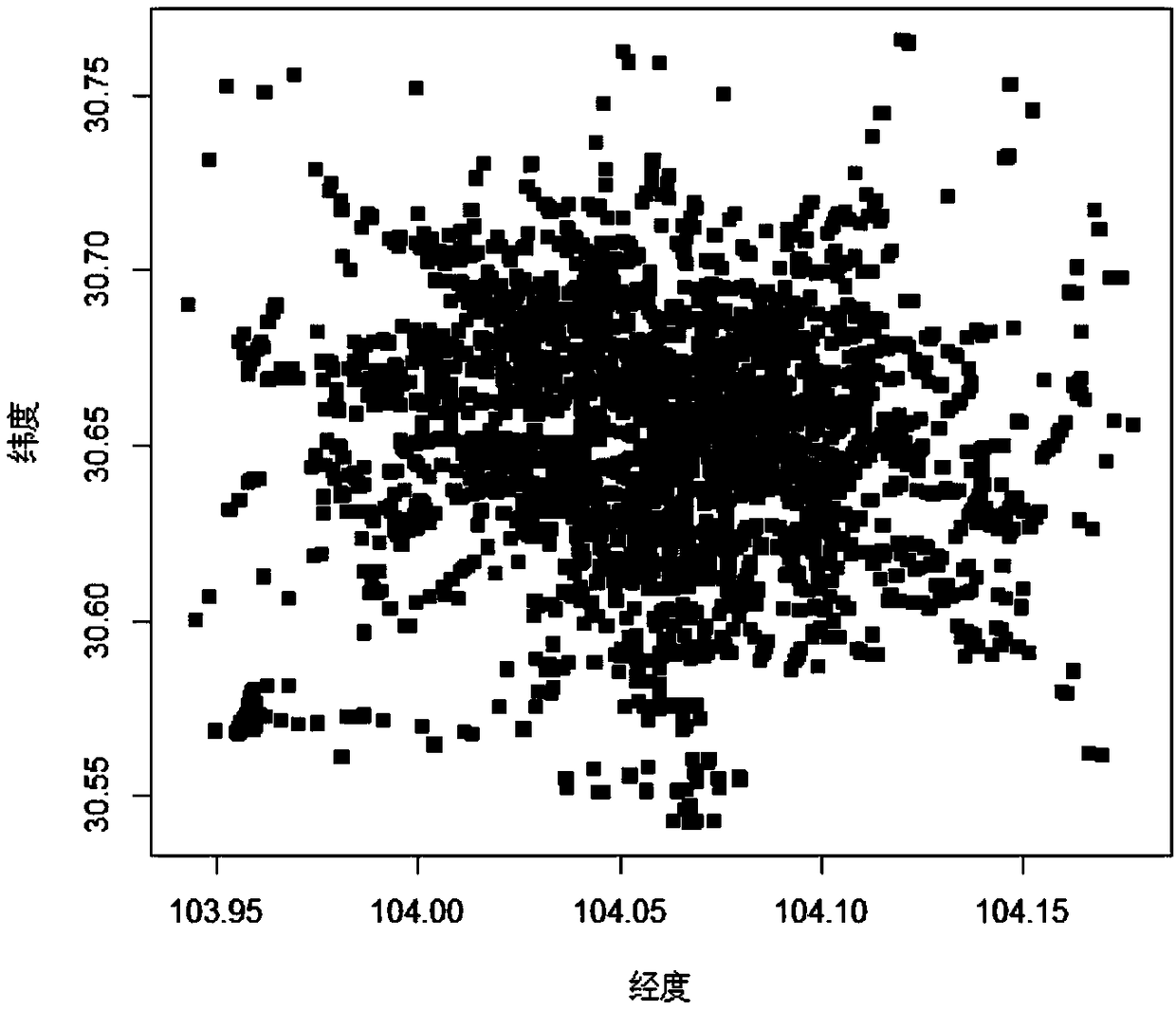
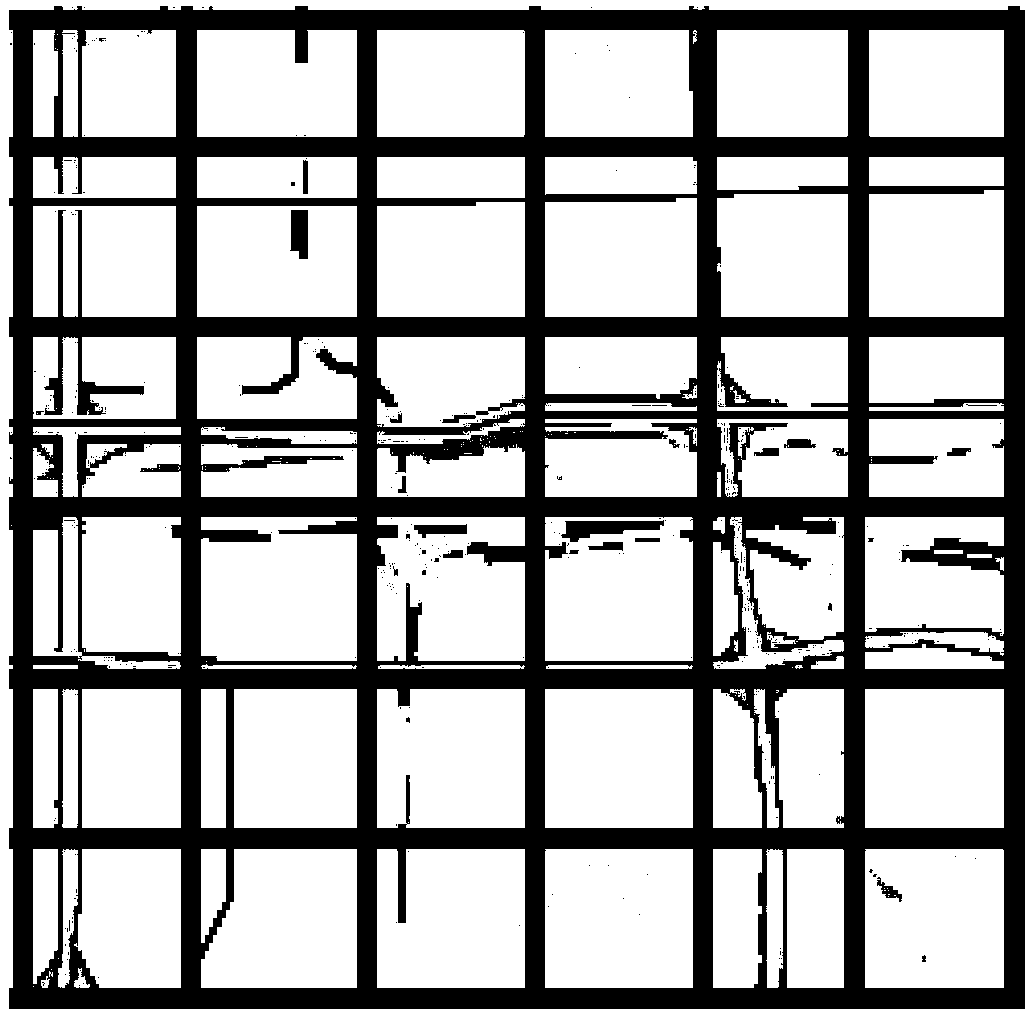
ActiveCN109448361ASolve situations that require traffic flow to be seasonalReduce model parametersDetection of traffic movementLocation information based serviceTraffic predictionSimulation
The invention discloses a resident traffic flow prediction system and a prediction method thereof. A full convolutional network can be adopted to perform prediction. Geographic grid division can be adopted; urban resident travel areas can be divided into multiple grid areas; the traffic flow data of the travelling of residents can be converted into flow diagrams as the input of the full convolutional network; data dimensions can be increased through the number of channels of different extended images; the characteristics of the traffic flow diagrams can be extracted through convolution layers;images whose magnitudes are equal to the magnitudes of input flow diagrams can be obtained through multiple deconvolution; and the whole network can be reversely adjusted through the error of actualflow diagrams and prediction flow diagrams at the next time quantum. Thus, fully connected operation of traditional convolutional networks can be removed, the traffic flow diagrams at the next time quantum can be predicted by adopting deconvolution, so that prediction precision can be enhanced, and model parameters and calculation consumption can be massively reduced.
Owner:YUNNAN UNIV
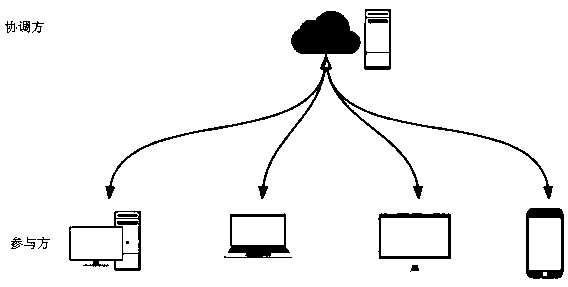
Information interaction system and method suitable for federated learning
ActiveCN111553470AEnsure safetyWon't leakNeural architecturesNeural learning methodsEngineeringGraph neural networks
The embodiment of the invention discloses an information interaction system and method suitable for federated learning. The system comprises at least two participants and a coordinator, each participant is provided with a graph network, and the graph network comprises a plurality of nodes; each participant represents all nodes in the graph network of the participant with a fixed-length vector to obtain a representation vector of each node, training of a graph neural network model is performed based on the representation vectors of the nodes, and gradient information is uploaded to the coordinator in the training process; the coordinator corrects the gradient information uploaded by each participant according to the gradient information uploaded by all participants, and issues the correctedgradient information to each participant; and each participant receives the corrected gradient information fed back by the coordinator, and updates the representation vector of the node based on thecorrected gradient information of the coordinator. Information interaction can be realized under the condition of guaranteeing the information security of each participant.
Owner:成都数联铭品科技有限公司
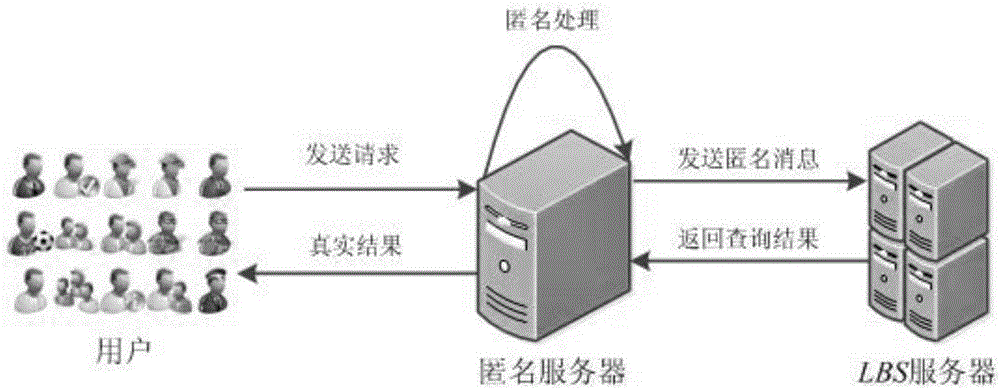
Mass equal request-oriented k-anonymous location privacy protection method
ActiveCN105792130AReduce computational overheadSolve the problem that the level of anonymity and privacy cannot be achievedTransmissionLocation information based serviceQuality of servicePrivacy protection
The invention discloses a mass equal request-oriented k-anonymous location privacy protection method, specifically comprising the steps of defining a user request message at a specific location; performing, by an anonymous server, anonymous processing on the user request message to generate a request message, and sending the request message to an LBS (Location-Based Service) server; returning, by the LBS server, a query result to the anonymous server; and after the anonymous server receives the query result returned by the server, performing traversing query on request messages in a current cluster, filtering respective needed real result according to the location of each user, returning the real result to each user, and finally emptying all messages of the current cluster. The method effectively reduces the computing consumption caused by repeated query while protecting the location privacy of mobile users, simultaneously reduces the communication overhead, and effectively improves the quality of service.
Owner:JIANGSU CIMER INFORMATION SECURITY TECH
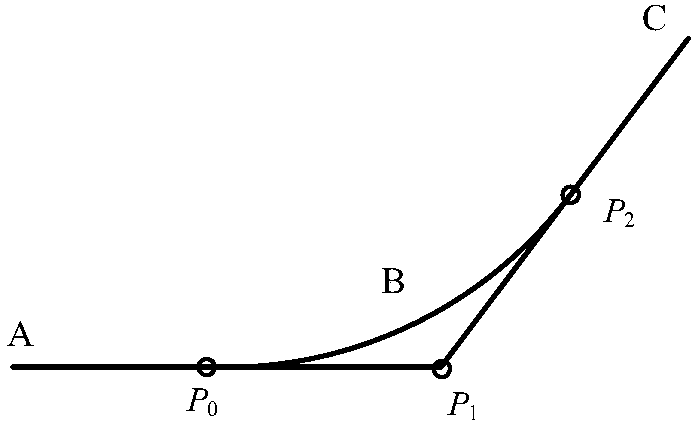
Trajectory link control method for Delta robot based on Bezier curve
ActiveCN108568817AHigh speedImprove smoothnessProgramme-controlled manipulatorDelta robotJoint spaces
The invention relates to a trajectory link control method for a Delta robot based on a Bezier curve. The trajectory link control method is characterized in that the method establishes a curve arc length model, and the curve arc length model represents the corresponding relation between the arc length of the Bezier curve and a curve parameter, the Bezier curve is constructed according to a given trajectory parameter and the curve arc length model to obtain a Cartesian space coordinate, transforming the Cartesian space coordinate to a joint space angle of the Delta robot based on an inverse kinematic model of the Delta robot, and carrying out trajectory link on the Delta robot. Compared with the prior art, the trajectory link control method for the Delta robot based on the Bezier curve disclosed by the invention has the advantages of improving the smoothness of the end motion of the Delta robot, reducing the loss of a motor and the like.
