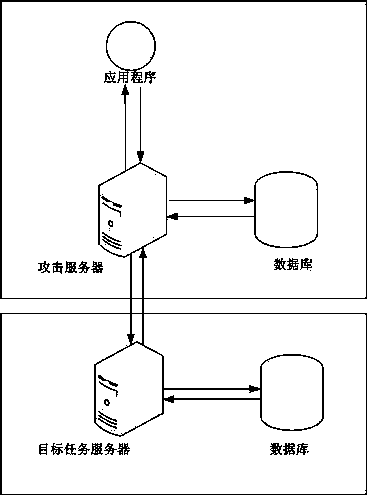
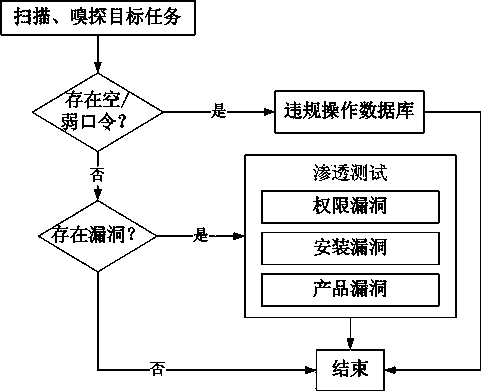
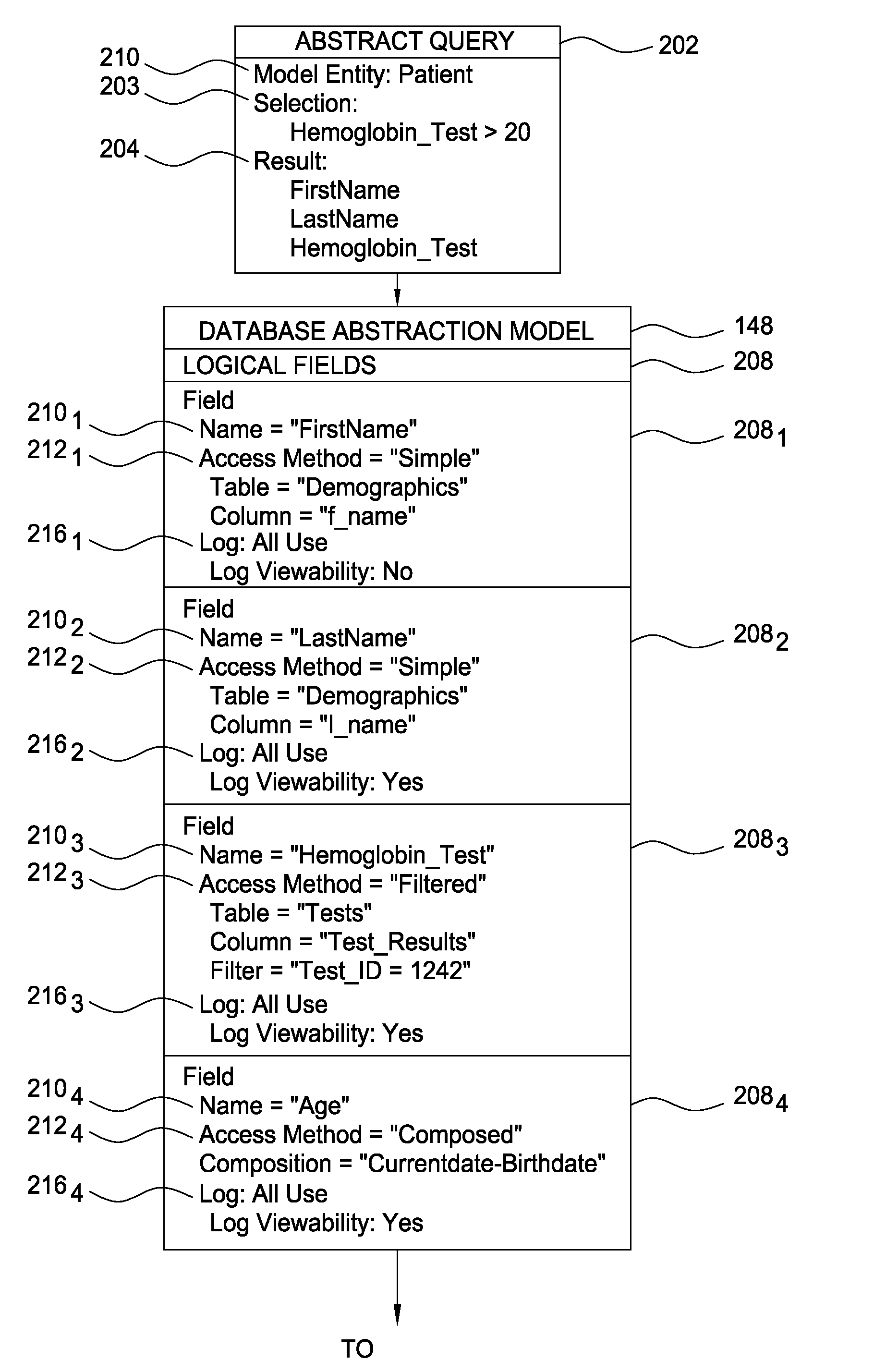
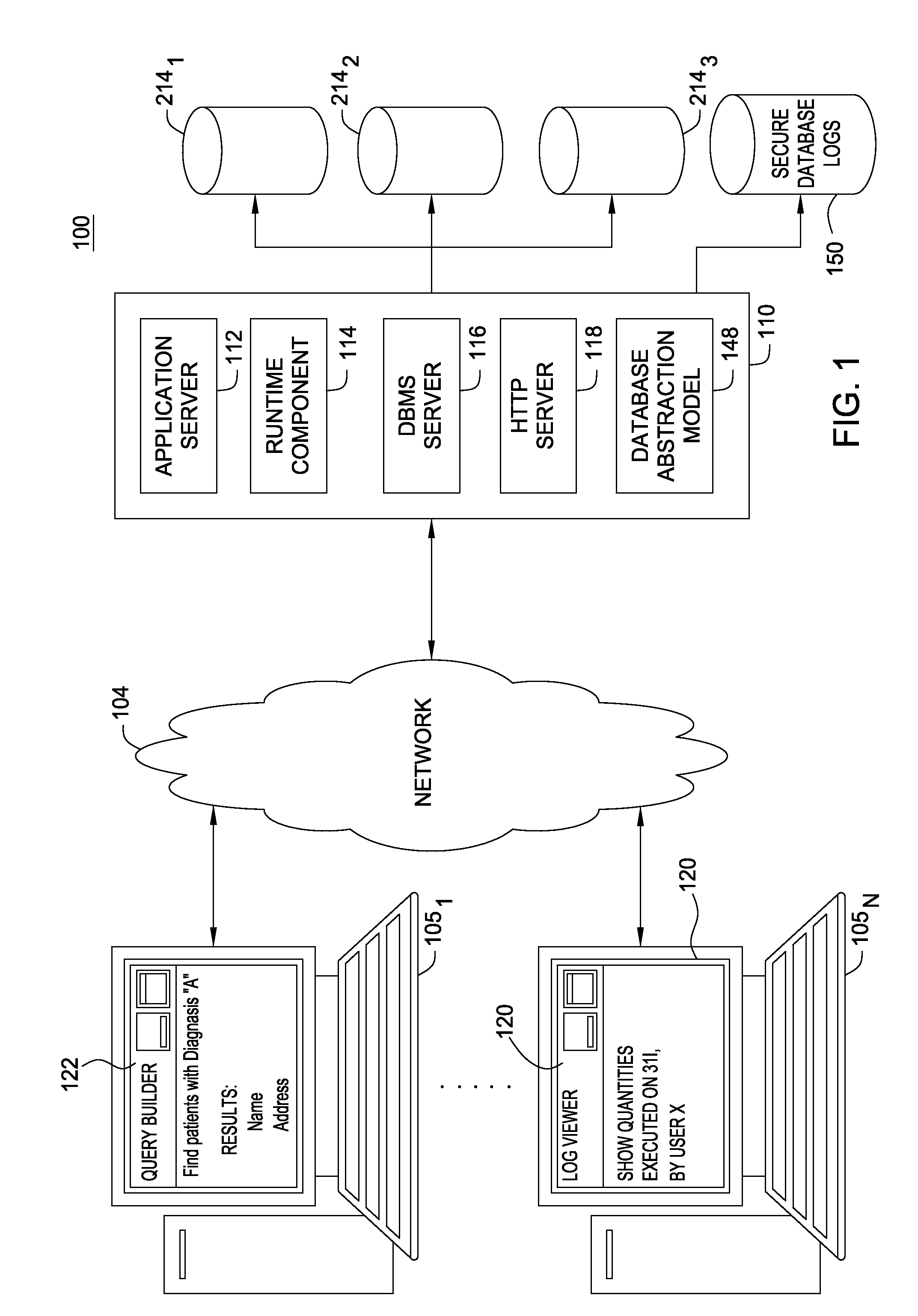
Patents
Literature
153 results about "Database administrator" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
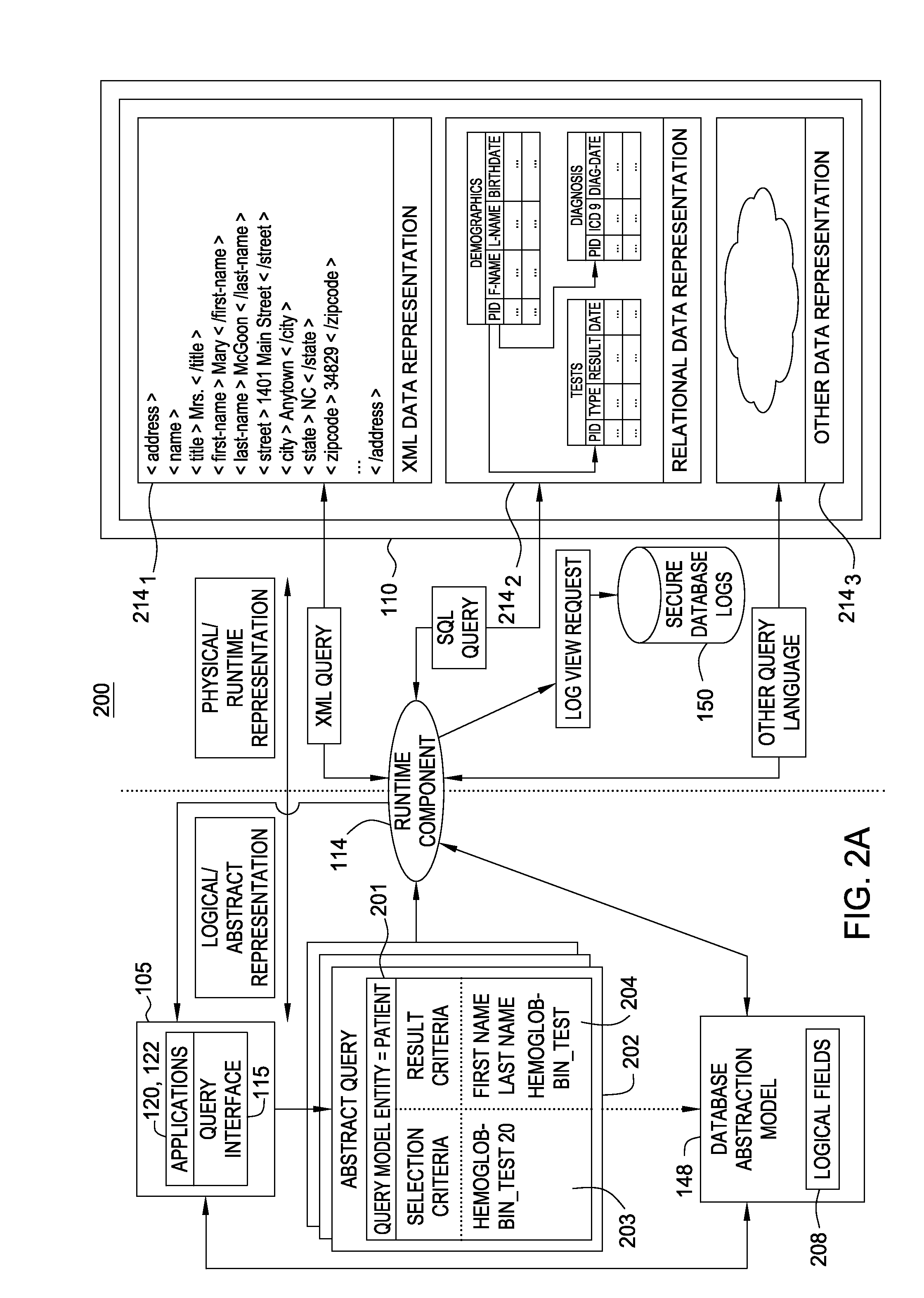
Database administrators (DBAs) use specialized software to store and organize data. The role may include capacity planning, installation, configuration, database design, migration, performance monitoring, security, troubleshooting, as well as backup and data recovery.
Method and apparatus for automatic database encryption
InactiveUS7111005B1Data processing applicationsMultiple keys/algorithms usageEncrypted functionDatabase encryption
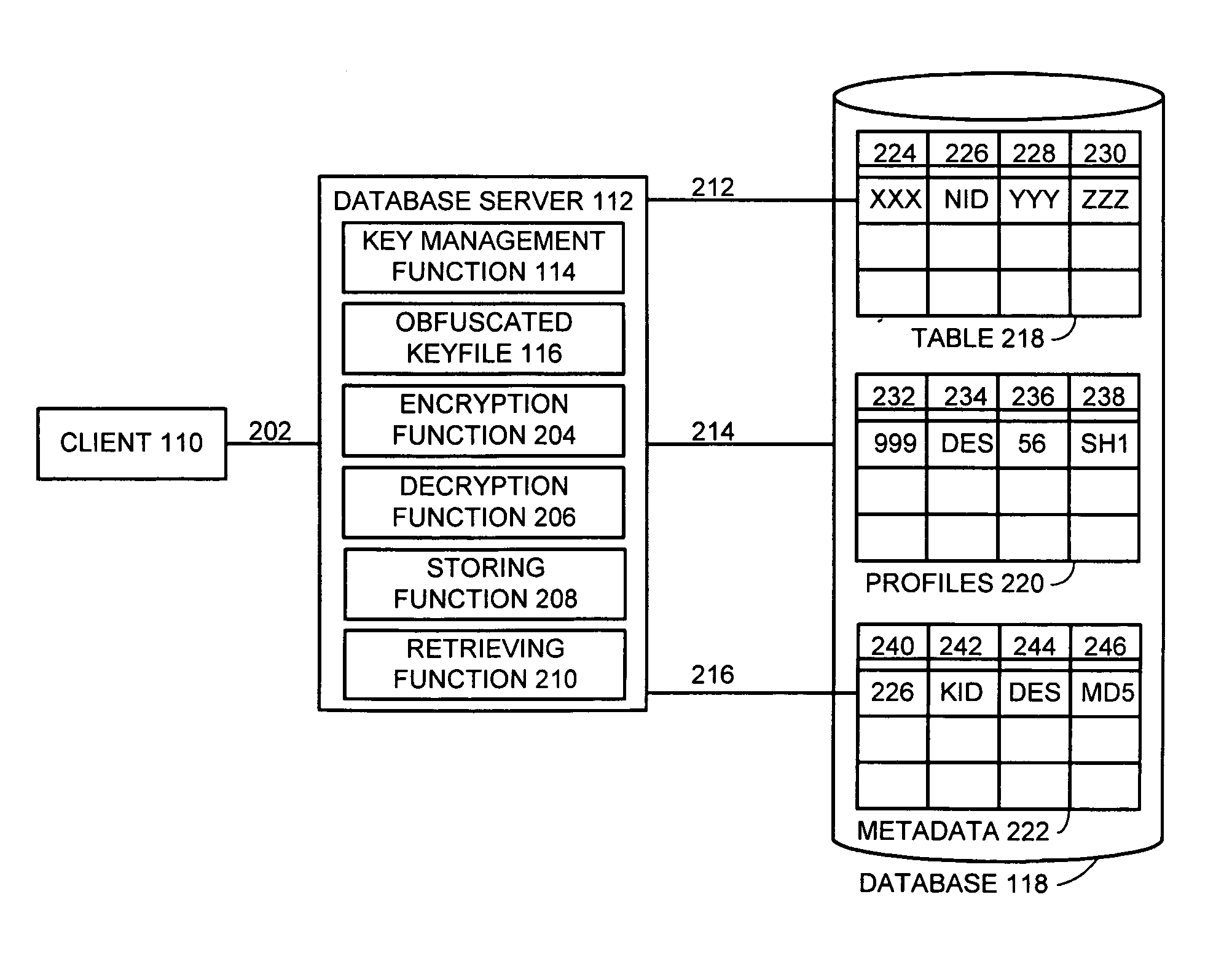
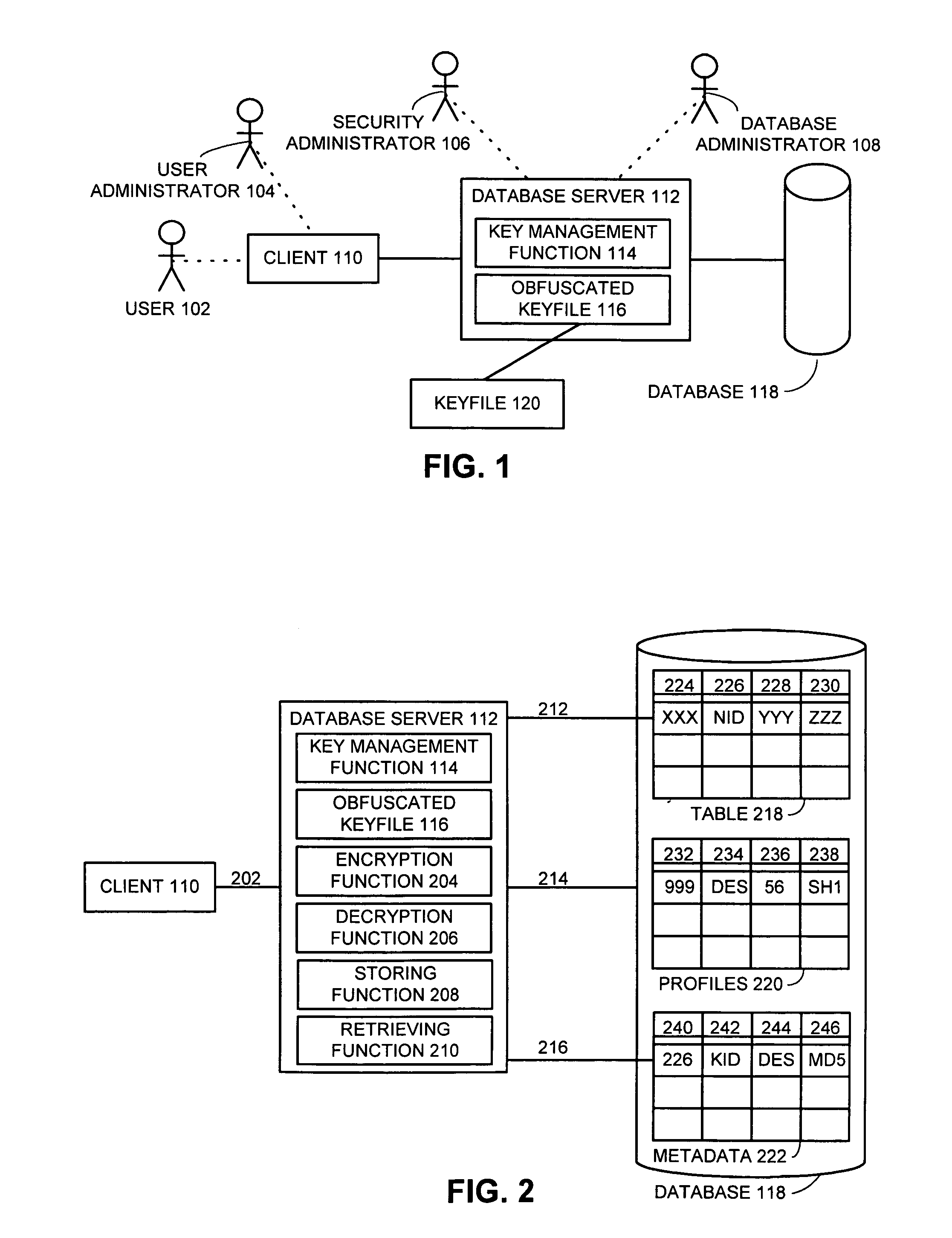
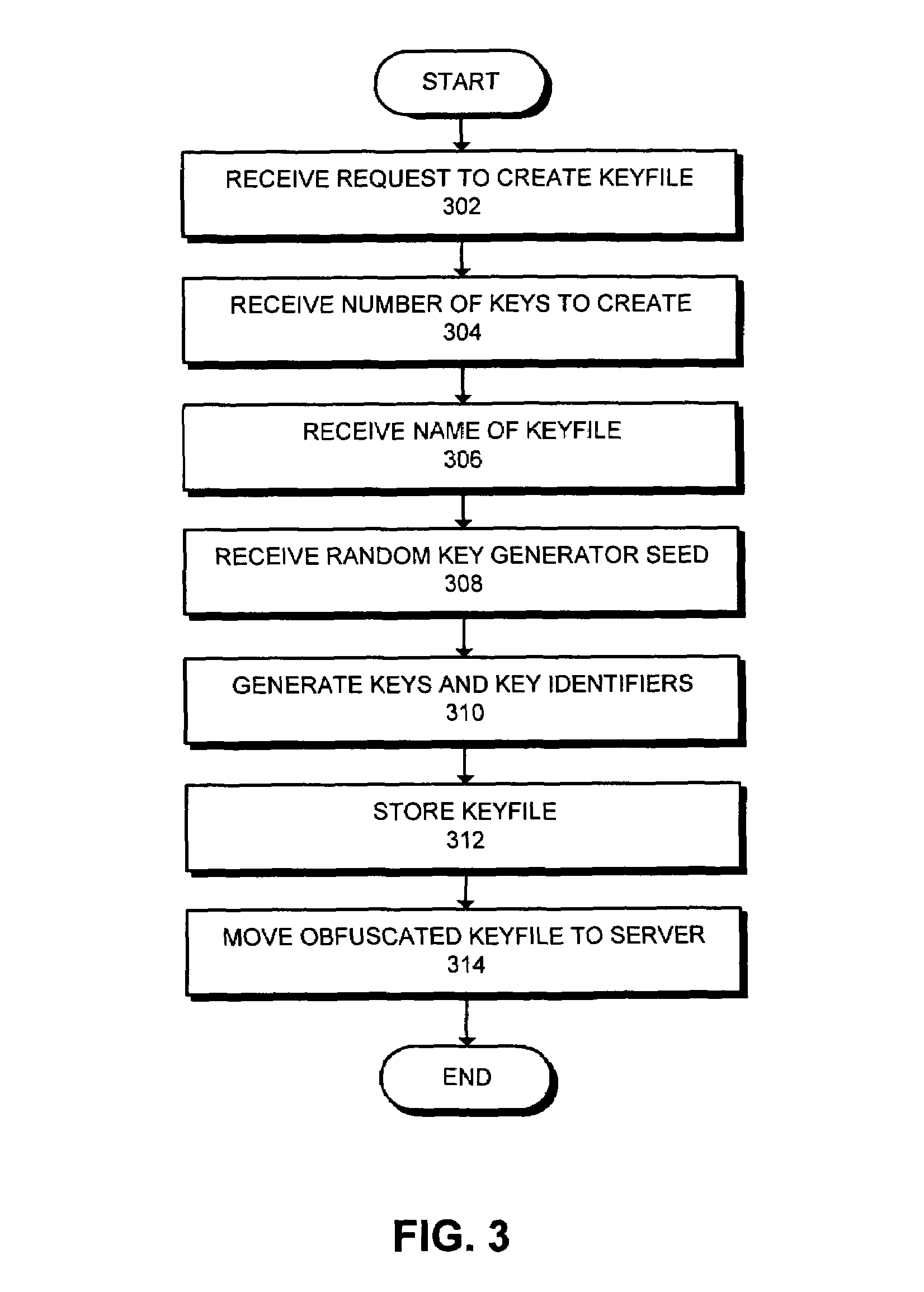
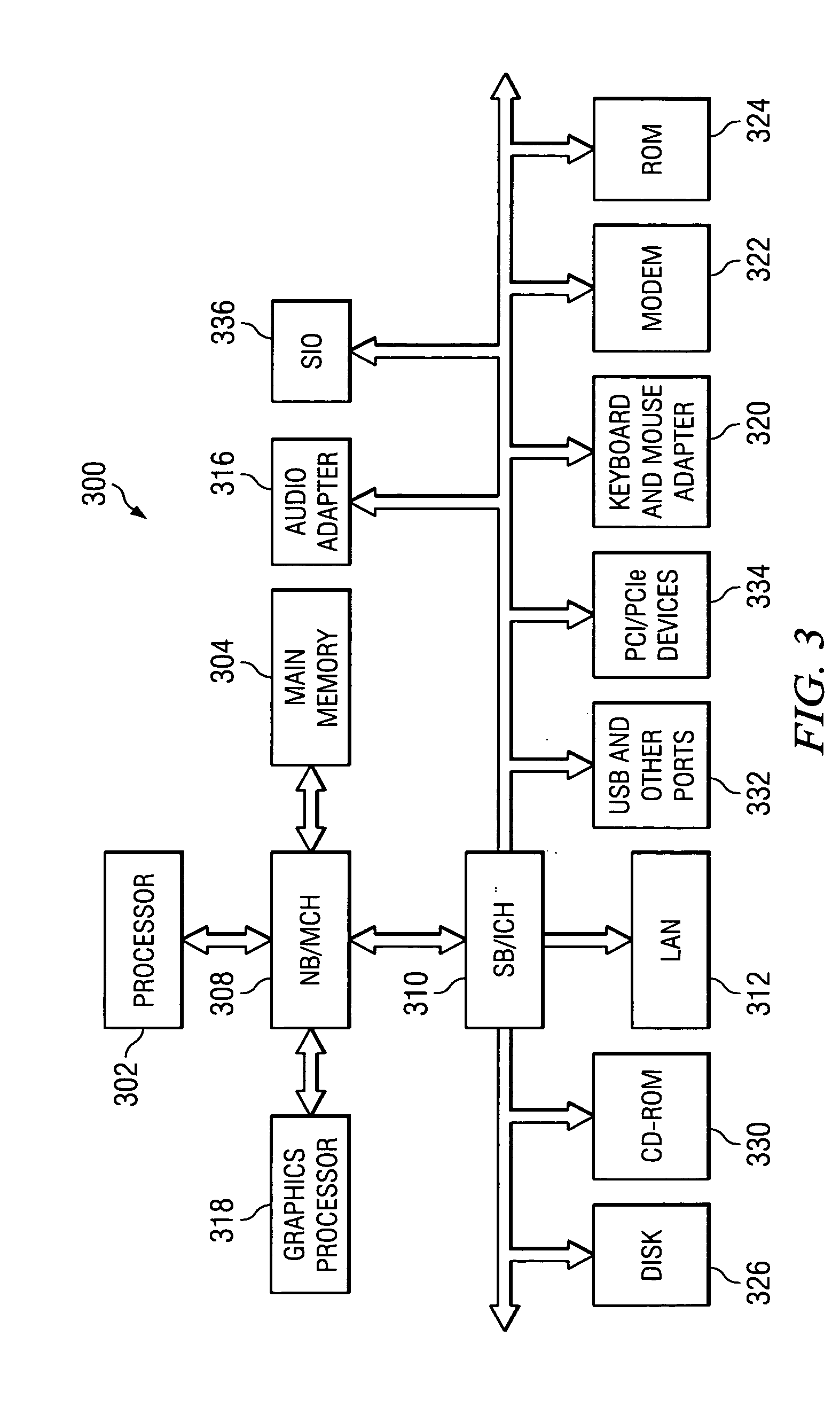
One embodiment of the present invention provides a system for managing encryption within a database system that is managed by a database administrator, and wherein a user administrator not otherwise associated with the database system, manages users of the database system. This system performs encryption automatically and transparently to a user of the database system. The system operates by receiving a request to store data in a column of the database system. If a user has designated the column as an encrypted column, the system automatically encrypts the data using an encryption function. This encryption function uses a key stored in a keyfile managed by the security administrator. After encrypting the data, the system stores the data in the database system using a storage function of the database system.
