Database security assessment method
A security assessment and database technology, applied in the field of database security, can solve problems such as hidden security risks and inability to understand vulnerability risk levels, and achieve the effect of reducing security risks and improving security strategies
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
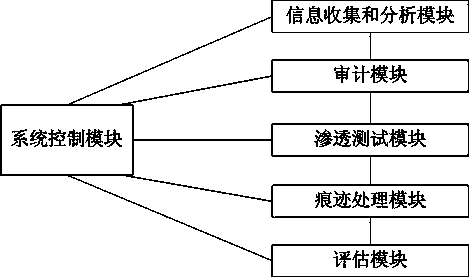
[0044] Such as figure 1 The shown database security assessment method includes an information collection and analysis module, an audit module, a penetration testing module, a trace processing module, an assessment module, and a system control module. The system control module is implemented by a programmable controller, which is connected with other modules to control the operation and data transmission of each module.
[0045] In this embodiment, the database security assessment method is divided into the following implementation steps:
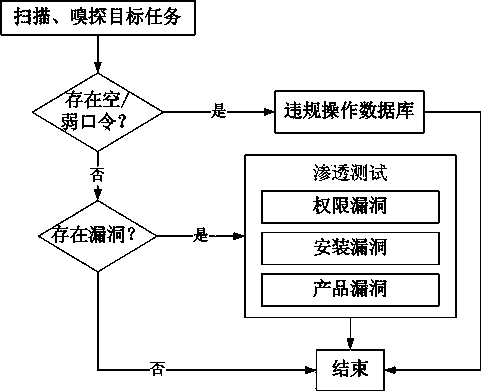
[0046] Step 1: Collect information on the target task, have a basic understanding of the target task's software and hardware environment, user settings, topology, and application conditions, and provide information for more in-depth penetration testing, and can formulate targeted penetration testing plan;
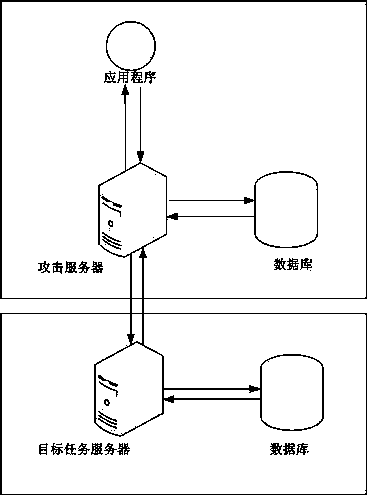
[0047] Such as figure 2 As shown, the information collection adopts the method of data synchronization between the attack server and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com