Automatic logion method based on IC card for server with multiple main domains
A server and authorization server technology, applied in the field of identity authentication and strengthening network security, to achieve the effects of ensuring irrelevance, reducing transplant costs, and increasing network burden
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The present invention will be further described through the following embodiments in conjunction with the accompanying drawings.
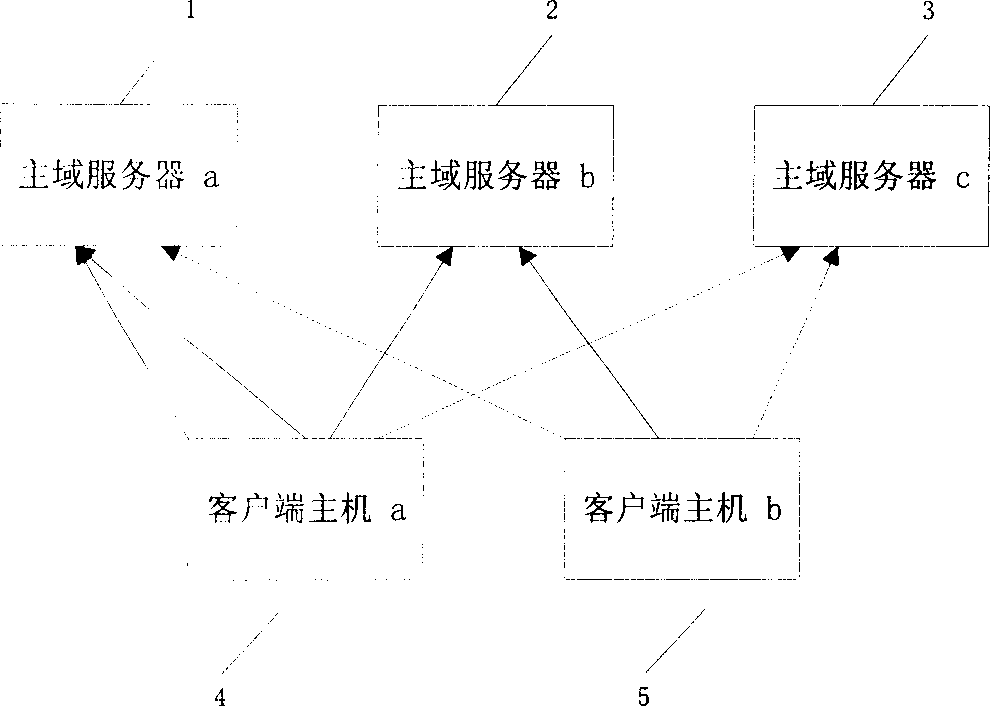
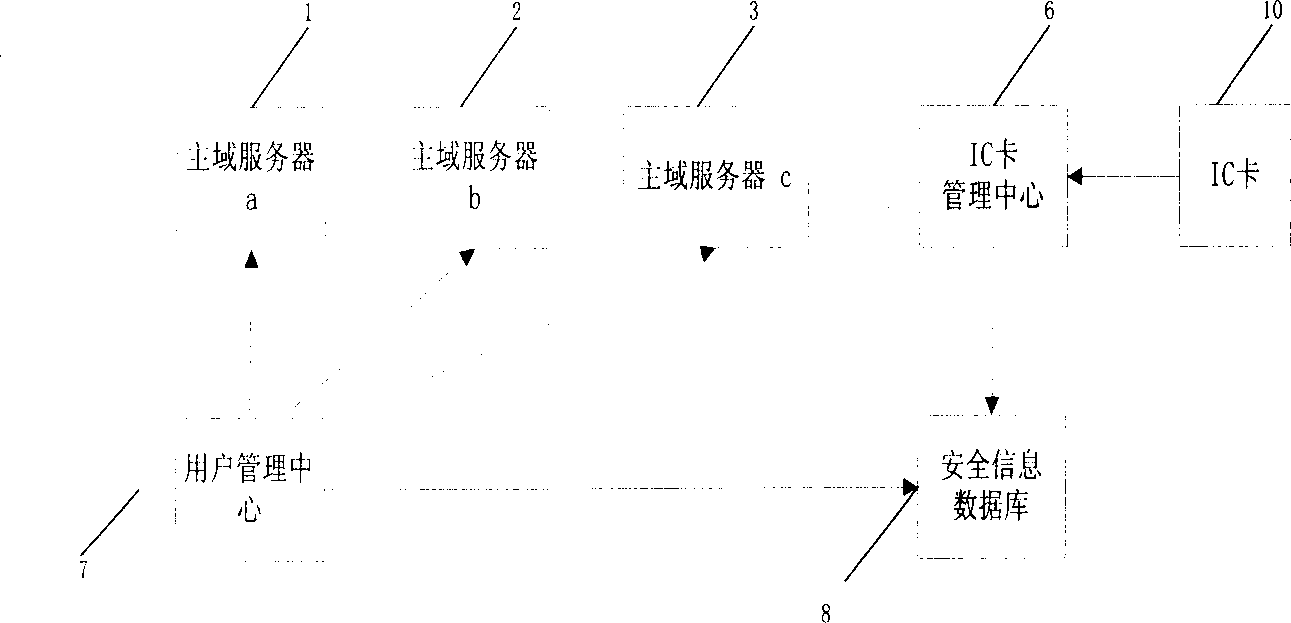
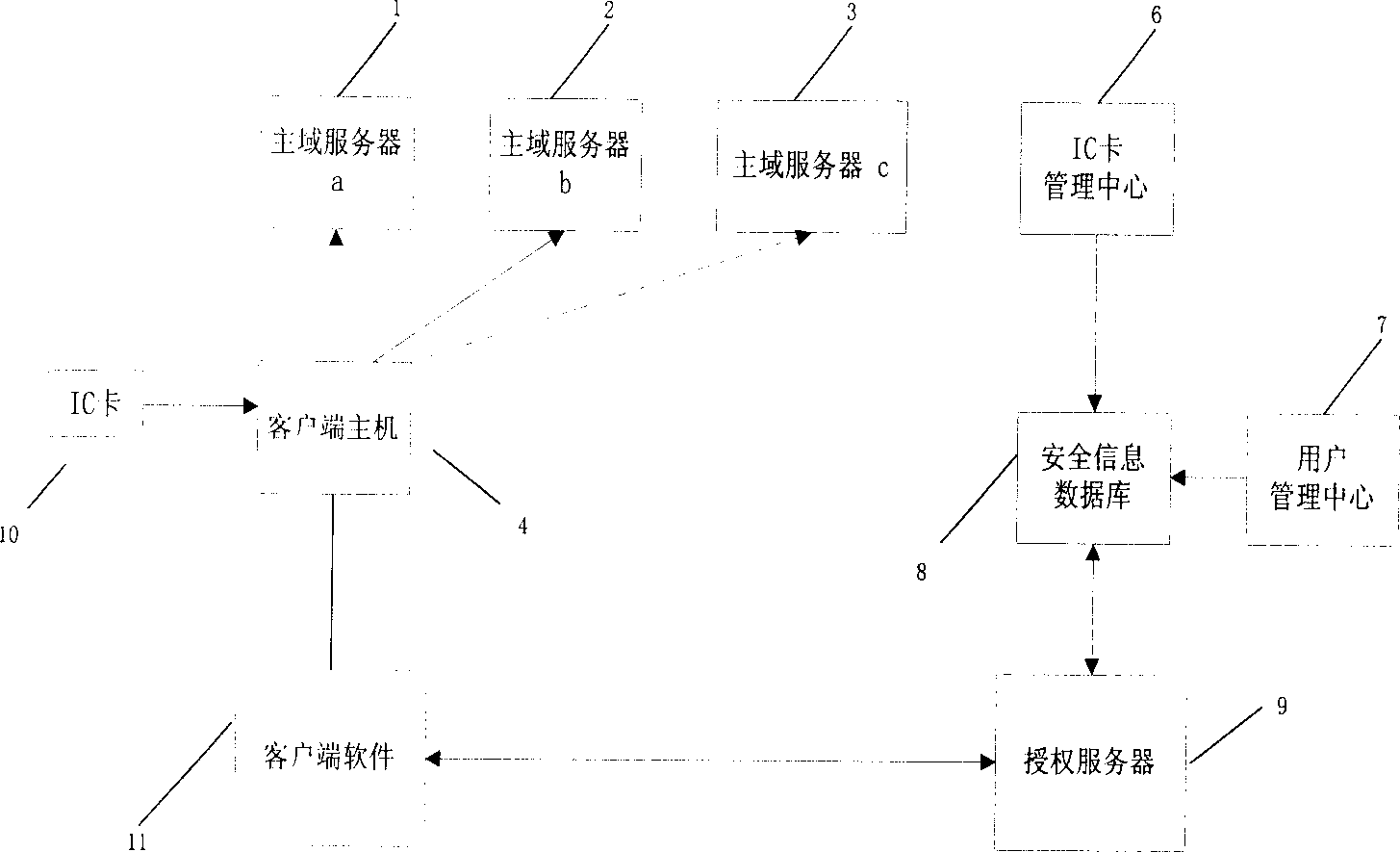
[0041] Described multi-main domain server automatic login method based on IC card is applied in an identity authentication system, and network environment is 100M Ethernet, and hardware equipment comprises HP server or other server, 100M Ethernet card, and operating platform is Chinese Windows NT Server4 .0+Service Pack6. Such as image 3 As shown, the authentication system includes a user management center 7, an IC card management center 6, a security information database 8, a client host 4 with client software 11 installed, an authorization server 9, a main domain server a1, a main domain server b2, a main domain server Domain server c3, the client host 4 is respectively connected with the primary domain server a1, primary domain server b2, and primary domain server c3, and the security information database 8 is respectively connected wit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com