Owner:TONGJI UNIV
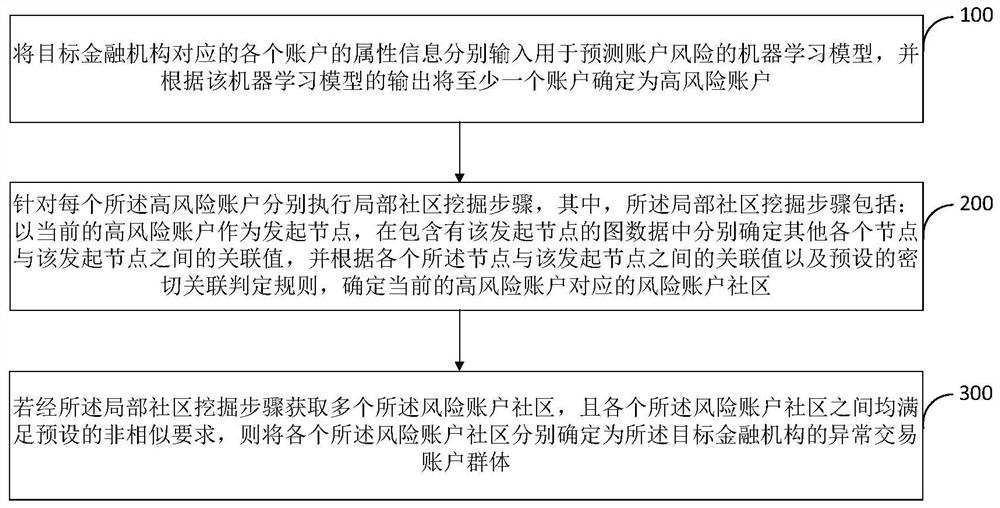
Abnormal transaction account group identification method and device
PendingCN111784502AImprove efficiencyImprove effectivenessFinanceEnsemble learningFinancial transactionData mining
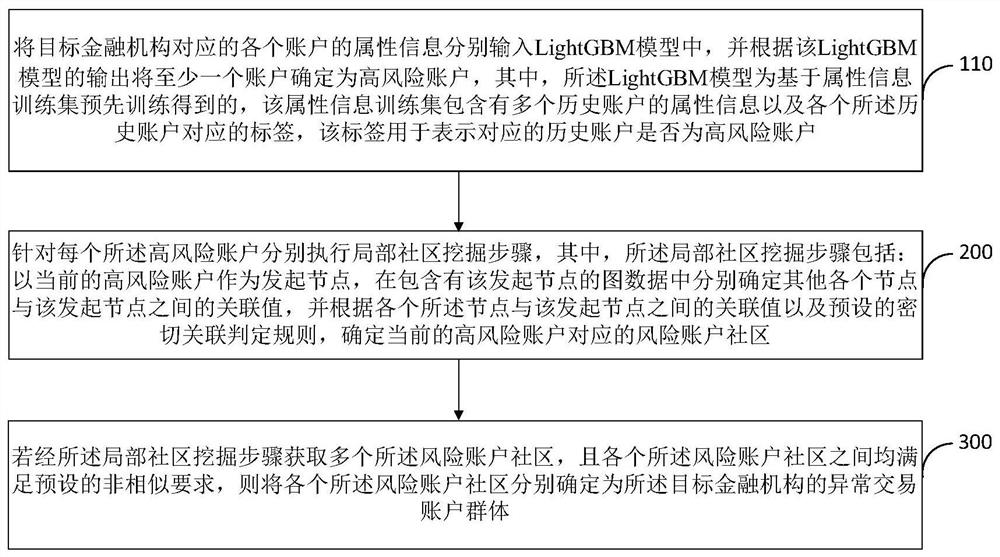
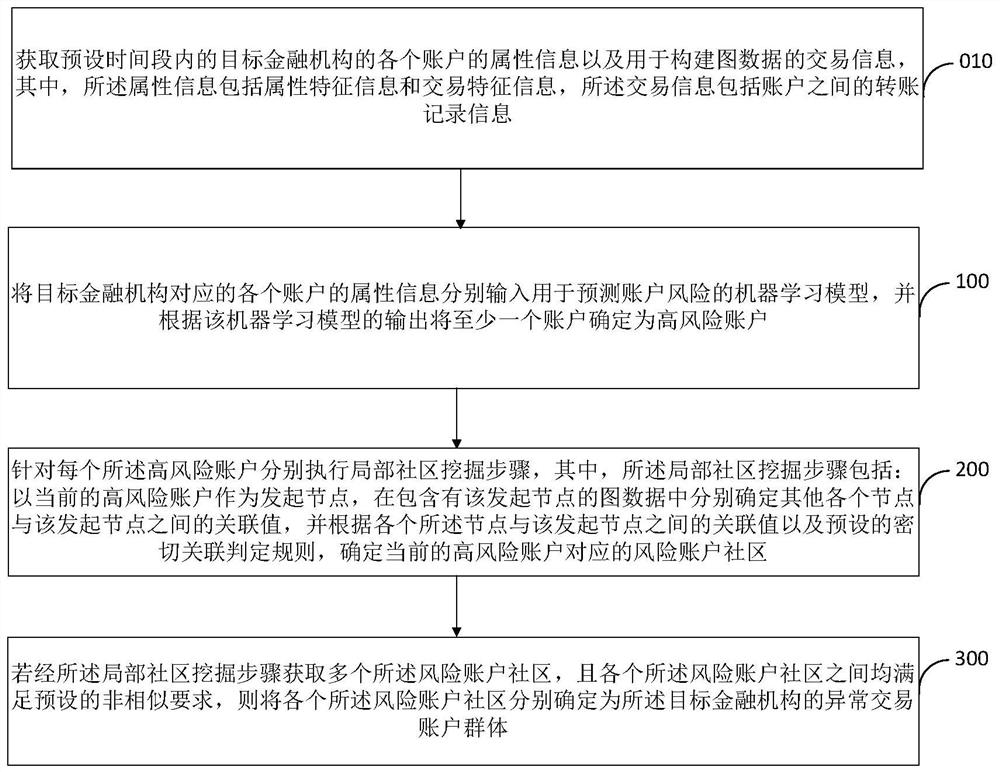
The embodiment of the invention provides an abnormal transaction account group identification method and device. The method comprises the steps of respectively inputting the attribute information of each account into a machine learning model for predicting an account risk, and determining at least one account as a high-risk account; respectively executing a local community mining step for each high-risk account: taking the current high-risk account as an initiating node, respectively determining association values between other nodes and the initiating node in the graph data, and determining arisk account community corresponding to the high-risk account; and if a plurality of risk account communities are obtained and the risk account communities meet a preset non-similar requirement, determining each risk account community as an abnormal transaction account group of the target financial institution. According to the invention, the efficiency, reliability and accuracy of abnormal transaction account group identification can be effectively improved, and the operation safety and reliability of a financial institution obtaining an abnormal transaction account group through identification can be further improved.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Terrain classification and recognition method based on learned vibration information
InactiveCN108830325AHigh feasibilityImprove accuracyScene recognitionLearning basedPattern recognition
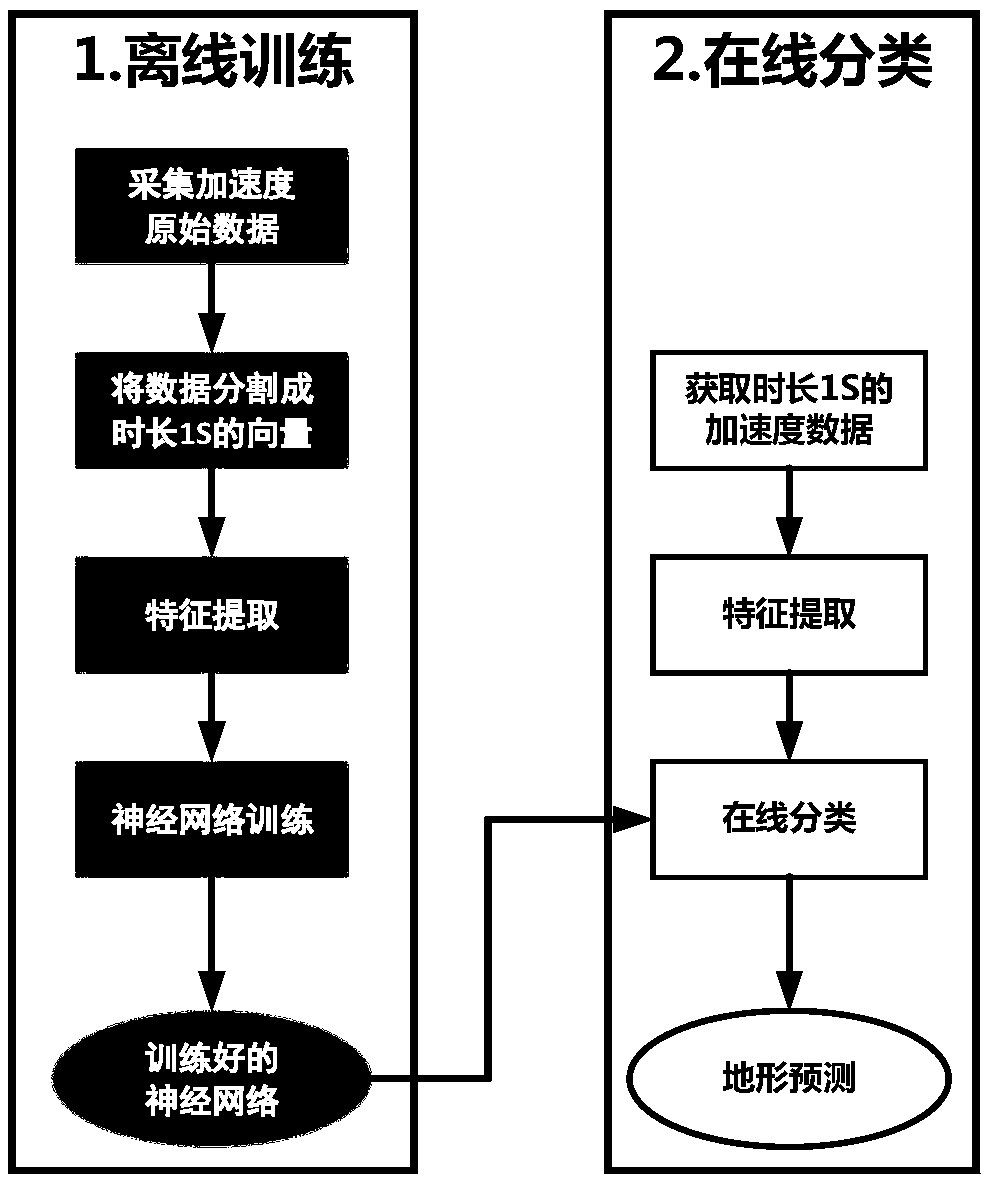
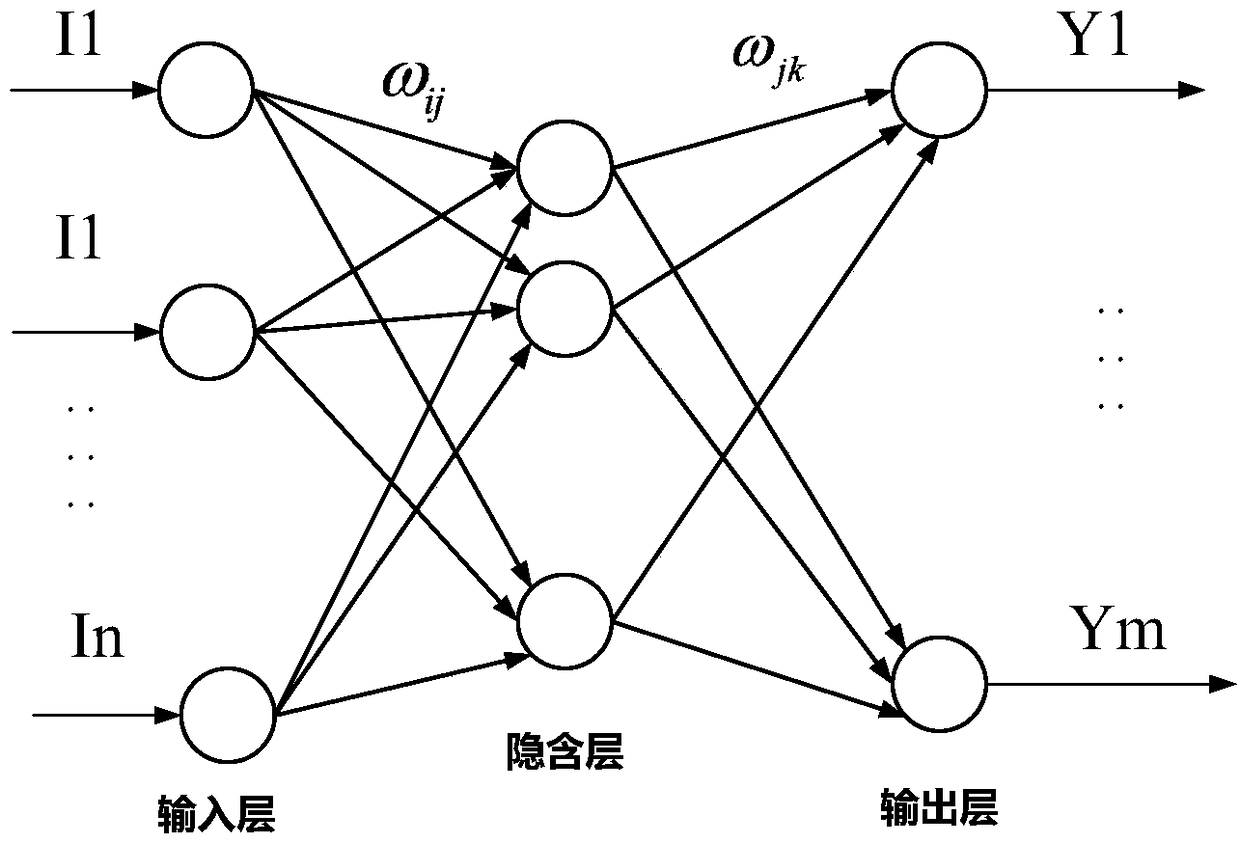
The invention relates to a terrain classification and recognition method based on learned vibration information, which aims to solve a problem of low accuracy of the existing classification and recognition method. The terrain classification and recognition method comprises the steps of first, collecting original data of vibration information of a sensor in the x-axis, y-axis and z-axis directionsin a coordinate system; second, performing segmentation processing on the original data to form n vectors with the time length being 1s; third, performing terrain type marking on the n vectors; fourth, converting the segmented n vectors into a frequency domain; fifth, performing off-line learning training on the n vectors converted into the frequency domain by using a multilayer feedforward neuralnetwork to obtain a trained multilayer feedforward neural network; and sixth, obtaining vibration data online in real time, executing the step two to the step four, and performing online classification and recognition by using the trained multilayer feedforward neural network in the step five to obtain the terrain type. The terrain classification and recognition method is applied to the technicalfield of recognition and classification.
