Internet of things system and acquisition and monitoring method for article information
An Internet of Things system and item information technology, which is applied in the field of Internet of Things system and item information acquisition and monitoring, can solve the problems of lack of middle layer, difficulty in building the Internet of Things, singleness, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0098] The technical solutions of the present invention will be further described below in conjunction with the accompanying drawings and through specific implementation methods.
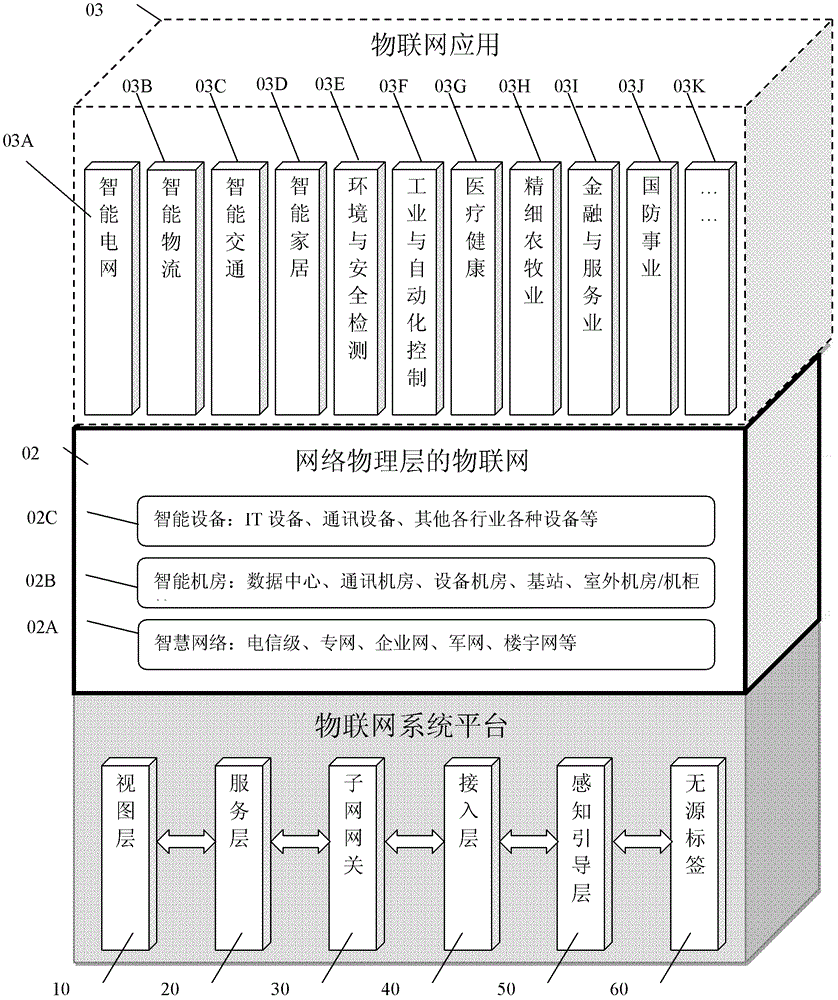
[0099] figure 1 It is a schematic diagram of the overall structure of the Internet of Things application system of the present invention. The Internet of Things application system of the present invention includes three parts, the Internet of Things system platform 01, the Internet of Things 02 at the physical layer of the network, namely "Internet of Things", and the Internet of Things application 03.