Owner:ORACLE INT CORP
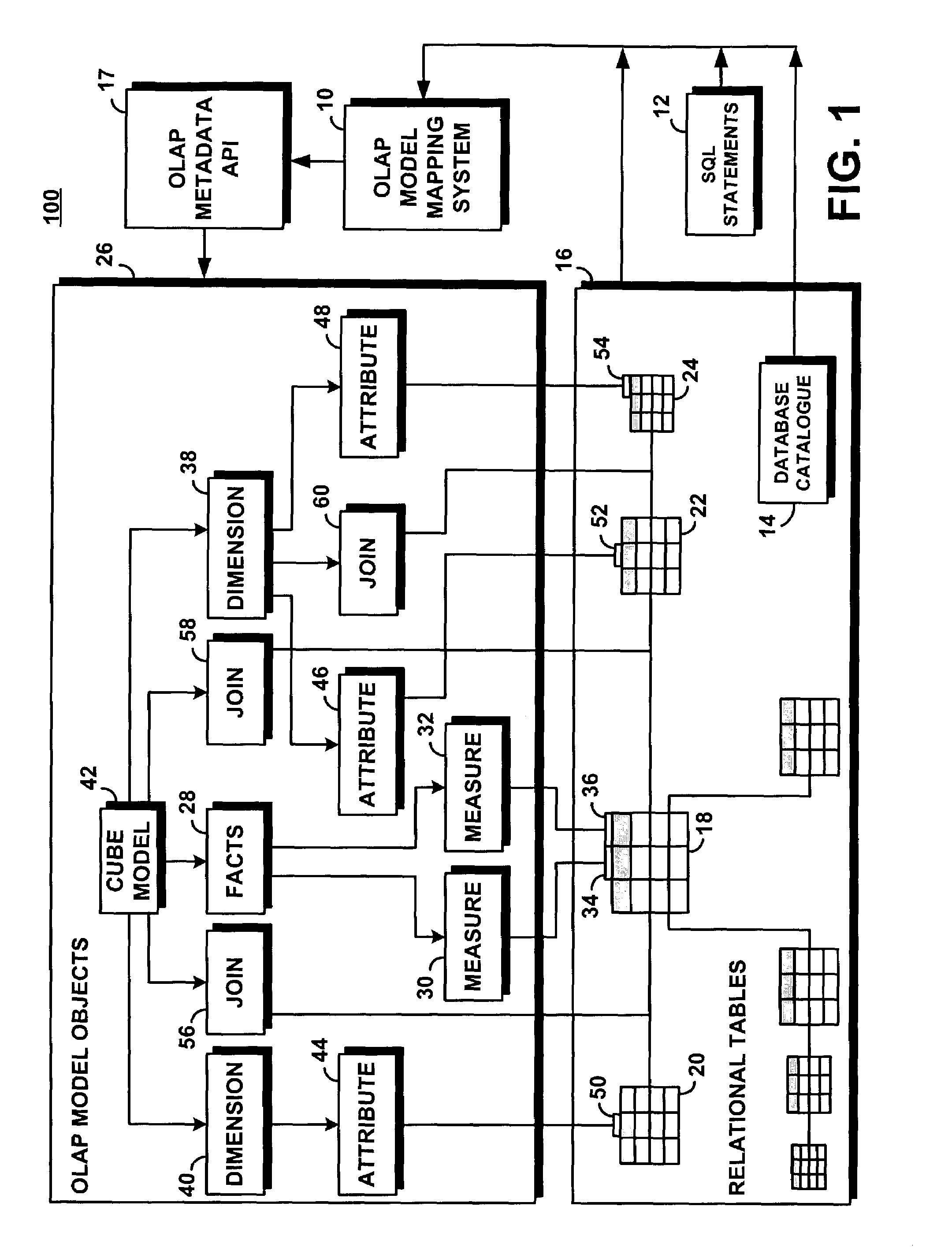
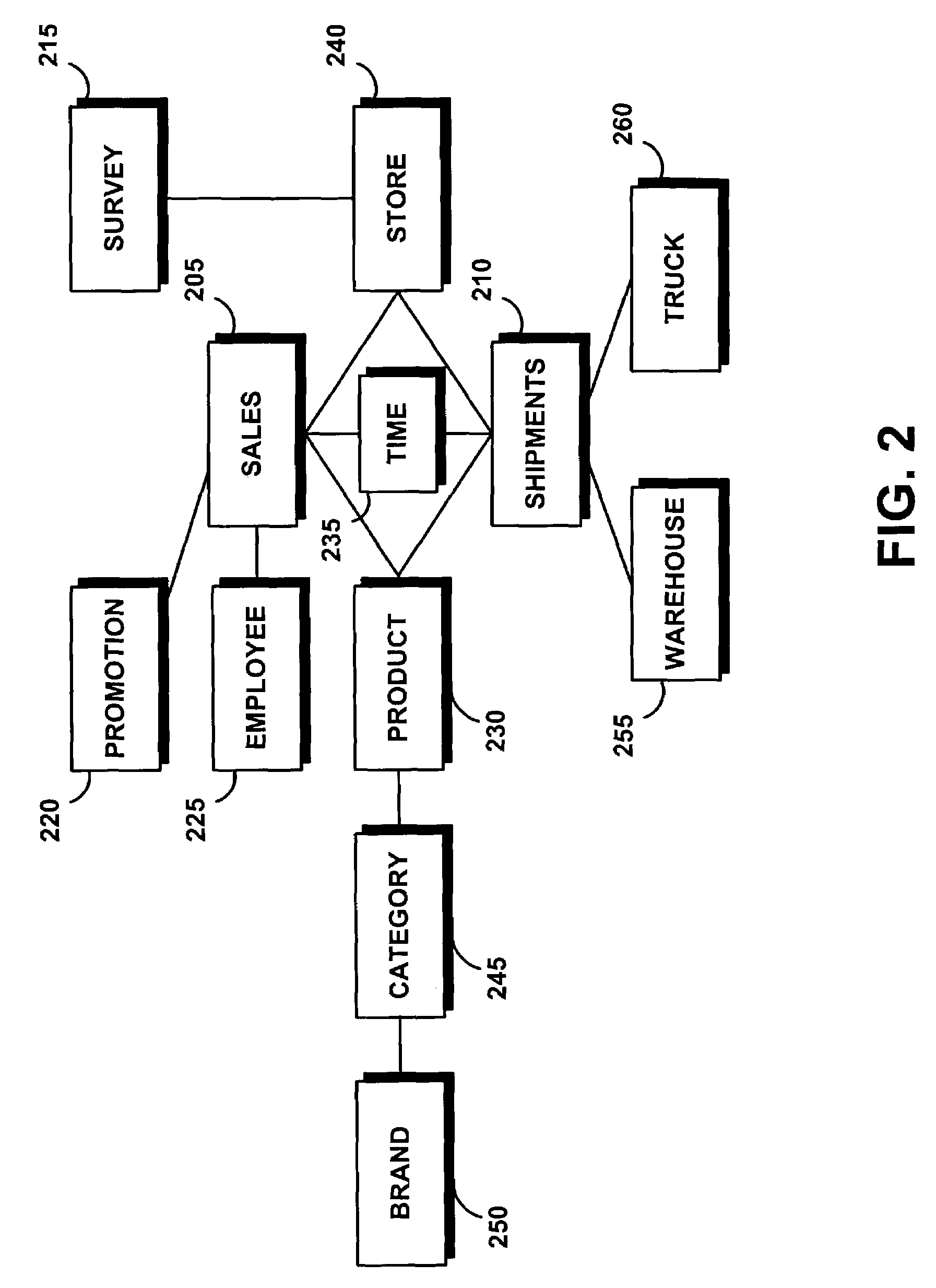
System and method for automatically building an OLAP model in a relational database
ActiveUS7716167B2Efficiently and quickly and automatically createEliminate needData processing applicationsDigital data processing detailsData setRelational database
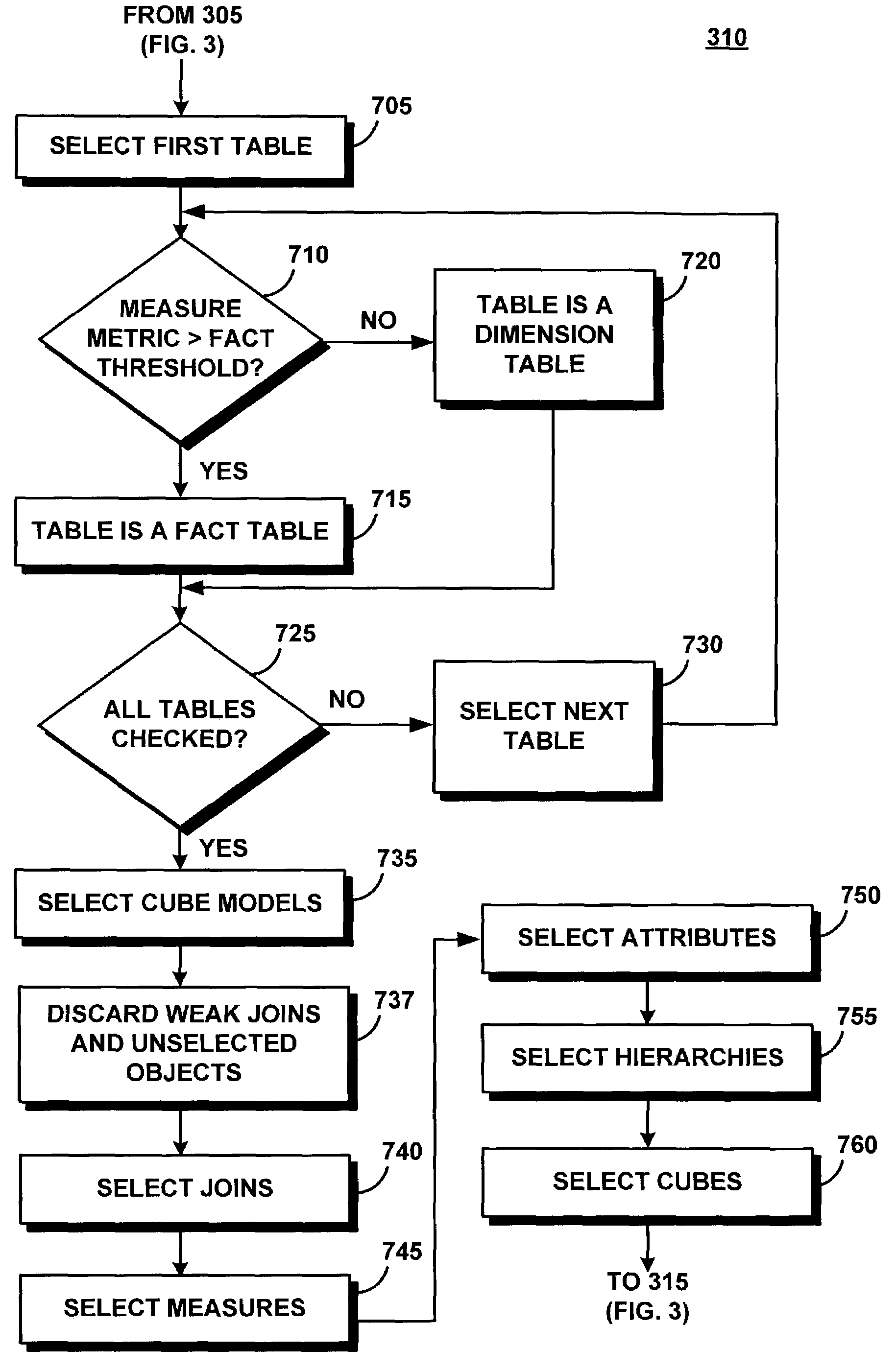
A system automatically generates OLAP metadata objects for a multidimensional analysis program such as OLAP from SQL statements without involving the database administrator, and eliminates the need for database administrators to manually perform this analysis and design. The system deconstructs a set of SQL statements into tables and aggregates metrics for measures and joins. It recognizes that the relational database structure contains both dimension tables and fact tables. Over many SQL statements, fact tables will have a large measure metric while dimension tables will have a low measure metric. Tables are linked based on large join metrics; small join metrics are ignored. The present system builds the OLAP cube model from the fact tables, dimension tables, and joins. The analysis of the SQL statements allows the system to map the hierarchies within the dimension table, and provides the system with information about attribute relationships and cubes.
Owner:GREEN MARKET SQUARE LTD
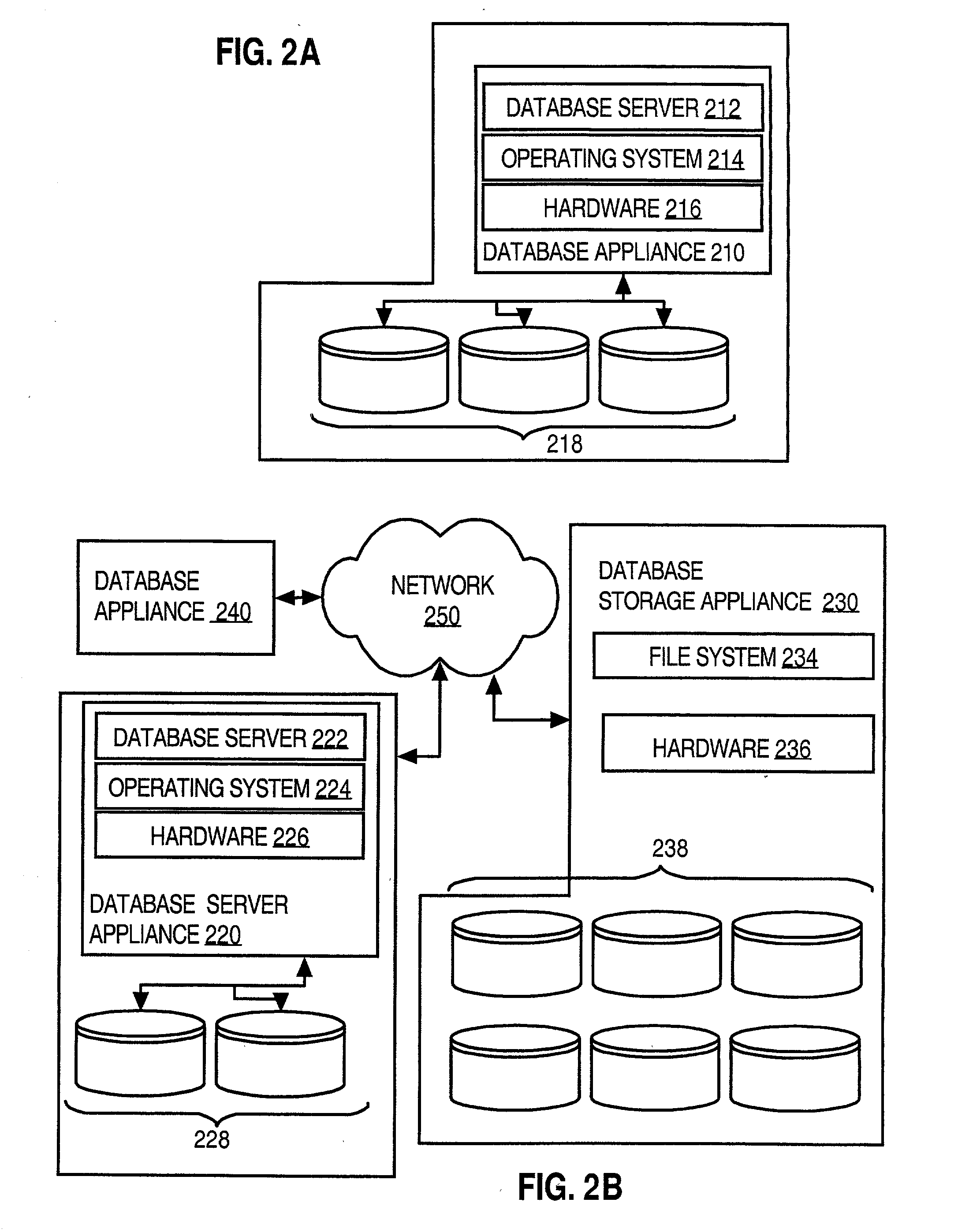
Techniques for managing database systems with a community server
ActiveUS6993657B1Low costReduce loadDigital data processing detailsUnauthorized memory use protectionDatabase administratorDatabase manager
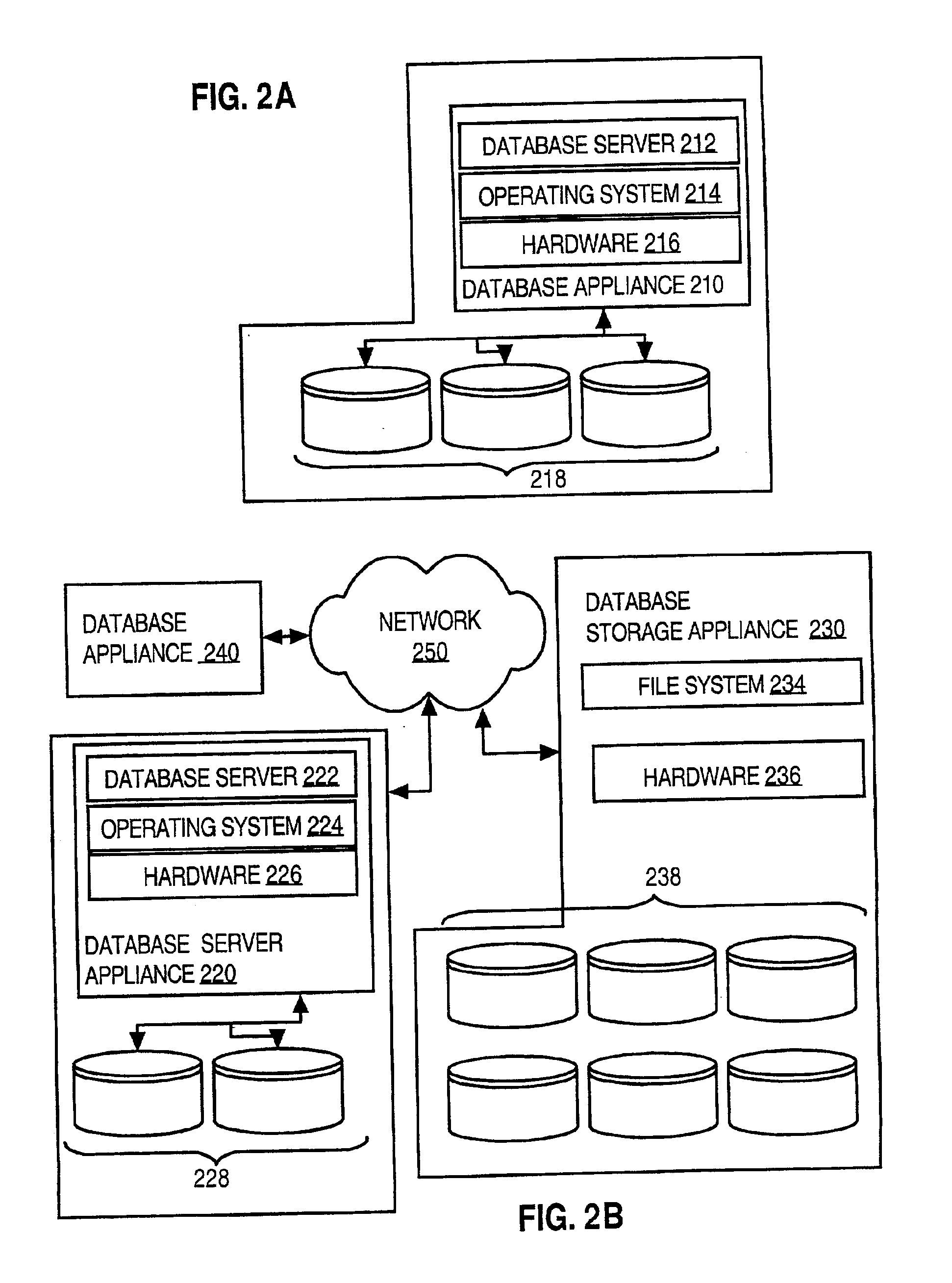
Techniques for managing databases include registering multiple databases at a community server. Each database is controlled by a different party. The community server is accessible over a first network to which one or more users from each party have access. Each database is installed on a different network than the first network. The community server receives from a user over the first network a request to perform a management operation relating to a particular database that is controlled by a particular party. The community server determines that the particular database is registered and determines whether the user is authorized to perform the management operation. If the user is authorized, then the community server causes the management operation to be performed.With these techniques, one or more database devices, such as database appliances, can be managed over the Internet with a browser, at least for many common database management functions. This alleviates the load on an enterprise database manager platform, provides metadata even when the database device or enterprise platform is not working, provides ready backup when a database device or enterprise platform returns to operation, and enables a database administrator for the enterprise to perform some management functions while on the road, away from the site of the enterprise. It can also provide users of an enterprise's database devices with access to some database metadata when the user is on the road or the enterprise equipment is not operating.
Owner:ORACLE INT CORP
Method and system for providing a tamper-proof storage of an audit trail in a database
InactiveUS6968456B1Improve securityKey distribution for secure communicationData processing applicationsTamper resistanceDatabase administrator
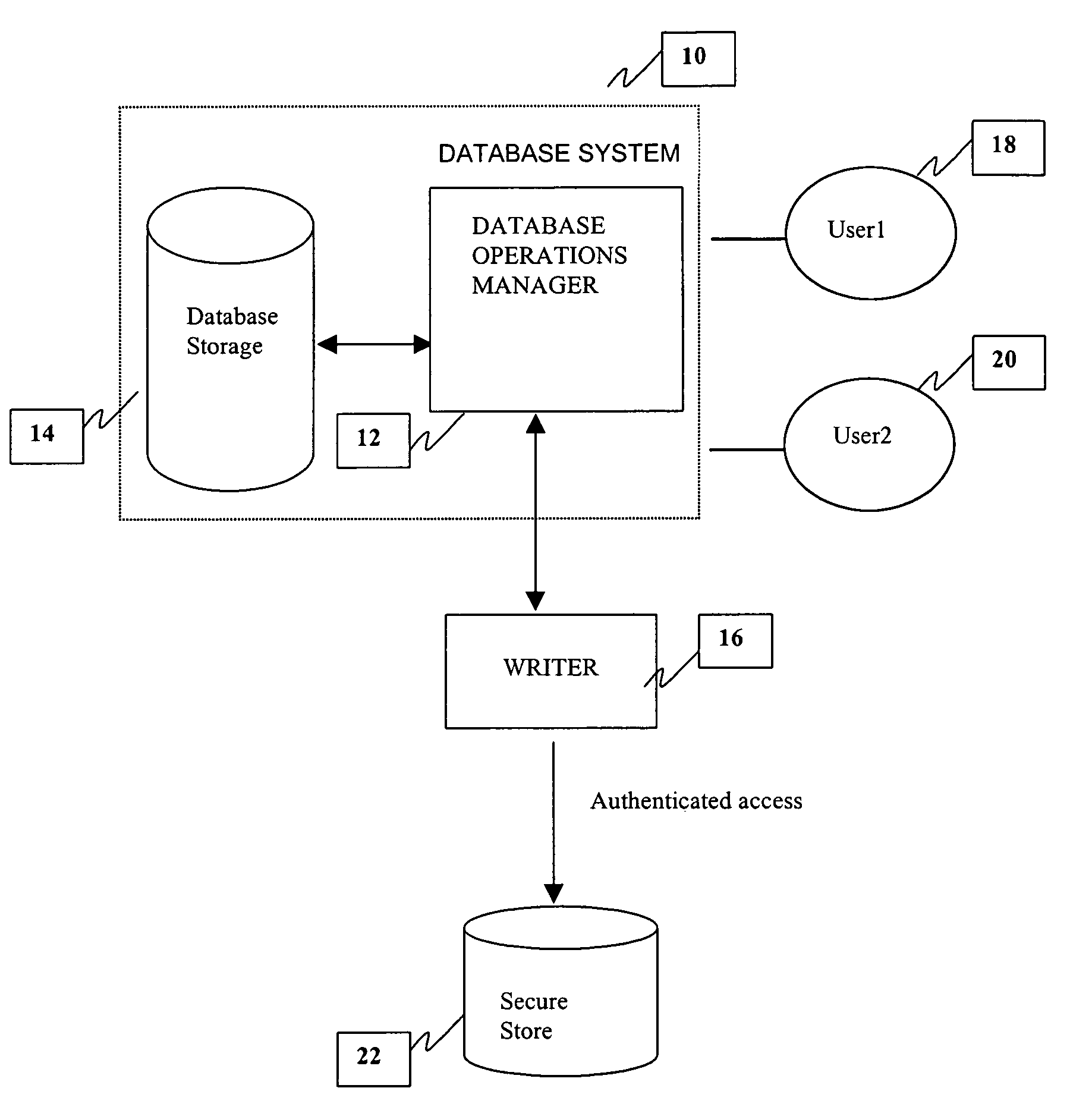
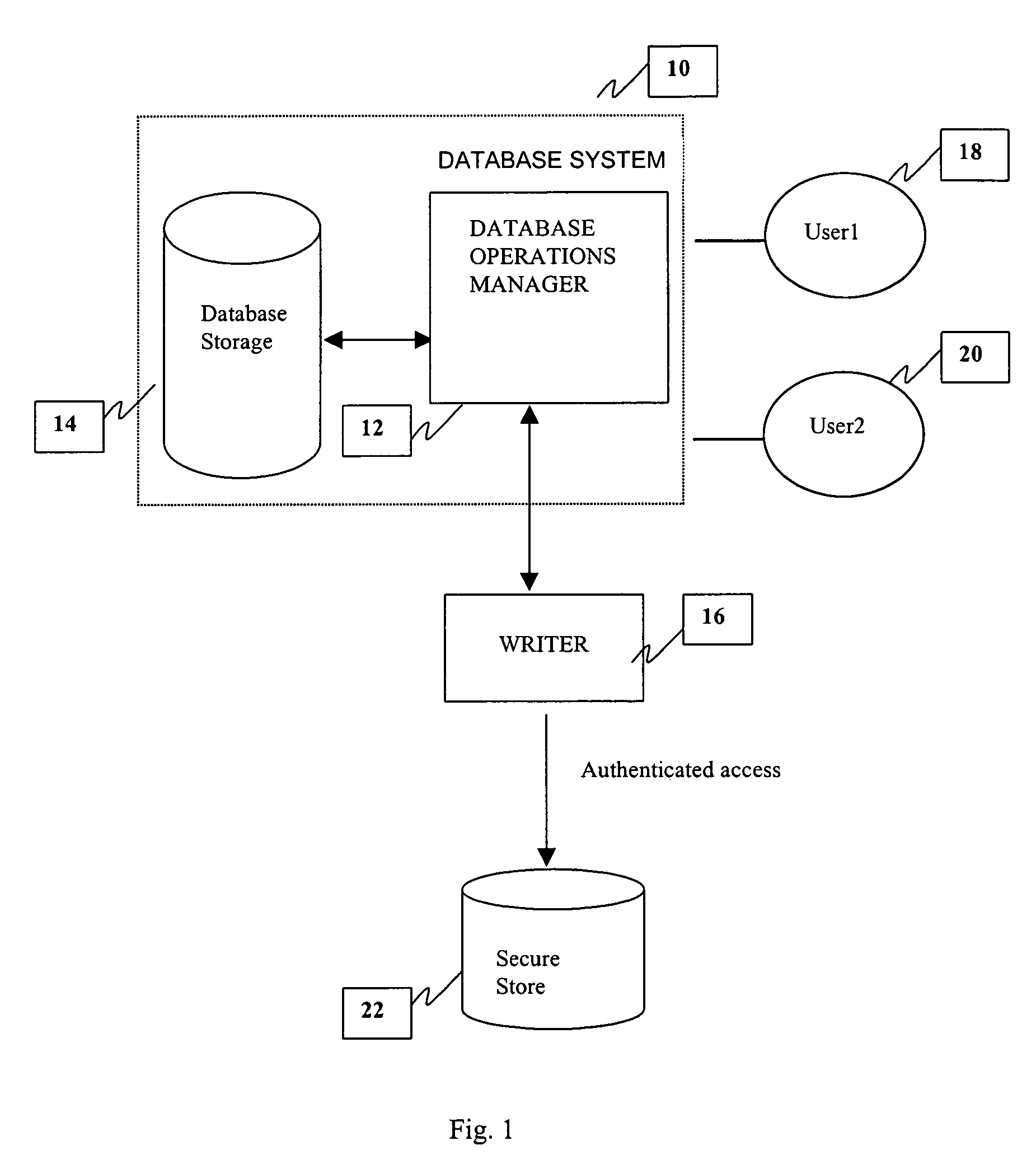
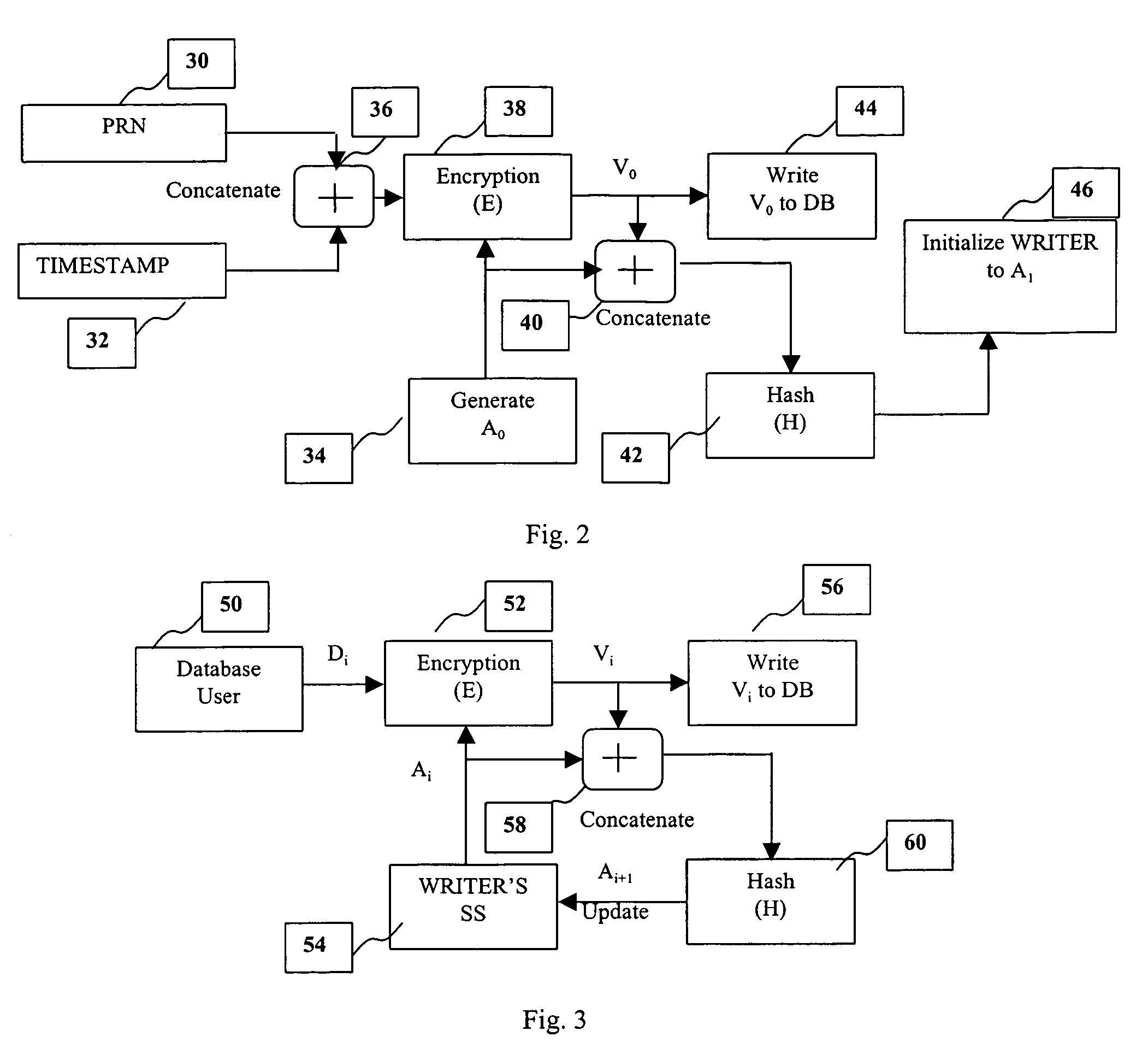
A method and system is provided for a tamper-proof storage of one or more records of an audit trail in a database. Since the integrity of the database records may be vulnerable to actions taken by a user such as a privileged database administrator, a mechanism is provided to efficiently detect any changes made by him to the database records. The method creates one or more authentication tokens, and generates one or more validation tokens from the authentication tokens through a combination of a hashing process and an encryption process. Once the validation tokens are created, they are further integrated into the records in the database. The authentication tokens are written to a secured information storage in a predetermined format by a writing machine inaccessible by the user but accessible by the auditor. When an authorized person such as an independent auditor who needs to check the integrity of the records, he can detect a tampering of the records by comparing a validation token computed from the stored validation token with the validation token integrated in the record.
Owner:ORACLE INT CORP
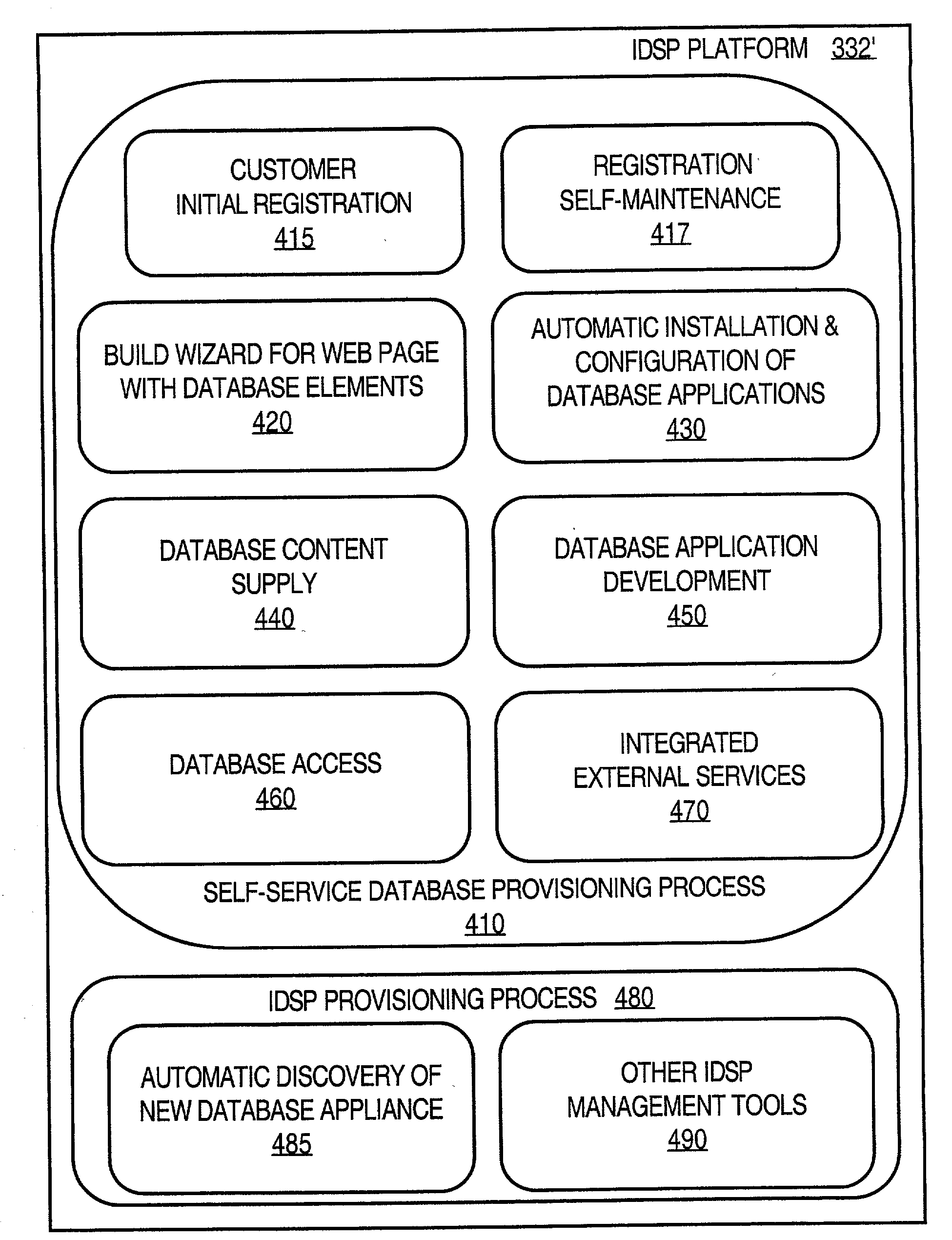
Techniques for automatically provisioning a database over a wide area network
InactiveUS20080306883A1Low costService is expensiveError detection/correctionDigital data processing detailsThe InternetDatabase application
Techniques for provisioning databases for users on a wide area network include a first party managing one or more database systems. Multiple second parties subscribe to database services supported by the database systems managed by the first party. The first party provides, over a network, to database applications controlled by the second parties, access to the database services to which the second parties are subscribed.The database systems may use database appliances. A database appliance includes a database process and a non-database process that is-tailored to the needs of the database process. The wide area network may be a public network of computer networks, such as the Internet. With the present invention, a user is able to obtain needed database resources from an Internet Database Service Provider (IDSP) with a minimum of user effort and without the user incurring the full costs of one or more database administrators, or the costs of a dedicated database equipment facility, or even the costs of a dedicated database device, depending on usage. At the same time, the IDSP can readily provide for several database users with minimum staffing loads on the IDSP because of self-service tools provided. Furthermore, the IDSP start-up and maintenance efforts are reduced through several tools, such as the costing model and automatic billing features.