Owner:HARBIN INST OF TECH
Graph neural network training method and device
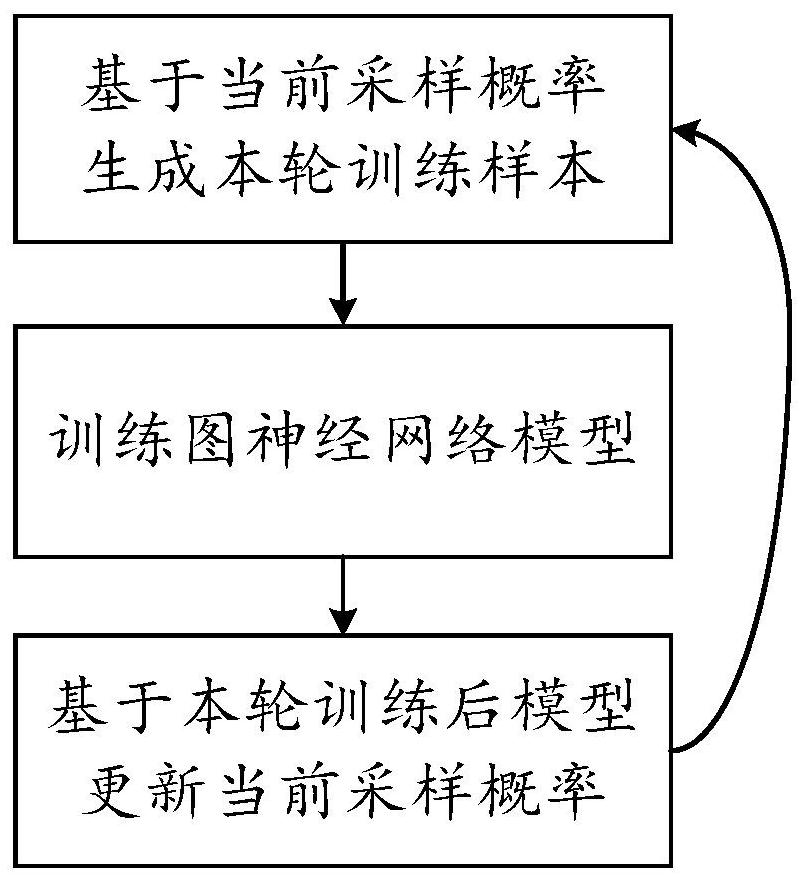
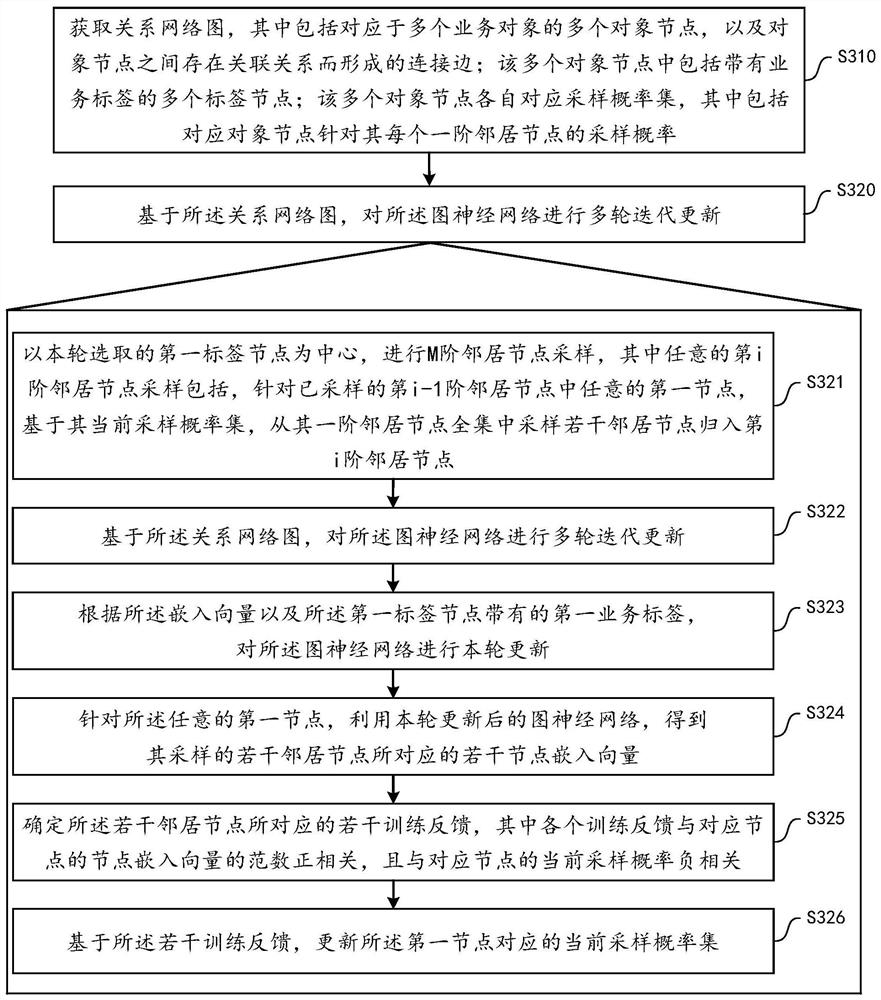
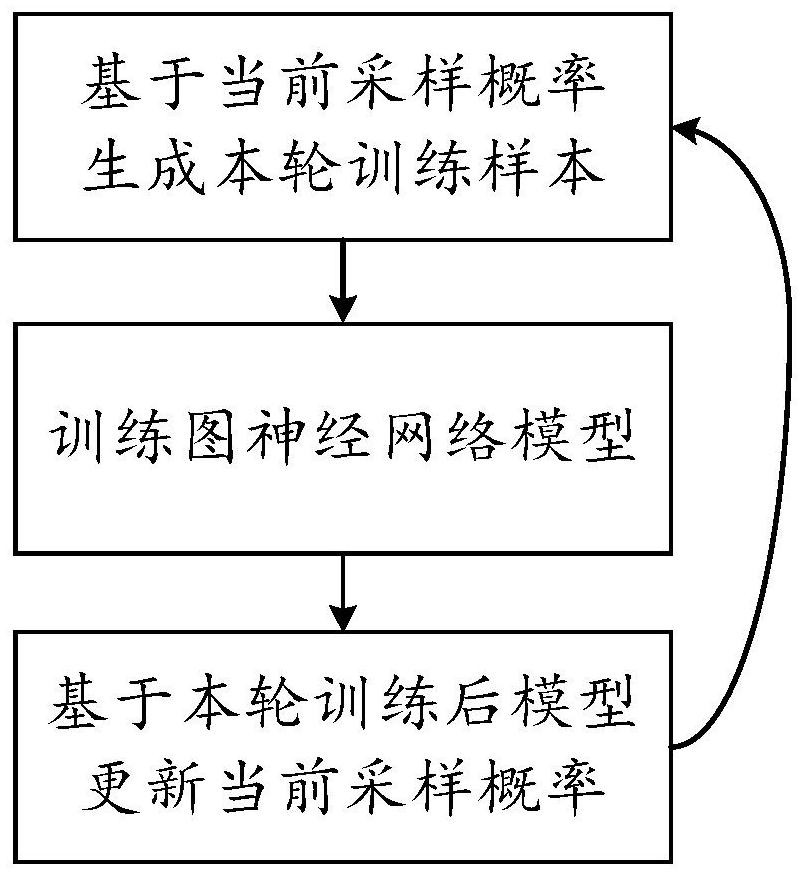
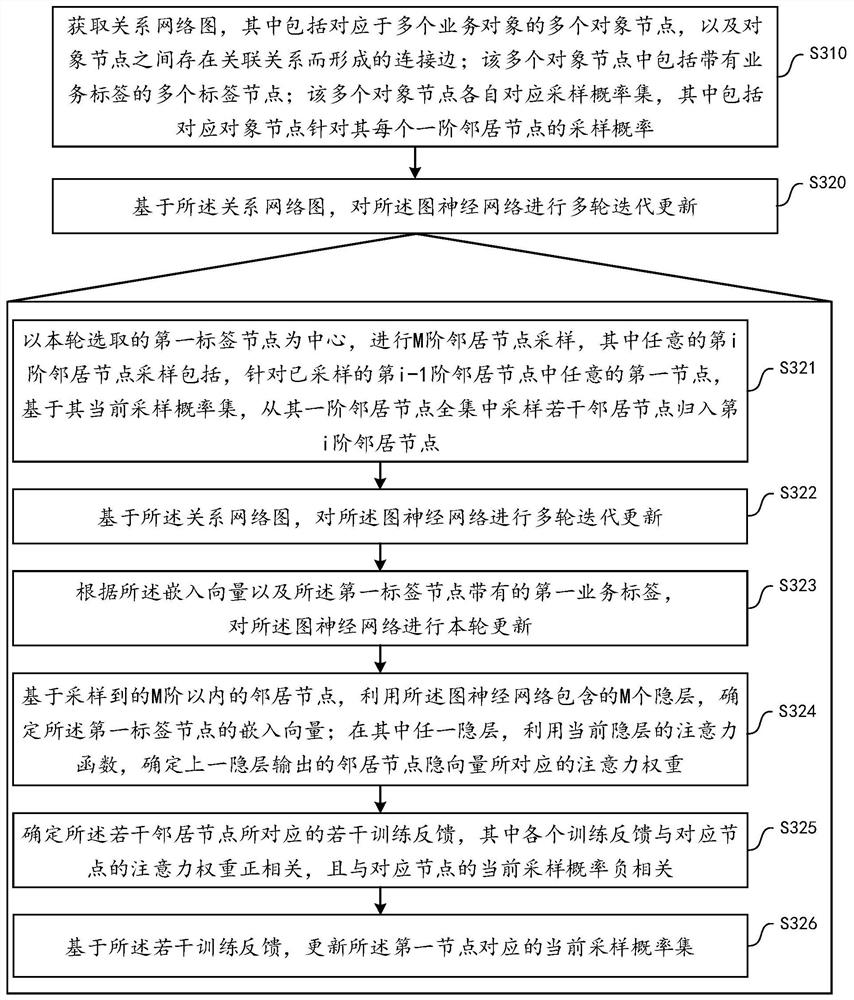
ActiveCN112085172AGuaranteed accuracyReduce memory usageNeural architecturesNeural learning methodsAlgorithmTheoretical computer science
The embodiment of the invention provides a graph neural network training method, wherein the method comprises the steps: obtaining a relation network graph, wherein each object node corresponds to a sampling probability set, and the sampling probability set comprises the sampling probability of each first-order neighbor node; performing multiple rounds of iterative updating on the graph neural network on the basis of the relation network graph, wherein any round comprises the steps of performing M-order neighbor node sampling by taking a first label node selected in the round as a center, wherein any i-order neighbor node sampling comprises any first node in a sampled i-1-order neighbor nodes; based on a current sampling probability set, sampling a plurality of neighbor nodes from a first-order neighbor node full set, and classifying the neighbor nodes into an i-order neighbor node; performing the current round of updating on the graph neural network based on the sampled neighbor nodes within the M order and the first service label carried by the first label node; and determining a plurality of training feedbacks corresponding to the plurality of neighbor nodes by using theupdated graph neural network, and then updating the current sampling probability set of the first node.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
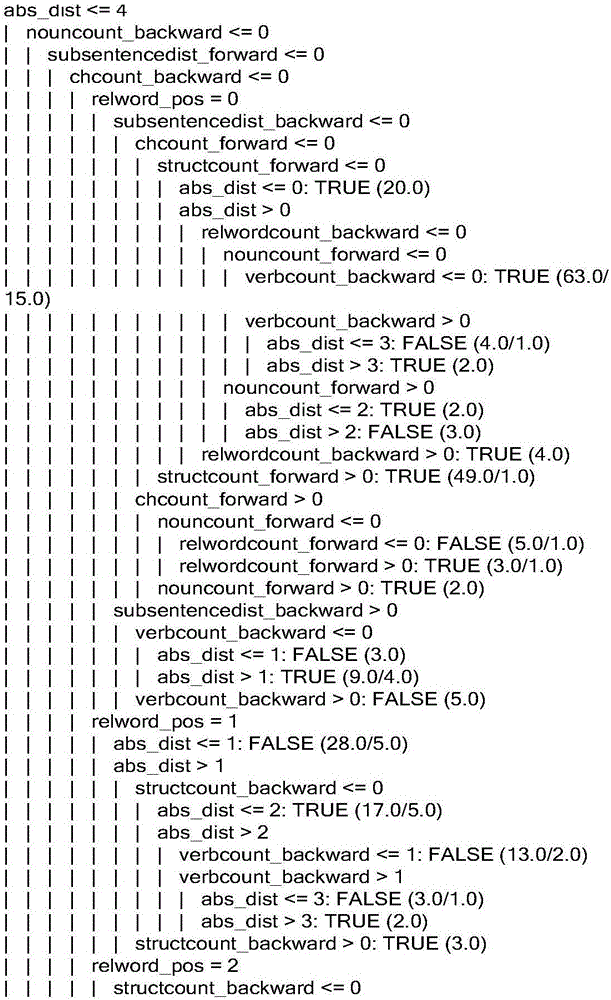
High-precision Chinese predicate identification method
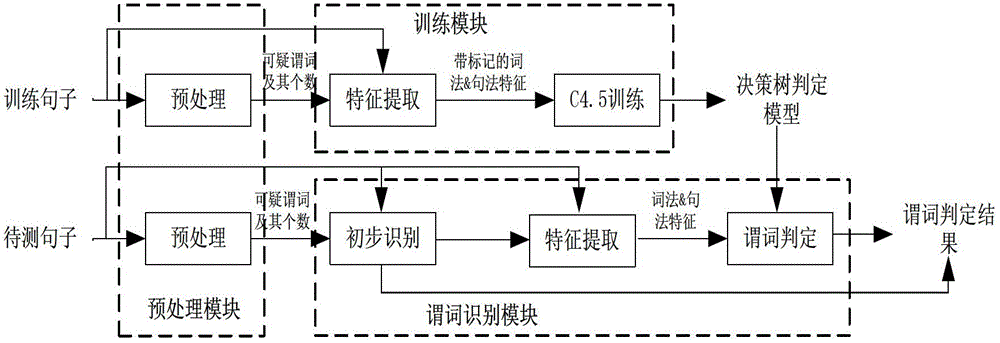
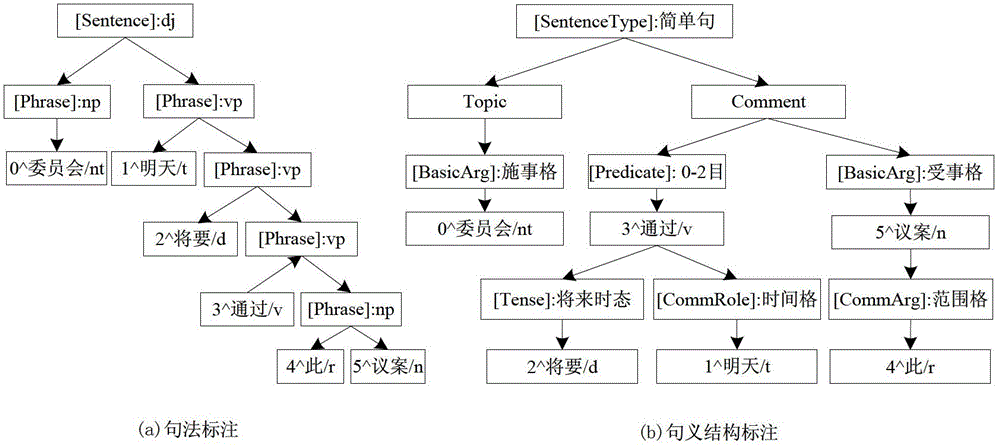
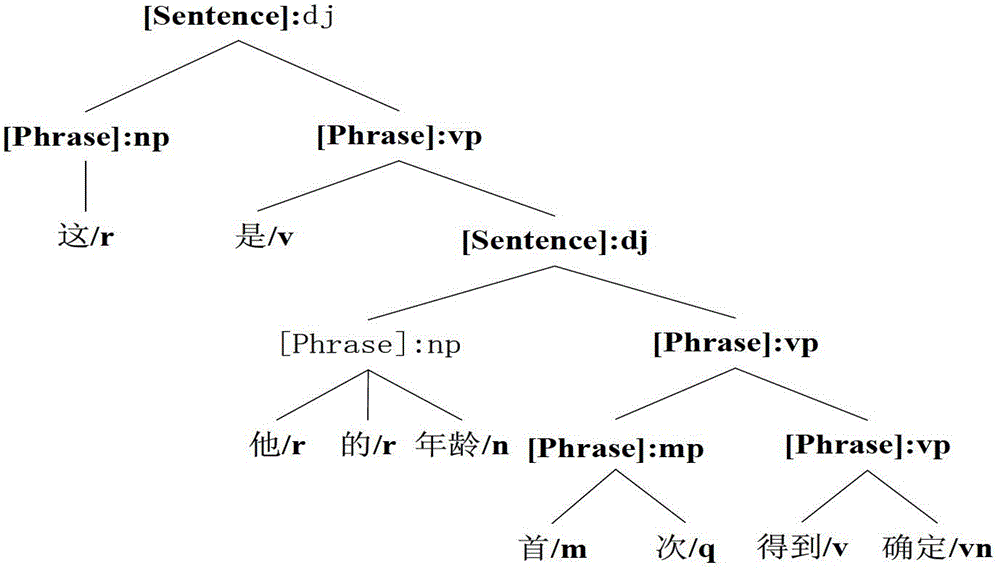
InactiveCN103150381AImprove accuracyImprove recognition efficiencySpecial data processing applicationsLexical analysisHigh effectiveness
The invention relates to a predicate identification method based on a combination of rules and statistics, and belongs to the field of natural language processing and machine learning. The identification method aims at achieving high-precision and high-efficiency predicate identification. The stepped identification method identifies predicates from morphology and syntax labeled sentences, and comprises the steps of conducting morphological analysis on the sentences to be detected, obtaining suspicious predicates and a number thereof, preliminarily identifying the predicates by using preliminary