Patents
Literature
343results about How to "Take security into consideration" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
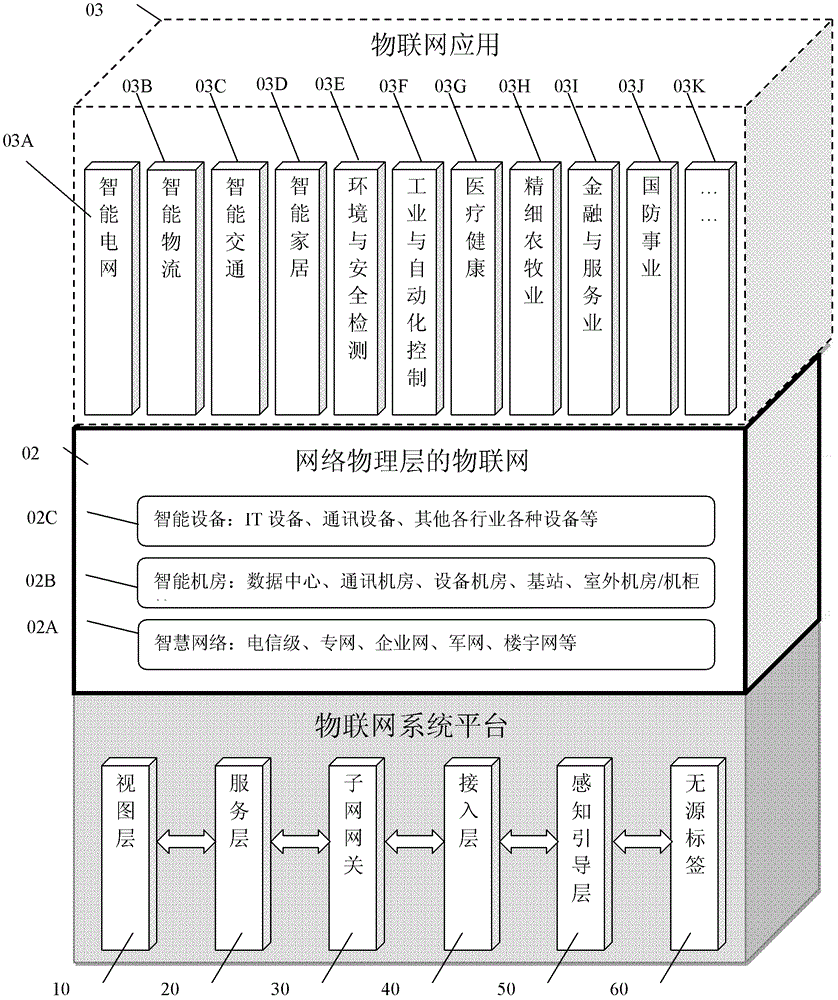
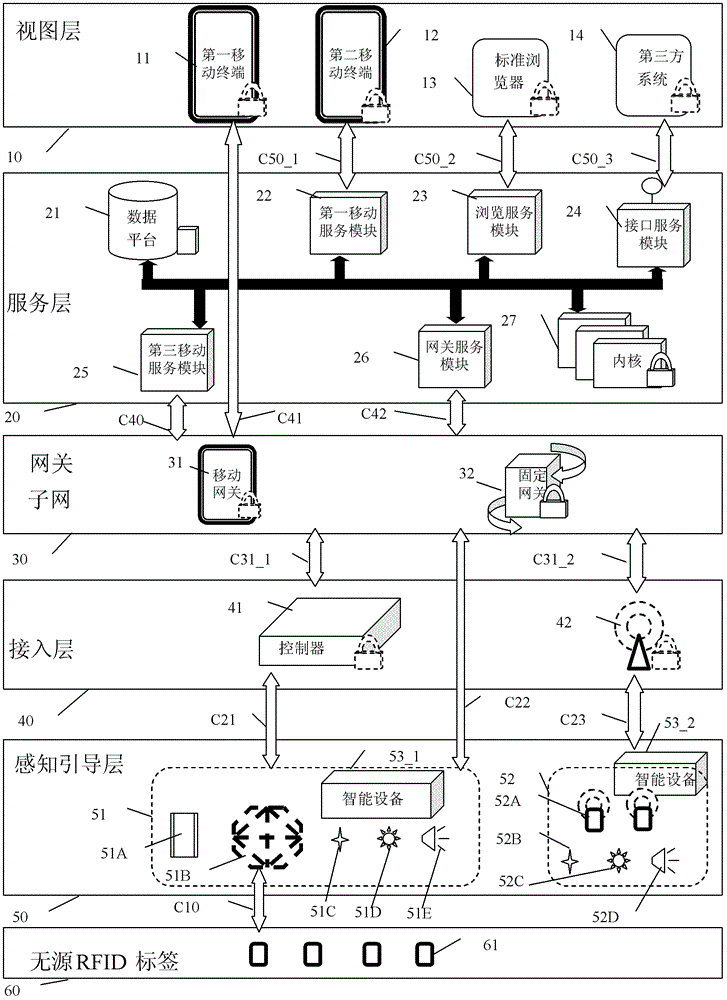
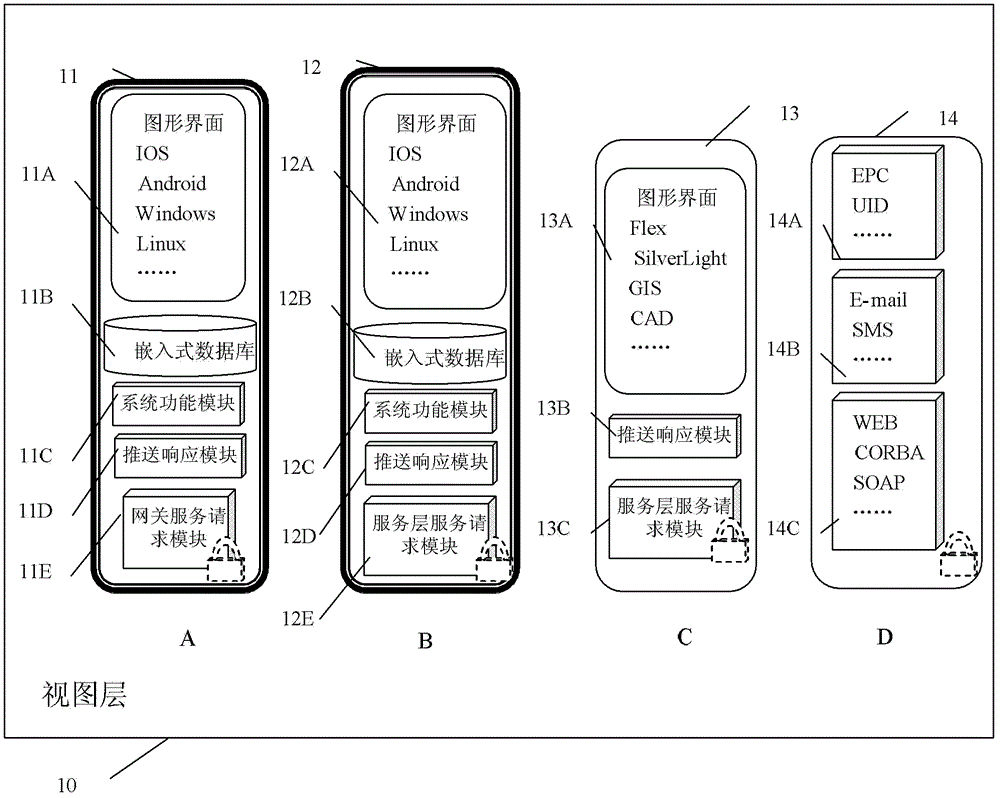
Internet of things system and acquisition and monitoring method for article information
ActiveCN102801773AEasy to set upIncrease flexibilityTransmissionSpecial data processing applicationsService layerProcessing Instruction
The invention discloses an Internet of things system and an acquisition and monitoring method for article information. The system comprises perception guiding equipment, a sub-network gateway, service layer equipment and view layer equipment, wherein the perception guiding layer equipment is used for controlling a monitored object of the Internet of things according to an instruction, acquiring data information and uploading the data information to the sub-network gateway; the sub-network gateway is used for processing the instruction, and performing the interaction of the data information interaction through a network and the service layer equipment; the service layer equipment is used for processing the instruction and the data information according to the service type of Internet of things application and preset configuration, and transmitting the processed data information to the view layer equipment; and the view layer equipment is used for requesting data to the service layer equipment and receiving the data of a service layer for display. By the system and the method, network Internet of things application and the Internet of things application of other industries can be extended.
Owner:SHANGHAI GOKEI INFORMATION TECH
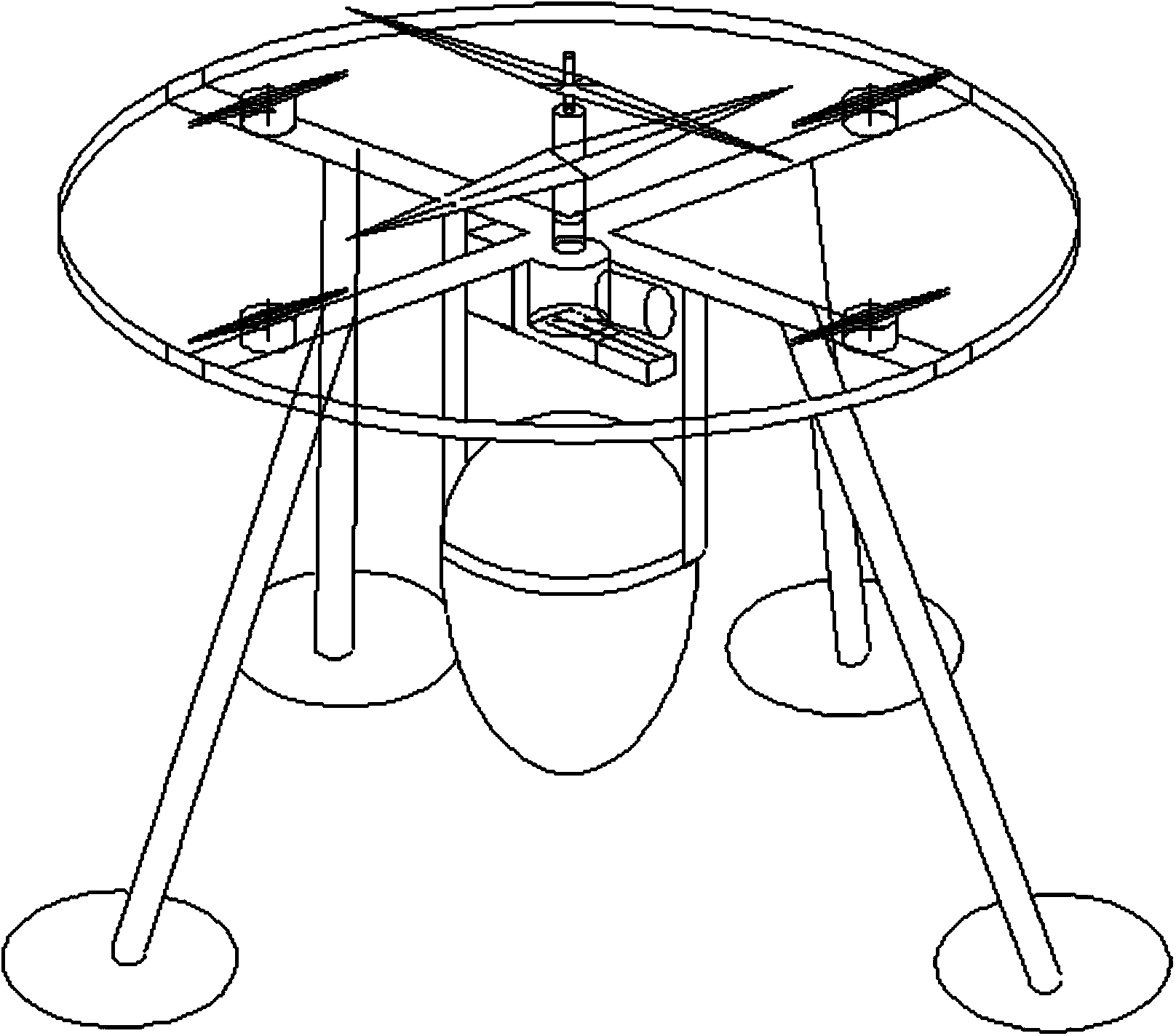
Unmanned logistics helicopter
ActiveCN104163241AEasy ground handlingReduced weight and structural complexityRotocraftRotary wingQuad rotor
The invention belongs to the technical field of aviation, relates to an unmanned aerial vehicle, and in particular relates to an unmanned logistics helicopter. The unmanned logistics helicopter comprises a body and rotor wings arranged on the body, wherein the body is of a cross-shaped structure; four body frames are fixed on the cross-shaped structure to support the body; central coaxial opposite-rotating double rotors are mounted at the central position of the body and are powered by an oil drive engine; four electric quad-rotor-wing supplying posture adjusting capacities are mounted at four tail ends of the cross-shaped structure and are powered by four brushless motors respectively; a cargo frame with a rectification shape is hung below the body through a cargo frame bracket. The unmanned logistics helicopter has the advantages of high endurance, safety, energy utilization and convenience in ground control, and can be put into use as an unmanned logistics aerial vehicle.
Owner:AVIATION IND INFORMATION CENT
Collision avoidance control method and system for automatic driving
ActiveCN108189835APreferential collision avoidance behaviorTaking into account driving efficiencyExternal condition input parametersVehicle drivingAutopilot
The invention discloses a collision avoidance control method for automatic driving. The method comprises the steps that when it is detected that an obstacle exists in a planning driving path of an automatic driving vehicle, the collision time of the automatic driving vehicle and the obstacle is calculated; if the collision time is smaller than a set safety threshold value, a safety collision avoidance operation is executed; if the collision time is smaller than or equal to a set emergent braking threshold value, an emergent braking operation is executed; the relative speed of the automatic driving vehicle and the obstacle is calculated; if the relative speed is larger than or equal to a common braking threshold value, a common braking operation is executed; if the relative speed is largerthan a vehicle following cruising threshold value, the real-time distance between the automatic driving vehicle and the obstacle is calculated, and if the real-time distance is longer than a minimum line changing distance, a line changing operation is executed; otherwise, a vehicle following cruising operation is executed. According to the collision avoidance control method for automatic driving,overall planning is conducted for different complex working conditions, an optimal collision avoidance behavioral mode is given based on a vehicle self-state under different working conditions, the method is suitable for a working condition that the vehicle speed of the automatic driving vehicle is 60 km / h or below, and the safety of efficient vehicle driving can be achieved.
Owner:清华大学苏州汽车研究院(吴江)
Multi-target dispatching method considering wind electricity output for electrical power system
InactiveCN107370188ATake security into considerationSingle network parallel feeding arrangementsWind energy generationPrediction intervalPollination
The invention discloses a multi-target dispatching method considering wind electricity output for an electrical power system. The method comprises the steps of outputting high and low limits of a prediction interval based on high-low limit evaluation method of a neural network, generating a wind electricity frequency scene in a prediction interval sequence to describe the randomness of wind electricity power, simultaneously considering the total fuel cost, the pollutant discharge amount, the risk cost and the rotary standby cost in an objective function by taking load shedding punishment expense expectation as a risk index, constructing an optimized dispatching model including a wind electricity power system, and carrying out optimization solution on the constructed multi-target objective function based on a flower pollination algorithm and a differential evolution algorithm so as to obtain the optimized dispatching method. According to the method, the load shedding punishment expense expectation is taken as the risk index, meanwhile, the rotary standby cost is considered in the objective function, the optimized dispatching model including the wind electricity power system is constructed, conventional operation constraints of a unit are considered by the constructed model, and besides, reliability constraints are further added, so that the environment, the economy and the safety are simultaneously considered by virtue of a dispatching decision.
Owner:STATE GRID SHANDONG ELECTRIC POWER +1
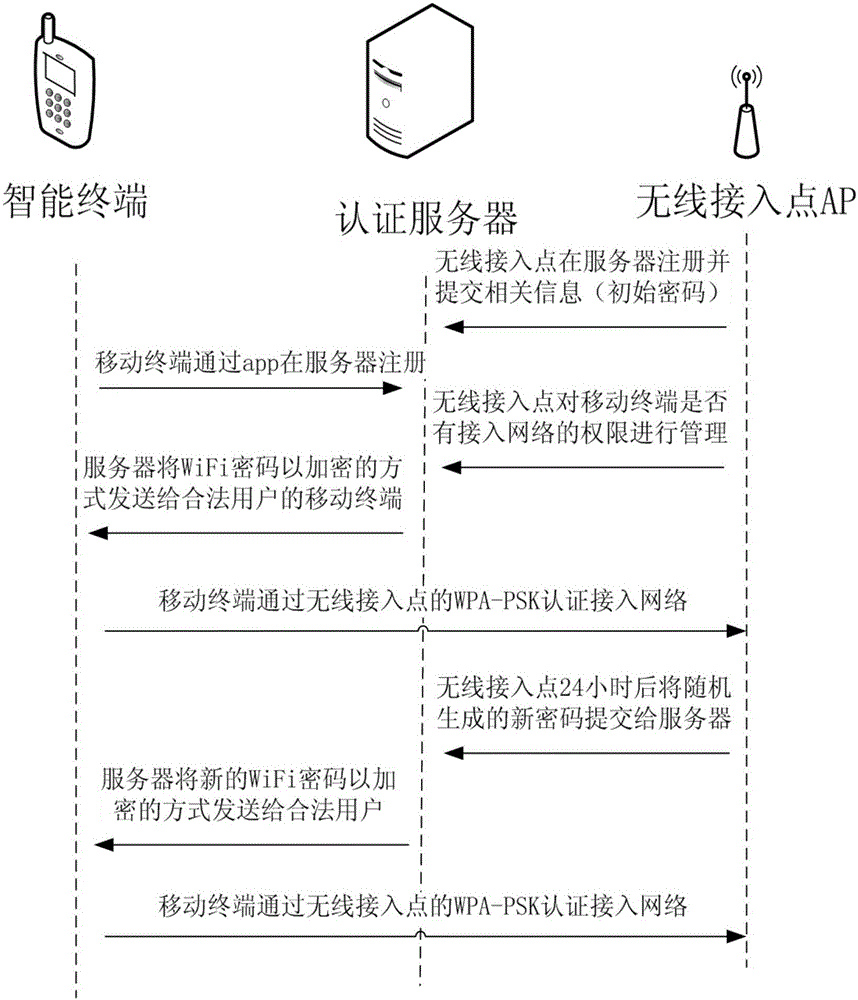
WiFi authentication system and method based on dynamic password
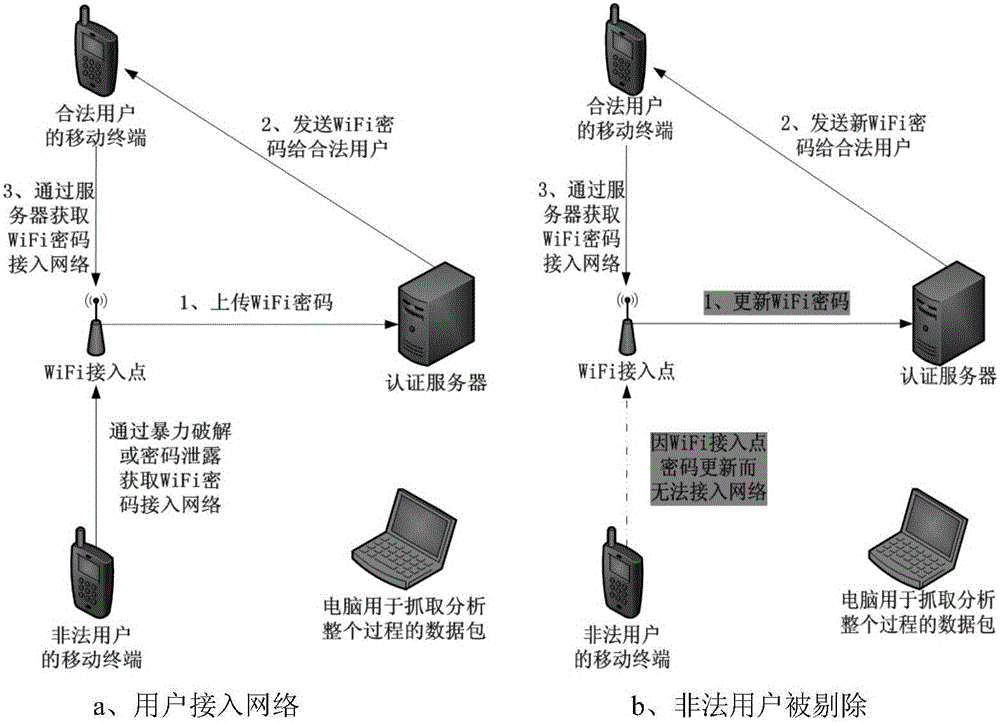
InactiveCN104994118AConsider operabilityTake security into considerationKey distribution for secure communicationSecurity arrangementWi-Fi Protected AccessRelevant information
The invention discloses a WiFi authentication system and method based on a dynamic password. A mobile terminal is arranged. The mobile terminal registers on a server; a wireless access point registers on an authentication server and submits relevant information; the wireless access point manages an authority to access or not access the network of the mobile terminal; the server sends a WiFi password to the mobile terminal of a legal user in an encryption manner; the mobile terminal passes Wi-Fi protected access pre-shared key (WPA PSK) authentication and accesses the network; 24 hours later, the wireless access point randomly generates a new strong password and submits the strong password to the authentication server; the server sends the new WiFi password to a legal user of the system in the encryption manner; and the mobile terminal of the legal user passes WPA PSK authentication and accesses the network. Through adoption of the system and method, problems of weak passwords and password leakage by insiders are solved, the digital dynamic password of very high security is adopted, and the password is updated and authenticated automatically, so that human factors are furthest reduced.