Owner:ORACLE INT CORP
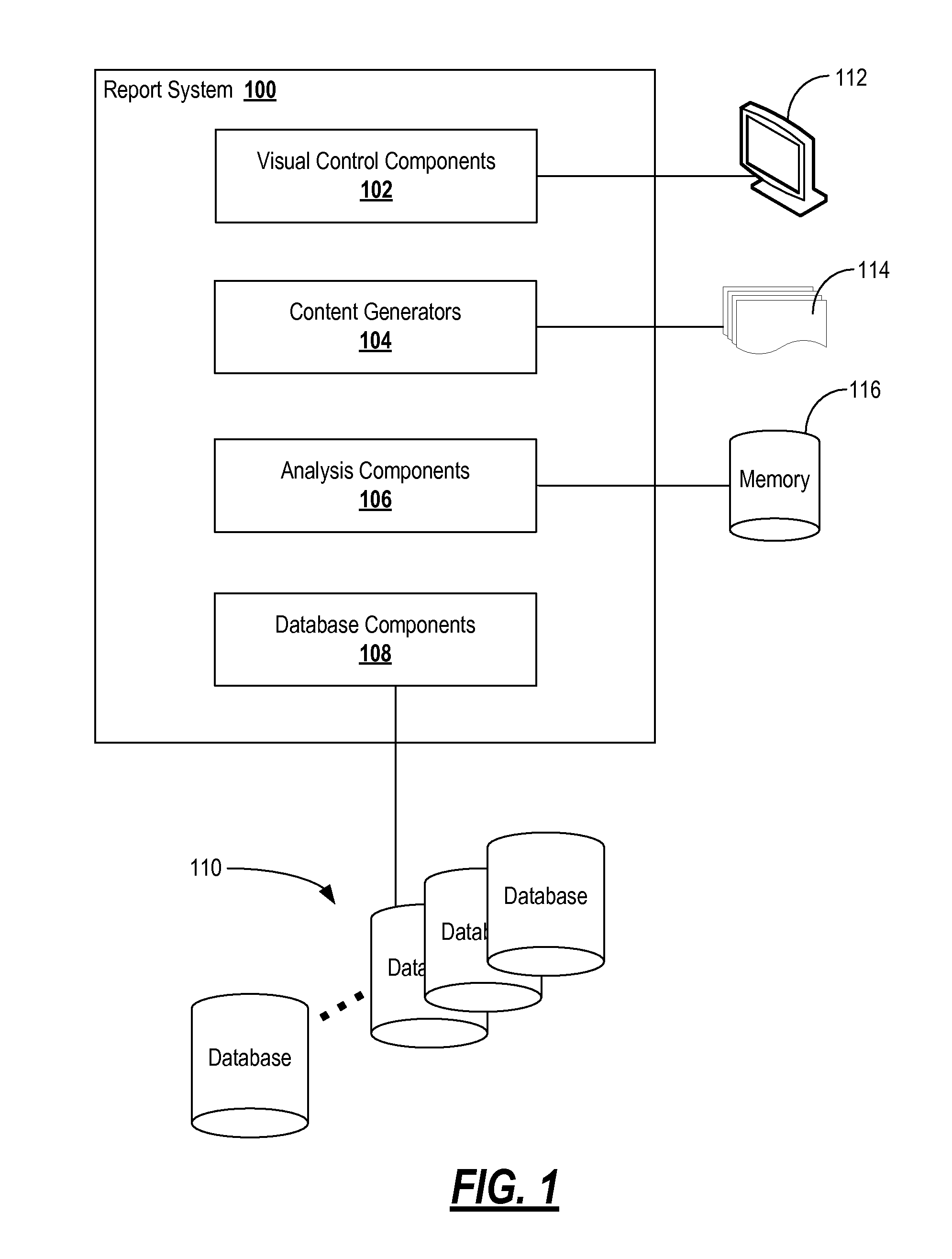
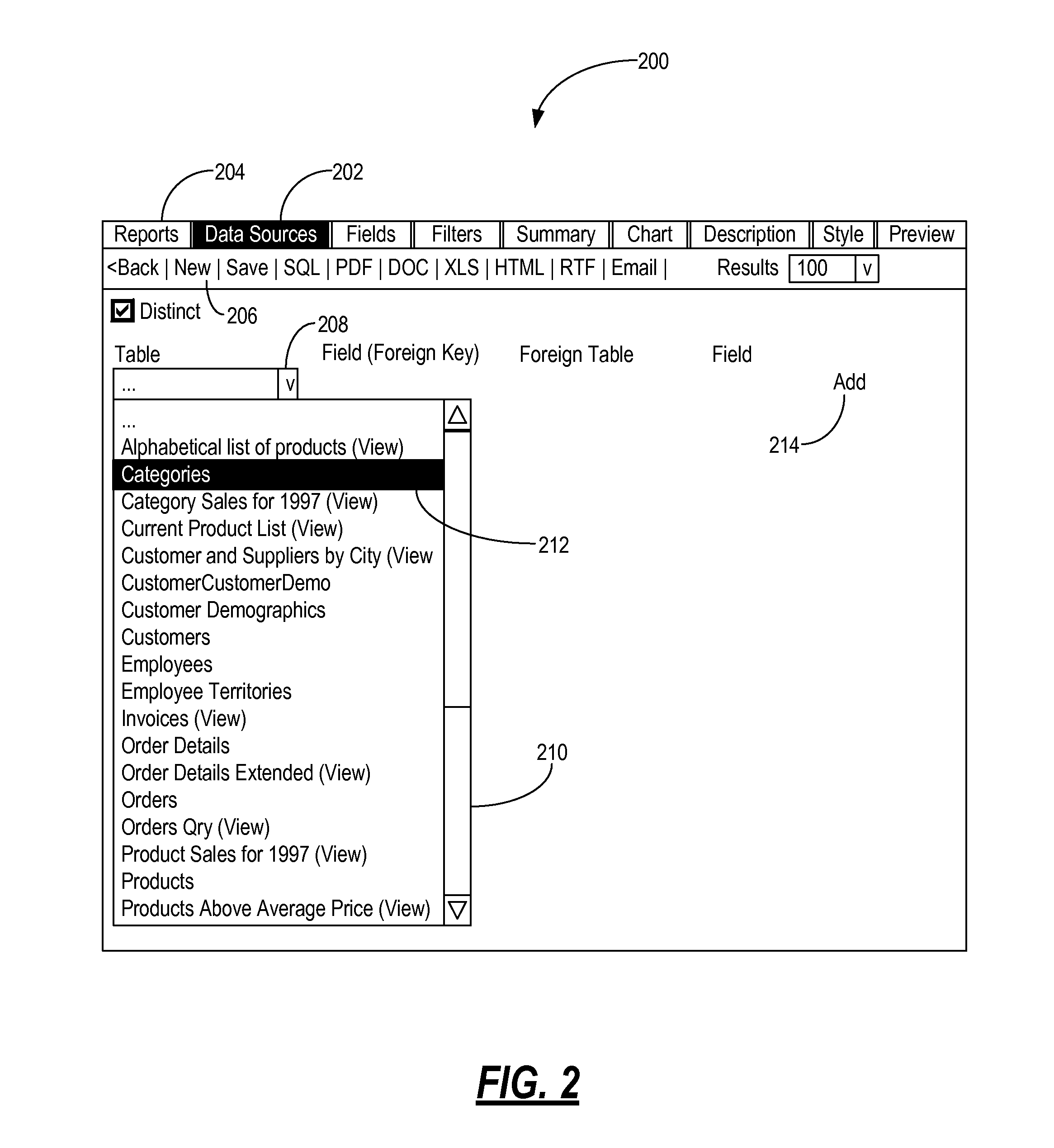
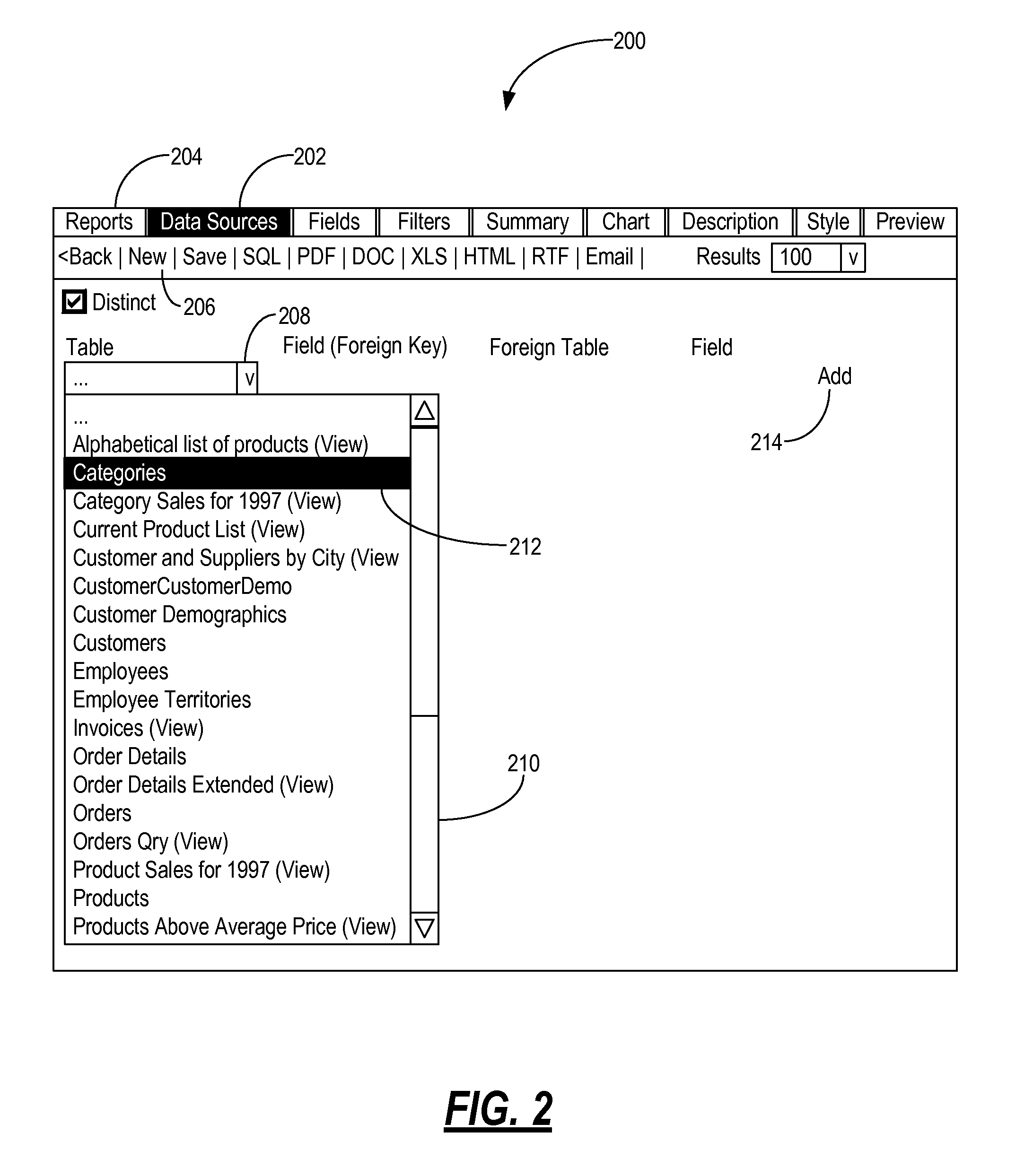
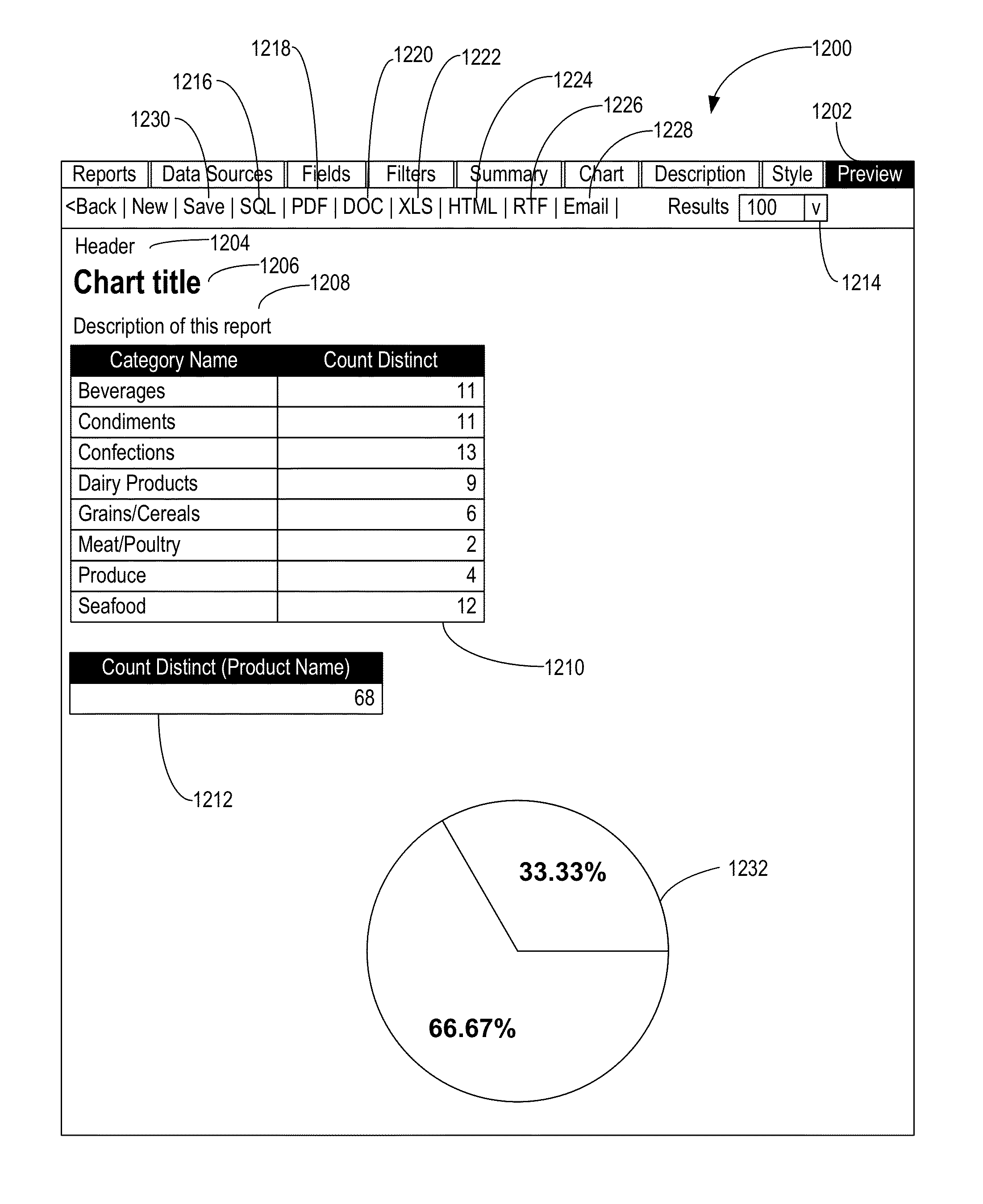
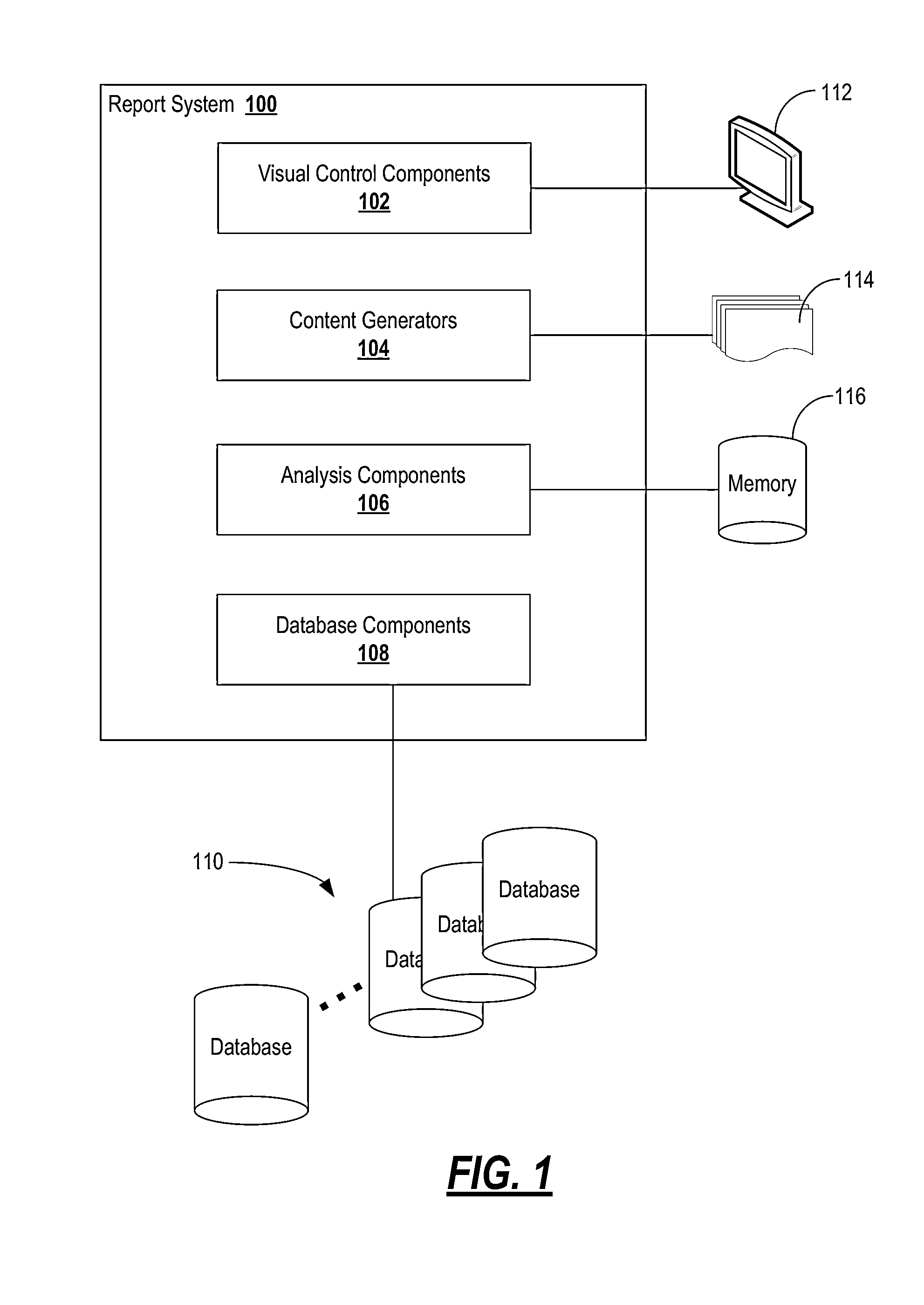
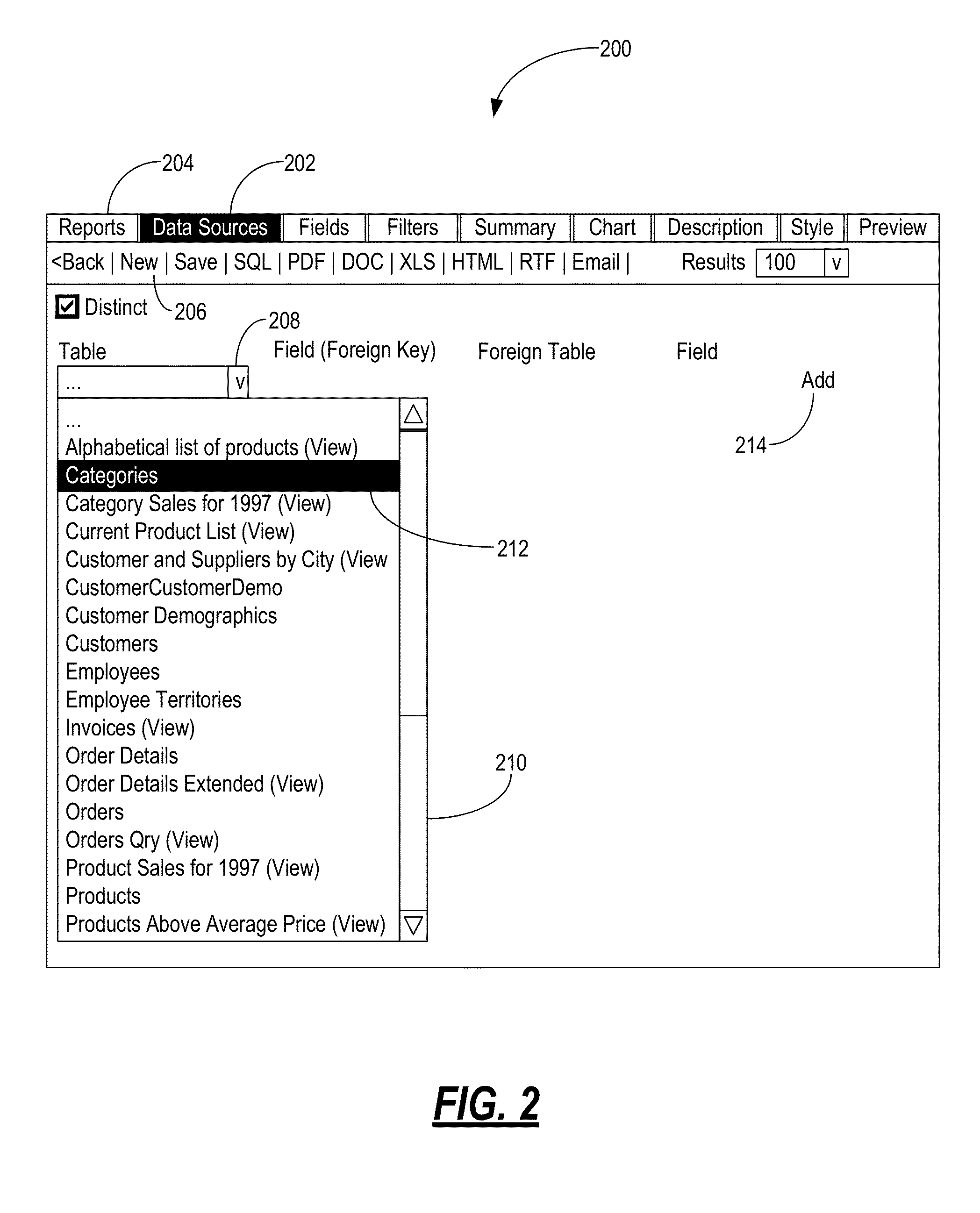
Systems and methods for interactively creating, customizing, and executing reports over the internet
ActiveUS7840600B1Digital data processing detailsWebsite content managementDashboardConfiguration item
The present invention enables users to interactively create, customize, and execute reports on data stored in databases using only a web browser. The user can create, customize, and execute reports by selecting various report elements including, for example, data sources, fields, filters, labels, charts, dashboards, and the like. Advantageously, the present invention enables users to create the reports through an Internet connection, without any special software, such as web browser plug-ins, database applications, and the like, without knowledge of data access languages, such as SQL, and without direct access to a database server. The present invention can directly connect to a plurality of different database types through a virtual or physical network connection. It fully functions without requiring the creation of additional configuration items like catalogs, models or secondary schemas by a programmer or database administrator (DBA).
Owner:IZENDA
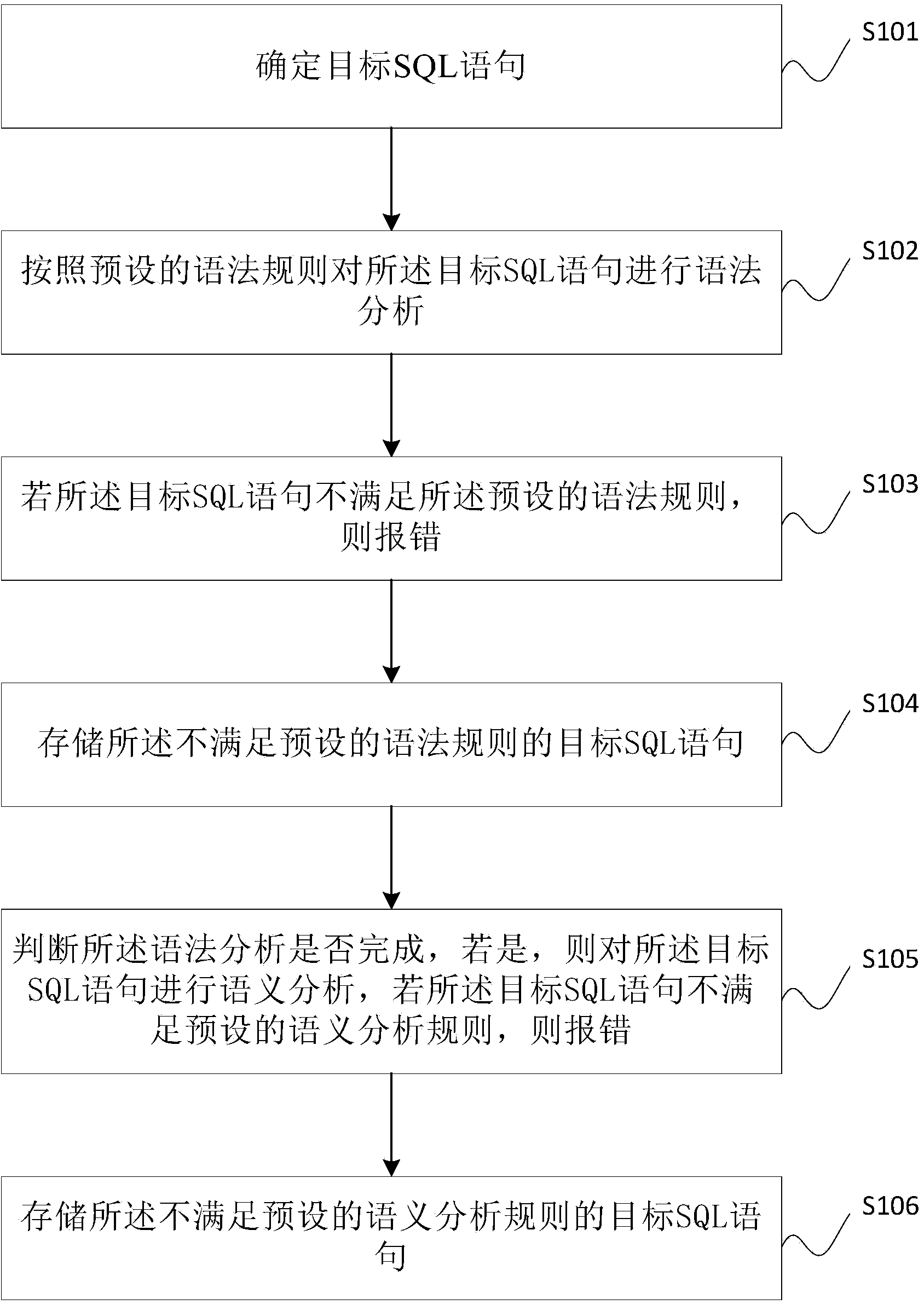
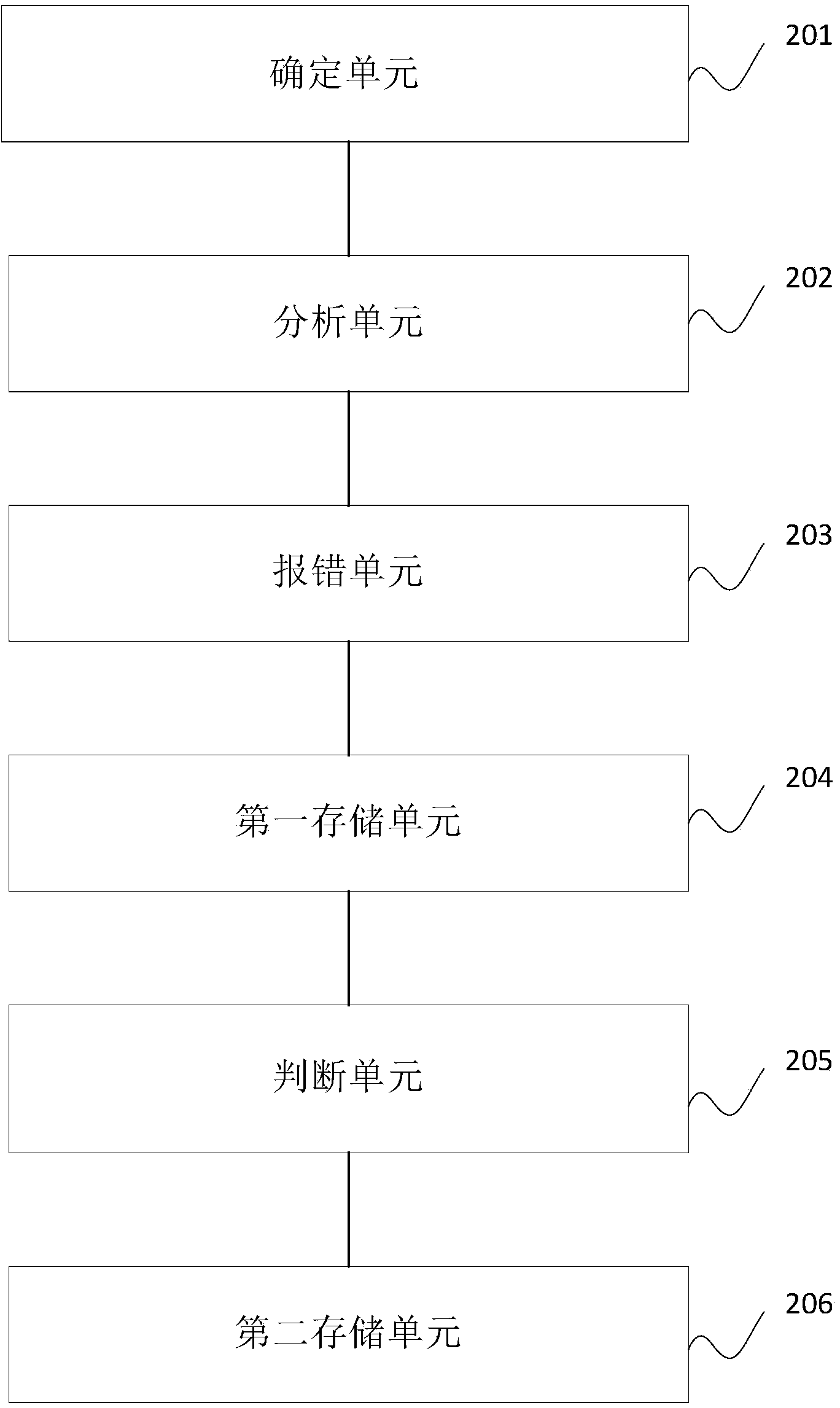
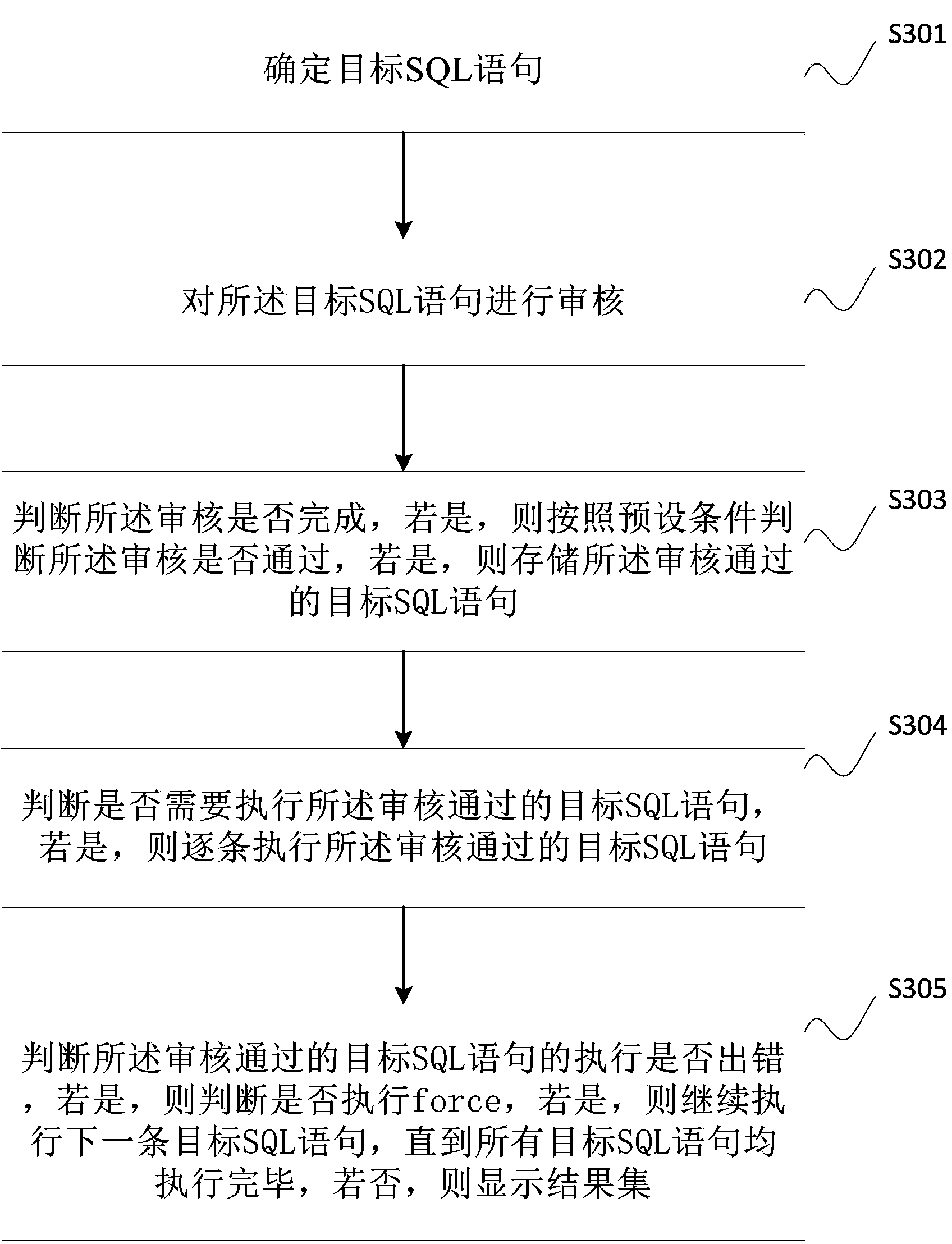
SQL (Structured Query Language) statement auditing method, and database operation and maintenance method and system
InactiveCN104391995AImprove review efficiencySpecial data processing applicationsDatabase design/maintainanceQuery languageDEVS
The invention discloses an SQL statement auditing method, a database operation and maintenance method and a database operation and maintenance system. The SQL statement auditing method provided by the invention comprises the following steps: determining a target SQL statement; respectively performing grammar and semantic analysis on the target SQL statement, and performing grammar analysis on the target SQL statement according to the preset grammar; if the target SQL statement cannot meet the preset grammar, reporting errors; saving the target SQL statement which cannot meet the preset grammar; judging whether the grammar analysis is finished or not; if yes, performing semantic analysis on the target SQL statement, and if the target SQL statement cannot meet the preset semantic analysis rule, reporting errors; saving the target SQL statement which cannot meet the preset semantic analysis rule. All that is needed is to set various preset rules for auditing in advance and the auditing algorithm, the auditing process of the SQL statement is executed according to the algorithm and the various preset rules; the process that database administrators communicate with developers about the SQL statement problems and the modification situation is avoided, so that the auditing efficiency can be increased.