identification judgment conditions, extracting relevant morphological and syntactic characteristics of the suspicious predicates dissatisfying the preliminary identification judgment conditions, judging the predicates with a decision-making tree judgment model obtained from C4.5 training, and finally summarizing identification results in the two steps to present the predicates of the sentences to be detected. The identification method has the characteristics of high accuracy rate, identification speed and identification rate for the non-verbal predicates, and the like, is applicable to the field requiring high-precision Chinese predicate identification, greatly promotes development of sentence meaning analysis, and has high application and popularization values.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
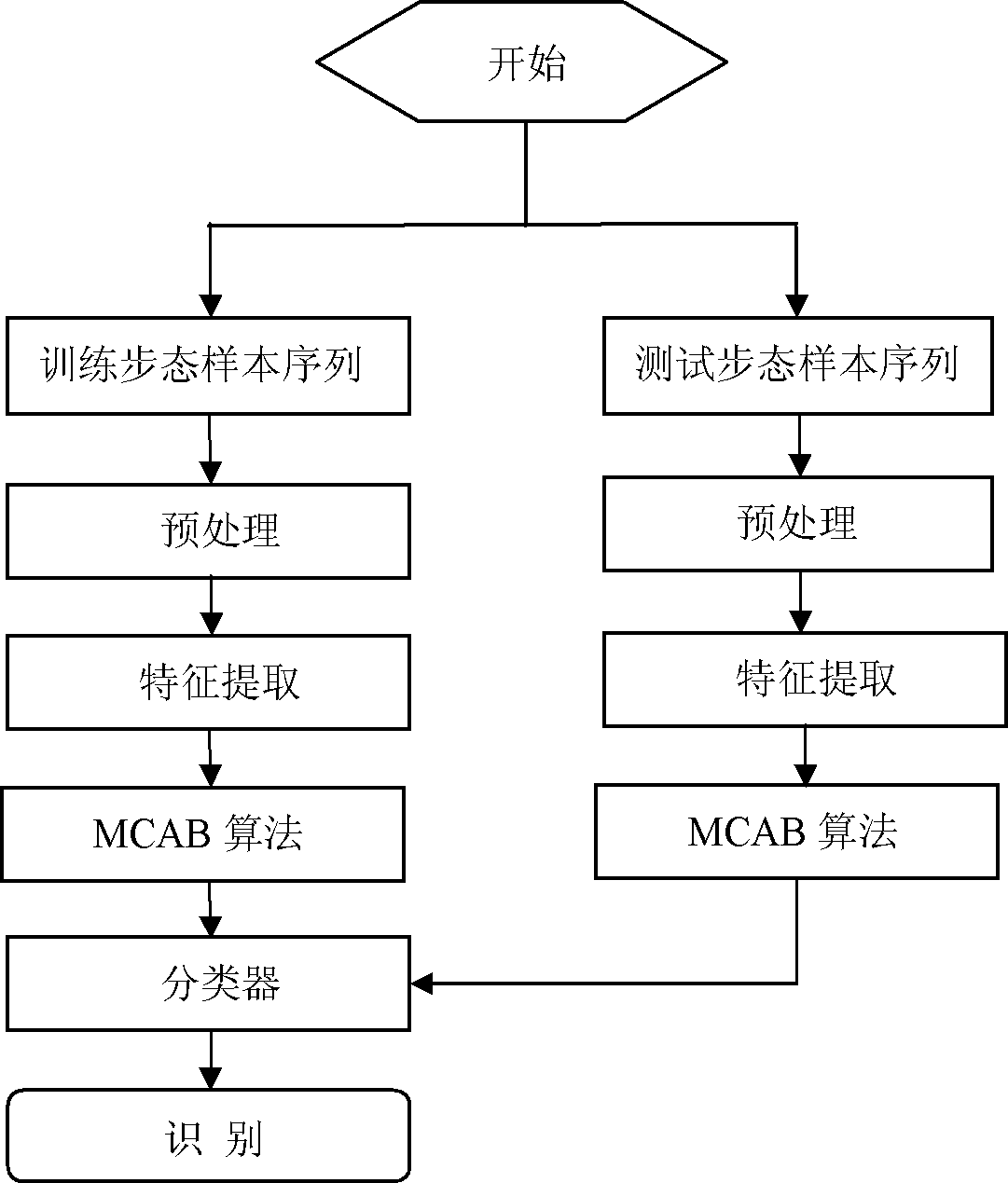
Multi-class Bagging gait recognition method based on multi-characteristic attribute
InactiveCN102663374AReduce data volumeImprove accuracyCharacter and pattern recognitionFeature extractionPrincipal component analysis
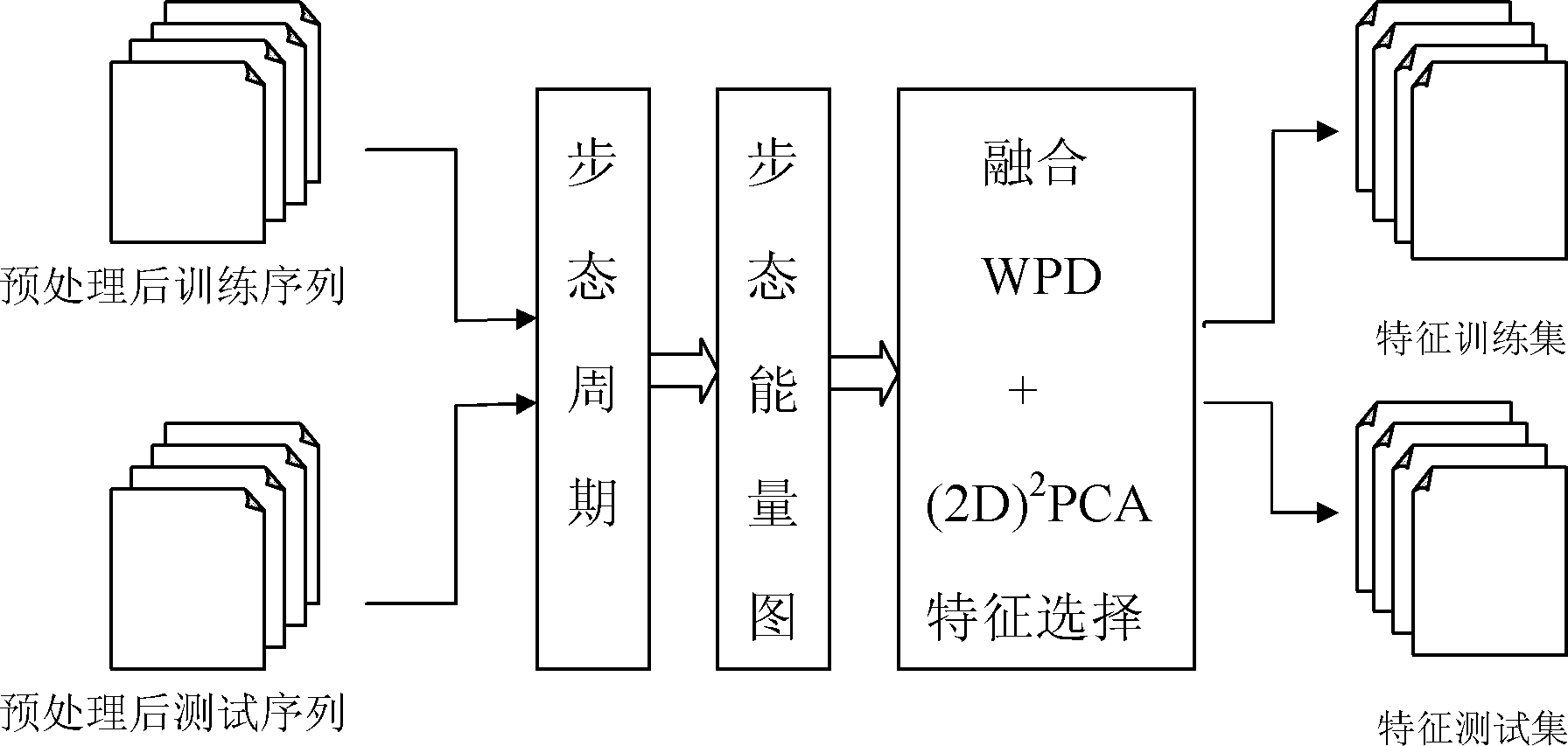
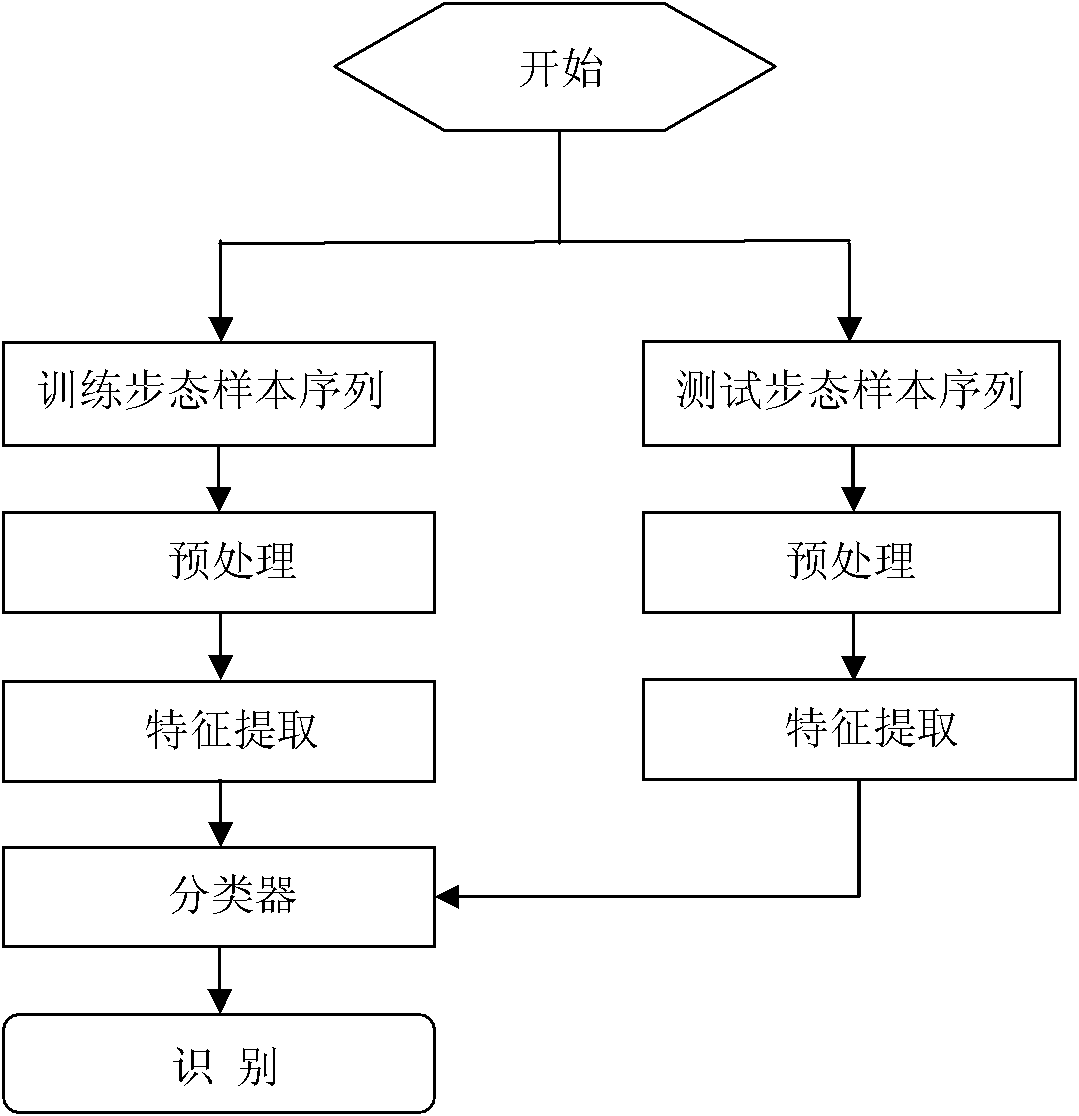
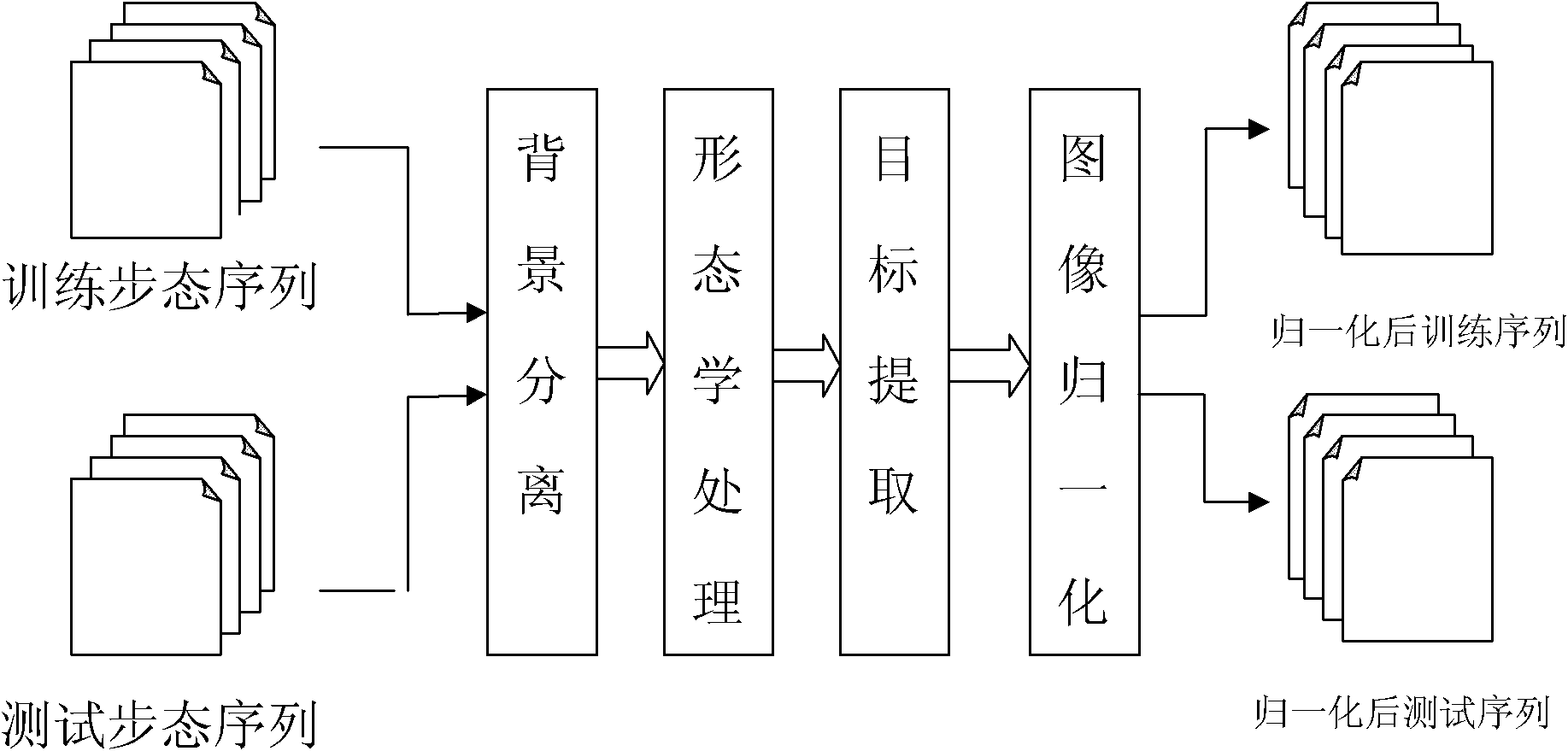
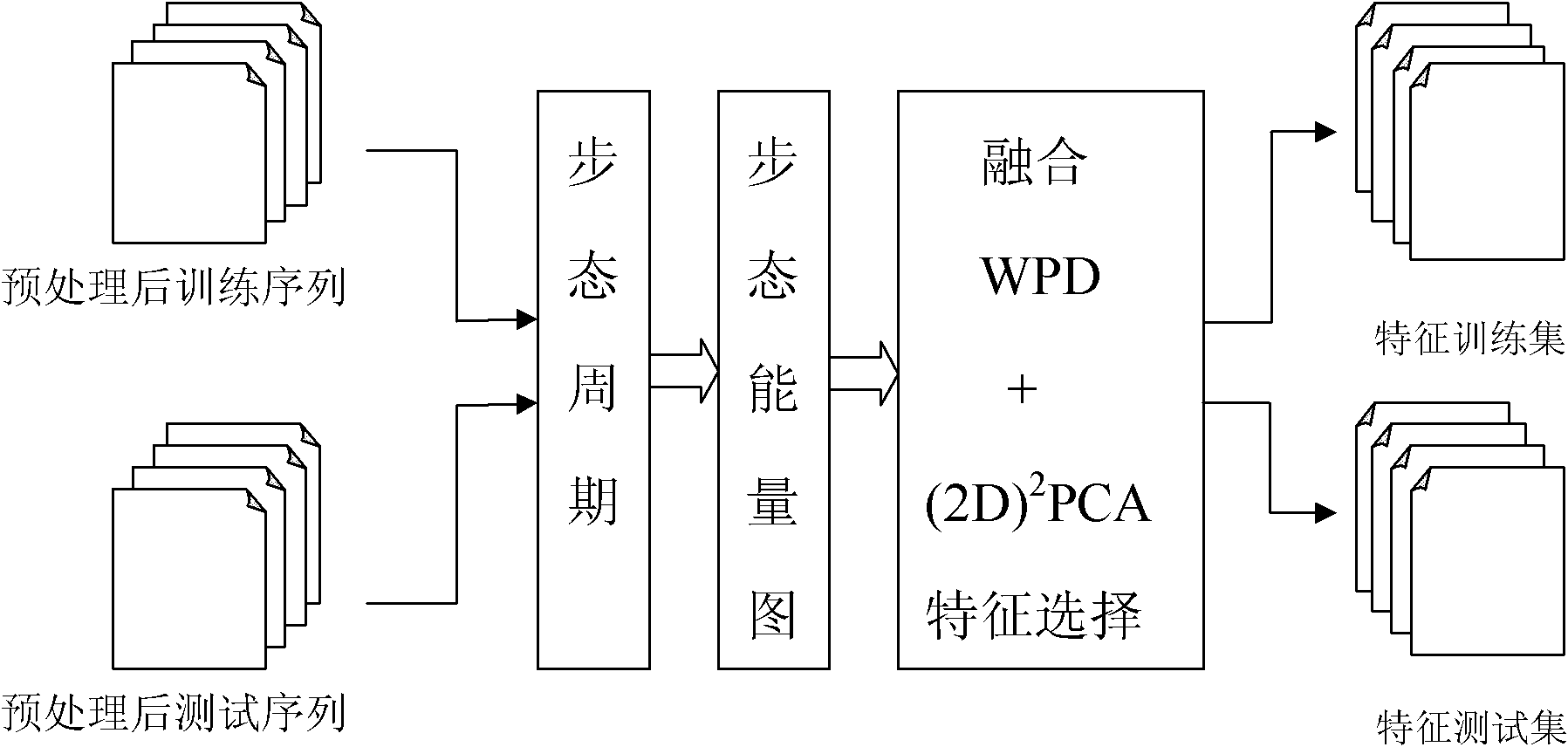
The invention relates to a multi-class Bagging gait recognition method based on a multi-gait characteristic attribute, which belongs to the technical field of pattern recognition. According to the method, a nearest neighbor classifier is used as a weak classifier, and an integration classifier is constructed by expanding a two-class attribute Bagging method to a plurality of classes on the basis of 20 gait attribute characteristic sets after wavelet packets are decomposed and principal components are completely analyzed so as to carry out gait identity identification. The method comprises the following steps of: preprocessing, extracting characteristics and finally classifying test samples by using a method combining a nearest neighbor classifying principle and an MCAB algorithm. According to the multi-class Bagging gait recognition method based on the multi-gait characteristic attribute, a method fusing wavelet packet decomposition (WPD) and (2D) 2 principal component analysis (PCA) is adopted for the first time to extract and also select gait characteristics. The problem of loss of high-frequency components in a traditional gait recognition method based on wavelet transformation or overlarge dimensionality caused by simply adopting all data is solved. The multi-class Bagging gait recognition method based on the multi-gait characteristic attribute has higher recognition rate and visual angle change robustness.