Owner:吴培希
Correlation-considered GEPOPF calculation method
InactiveCN105005940AGuaranteed safe operationOptimization results are optimisticData processing applicationsSystems intergating technologiesElectricityControl objective
The invention discloses a correlation-considered GEPOPF (Combined Natural Gas and Electric Probabilistic Optimal Power Flow) calculation method. The lowest total operation cost of an interconnection system is used as an optimization control objective; the safety of an electric system and the safety of a natural gas system are considered; the influence of random factors is considered in an optimization process; the correlation among random variables is considered; and through the probabilistic OPF (Optimal Power Flow) calculation, the probability statistics information of the state variables and an objective function is obtained.
Owner:HOHAI UNIV
Data processing method and device based on automatic driving, equipment and medium
ActiveCN111897305AImprove test efficiencyTaking into account authenticityProgramme controlElectric testing/monitoringVehicle dynamicsSimulation
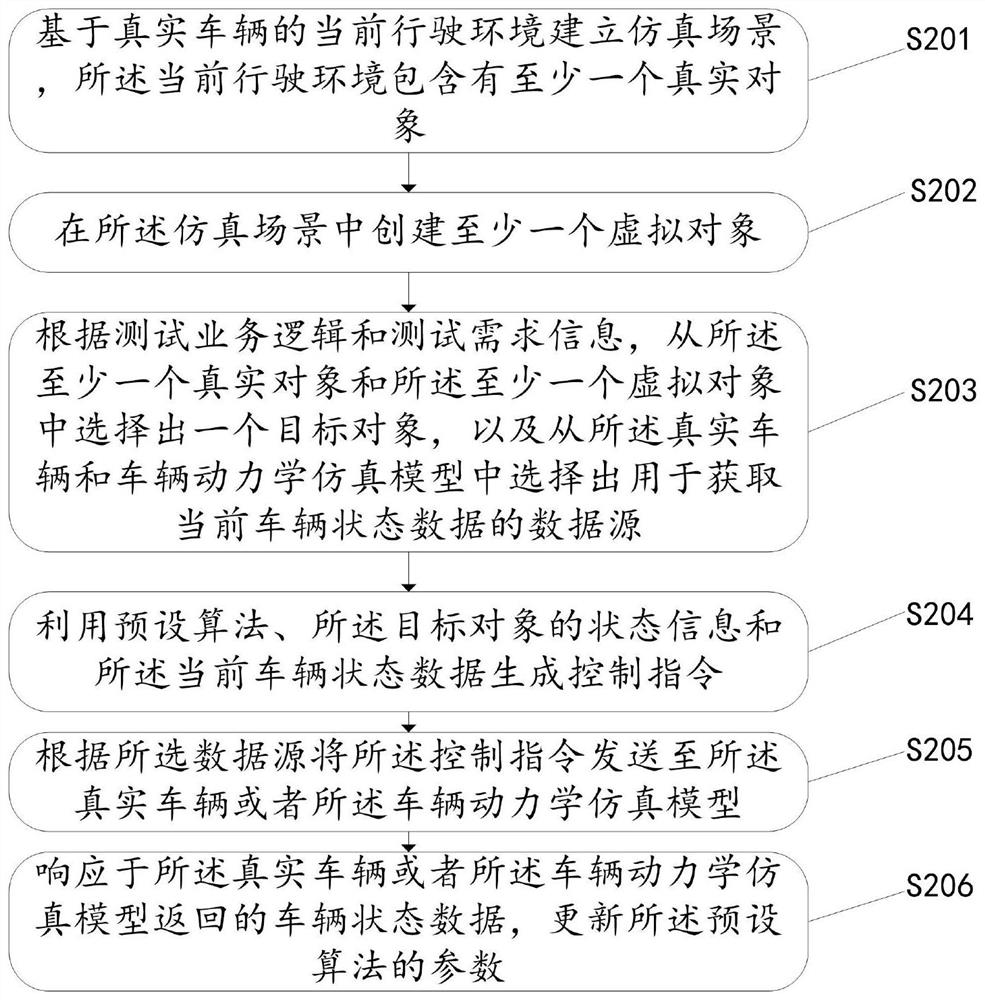
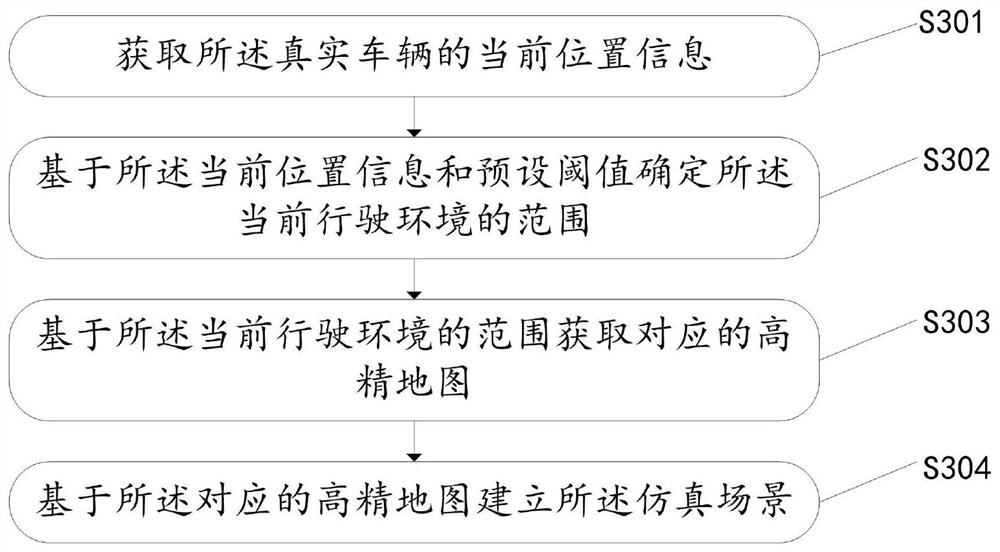
The invention discloses a data processing method and device based on automatic driving, equipment and a medium. The method comprises the following steps of establishing a simulation scene based on a current driving environment of a real vehicle, wherein the current driving environment comprises at least one real object, creating at least one virtual object in the simulation scene, selecting a target object from the at least one real object and the at least one virtual object according to a test service logic and a test demand information, and selecting a data source for acquiring current vehicle state data from the real vehicle and the vehicle dynamics simulation model, generating a control instruction by using a preset algorithm, the state information of the target object and the currentvehicle state data, sending the control instruction to a real vehicle or a vehicle dynamics simulation model according to the selected data source, and updating parameters of a preset algorithm in response to the vehicle state data returned by the real vehicle or the vehicle dynamics simulation model.
Owner:ZHEJIANG GEELY AUTOMOBILE RES INST CO LTD +1
Vehicle collision avoidance dynamic safety path planning method based on accurate trajectory prediction
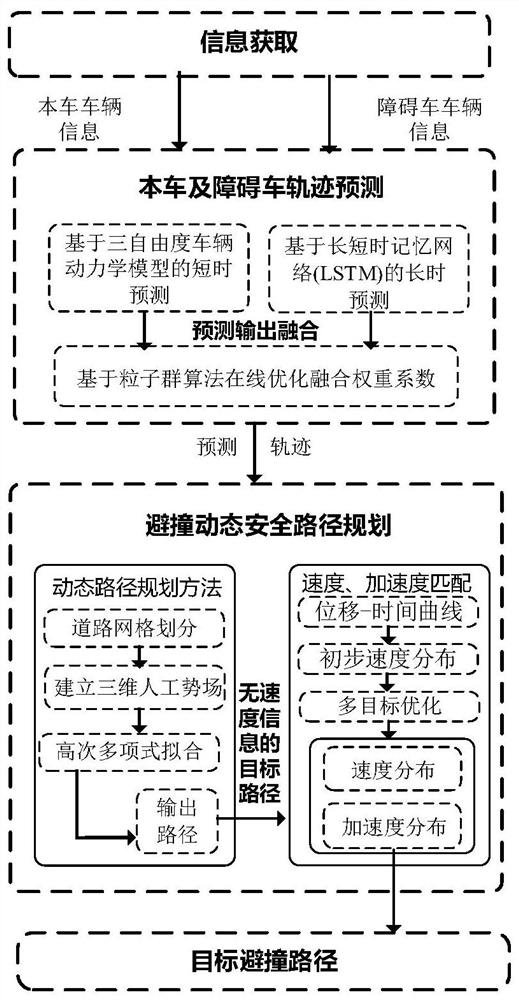
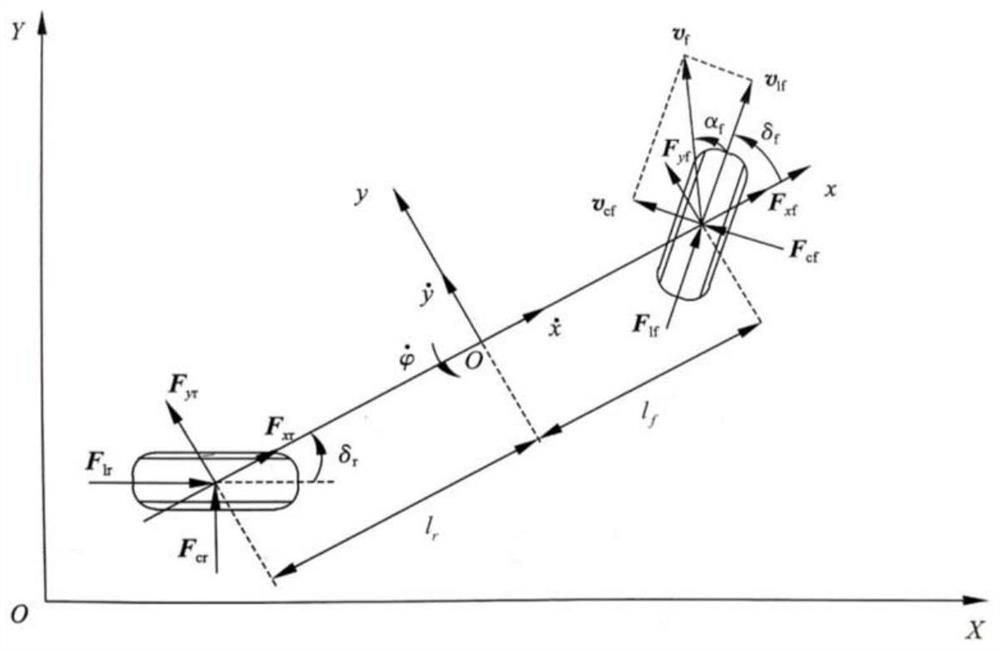
The invention relates to a vehicle collision avoidance dynamic safety path planning method based on accurate trajectory prediction. The method comprises the steps of obtaining vehicle state information and parameter information of a vehicle and an obstacle vehicle; constructing a vehicle trajectory prediction model based on a three-degree-of-freedom vehicle dynamics model and a long-short-term memory recurrent neural network LSTM; using the vehicle trajectory prediction model to predict the driving trajectories of the vehicle and the obstacle vehicle, and obtaining the driving trajectory prediction data of the vehicle and the obstacle vehicle; constructing a vehicle dynamic safety path planning model by fusing mesh generation, an artificial potential field method and a high-order polynomial curve fitting method; based on the driving trajectory prediction data of the vehicle and the obstacle vehicle obtained in the step 3, using the vehicle dynamic safety path planning model to obtain an optimal collision avoidance path of the vehicle; and carrying out speed and acceleration real-time matching on the optimal collision avoidance path obtained in the step 5. Compared with the prior art, the method has the advantages of high precision, safety, feasibility, comfort and the like.
Owner:TONGJI UNIV
Intelligent cup
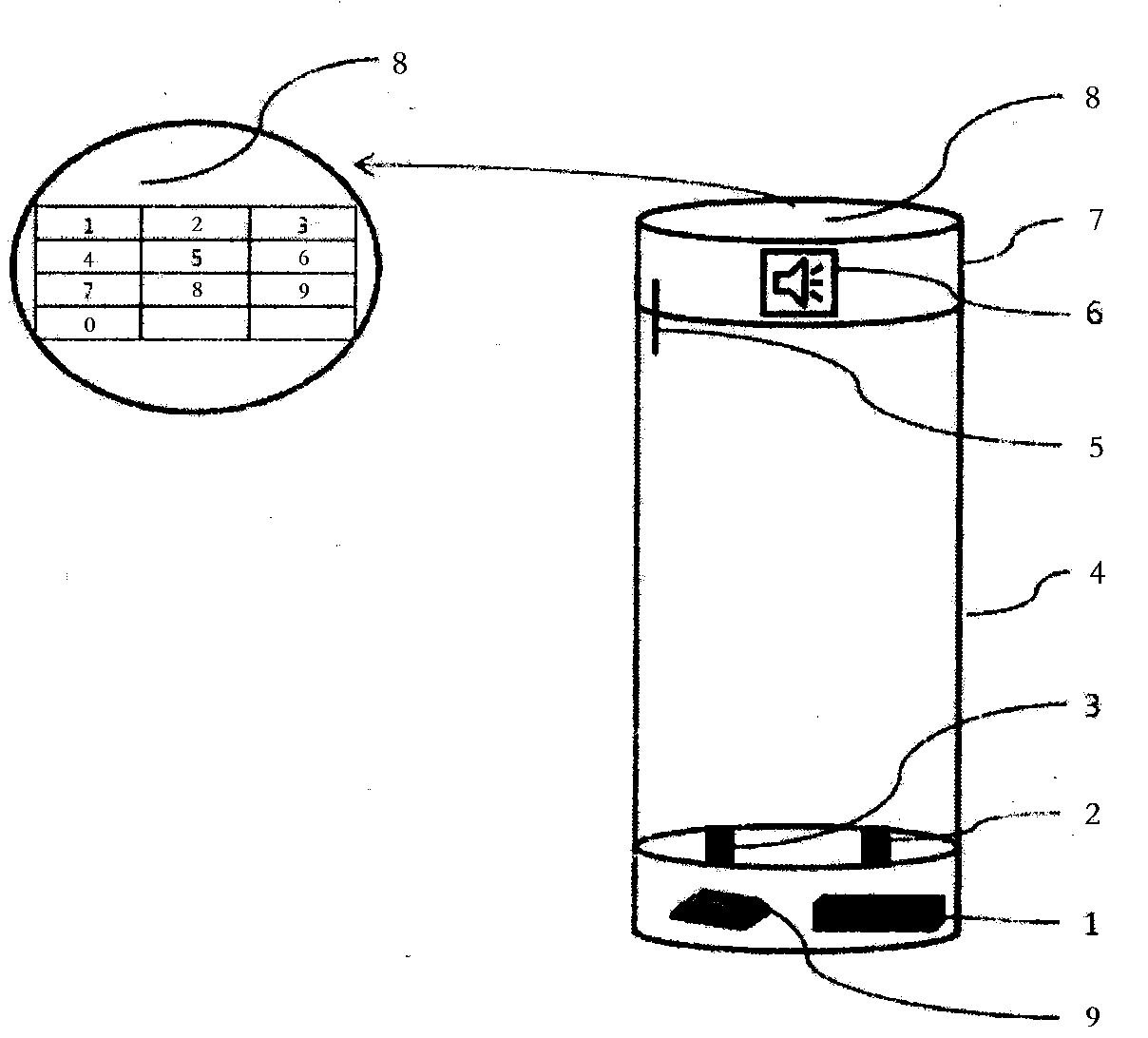
InactiveCN103735113ARealize intelligent functionsWith determinationDrinking vesselsPhysicsElectrical battery
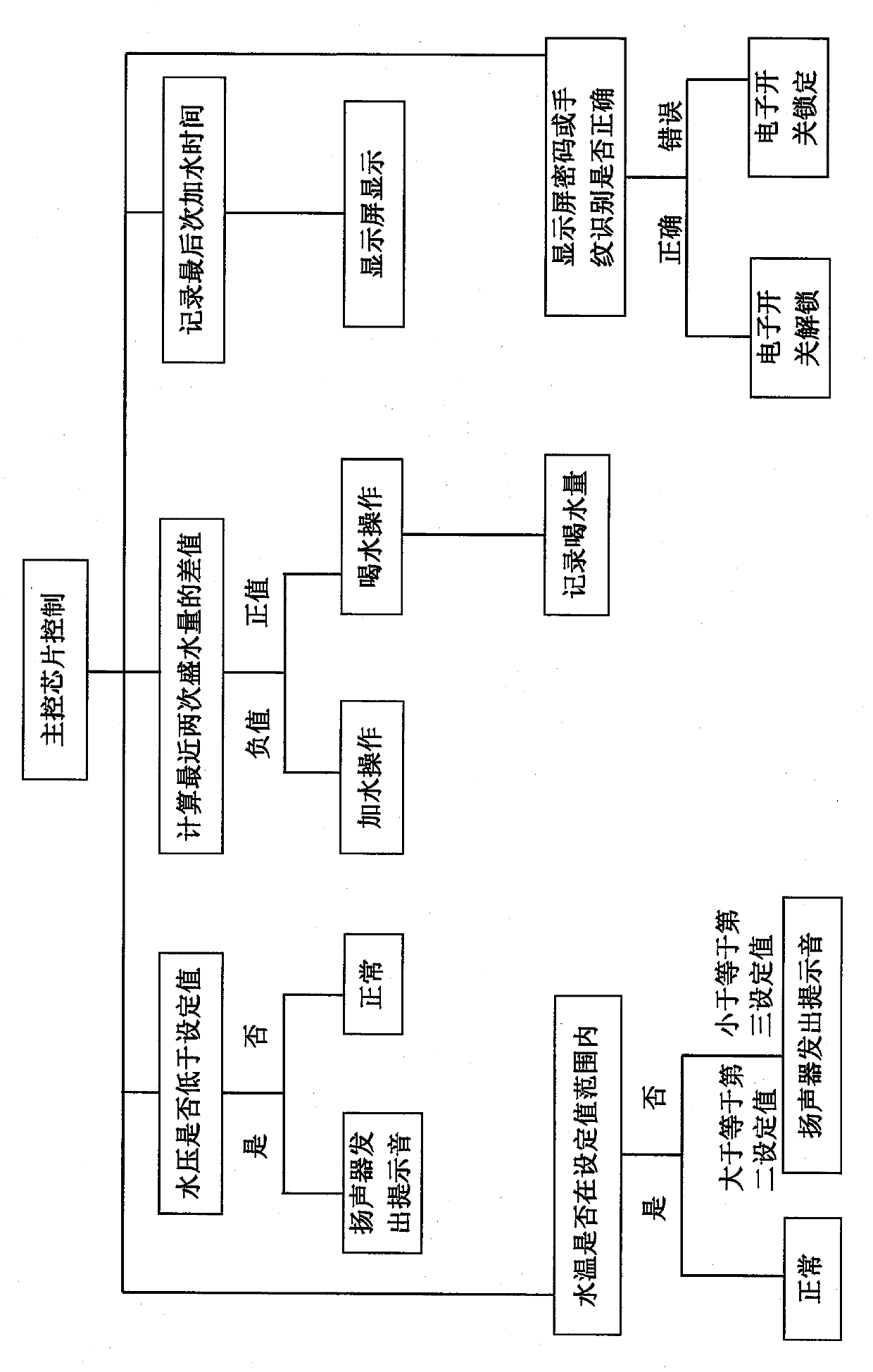
The invention relates to an intelligent cup. The intelligent cup comprises a cup body, a cup cover, a display screen, an electronic switch, a pressure sensor, a temperature sensor, a loudspeaker, a main control chip and a battery, wherein the cup body is used for containing water; the cup cover is arranged above the cup body; the display screen is arranged on the cup cover and used for displaying the water containing amount and the water temperature conditions in the cup body, and encryption control over the cup body can be carried out by inputting passwords or handprint identification on the display screen; the electronic switch is connected with the main control chip and the display screen and controlled to be turned on or turned off through the main control chip; the pressure sensor is arranged at the bottom of the cup body and used for determining and timely recording the water containing amount in the cup body; the temperature sensor is arranged at the bottom of the cup body and used for determining the water temperature in the cup body; the loudspeaker is arranged on the cup cover and used for giving a warning tone when the water containing amount and the water temperature achieve or do not achieve setting values; the main control chip is connected with the display screen, the electronic switch, the pressure sensor, the temperature sensor and the loudspeaker, and used for conducting information collation, recording, controlling and warning; the battery is used for providing electric energy for the intelligent cup.
