Password-less login realization method based on enterprise-level intranet and extranet environment
An implementation method, the technology of internal and external networks, applied in the field of convenient login of LAN users, can solve problems such as doubtful security, unfavorable promotion and access, cumbersome memory of account passwords, etc., and achieve good scalability effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0053] At first, before explaining the solution method that the present invention adopts, the terms or concepts involved in the present invention are explained as follows:
[0054] Secretless login: Secretless login refers to a login method that is different from the traditional login method and based on a specific application scenario. It does not need to use an account password to complete login authentication. It does not specifically refer to a certain login implementation. .
[0055] Two-dimensional code: Two-dimensional code is also called QR Code, and the full name of QR is Quick Response. It is a very popular coding method on mobile devices in recent years. It can store more information than the traditional Bar Code More data types: such as: characters, numbers, Japanese, Chinese, etc.
[0056] SSO: Single Sign-on single sign-on.
[0057] SSL: (Secure Sockets Layer) protocol, and its successor TLS (TransportLayer Security) protocol, is a security protocol that provid...
Embodiment 2
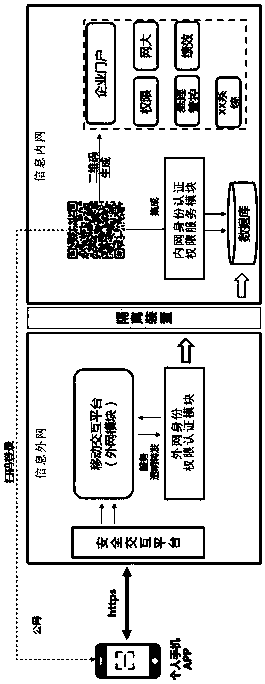
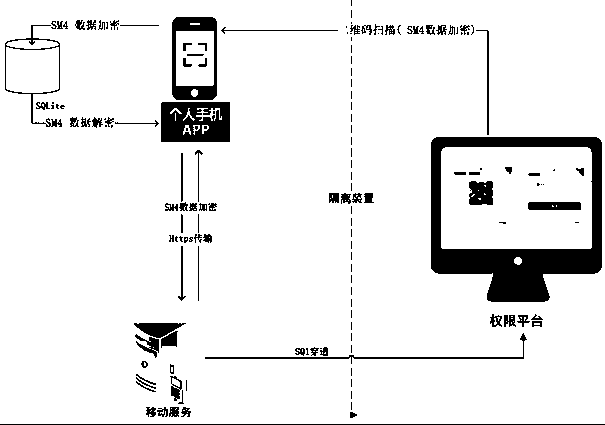
[0085] combined with figure 2 As shown, a passwordless login implementation method based on an enterprise-level internal and external network environment is to use a mobile electronic device with the function of scanning a two-dimensional code to scan the two-dimensional code to obtain the data information of the specified enterprise intranet, including as Communication mobile electronic devices with code-scanning functions that are convenient for users to access on the mobile terminal, information extranet and information intranet for wireless communication with the electronic devices:
[0086]The information extranet includes a secure interactive platform communicating with electronic devices including https, and an extranet identity authority authentication module for exchanging data with the secure interactive platform; and
[0087] The information intranet includes a database for storing user information, and an intranet identity authentication authority service module f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com