Owner:BEIJING UNIV OF TECH
Intelligent underwater robot autonomous butting method based on bi-sight-vision guiding
ActiveCN104766312AImprove reliabilityLarge docking position deviationImage analysisVision processingControl theory
The invention relates to an intelligent underwater robot autonomous butting method based on bi-sight-vision guiding. The intelligent underwater robot autonomous butting method comprises the steps that firstly, three-dimensional calibration is conducted on a bi-sight-vision system; secondly, an image collecting module collects bi-sight-vision images, and the bi-sight-vision images are transmitted to a light vision processing computer through a bus; thirdly, whether an intelligent underwater robot achieves butting successfully or not is judged, if not, the second step is executed, and if yes, the procedure is stopped. According to the intelligent underwater robot autonomous butting method, gauss downsampling and nonlinear transforming are conducted on the collected left view and the collected right view of the bi-sight-vision system, noise in the images is effectively restrained, the calculation consumption is reduced, and the real-time performance and the robustness of the autonomous butting method are guaranteed.
Owner:HARBIN ENG UNIV
Three-dimensional scene reconstruction method and device and storage medium
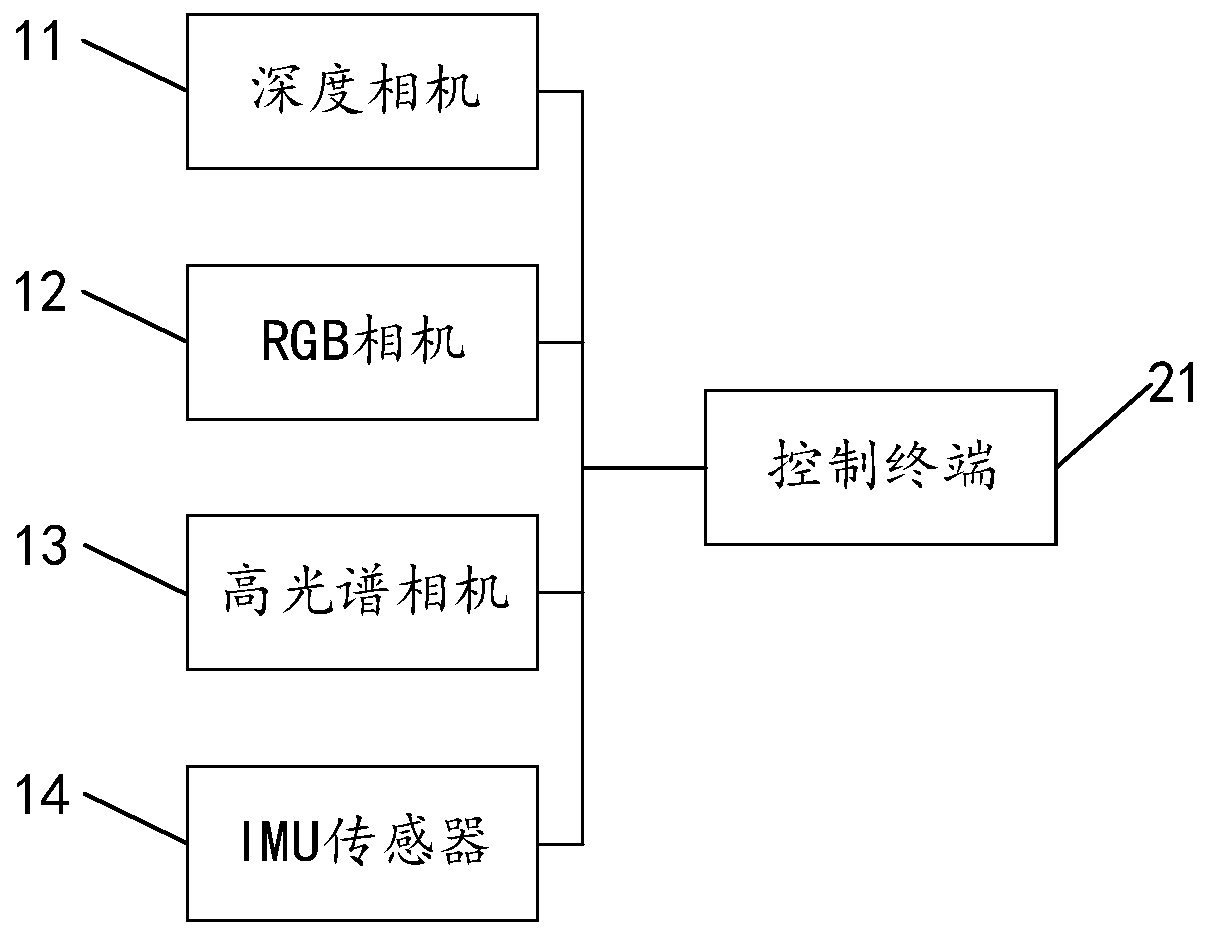
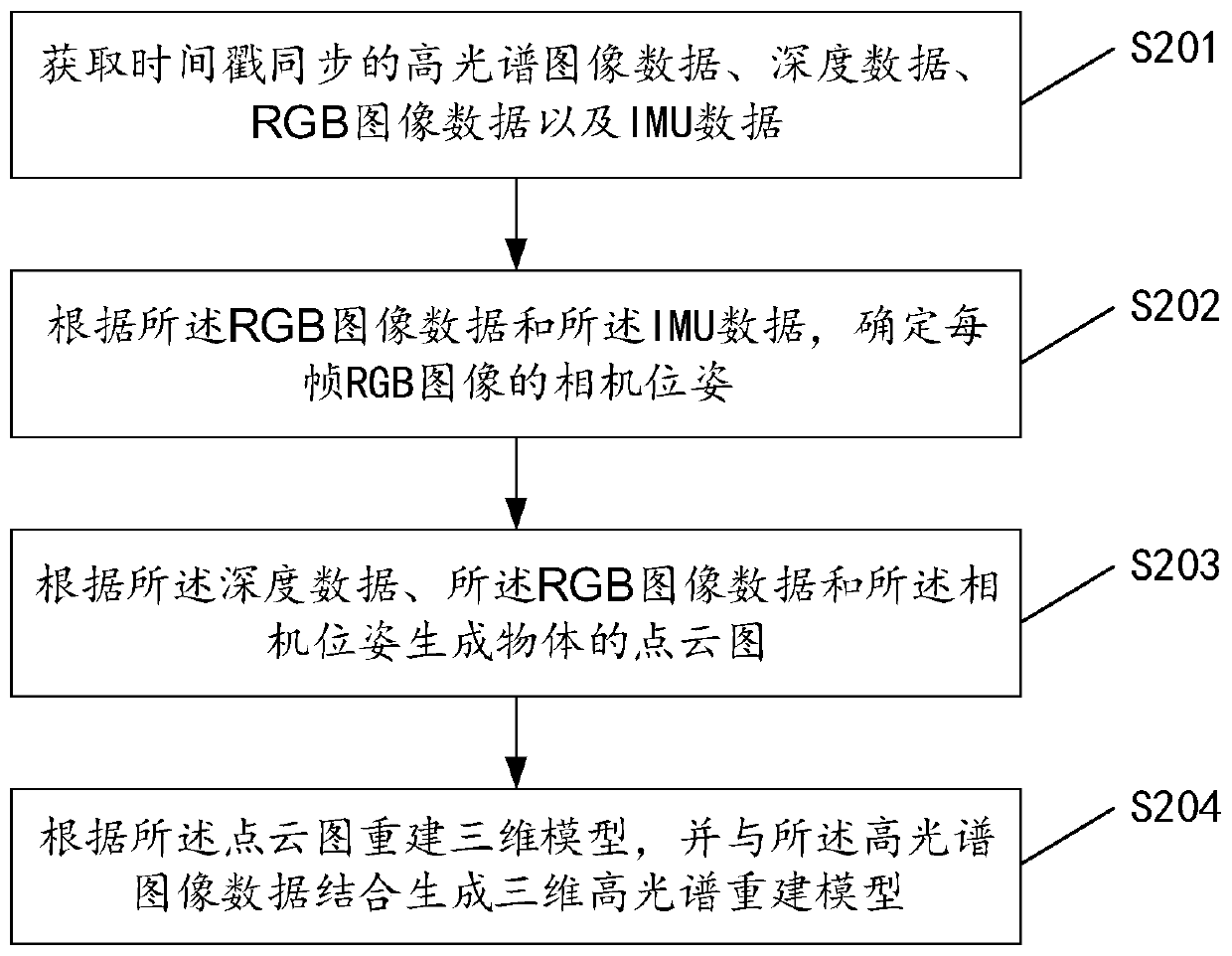
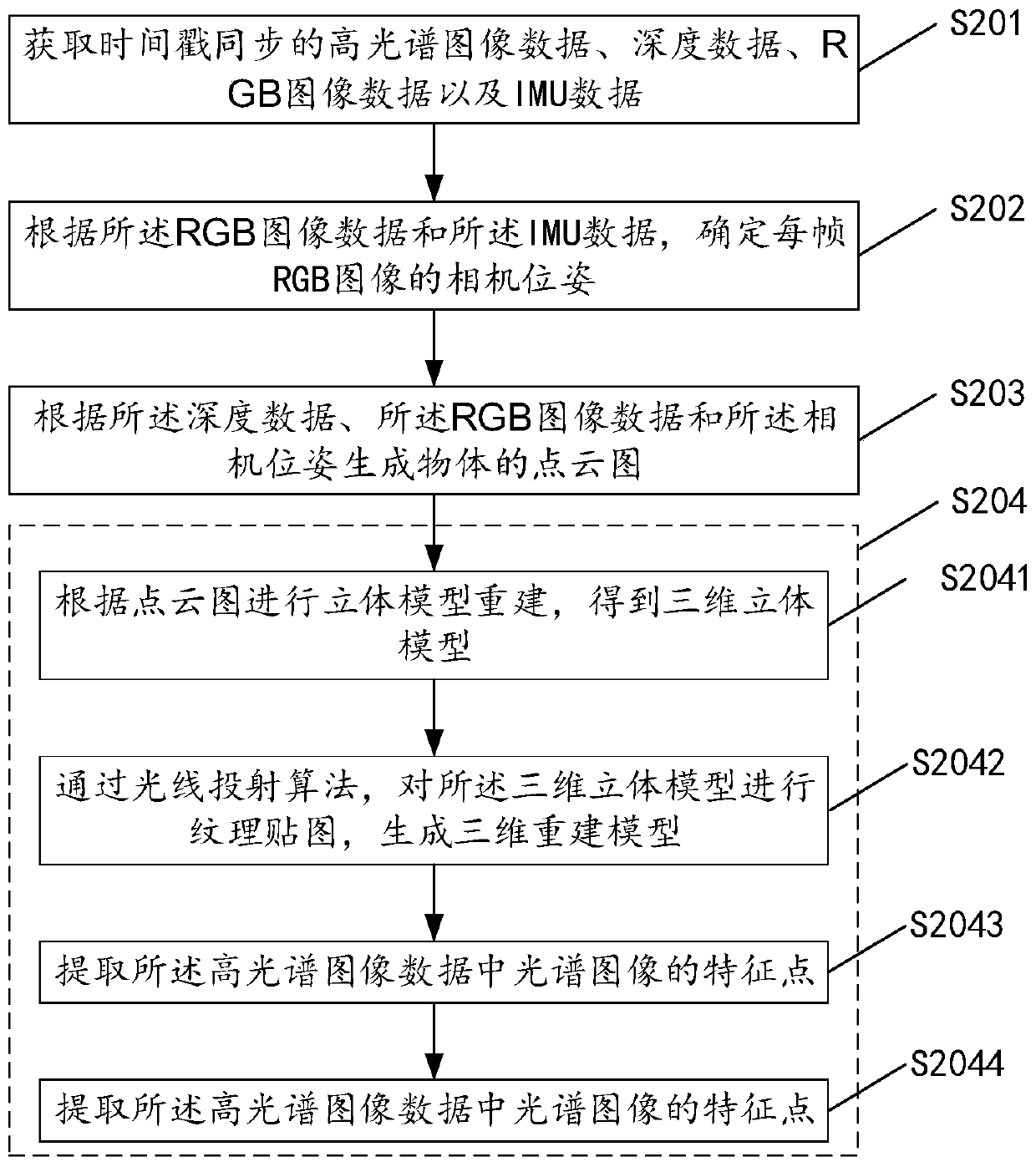
ActiveCN109978931ASpeed up 3D reconstructionReduce computing consumptionImage enhancementImage analysisInertial measurement unitThree dimensional model
The invention discloses a three-dimensional scene reconstruction method and device and a storage medium. The method comprises the steps of obtaining the hyperspectral image data, the depth data, the three-primary-color RGB image data and the inertial measurement unit IMU data which are synchronous in timestamp; determining a camera pose of each frame of RGB image according to the RGB image data and the IMU data; generating a point cloud picture of an object according to the depth data, the RGB image data and the camera pose; and reconstructing a three-dimensional model according to the point cloud picture, and combining the hyperspectral image data to generate a three-dimensional hyperspectral reconstruction model. According to the method provided by the embodiment of the invention, the time for generating the three-dimensional hyperspectral reconstruction model is shorter, and the real-time three-dimensional scene reconstruction can be realized.