Owner:陈建军
Lithium ion secondary battery
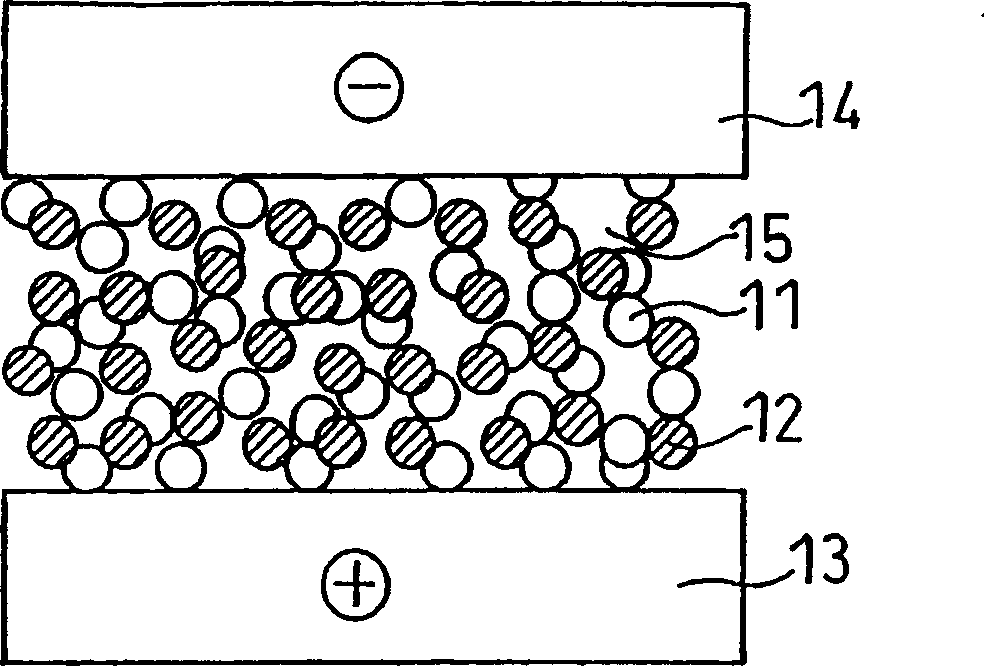
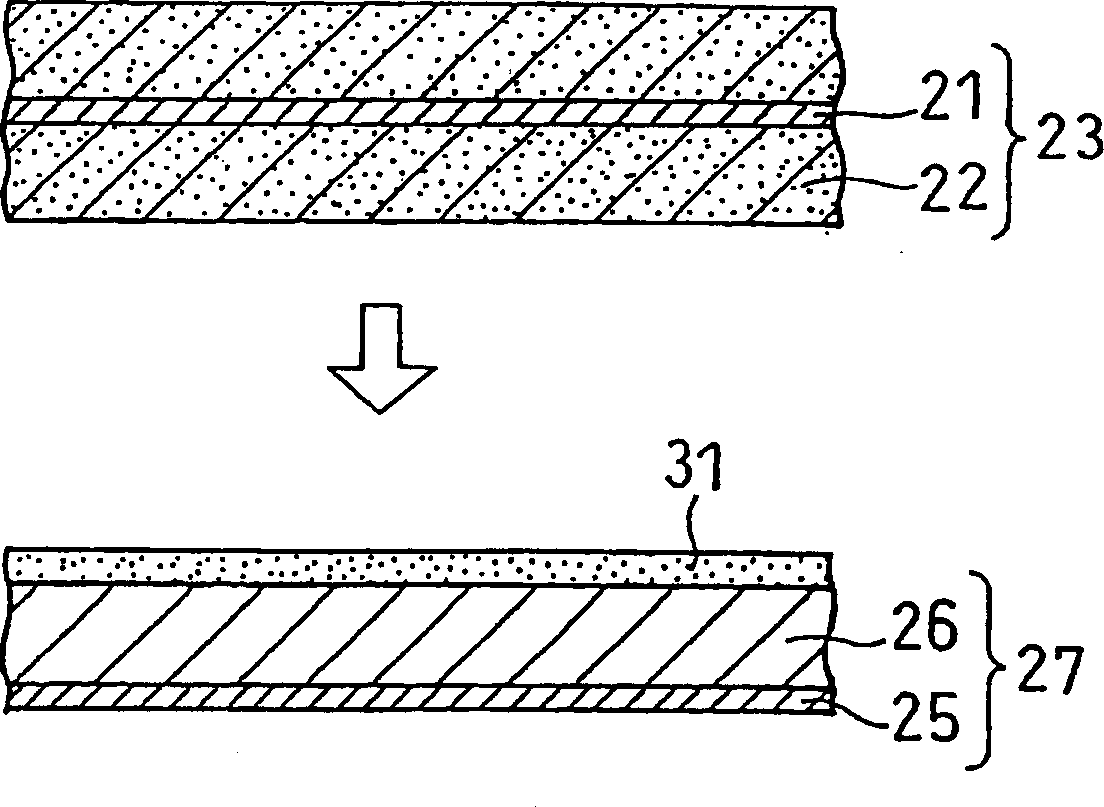
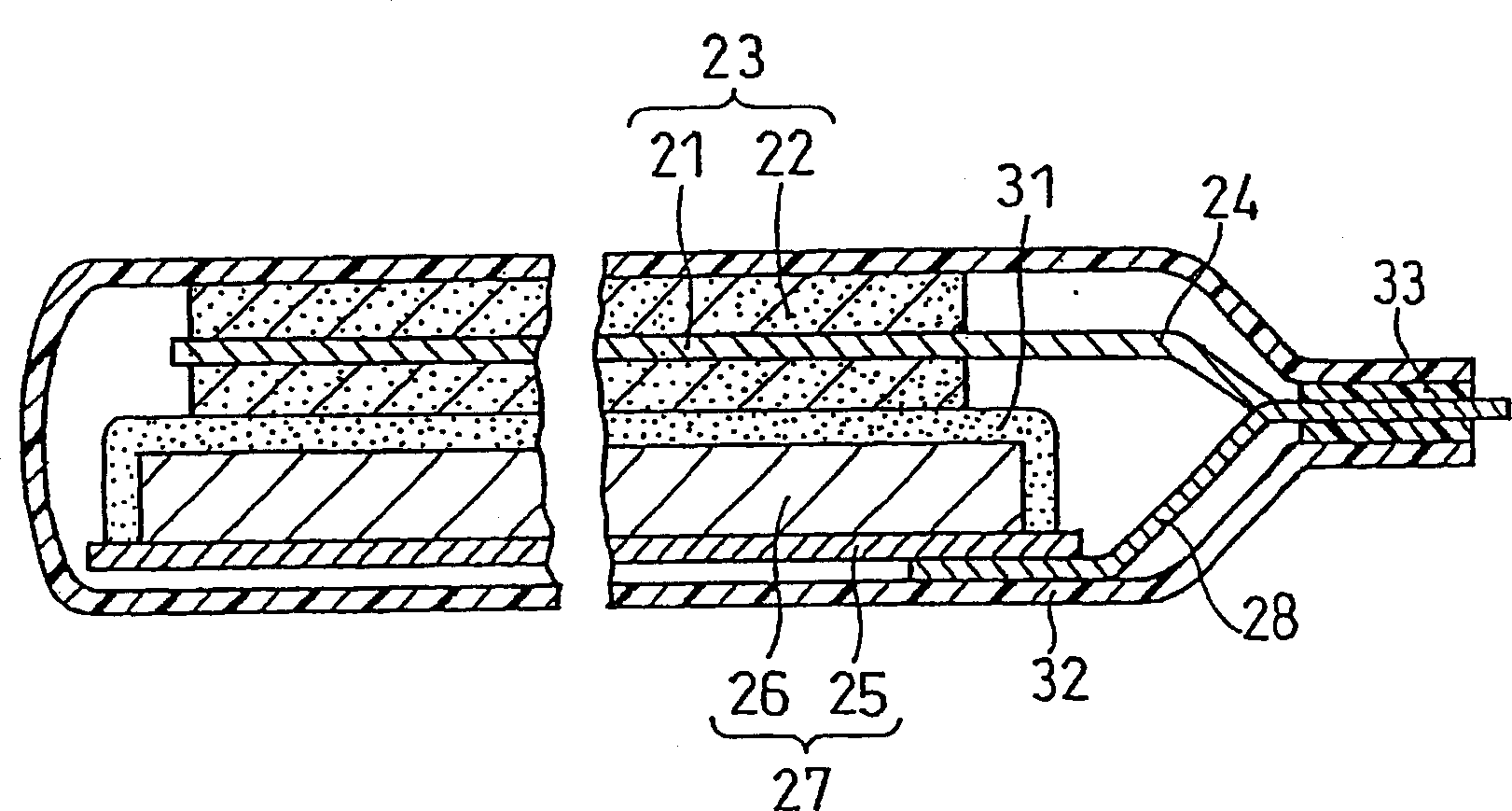
ActiveCN1795578AGuaranteed heat resistanceTake security into considerationCell seperators/membranes/diaphragms/spacersFinal product manufactureMethacrylateMaterials science
A lithium ion secondary battery includes a positive electrode capable of absorbing and desorbing lithium ion, a negative electrode capable of absorbing and desorbing lithium ion, a porous film interposed between the positive electrode and the negative electrode, and a non-aqueous electrolyte: the porous film being adhered to a surface of at least one of the positive electrode and the negative electrode; the porous film including a filler and a resin binder; the resin binder content in the porous film being 1.5 to 8 parts by weight per 100 parts by weight of the filler; and the resin binder including an acrylonitrile unit, an acrylate unit, or a methacrylate unit.
Owner:PANASONIC CORP
Network access method, mobile terminal and computer readable storage medium
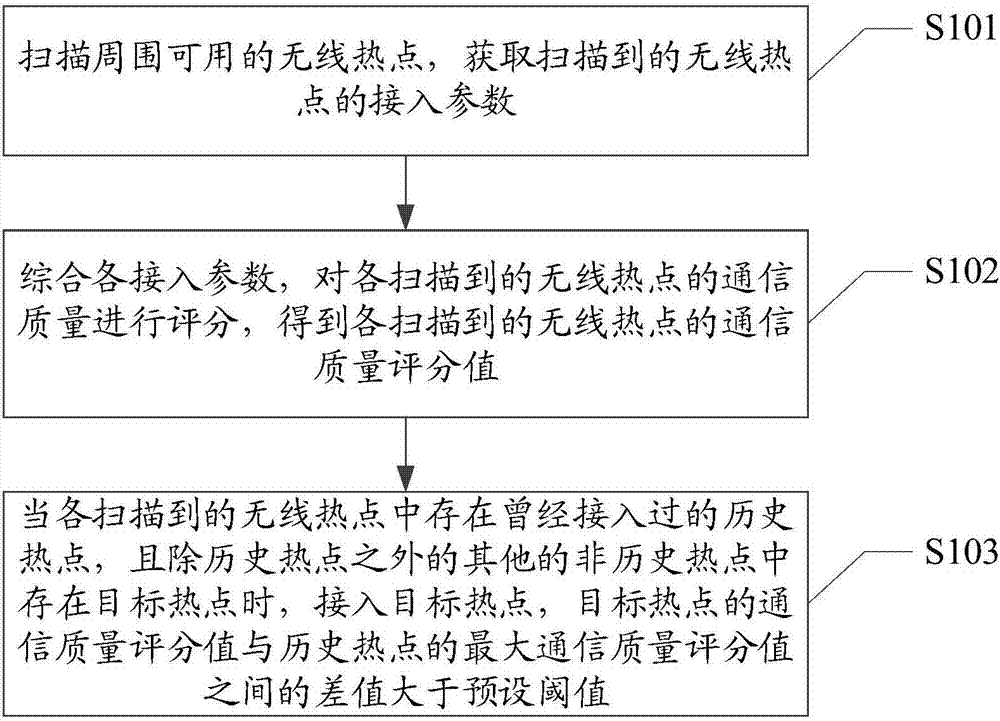
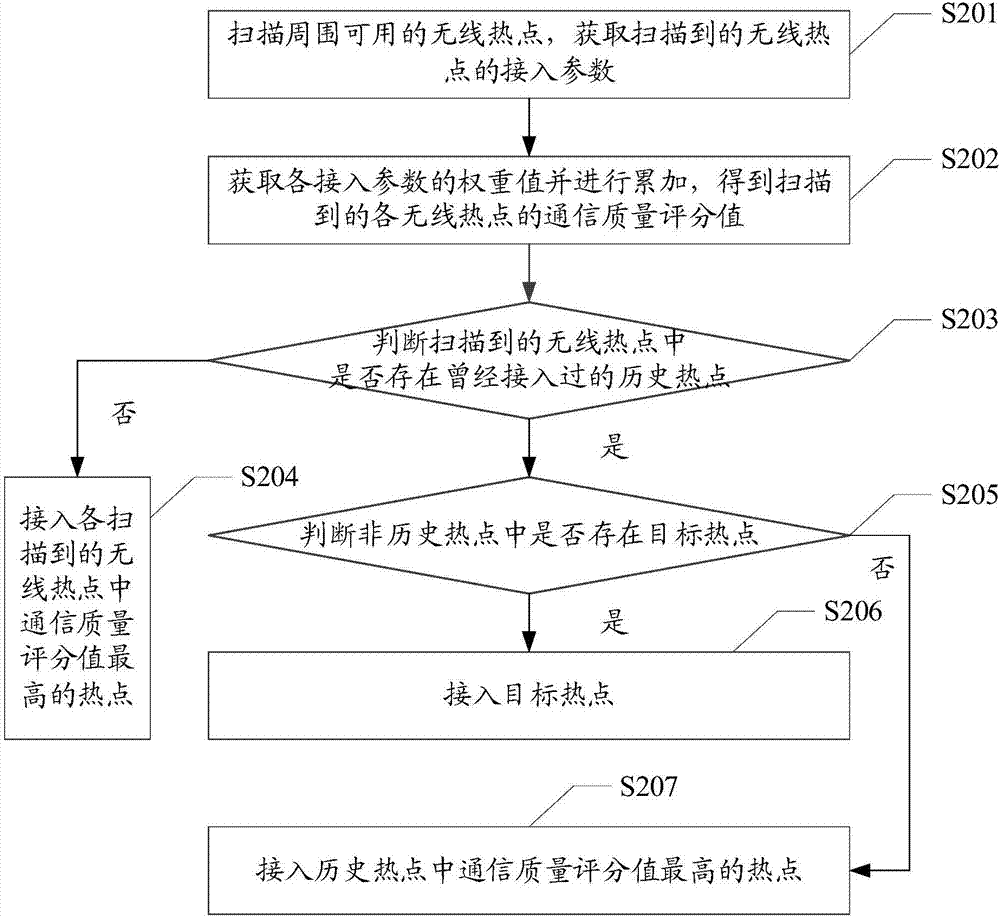
InactiveCN107241782APrecise positioningTroubleshoot Poor Communication QualityAssess restrictionCommunication qualityAccess method
The embodiment of the present invention discloses a network access method, which is applied in the field of communication technology, including: scanning available wireless hotspots around, and obtaining access parameters of the scanned wireless hotspots; Scoring the communication quality of wireless hotspots to obtain the communication quality score value of each scanned wireless hotspot; when each scanned wireless hotspot has historical hotspots that have been accessed, and other When there is a target hotspot in , the target hotspot is accessed, and the difference between the communication quality score value of the target hotspot and the maximum communication quality score value of the historical hotspot is greater than a preset threshold. The embodiment of the invention also discloses a mobile terminal and a computer-readable storage medium, which can effectively solve the problem of poor communication quality of the accessed network.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Information exchange system with safety isolation
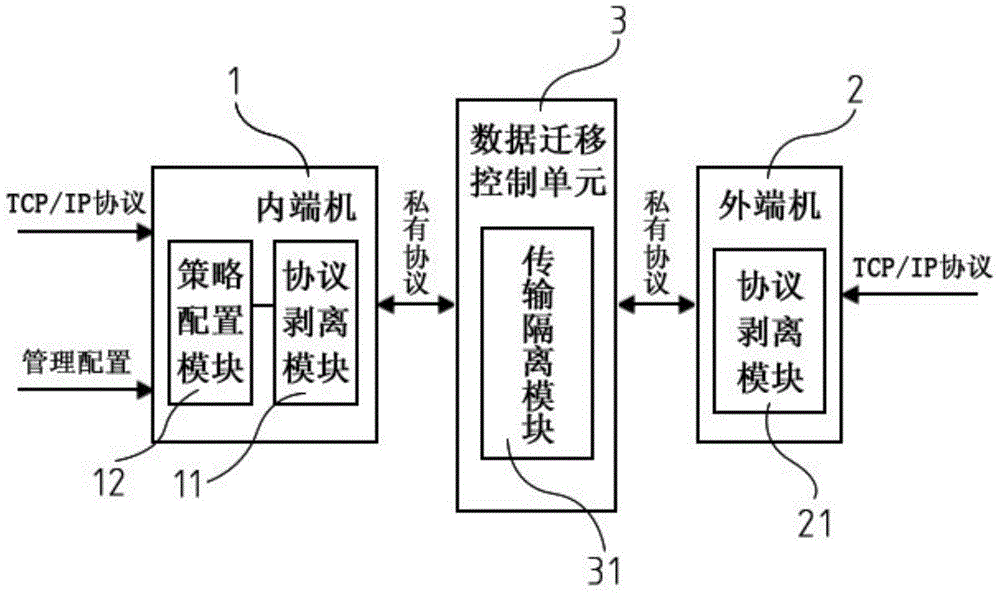
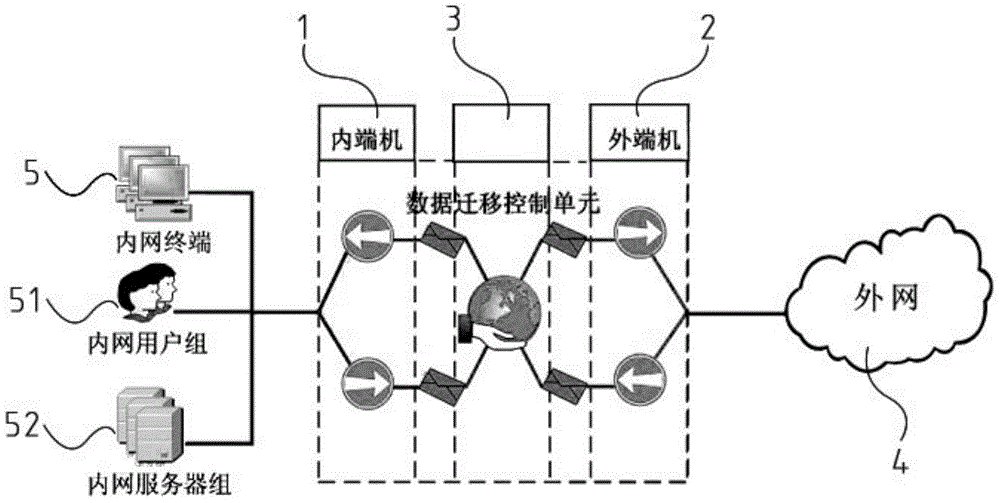
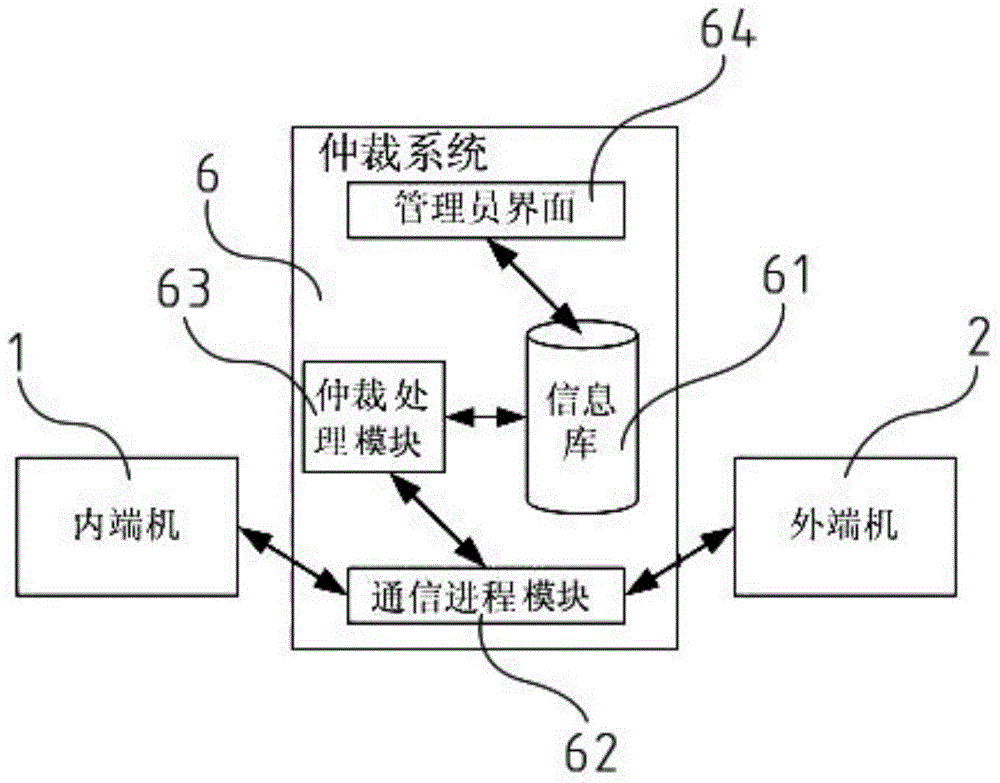
InactiveCN105007272APrevent malicious attacksPrevent leakageTransmissionInformation transmissionControl data
The invention discloses an information exchange system with safety isolation, relating to the field of information safety. Real-time communication of an internal network and an external network cannot be considered simultaneously, so that the conventional information exchange system has poor convenience and security. The information exchange system with safety isolation solves the above problem. The system comprises an inner end machine and an outer end machine which are each provided with a protocol stripping module. The inner end machine and the outer end machine establish a communication connection through a data migration control unit. The data migration control unit is provided with a transmission isolation module. Due to the protocol stripping module, a network protocol of one party cannot extend to an opposite party. All previous application layer information is stripped off from the protocol stripping module and is restored to application layer information. The stripped data is transmitted between the inner end machine and the outer end machine through the data migration control unit. The transmission isolation module guarantees information transmission and simultaneously prevents one end machine from attacking the other end machine. While the internal network and external network are isolated effectively, safe and controlled data exchange between the internal network and the external network is realized.
