Internet e-commerce platform user privacy data encryption and decryption method
An e-commerce platform and user privacy technology, applied in the field of information security, can solve problems such as difficulty in upgrading and maintenance, operation errors, and no support for encrypted data sharing, so as to avoid acquisition or illegal operations and improve the encryption level.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
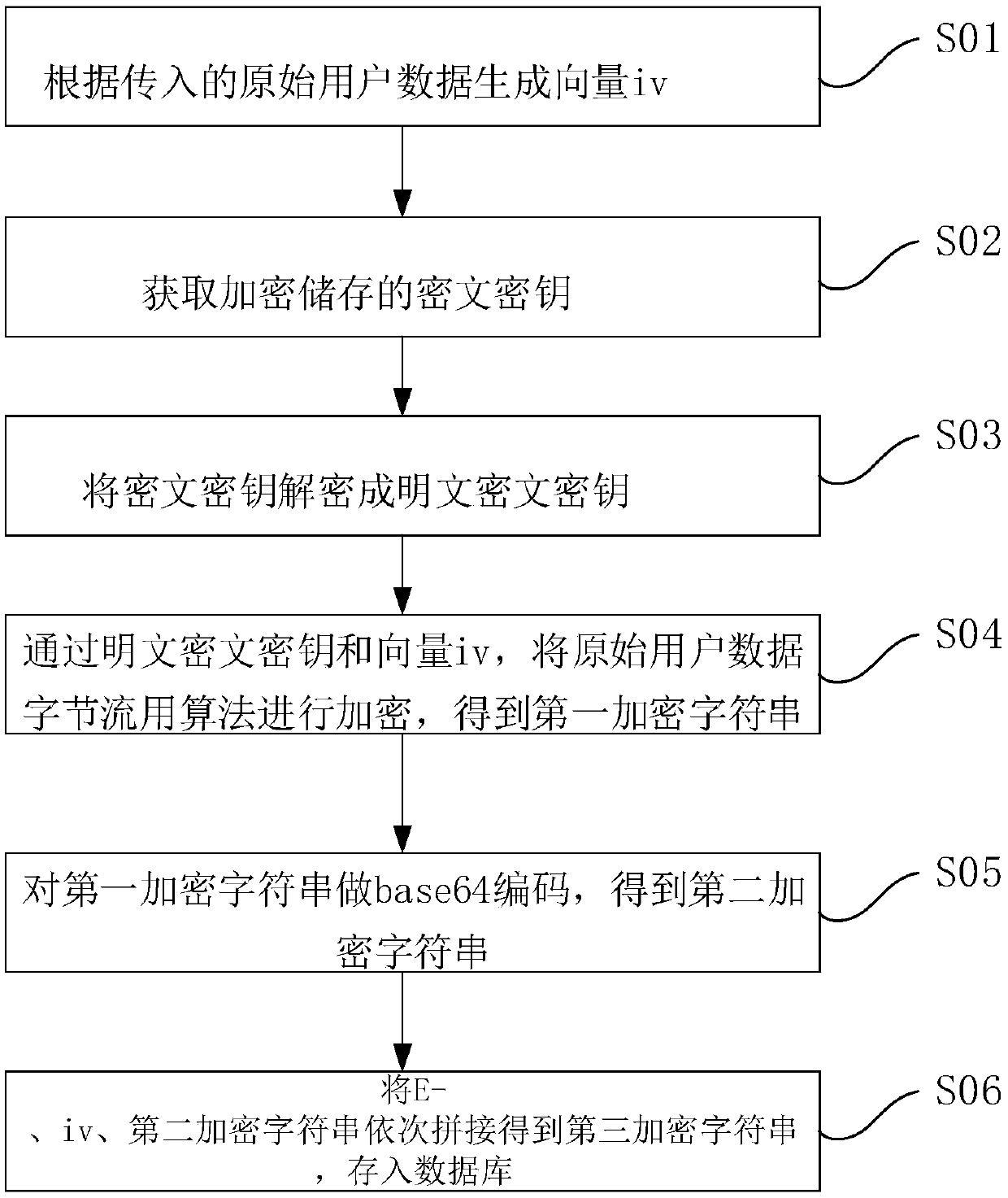
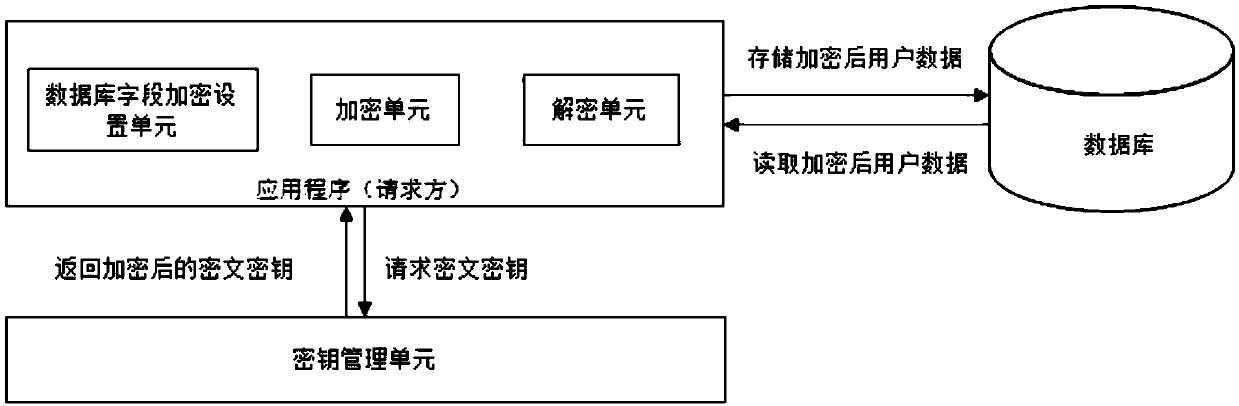
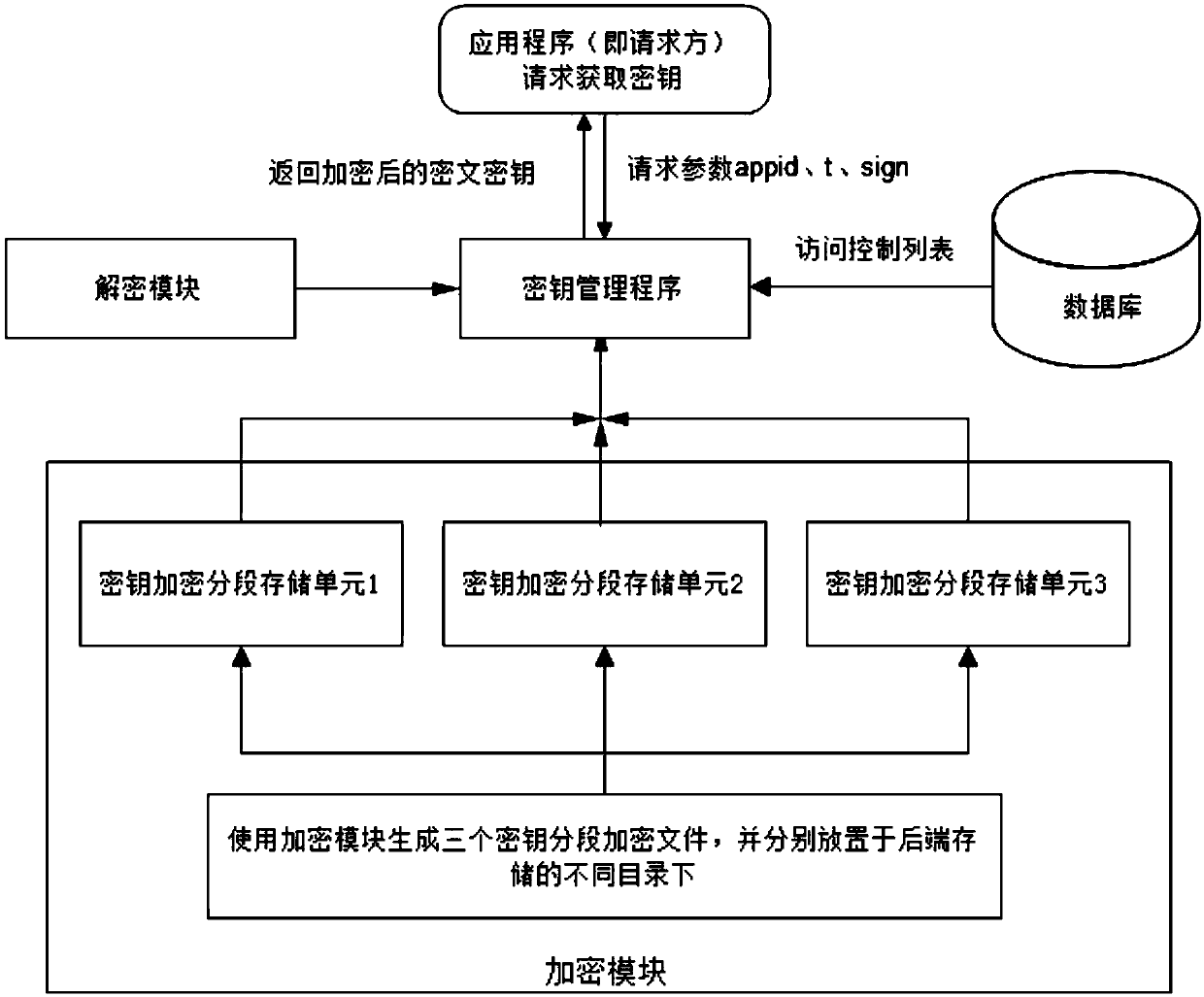
[0063] Such as figure 2 As shown, the Internet e-commerce platform user privacy data encryption device based on the aforementioned encryption and decryption method is composed of a database field encryption setting unit, an encryption unit, a decryption unit, and a key management unit, wherein the database field encryption setting unit, the encryption unit, and the decryption unit Together they form an application program, that is, the requesting party. The application program and the key management unit exist independently, and the application program requests the ciphertext key from the key management unit; its basic functions are as follows:
[0064] Database field encryption setting unit: according to the characteristics of user privacy information, it is used to set whether the storage fields in the database are encrypted. The principle of judging whether the storage fields are encrypted is determined by the content of the configuration file. For example, if the fields su...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com