Owner:中科海微(北京)科技有限公司
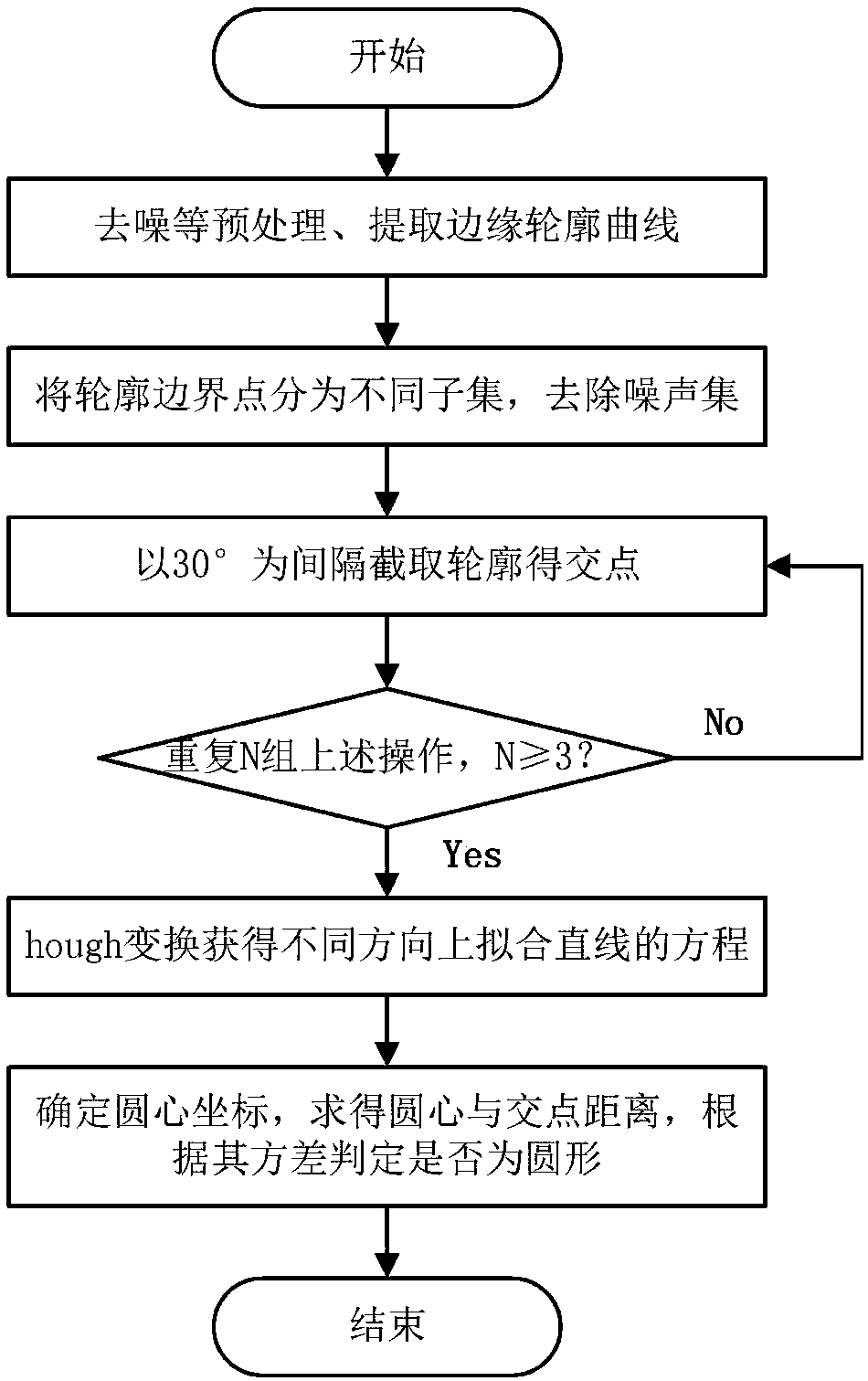
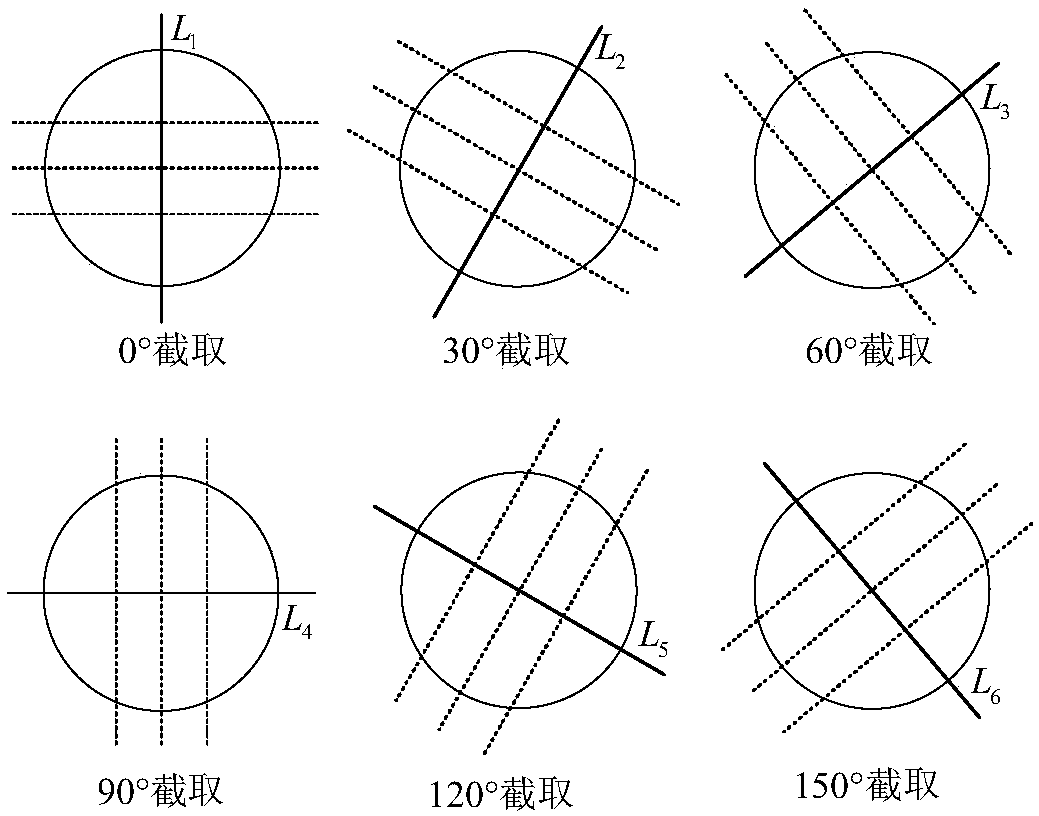
A hub contour detection method based on improved Hough transform
InactiveCN108986038AReduce computing consumptionSpace Dimensionality ReductionImage enhancementImage analysisHough transformIntersection of a polyhedron with a line
The invention discloses a hub contour detection method based on improved Hough transform, which comprises the following steps: firstly, preprocessing the wheel hub image to extract the edge contour curve of the wheel hub; then dividing the contour boundary points into different subsets and removing the noise set; obtaining the intersection points of each section line and contour line by cutting the images at intervals of 30 degrees, and obtaining the equations of fitting straight lines in different directions by Hough transform; determining the coordinates of the center of the circle, obtaining the distance between the center of the circle and the intersection point, judging whether the circle is circular or not according to its variance, and finally obtaining the center and radius of thecircle. Compared with conventional Hough transform and a random Hough transform algorithm, the detection method of the invention has the advantages of short running time, fast running speed and higherdetection precision.
Owner:ZHEJIANG UNIV
High-spectral image sharpening method based on probability matrix decomposition
ActiveCN106447630AEasy extractionEasy to learnImage enhancementImage analysisHypothesisDecomposition
The invention discloses a high-spectral image sharpening method based on probability matrix decomposition, and belongs to the field of remote sensing image processing. The method is characterized in that the method comprises the steps: carrying out the preprocessing of two inputted images based on the hypothesis that a pixel spectrum vector of a high-resolution high-spectral image is just formed by the linear superposition of a few of vectors with the hidden spectrum features according to one low-resolution high-spectral image and one high-resolution high-spectral image and the frequency response matrix, decomposition matrix dimensions and algorithm iteration number, corresponding to the high-spectral images, of a multispectral camera, wherein the low-resolution high-spectral image and the high-resolution high-spectral image are taken at the same height in the same target region at the same time; listing mathematical equations of the two processed images and a to-be-solved high-resolution high-spectral image, and building a Bayesian model; calculating the posteriori probability distribution of the decomposition matrix, and obtaining a matrix with the hidden spectrum features in the decomposition matrix, and solving the mean value of linear superposition vectors corresponding to the two images after preprocessing, thereby obtaining the to-be-solved high-resolution high-spectral image. The method greatly reduces the time consumption of calculation while improving the sharpening precision, and is easy to adjust.
Owner:TSINGHUA UNIV
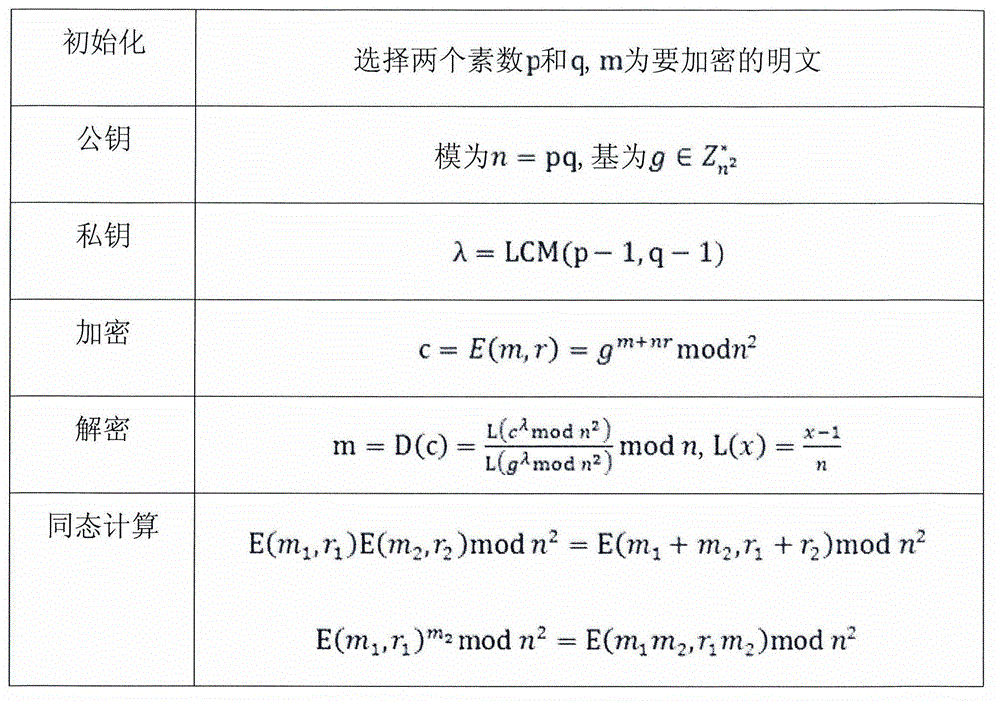
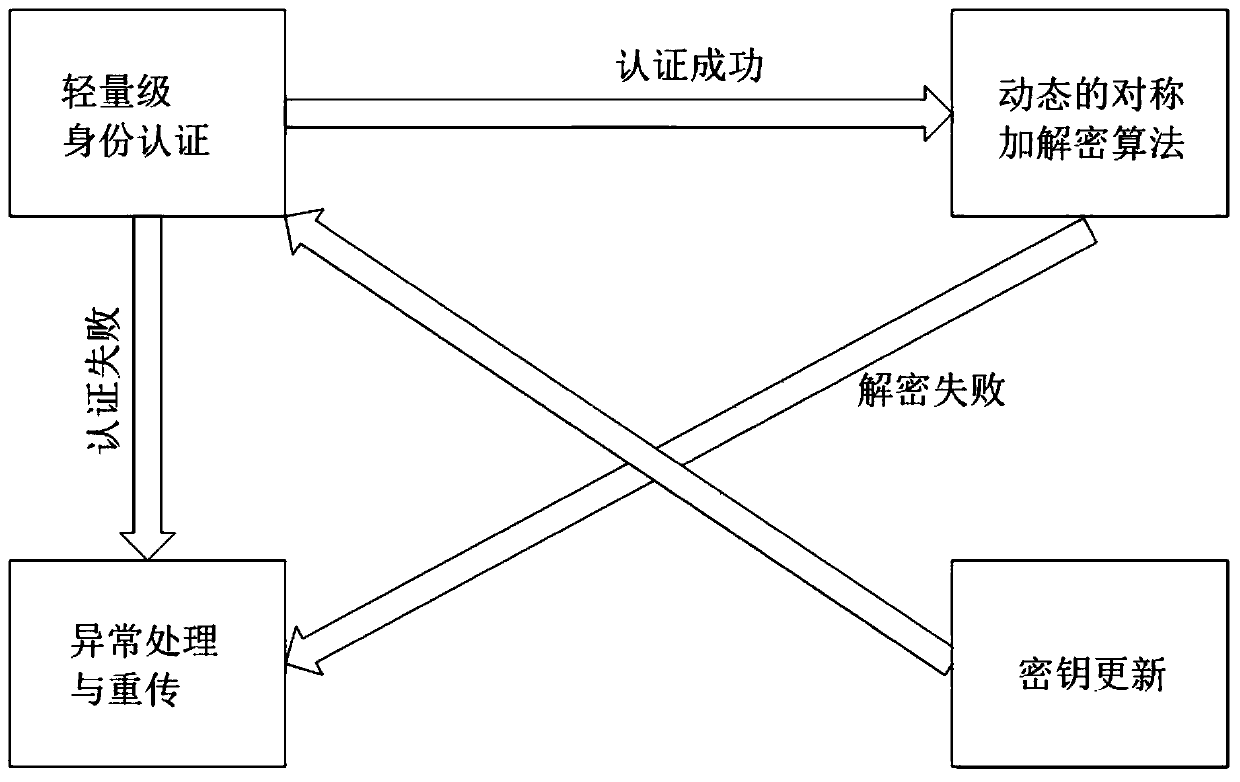
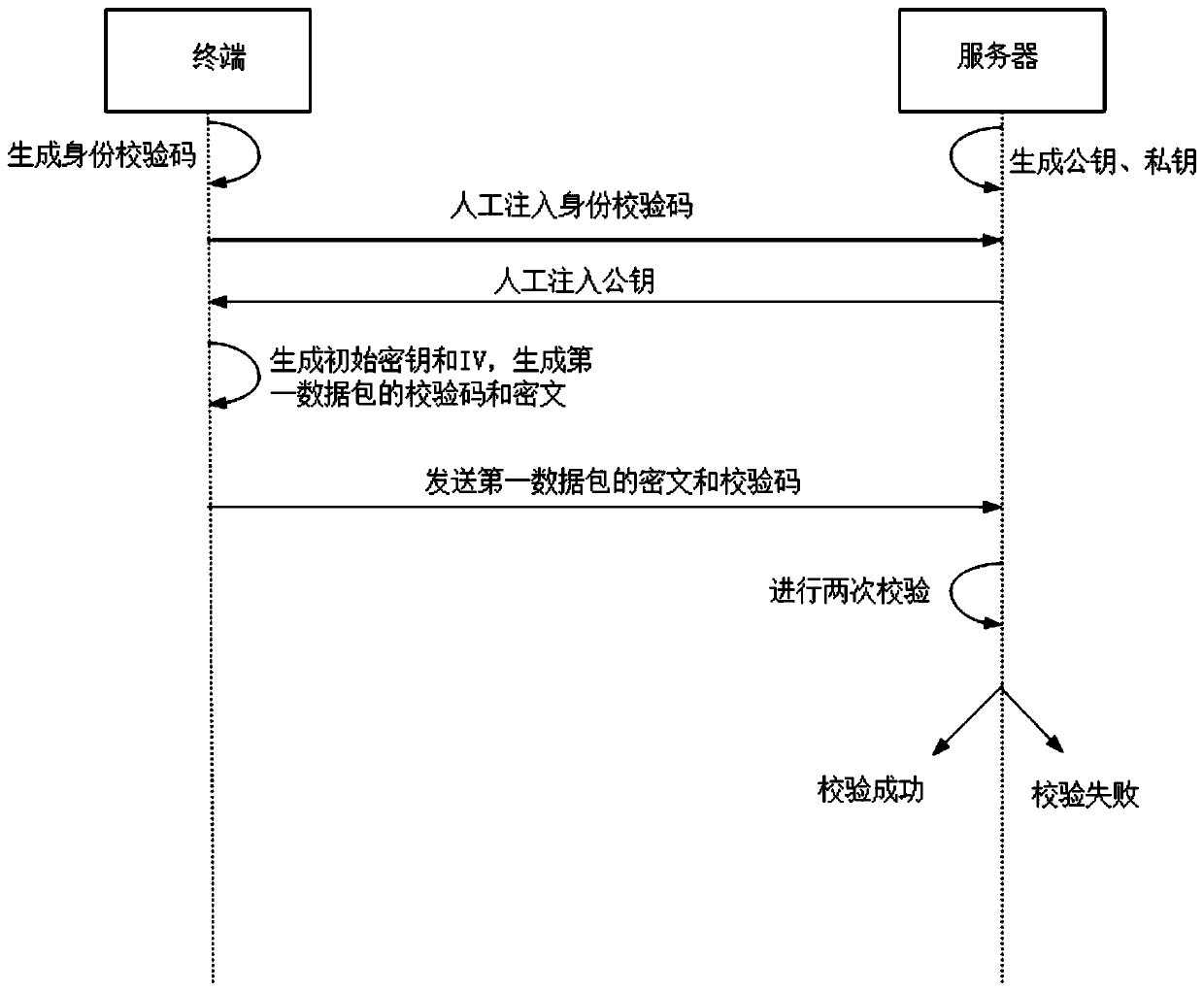
Security hybrid encryption method based on narrowband Internet of Things
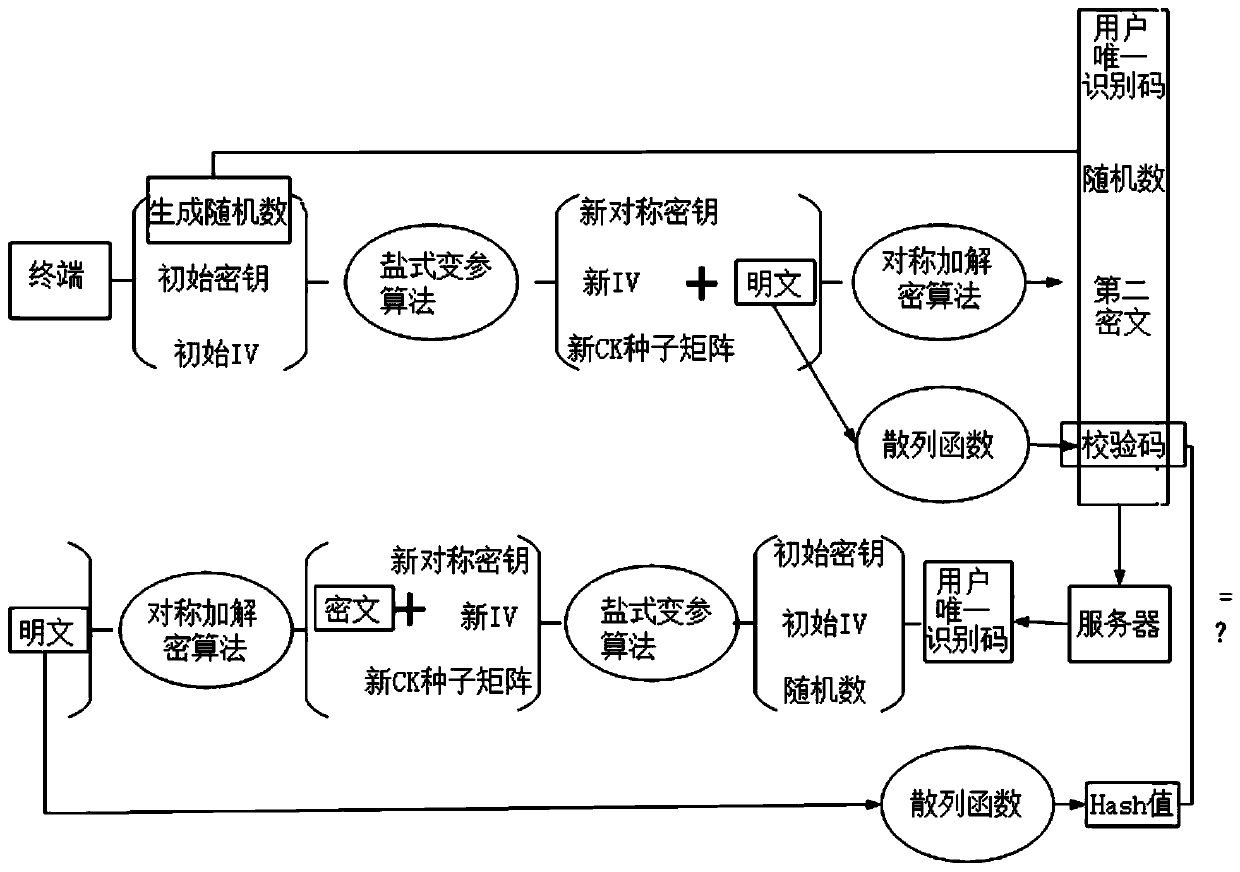
ActiveCN111541677AIncrease aggressivenessEasy to primeKey distribution for secure communicationMultiple keys/algorithms usageIdentity recognitionEngineering
The invention provides a security hybrid encryption method based on narrowband Internet of Things, which comprises the following steps of carrying out lightweight identity authentication on each terminal and a server, and realizing the identity authentication of the terminal and the transmission of an initial key and an initial IV vector by using unidirectional asymmetric encryption in the lightweight identity authentication, and after the identity authentication of the terminal succeeds, performing encryption communication between the terminal and the server by adopting a dynamic symmetric encryption and decryption algorithm, so that the symmetric encryption and decryption algorithm uses different symmetric keys and different structural parameters in each time of encryption communicationof each terminal. Lightweight identity recognition is adopted; on the basis of ensuring the security, the authentication time and the calculation consumption are greatly reduced, a dynamic symmetric encryption and decryption algorithm is adopted, a symmetric key and a set of structural parameters are ensured to be set at a time, the structural parameters of the algorithm are changed in a nonlinearmode under the condition that the large structure is not changed, and the capacity of the algorithm for resisting side channel attacks such as energy analysis is improved.
Owner:SHANGHAI INST OF MICROSYSTEM & INFORMATION TECH CHINESE ACAD OF SCI