Owner:陈巨根
Environment-friendly electrostatic spraying antirust oil and preparation method thereof
The invention discloses an environment-friendly electrostatic spraying antirust oil which is prepared from the following raw materials in percentage by mass: 70.0-90.0% of base oil, 5.0-25.0% of rust inhibitor, 1.0-5.0% of surfactant and 0.5-5.0% of antioxidant. The preparation method of the environment-friendly electrostatic spraying antirust oil comprises the following steps: mixing the measured base oil, rust inhibitor, surfactant and antioxidant, heating, and stirring uniformly to obtain the environment-friendly electrostatic spraying antirust oil. The antirust oil has the advantages of higher breakdown voltage, high safety, high atomization tendency of the oil product and low viscosity, and is convenient for cleaning; and the antirust oil can satisfy the requirement for antirust properties and conform to the requirement for environmental protection.
Owner:广州中机实业有限公司 +1
Robot trajectory tracking method and system and storage medium
ActiveCN111506081AImprove trajectory tracking performanceAccurate descriptionPosition/course control in two dimensionsSimulationObstacle avoidance
The invention discloses a robot trajectory tracking method, a robot trajectory tracking system and a storage medium which integrate the trajectory optimization and control, and better ensure the feasibility of trajectory tracking of a robot. When the robot passes through a dense obstacle, the weight in the target function is correspondingly adjusted according to the shortest distance between the current position of the differential robot and the obstacle by adopting the self-adaptive weight, so that the safety and the running speed can be considered when the robot performs trajectory tracking,and the trajectory tracking performance of an obstacle area is improved. According to the method, the obstacle avoidance constraint is put into the target function and is converted into the soft constraint, the optimal control input is found in the mode of sampling in the allowable control space, the non-convex optimization problem is solved, and meanwhile, the obstacle avoidance performance of the mobile robot is improved in the mode of dynamically adjusting the weight.
Owner:CENT SOUTH UNIV
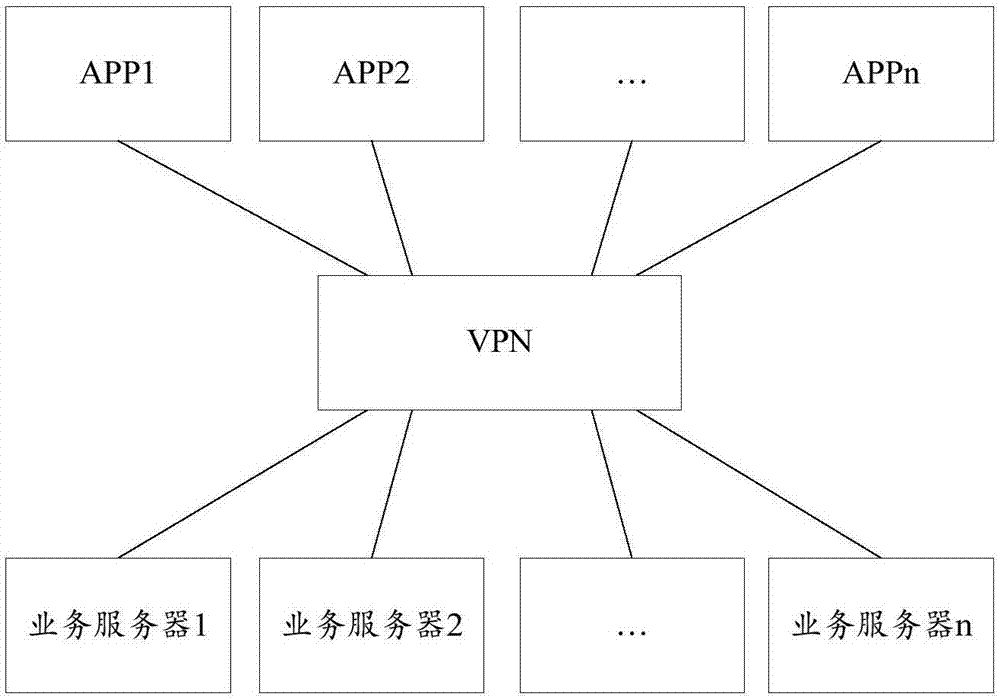
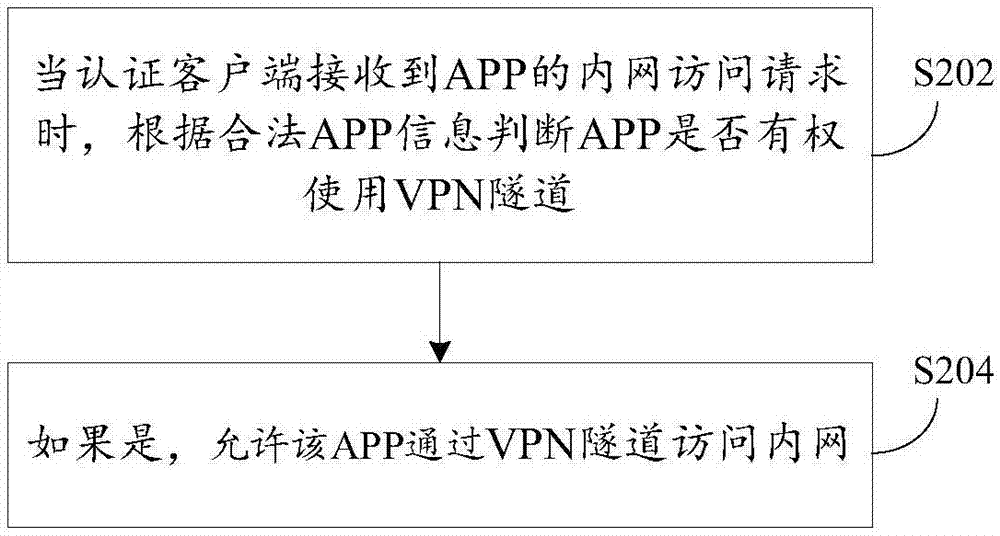
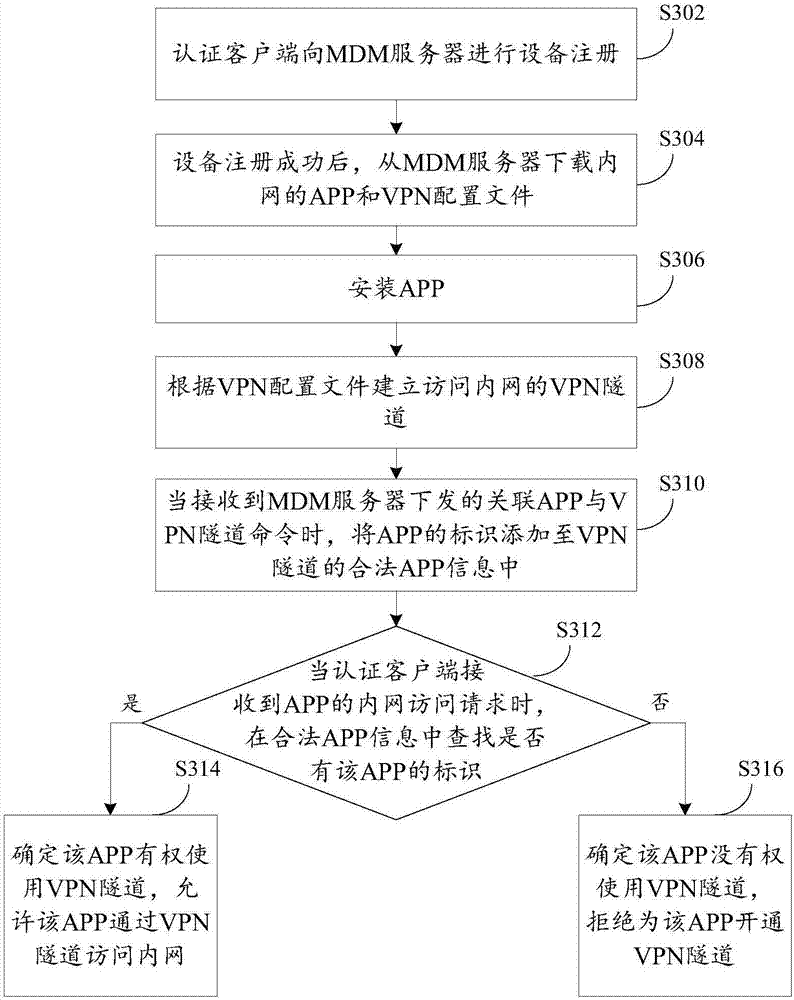
Control method, device and system for remote accessing intranet, and terminal equipment
ActiveCN107579966AEasy accessGuaranteed operational safetyNetworks interconnectionSecurity arrangementTerminal equipmentClient-side
The invention provides a control method, device and system for remotely accessing the intranet, and terminal equipment. The method is applied to the terminal equipment, an authentication client is installed in the terminal equipment, a VPN tunnel is established between the authentication client and the intranet, and legal APP information of the VPN tunnel is saved; the method comprises the following steps: when the authentication client receives an intranet access request of an APP, judging whether the APP is permitted to use the VPN tunnel according to the legal APP information; if the APP ispermitted to use the VPN tunnel, allowing the APP to access the intranet through the VPN tunnel. The control method provided by the invention can take both the convenience and the security of accessing the intranet by the terminal equipment into consideration, and the system performance is improved.
Owner:NEW H3C TECH CO LTD
Road intersection traffic light control system and control method thereof
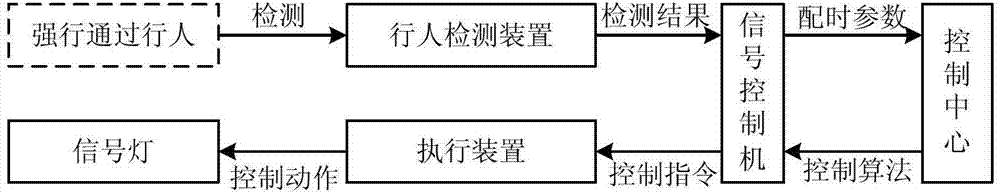
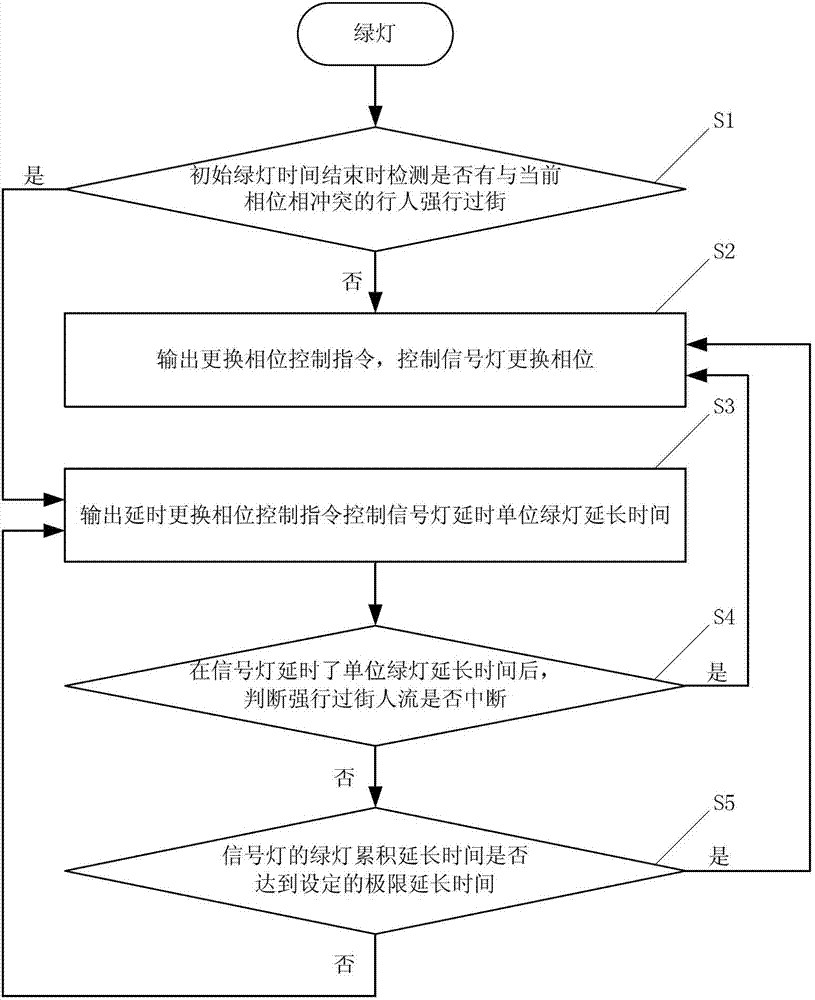
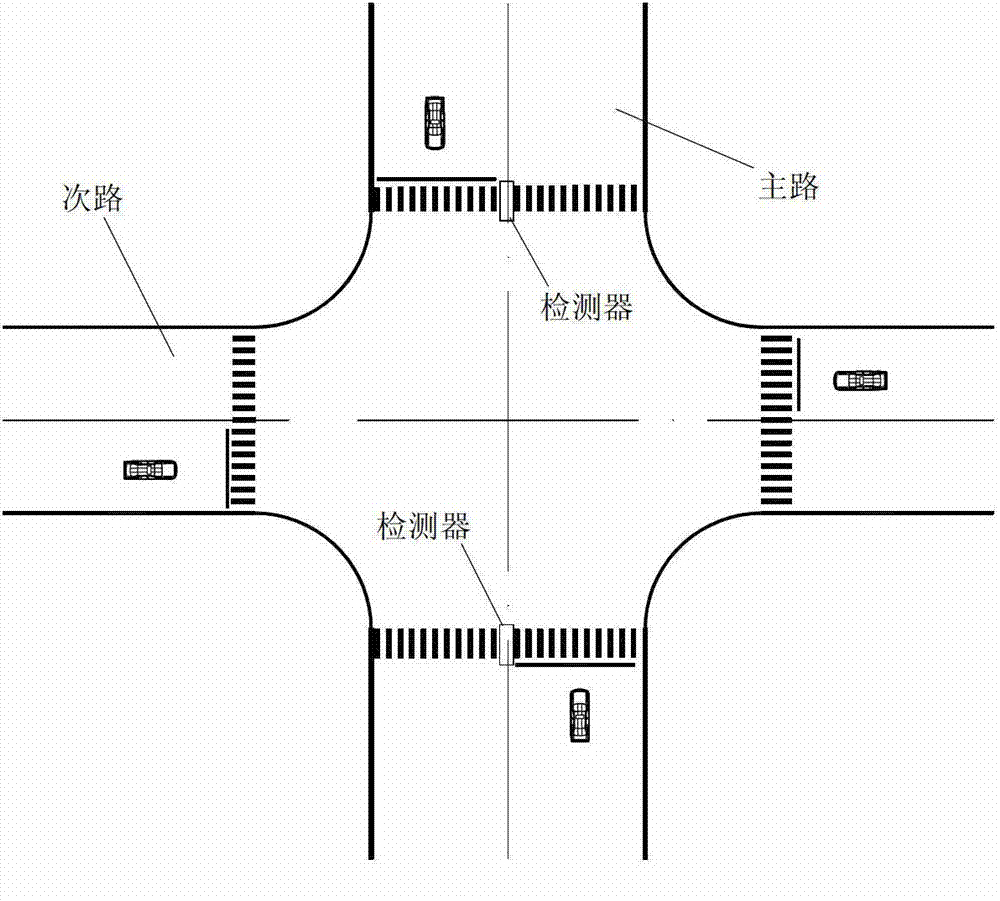
ActiveCN102930725ATraffic Safety GuaranteeEnsure safetyControlling traffic signalsRoad traffic controlAir traffic control
The invention discloses a road intersection traffic light control system and a control method thereof. Vehicle delay minimizing is not the only purpose, and the optimization objective is that the traffic safety of a pedestrian who crosses a road forcibly is guaranteed. Due to the fact that when an initial green light is over, the fact whether the pedestrian who is in conflict with the current phase condition crosses the road forcibly is judged, whether the duration time of the green light is prolonged is determined. When the initial green light is over, if the pedestrian who is in conflict with the current phase condition crosses the road forcibly, the duration time of the green light is prolonged, otherwise, the phase condition of the green light and a red light is changed normally. Due to the fact that ultimate prolonging time is set, not only is the safety of the pedestrian who crosses the road forcibly guaranteed, but also the delay at a road intersection is avoided. Therefore, the possibility that when the pedestrian crosses the road forcibly, accidents happen is reduced, the person oriented idea is emphasized, and the control system and the control method are particularly suitable for traffic control on a city intersection of a low-saturation city.
Owner:王晓宁
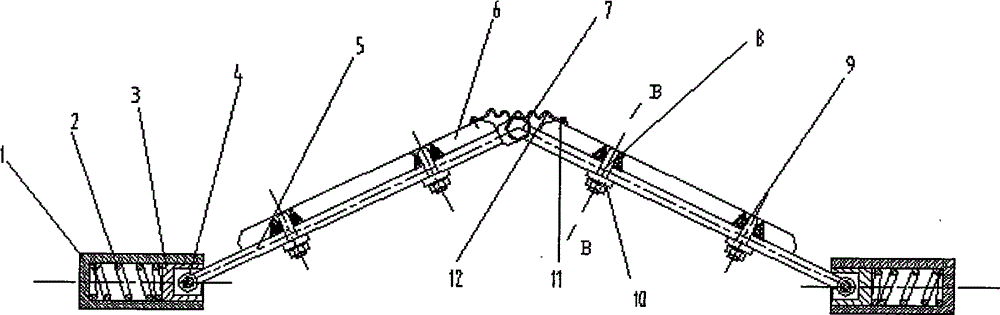
Elastic damage-free speed hump for vehicles
The invention discloses an elastic damage-free speed hump for vehicles. The speed hump comprises two pressing plates which are connected with a connecting rod mechanism so as to be folded and hunched; two connecting rod groups which are hinged to each other are arranged at the bottoms of the pressing plates; one end of one connecting rod of one connecting rod group is hinged to the corresponding end of one connecting rod of the other connecting rod group through a pin bolt, and the other end of each connecting rod is hinged to a sliding block through a connecting pin; each sliding block slides along a sliding chute formed in a sliding chute base which is fixedly arranged; a compression spring which is connected with the corresponding sliding block is arranged in each sliding chute base. The speed hump disclosed by the invention is simple in structure, and convenient to maintain; under the premise that the road safety is guaranteed, the driving and riding comfort of drivers and passengers can also be achieved; the damage caused by the speed hump to vehicles is reduced; the production cost and the using cost are reduced; the speed hump can be extensively generalized and applied on various roads which need the speed hump.
