Energy-efficient identity authentication method in multi-level clustering wireless sensor network
A wireless sensor and identity authentication technology, which is applied in the field of computer networks, can solve the problems of affecting the network survival time, the energy consumption of cluster head nodes, and the energy consumption of nodes, so as to avoid the effect of authentication process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
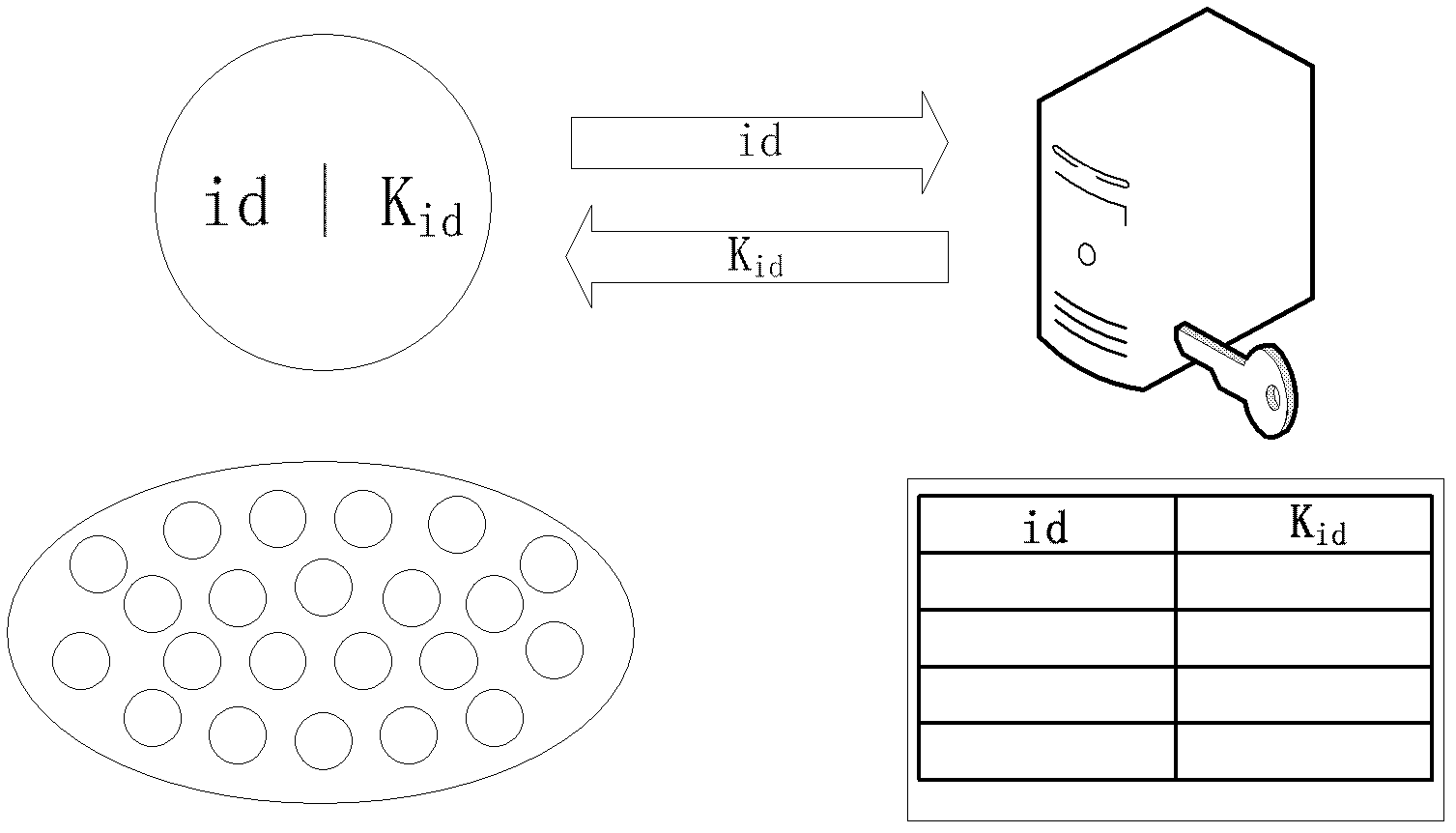
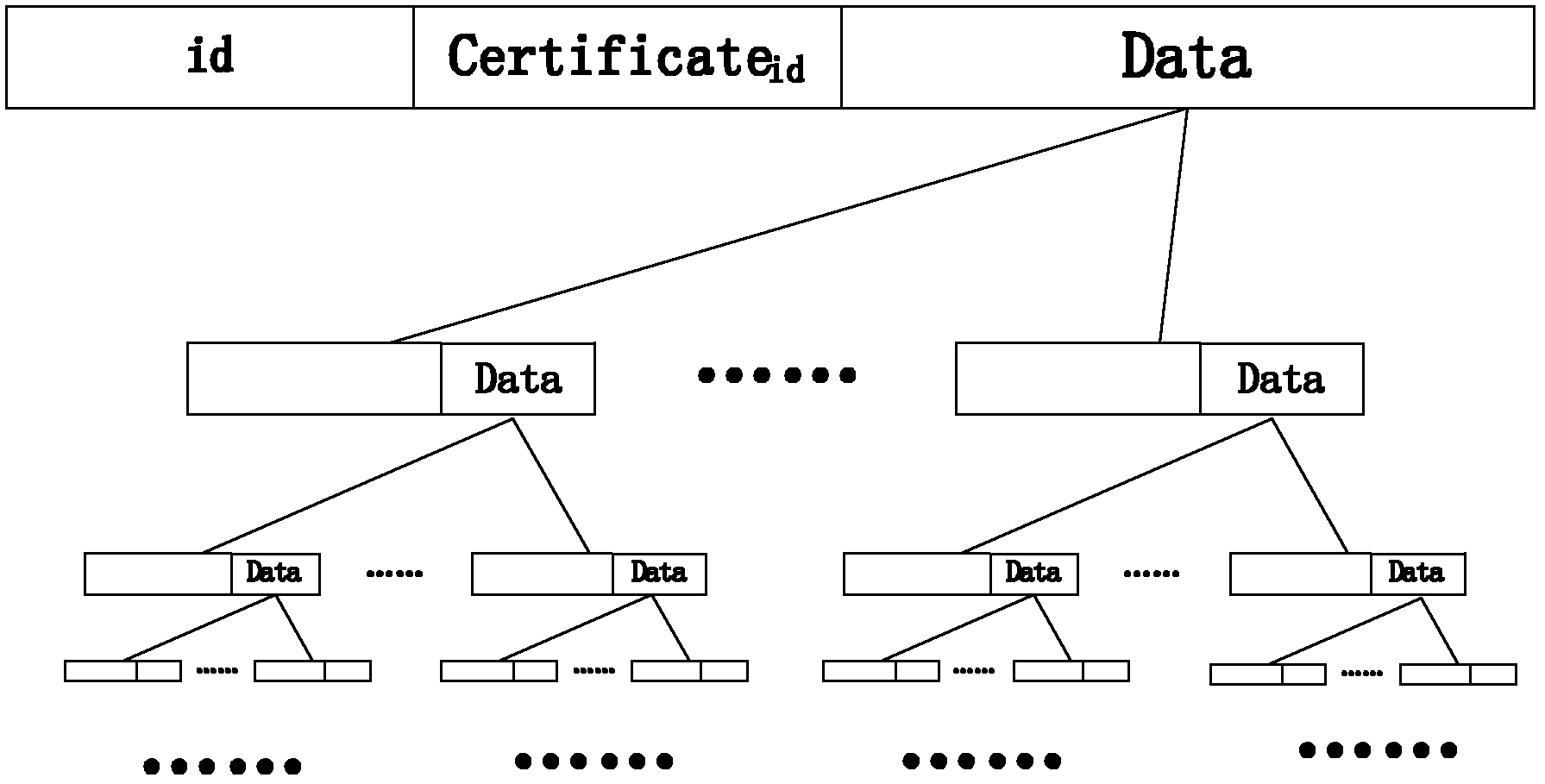
[0028] The whole technical solution includes three stages: the key pre-distribution stage, the whole network identity authentication stage, and the partial re-authentication stage. First, assign a unique authentication key to each node before node deployment, and store it in the base station. Afterwards, after the multi-level clustered wireless sensor network is formed, the identity authentication of the whole network is carried out. At this stage, the similarity of authentication information can be used to perform data compression and fusion well and reduce communication energy consumption. Finally, for the cluster heads whose identity authentication fails in the whole network, a new cluster head election is carried out in the corresponding cluster, and local re-authentication is carried out. This process can be repeated until all no...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com