Owner:BEIJING QUNAR SOFTWARE TECH
Self-service database reporting systems and methods
ActiveUS20110035744A1Digital data processing detailsWebsite content managementDashboardConfiguration item
The present disclosure enables users to interactively create, customize, and execute reports on data stored in databases using only a web browser. The user can create, customize, and execute reports by selecting various report elements including, for example, data sources, fields, filters, labels, charts, dashboards, and the like. Advantageously, the present invention enables users to create the reports through an Internet connection, without any special software, such as web browser plug-ins, database applications, and the like, without knowledge of data access languages, such as SQL, and without direct access to a database server. The present invention can directly connect to a plurality of different database types through a virtual or physical network connection. It fully functions without requiring the creation of additional configuration items like catalogs, models or secondary schemas by a programmer or database administrator (DBA).
Owner:IZENDA
Optimized distinct count query system and method
InactiveUS20050177553A1Reduced execution timeReduce processing timeDigital data processing detailsMulti-dimensional databasesData miningDatabase administrator
The present invention relates to a system and method of optimizing execution of a distinct count query. The system and method allows clients or database administrators to improve queries by properly designing data cubes and partitions of the data in the cube. The partition data can also be ordered so as to facilitate determining the range of each partition. Partitions with overlapping ranges can be executed in parallel. Furthermore, partitions with non-overlapping ranges can also be executed in parallel to optimize query execution rather than digressing from parallel to sequential execution by virtue of their range.
Owner:MICROSOFT TECH LICENSING LLC
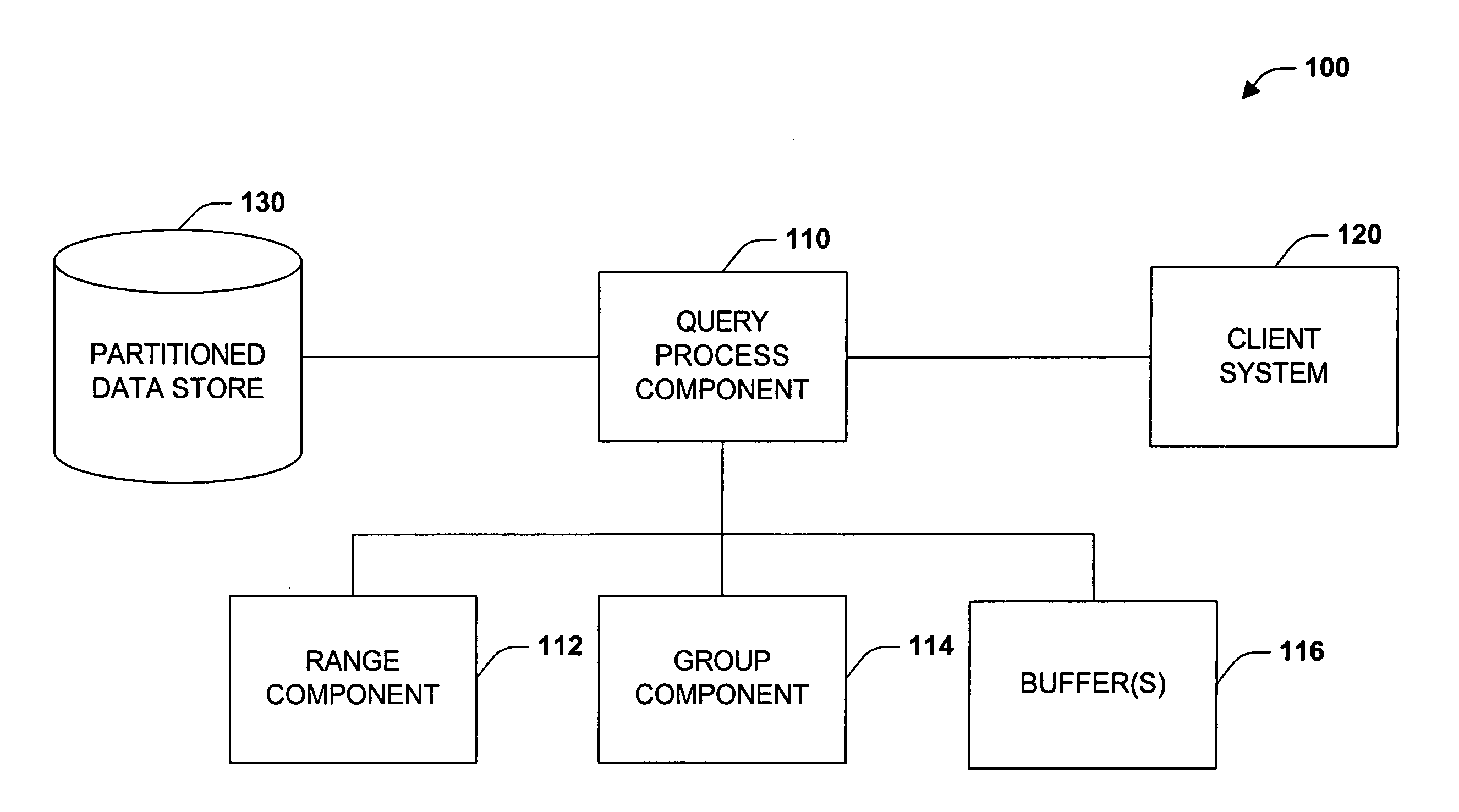
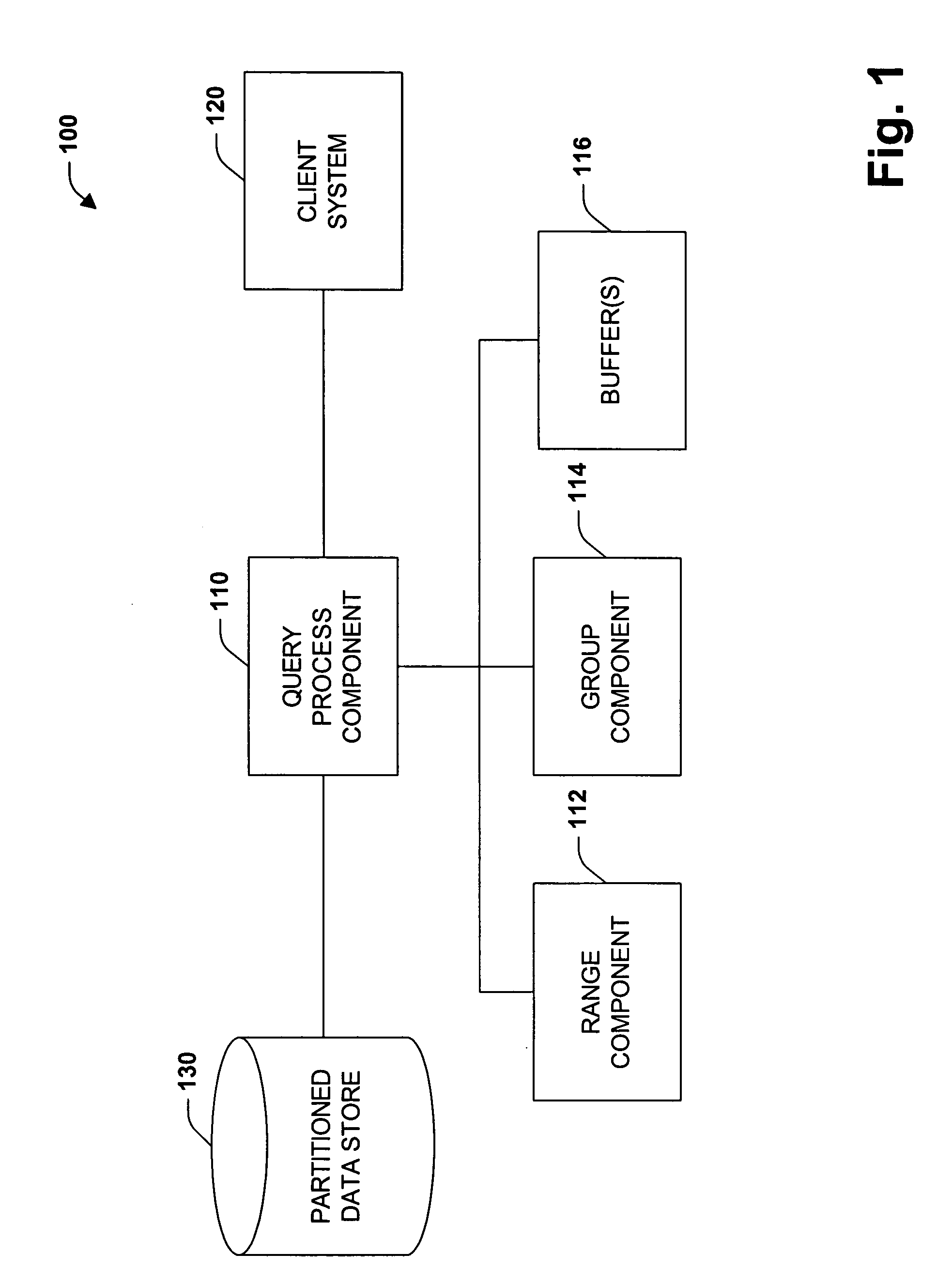
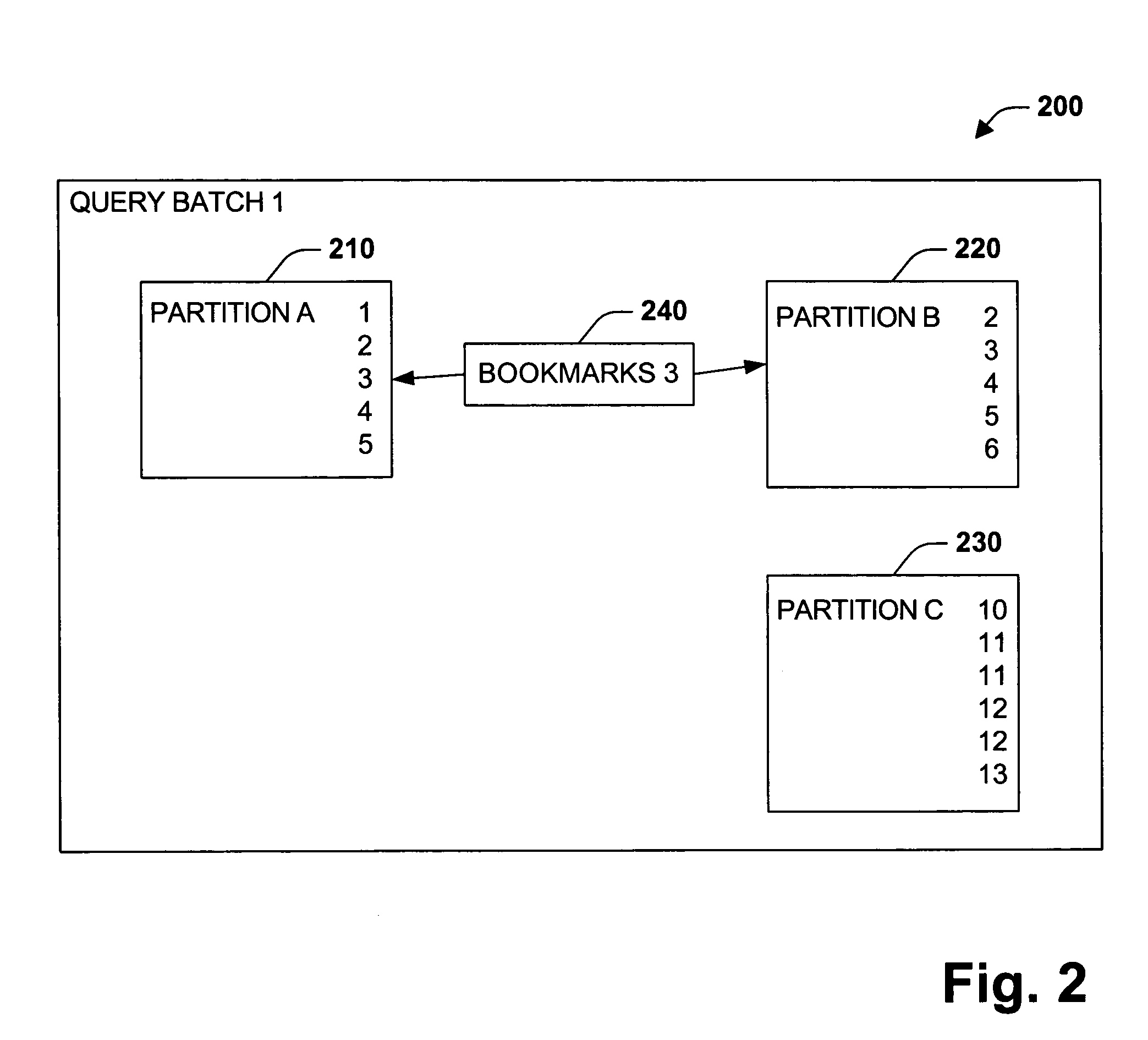
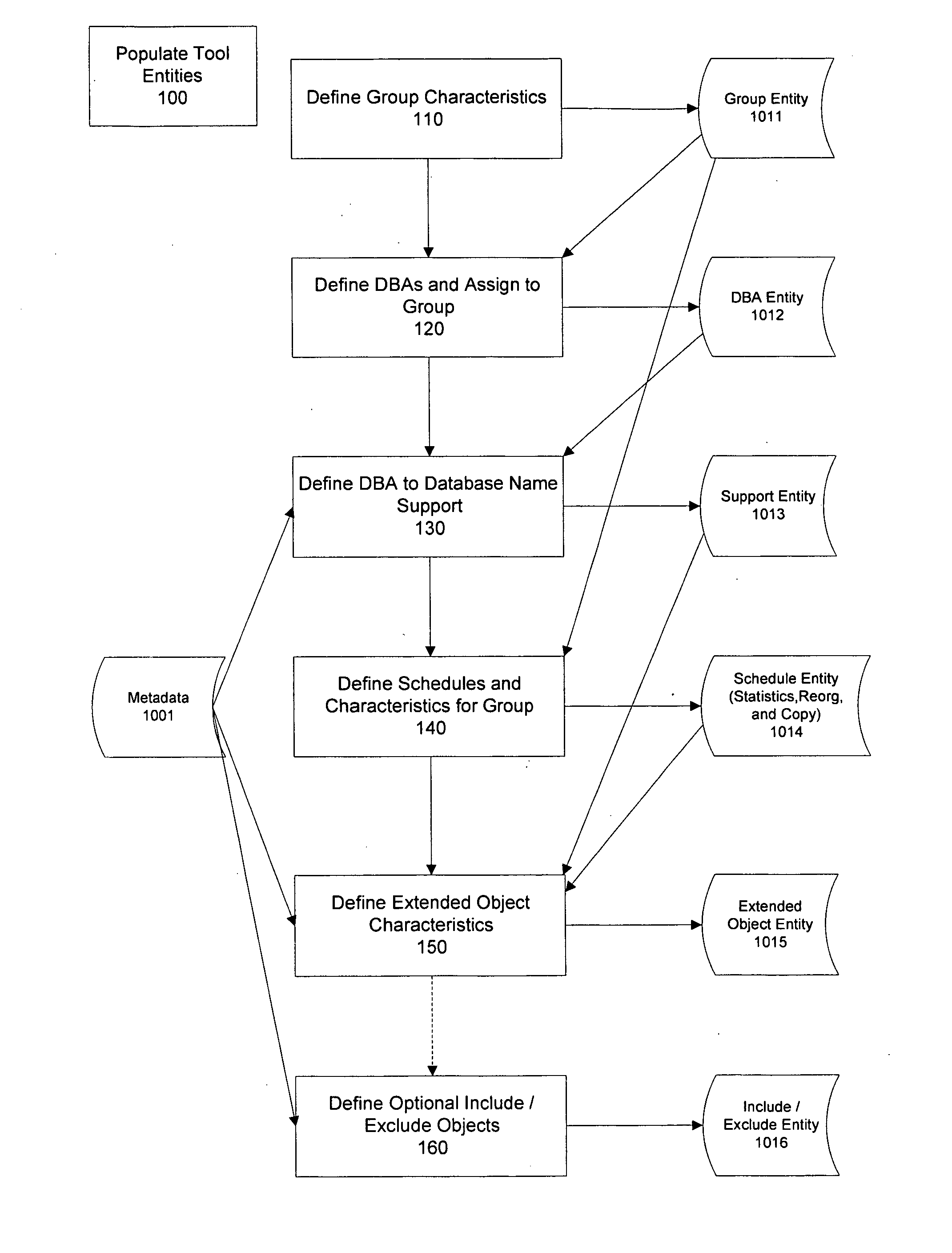
Method and system for balancing and scheduling database maintenance tasks
InactiveUS20050223046A1Improve consistencyEfficiency of maintenance is maximizedDigital data processing detailsError detection/correctionControl mannerDistributed database
Database administrators input database object characteristics and constraints, and maintenance tasks such as object statistics, reorganization, copy, and recovery tasks are prioritized and balanced with a dynamically generated grid of tasks. Reorganization tasks are directly linked to statistics generation and threshold violation analysis. Recovery tasks are automatically generated from copy tasks. The dynamically generated grid distributes database objects across concurrent procedures, based on criteria such as cumulative job size so that each set of procedures process approximately the same amount of data. Maintenance procedures are built and executed in a controlled manner according to maintenance policies of an organization. The user knows what objects will be processed, prior to a maintenance window.
Owner:SMITH RICK A
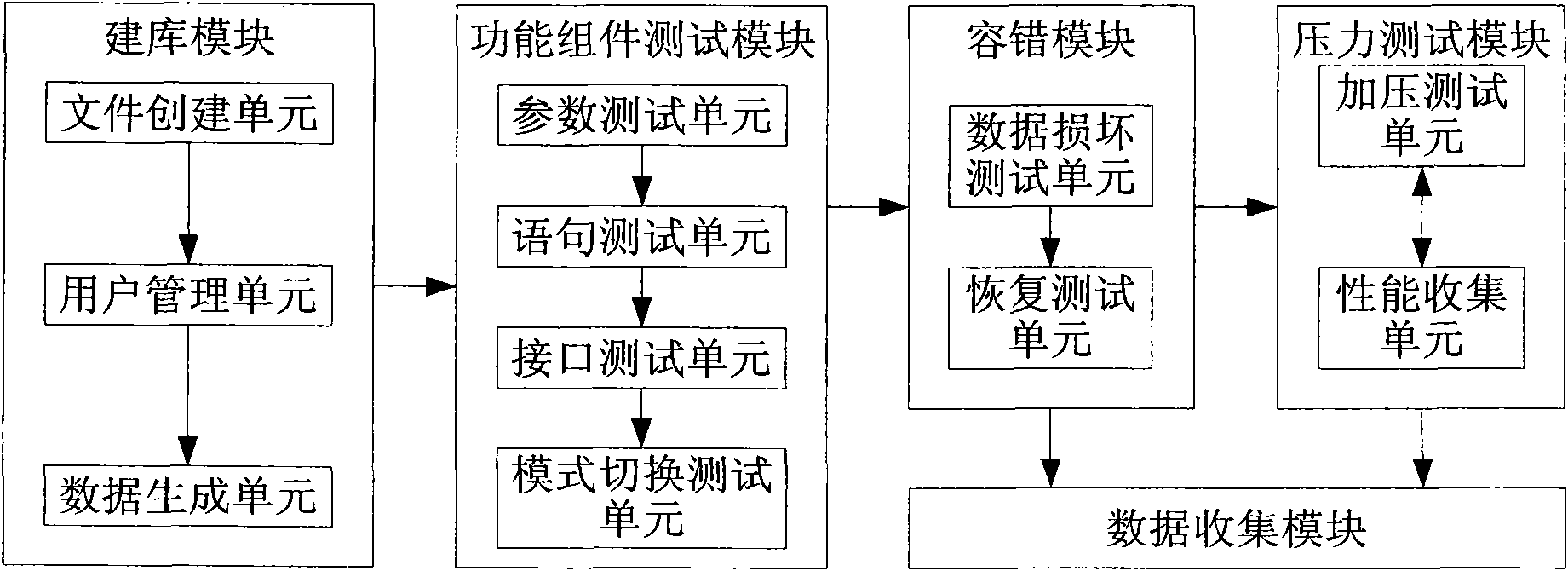
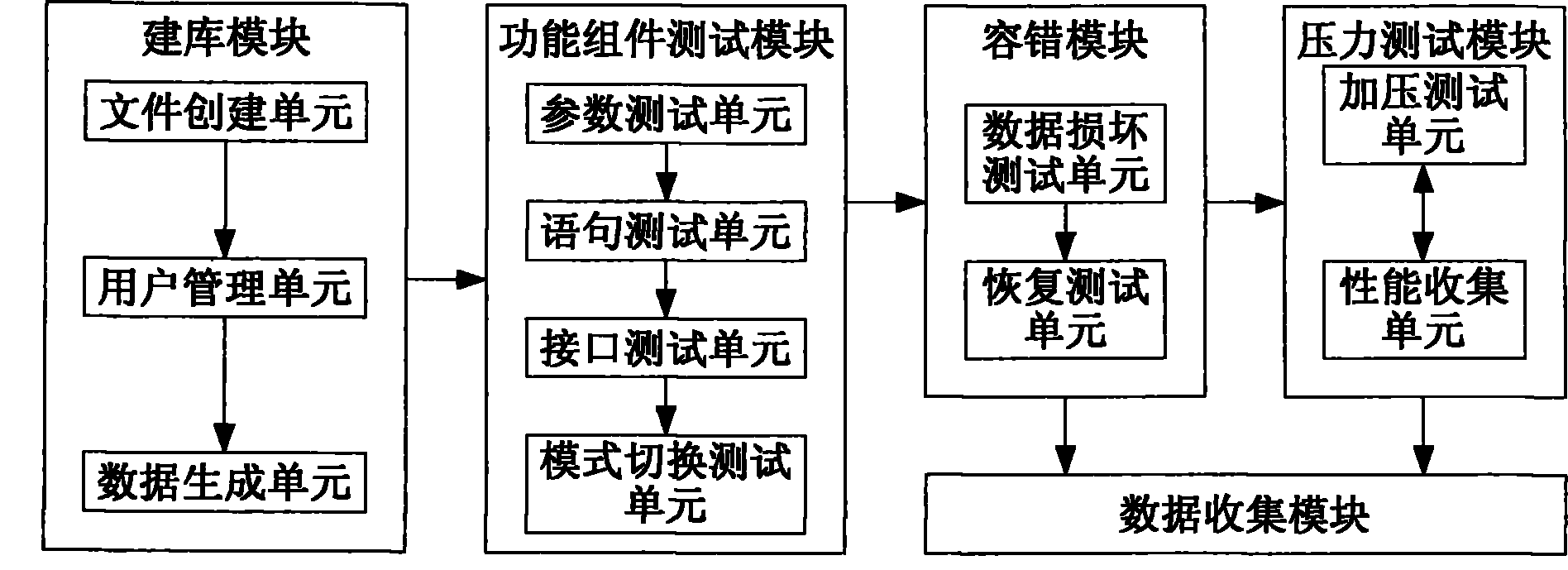
Database compatibility test device and method for server
ActiveCN101789002ARelease performanceWide range of testsSpecial data processing applicationsRedundant hardware error correctionComputer compatibilityClient-side
The invention relates to a database compatibility test device and a method for a server. The method comprises the following steps: building a database on the server and carrying out data sufficiency on the database by generated data or actual data; simulating operation of a database administrator to regulate and test functional units provided by the database; deleting data in the database, testing whether the deleted database can be accessed and restored; simulating database access by a plurality of clients to test limitation performance of the server and maximum concurrent number and transaction ability of a hardware platform; and judging whether the built database is compatible with the server based on test results of the functional unit test module, fault-tolerant module and pressure test module. The invention has strong promptness, accuracy and flexibility, can be unmanned, and conducts test based on true database protocol.
Owner:SUZHOU LANGCHAO INTELLIGENT TECH CO LTD
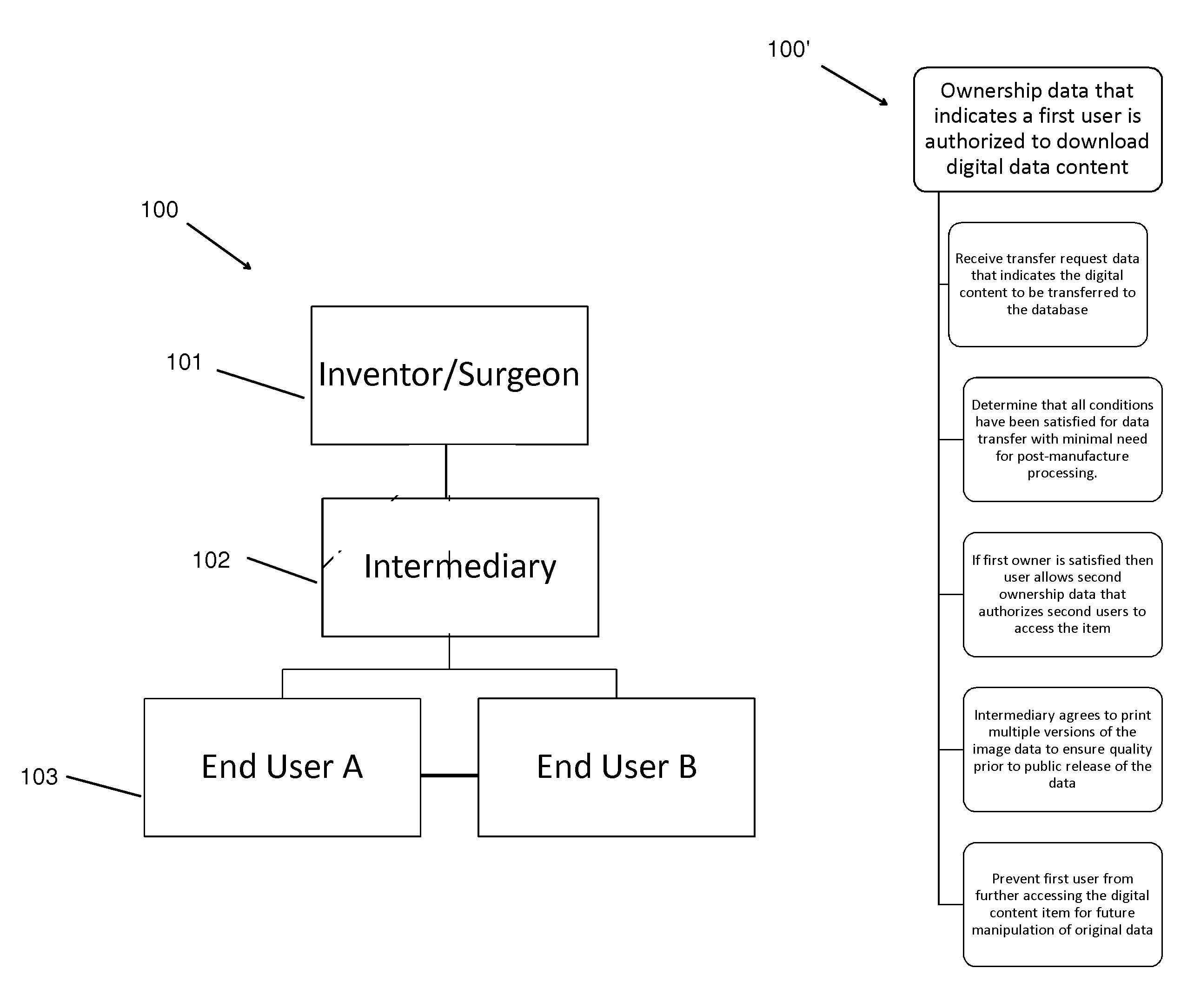
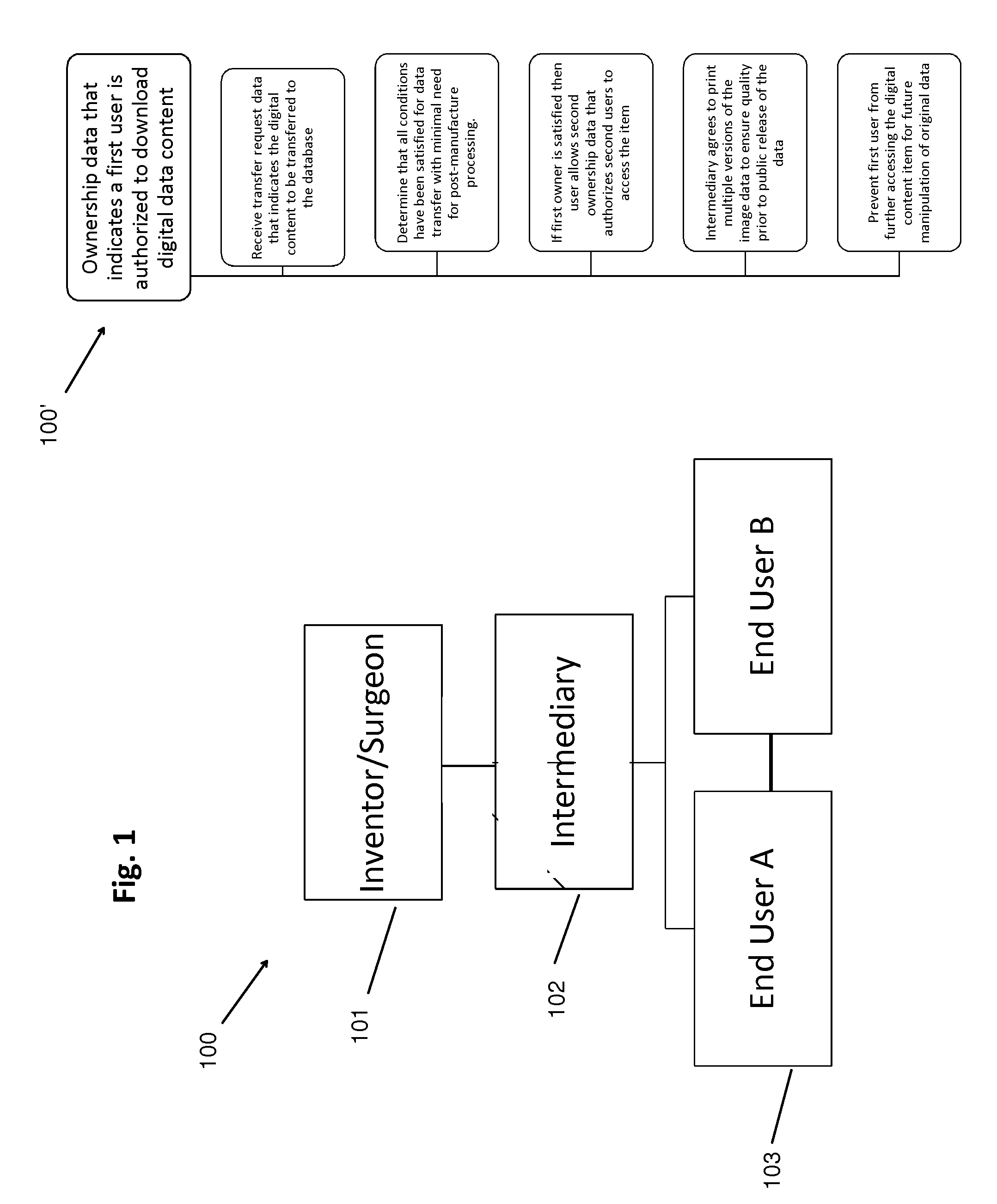
Database and marketplace for medical devices
InactiveUS20150343709A1Improve convenienceFlexibilityMedical simulationPhysical therapies and activitiesMedical equipmentProsthesis
The present disclosure provides a database and methods to allow users to download and / or upload scanned or raw data for objects from or into a database. The data relating to the objects will be stored in a design file on the database, and will allow for end users to print the objects on a 3D printer at their location. A fee may be charged by a manager of the database. The database will allow for sharing of images between health care providers so that they can reproduce and / or redesign the saved images to produce instruments, cutting guides, models, prosthesis for procedures that are specifically suited for their procedure and patient.