Owner:HUNAN AGRICULTURAL UNIV
Login authorization method and device, login method and device
The invention relates to a login authorization method and device, a login method and device. The login authorization method comprises the following steps: receiving a login request sent by a terminal; extracting a login credential and a terminal identifier from the login request, wherein the extracted login credential is generated and issued to the terminal when the terminal finishes the previous login authorization; querying the login credential, which is generated and stored when finishing the previous login authorization, corresponding to the terminal identifier; when the extracted login credential is consistent with the queried login credential, performing the login authorization corresponding to the terminal identifier; updating the stored login credential corresponding to the terminal identifier; and issuing the updated login credential to the terminal. By use of the login authorization method and device, the login method and device provided by the invention, a user can rapidly and safely login.
Owner:TENCENT TECH (SHENZHEN) CO LTD
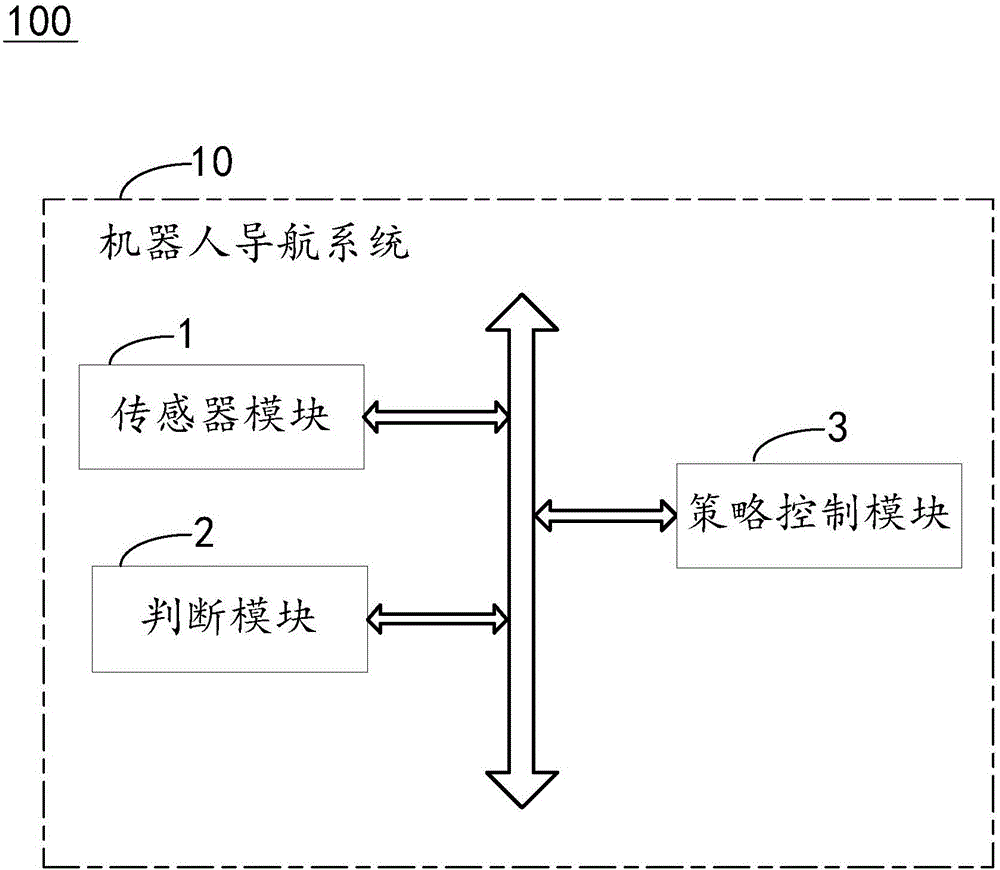
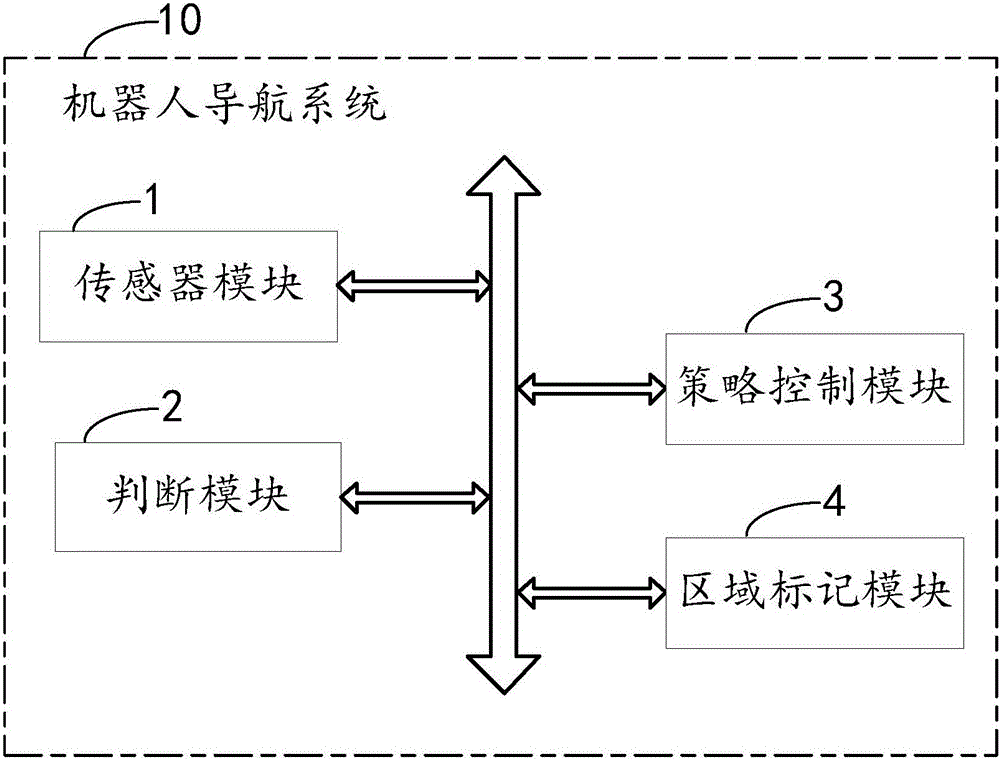
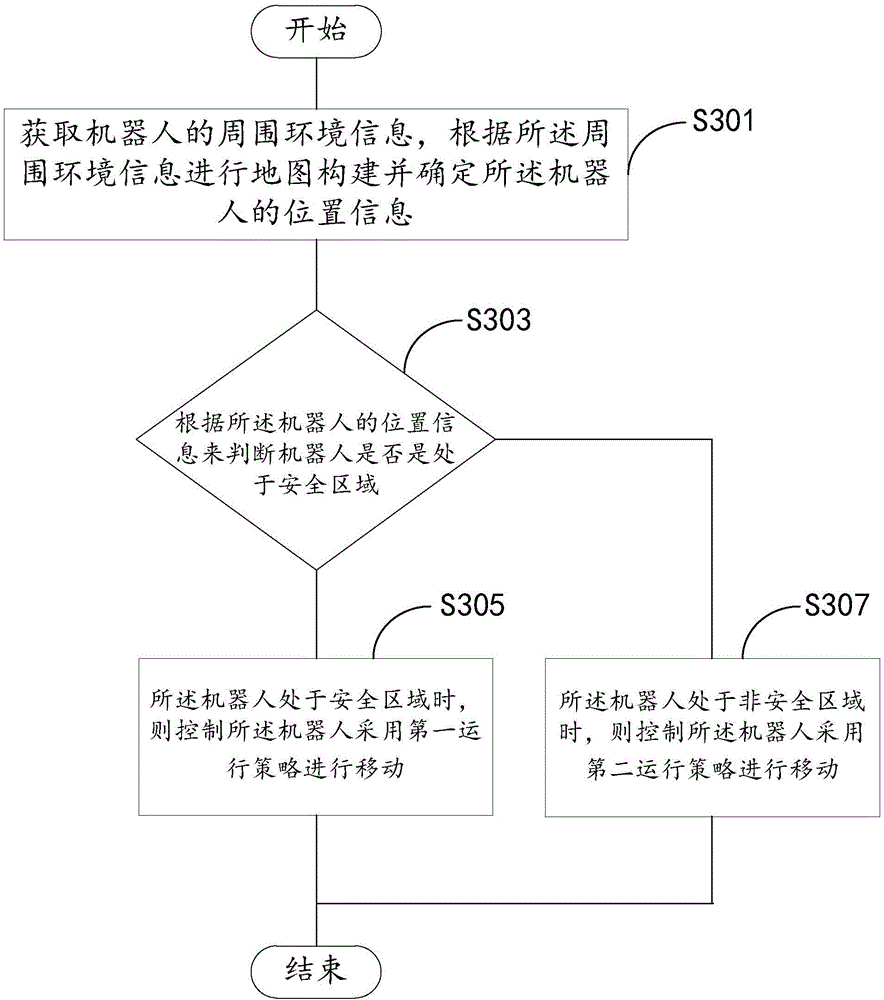
Robot navigation system and method
PendingCN105867386AConsider movement speedTake security into considerationPosition/course control in two dimensionsVehiclesSimulationNavigation system
The invention discloses a robot navigation system which comprises a sensor module, a judgment module and a strategy control module. The sensor module is used for emitting distance information, receiving returned distance information, performing calculation according to the returned distance information, performing mapping and outputting position information of a robot. The judgment module is used for judging whether the robot is located in a safety region or not according to the position information of the robot. The strategy control module is used for controlling the robot to adopt a first operating strategy for movements when determining that the robot is located in the safety region, or controlling the robot to adopt a second operating strategy for movements when determining that the robot is located in a non-safety region. The invention further discloses a robot navigation method. The robot navigation system and the robot navigation method give consideration to the operating efficiency of the robot and the reliability for responding to a complex environment and improve the movement efficiency and safety of the robot.
Owner:SHENZHEN LDROBOT CO LTD
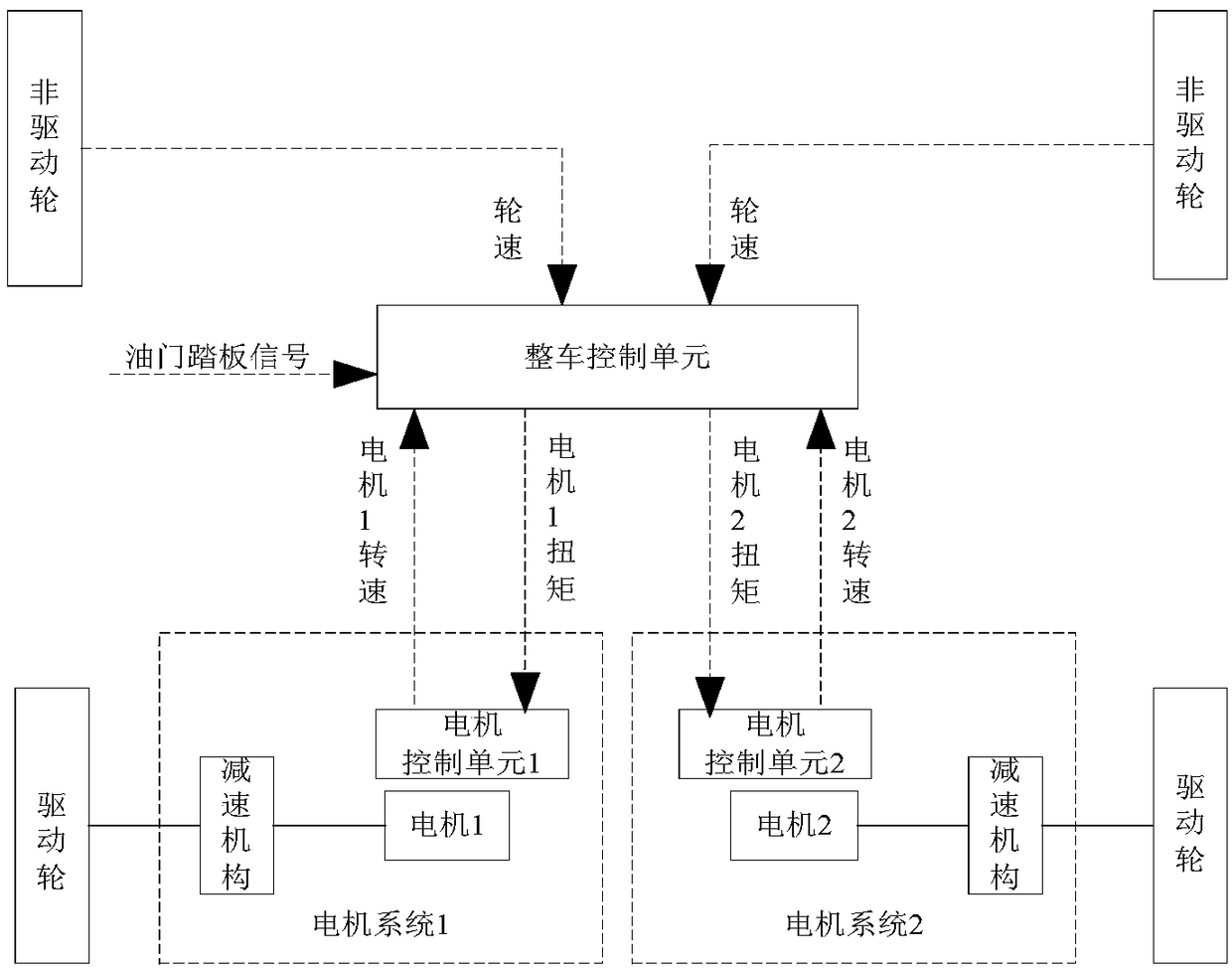
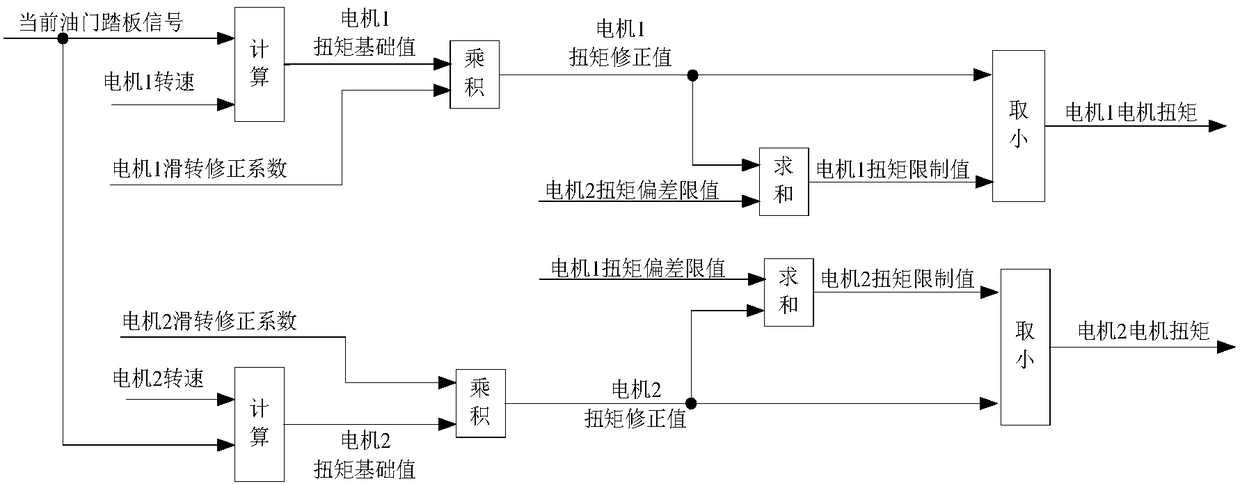
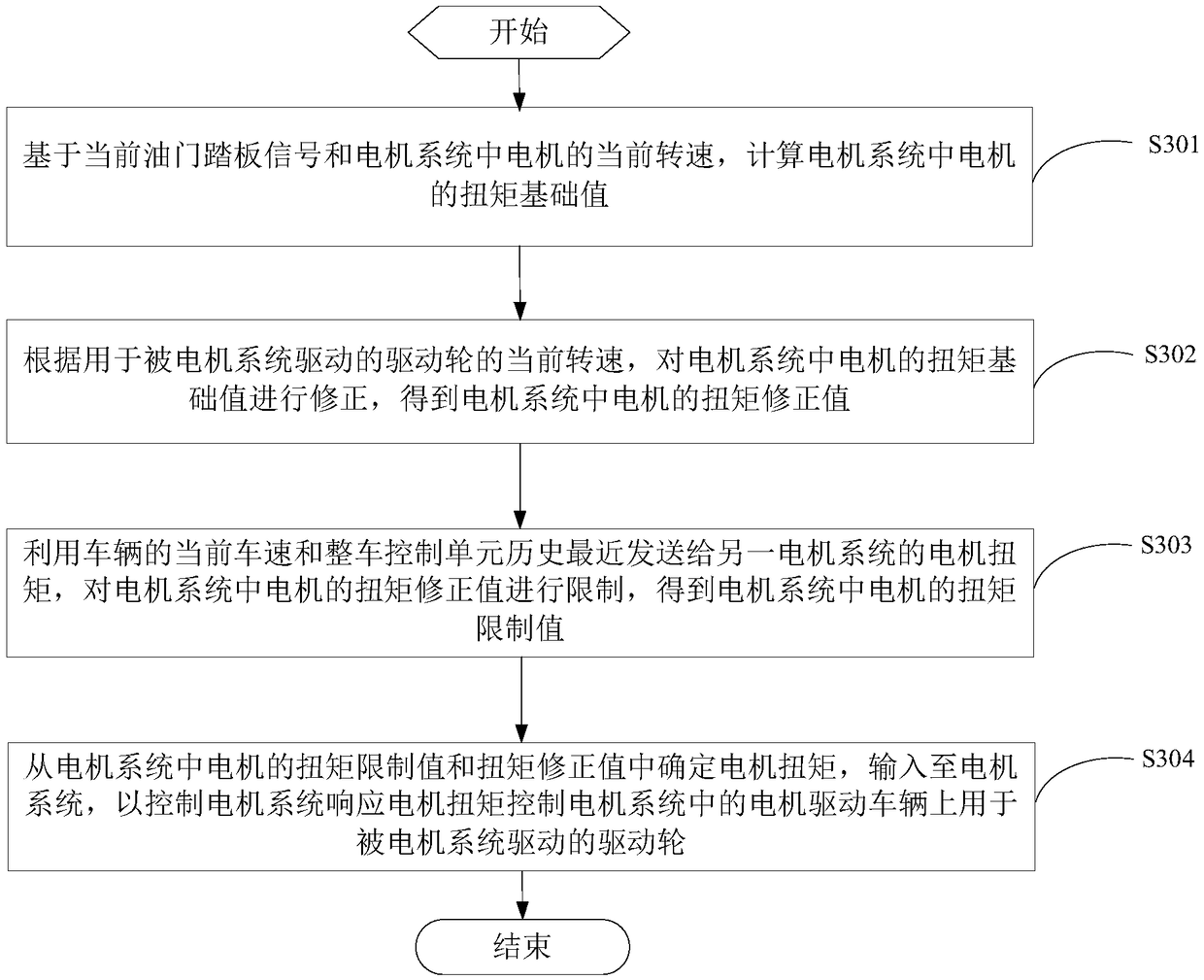
Motor torque control method and wheel rim motor distributed drive system
ActiveCN109353227ARealize closed-loop controlAvoid excessive slipSpeed controllerElectric devicesDrive wheelEngineering
The invention provides a motor torque control method and a wheel rim motor distributed drive system. The method is applied to a vehicle control unit in the system. The system further comprises two motor systems. The motor systems comprise motors. By means of the method, the following motor torque control process is executed to the motor systems at the same time. Based on current accelerator pedalsignals and the current rotating speeds of the motors in the motor systems, torque basic values of the motors in the motor systems are calculated; the torque basic values of the motors are corrected,and torque corrected values of the motors are obtained; the torque corrected values of the motors are limited through the current vehicle speed of a vehicle and the motor torque recently sent to the other motor system by the vehicle control unit historically, and torque limited values of the motors are obtained; the motor torque is determined from the torque limited values and the torque correctedvalues of the motors and input in the motor systems to which the motors belong, and therefore the motor systems are controlled to respond to the motor torque to control the motors in the motor systems to drive driving wheels, used for being driven by the motor systems, on the vehicle.
