Dynamic access control method of pervasive computing
An access control and pervasive computing technology, applied in digital transmission systems, electrical components, transmission systems, etc., can solve the problems of not considering unfamiliar subjects, access control, and not considering the characteristics of information space and physical space at the same time, so as to achieve simplification Authorization decision, effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] According to the hierarchical trust model, the present invention realizes dynamic access control by extending the role-based access control model.
[0039] The service provider evaluates the basic trust value T of the service requester a .
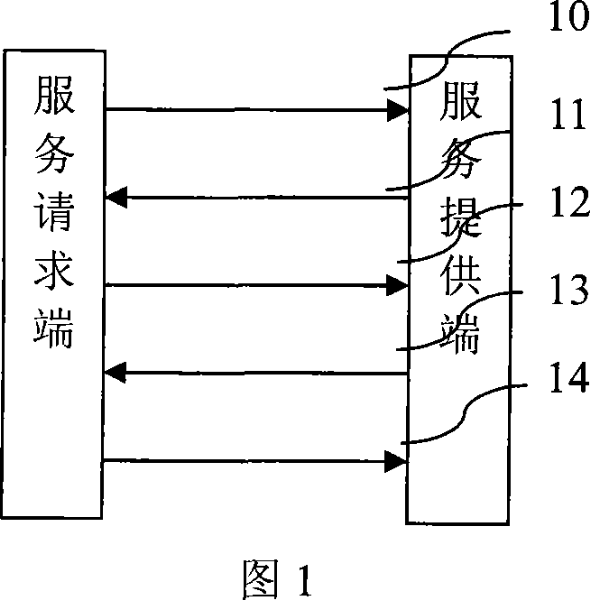
[0040] Trust value T a Formation Referring to Figure 1, the service requester initiates a service request 10; the service provider requires the service requester to provide some attributes 11 according to the trust policy of the accessed service; the service requester presents these attributes 12, or in order to protect its own sensitive attributes, Before presenting these attributes, the service provider needs to display certain attributes 13, and when its own attribute access policy is satisfied, the service requester provides attributes 14 to the other party.
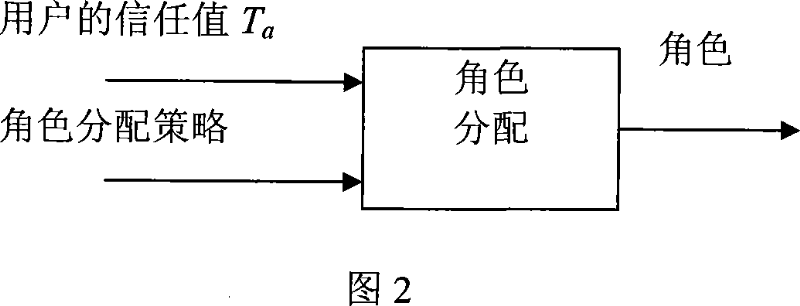
[0041] Subject-based trust value T a , the principal is assigned a set of roles.
[0042] Refer to Figure 2 for user role assignment, according to the user's trust val...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com