Owner:OSIRIS BIOMED 3D
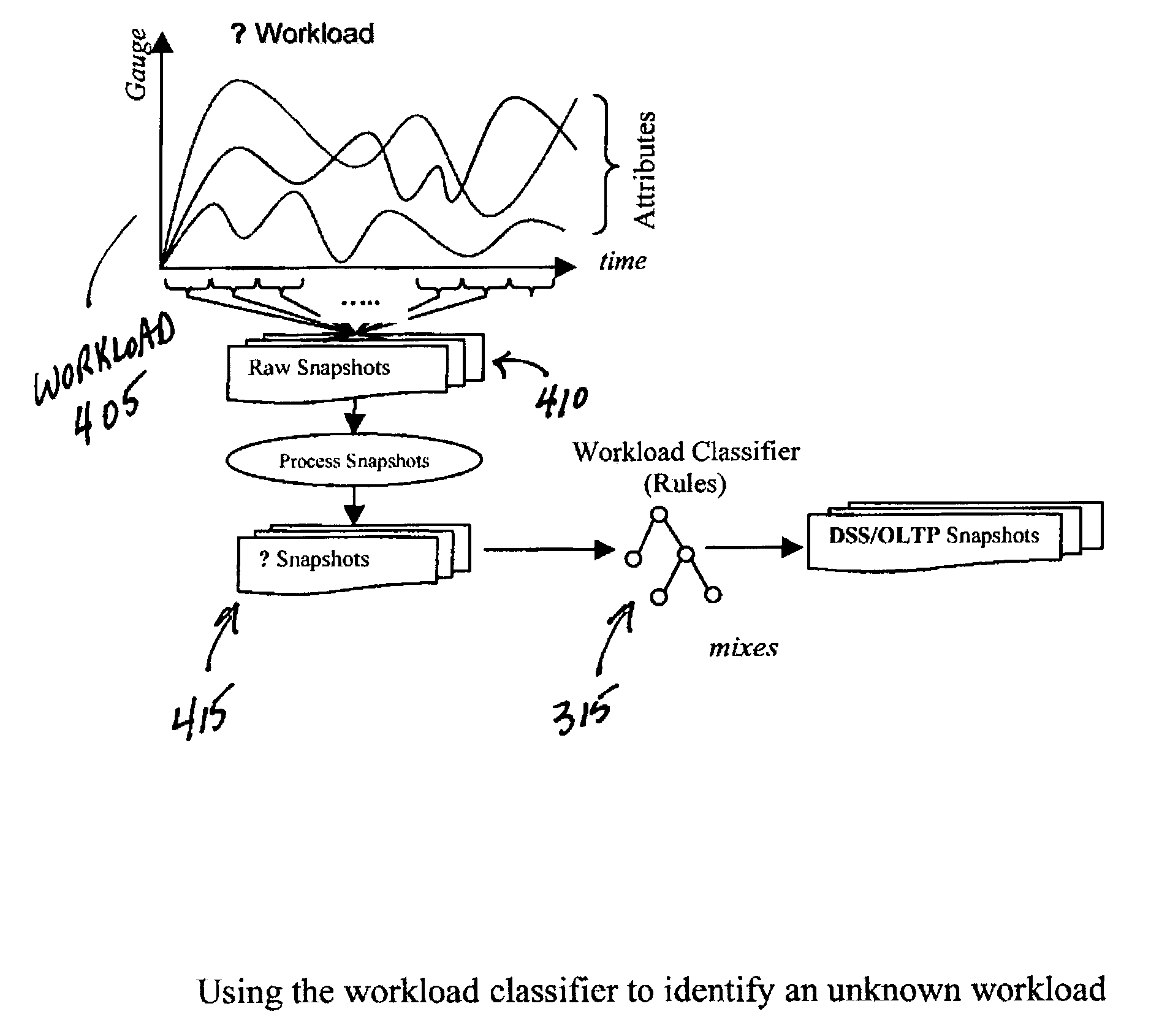
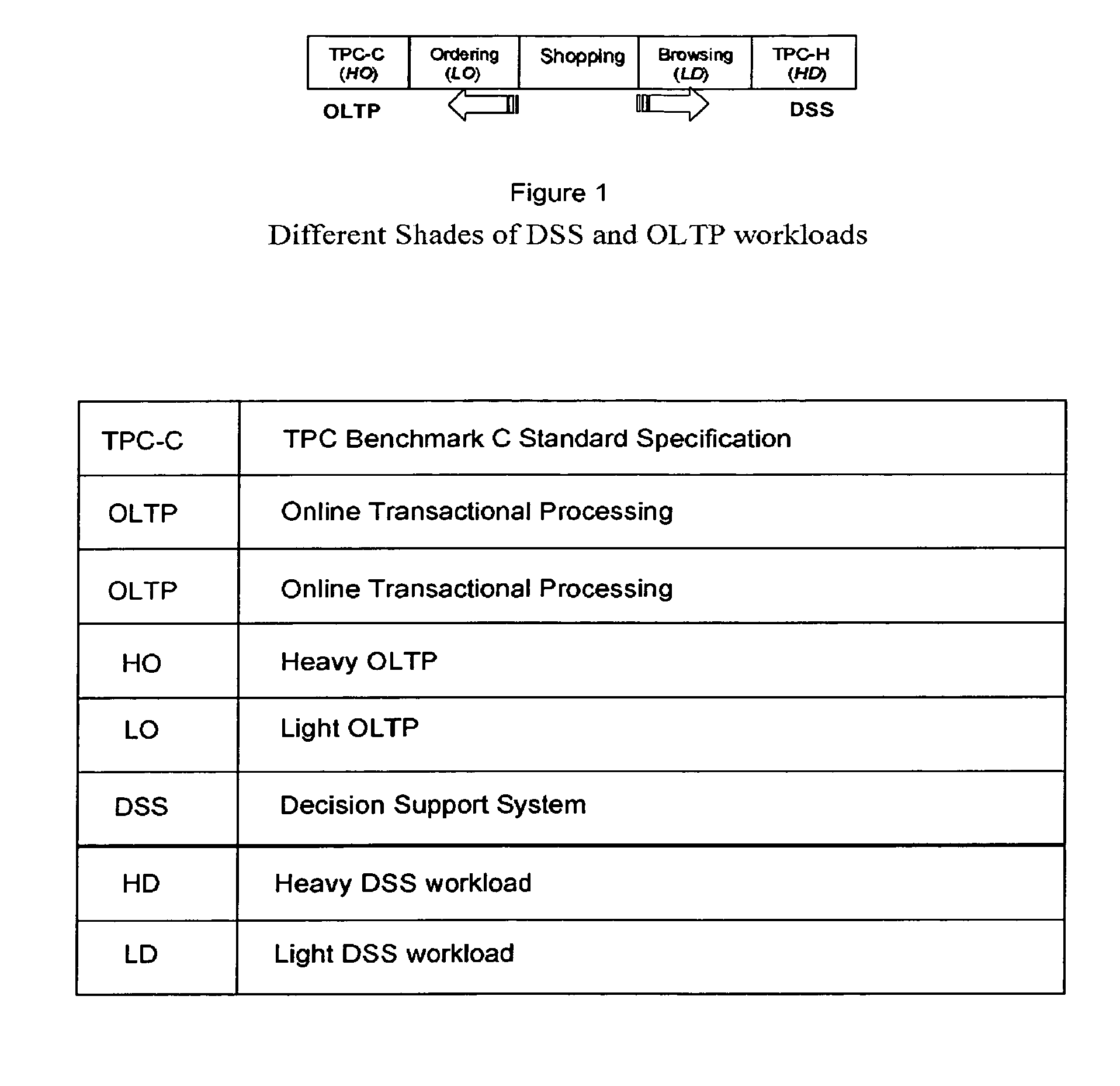
Method for identifying a workload type for a given workload of database requests
InactiveUS7499908B2Easy to operateEfficiently process workloadData processing applicationsResource allocationDecision takingWorkload
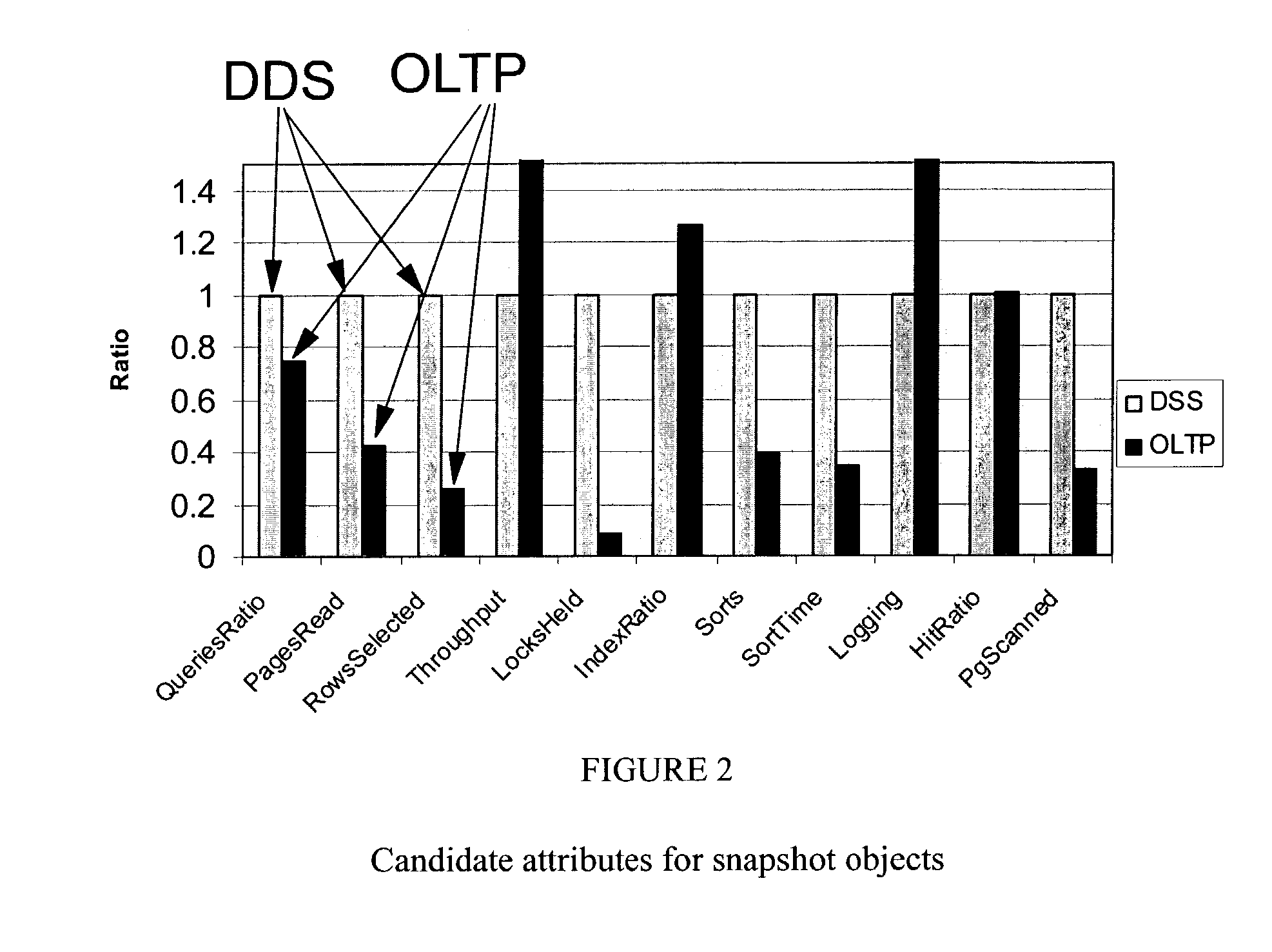
Workload type to be managed by a database management system (DBMS) is a key consideration in tuning the DBMS. Allocations for resources, such as main memory, can be very different depending on whether the workload type is Online Transaction Processing (OLTP) or Decision Support System (DSS). The DBMS also experiences changes in workload type during the normal processing cycle of the DBMS. It would be preferable for the database administrators to recognize the significant shifts of workload type that demand reconfiguring the DBMS to maintain acceptable levels of performance. Disclosed is a workload type classifier module, used by a DBMS, for recognizing workload types so that the DBMS may then manage or adjust its performance and reconfigure its resources accordingly. The classifier may be constructed based on the most significant workload characteristics that differentiate OLTP from DSS. The classifier is then used for identifying changes in workload types contained in a workload.
Owner:IBM CORP
Data Grid Advisor
ActiveUS20120158723A1Improve performanceDigital data information retrievalDigital data processing detailsIn-memory databaseDatabase application
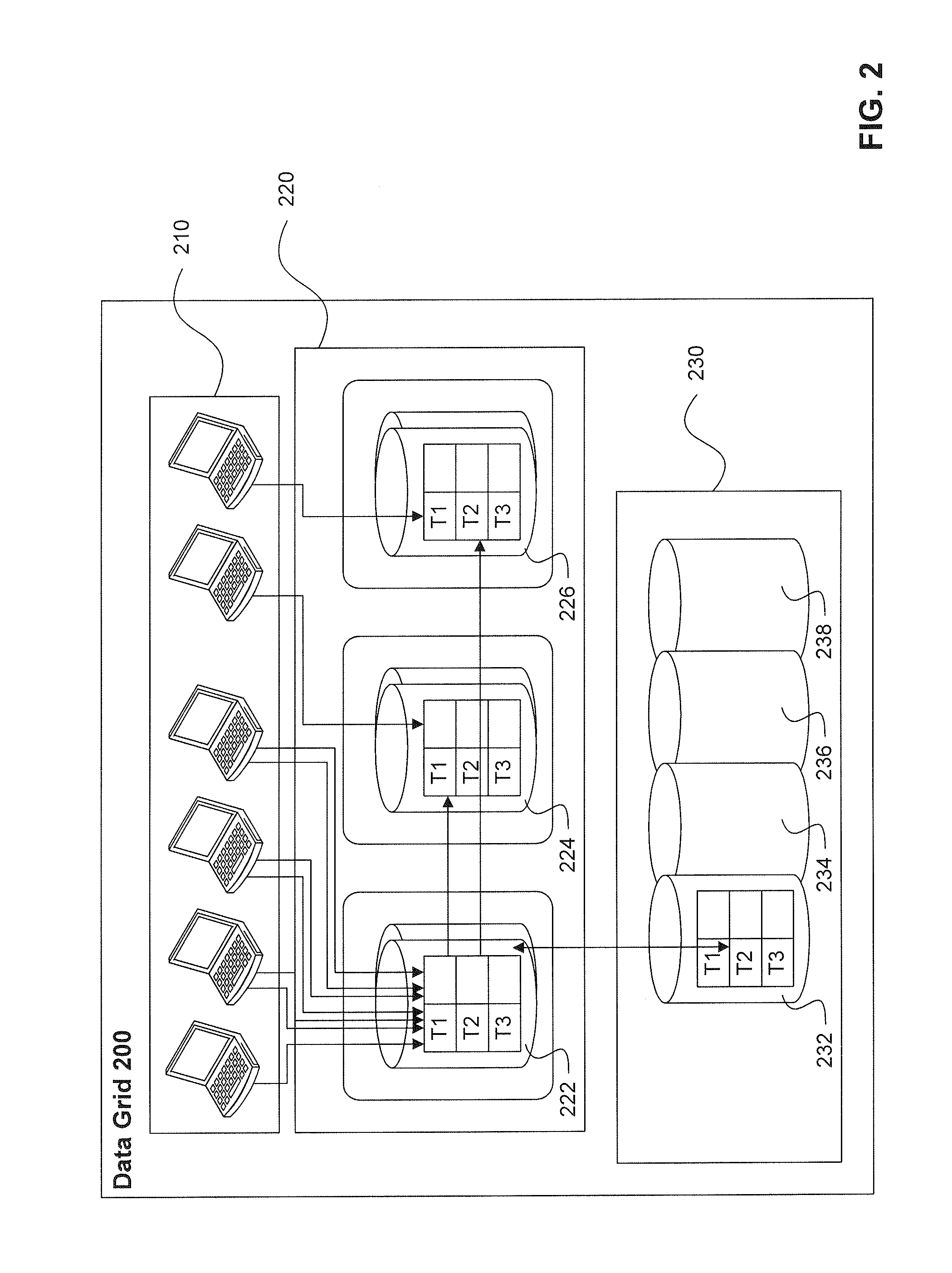
A system and method to generate an improved layout of a data grid in a database environment is provided. The data grid is a clustered in-memory database cache comprising one or more data fabrics, where each data fabric includes multiple in-memory database cache nodes. A data grid advisor capability can be used by application developers and database administrators to evaluate and design the data grid layout so as to optimize performance based on resource constraints and the needs of particular database applications.
Owner:SYBASE INC
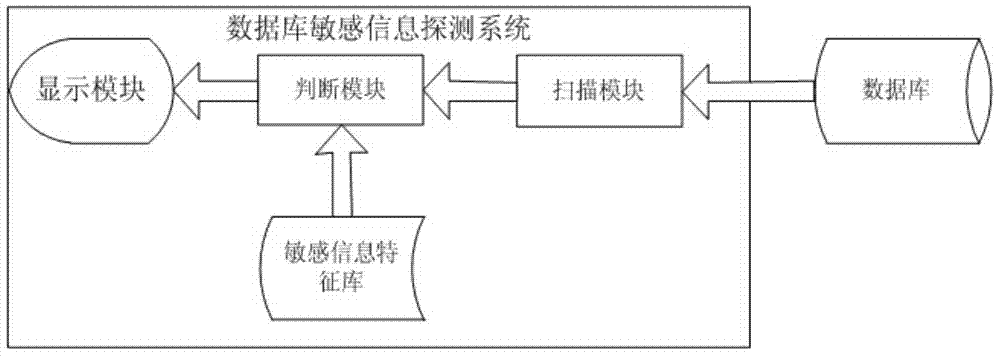
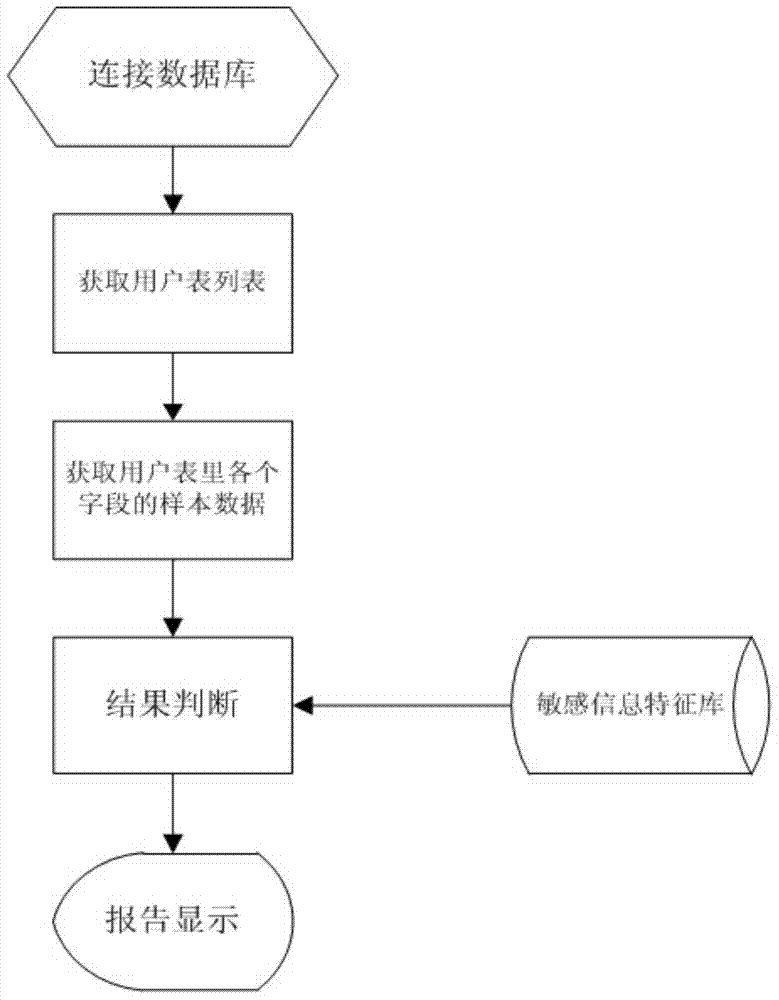
Method and system for detecting sensitive information in database
ActiveCN104123370AKey protectionKey auditSpecial data processing applicationsPayment card numberInformation security
The invention relates to the technical field of information security, and provides a method and system for detecting sensitive information in a database. The method for detecting the sensitive information in the database comprises the steps of scanning a system view of the database to acquire all user tables, extracting a part of data from each field of each user table as a sample, and carrying out analysis and matching on the samples to judge whether the sensitive information exists. The system for detecting the sensitive information in the database comprises a system table, a scanning module, a judgment module and a display module, wherein the scanning module is connected with the database, and the judgment module is connected with a sensitive information feature base, the scanning module and the display module. According to the method and system for detecting the sensitive information in the database, based on the regular expression feature base, by carrying out scanning detection on the user data in the database through the feature base, the position of the sensitive information of mobile phone numbers, bank card numbers, ID numbers, e-mail addresses and the like can be found, a detailed scanning report can be provided, and then a database administrator can carry out key protection and auditing.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
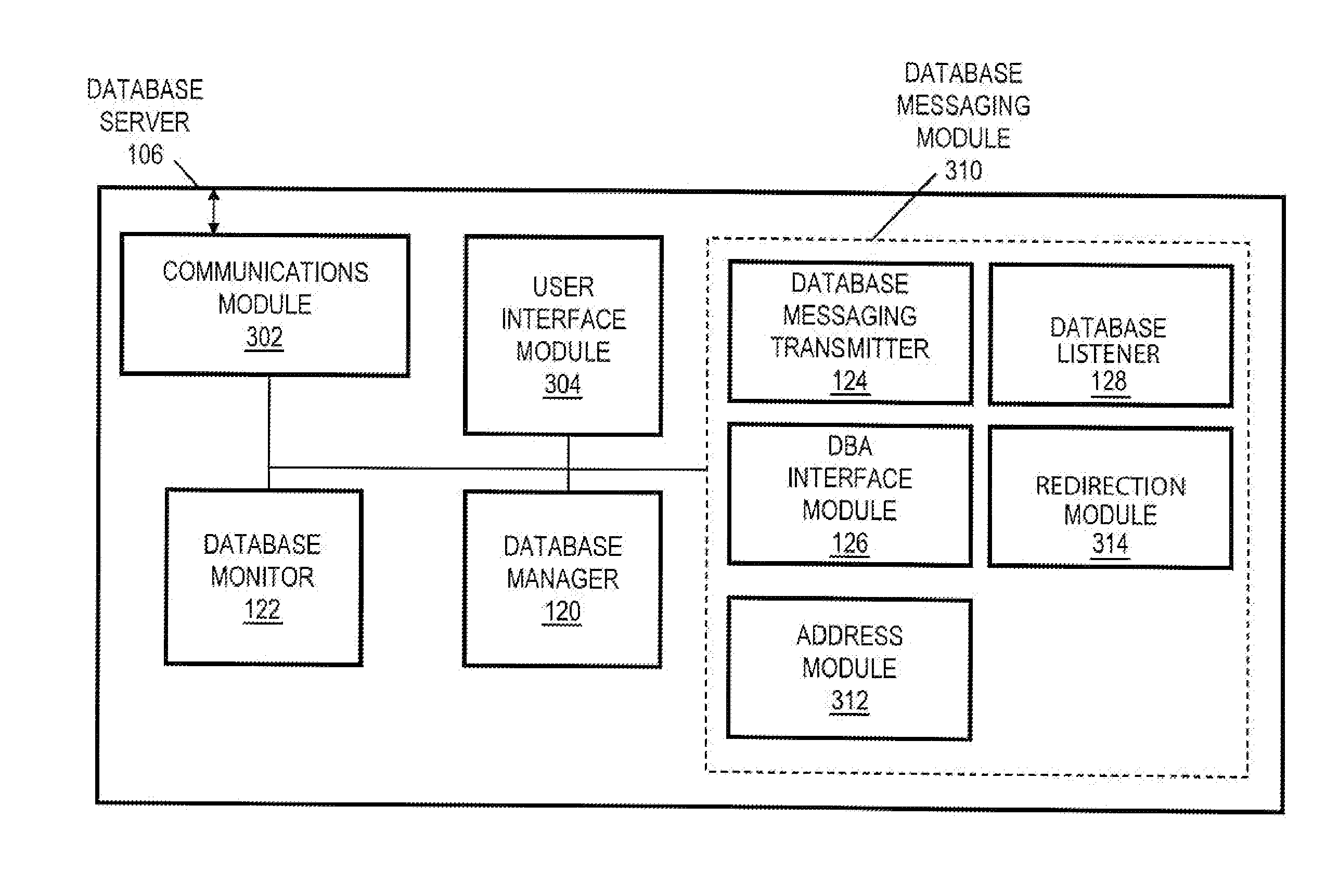
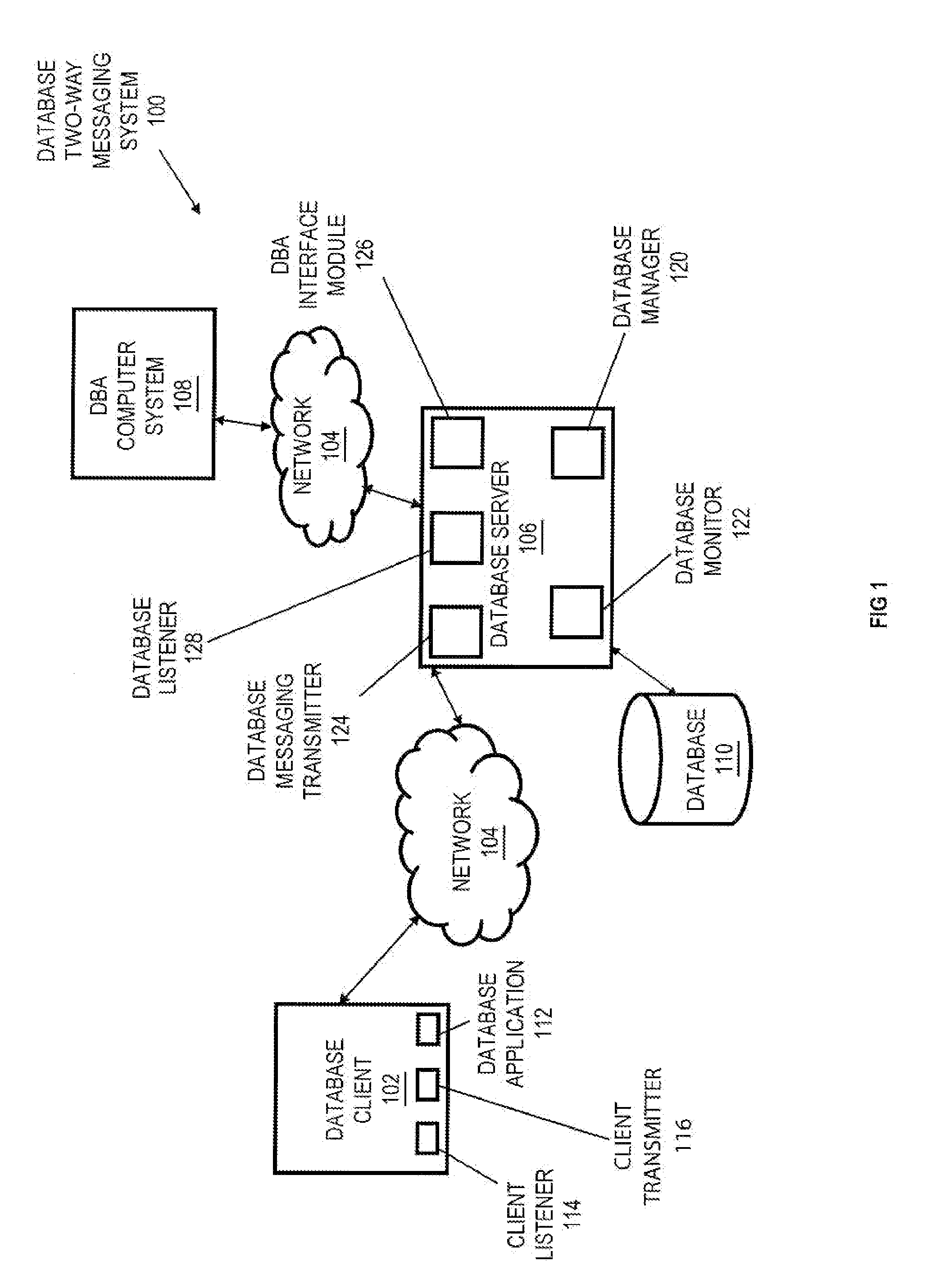
Integrated Two-Way Communications Between Database Client Users and Administrators
InactiveUS20080222264A1Multiple digital computer combinationsData switching networksIp addressClient-side
Systems, methods and media for two-way communication between database client users and administrators are disclosed. Embodiments may include a method for communicating between database client users and administrators. Embodiments may include receiving a message request to send to one or more recipients, the message request including message content and an indication of the one or more recipients to which the message will be sent. Embodiments may also include determining an Internet Protocol (IP) address associated with each of the one or more recipients based on the message request and transmitting a message to each of the determined IP addresses, where the message includes the received message content. Embodiments may also include receiving a second message from one of the determined IP addresses. Further embodiments may include displaying the second message in a display window. Recipients of messages may include database administrators (DBAs) or database client users.