Owner:WEICHAI POWER CO LTD
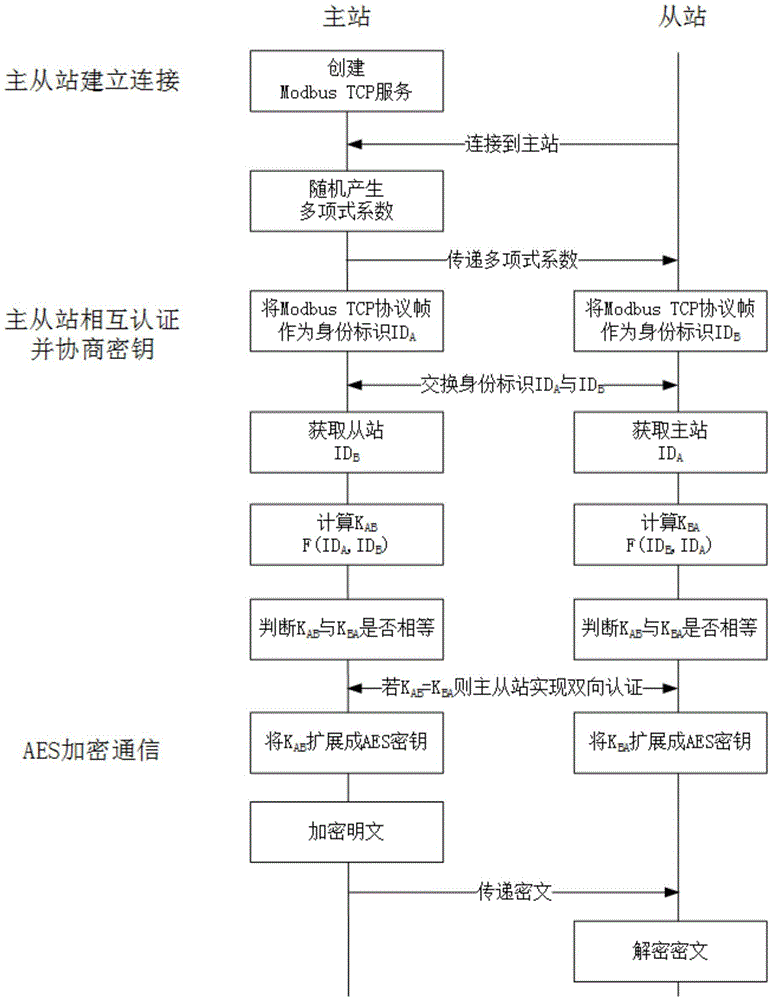
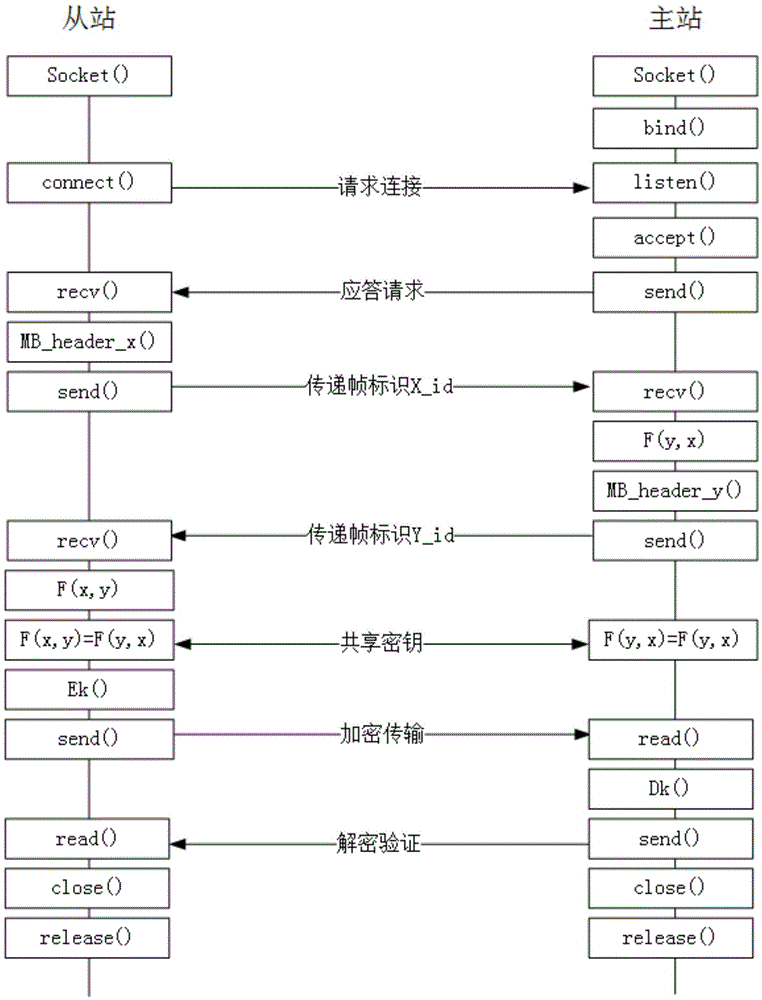
Method and system for identity authentication between master station and slave station in SCADA (Supervisory Control and Data Acquisition) system
ActiveCN105610837AReduce computational complexityTake security into considerationTransmissionMessage switchingProtocol for Carrying Authentication for Network Access
The invention provides a method and system for identity authentication between a master station and a slave station in an SCADA system. The method comprises following steps that: the master station A creates service and generates a symmetric polynomial coefficient aij; the slave station B builds connection with the master station A according to the IP address of the server of the master station A; after the connection is built successfully, the slave station B and the master station A share the symmetric multinomial parameter; both the master station and the slave station take the data frames of a communication protocol as own identity identifier IDA and IDB; the master station and the slave station exchange mutual identity identifiers; the identity identifiers are substituted into a symmetric polynomial for calculation; if f(IDA, IDB) is equal to f(IDB, IDA), the slave station B and the master station A realize two-way authentication; and a symmetric encryption key KAB is obtained through calculation and extension. According to the method and the system of the invention, the shared key is generated by the symmetric polynomial; the shared key is taken as the symmetric encryption key; a symmetric encryption algorithm is used in the message exchange process; and therefore, the calculation complexity is reduced.
Owner:SHANGHAI JIAO TONG UNIV +1
Scheduling method for virtual machine migration and system
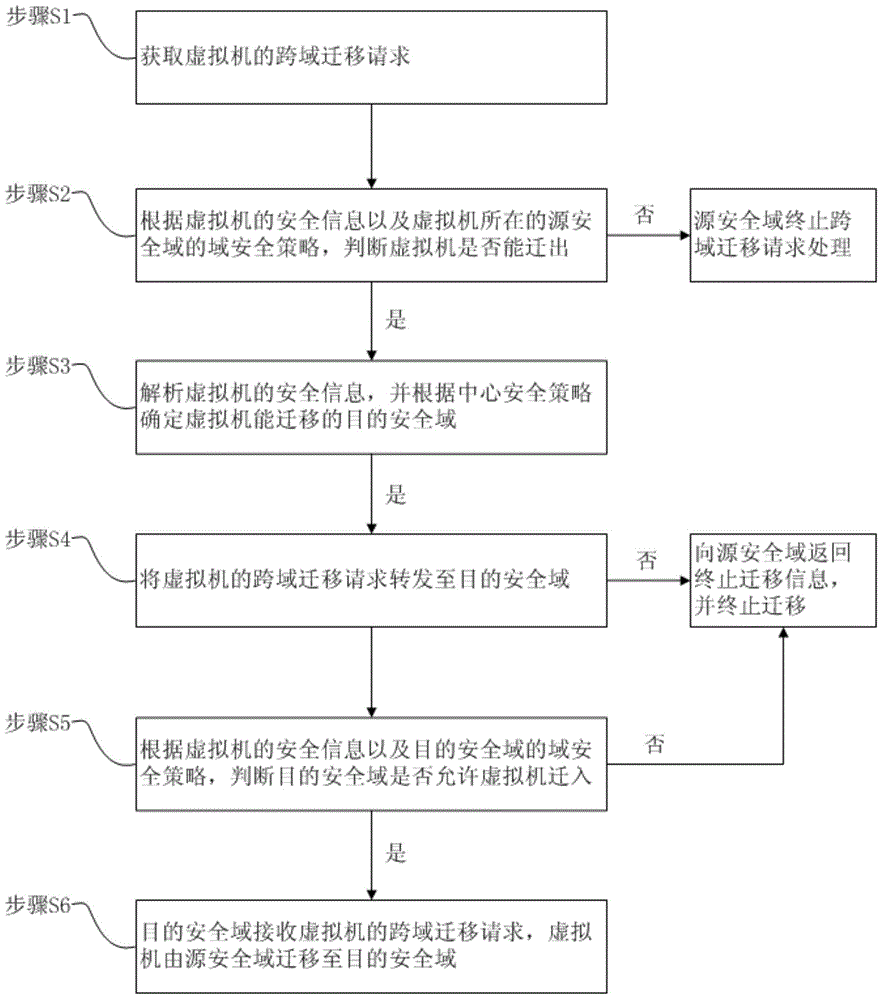
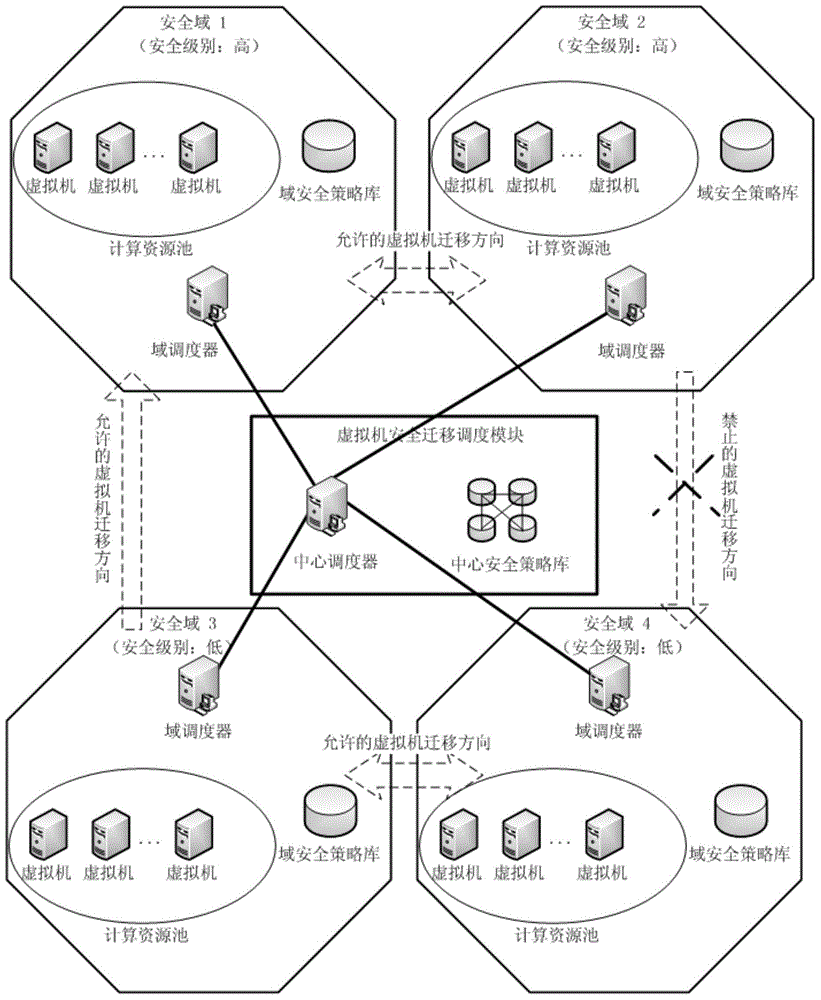
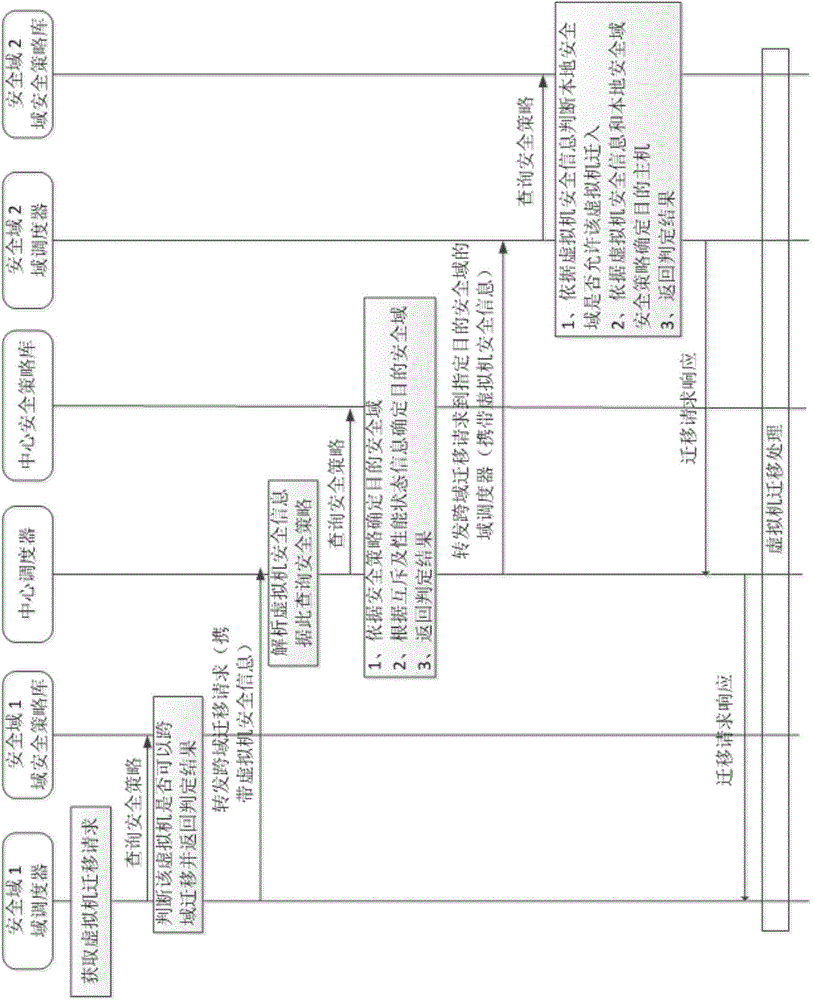
ActiveCN104158826AAvoid safety hazardsGuarantee security strengthResource allocationTransmissionSecurity policyVirtual machine
The invention provides a scheduling method for virtual machine migration. The scheduling method includes the flowing steps that S1, a cross-domain migration request of a virtual machine is obtained; S2, whether the virtual machine can be migrated out or not is judged according to safety information of the virtual machine and the domain safety strategy of a source safety domain where the virtual machine is located; S3, if yes, the safety information of the virtual machine is parsed, and the target safety domain to which the virtual machine can be migrated is determined according to the central safety strategy; S4, the cross-domain migration request of the virtual machine is transferred to the target safety domain; S5, whether the target safety domain allows the virtual machine to be migrated to the target safety domain or not is judged according to the safety information of the virtual machine and the domain safety strategy of the target safety domain; S6, if yes, the target safety domain receives the cross-domain migration request of the virtual machine, and the virtual machine is migrated to the target safety domain from the source safety domain. By means of the scheduling method and system for virtual machine migration, potential safety hazards caused by migration of the virtual machine can be avoided, optimizing operation of system overall performance and load balance are guaranteed, and service safety and performance of the system are taken into consideration as well.