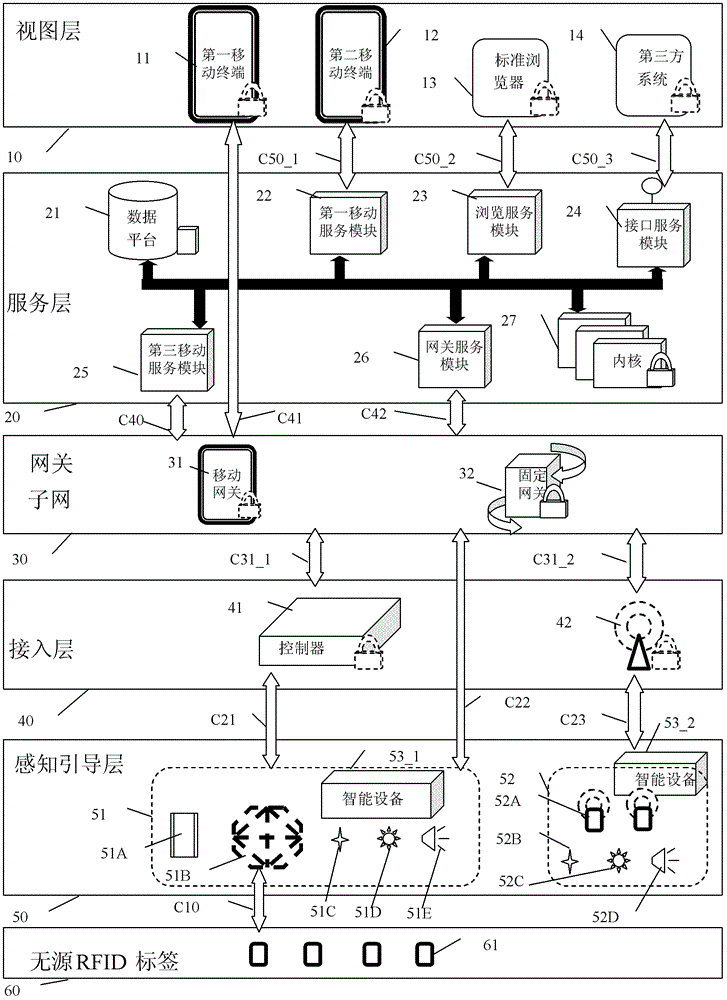
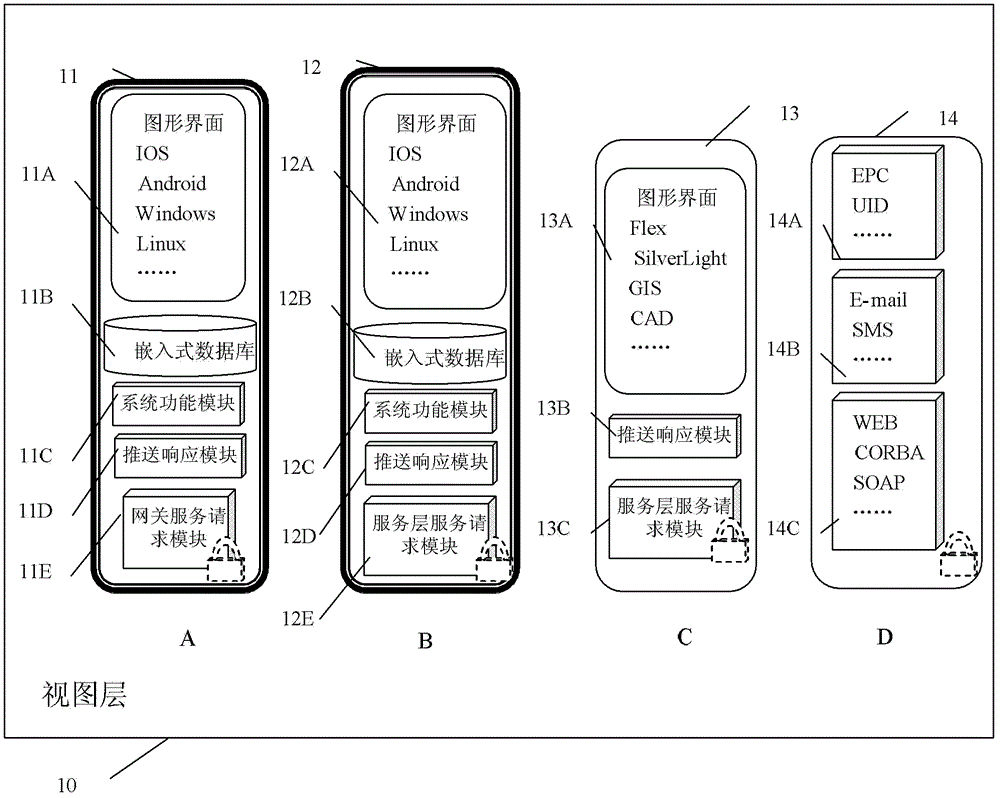
[0100] Among them, the IoT system platform is divided into six layers, namely the view layer 10, the service layer 20, the subnet gateway layer 30, the access layer 40, the perception guidance layer 50 and the passive RFID electronic tag 60. A complete IoT system basically consists of some or all of these six parts.
[0101] The Internet of Things at the network physical layer is a typical Interne...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com