Smart identity authentication method and device for rail transit device
A technology for identity authentication and rail transit, which is applied in the field of intelligent identity authentication methods and devices, and can solve problems such as high cost, long physical distance, and low efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
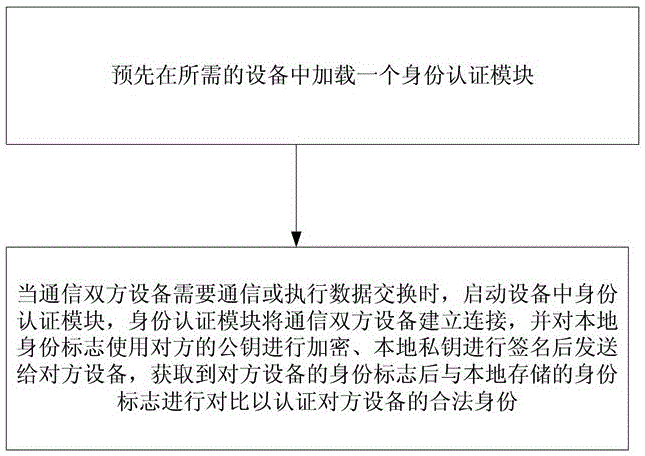
[0071] Such as figure 1 As shown, this embodiment is used for the intelligent identity authentication method of rail transit equipment, and the steps include:
[0072] 1) Pre-load an identity authentication module in the required device;
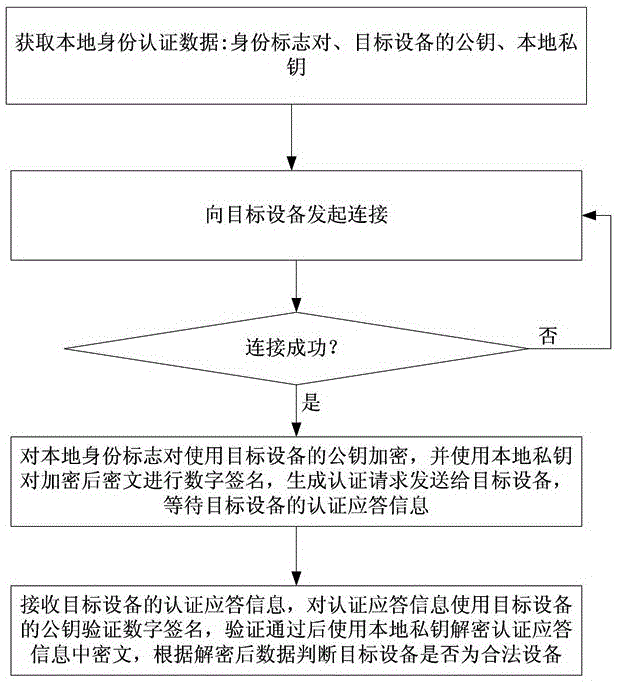
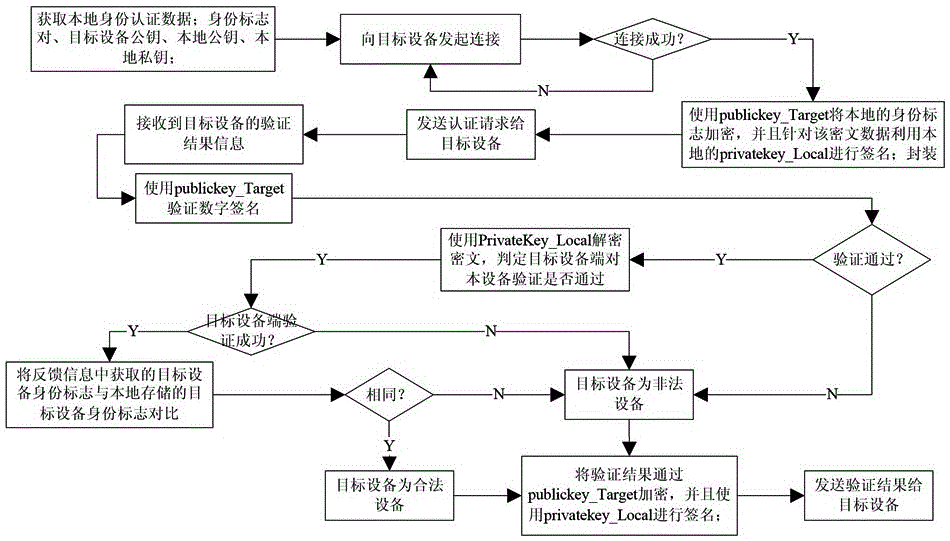
[0073] 2) When the devices on both sides of the communication need to communicate or perform data exchange, start the identity authentication module in the device, the identity authentication module will establish a connection between the two devices of the communication, and encrypt the local identity mark with the public key of the other party and sign it with the local private key Send it to the other party's device, and compare it with the locally stored identity mark after obtaining the identity mark of the other party's device to verify the legal identity of the other party's device.
[0074] In this embodiment, the specific steps of step 2) are: when the source device and the target device need to communicate or perform data exchange...
Embodiment 2
[0116] The difference between this embodiment and Embodiment 1 is that when it is the first identity authentication, the step 2) also includes the intelligent initialization step of the legal identity of the device, such as Figure 5 As shown, the specific steps are:
[0117] S1) Load an initialization module in the required device in advance;
[0118] S2) When the source device communicates with the target device or performs data exchange, if it is the first identity authentication, the initialization module in the source device will be started, and the initialization module will establish a connection between the source device and the target device, and judge whether the local of the source device is connected each time a connection is established. There is a legal identity mark corresponding to the target device, and if it is judged that there is no legal identity mark, the corresponding legal identity mark is obtained from the target device.
[0119] In this embodiment, w...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com