Owner:CEC CYBERSPACE GREAT WALL
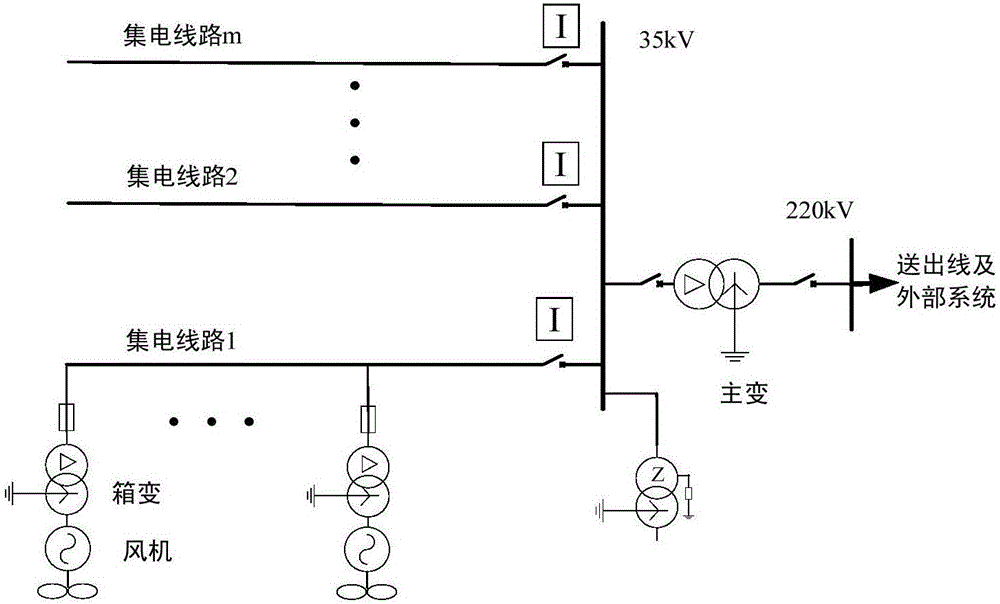
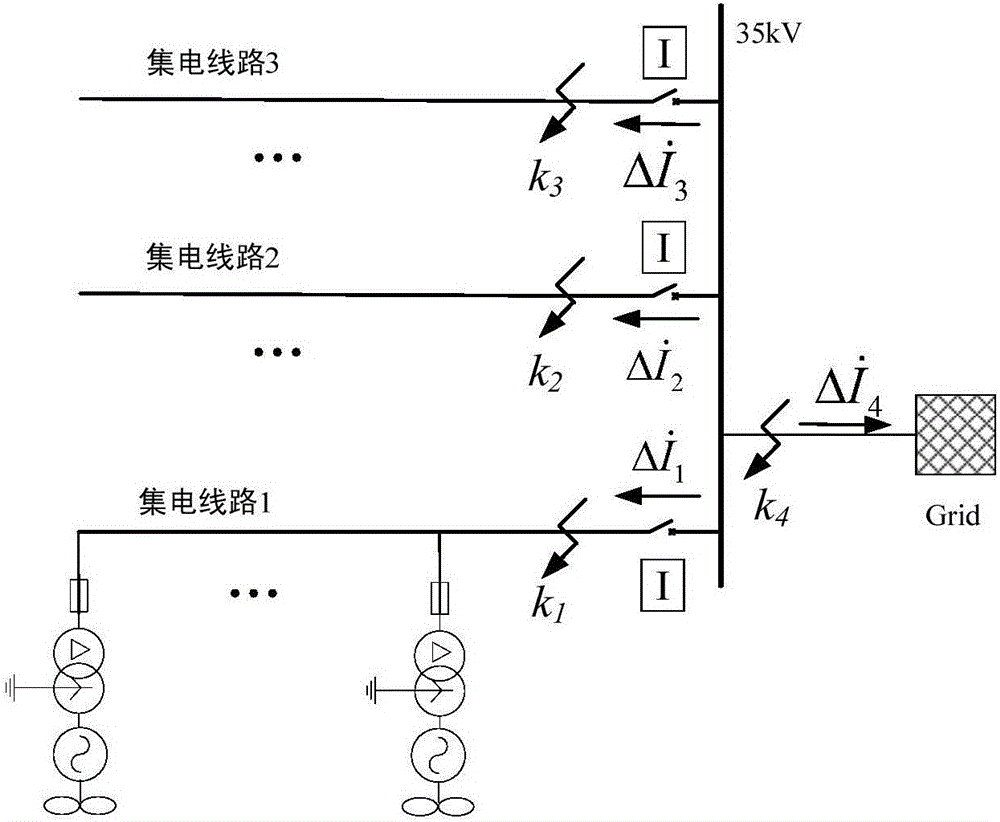
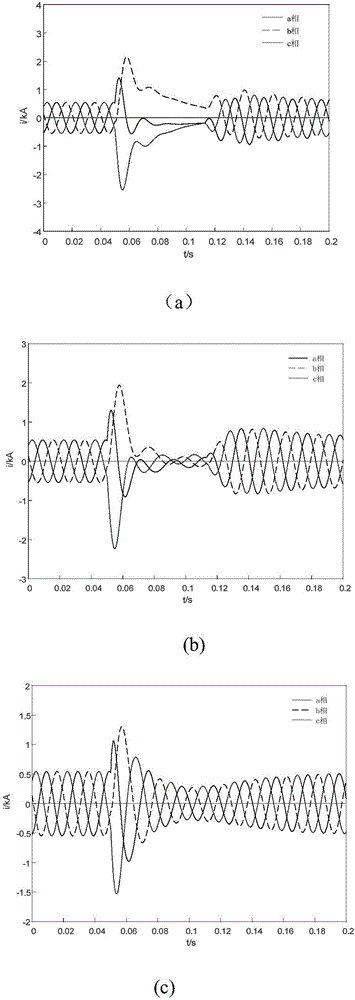
Wave correlation based current protection method for power collecting lines in wind farm
InactiveCN106786427ASufficient reliabilityIncrease the requirements of the four sexesEmergency protective circuit arrangementsCorrelation coefficientPower flow
The invention relates to a wave correlation based current protection method for power collecting lines in a wind farm. The method comprises the following steps: firstly, three-phase current in protective mounting position of each power collecting line in the wind farm is collected; filtering is performed, and fault component current of each phase is extracted by programming; correlation coefficients of the phases between the power collecting lines is calculated according to the fault component current, and the correlation coefficients are traversed pairwise; if the correlation coefficient of one phase belongs to (0, 1], the phase of the two power collecting lines has no fault, and the two power collecting lines are written as line i and line j; if the correlation coefficient of the one phase does not belong to (0,1], the phase of one and only one of the two power collecting lines has a fault, and the two power collecting lines are written as line u and line v; at the moment, when the correlation coefficient of the phase between the line u and the line j belongs to (0,1], the phase of the power collecting line u has no fault, while the phase of the power collecting line v has a fault; when the correlation coefficient of the phase between the line u and the line j does not belong to (0,1], the phase of the power collecting line u has a fault, while the phase of the power collecting line v has no fault.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING) +1
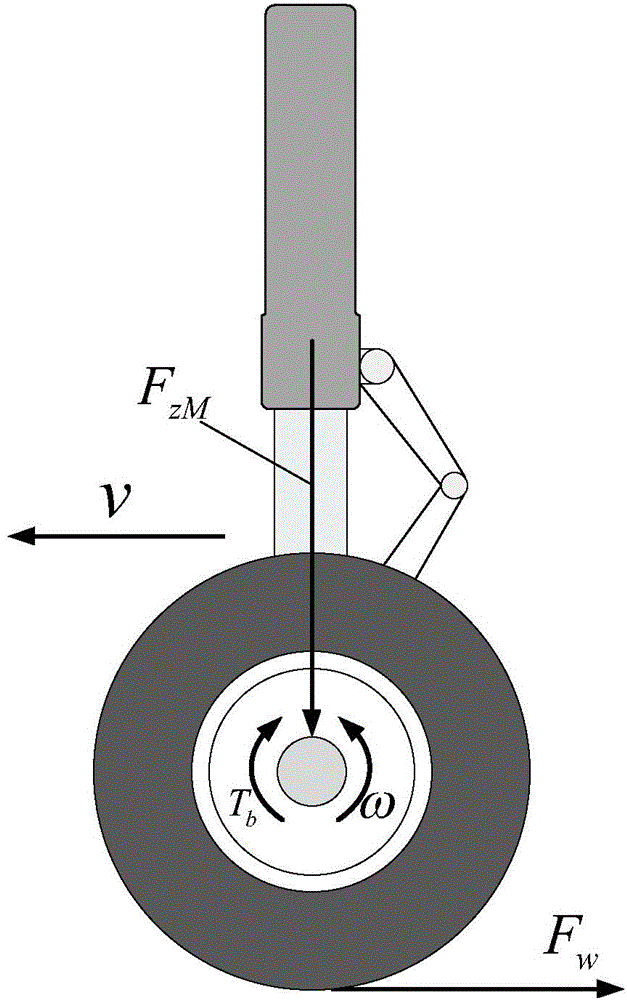
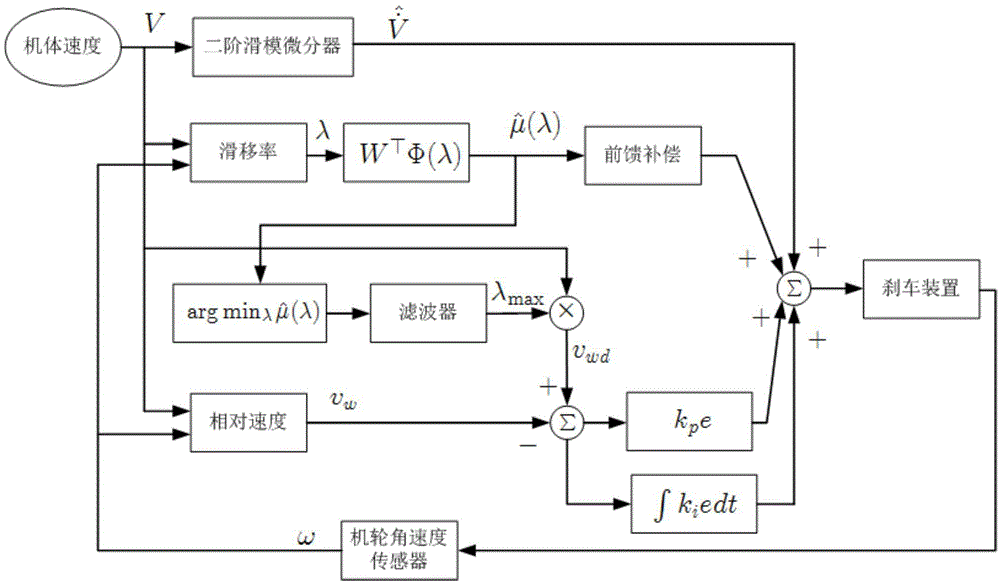
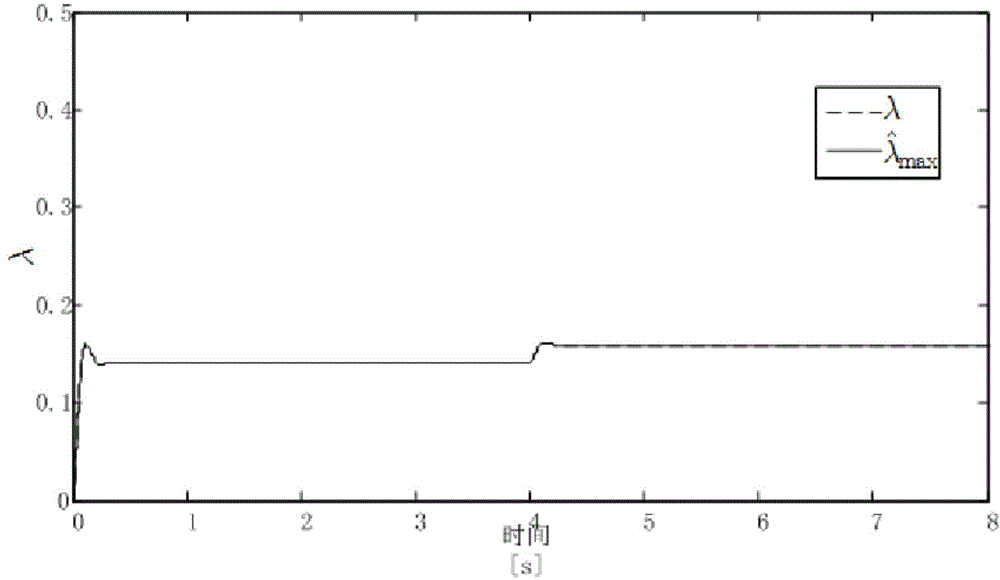
Aircraft anti-skid brake control method
InactiveCN103552685AAvoid learning to identifyTaking into account efficiencyAircraft braking arrangementsBraking systemsReduction rateDifferentiator
The invention relates to an aircraft anti-skid brake control method. According to the aircraft anti-skid brake control method, an aircraft reduction rate signal is constructed by means of the robustness and anti-interference characteristics of a tracking differentiator or a second-order sliding mode differentiator, and is used for calculating slip force, and learning identification in a longitudinal dynamics process is avoided. According to the method, braking longitudinal force does not need to be assumed to be uniformly distributed, and the method can be used for a multi-wheel brake system. In addition, a safety operation range of the brake system is considered, the brake pressure is constrained, the anti-skid brake efficiency and anti-lock safety are considered simultaneously, and the method has certain advancement.
Owner:渭南高新区晨星专利技术咨询有限公司
Single-power-source automatic double door controlled by crank double-slider mechanism
ActiveCN104612545AThe structure is novel and uniqueEasy to operateWing operation mechanismsConstruction fastening devicesAutomatic controlPulley
A single-power-source automatic double door controlled by a crank-slider mechanism is composed of a right door body, a first shaft, a first connection bridge, a first spring, a first fixed rod, a connecting rope, a fixed pulley, a first fixed disk, a second shaft, a second connection bridge, a second spring, a second fixed rod, a second fixed disk, a door frame, a first pin shaft, a first joint lever, a second pin shaft, a second joint lever, a first slider, a third pin shaft, a third joint lever, a second slider, a fourth pin shaft, a rail, a fourth joint lever, a fifth pin shaft, a third slider, a fifth joint lever, a left door body, a sixth pin shaft, a sixth joint lever, a seventh pin shaft, a lever, a rotation shaft, a fixed block and an ejector rod. Compared with an existing single door, the single-power-source automatic double door can achieve opening and closing of the doors and a lock through automatic control, the operation is easier and more convenient when controlling is performed, the single-action-source automatic double-leave door can be opened and closed both inwards and outwards, and therefore the theftproof performance is better; meanwhile, the single-power-source automatic double door can be made of materials such as wood, metal and glass, and therefore the double door has the advantages of low cost, aesthetic property, practicability and safety.
Owner:湖州市双林工业园区开发有限公司
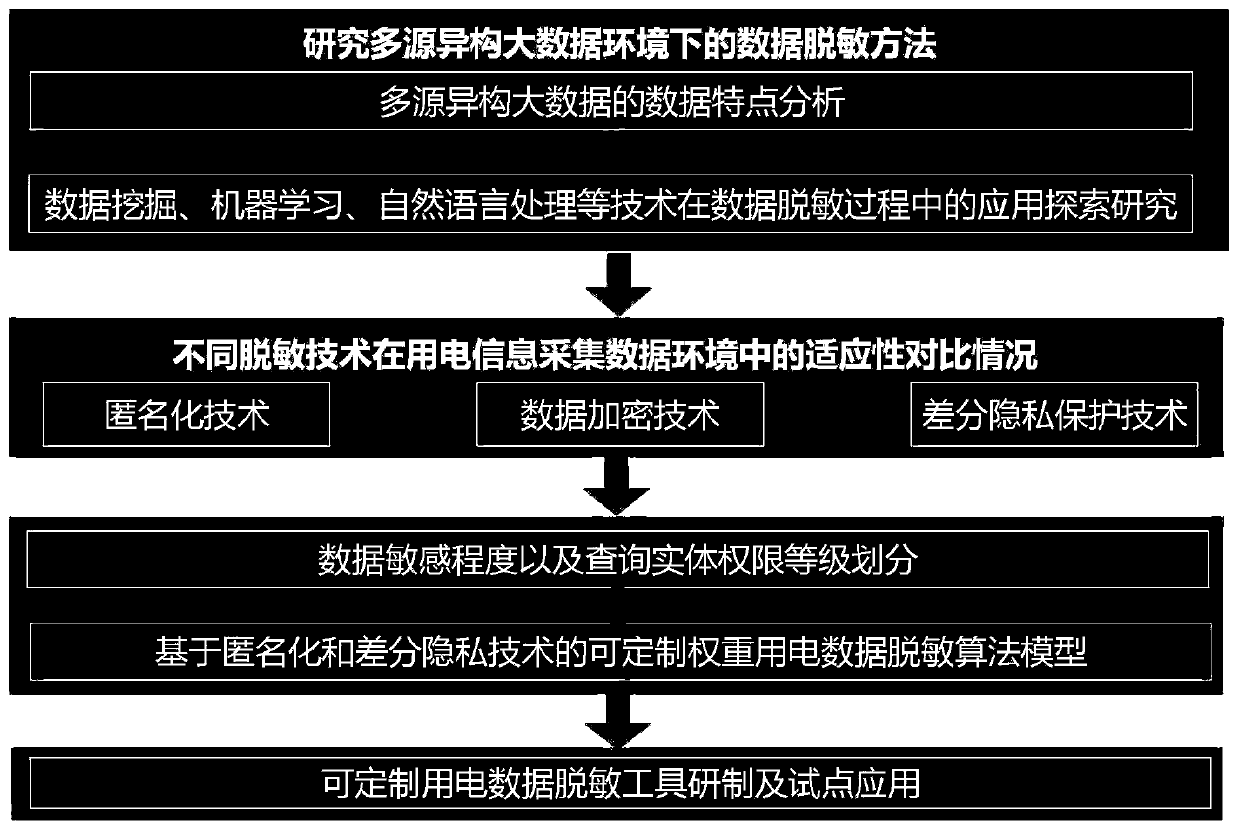
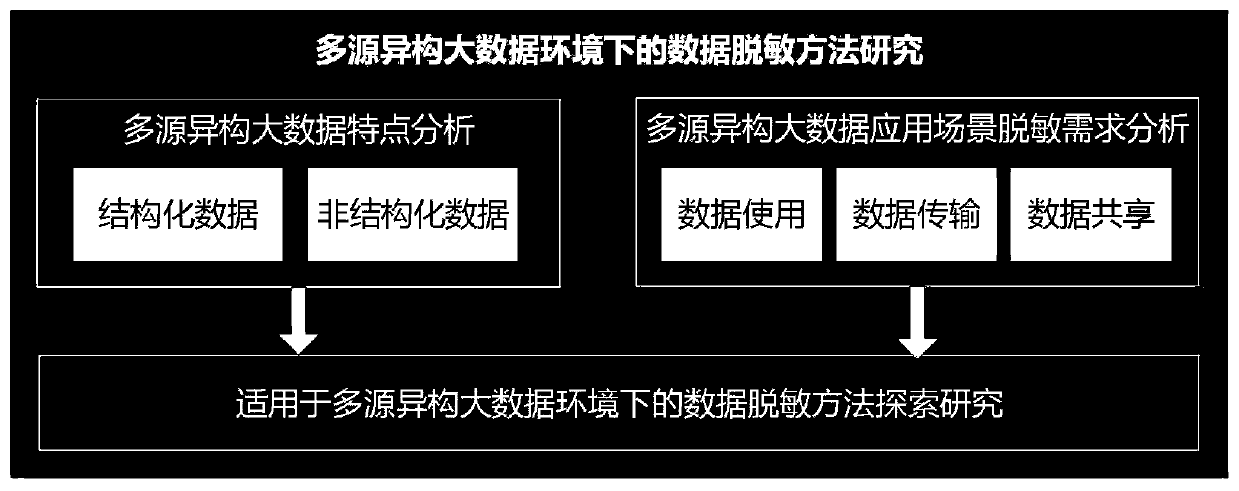
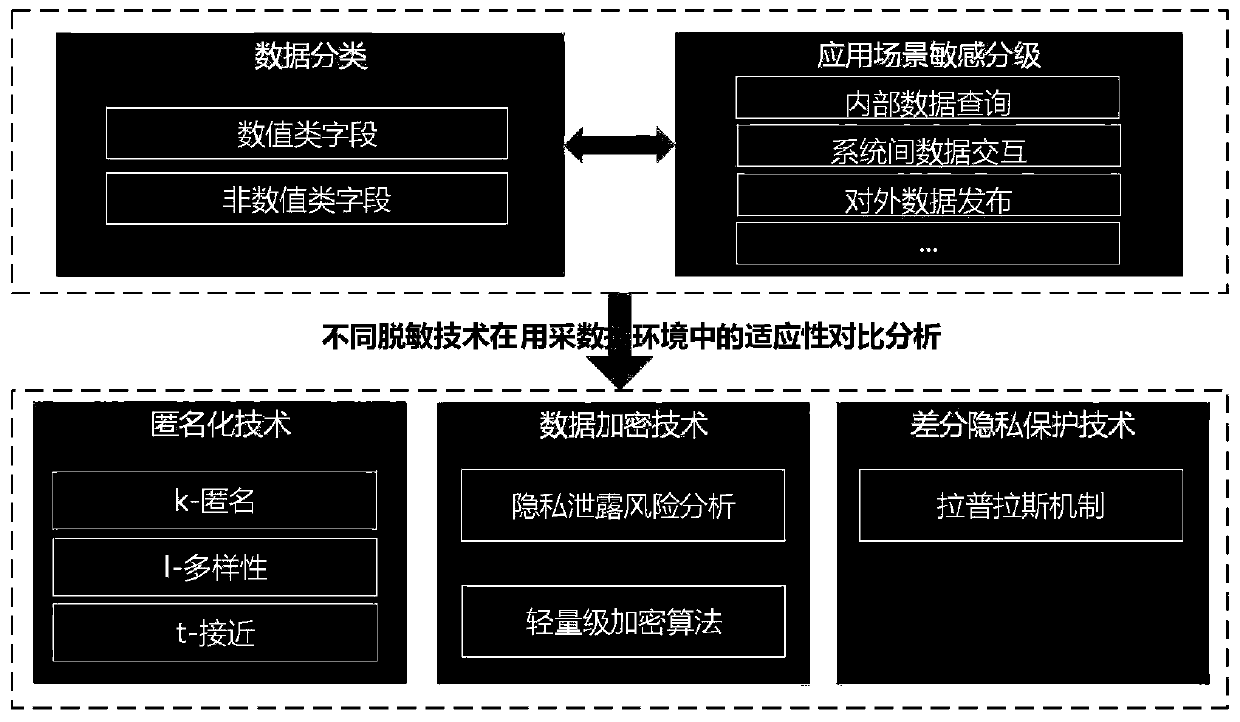
Power consumption data desensitization algorithm model construction method based on anonymization privacy technology
PendingCN110851860AMeet desensitization needsConvenienceData processing applicationsDigital data protectionInformation sharingDifferential privacy
The invention relates to a power consumption data desensitization algorithm model construction method based on an anonymization privacy technology. The method is characterized by comprising the following steps of 1, researching a data desensitization method in a multi-source heterogeneous big data environment; 2, analyzing and comparing the adaptability conditions of anonymization, data encryptionand differential privacy technologies in a power consumption information acquisition data environment; 3, constructing a power consumption data desensitization algorithm model based on anonymizationand differential privacy technologies; and step 4, researching and developing a power consumption data desensitization tool and carrying out trial point application. The invention discloses a power utilization data desensitization algorithm model construction method based on an anonymization privacy technology. A customizable power consumption data desensitization algorithm model is constructed; the desensitization requirements of different users can be accurately met, the convenience and safety of information sharing are considered, the privacy safety of sensitive data in use, release and sharing links in marketing and acquisition systems is guaranteed, and the leakage risk of mass power marketing data, power customer data and personal power consumption information of state grid companiesis effectively reduced.