Owner:SNAPCHAT
Database control method
ActiveUS20050027719A1Eliminate useImprove usabilityInput/output to record carriersDigital data processing detailsDatabase managerEngineering
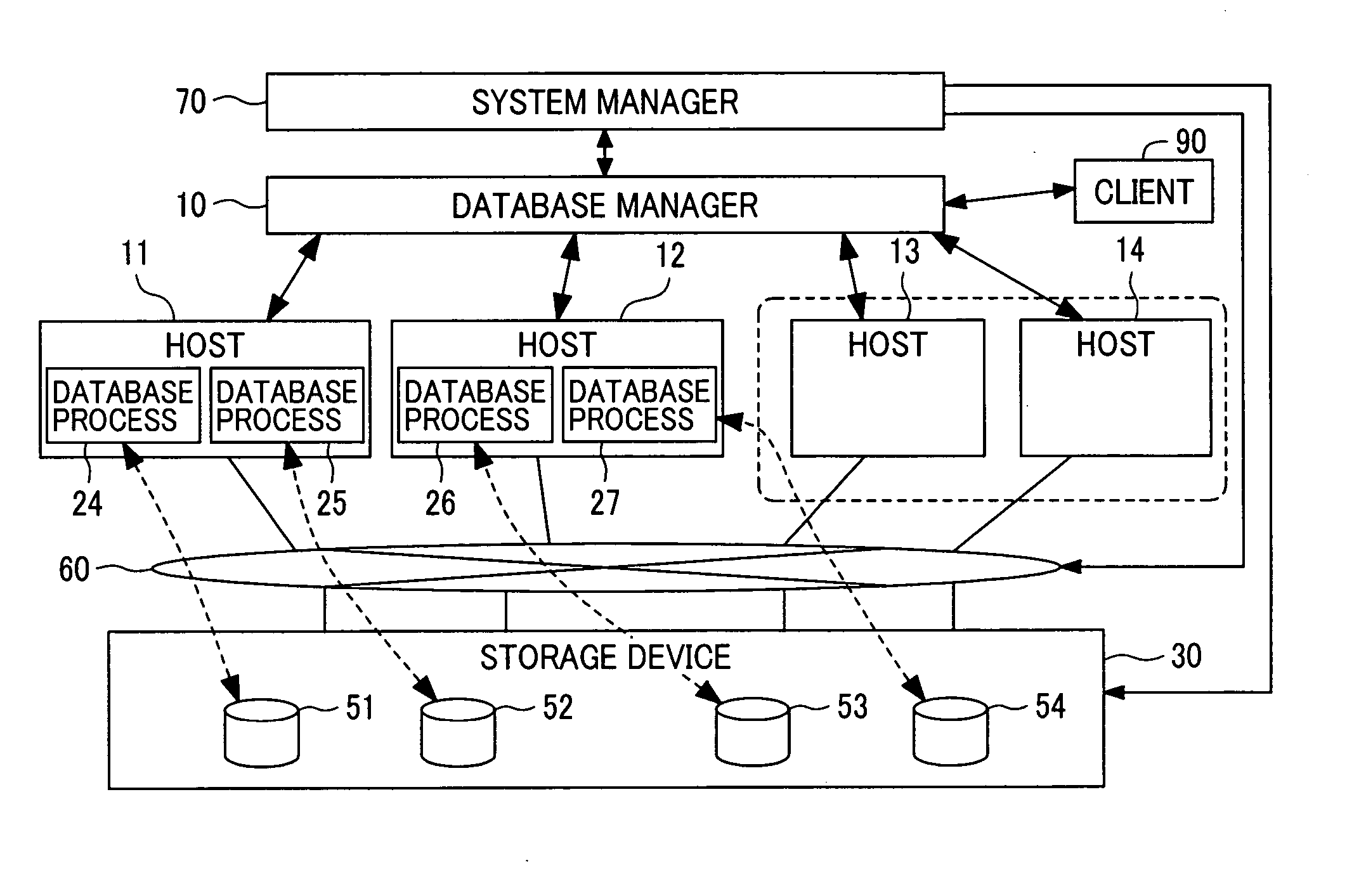
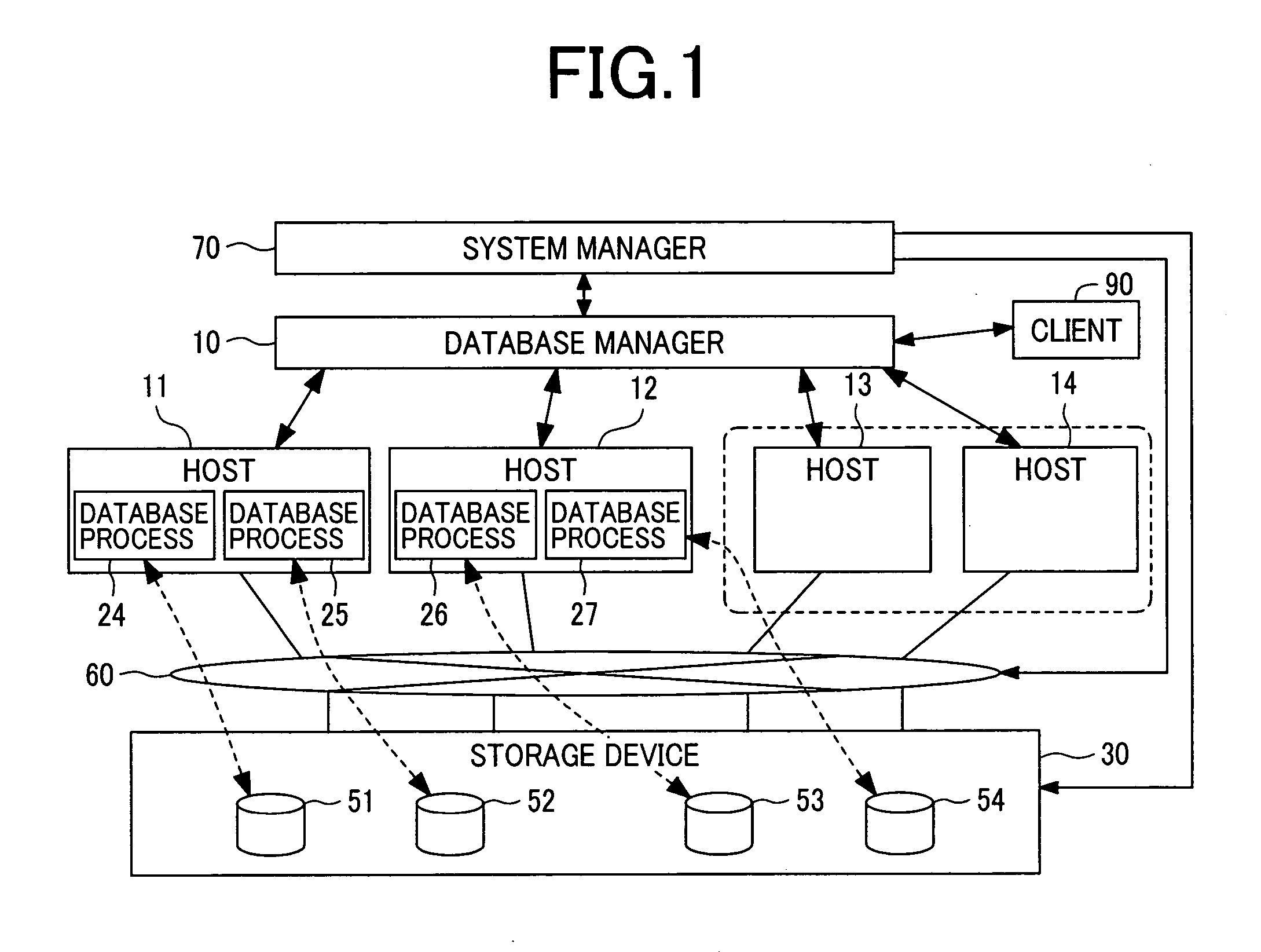
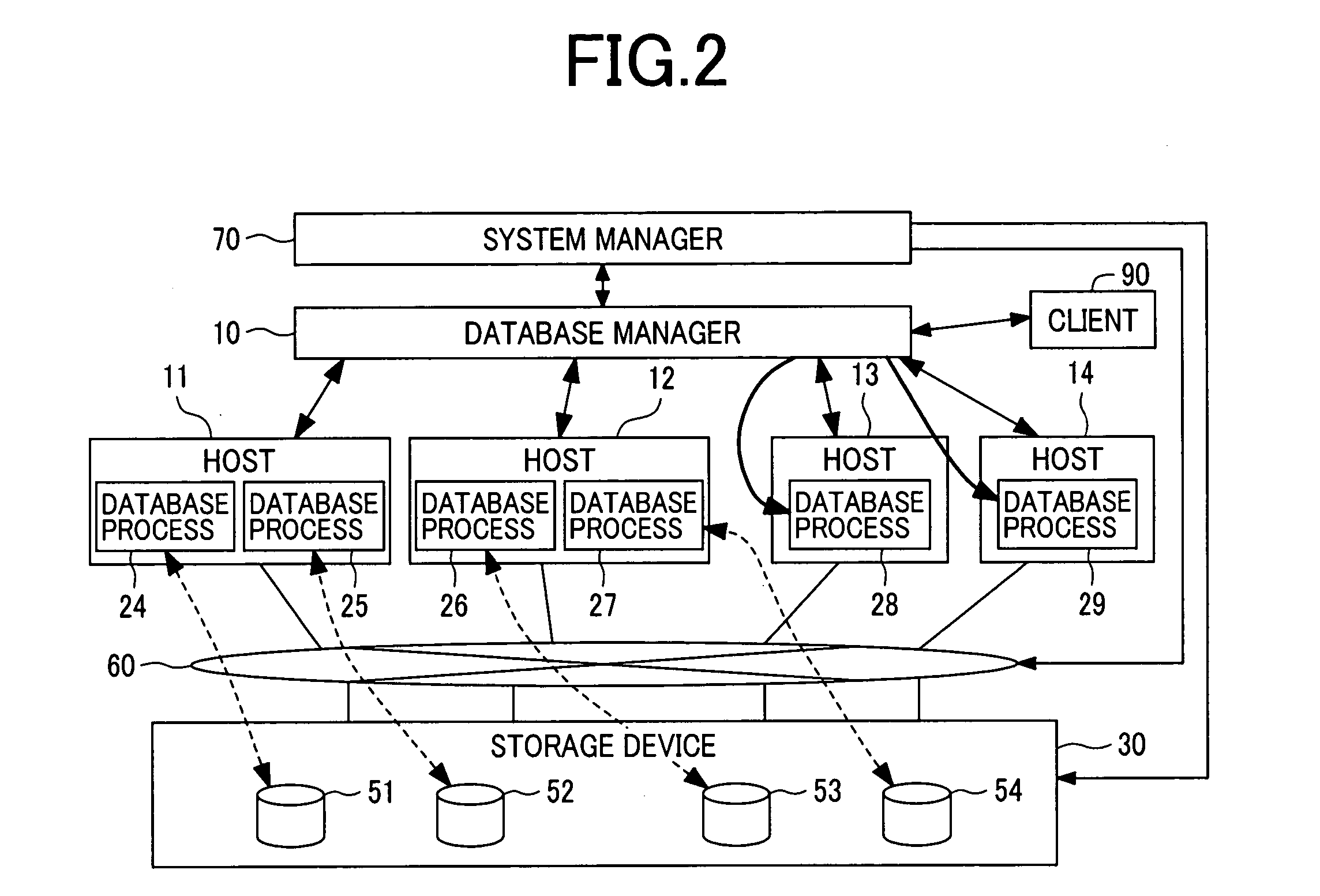
The present invention aims to dynamically re-configure hosts and storage in a shared-nothing database. In the shared-nothing database, processes 24 to 29 executed in the hosts 11 to 14 access data of a storage device 30. A system manager 70 and a database manager 10 manage the hosts 11 to 14 and the storage device 30. The processes 24 to 29 access one or more disks 51 to 54 of the storage device. To add or reduce the number of the hosts, the processes 24 to 29 are reassigned among the hosts 11 to 14.
Owner:HITACHI LTD
Software performance and management system
InactiveUS20020129035A1Efficient identificationAccurate measurementData processing applicationsDigital data processing detailsSoftware systemApplication software
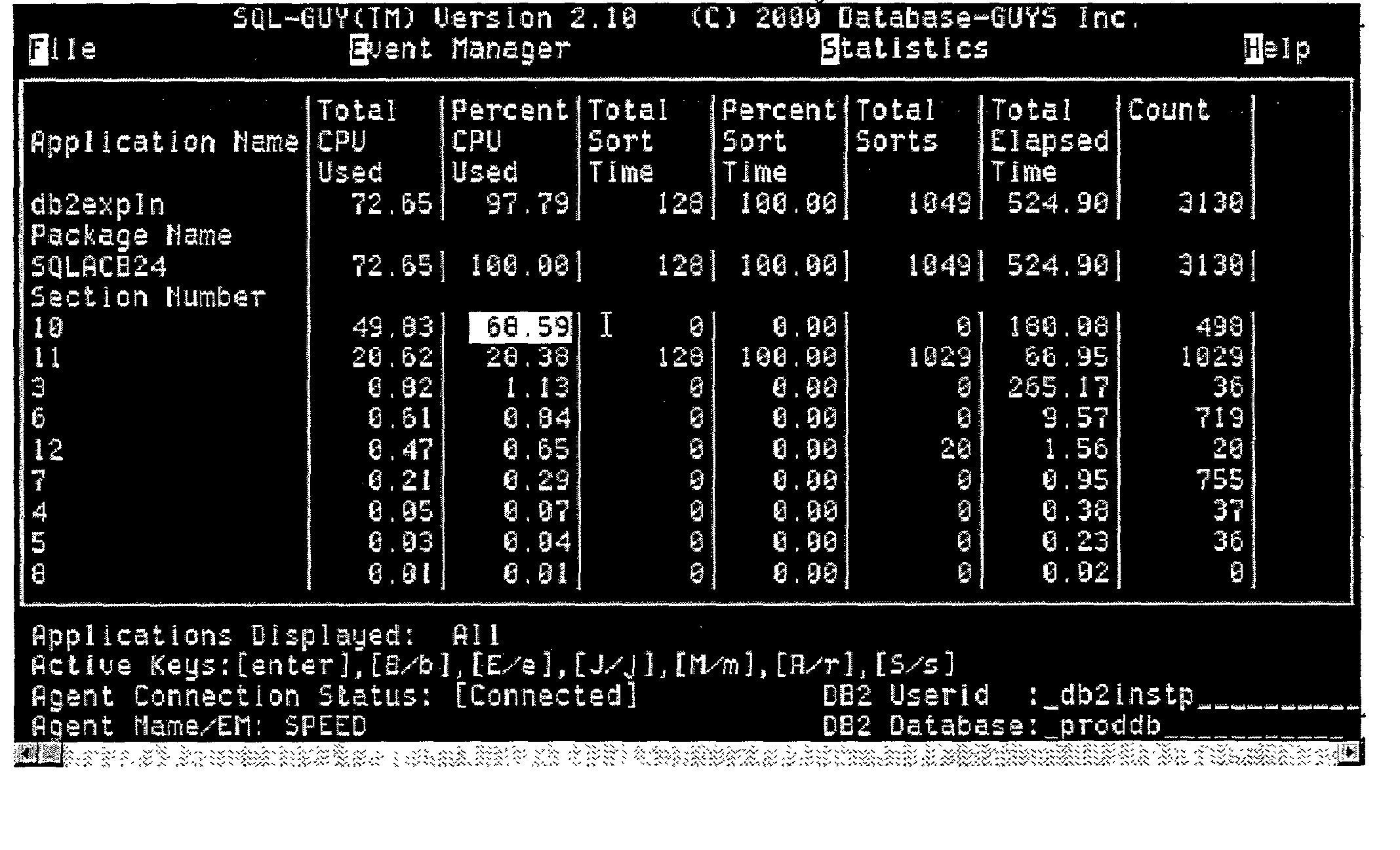
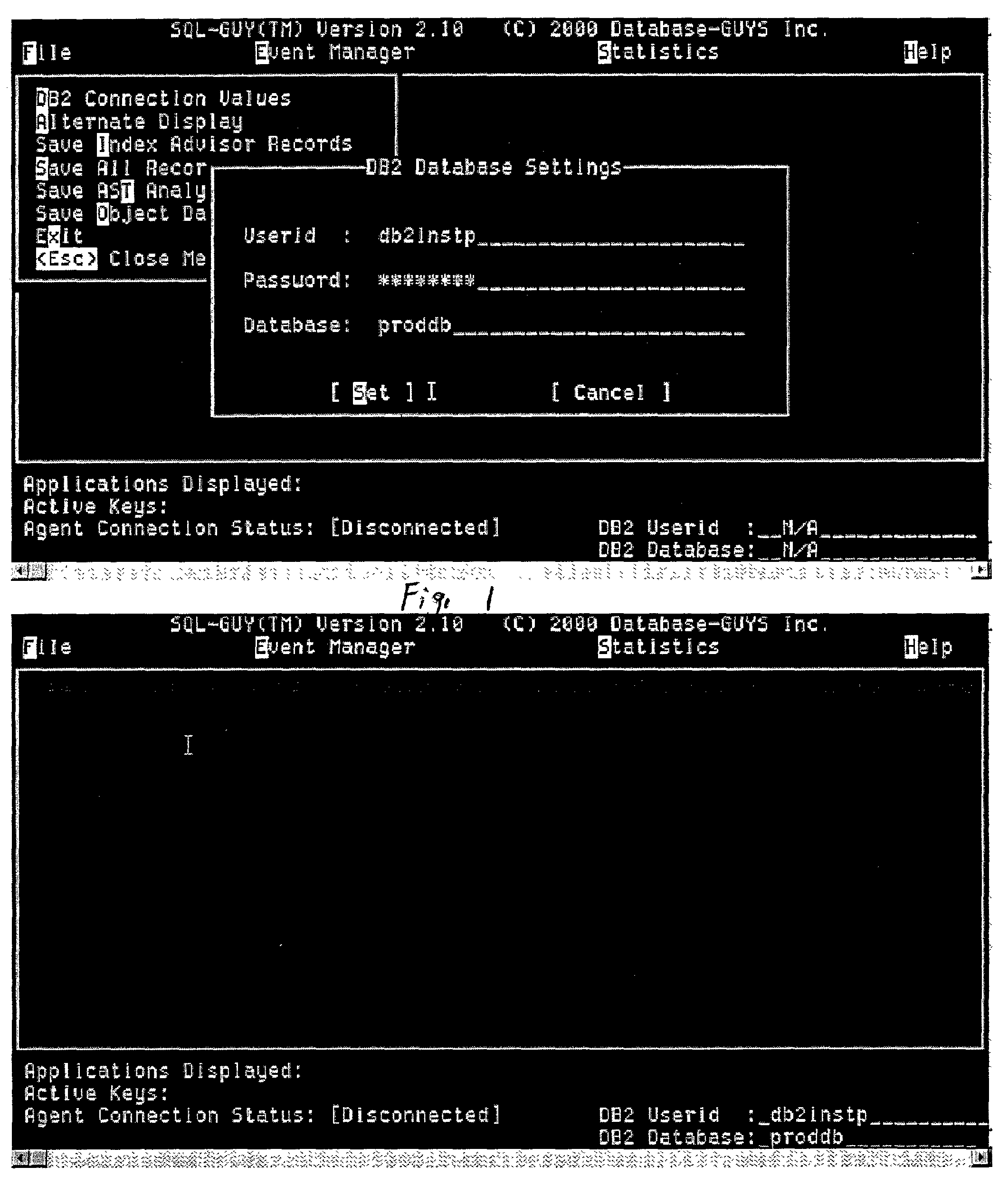
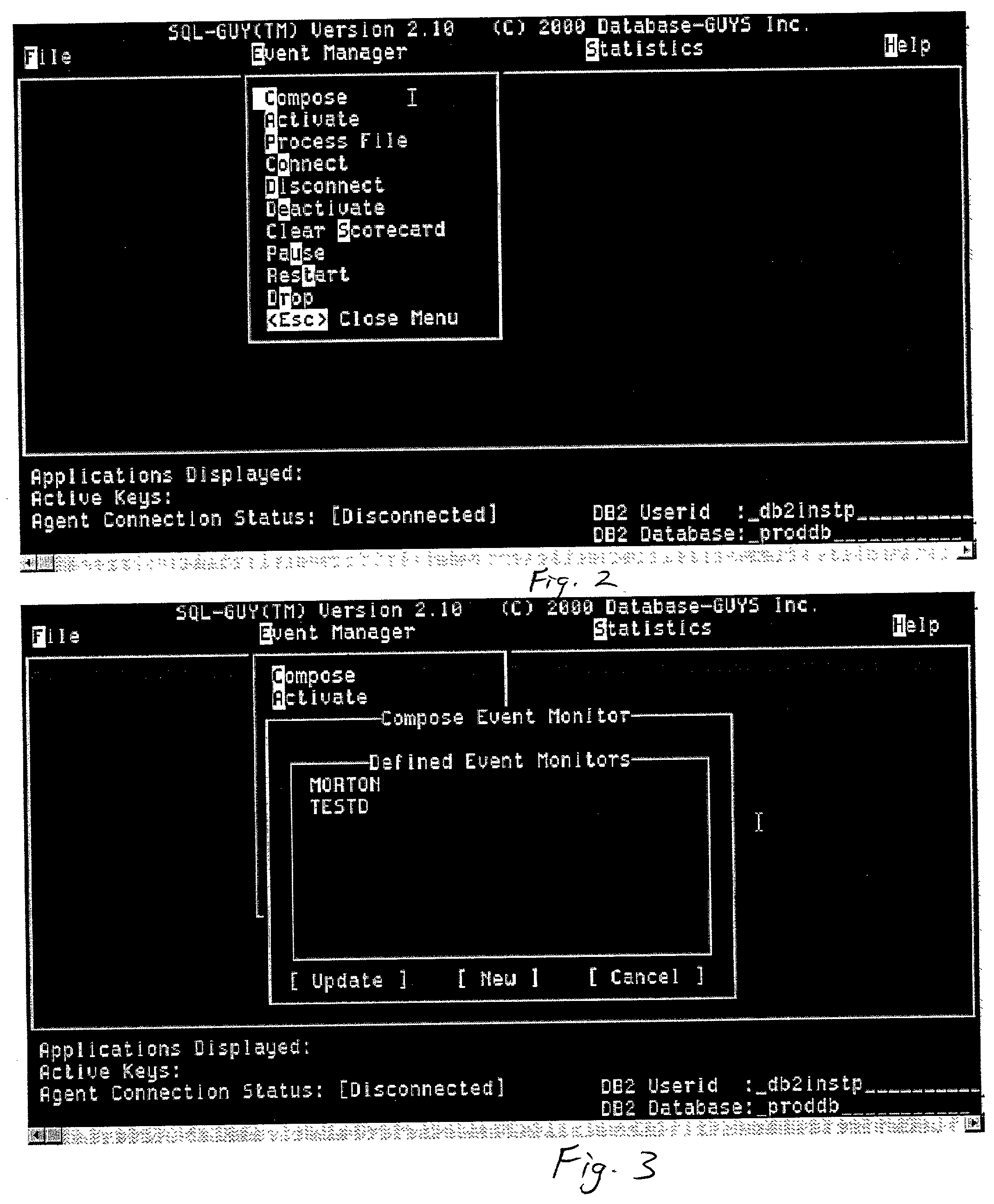
A system providing precise determination of resource use within a software system such as a database system. A user, such as a database administrator, operates a user interface to select and analyze portions of an application for resource use. In one embodiment in a DB2 database system individual SQL statement resource use can be determined. The invention is capable of uniquely identifying even dynamic SQL statements (i.e., Equalized I.D). Prediction information is presented for when a query, or other database task, will end based on selectable parameters such as optimizer cost, estimated cardinality, and delta delivery rates of data. A user can create or select event monitors to acquire statistical data on a database task. The results of activating the event monitor are presented to the user such that the user can progressively examine portions of an application, package, section and even individual statements. The user interface allows a user to efficiently and precisely identify processing shortcomings so that the performance of a database task can be improved. The interface also allows a user to sort, or otherwise organize, the statistical data so that analysis of the data is improved and maximum value is derived from the SQL cost evaluated data.
Owner:DATABASE GUYS INC +1
Database security assessment method
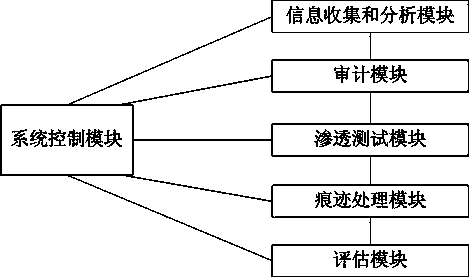
InactiveCN103473381ALow security settingsReliablePlatform integrity maintainanceSpecial data processing applicationsRisk levelData acquisition
The invention relates to a database security assessment method, belonging to the technical field of database security. In the method, the following modules are involved: (1) an information collection module, (2) an audit module, (3) a penetration testing module, (4) a trace processing module, (5) an assessment module and (6) a system control module. The system control module is implemented by the adoption of a programmable controller, is connected with other modules, and controls the operation and the data acquisition of each module. By the database security assessment method, a database security assessment report with reliability and security can be provided aiming at the problem that commercial vulnerability scanning tools hide test results in practical application, the current vulnerability risk level of the database is emphasized, the current security problems of the database are learnt by a database administrator intuitively, a security policy is completed, and security risks are lowered.
Owner:福州宇科信息技术有限公司
Abstraction based audit and security log model for increased role and security enforcement
ActiveUS20090019092A1Increased roleIncreased security enforcementDigital data processing detailsComputer security arrangementsMedical recordDatabase administrator
Embodiments of the invention store log event records in a secure database log by encrypting information in a query, or in query results, that would otherwise be subject to unwanted disclosure (either from within or without a given organization). For example, an organization (e.g., a research institution) may allow a database administrator to review log event records to diagnose and correct system performance issues, without being forced to trust the administrator with sensitive medical data (e.g., medical records related to participants in a research study). Thus, the security of sensitive information may be maintained, while at the same time, the database administrator may still access the information needed to maintain a working system.
Owner:SERVICENOW INC
Method for restoring data table content deleted mistakenly
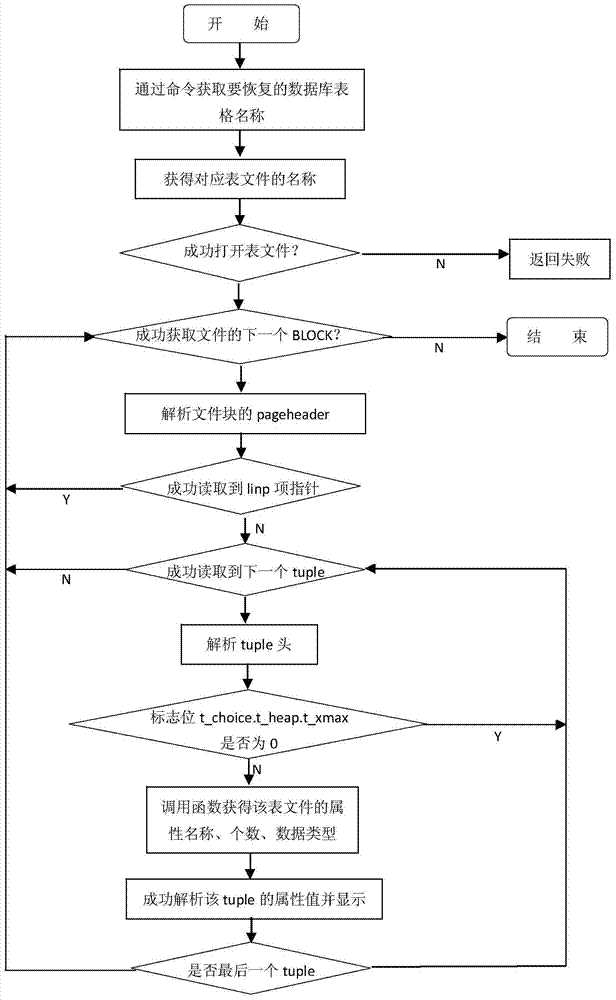
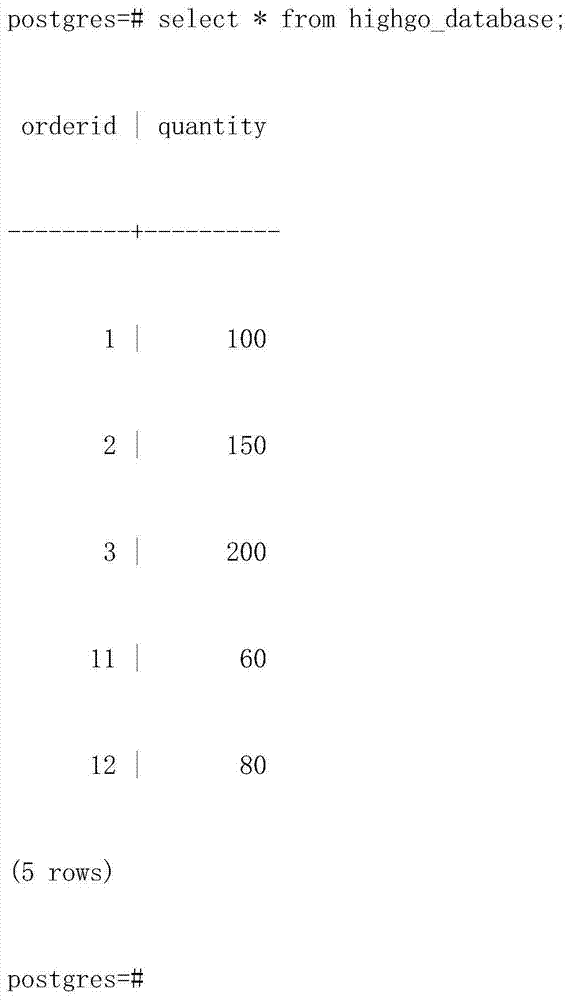
InactiveCN103617277ASave storage spaceShorten the timeError detection/correctionSpecial data processing applicationsExternal storageComputers technology
The invention discloses a method for restoring data table content deleted mistakenly. External storage management of a database is responsible for the interaction process of the database and external storage media. Table file management is the most important part in external storage management of the database, all table files in the database correspond to only one database table, and each table file is stored in a disk in a certain structure. Meanwhile, content of the table files is stored according to certain rules. When a tuple in the database table is deleted, the database will change the corresponding marker bit in the corresponding table file. According to the method, tuple content which is deleted is restored by reading and analyzing the files of the database. The method is applied to the field of computer technologies and databases so as to protect the content of the database table and prevent the situation that due to misoperations of database administers, users and other database operation class programs, the content of the database table is deleted accidentally.