Gait recognition method based on two-dimension wavelet packet decomposition and complete PCA (Principal Component Analysis)
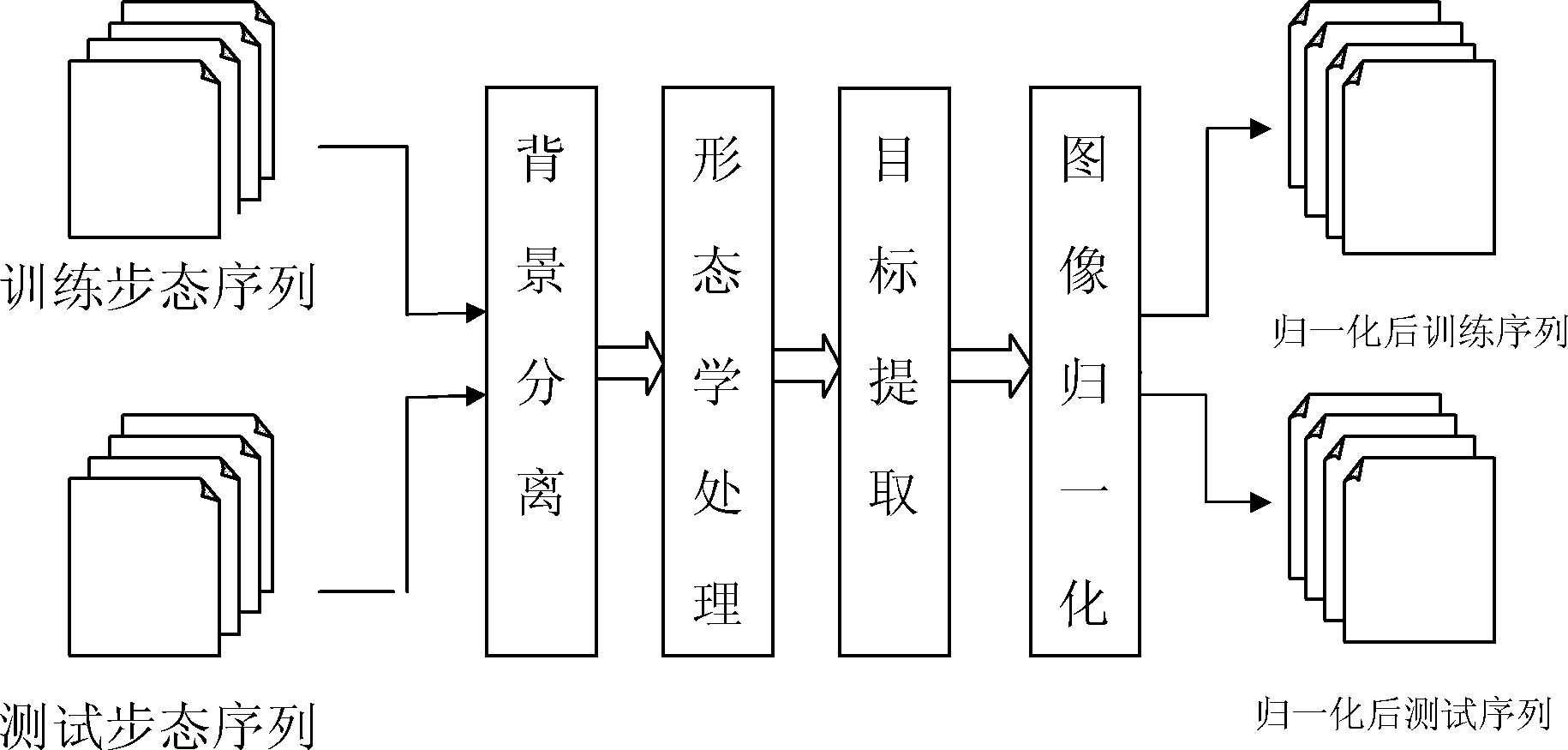
InactiveCN102222215AReduce data volumeImprove accuracyCharacter and pattern recognitionComputation complexityFeature extraction
The invention discloses a gait recognition method, particularly the gait recognition method based on two-dimension wavelet packet decomposition and complete PCA (Principal Component Analysis), which belongs to the technical field of pattern recognition. The method comprises the following steps of: pretreatment (morphologic treatment, target extraction and image normalization), feature extraction (gait cycle, gait energy image and fusion of WPD plus (2D) 2 PCA selection feature) and classification of the test samples to a corresponding class according to the nearest neighbor classification principle. the method integrates periodic frames in one mean chart by utilizing the gait energy diagram so as to eliminate the influence of difference of periodic frame numbers on the feature extraction, thereby reducing the computational complexity; and besides, the method extracts and selects gait features by initially adopting the method of fusing WPD with (2D) 2 PCA so as to solve the problems of loosing of high-frequency components or excessive dimensionality due to the simple adoption of all data of the existing gait recognition method based on wavelet transformation, and has higher recognition rate as well as higher robustness of vision angle change.
Owner:BEIJING UNIV OF TECH
Graph neural network training method and device
PendingCN112085615AGuaranteed accuracyReduce memory usageData processing applicationsNeural architecturesAlgorithmTheoretical computer science
The embodiment of the invention provides a graph neural network training method, and the method comprises the steps: obtaining a relation network graph, wherein each object node corresponds to a sampling probability set, and the sampling probability set comprises the sampling probability of each first-order neighbor node; performing multiple rounds of iterative updating on the graph neural networkon the basis of the relation network graph, wherein any round includes performing M-order neighbor node sampling by taking the first label node selected in the current round as a center, wherein anyi-order neighbor node sampling includes, for any first node in the sampled i-1th-order neighbor nodes, based on the current sampling probability set, sampling a plurality of neighbor nodes from a first-order neighbor node set, and classifying the neighbor nodes into an ith-order neighbor node; performing the current round of updating on the graph neural network based on the sampled neighbor nodeswithin the M order and the first service label carried by the first label node; and determining a plurality of training feedbacks corresponding to the plurality of neighbor nodes by using the updatedgraph neural network, and then updating the current sampling probability set of the first node.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
Sum and product computing method for protecting data privacy security of arbitrary user group
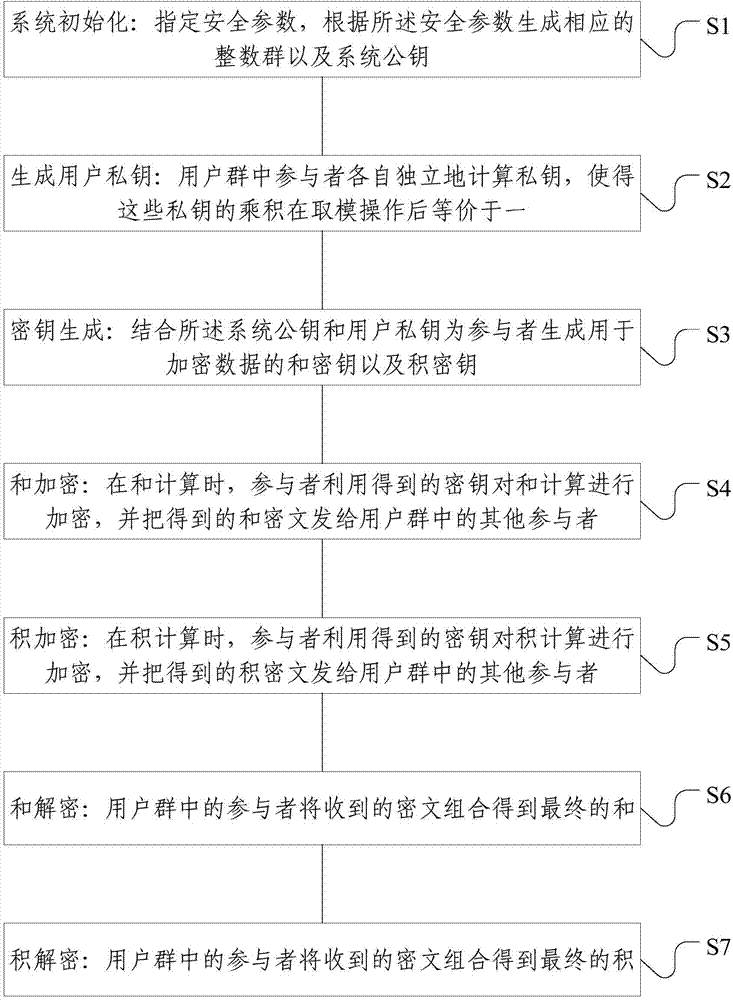
ActiveCN103763100AGuaranteed privacyRobustPublic key for secure communicationCiphertextSecurity parameter
The invention relates to a sum and product computing method for protecting data privacy security of an arbitrary user group. The computing method comprises the following steps of system initialization, user private key generation, secret key generation, sum encryption, product encryption, sum decryption, and product decryption. To be specific, according to the system initialization, a security parameter is specified; and a corresponding integer group and a system public key are generated by the security parameter. According to the user private key generation, participants in the user group compute private keys independently and respectively, so that the product of the private keys is equal to one after modulus operation. According to the secret key generation, a sum secret key and a product secret key for encryption data are generated for the participants based on combination of the system public key and the user private keys. According to the sum encryption, during the sum computing, the participants utilize the obtained secret keys to carry out encryption on the sum computing and send obtained sum ciphertexts to other participants in the user group. According to the product encryption, during product computing, the participants utilize the obtained secret keys to carry out encryption on the product computing and send obtained product ciphertexts to other participants in the user group. According to the sum decryption, the participants in the user group combine the received ciphertexts to obtain a final sum. And according to the product decryption, the participants in the user group combine received ciphertexts to obtain a final product.