Owner:ELECTRIC POWER SCI & RES INST OF STATE GRID TIANJIN ELECTRIC POWER CO +2
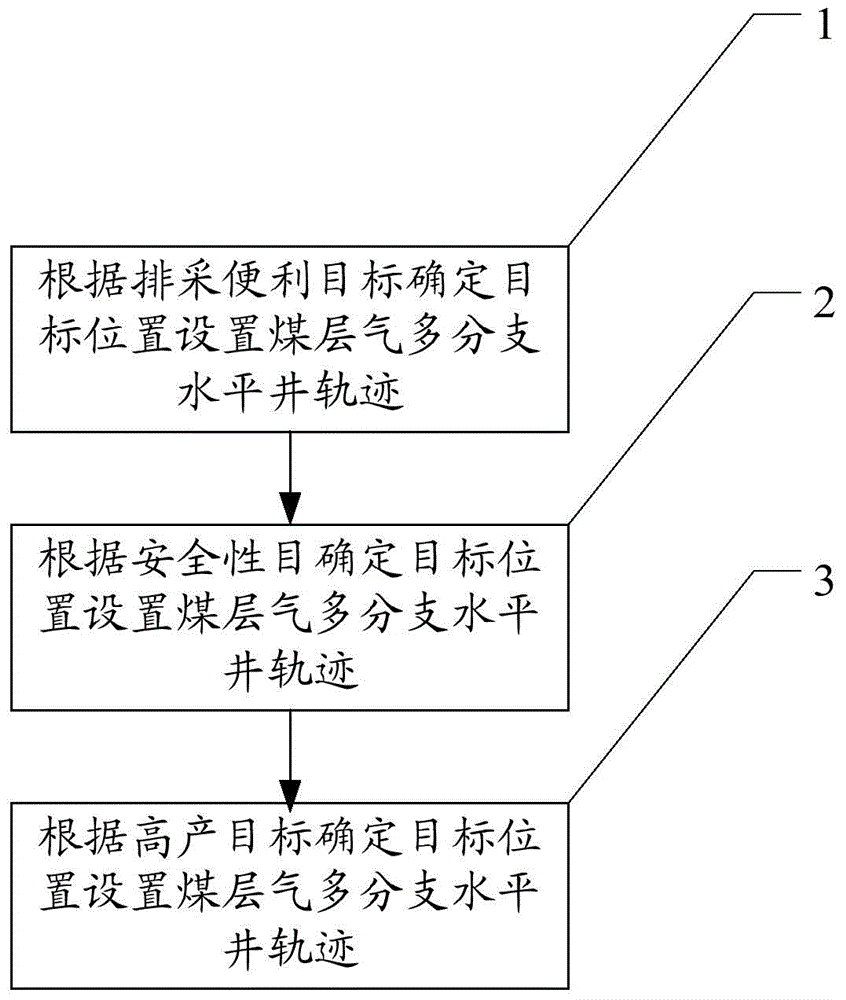
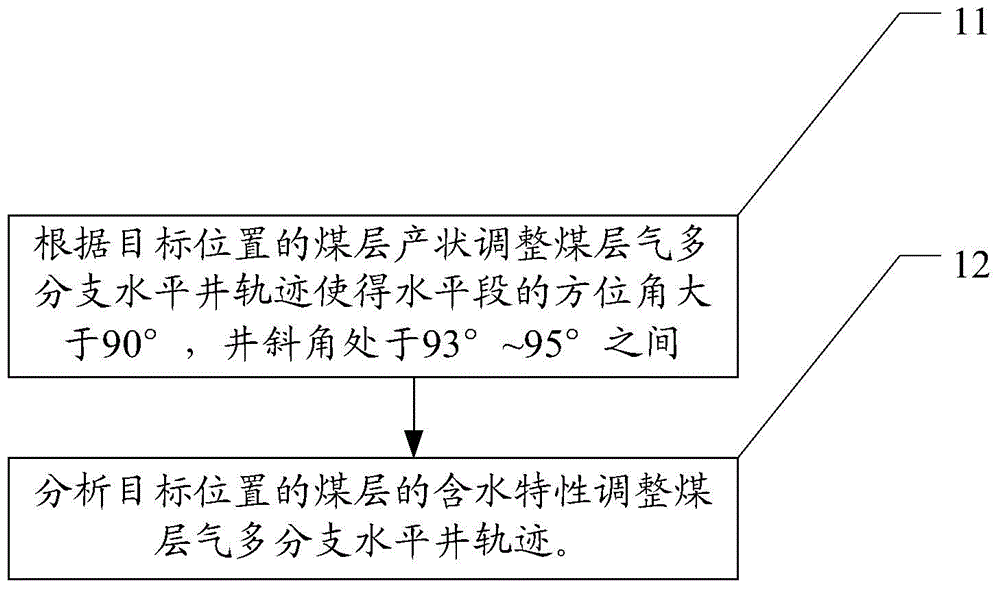
Optimization method for coal bed gas multi-branch horizontal well trajectory
InactiveCN104453835AImprove convenienceTake security into considerationFluid removalCoalEnvironmental geology
The embodiment of the invention discloses an optimization method for a coal bed gas multi-branch horizontal well trajectory. The optimization method for the coal bed gas multi-branch horizontal well trajectory includes the steps that (1) the coal bed gas multi-branch horizontal well trajectory is set according to the discharge and mining convenience target determined target location; (2) the coal bed gas multi-branch horizontal well trajectory is set according to the safety target determined target location; (3) the coal bed gas multi-branch horizontal well trajectory is set according to the high-yield target determined target location. According to the scheme, the coal bed gas multi-branch horizontal well trajectory is optimized by meeting the requirements for geology, drilling and completion, discharge and mining and the like, so that by adoption of the scheme, the requirements for discharge and mining convenience, safety and high yield are met.
Owner:CHINA UNITED COALBED METHANE
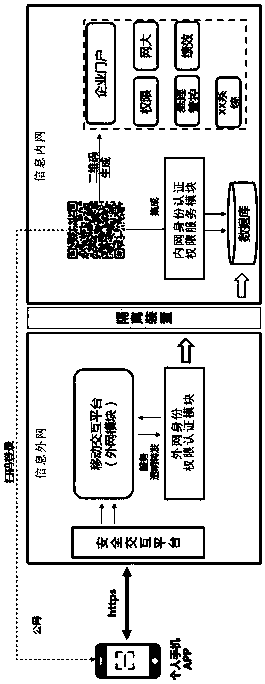
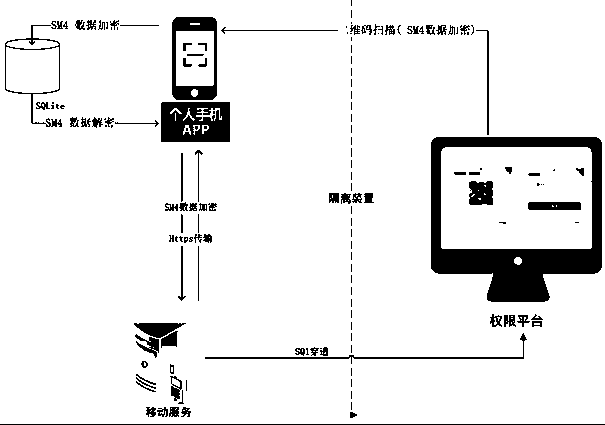
Password-less login realization method based on enterprise-level intranet and extranet environment
InactiveCN107733861ATake security into considerationTake care of the login processTransmissionPasswordEnterprise level
The invention discloses a password-less login realization method based on enterprise-level intranet and extranet environment. The method specifically comprises the following steps: step S100, scanningQR code through an APP by using any communication electronic equipment with code-scanning function; step S200, logging in the QR code and acquiring the information in the QR code, sending the information to a mobile interaction platform of the enterprise through a national encryption algorithm SM4 data encryption way; step S300, judging whether the QR code scanned in the step S100 is the directlylinked intranet authentication service or extranet authentication service, and then performing the routing strategy matching; step S310, requesting an extranet permission platform to perform the authentication if the QR code is the extranet authentication service; and accessing an intranet database through an isolating device SQL penetrating way if the QR code is the intranet authentication service; and accomplishing the authentication service. By using the QR code identification login, a problem that the intranet login of the traditional enterprise performs the authentication by inputting the account and password is avoided, the security is improved, and meanwhile, the non-technical measure leakages of request interception, hijacking and like are avoided.
Owner:SICHUAN ZHONGDIAN AOSTAR INFORMATION TECHNOLOGIES CO LTD
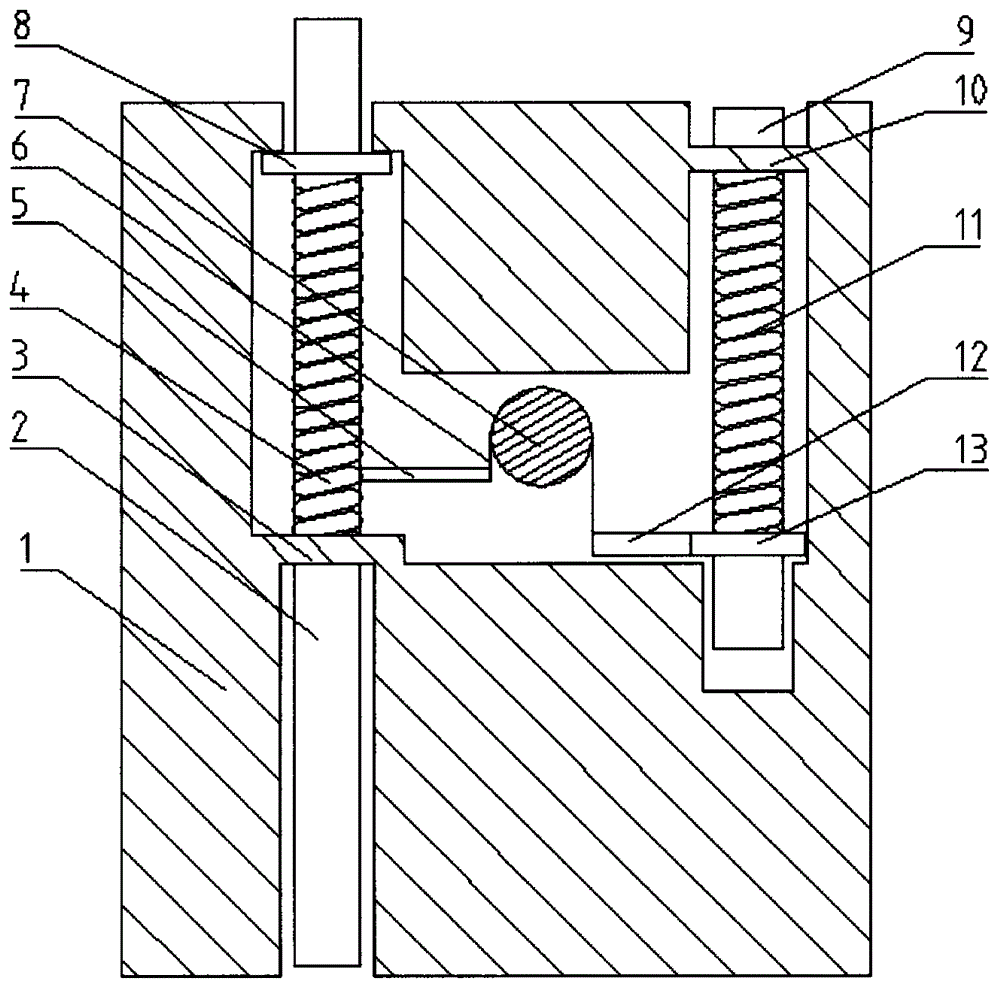
Solenoid valve assembly externally arranged on absorber and absorber
InactiveCN105782324AContinuously adjustable dampingDamping adjustment responds quicklyOperating means/releasing devices for valvesSpringsSolenoid valveOil pressure
The invention provides a solenoid valve assembly externally arranged on an absorber and the absorber. The solenoid valve assembly externally arranged on the absorber comprises a solenoid valve part and an overflow valve. The solenoid valve part comprises a solenoid valve deck, a solenoid valve body, a coil, a solenoid valve element, an armature, a first spring and a second spring. The overflow valve comprises an overflow valve deck provided with open holes formed in the two ends in the axial direction, an overflow valve body provided with an oil inflow hole and an overflow hole, an overflow valve seat provided with a center hole, an overflow adjusting assembly, an overflow valve element, a pressure adjusting spring and a supporting piece. Through the overflow valve of the solenoid valve assembly externally arranged on the absorber, damping adjustment can be achieved through the overflow adjusting assembly of the overflow valve when the oil pressure is small and a throttling hole is closed, so that the solenoid valve assembly externally arranged on the absorber is high in damping adjustment response speed, stable in performance and capable of meeting the requirements that damping force is adjusted continuously in real time in the suspension frame movement process.
Owner:GUANGZHOU AUTOMOBILE GROUP CO LTD
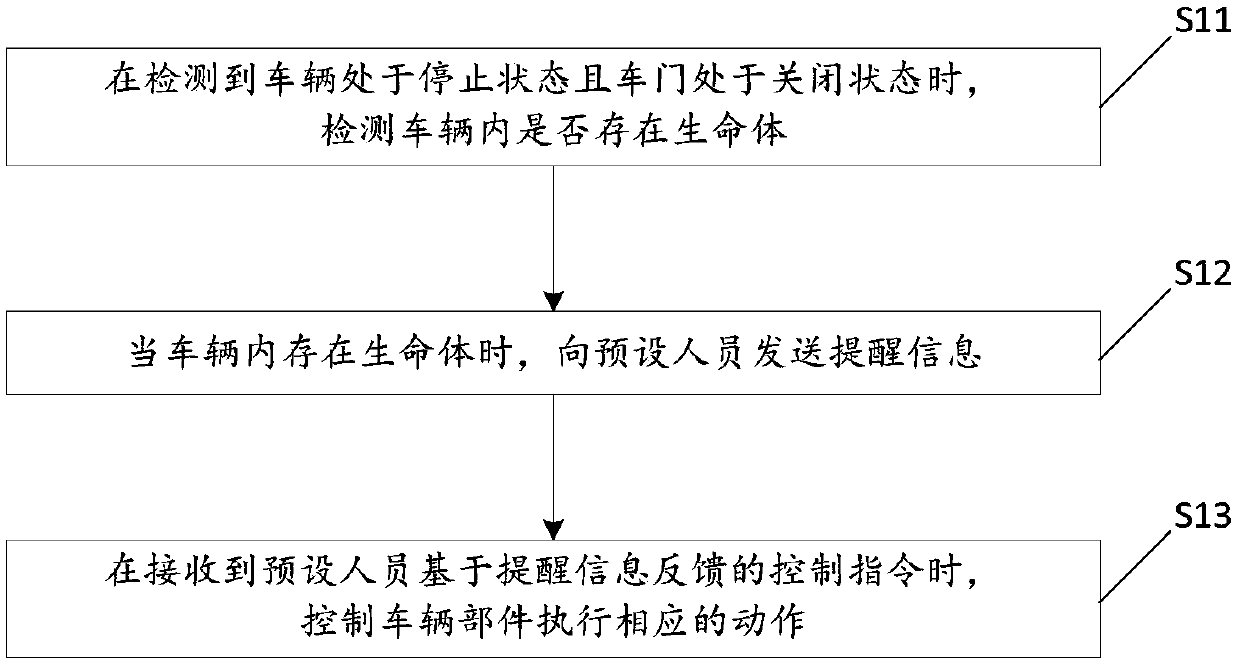
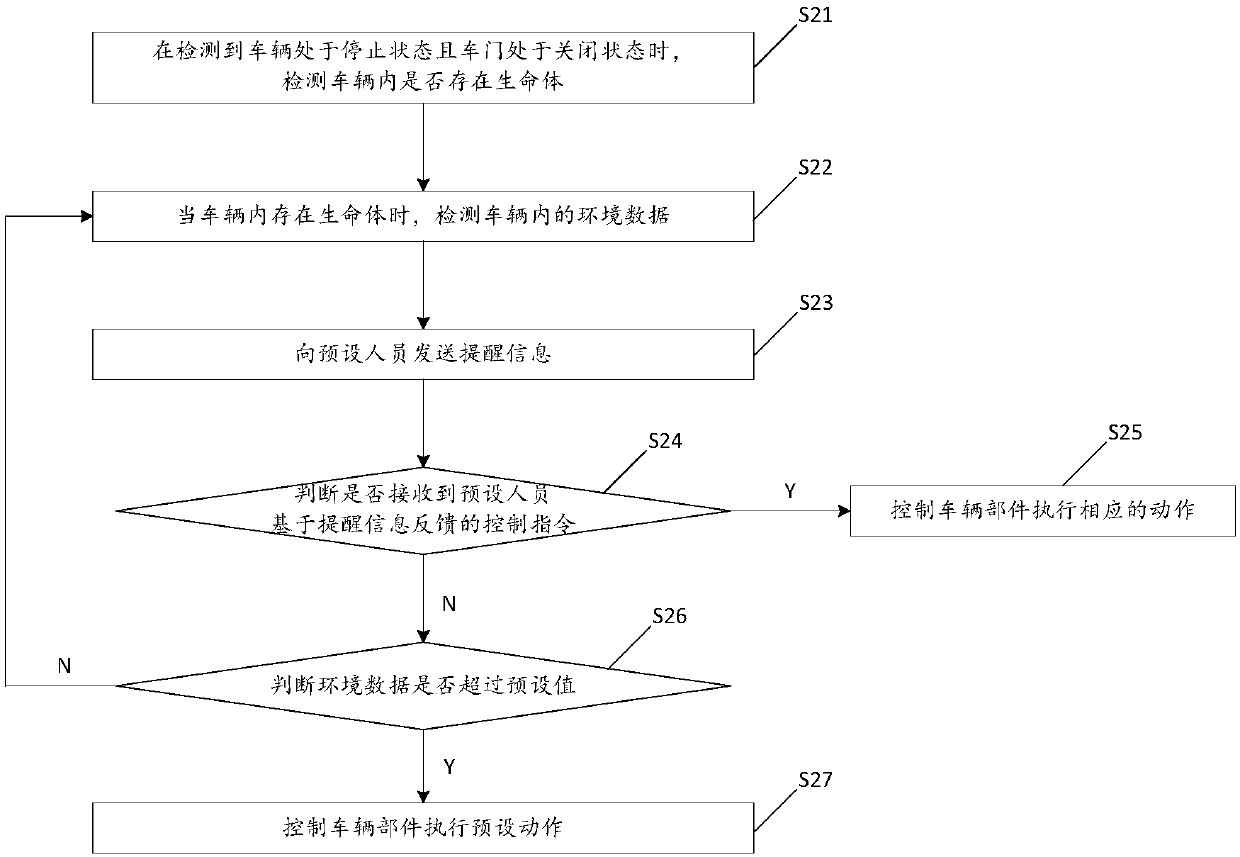
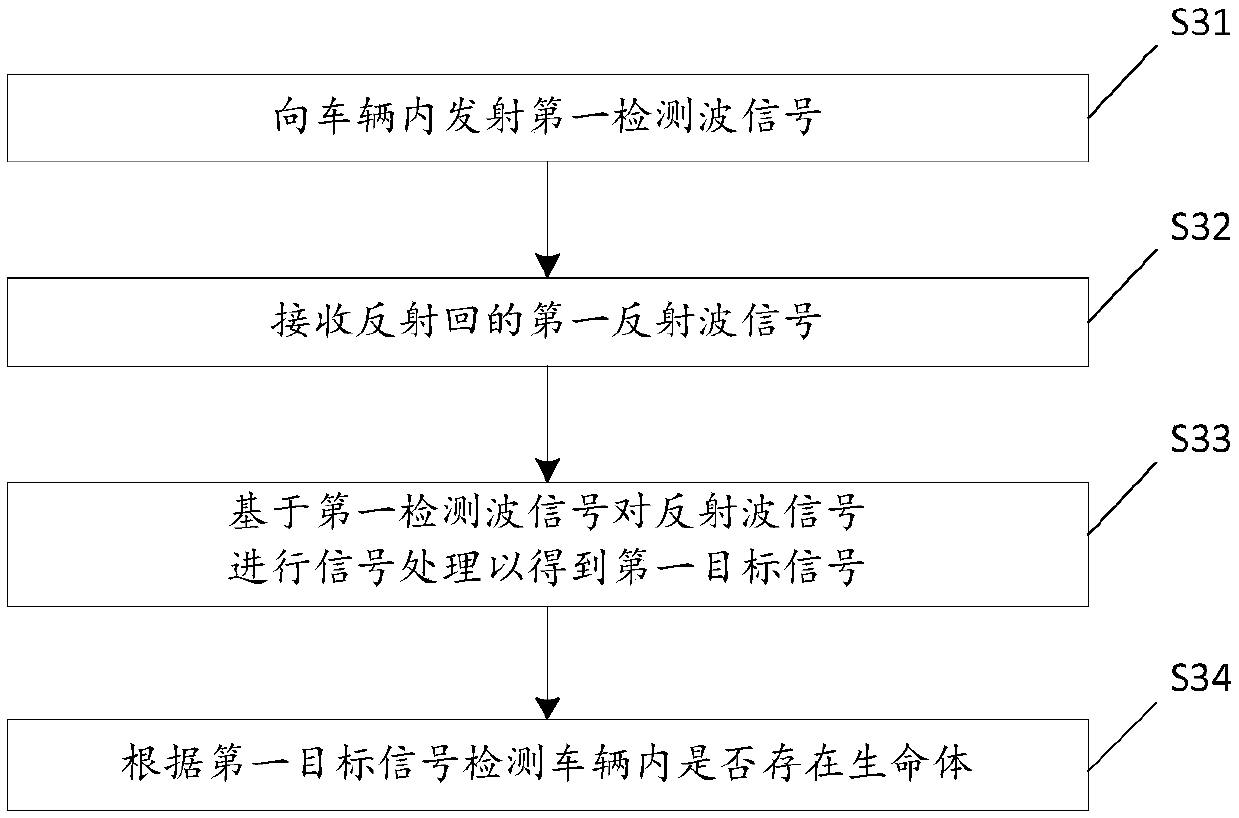
In-vehicle living thing warning method and device
ActiveCN109532742AImprove securityImprove accuracyAir-treating devicesPedestrian/occupant safety arrangementIn vehicleEngineering
The invention relates to the technical field of living thing detection, in particular to an in-vehicle living thing warning method and device. The method comprises the steps that when it is detected that a vehicle is in a stopping state, and a door of the vehicle is in a closing state, whether or not living things exist in the vehicle; if yes, a warning message is sent to a pre-installing person;when a control command fed back by the pre-installing person is received based on the warning message, vehicle components are controlled to execute corresponding operation. According to the method, when it is detected that the living things exist in the vehicle, the warning message is sent to the pre-installing person, and when the feedback control command is received, the vehicle components are controlled to execute corresponding operation, that is, the warning message is sent to the pre-installing person to warn the pre-installing person of existing of the living things, it is ensured that the vehicle components can execute corresponding operation according to the control command of the pre-installing person, and the safety of the living things in the vehicle is improved.
Owner:SENSEED TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com