Owner:HIGHGO SOFTWARE
PostgreSQL database mass data management method and system
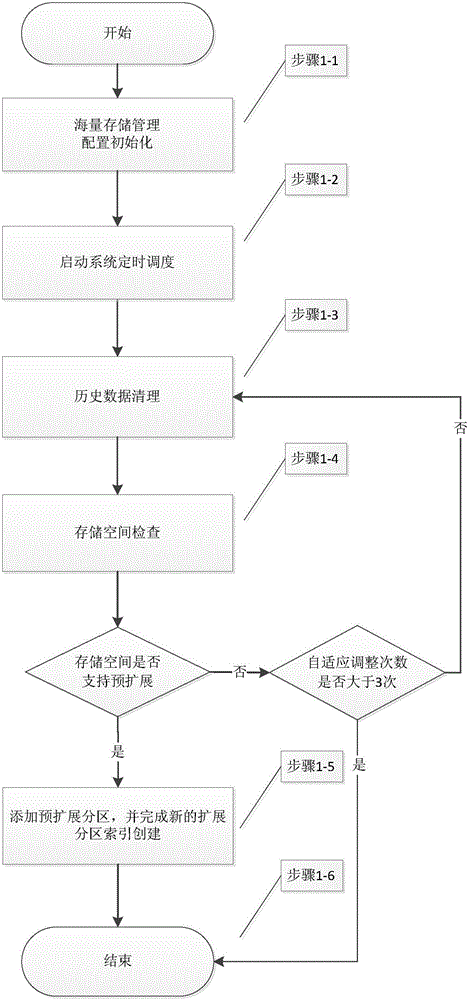
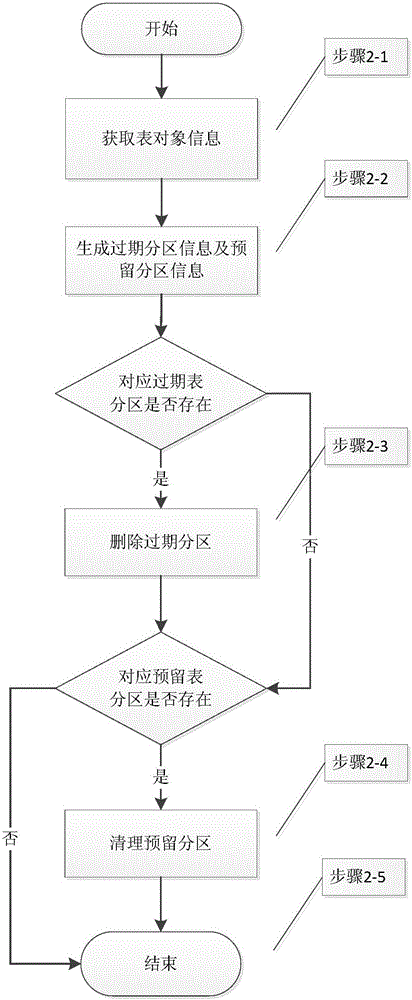
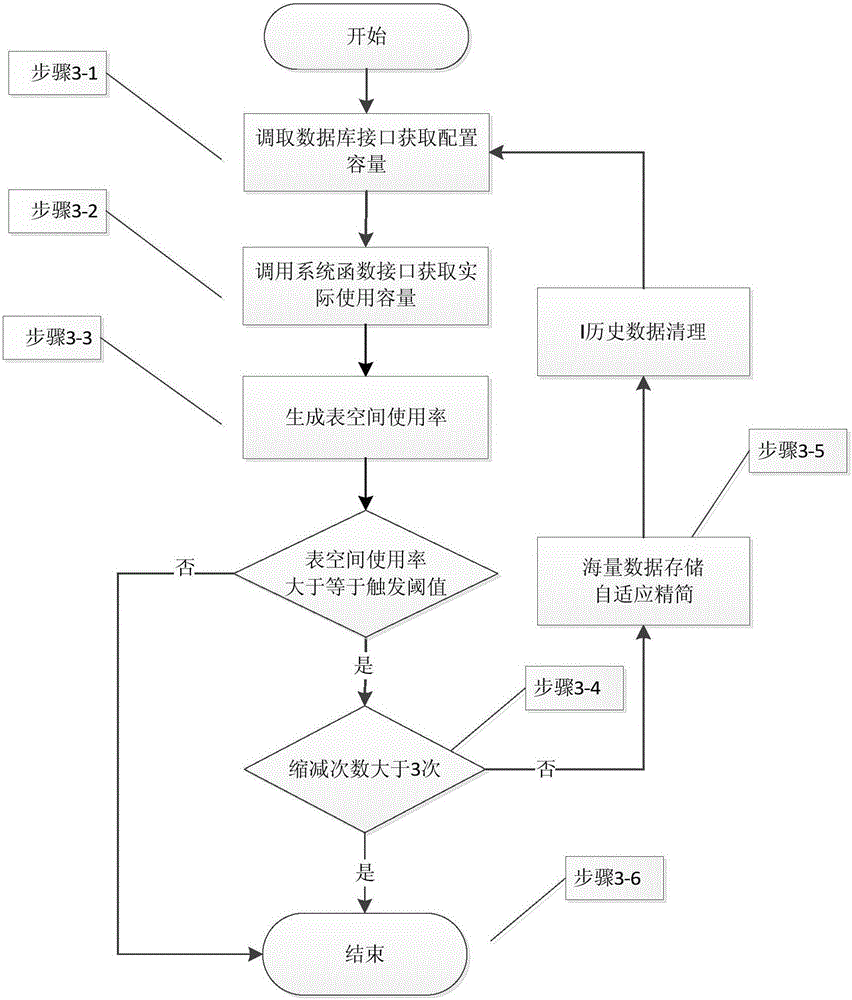
ActiveCN105893531AGuaranteed validityGuaranteed availabilityInput/output to record carriersSpecial data processing applicationsMass storagePre expansion
The invention provides a postgreSQL database mass data management method and system. The method is implemented based on a Linux platform and includes the steps that mass storage management configuration initialization is performed, and system timing scheduling is started; stale data partitions beyond a reserved time quantum are deleted, and then partition data, within a reserved time quantum and beyond an actual storage cycle, in non-stale data partitions is cleared away; storage space checking is performed, whether a storage space supports pre-expansion or not is judged, if yes, partition pre-expansion operation and index establishment are performed, and otherwise, an adaptive simplification mechanism is triggered. According to the postgreSQL database mass data management method and system, the validity, availability and expandability of data are guaranteed, a numerical basis is provided for data expansion, the maintenance efficiency of database administrators is effectively improved, the database management and maintenance cost is greatly reduced, and the postgreSQL database mass data management method and system have significant market value.
Owner:WUHAN HONGXIN TECH SERVICE CO LTD
Method and system for dynamic security checking of heterogeneous database environments
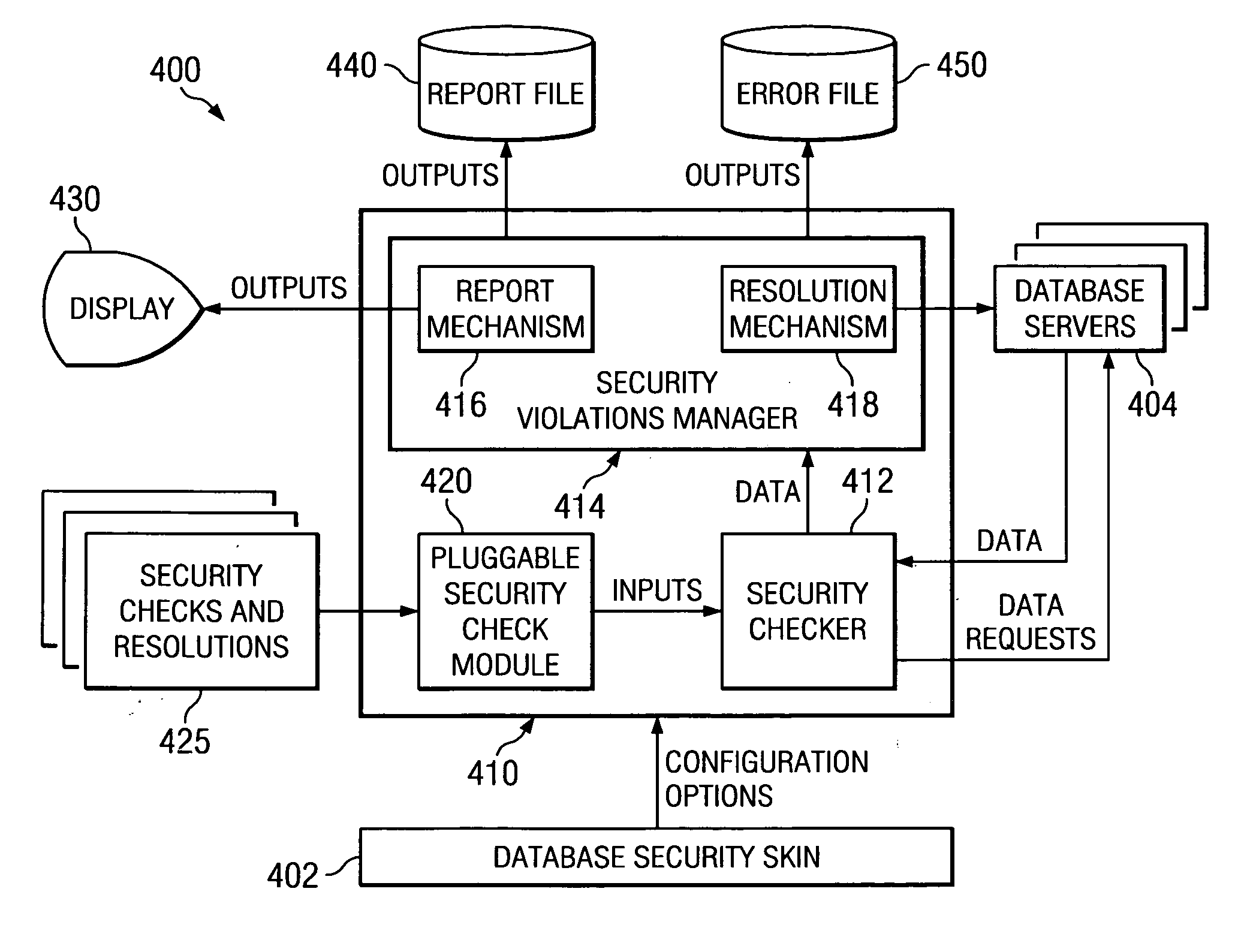
InactiveUS20050268117A1User identity/authority verificationUnauthorized memory use protectionError reportingSecurity check
A database skin allows a database administrator to configure which security checks are to be implemented, the frequency with which the security checks are to be executed, the look and feel of the output, how security violations are to be resolved, where reports are to be sent, details of each security check as it is executed, statistics or metrics to be collected, and the like. A security checker is pre-loaded with security checks that always need to be executed for databases. Pluggable security check modules may also be used. A security violations manager includes a report mechanism for reporting security violations and a resolution mechanism for resolving security violations, if possible or if instructed by the database skin. The security violations manager reports errors to an error file and sends data to be reported to a report file.
Owner:IBM CORP
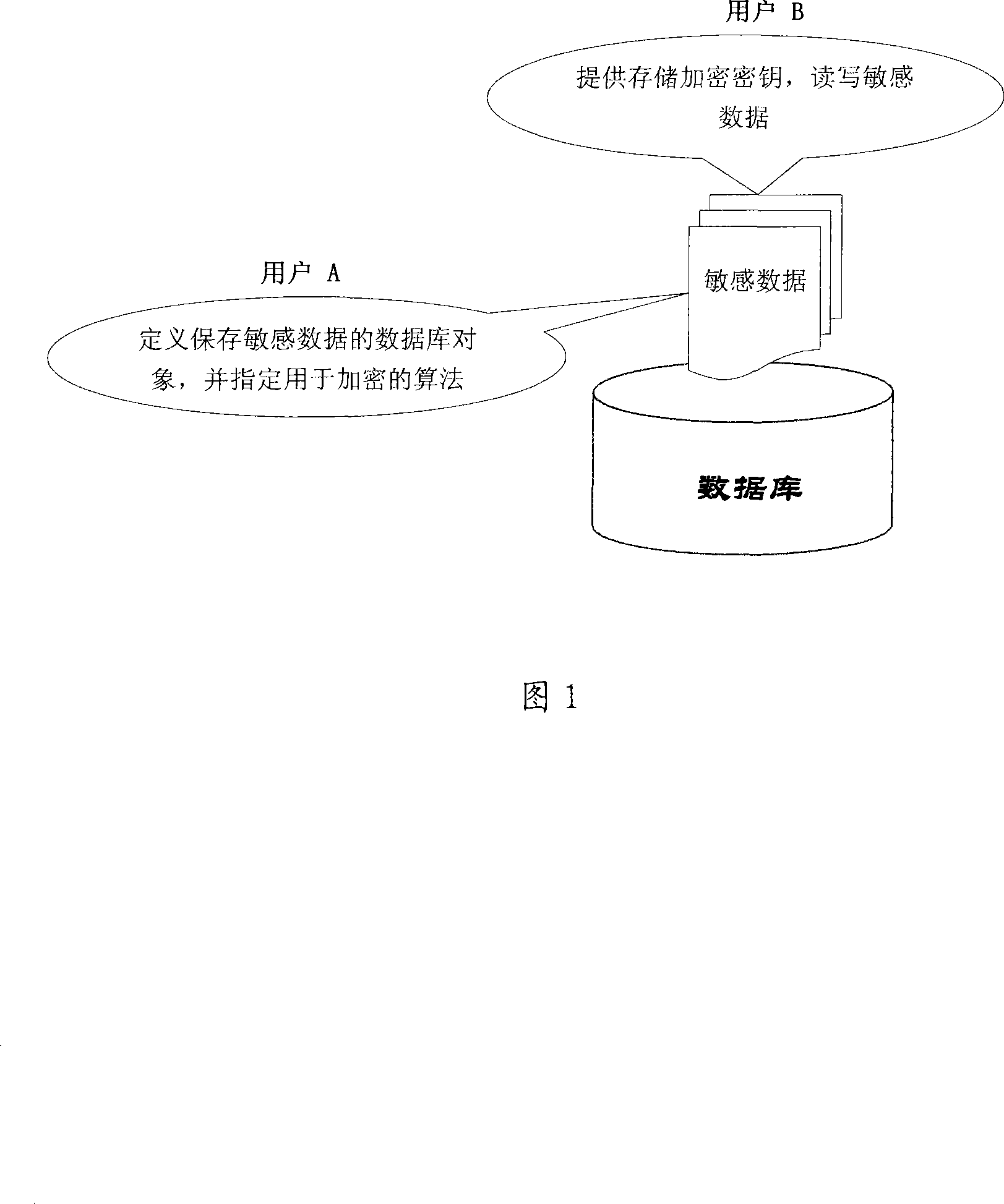
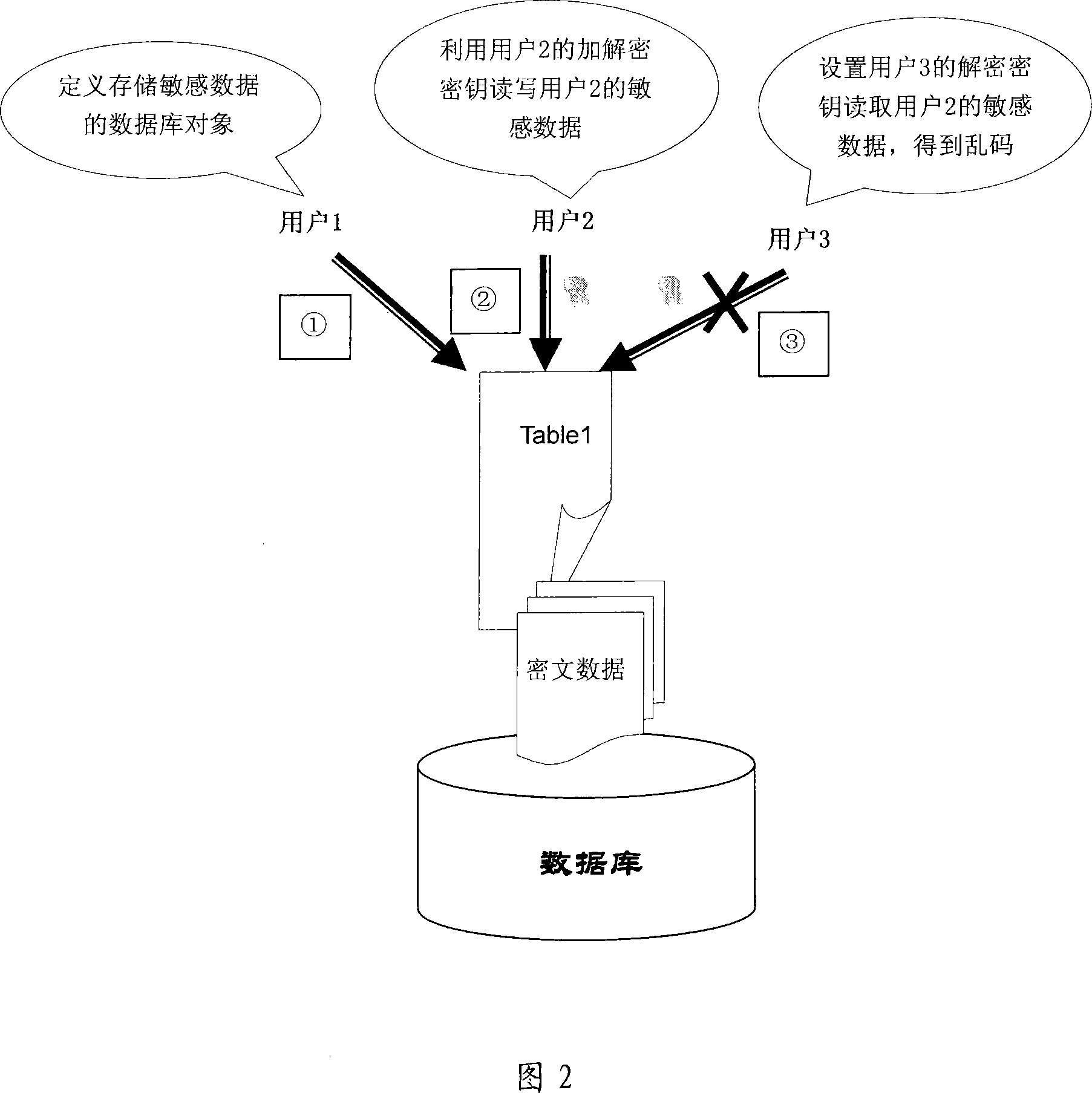
Data-base storage ciphering method based on conversation
InactiveCN101183419AData type is not limitedFlexible useDigital data protectionSpecial data processing applicationsComputer hardwareRelevant information
The invention relates to a data base memory encryption method based on conversation, which adopts the following methods: relative information of encryption algorithm is linked with an encrypted object, which is preset by a database administrator in advance; secret key is linked with information of users, which is preset by users in advance; relative information of encryption algorithm and the secret key are respective stored and are combined for used when encryption and decryption are needed for the encrypted object. Due to respectively storing of relative information of encryption algorithm and the secret key and the combination used when encryption and decryption are needed for the encrypted object, the invention can adopt different encryption algorithm for different encrypted object, thereby flexibly using without changing existing application system. The invention has the advantages of very good transplantation, ability to protect private sensitive data of users and no limit for data type of the encrypted object..
Owner:WUHAN DAMENG DATABASE
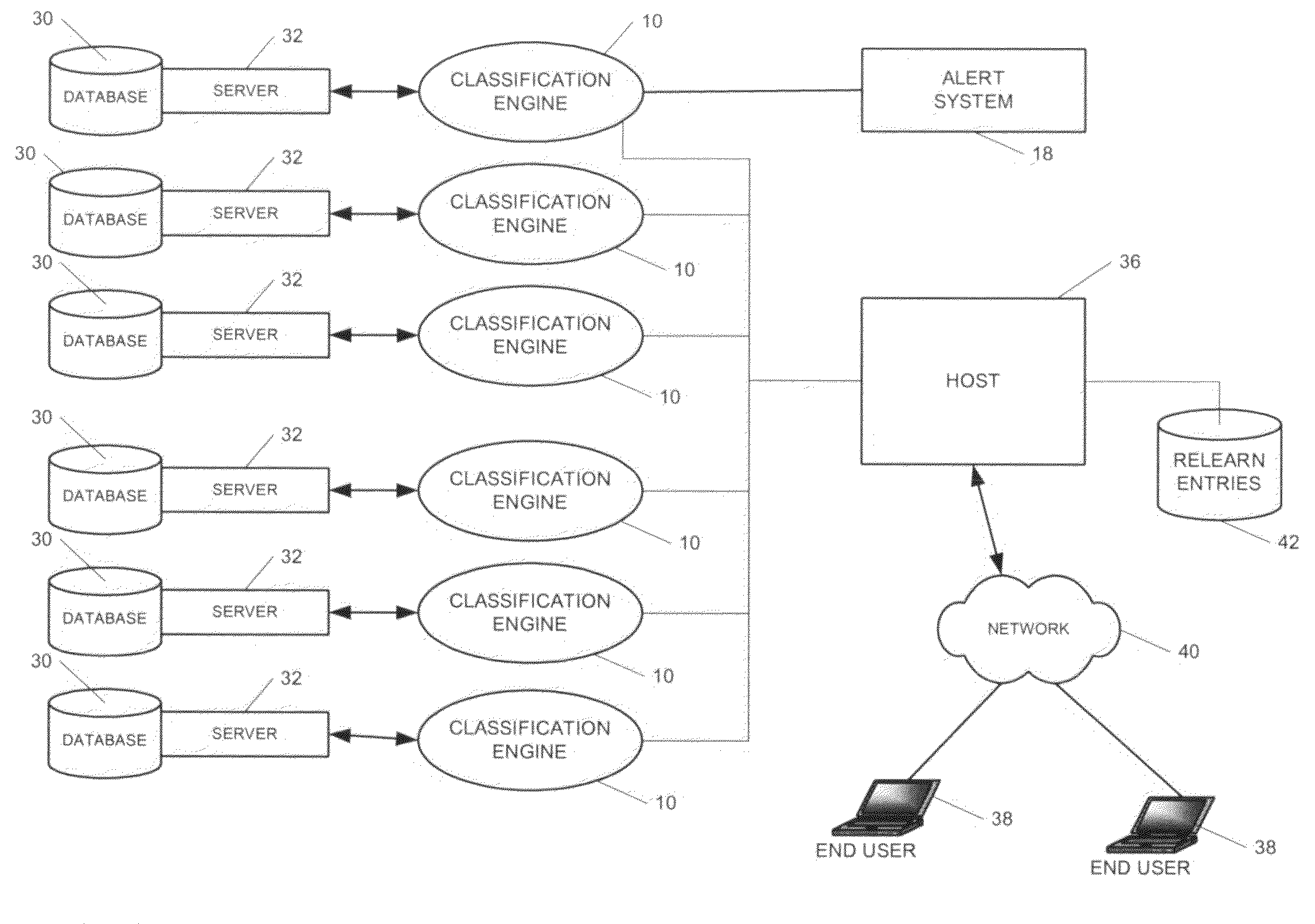
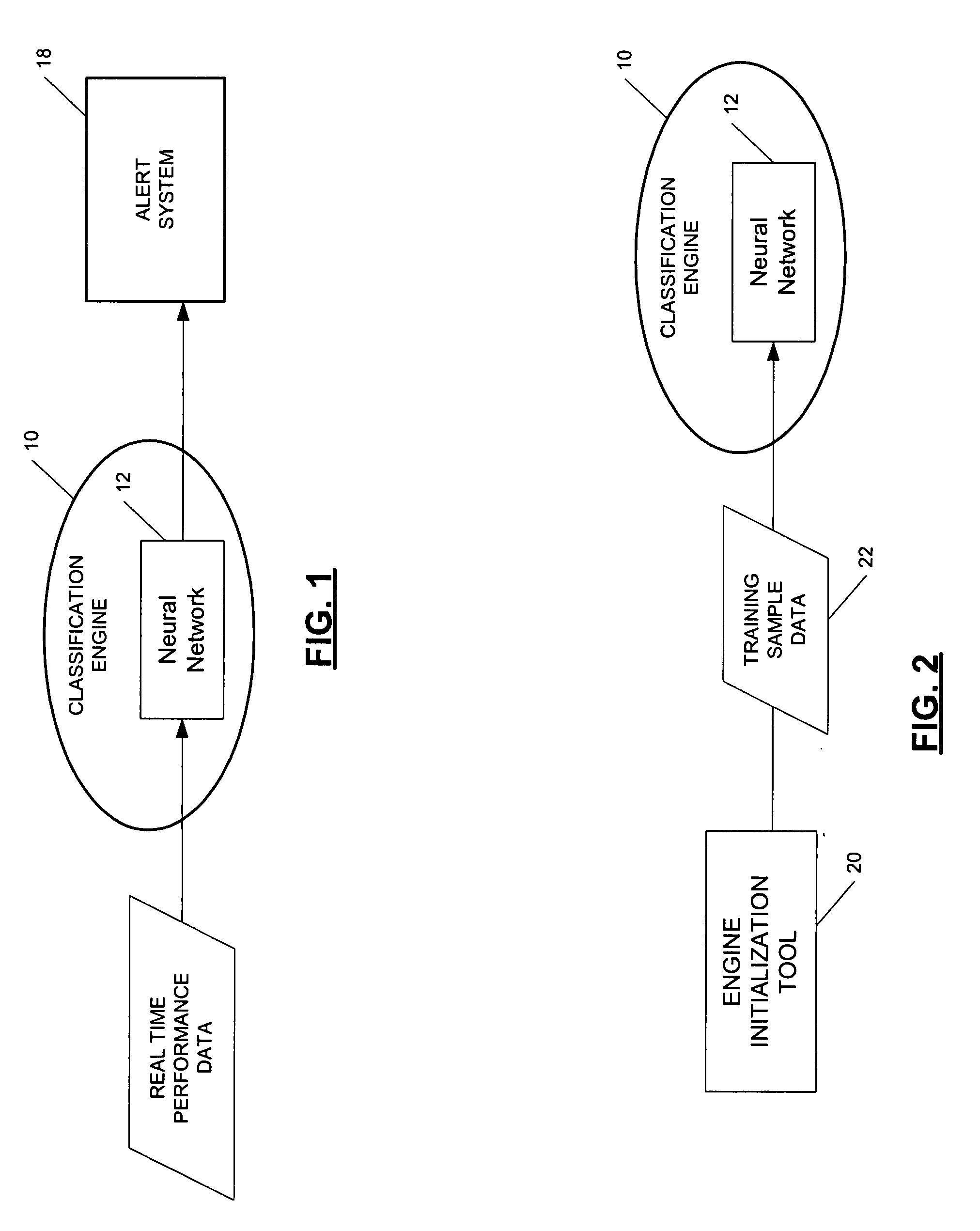
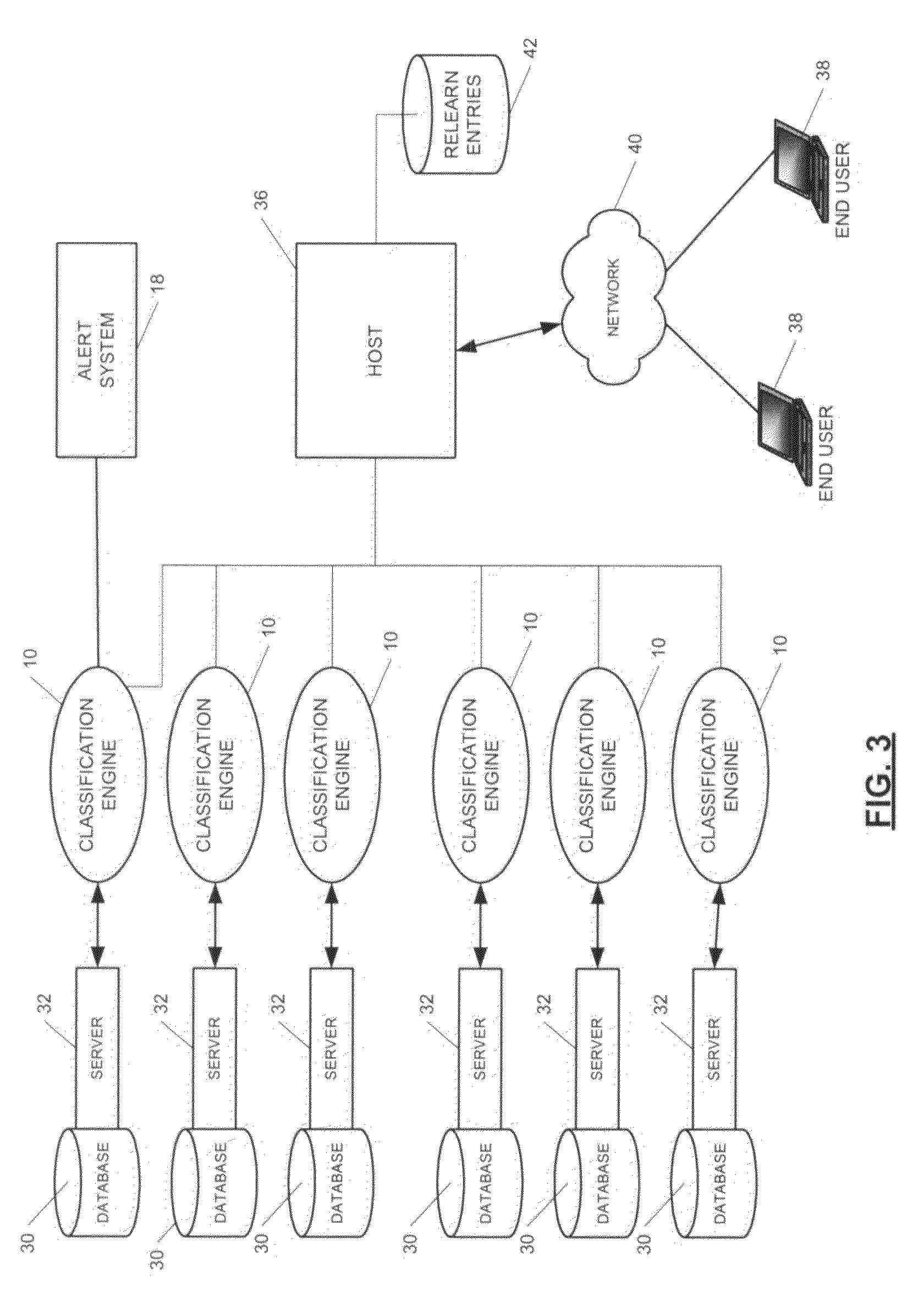
Adaptive database management and monitoring
Systems and methods for adaptive database management and monitoring are disclosed. According to various embodiments, the present invention comprises training a neural network of a classification engine with real time performance data of a database. Once the neural network has been trained, real time performance data for the database may be input to the classification engine. If the classification engine detects a deviation in performance, it may cause an alert to be sent to a database administrator. In addition, the classification engine may send results of its analysis to a host, which posts the results on a web page. Users may provide feedback on the results to a batch relearn entries database or file. The classification may read the batch relearn entries to use in a backpropogation algorithm to update / retrain the neural network of the classification engine.
Owner:MORGAN STANLEY
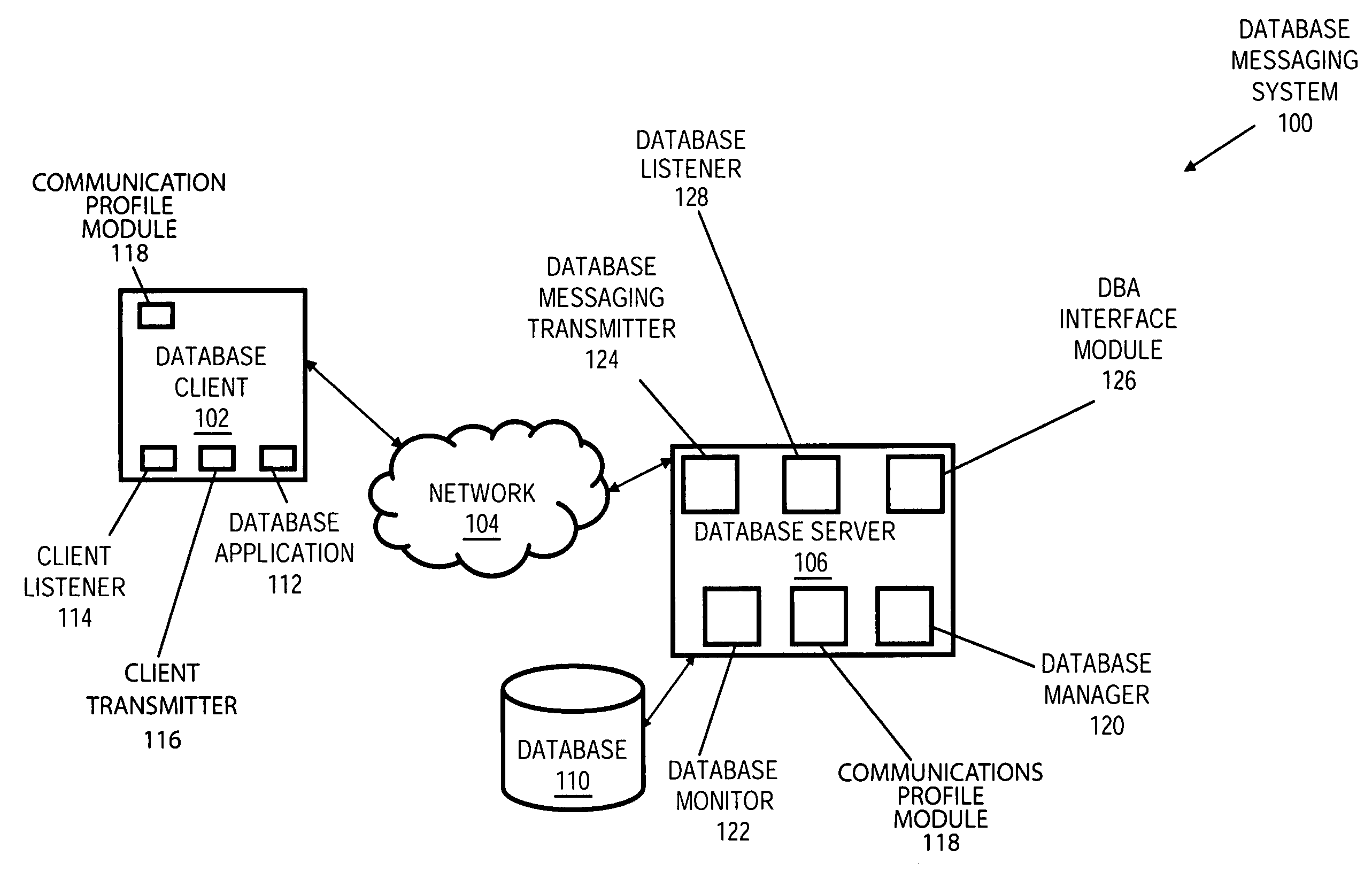
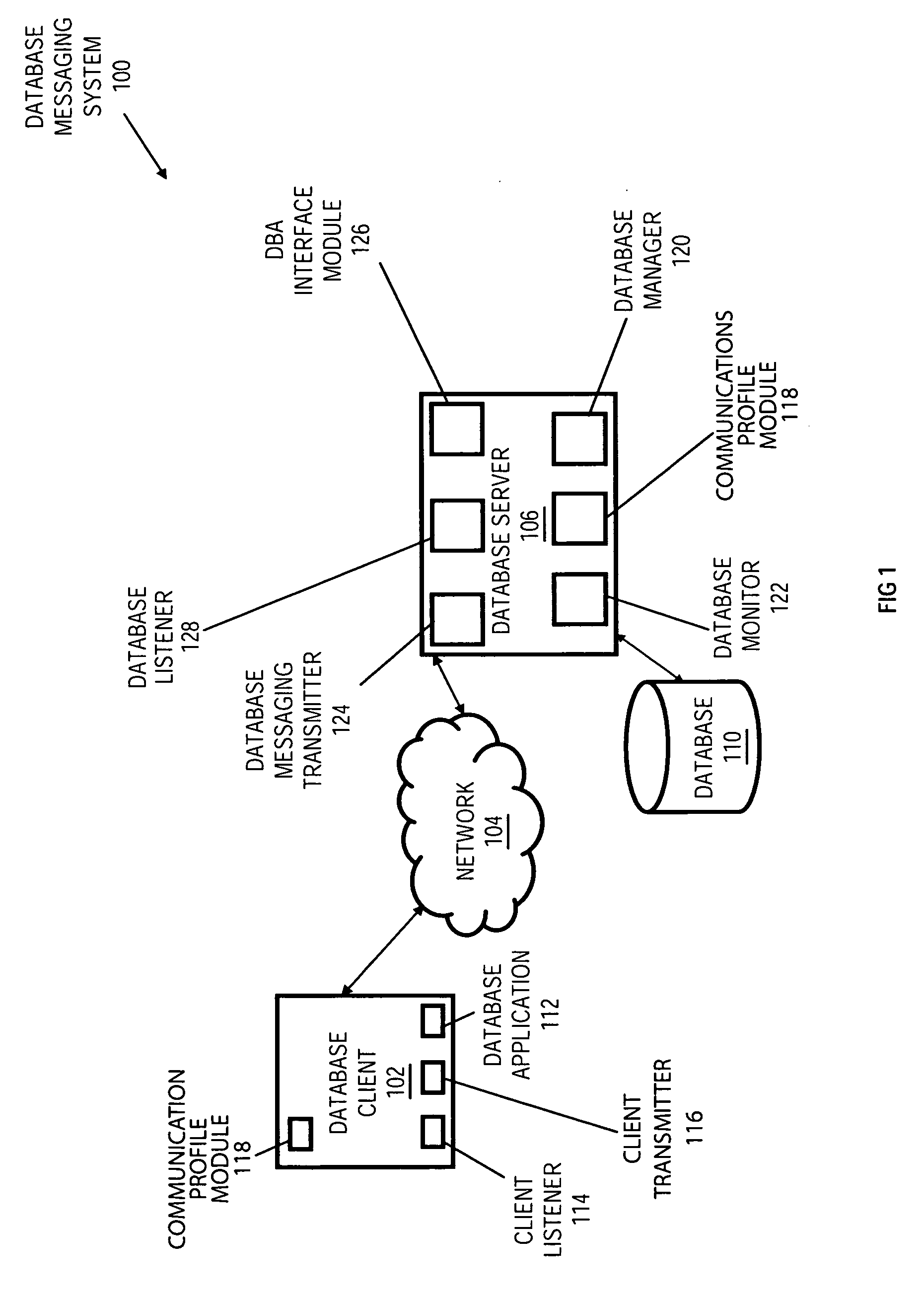
Communication profiles for integrated database messaging system
InactiveUS20070174477A1Multiple digital computer combinationsTransmissionIntegrated databaseMessage delivery
Systems, methods and media for providing communication profiles for an integrated database messaging system are disclosed. Embodiments of the method may include receiving from a user of the database messaging system a request for one or more profiles and determining one or more profiles associated based on the attributes of each profile request by accessing a profile database. The one or more profiles may include an indication of a user of the database messaging system and an Internet Protocol (IP) address. Embodiments may also include providing the one or more determined profiles to the requesting user. Further embodiments may include receiving an indication of one or more changes to the profile database and modifying the profile database. The user may include a database administrator (DBA) or user of a database. Each profile may contain personal, organizational, contact, group or other types of information.
