Identity authentication method and device based on security chip, and medium
A security chip and identity authentication technology, applied in the field of identity authentication based on security chips, can solve problems in dangerous environments and achieve the effect of identity authentication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
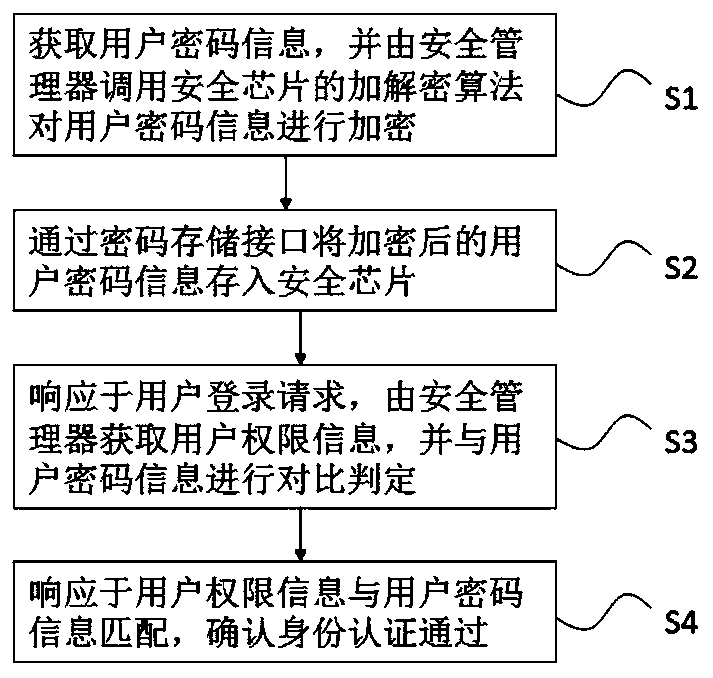
[0030]According to some embodiments of the present invention, the security chip is a TCM trusted cryptographic module security chip. TCM (Trusted Cryptography Module, Trusted Cryptography Module) is a security chip built based on embedded chip technology and completely using the cryptographic algorithm and engine independently developed by my country. The TCM security chip provides basic security services for the system platform and software, and establishes a more secure and reliable system platform environment. Using the TCM security chip can solve the flaw of data insecurity in the shiro security framework. The TCM security chip replaces Shiro's original encryption and decryption algorithm to increase the rate of encryption and decryption. The security data source is inside the TCM security chip, ensuring data privacy.
[0031] It should be pointed out that each step in each embodiment of the security chip-based identity authentication method can intersect, replace, add, a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com