Owner:TSINGHUA UNIV
Traditional Chinese medicine clinical big data storage method based on multi-mark feature selection and classification
ActiveCN109119133AGuaranteed validityGuaranteed interpretabilityMedical data miningCharacter and pattern recognitionData dredgingData set
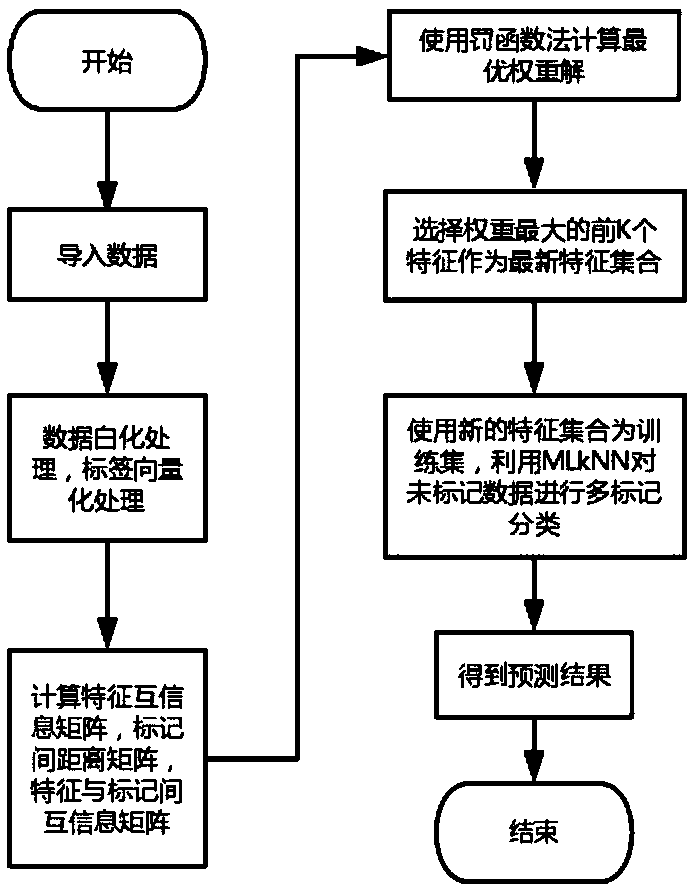
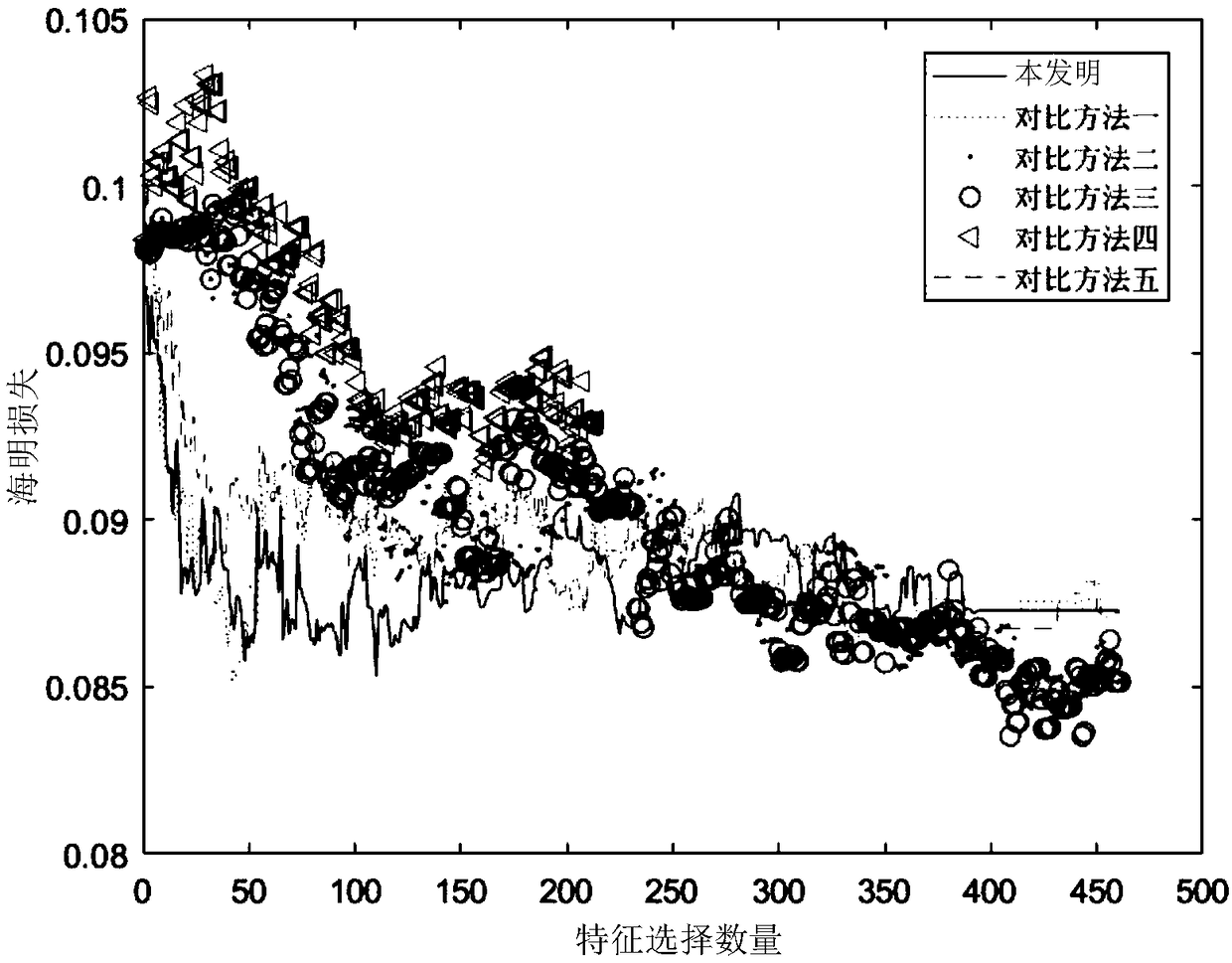
The invention, which relates to the cross technology application field of big data mining and traditional Chinese medicine digitalization, provides a traditional Chinese medicine clinical big data storage method based on multi-mark feature selection and classification. Information acquisition is carried out on a patient, quantified grading is carried out based on symptoms of different patients, and corresponding multi-type labels are given; the collected patient data are normalized, vectorization processing is carried out on a marking data set to obtain a standard multi-mark data set, and themulti-mark data set is divided into a training set and a testing set to verify the effectiveness of algorithm; a needed related matrix for feature selection of the training set is calculated and global optimal feature weight distribution is calculated by using a penalty function method; and first K feature sub sets with the largest weights are selected, a testing set prediction result is obtainedbased on an MLkNN method, and an optimal feature sub set is selected to carry out new patient disease prediction.
Owner:XIAMEN UNIV
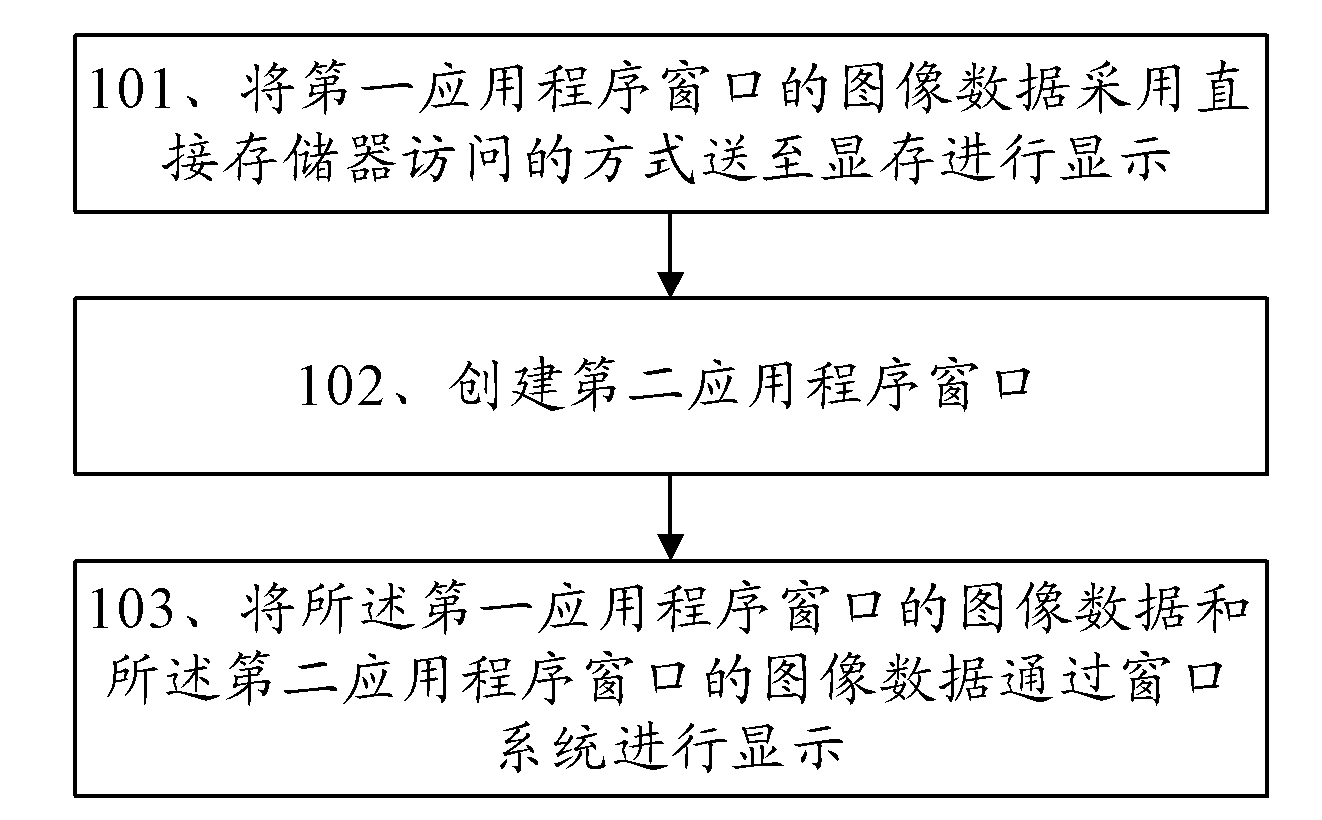
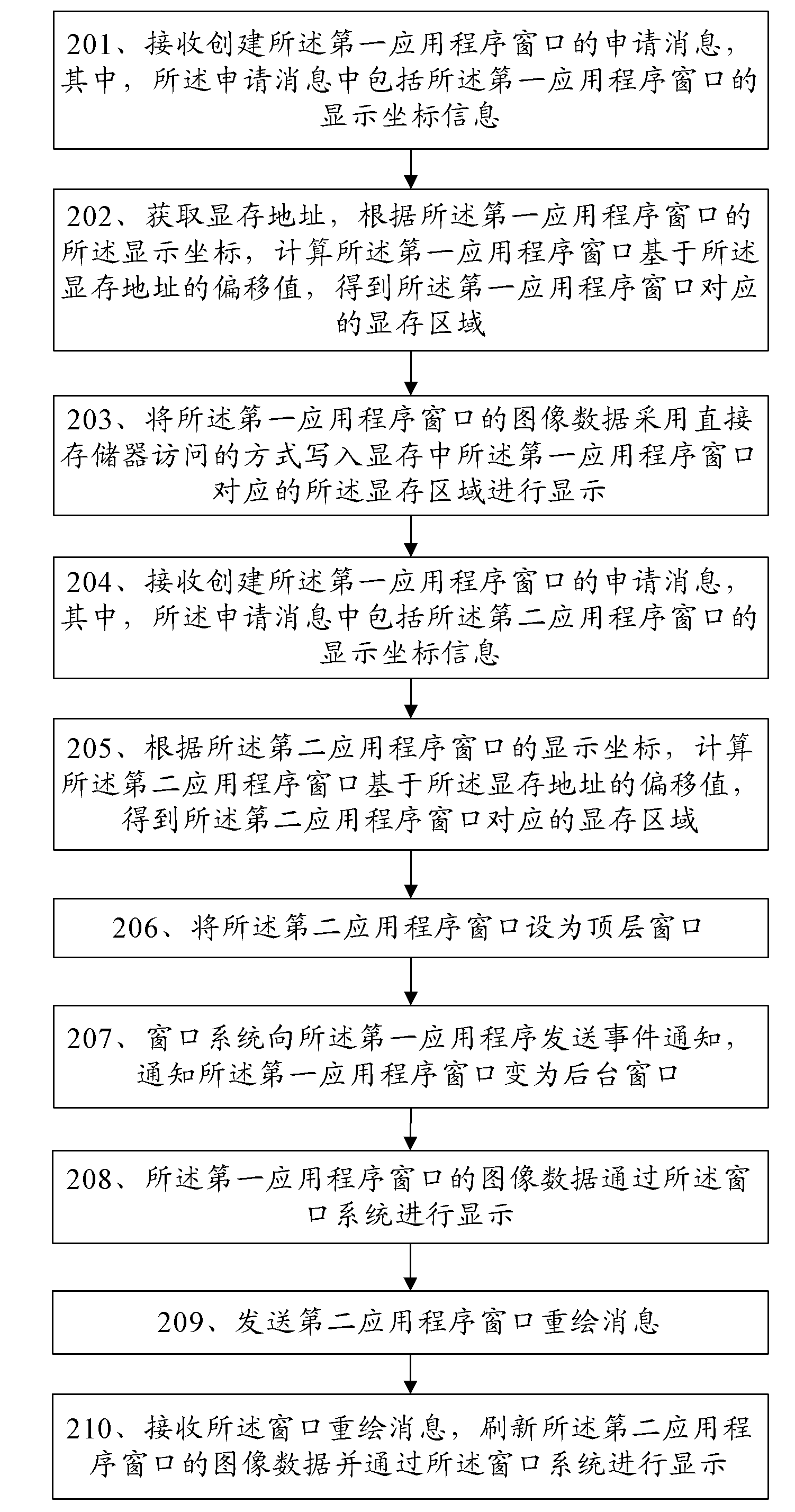
Window management method and terminal
InactiveCN101937317AGuaranteed image display effectAvoid time resourcesInput/output processes for data processingGraphicsVideo memory
The embodiment of the invention discloses a window management method and a terminal and relates to the technical field of a graphical user interface. The invention is designed to reduce calculation consumption of the terminal in the process of image display and optimize the image display method. The method of the embodiment of the invention comprises the following steps: delivering the image data of a first application program window to a local video memory for display by a direct memory access (DMA) way; building a second application program window; and displaying the image data of the first application program window and the image data of the second application program window via a window system. The embodiment of the invention also provides the terminal for realizing the method. The embodiment of the invention is applied to single or multiple window display.
Owner:BEIJING WATCH DATA SYST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com