Owner:IBM CORP
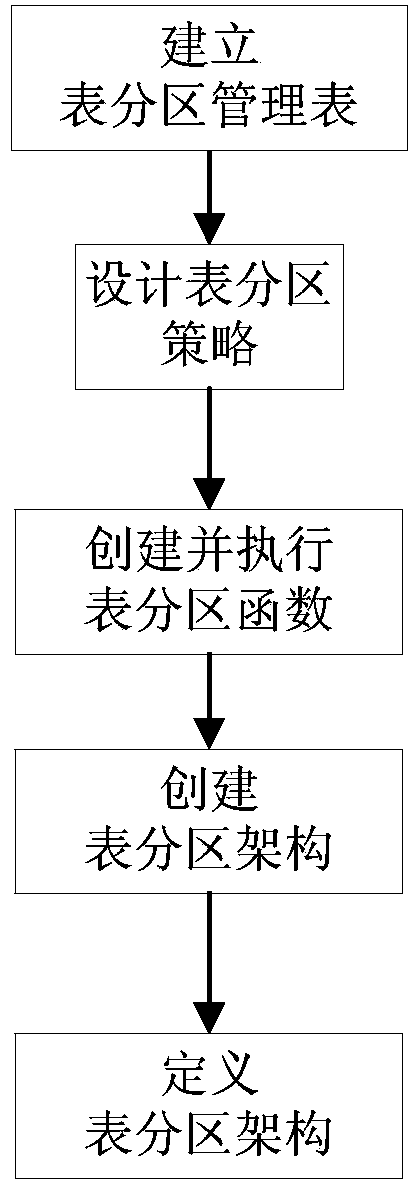
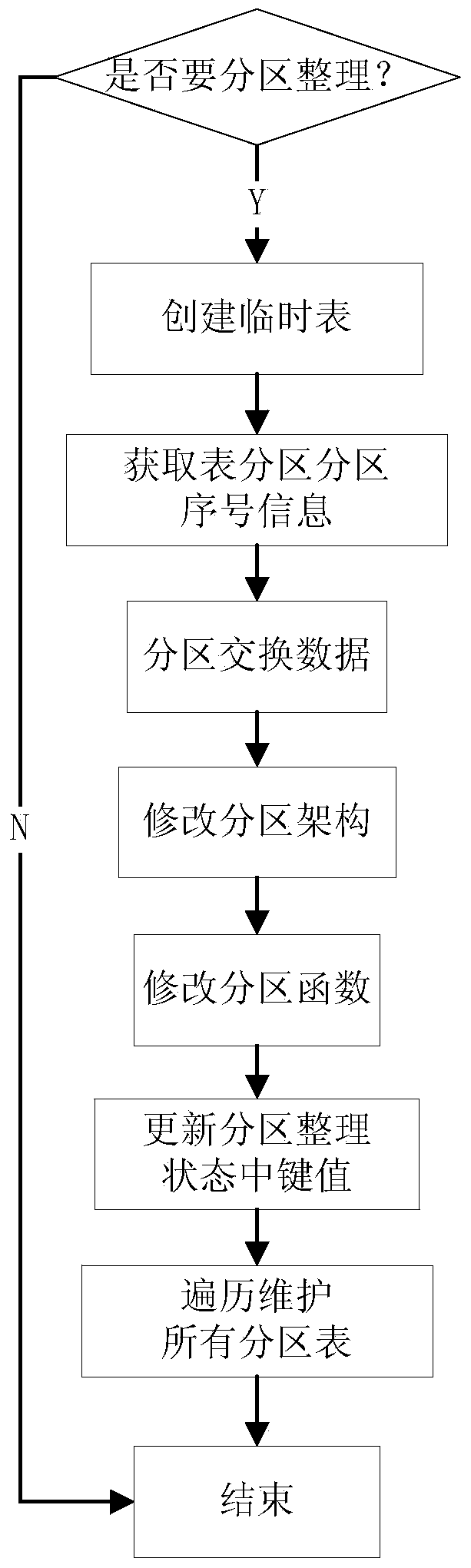
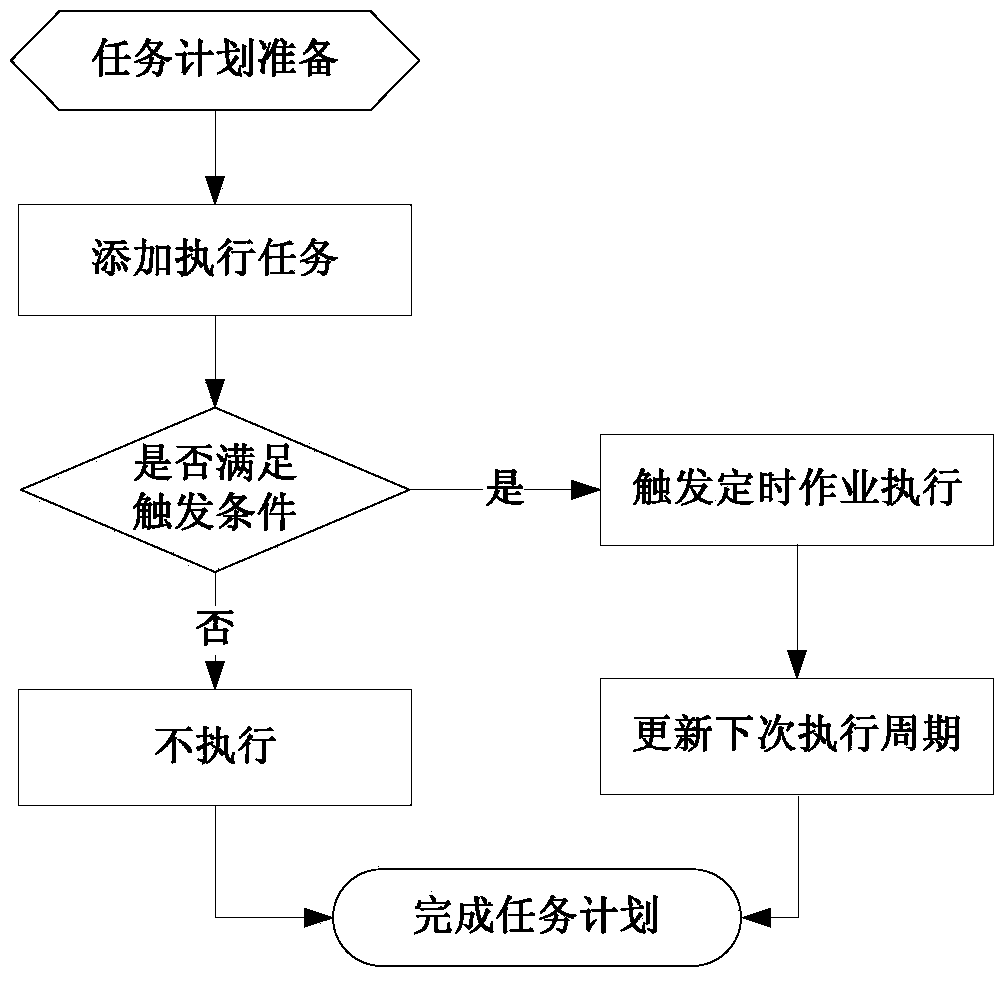
MSSQL SERVER based table partition and automatic maintenance method and system
ActiveCN103699676AImprove Storage Spaces PerformanceReduce workloadSpecial data processing applicationsData needsWorkload
The invention provides an MSSQL SERVER based table partition and automatic maintenance method and system. When tables are created, the same class of tables refer to data retention strategies and a same partition function, a partition framework and structural definitions are configured, and further when maintenance is needed, functions of automatic dumping of historical data of MSSQL server table partitions, automatic addition of new partitions, automatic merging of data-dumped old partitions, duty-cycle operation of file groups and the like are realized according to the data retention strategies made in advance; data needed by set services in the data retention strategies are retained, and stale data are deleted or dumped, so that the purposes for automatically maintaining a large amount of partitioned tables and maintaining forms of a database by itself are achieved, storage space performance of the database is improved effectively, and workload of a dba (database administrator) is relieved greatly so as to enable the dba to concentrate more energy on other critical fields.
Owner:XIAMEN MEIYA PICO INFORMATION
Authentication of user database access
InactiveUS20100043054A1Solve the quick installationEasy maintenanceDigital data processing detailsUser identity/authority verificationOperational systemSecure authentication
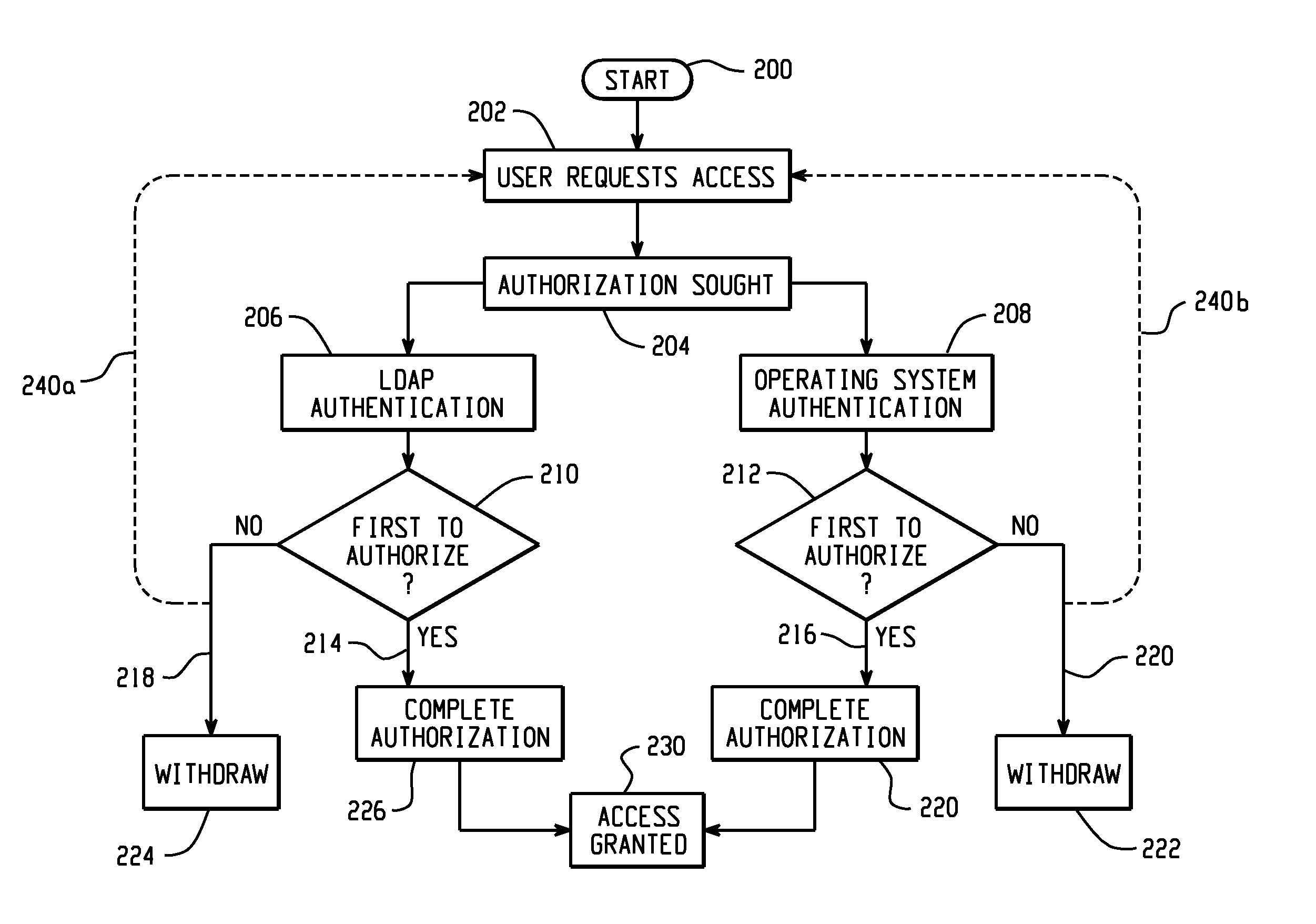
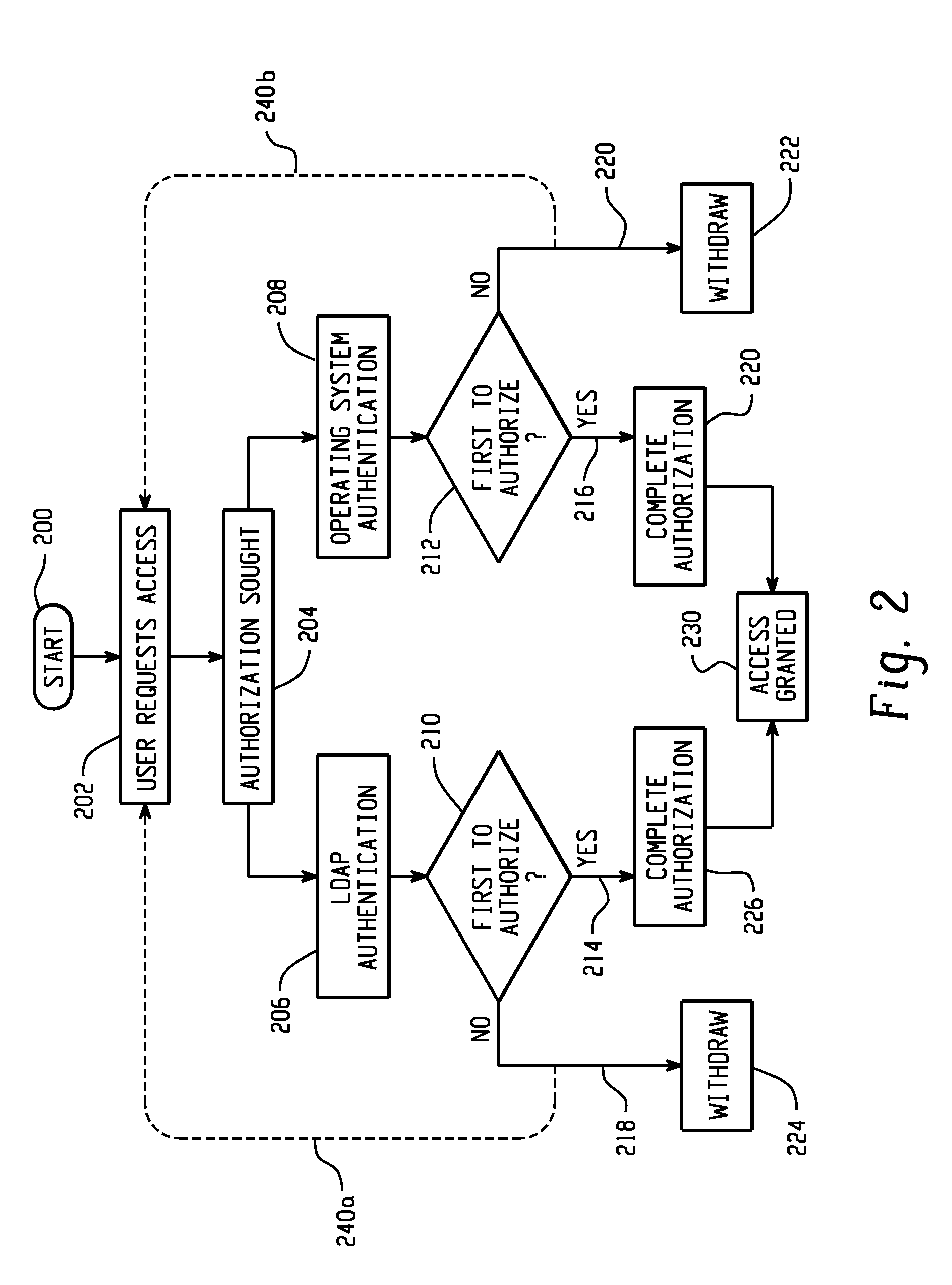
A database system and method combines the ability to concurrently utilize LDAP based authentication and operating system-based authentication. The database authentication tries both methods of authentication, both at the database layer and at the application layer. Security authentication of the user then occurs by whichever mechanism is first to return a successful result. Database administrators can, if desired, configure the system to prefer one mechanism (LDAP or operating system) over the other. With the present invention, a large end user population can be managed using standard LDAP tools, in an automated, administered, or “self-service” manner, as preferred. Thus, system accounts, such as the database owner, can remain within the operating system, easing installation and maintenance of the database product itself.
Owner:IBM CORP
Self-service database reporting systems and methods
InactiveUS20140244627A1Digital data processing detailsWebsite content managementDashboardConfiguration item
Users interactively create, customize, and execute reports on data stored in databases using only a web browser. The user can create, customize, and execute reports by selecting various report elements including, for example, data sources, fields, filters, labels, charts, dashboards, and the like. Advantageously, the present disclosure enables users to create the reports through an Internet connection, without any special software, such as web browser plug-ins, database applications, and the like, without knowledge of data access languages, such as SQL, and without direct access to a database server. The present disclosure can directly connect to a plurality of different database types through a virtual or physical network connection. It fully functions without requiring the creation of additional configuration items like catalogs, models or secondary schemas by a programmer or database administrator (DBA).
Owner:IZENDA
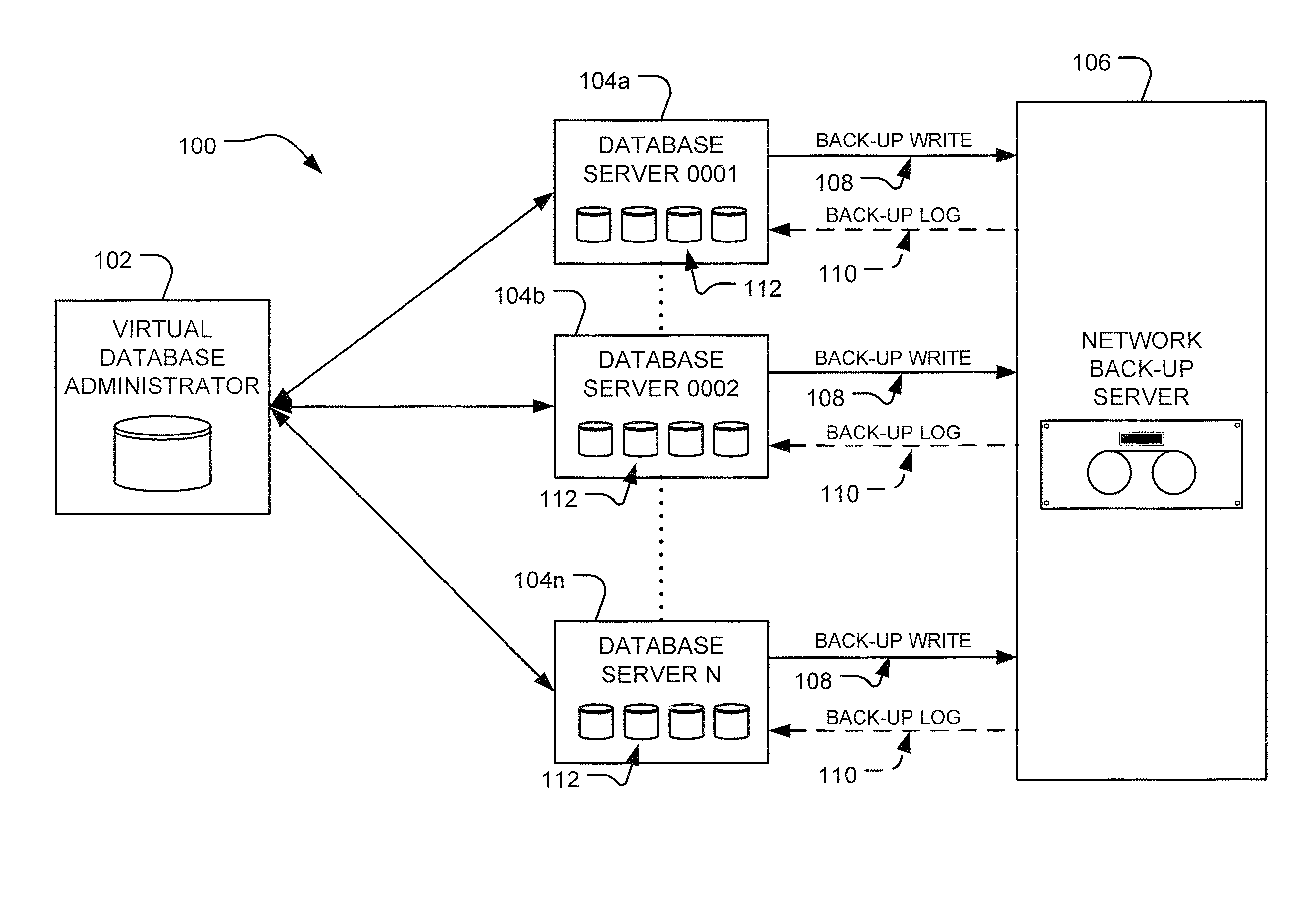
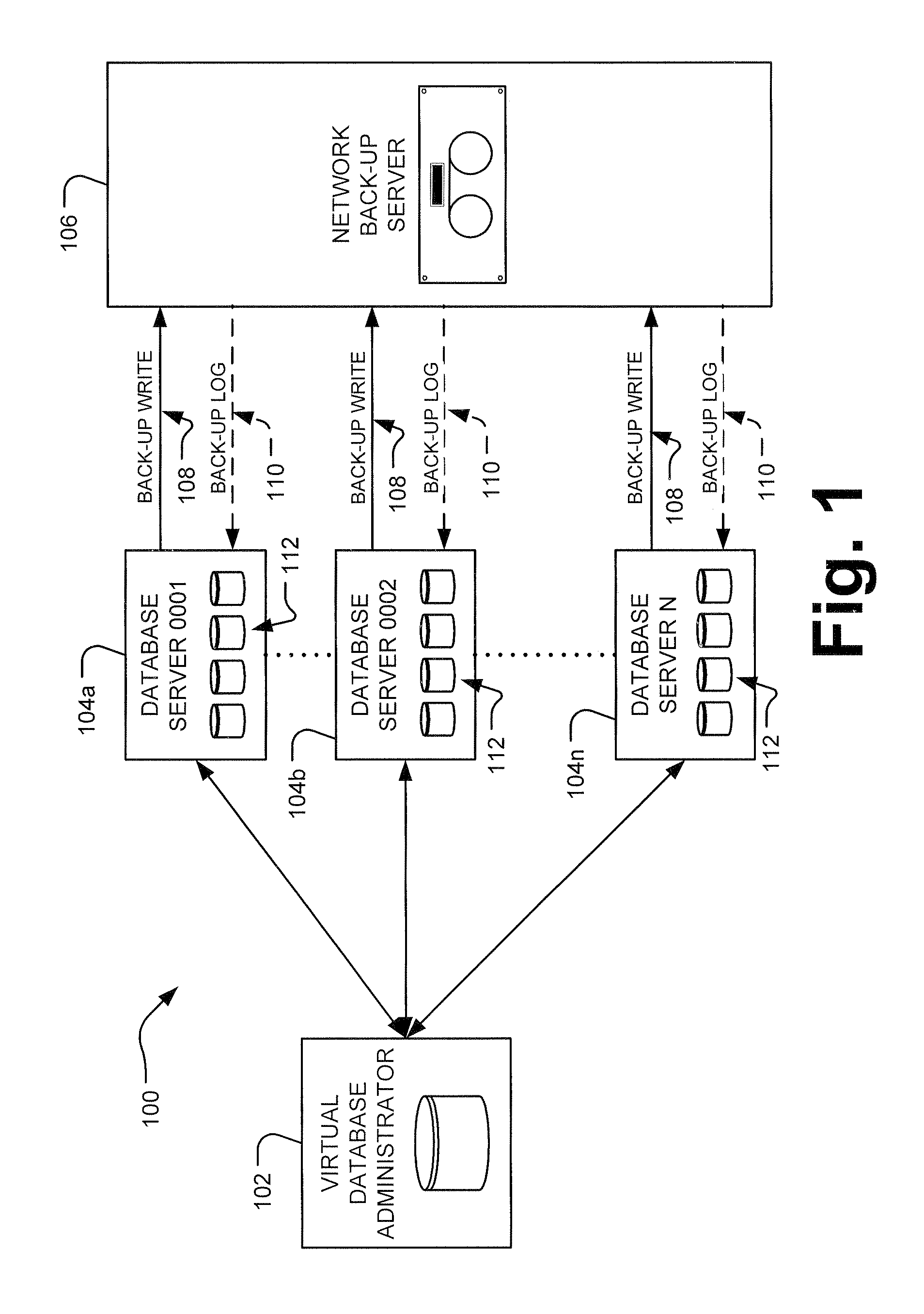
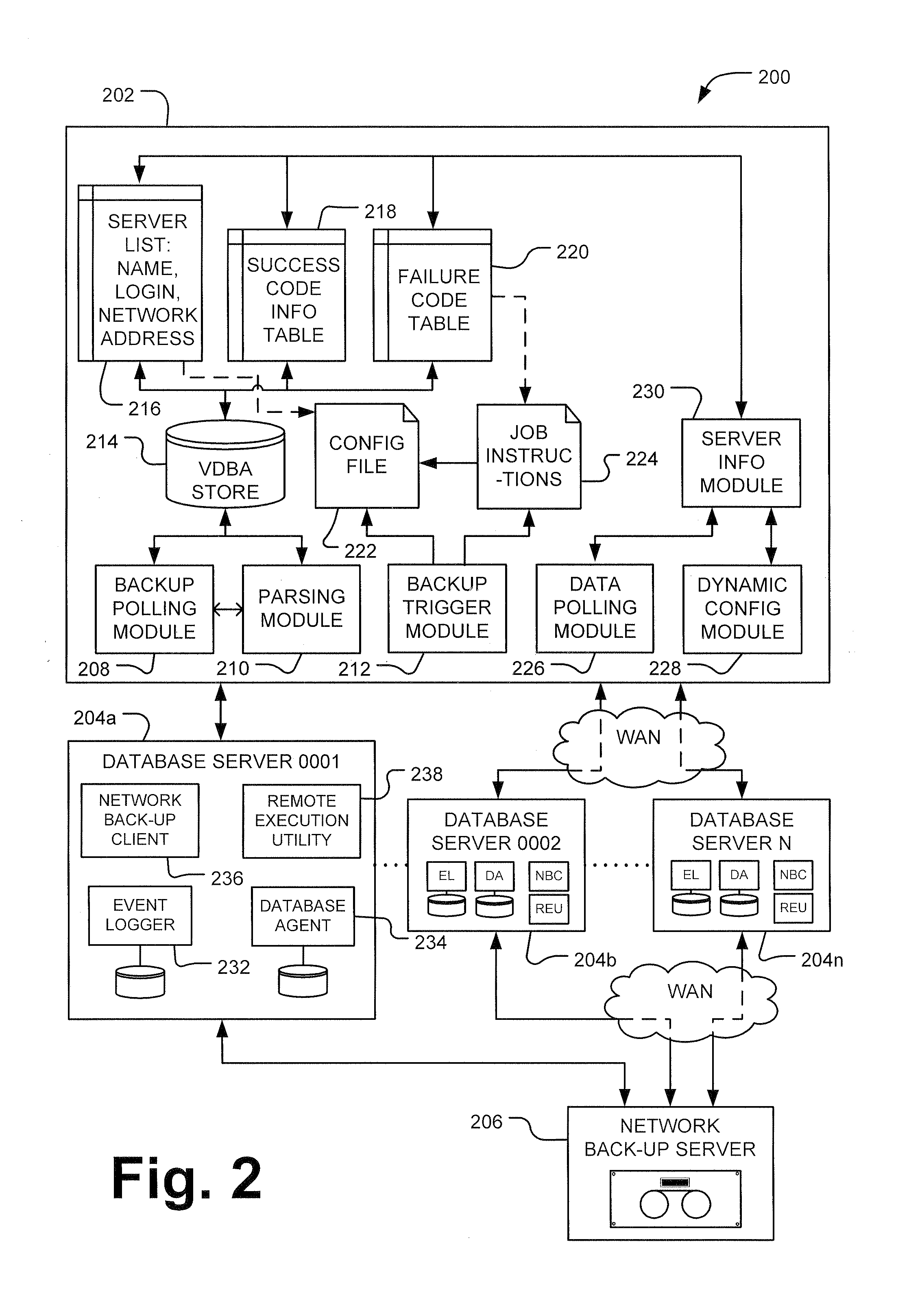
Virtual database administrator
ActiveUS20090172044A1Save network resourcesStructured data retrievalSpecial data processing applicationsDatabase serverDatabase administrator
A virtual database administrator (VDBA) is implemented in a database server network to monitor back-up write events from the database servers on the network to a network back-up server and correct failed back-up attempts. The VDBA regularly polls the database servers for copies of event logs that include information about back-up attempts. The VDBA parses each of the event logs, searching for the back-up log entries indicating successful or failed back-up writes for particular databases. For failed back-up writes, the VDBA instructs the specific database server to retry the back-up write for the particular database. The back-up retry instructions are specific to the database server and cause a back-up retry limited to the particular database on the server that experienced the failure.
Owner:LEVEL 3 COMM LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com